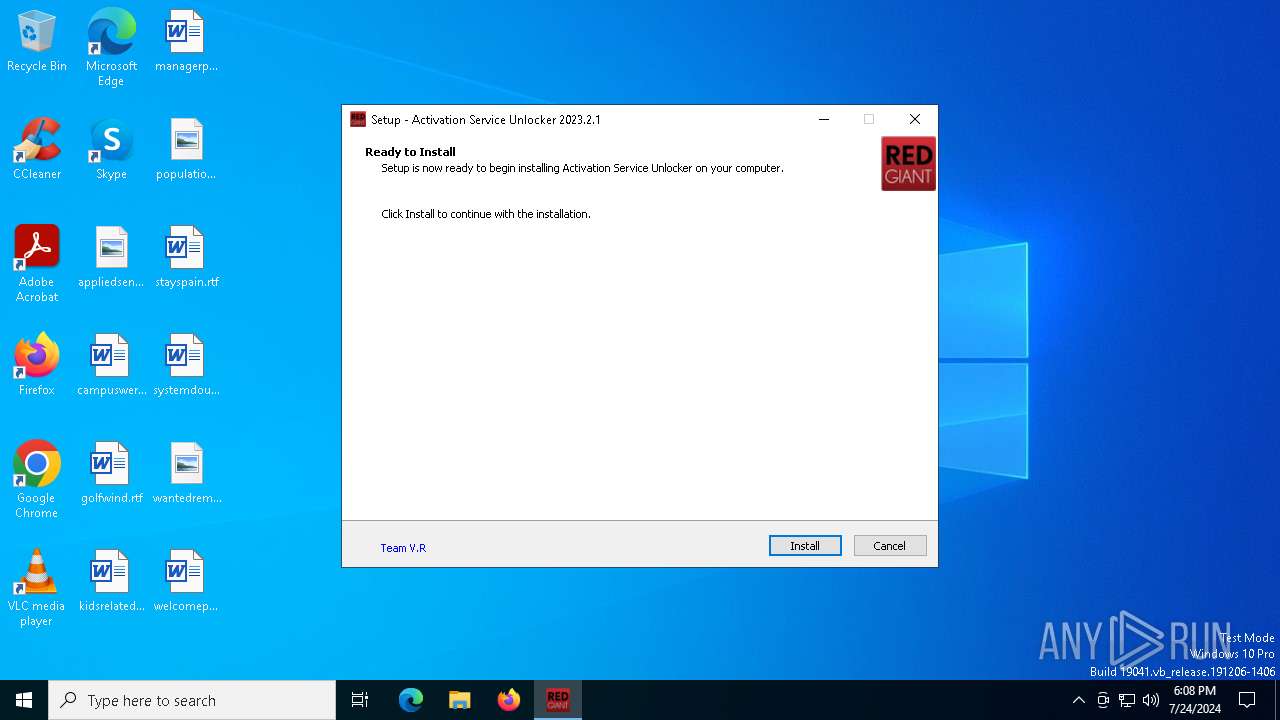
| File name: | RedGiant Activation Service Unlocker 2023.2.1.exe |
| Full analysis: | https://app.any.run/tasks/f43c0762-2e0c-4c12-81e2-54a0abc25b58 |
| Verdict: | Malicious activity |
| Analysis date: | July 24, 2024, 18:07:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | EF86450CA1EF20A87F9B3297AA8BB8E8 |
| SHA1: | DA5D2A3D72B1863B747F7B5148F65B7939C5F28C |
| SHA256: | A0FB2DD97975F0E746CC5C2FB2CB30D980CAD135D3F4F7237B8324E0831AE7AF |
| SSDEEP: | 98304:MkLTpSZNWOn2F8IXgtSUg4cHprsrRmGS/kegYIiWrhOvmtZ45cYJkO0tI4NzFo:r0ZN9k8IXWpcHOYk5iWJtZmet3NzFo |
MALICIOUS
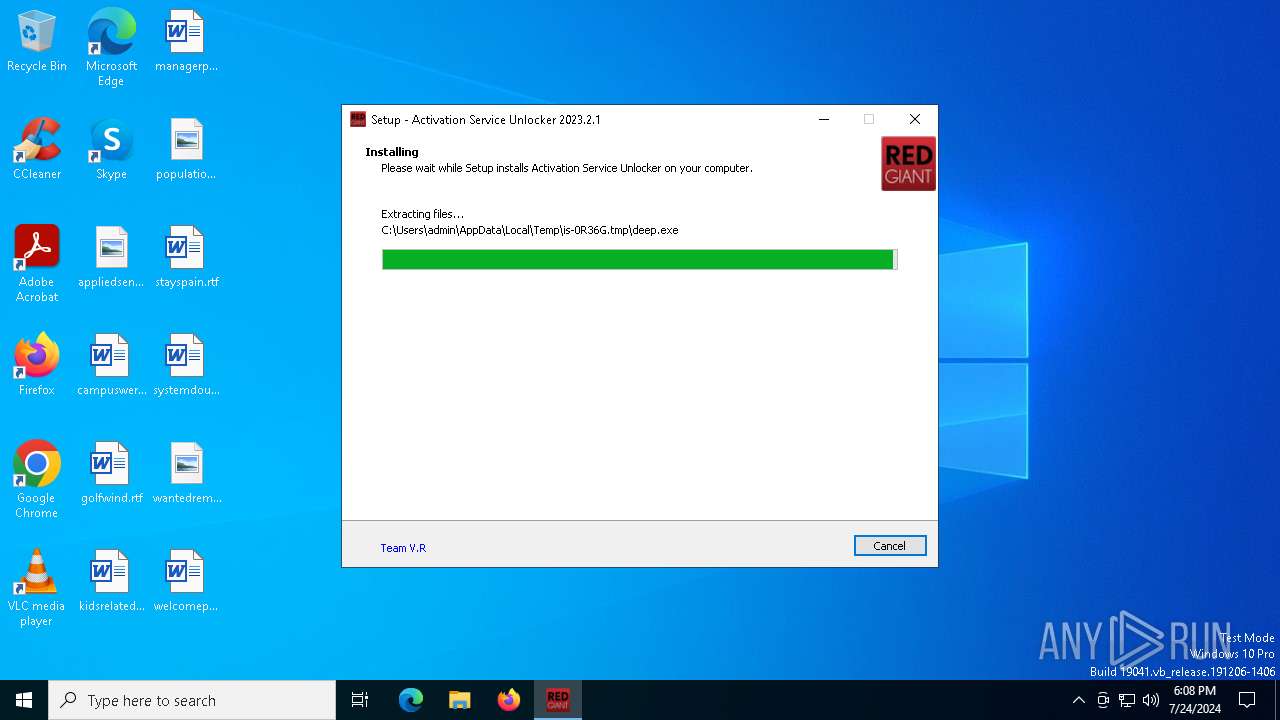
Drops the executable file immediately after the start
- RedGiant Activation Service Unlocker 2023.2.1.exe (PID: 3140)
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.exe (PID: 6332)
- deep.tmp (PID: 6616)
Starts NET.EXE for service management
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- net.exe (PID: 256)
- net.exe (PID: 6328)
- net.exe (PID: 7124)
SUSPICIOUS
Reads the Windows owner or organization settings
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.tmp (PID: 6616)
Executable content was dropped or overwritten
- RedGiant Activation Service Unlocker 2023.2.1.exe (PID: 3140)
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.exe (PID: 6332)
- deep.tmp (PID: 6616)
Uses TIMEOUT.EXE to delay execution
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
Uses TASKKILL.EXE to kill process
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.tmp (PID: 6616)
INFO
Create files in a temporary directory
- RedGiant Activation Service Unlocker 2023.2.1.exe (PID: 3140)
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.exe (PID: 6332)
- deep.tmp (PID: 6616)
Checks supported languages
- RedGiant Activation Service Unlocker 2023.2.1.exe (PID: 3140)
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.exe (PID: 6332)
- deep.tmp (PID: 6616)
- TextInputHost.exe (PID: 3560)
Reads the computer name
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.tmp (PID: 6616)
- TextInputHost.exe (PID: 3560)
Creates files in the program directory
- RedGiant Activation Service Unlocker 2023.2.1.tmp (PID: 3328)
- deep.tmp (PID: 6616)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (51.8) |
|---|---|---|
| .exe | | | InstallShield setup (20.3) |
| .exe | | | Win32 EXE PECompact compressed (generic) (19.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (3.1) |
| .exe | | | Win32 Executable (generic) (2.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:02:15 14:54:16+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 741888 |
| InitializedDataSize: | 57344 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xb5eec |
| OSVersion: | 6.1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2023.2.1.0 |
| ProductVersionNumber: | 2023.2.1.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | Red Giant, LLC |
| FileDescription: | Activation Service Unlocker Setup |
| FileVersion: | 2023.2.1 |
| LegalCopyright: | © Red Giant LLC |
| OriginalFileName: | |
| ProductName: | Activation Service Unlocker |
| ProductVersion: | 2023.2.1 |
Total processes
148
Monitored processes
23
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 256 | "C:\WINDOWS\system32\net.exe" stop mxredirect | C:\Windows\System32\net.exe | — | RedGiant Activation Service Unlocker 2023.2.1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1912 | "C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2023.2.1.exe" | C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2023.2.1.exe | — | explorer.exe | |||||||||||
User: admin Company: Red Giant, LLC Integrity Level: MEDIUM Description: Activation Service Unlocker Setup Exit code: 3221226540 Version: 2023.2.1 Modules
| |||||||||||||||
| 2120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | taskkill.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2708 | "C:\WINDOWS\system32\taskkill.exe" /f /im "MxNotify.exe" | C:\Windows\System32\taskkill.exe | — | RedGiant Activation Service Unlocker 2023.2.1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3140 | "C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2023.2.1.exe" | C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2023.2.1.exe | explorer.exe | ||||||||||||
User: admin Company: Red Giant, LLC Integrity Level: HIGH Description: Activation Service Unlocker Setup Exit code: 0 Version: 2023.2.1 Modules
| |||||||||||||||
| 3220 | C:\WINDOWS\system32\net1 stop mxredirect | C:\Windows\System32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3328 | "C:\Users\admin\AppData\Local\Temp\is-MHQSO.tmp\RedGiant Activation Service Unlocker 2023.2.1.tmp" /SL5="$301D4,4765645,800256,C:\Users\admin\AppData\Local\Temp\RedGiant Activation Service Unlocker 2023.2.1.exe" | C:\Users\admin\AppData\Local\Temp\is-MHQSO.tmp\RedGiant Activation Service Unlocker 2023.2.1.tmp | RedGiant Activation Service Unlocker 2023.2.1.exe | ||||||||||||
User: admin Company: Red Giant, LLC Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3560 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 3968 | "C:\WINDOWS\system32\taskkill.exe" /f /im "RGContentService.exe" | C:\Windows\System32\taskkill.exe | — | RedGiant Activation Service Unlocker 2023.2.1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 432
Read events
3 408
Write events
12
Delete events
12
Modification events
| (PID) Process: | (3328) RedGiant Activation Service Unlocker 2023.2.1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 000D0000EF8B0377F4DDDA01 | |||
| (PID) Process: | (3328) RedGiant Activation Service Unlocker 2023.2.1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 0BC4DD0F41D878AA433A6440BB8BE3677D25CCB6C5F5F570F03EDE3A4D99767F | |||
| (PID) Process: | (3328) RedGiant Activation Service Unlocker 2023.2.1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (3328) RedGiant Activation Service Unlocker 2023.2.1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Users\admin\AppData\Local\Temp\is-0R36G.tmp\deep.exe | |||
| (PID) Process: | (3328) RedGiant Activation Service Unlocker 2023.2.1.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: BFDB79F4D6F2EA8D6984B10FE1E176DF7978393F94199F14701ACBED3721171D | |||
| (PID) Process: | (6616) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Owner |
Value: D81900006B666B7DF4DDDA01 | |||
| (PID) Process: | (6616) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | SessionHash |
Value: 9EF8C8540371715325DD02A1256850D2AF1F4886BC28B9DEA55E254B2F6BCD6B | |||
| (PID) Process: | (6616) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (6616) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Program Files\Red Giant\Services\Red Giant Service.exe | |||
| (PID) Process: | (6616) deep.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\RestartManager\Session0001 |
| Operation: | write | Name: | RegFilesHash |
Value: 599063CE0EB7D29C448A682E0A58D3AA138D90043407EE9F64A101D9185B6829 | |||
Executable files
10
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3328 | RedGiant Activation Service Unlocker 2023.2.1.tmp | C:\ProgramData\Maxon\RLM\vr.lic | text | |
MD5:683896C6A48196B6597116AA99823530 | SHA256:63931D59B463CECA304853DE2E6C68526F975D6B530EFB17A98801896C412F56 | |||
| 3328 | RedGiant Activation Service Unlocker 2023.2.1.tmp | C:\ProgramData\Maxon\RLM\is-RQH9V.tmp | text | |
MD5:683896C6A48196B6597116AA99823530 | SHA256:63931D59B463CECA304853DE2E6C68526F975D6B530EFB17A98801896C412F56 | |||
| 3140 | RedGiant Activation Service Unlocker 2023.2.1.exe | C:\Users\admin\AppData\Local\Temp\is-MHQSO.tmp\RedGiant Activation Service Unlocker 2023.2.1.tmp | executable | |
MD5:477C6F63CC670107DC6E58BADFDC5845 | SHA256:95CEBCC405540FDFE59FE4EC0B86D809C31109BC13DACB7F83FC8E1F423CDA40 | |||
| 6616 | deep.tmp | C:\Users\admin\AppData\Local\Temp\is-JQLAJ.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 3328 | RedGiant Activation Service Unlocker 2023.2.1.tmp | C:\Users\admin\AppData\Local\Temp\is-0R36G.tmp\_isetup\_iscrypt.dll | executable | |
MD5:A69559718AB506675E907FE49DEB71E9 | SHA256:2F6294F9AA09F59A574B5DCD33BE54E16B39377984F3D5658CDA44950FA0F8FC | |||
| 6616 | deep.tmp | C:\Users\admin\AppData\Local\Temp\is-JQLAJ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6332 | deep.exe | C:\Users\admin\AppData\Local\Temp\is-GLG3I.tmp\deep.tmp | executable | |
MD5:477C6F63CC670107DC6E58BADFDC5845 | SHA256:95CEBCC405540FDFE59FE4EC0B86D809C31109BC13DACB7F83FC8E1F423CDA40 | |||
| 3328 | RedGiant Activation Service Unlocker 2023.2.1.tmp | C:\Users\admin\AppData\Local\Temp\is-0R36G.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 6616 | deep.tmp | C:\Program Files\Red Giant\Services\Red Giant Service.exe | executable | |
MD5:AC3F9AF7109D3EC3CE5C008601C5016C | SHA256:AFB134CDF3A3D34235AD7C5EA5FA27B7C9184C16CC5626DB0E930EDC51A079BF | |||
| 6616 | deep.tmp | C:\Program Files\Red Giant\Services\is-IB6MD.tmp | executable | |
MD5:AC3F9AF7109D3EC3CE5C008601C5016C | SHA256:AFB134CDF3A3D34235AD7C5EA5FA27B7C9184C16CC5626DB0E930EDC51A079BF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
51
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5368 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 92.122.215.99:443 | — | Akamai International B.V. | DE | unknown |
— | — | 4.208.221.206:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1156 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5368 | SearchApp.exe | 104.126.37.163:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |