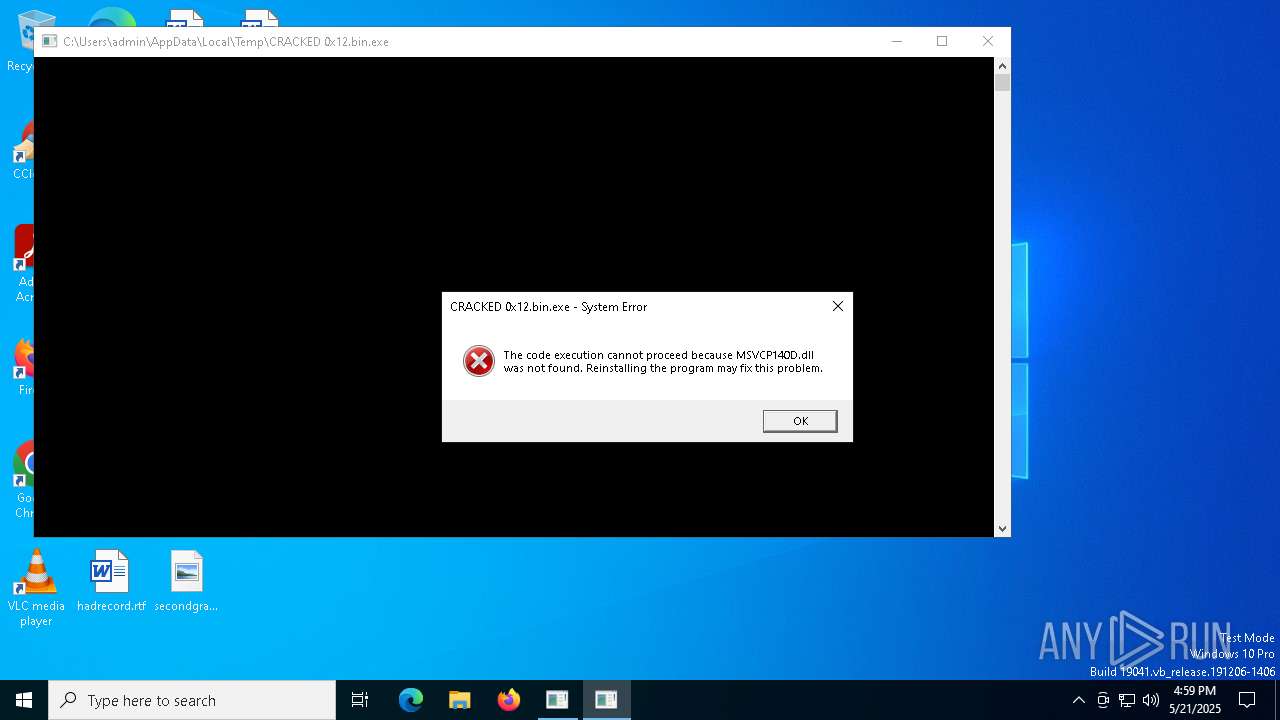
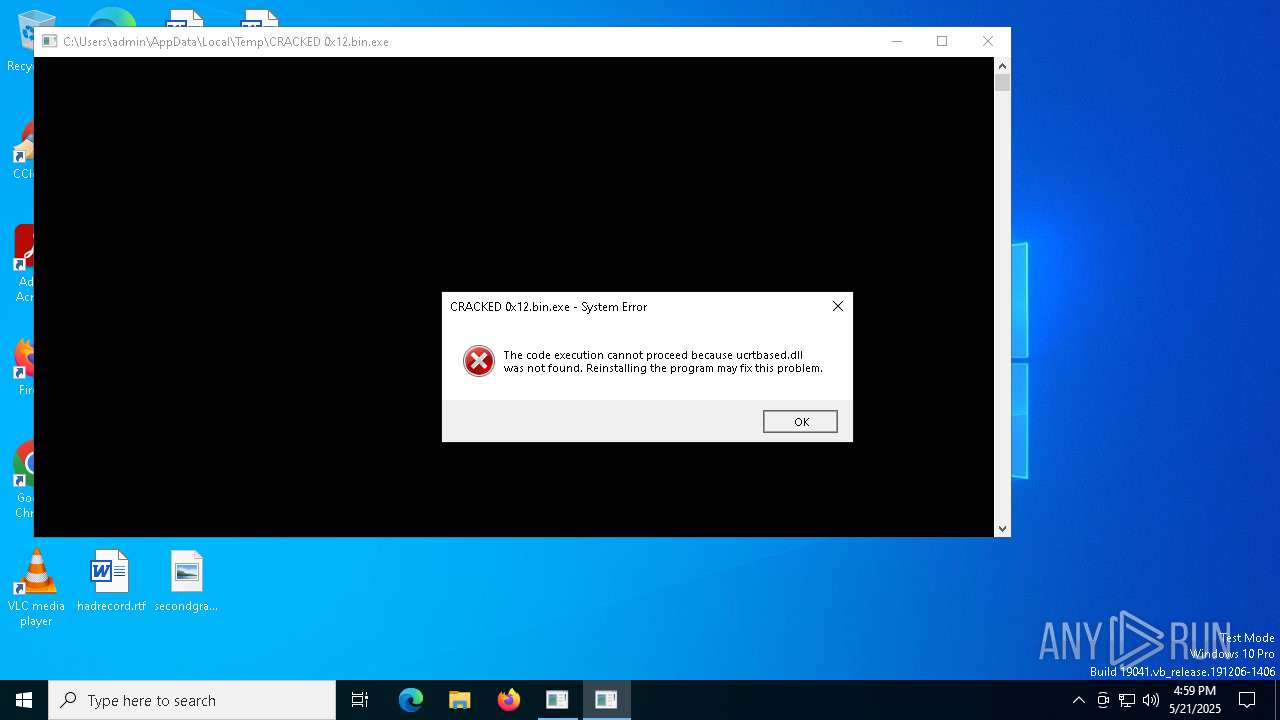
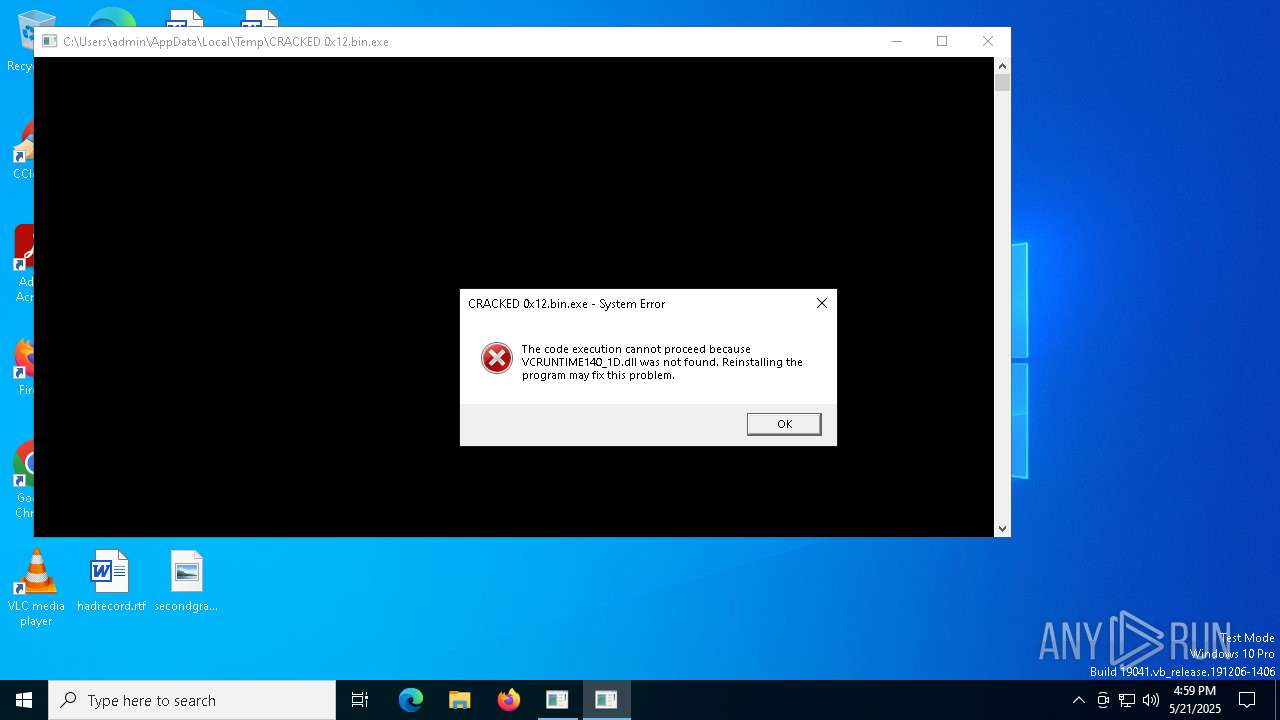
| File name: | CRACKED 0x12.bin |
| Full analysis: | https://app.any.run/tasks/6b3b82e5-5de0-463d-addc-e63730276b9f |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2025, 16:58:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 14 sections |
| MD5: | ED9277E5624DD90CC9501A29A457D7AF |
| SHA1: | 2BD6A4D1CDF03C4FE0D949E7D3FC0BFF1A6164AD |
| SHA256: | A1075671BE0FD3264B2DEB7803C46080E4427200A5CE1981C13DC24B49AFB352 |
| SSDEEP: | 98304:o4WdVp3QEIdMlumP2C3PQPHlZsifRNuS1hXbIj/c2l4nbFAniLsQ1ZNS7ONKrBOF:lF1wvJTv0R |
MALICIOUS
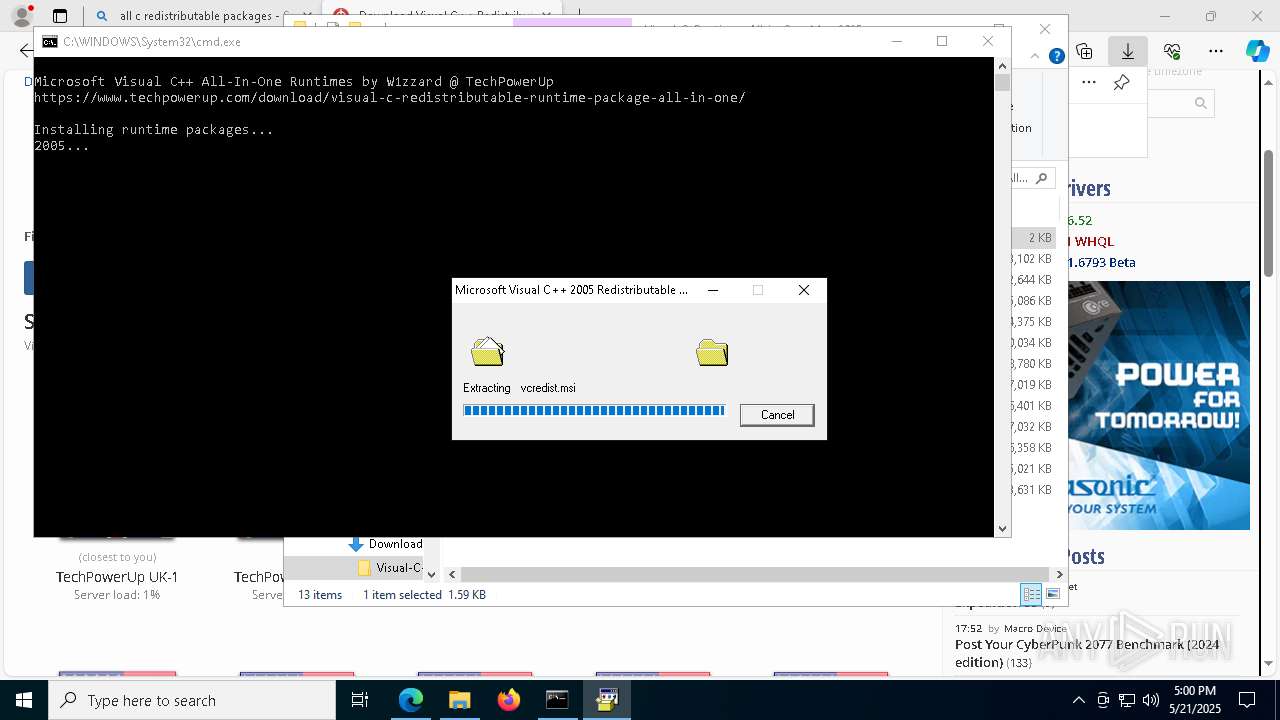
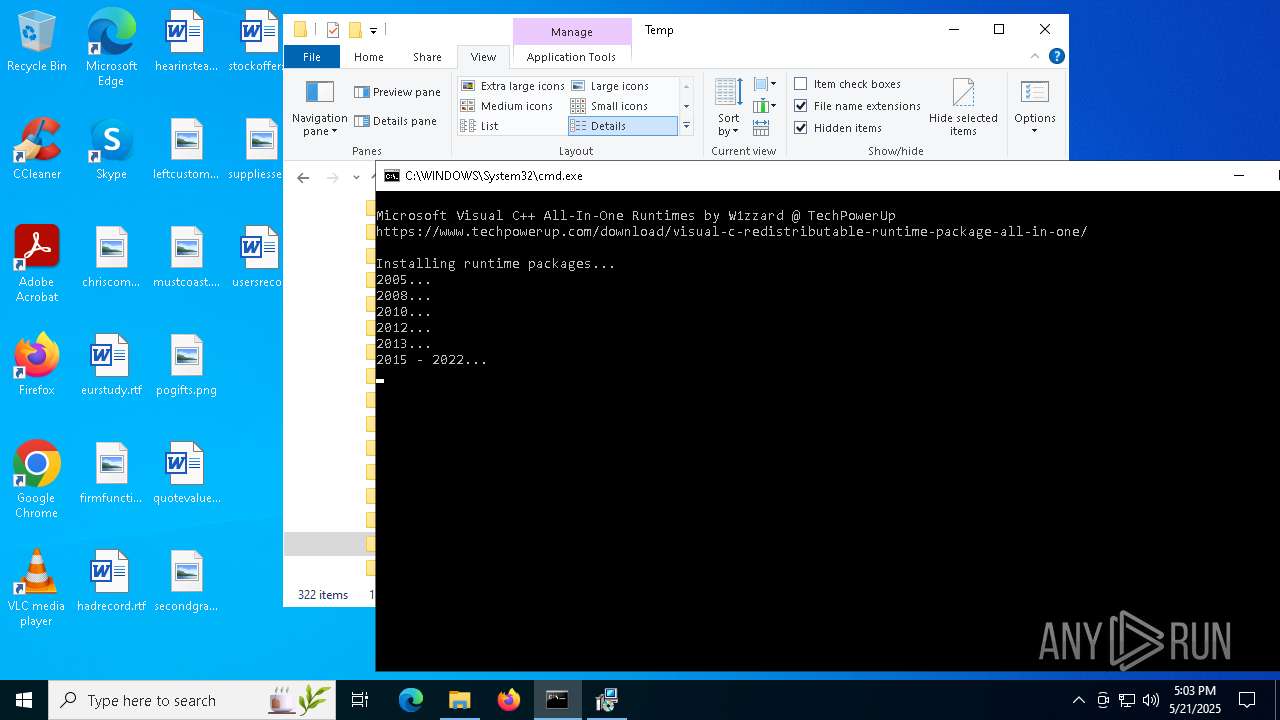
Executing a file with an untrusted certificate
- vcredist2005_x86.exe (PID: 6980)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2005_x64.exe (PID: 5720)
- install.exe (PID: 2104)
- vcredist2008_x64.exe (PID: 7704)
- install.exe (PID: 5776)
- vcredist2010_x86.exe (PID: 2340)
- Setup.exe (PID: 2108)
- vcredist2010_x64.exe (PID: 5116)
- Setup.exe (PID: 2664)
- vcredist2012_x86.exe (PID: 8092)
- vcredist2012_x86.exe (PID: 8016)
- vcredist2012_x64.exe (PID: 8160)
- vcredist2012_x64.exe (PID: 5544)
- vcredist2013_x86.exe (PID: 7852)
- vcredist2013_x86.exe (PID: 4016)
- vcredist2013_x64.exe (PID: 240)
- vcredist2013_x64.exe (PID: 2092)
SUSPICIOUS
Process drops legitimate windows executable
- msedge.exe (PID: 8004)
- msedge.exe (PID: 4008)
- WinRAR.exe (PID: 5172)
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- vcredist2012_x86.exe (PID: 8092)
- msiexec.exe (PID: 5172)
- vcredist2012_x64.exe (PID: 5544)
- vcredist2012_x86.exe (PID: 8016)
- vcredist2012_x64.exe (PID: 8160)
- vcredist2013_x86.exe (PID: 4016)
- vcredist2013_x86.exe (PID: 7852)
- vcredist2013_x64.exe (PID: 2092)
- vcredist2015_2017_2019_2022_x86.exe (PID: 5528)
- vcredist2015_2017_2019_2022_x86.exe (PID: 7292)
- VC_redist.x86.exe (PID: 7564)
- vcredist2013_x64.exe (PID: 240)
- VC_redist.x86.exe (PID: 6456)
- vcredist2015_2017_2019_2022_x64.exe (PID: 5488)
- vcredist2015_2017_2019_2022_x64.exe (PID: 6476)
- VC_redist.x64.exe (PID: 7172)
- VC_redist.x64.exe (PID: 6392)
Executable content was dropped or overwritten
- vcredist2005_x86.exe (PID: 6980)
- TiWorker.exe (PID: 7592)
- vcredist2005_x64.exe (PID: 5720)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- vcredist2012_x86.exe (PID: 8016)
- vcredist2012_x86.exe (PID: 8092)
- vcredist2012_x64.exe (PID: 8160)
- vcredist2012_x64.exe (PID: 5544)
- vcredist2013_x86.exe (PID: 4016)
- vcredist2013_x86.exe (PID: 7852)
- vcredist2013_x64.exe (PID: 240)
- vcredist2015_2017_2019_2022_x86.exe (PID: 5528)
- VC_redist.x86.exe (PID: 4024)
- vcredist2015_2017_2019_2022_x86.exe (PID: 7292)
- VC_redist.x86.exe (PID: 7564)
- vcredist2013_x64.exe (PID: 2092)
- vcredist2015_2017_2019_2022_x64.exe (PID: 6476)
- vcredist2015_2017_2019_2022_x64.exe (PID: 5488)
- VC_redist.x64.exe (PID: 7172)
- VC_redist.x64.exe (PID: 8140)
- VC_redist.x86.exe (PID: 6456)
- VC_redist.x64.exe (PID: 6392)
Executes as Windows Service
- VSSVC.exe (PID: 5204)
The process drops C-runtime libraries
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2010_x86.exe (PID: 2340)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
Application launched itself
- vcredist2012_x86.exe (PID: 8092)
- vcredist2012_x64.exe (PID: 8160)
- vcredist2013_x86.exe (PID: 7852)
- vcredist2013_x64.exe (PID: 2092)
- VC_redist.x86.exe (PID: 6700)
- VC_redist.x64.exe (PID: 5556)
- VC_redist.x86.exe (PID: 4024)
- VC_redist.x64.exe (PID: 8140)
Starts a Microsoft application from unusual location
- vcredist2015_2017_2019_2022_x86.exe (PID: 7292)
- VC_redist.x86.exe (PID: 7564)
- VC_redist.x64.exe (PID: 7172)
- vcredist2015_2017_2019_2022_x64.exe (PID: 6476)
Starts itself from another location
- vcredist2015_2017_2019_2022_x86.exe (PID: 7292)
- vcredist2015_2017_2019_2022_x64.exe (PID: 6476)
INFO
Reads Environment values
- identity_helper.exe (PID: 2152)
Checks supported languages
- identity_helper.exe (PID: 2152)
Manual execution by a user
- msedge.exe (PID: 8004)
- WinRAR.exe (PID: 5172)
- cmd.exe (PID: 6184)
- CRACKED 0x12.bin.exe (PID: 4016)
- CRACKED 0x12.bin.exe (PID: 5328)
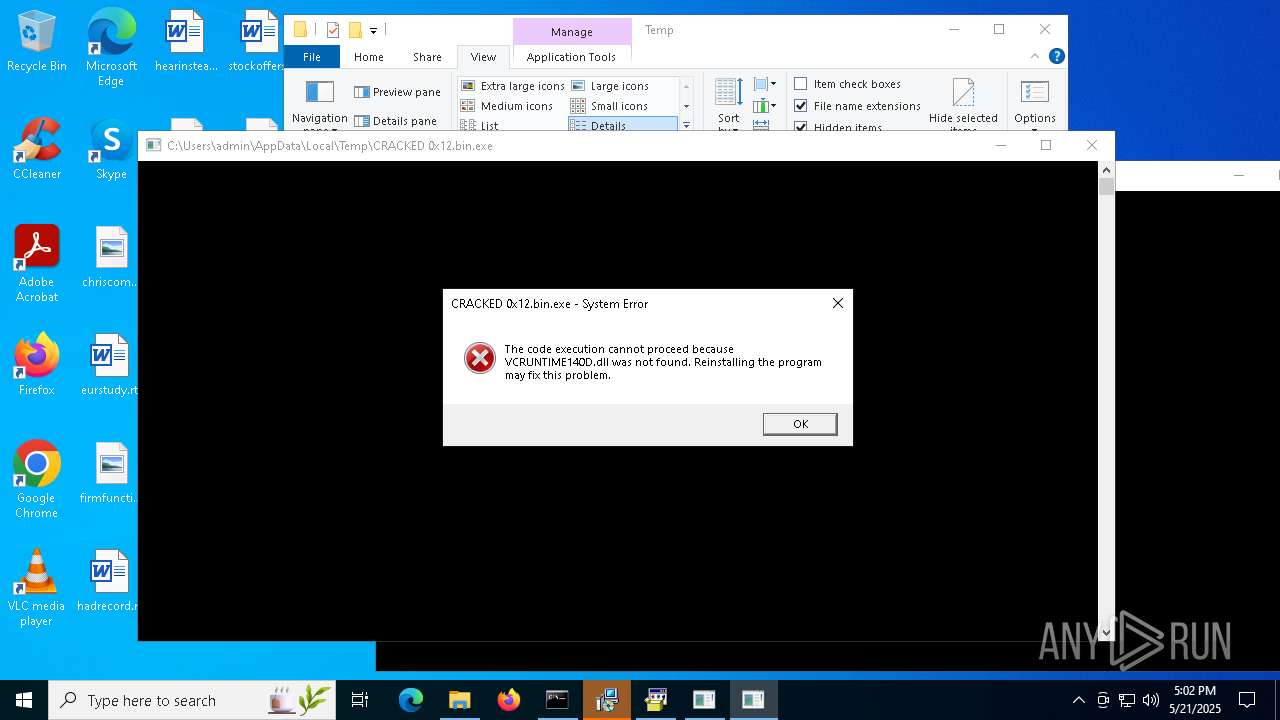
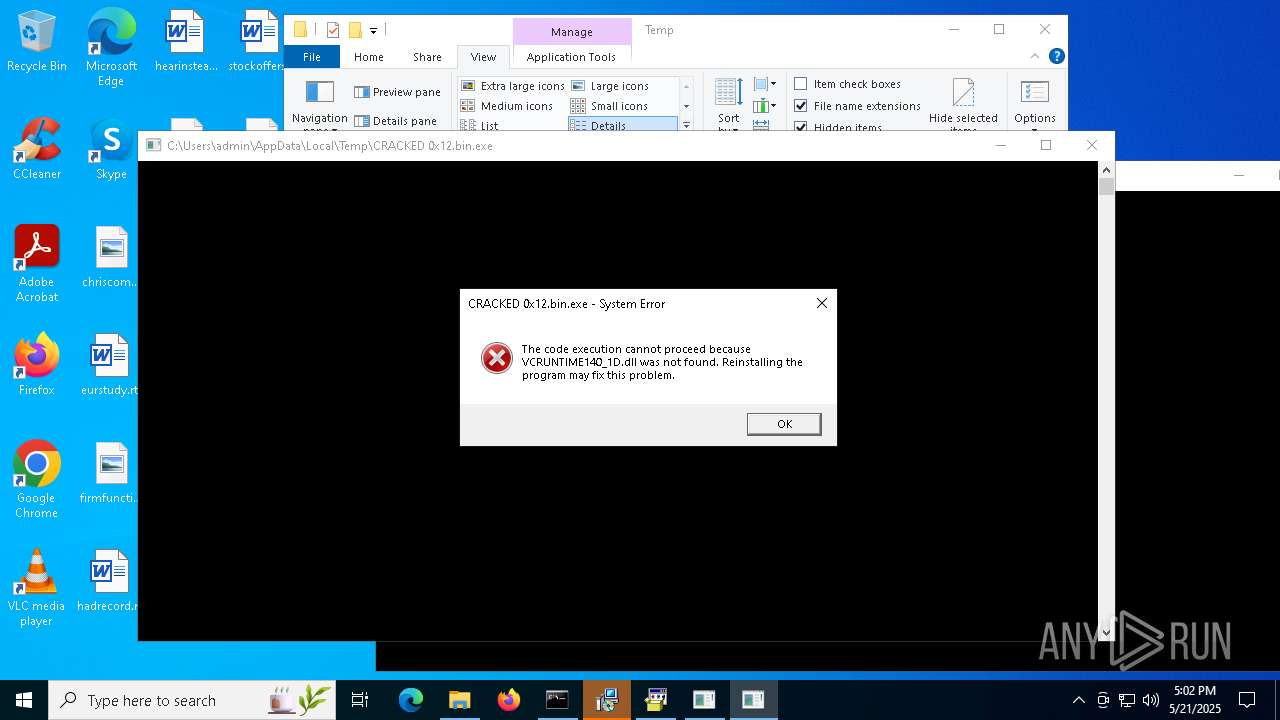
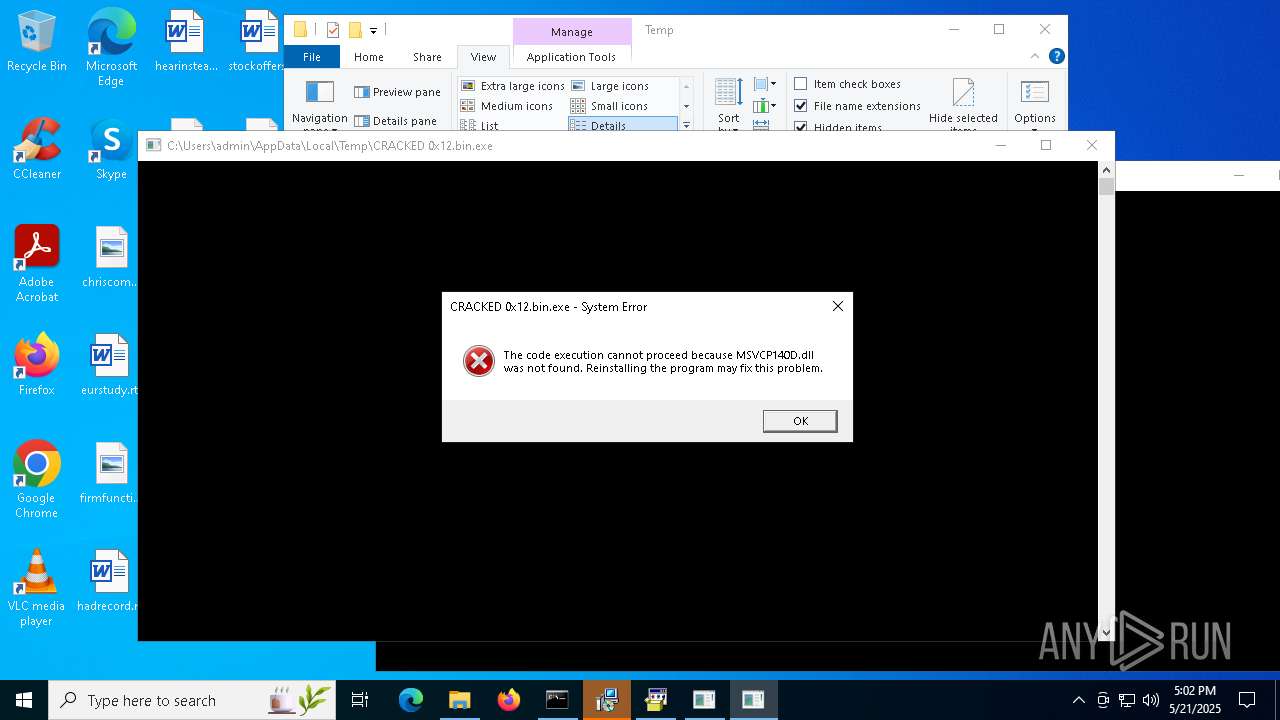
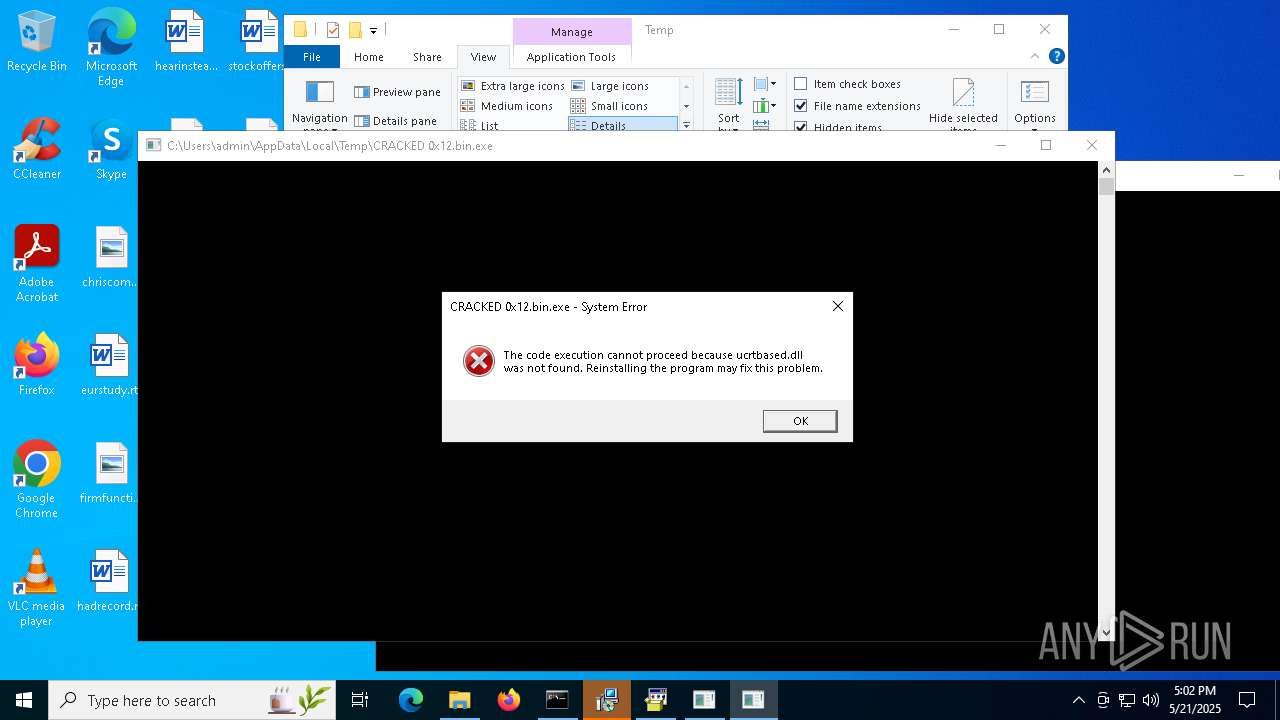
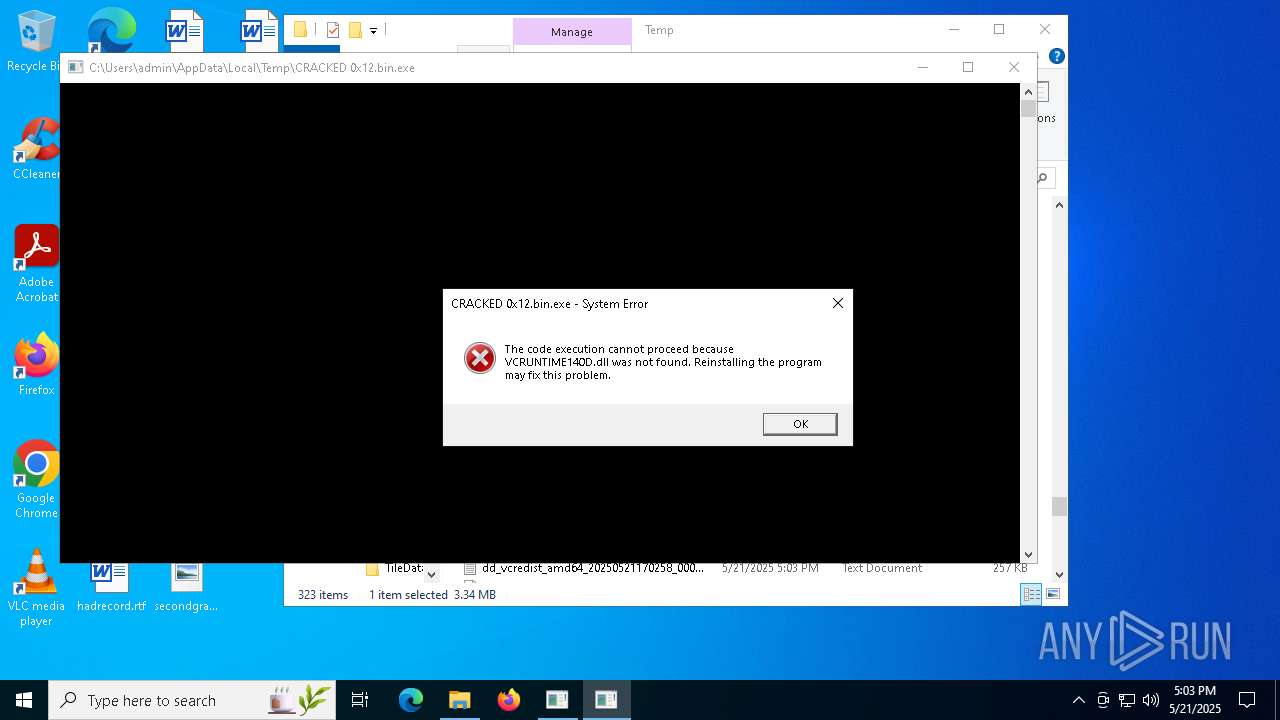
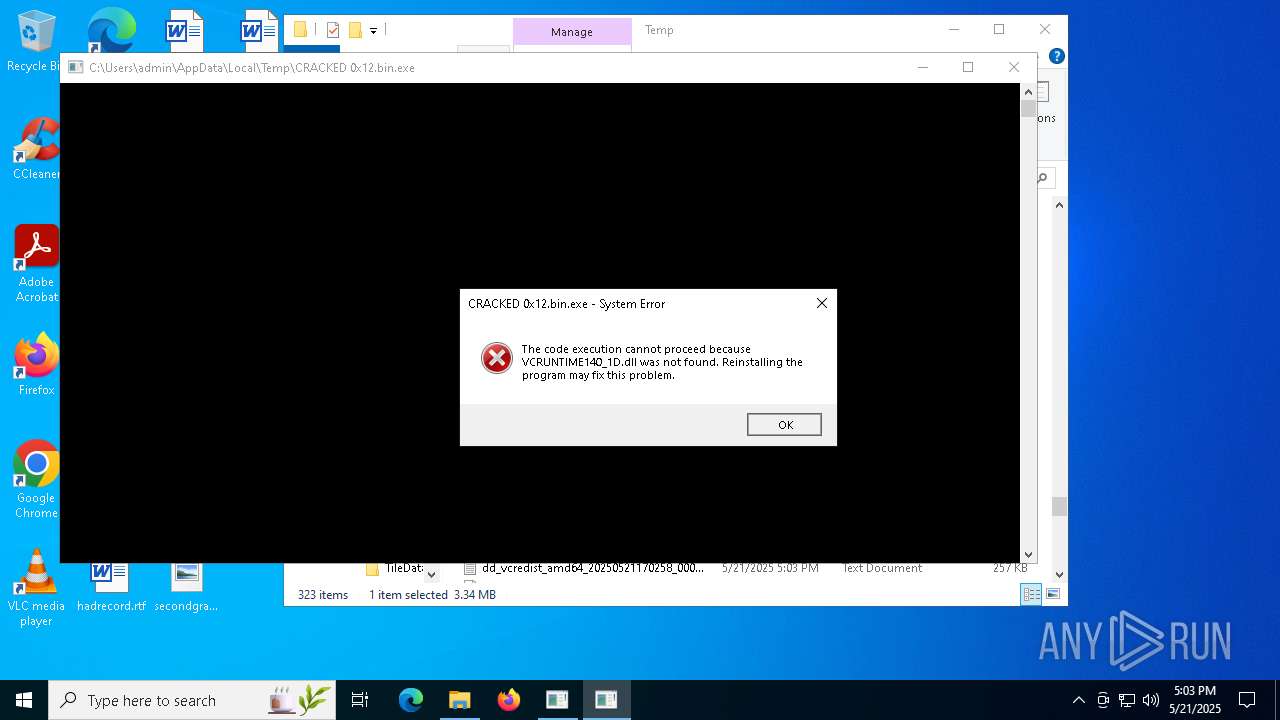
Themida protector has been detected
- CRACKED 0x12.bin.exe (PID: 7360)
The sample compiled with english language support
- msedge.exe (PID: 8004)
- msedge.exe (PID: 4008)
- WinRAR.exe (PID: 5172)
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- vcredist2012_x86.exe (PID: 8092)
- msiexec.exe (PID: 5172)
- vcredist2012_x86.exe (PID: 8016)
- vcredist2012_x64.exe (PID: 5544)
- vcredist2013_x86.exe (PID: 4016)
- vcredist2012_x64.exe (PID: 8160)
- vcredist2013_x86.exe (PID: 7852)
- vcredist2013_x64.exe (PID: 2092)
- vcredist2015_2017_2019_2022_x86.exe (PID: 5528)
- vcredist2015_2017_2019_2022_x86.exe (PID: 7292)
- VC_redist.x86.exe (PID: 7564)
- VC_redist.x86.exe (PID: 4024)
- vcredist2013_x64.exe (PID: 240)
- VC_redist.x86.exe (PID: 6456)
- vcredist2015_2017_2019_2022_x64.exe (PID: 5488)
- vcredist2015_2017_2019_2022_x64.exe (PID: 6476)
- VC_redist.x64.exe (PID: 7172)
- VC_redist.x64.exe (PID: 8140)
- VC_redist.x64.exe (PID: 6392)
Application launched itself
- msedge.exe (PID: 8004)
- msedge.exe (PID: 3272)
Reads the computer name
- identity_helper.exe (PID: 2152)
Reads the software policy settings
- slui.exe (PID: 7484)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5172)
- msiexec.exe (PID: 6708)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
Manages system restore points
- SrTasks.exe (PID: 7768)
- SrTasks.exe (PID: 8088)
- SrTasks.exe (PID: 5200)
- SrTasks.exe (PID: 5020)
The sample compiled with chinese language support
- TiWorker.exe (PID: 7592)
- msiexec.exe (PID: 6708)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with german language support
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with spanish language support
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with french language support
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with Italian language support
- msiexec.exe (PID: 6708)
- vcredist2008_x86.exe (PID: 4428)
- TiWorker.exe (PID: 7592)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with japanese language support
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with korean language support
- msiexec.exe (PID: 6708)
- TiWorker.exe (PID: 7592)
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
The sample compiled with russian language support
- vcredist2008_x86.exe (PID: 4428)
- vcredist2008_x64.exe (PID: 7704)
- TiWorker.exe (PID: 7592)
- msiexec.exe (PID: 6708)
- vcredist2010_x86.exe (PID: 2340)
- vcredist2010_x64.exe (PID: 5116)
- msiexec.exe (PID: 6036)
- msiexec.exe (PID: 5172)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:05:20 19:44:36+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.44 |
| CodeSize: | 68096 |
| InitializedDataSize: | 35840 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5dc058 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
283
Monitored processes
137
Malicious processes
18
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | "C:\Users\admin\Downloads\Visual-C-Runtimes-All-in-One-May-2025\vcredist2013_x64.exe" /passive /norestart -burn.unelevated BurnPipe.{BEB414CC-7F3B-408E-9DCC-0BD502242F66} {B98716E1-7D94-4A5D-A366-ECF259069ED9} 2092 | C:\Users\admin\Downloads\Visual-C-Runtimes-All-in-One-May-2025\vcredist2013_x64.exe | vcredist2013_x64.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.40664 Exit code: 0 Version: 12.0.40664.0 Modules
| |||||||||||||||
| 456 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6356 --field-trial-handle=2412,i,4084386824045126842,15178595608387879383,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 668 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5544 --field-trial-handle=2412,i,4084386824045126842,15178595608387879383,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 736 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6520 --field-trial-handle=2484,i,3787770228196479246,817462445825041942,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 896 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --extension-process --renderer-sub-type=extension --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=4136 --field-trial-handle=2484,i,3787770228196479246,817462445825041942,262144 --variations-seed-version /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 928 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --no-appcompat-clear --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=17 --mojo-platform-channel-handle=4292 --field-trial-handle=2412,i,4084386824045126842,15178595608387879383,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1272 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1272 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5992 --field-trial-handle=2412,i,4084386824045126842,15178595608387879383,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1276 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4256 --field-trial-handle=2412,i,4084386824045126842,15178595608387879383,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1300 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=4036 --field-trial-handle=2412,i,4084386824045126842,15178595608387879383,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
100 217
Read events
92 114
Write events
6 784
Delete events
1 319
Modification events
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 011EF8913E942F00 | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BCACF1913E942F00 | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {168A5896-234C-46AE-B126-2CE23BC8D295} | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {31DE9989-0FC2-45A4-BF47-28F5A96B32B4} | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {60DA8FEC-0E5C-4F16-9496-BAF289D0CAE4} | |||
| (PID) Process: | (8004) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328396 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {FC244F1F-7E2C-4BF0-A20C-40E0D3B632DC} | |||
Executable files
719
Suspicious files
1 282
Text files
741
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF110c32.TMP | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF110c42.TMP | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF110c42.TMP | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF110c42.TMP | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF110c51.TMP | — | |
MD5:— | SHA256:— | |||
| 8004 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
41
TCP/UDP connections
179
DNS requests
161
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.16.241.19:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7672 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7672 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5048 | svchost.exe | HEAD | 200 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1748292395&P2=404&P3=2&P4=n5PV40GkvHIOFpf7udE9ijzN331PJL9xJIpDBf92uDN6ppEIdnoLBsHhFxQ52fUkI62qHZG0ubenuT0RJX2lYA%3d%3d | unknown | — | — | whitelisted |
5048 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1748292395&P2=404&P3=2&P4=n5PV40GkvHIOFpf7udE9ijzN331PJL9xJIpDBf92uDN6ppEIdnoLBsHhFxQ52fUkI62qHZG0ubenuT0RJX2lYA%3d%3d | unknown | — | — | whitelisted |
5048 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/bf8090eb-6e5c-4c51-9250-5bf9b46cf160?P1=1748292395&P2=404&P3=2&P4=n5PV40GkvHIOFpf7udE9ijzN331PJL9xJIpDBf92uDN6ppEIdnoLBsHhFxQ52fUkI62qHZG0ubenuT0RJX2lYA%3d%3d | unknown | — | — | whitelisted |
5048 | svchost.exe | HEAD | 200 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1748292395&P2=404&P3=2&P4=Flu6byWJk66kjGpd3Orc78RvfiKK7QANTfQjpJDWcFYYn8X1gTC7gA3t4OGtCaclMjXI%2bHNrP92mexIRTxhLGQ%3d%3d | unknown | — | — | whitelisted |
5048 | svchost.exe | GET | 206 | 208.89.74.23:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1748292395&P2=404&P3=2&P4=Flu6byWJk66kjGpd3Orc78RvfiKK7QANTfQjpJDWcFYYn8X1gTC7gA3t4OGtCaclMjXI%2bHNrP92mexIRTxhLGQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.16.241.19:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|