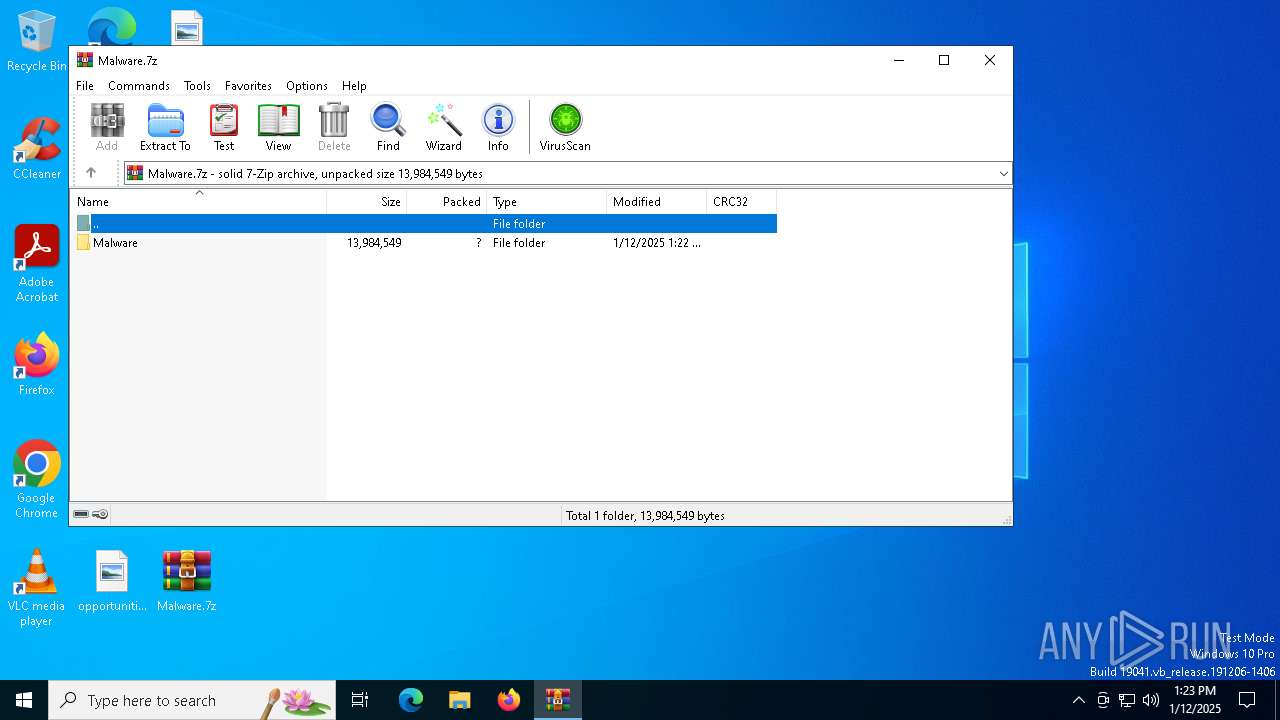
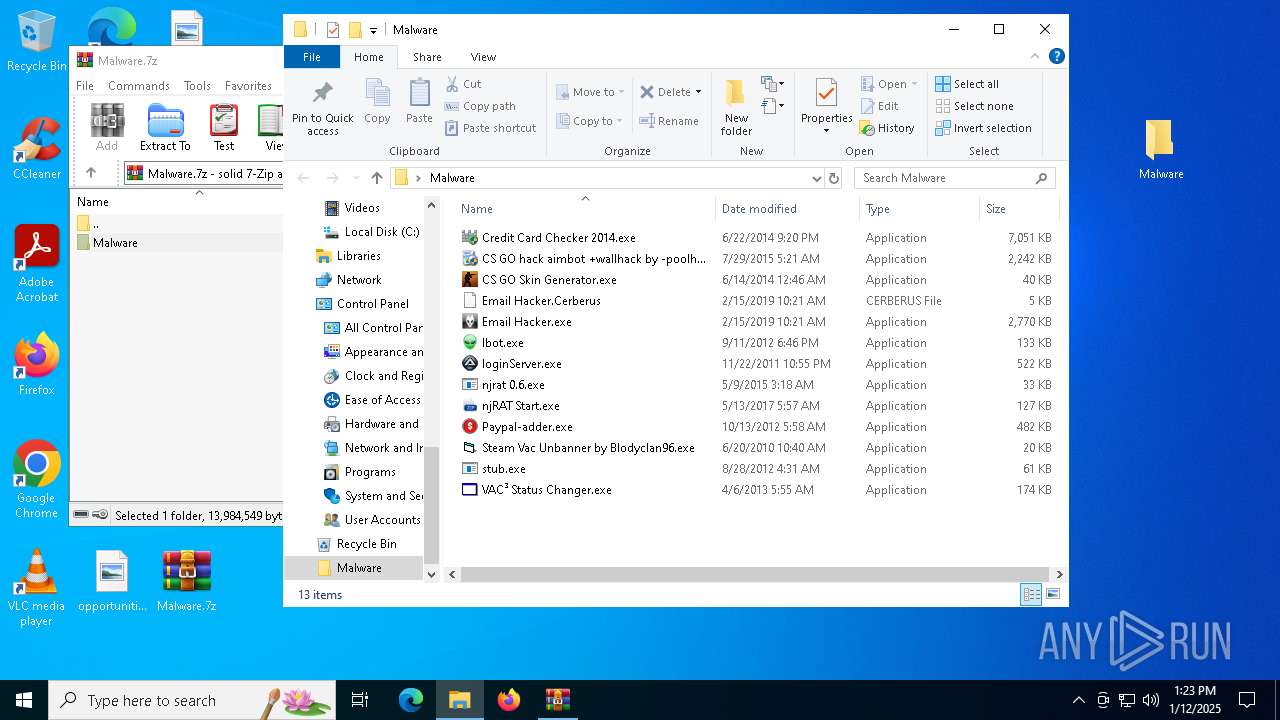
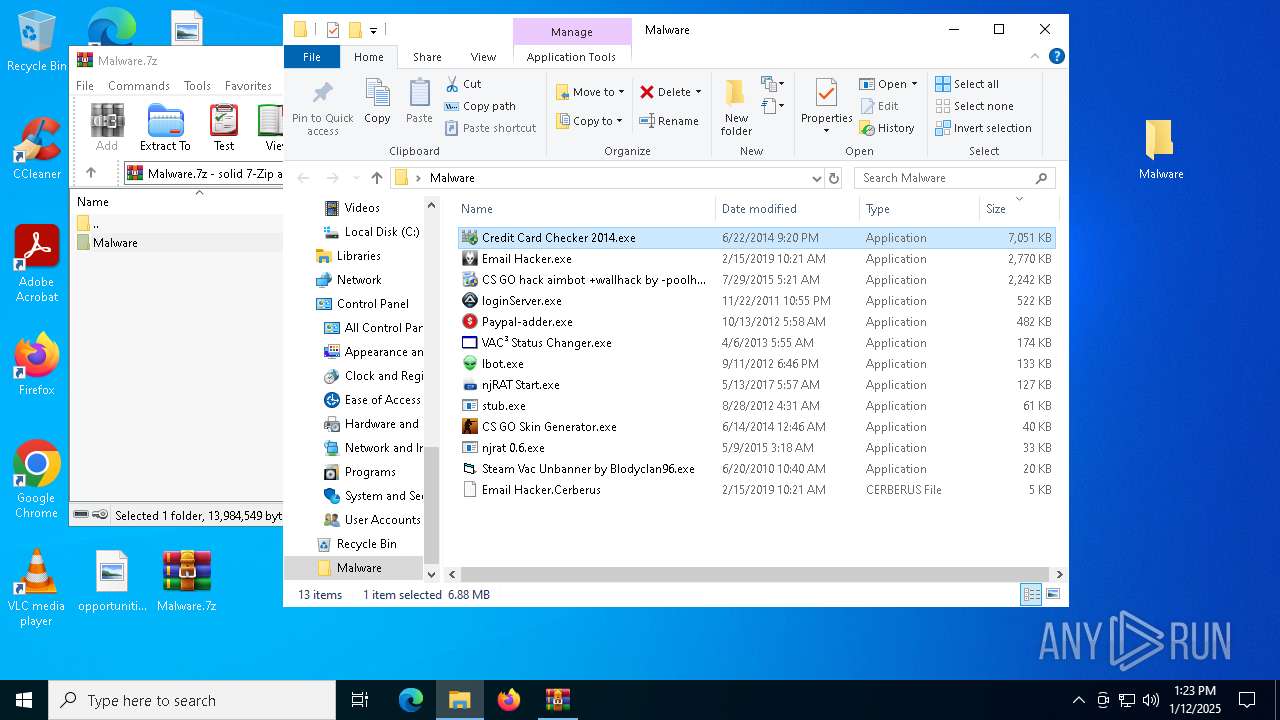
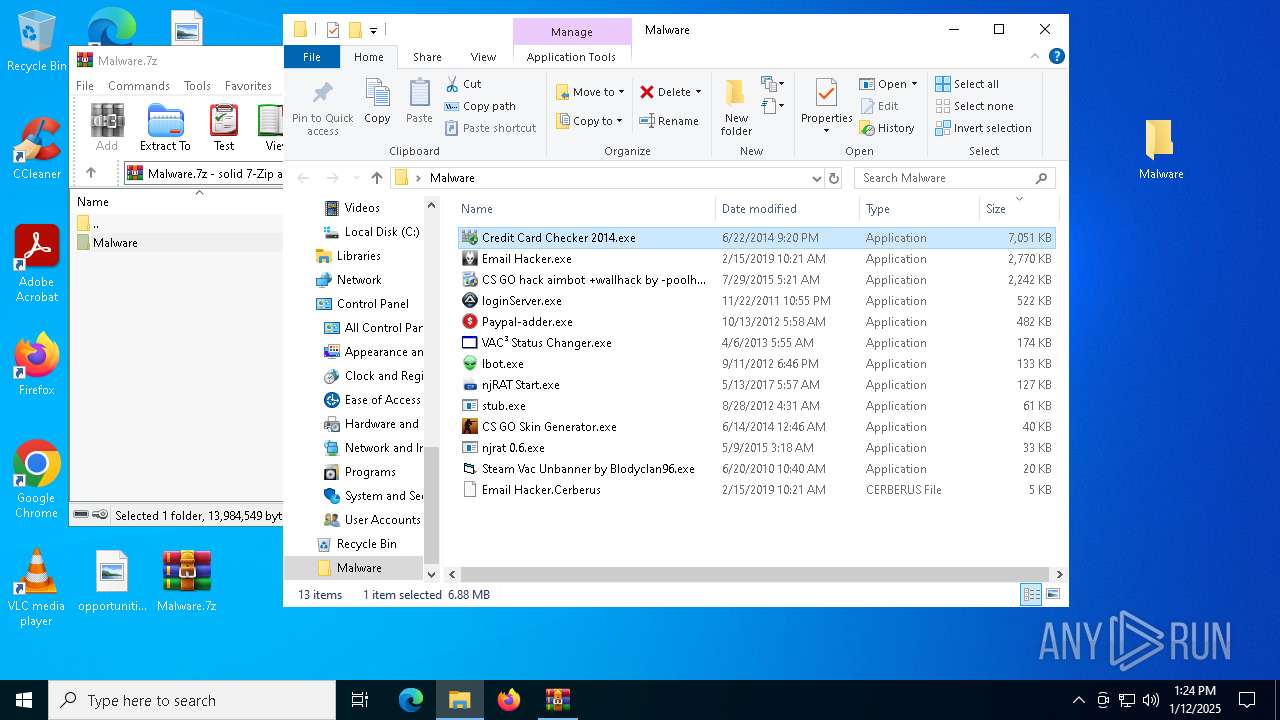
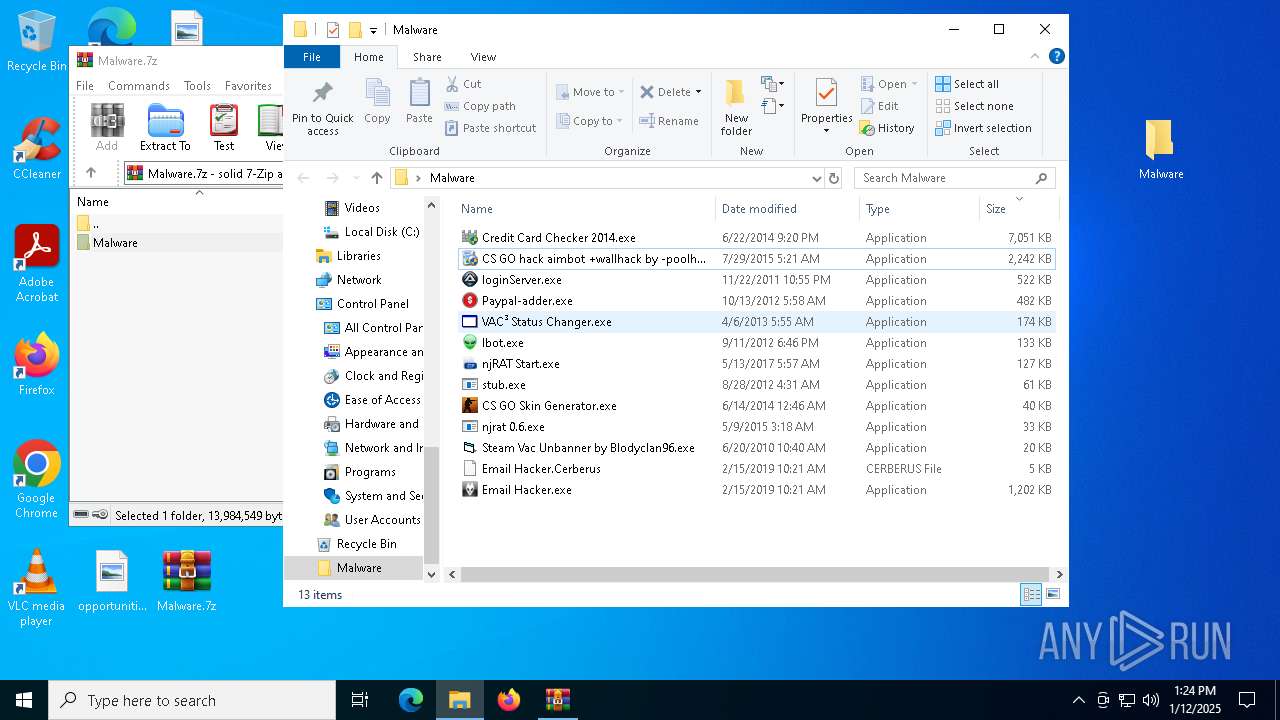
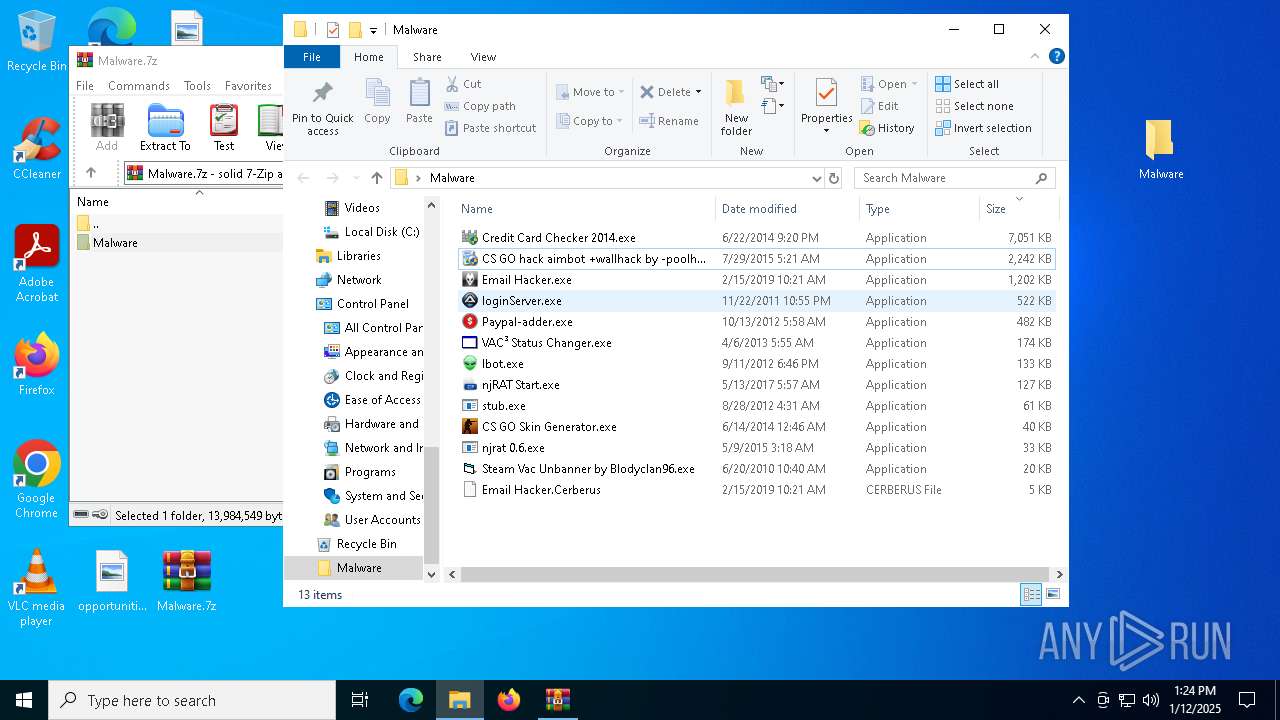
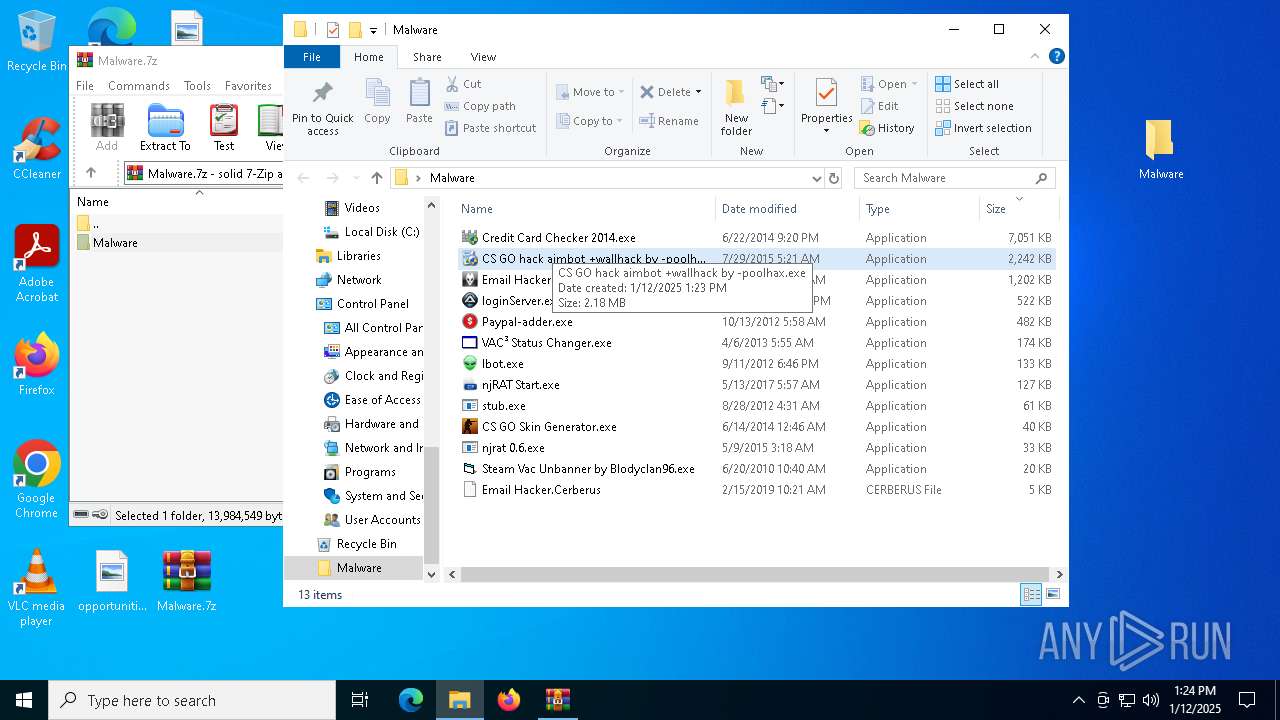
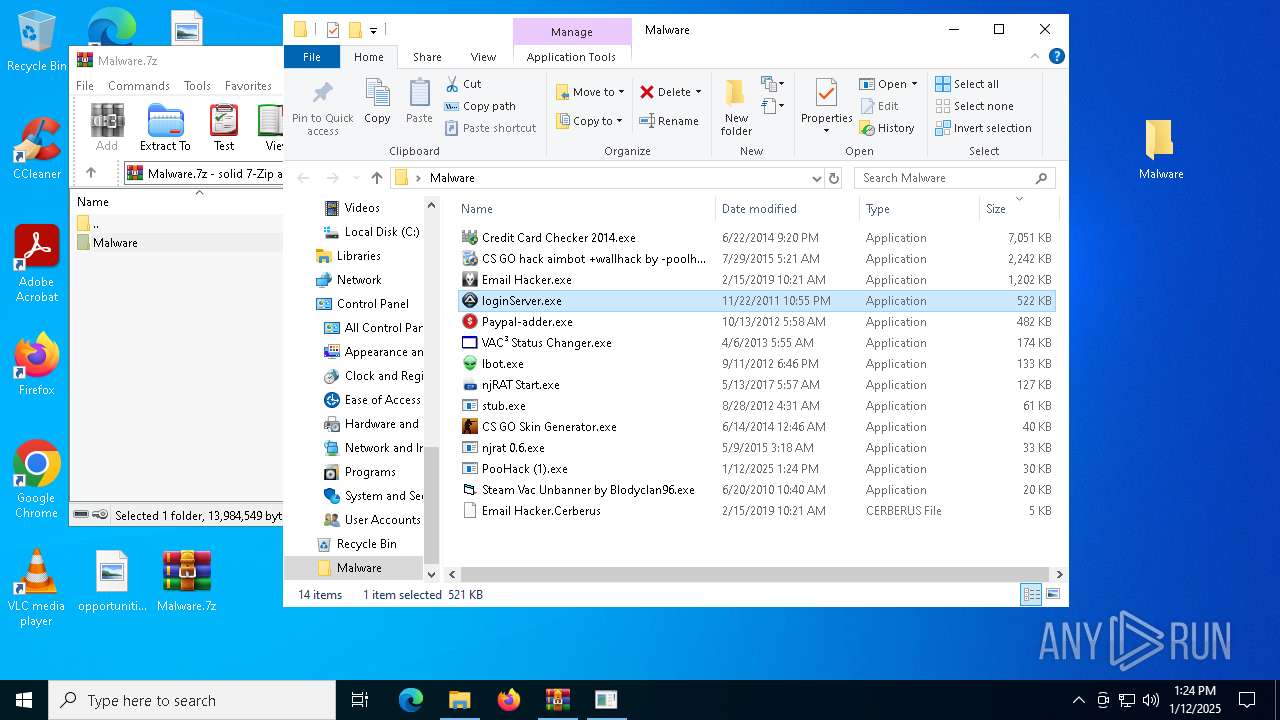
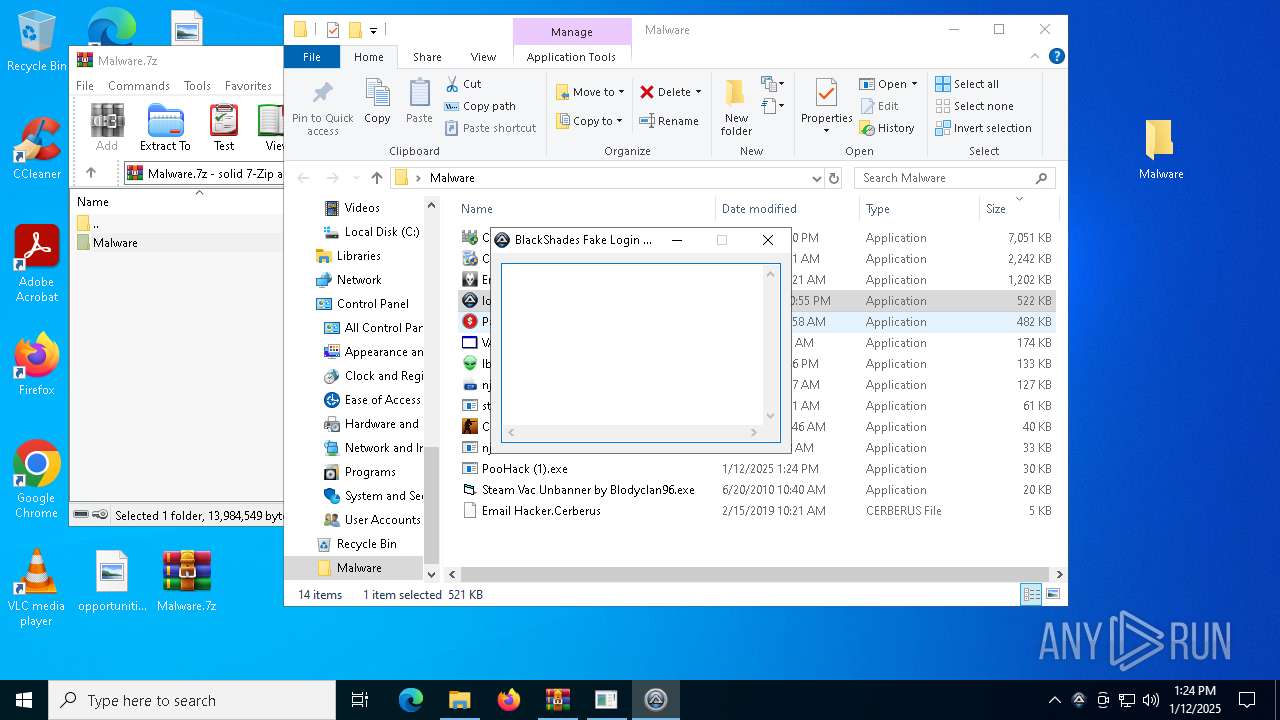
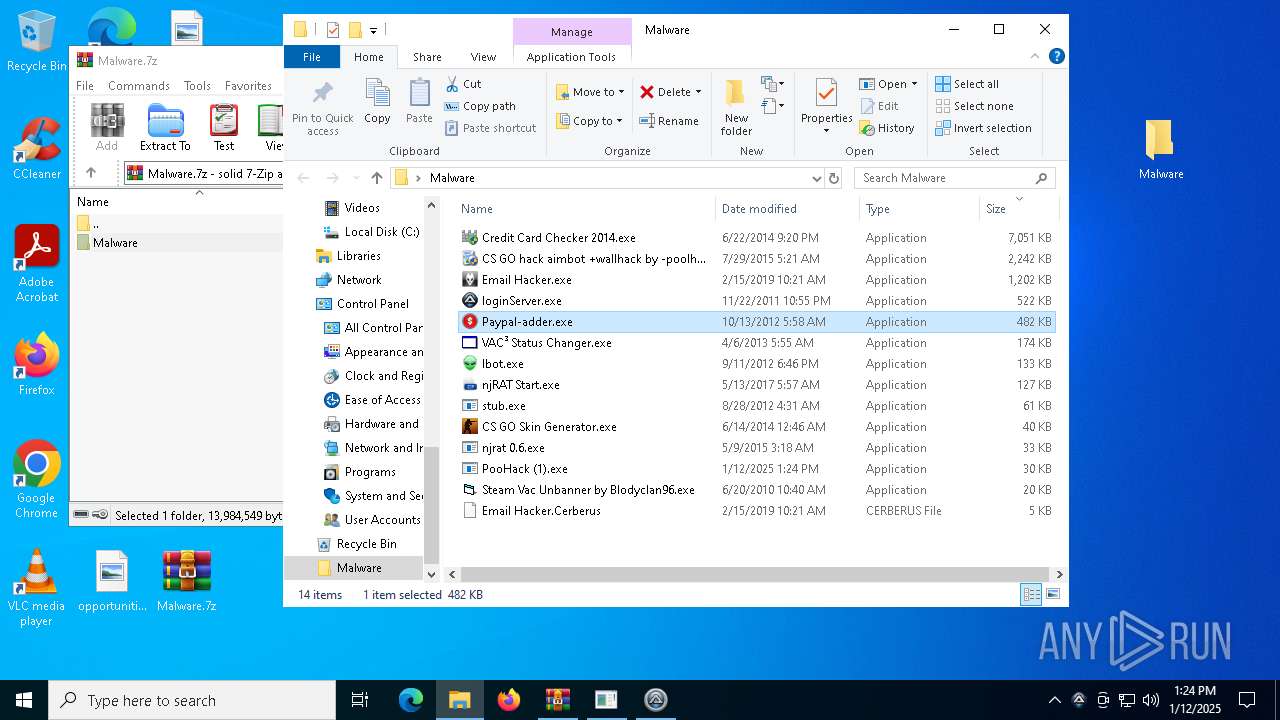
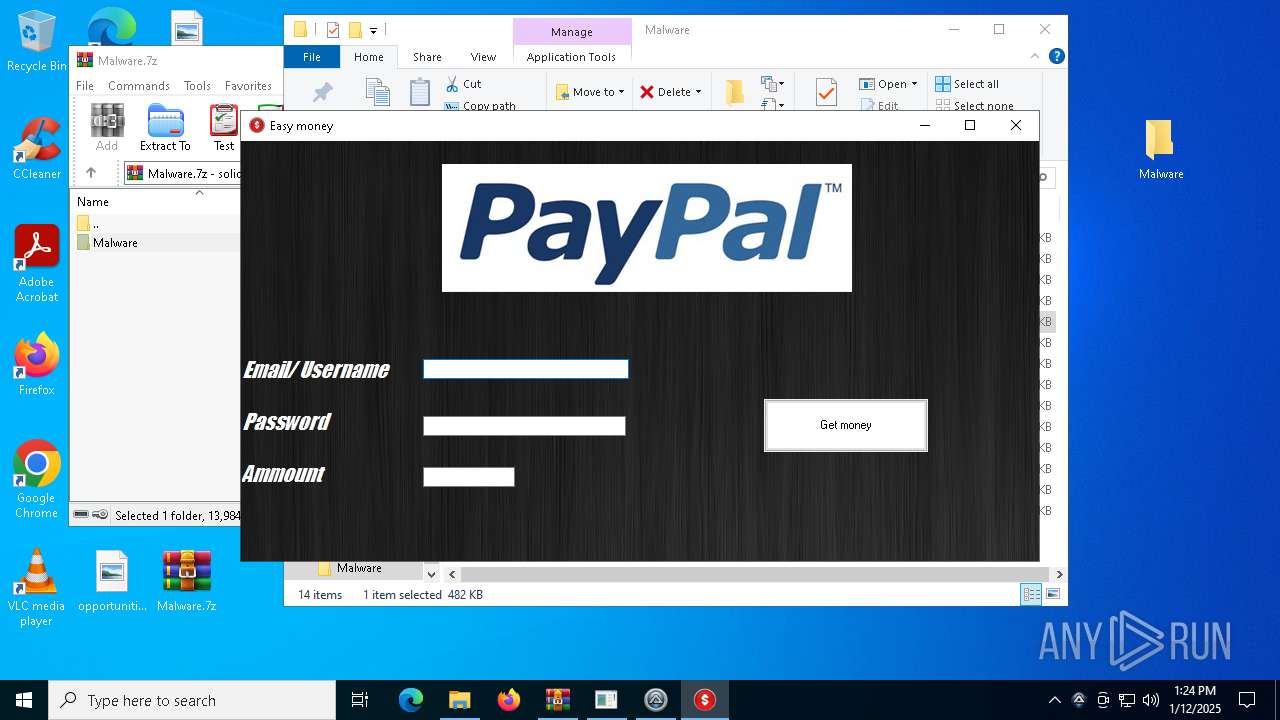
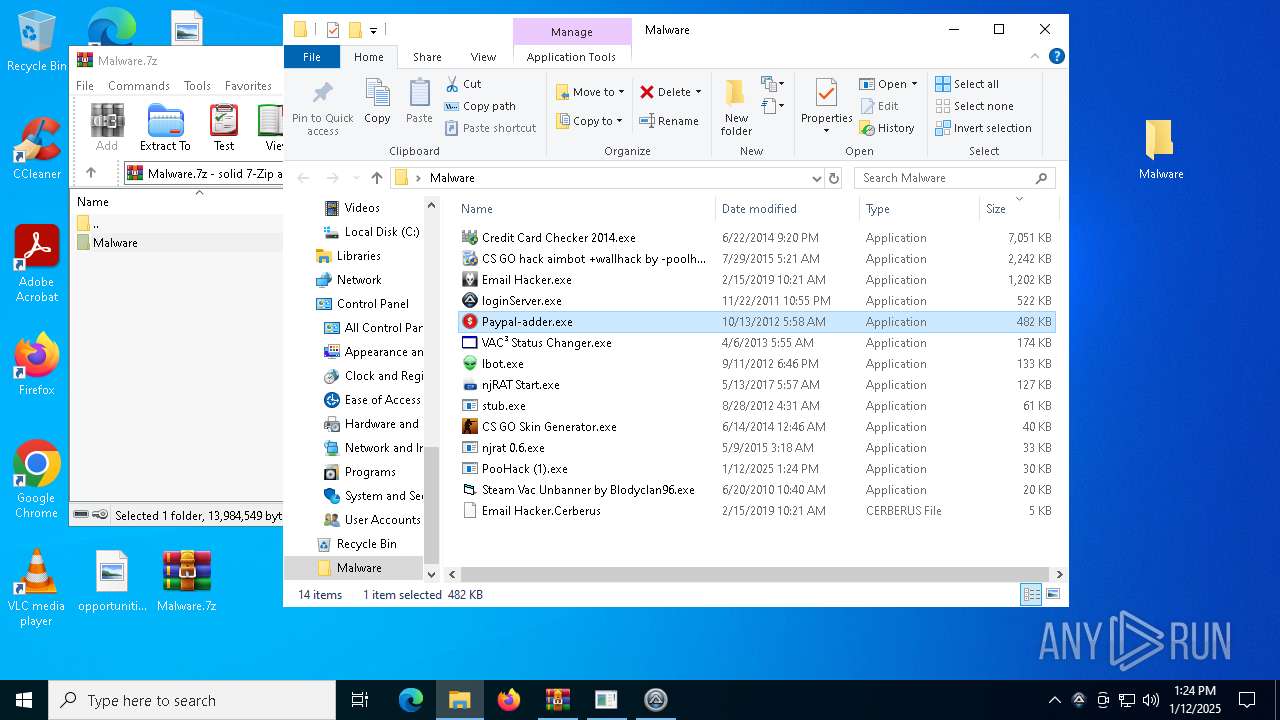
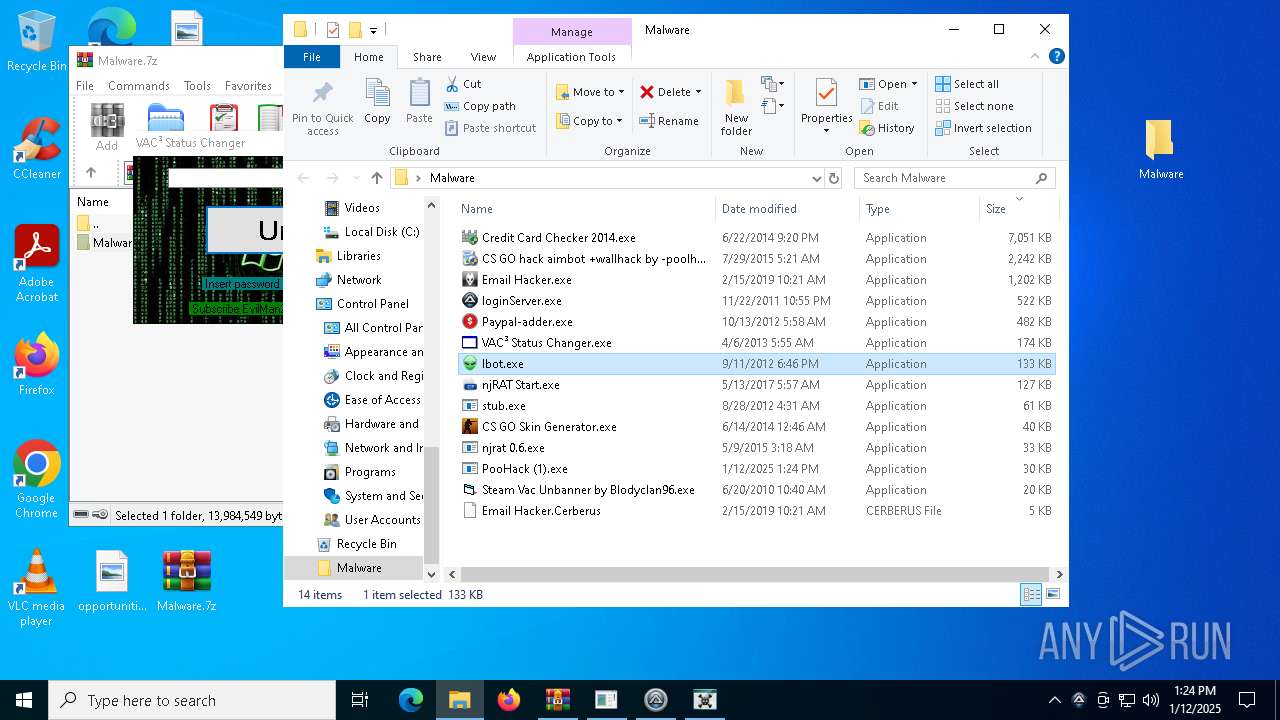
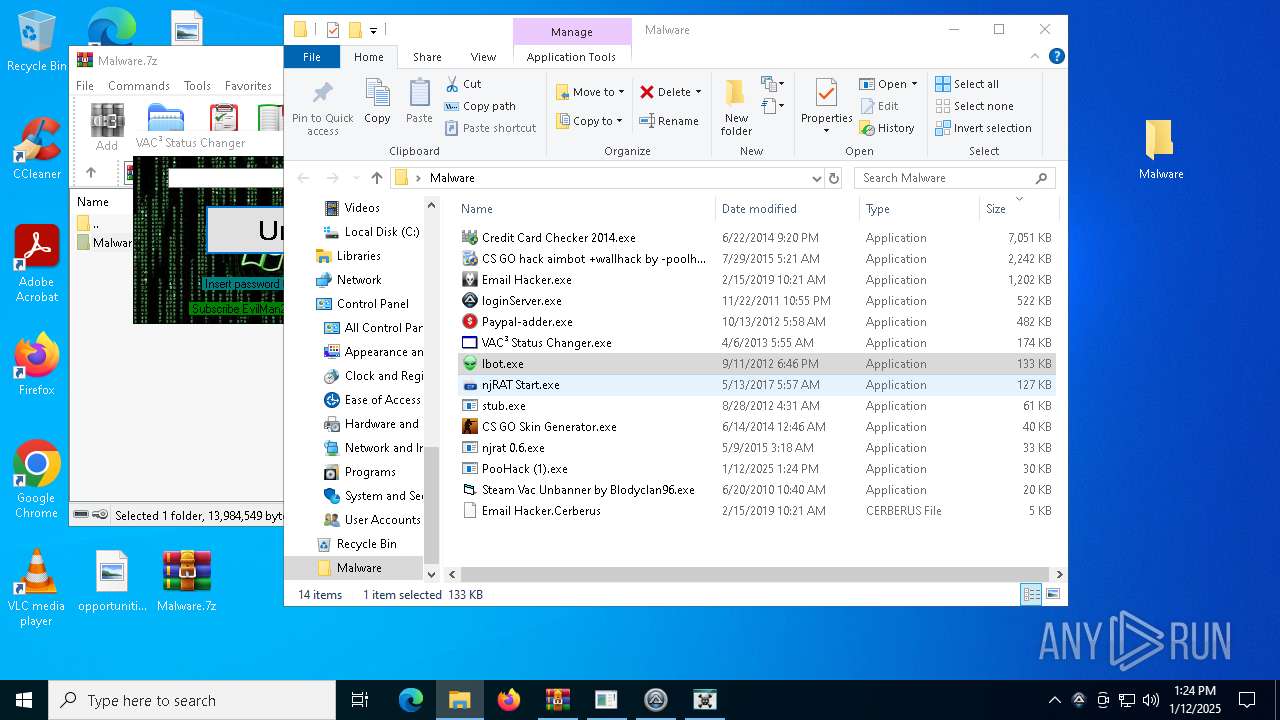
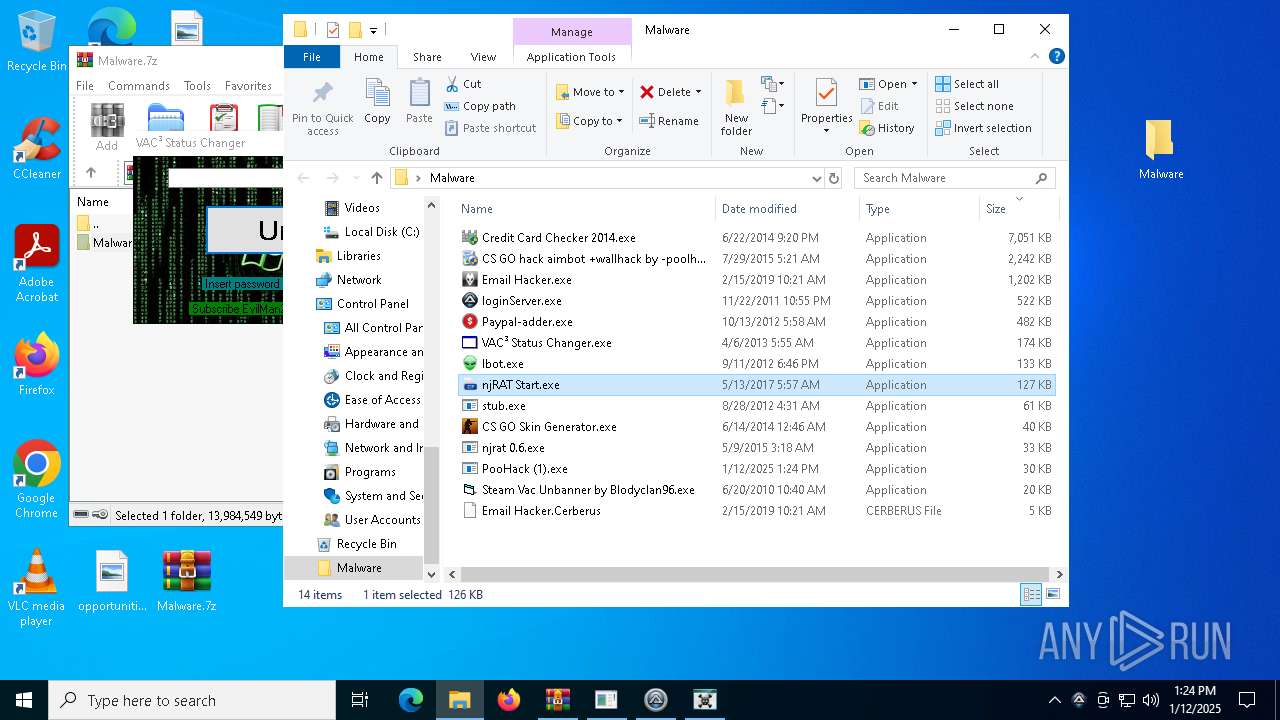
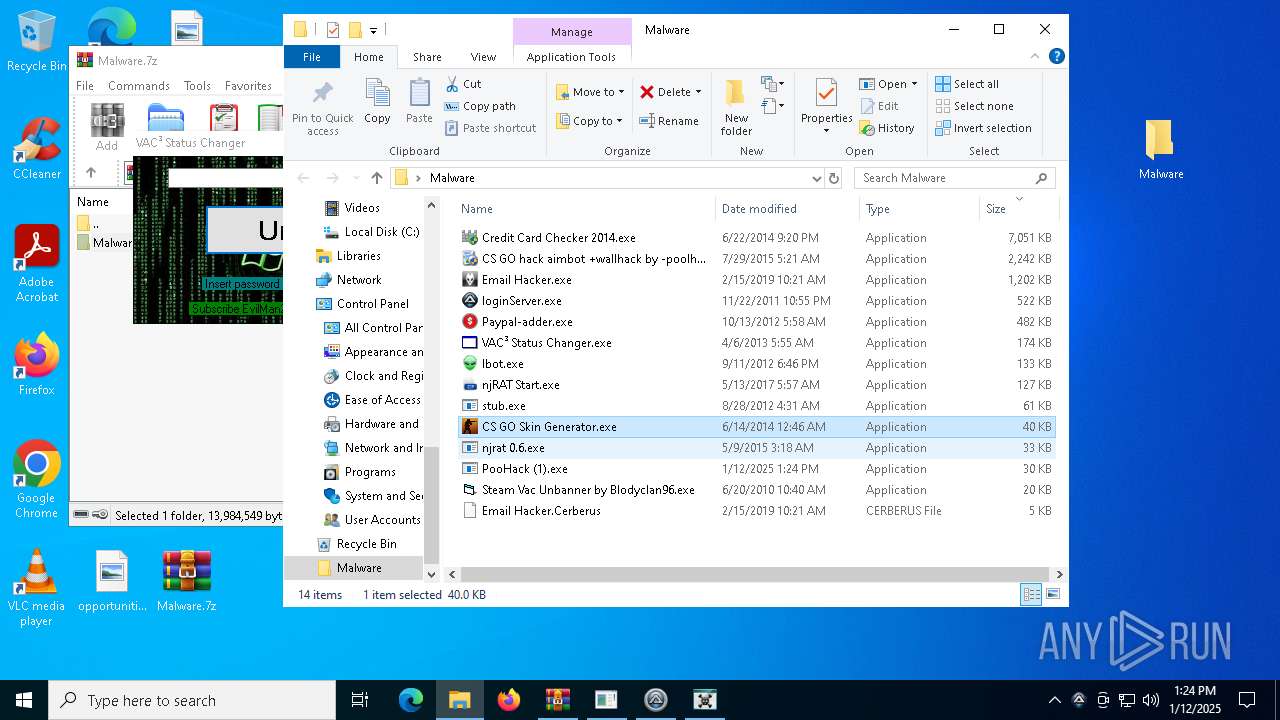
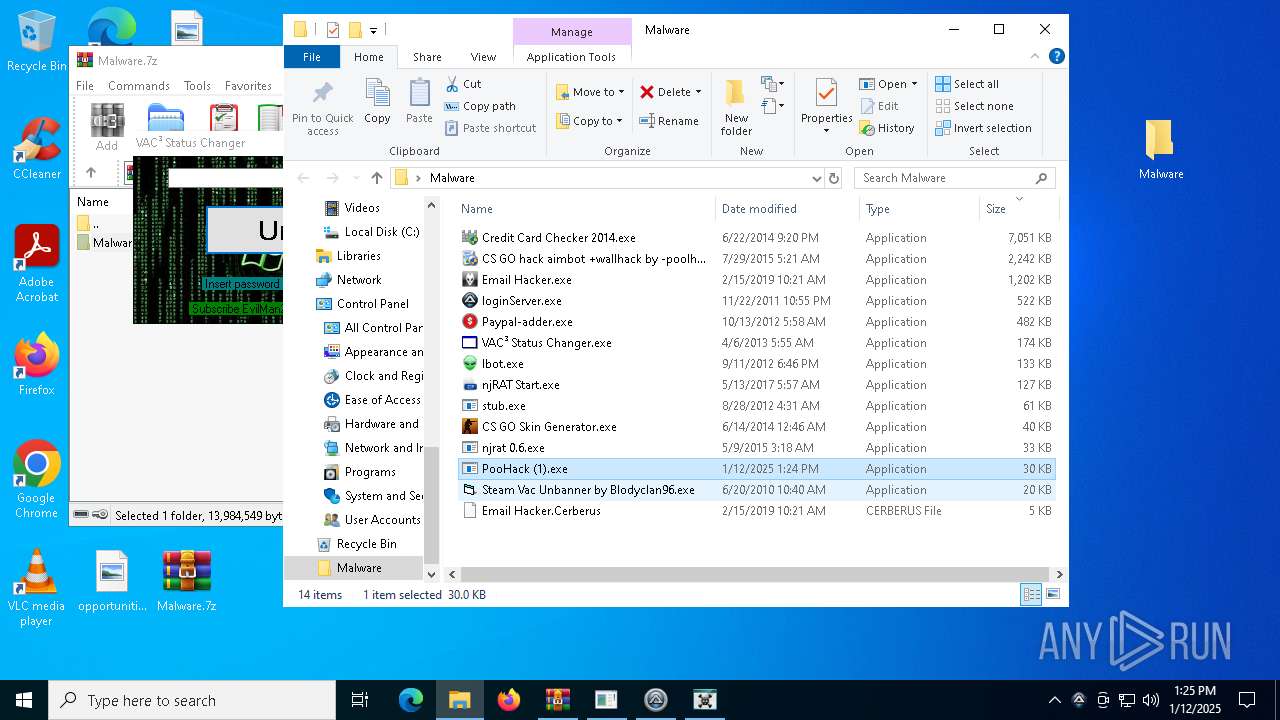
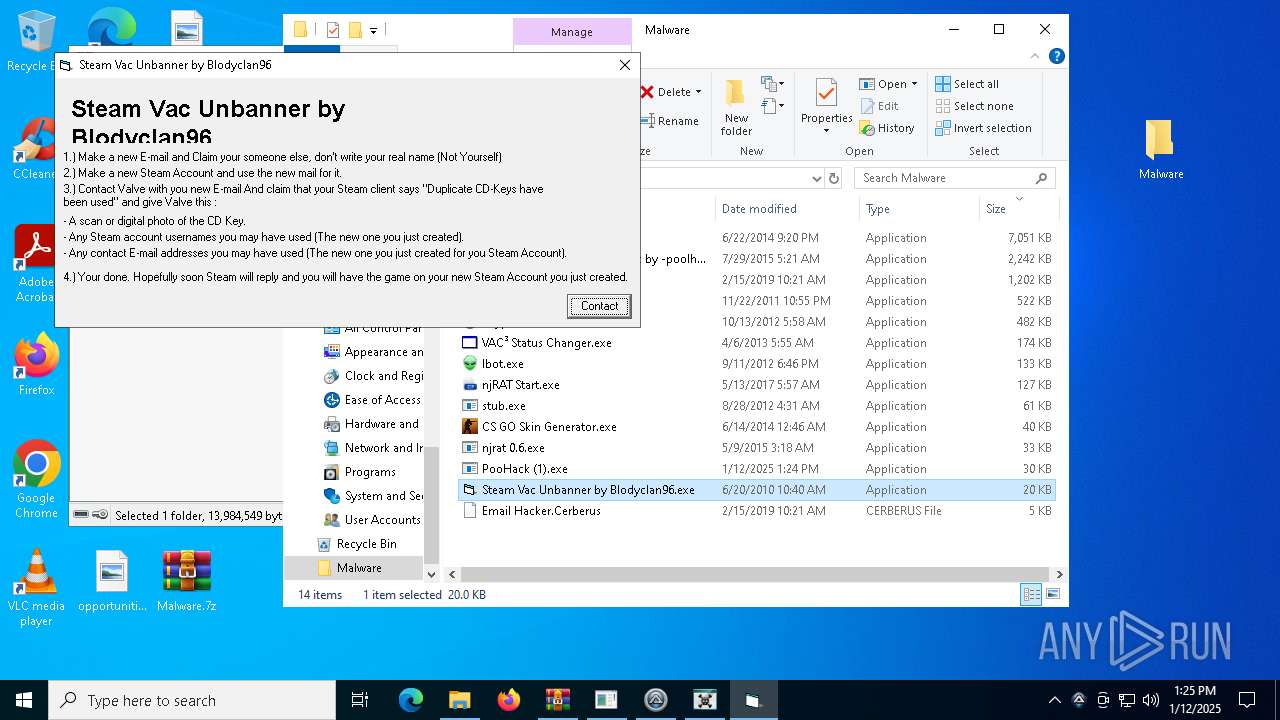
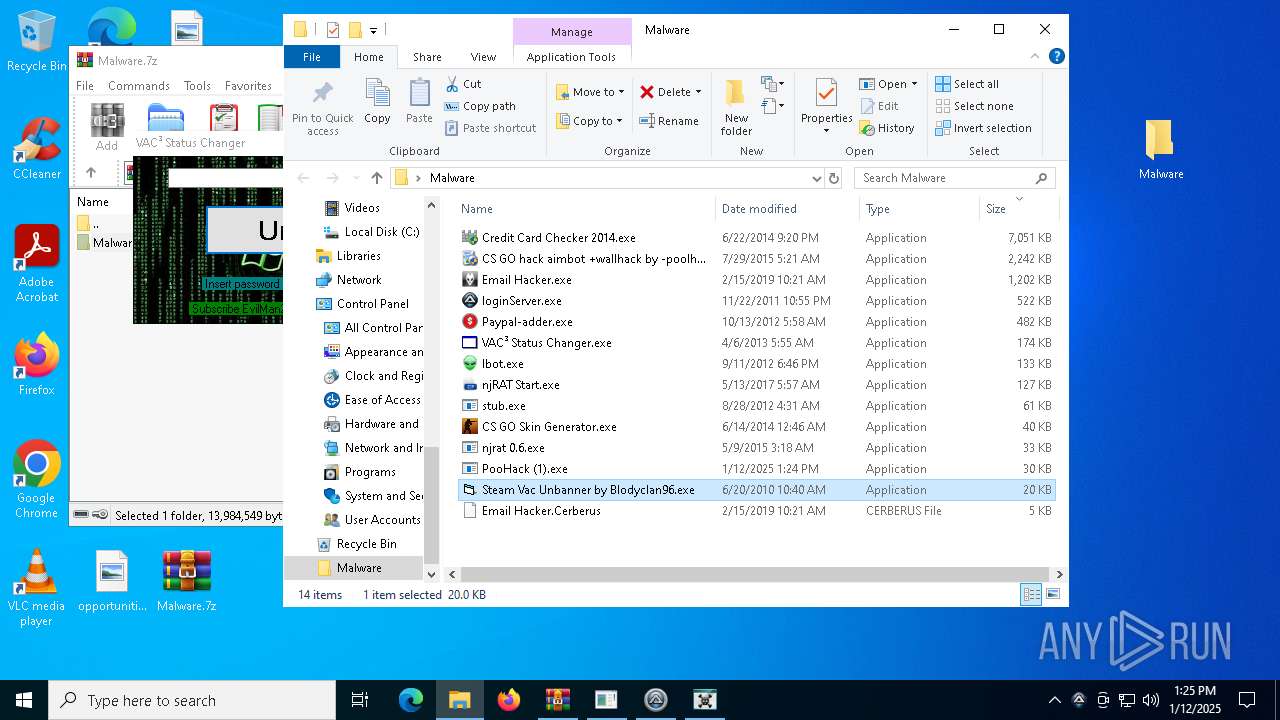
| File name: | Malware.7z |
| Full analysis: | https://app.any.run/tasks/0ac53bd2-5d20-4d19-a1cf-a38c174495b7 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 12, 2025, 13:23:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | C73525D45B259E3BD508E0EAF464F533 |
| SHA1: | 30F07C93417192663EF8A305509A8316A5DE703C |
| SHA256: | A0F417D451039288CD8B3EA7D13DBAA0382DB7EC023EE779AA04532AF6C1CC6D |
| SSDEEP: | 98304:FtnUY7CPcYkLttKS1qory6lCAkFftzYDcxYvjMiqoNt1xeEsd0sL0tbaqCCthuhd:NunIMEFsh0vHgkq8629+4FEir9Ly |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 828)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Gets startup folder path (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Reads the value of a key from the registry (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Creates a new registry key or changes the value of an existing one (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Create files in the Startup directory
- wscript.exe (PID: 6228)
- JeuxNul.exe (PID: 6744)
- ctfmon.exe (PID: 6956)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Modifies registry startup key (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Opens a text file (SCRIPT)
- wscript.exe (PID: 6280)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 6280)
Gets username (SCRIPT)
- wscript.exe (PID: 6280)
Accesses information about the status of the installed antivirus(Win32_AntivirusProduct) via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6280)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 6280)
Changes the autorun value in the registry
- Email Hacker.exe (PID: 6732)
- loginServer.exe (PID: 7656)
- ctfmon.exe (PID: 6956)
- BLE.exe (PID: 7492)
- google.exe (PID: 3464)
- mstwain32.exe (PID: 8108)
- csrss.exe (PID: 5208)
- JeuxNul.exe (PID: 6744)
MODILOADER mutex has been found
- Ibot.exe (PID: 8064)
- mstwain32.exe (PID: 8108)
NjRAT is detected
- ctfmon.exe (PID: 6956)
- JeuxNul.exe (PID: 6744)
- csrss.exe (PID: 5208)
NJRAT has been detected (YARA)
- csrss.exe (PID: 5208)
- JeuxNul.exe (PID: 6744)
SUSPICIOUS
Executable content was dropped or overwritten
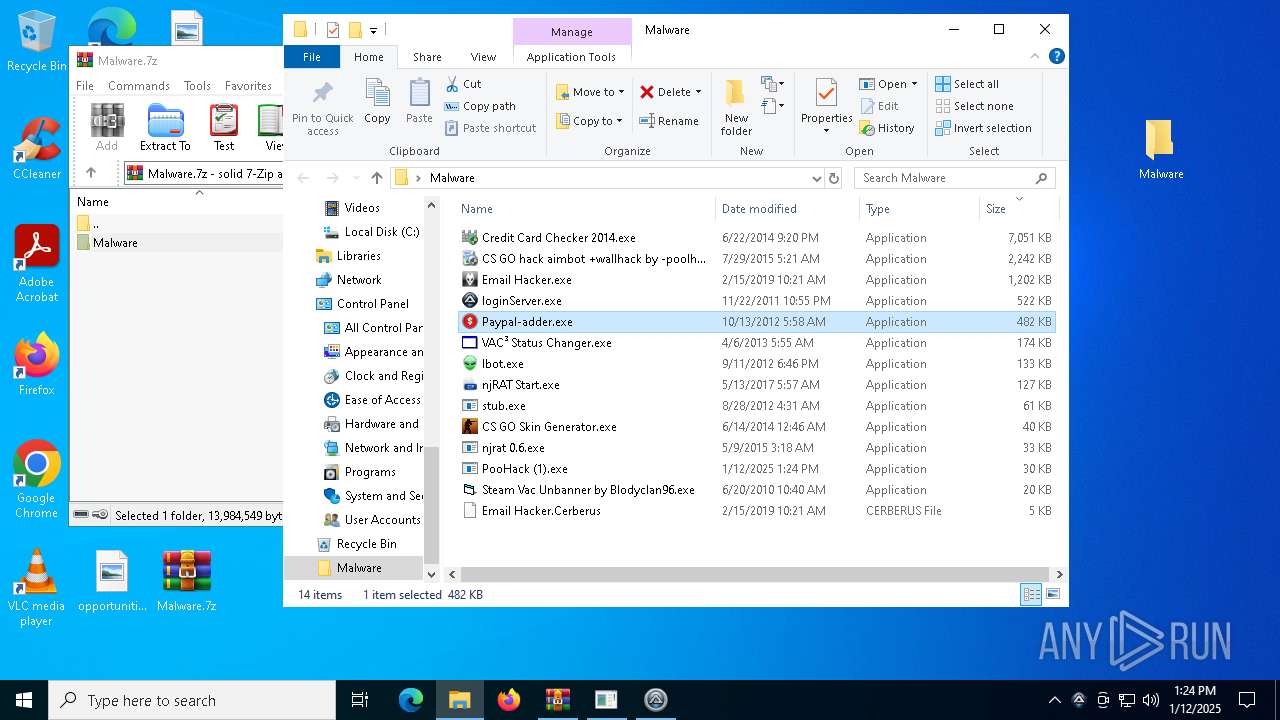
- Credit Card Checker 2014.exe (PID: 4504)
- Email Hacker.exe (PID: 6500)
- cmd.exe (PID: 6544)
- Email Hacker.exe (PID: 6732)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- loginServer.exe (PID: 7656)
- Ibot.exe (PID: 8064)
- mstwain32.exe (PID: 8108)
- njRAT Start.exe (PID: 8160)
- JeuxNul.exe (PID: 6744)
- stub.exe (PID: 6884)
- ctfmon.exe (PID: 6956)
- njrat 0.6.exe (PID: 7156)
- CS GO Skin Generator.exe (PID: 7116)
There is functionality for taking screenshot (YARA)
- autorun.exe (PID: 4076)
Reads security settings of Internet Explorer
- autorun.exe (PID: 4076)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- Ibot.exe (PID: 8064)
- BLE.exe (PID: 7492)
- njRAT Start.exe (PID: 8160)
- stub.exe (PID: 6884)
- njrat 0.6.exe (PID: 7156)
- CS GO Skin Generator.exe (PID: 7116)
The process executes VB scripts
- autorun.exe (PID: 4076)
- wscript.exe (PID: 6228)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 6228)
- wscript.exe (PID: 6280)
Application launched itself
- wscript.exe (PID: 6228)
- Email Hacker.exe (PID: 6684)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6228)
Checks whether the drive is ready (SCRIPT)
- wscript.exe (PID: 6280)
Gets disk free space (SCRIPT)
- wscript.exe (PID: 6280)
Accesses local storage devices (Win32_LogicalDisk) via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Accesses current user name via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Gets the drive type (SCRIPT)
- wscript.exe (PID: 6280)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- wscript.exe (PID: 6280)
Gets computer name (SCRIPT)
- wscript.exe (PID: 6280)
Accesses computer name via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Accesses OperatingSystem(Win32_OperatingSystem) via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 6280)
Accesses operating system name via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Accesses antivirus product name via WMI (SCRIPT)
- wscript.exe (PID: 6280)
Accesses WMI object caption (SCRIPT)
- wscript.exe (PID: 6280)
Adds, changes, or deletes HTTP request header (SCRIPT)
- wscript.exe (PID: 6280)
Searches for installed software
- Email Hacker.exe (PID: 6500)
Accesses WMI object display name (SCRIPT)
- wscript.exe (PID: 6280)
Executing commands from a ".bat" file
- Email Hacker.exe (PID: 6500)
Starts CMD.EXE for commands execution
- Email Hacker.exe (PID: 6500)
The executable file from the user directory is run by the CMD process
- VaporLoader.exe (PID: 6644)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6544)
Gets a collection of all available drive names (SCRIPT)
- wscript.exe (PID: 6280)
Connects to SMTP port
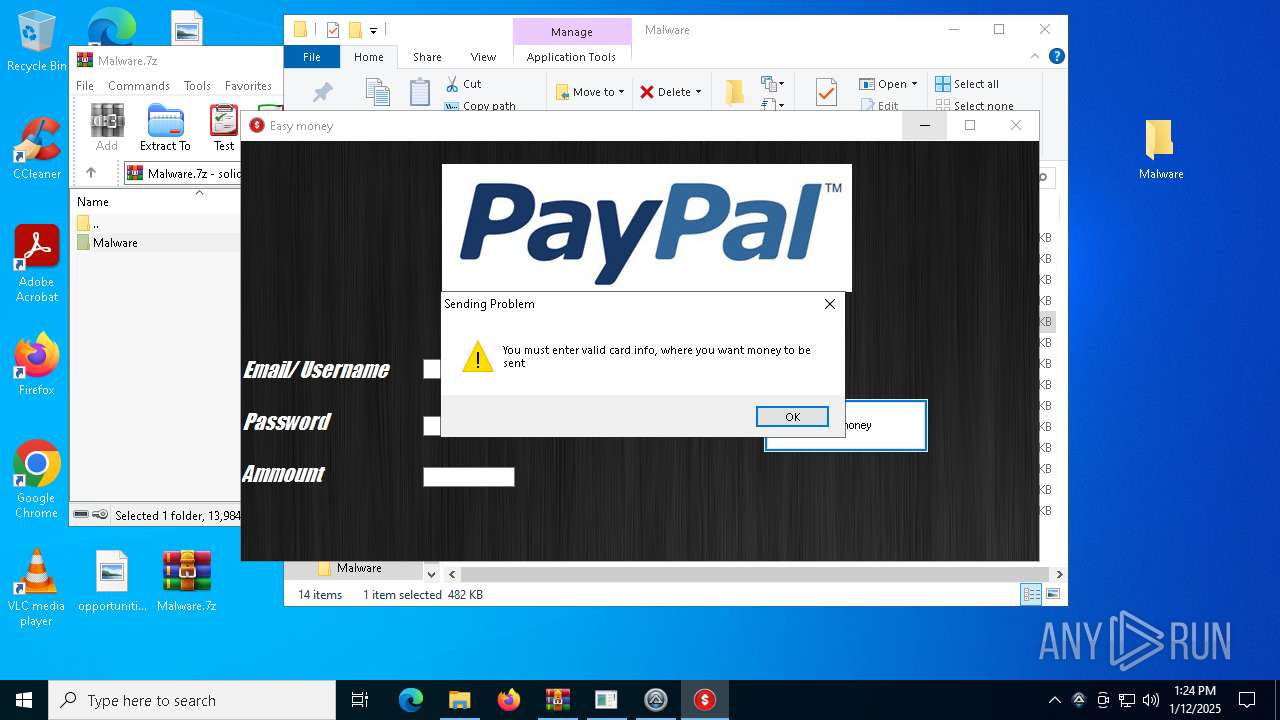
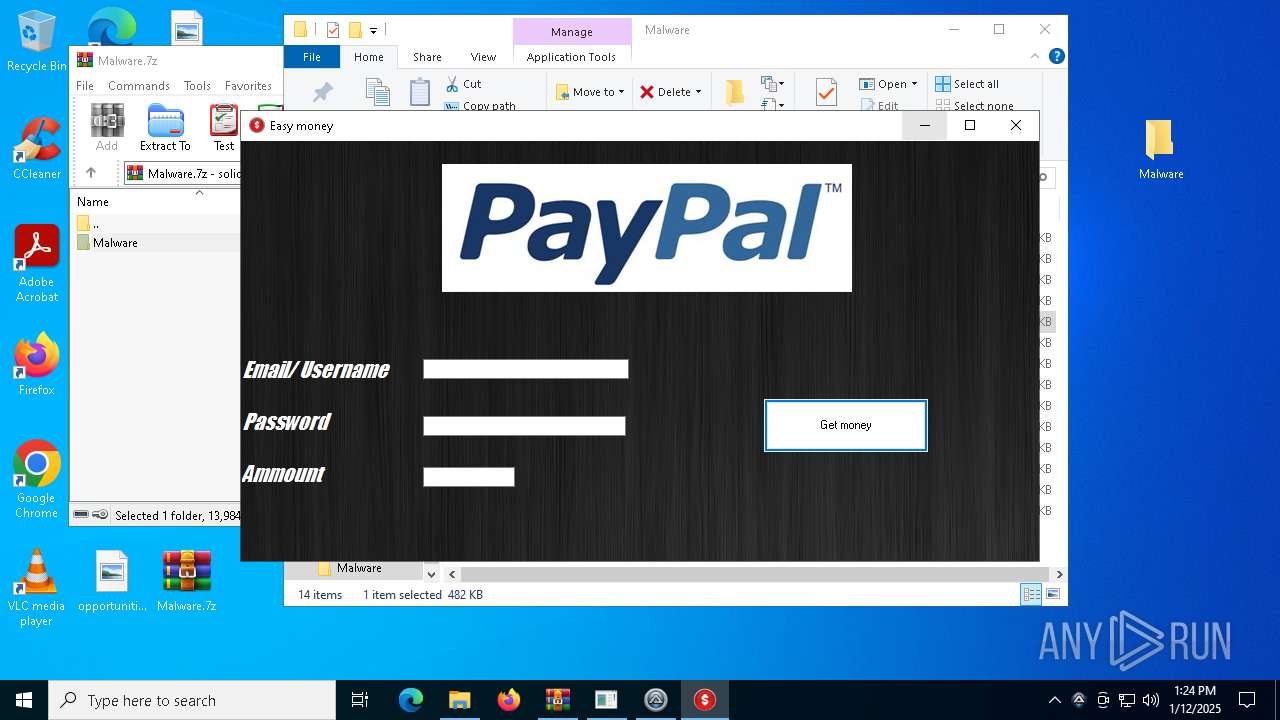
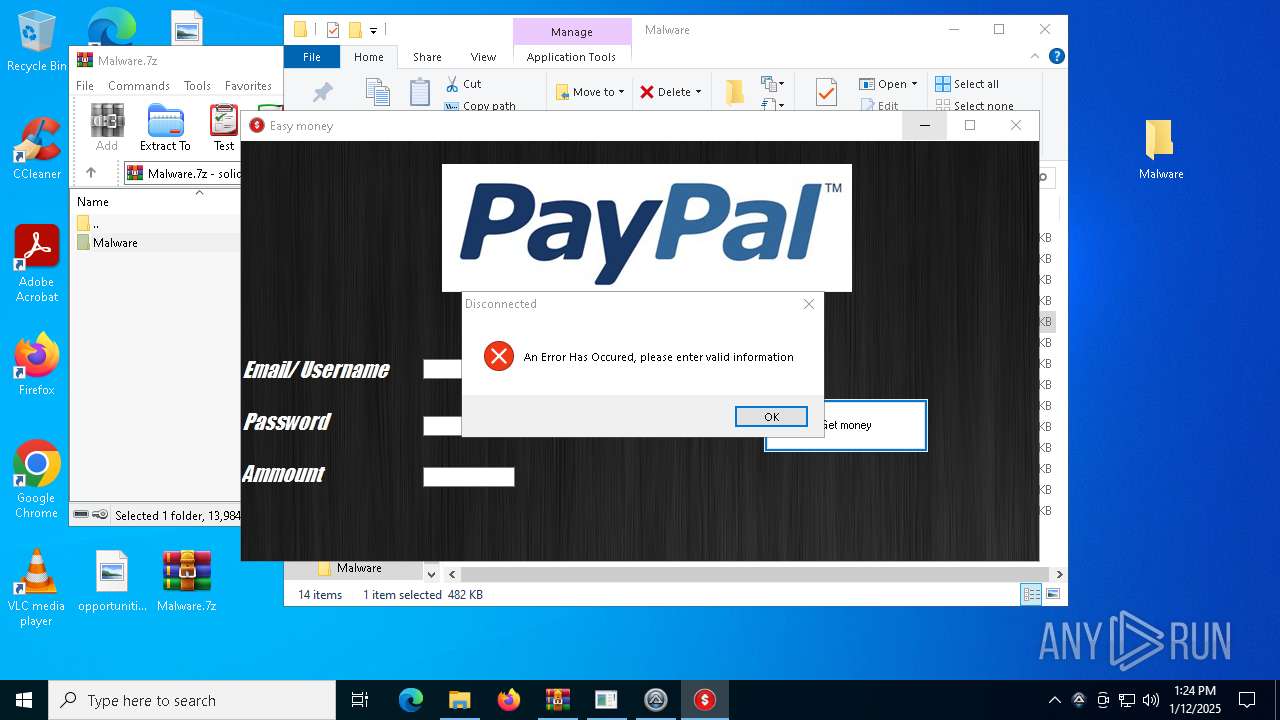
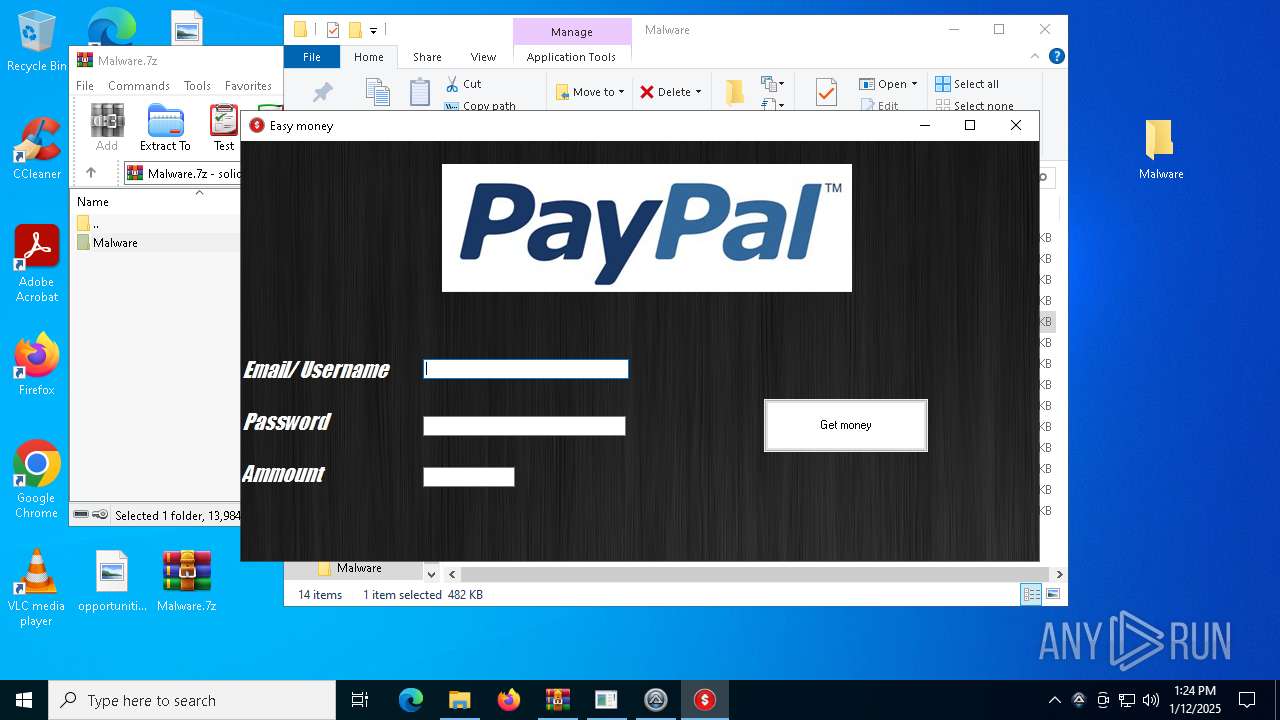
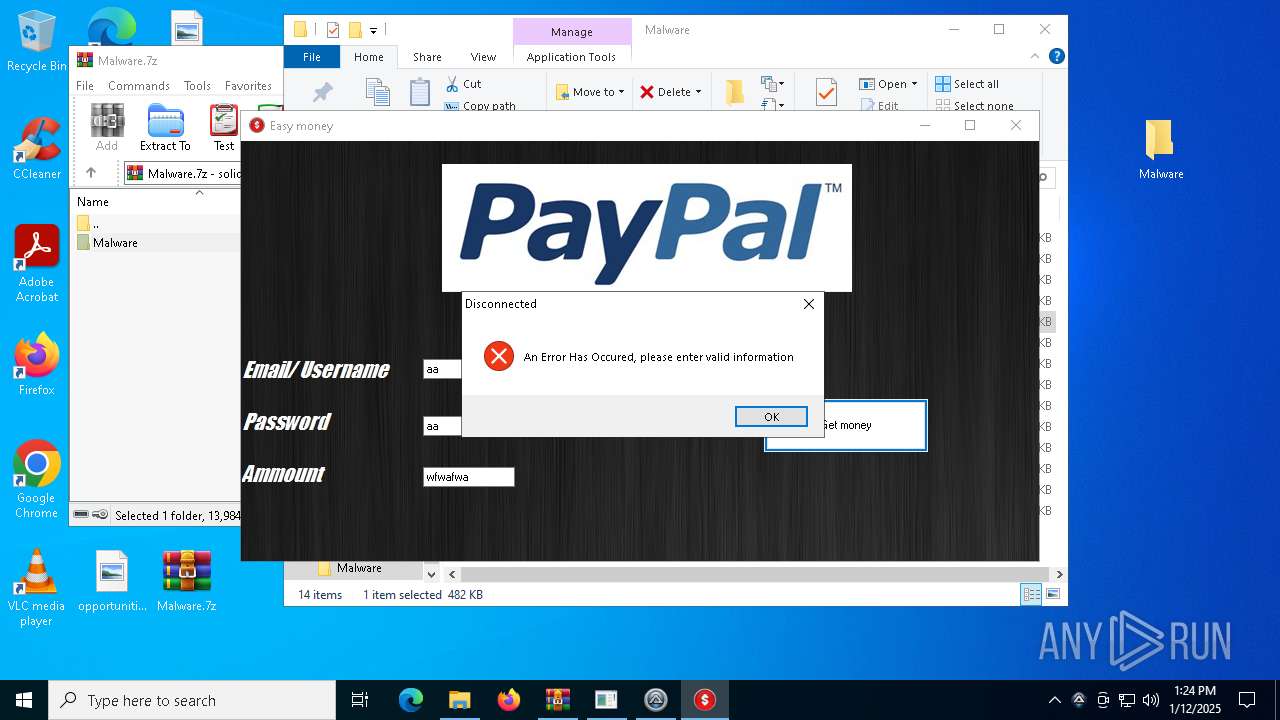
- Paypal-adder.exe (PID: 7736)
- Paypal-adder.exe (PID: 7856)
Connects to FTP
- BLE.exe (PID: 7492)
Starts itself from another location
- njRAT Start.exe (PID: 8160)
- stub.exe (PID: 6884)
- njrat 0.6.exe (PID: 7156)
- CS GO Skin Generator.exe (PID: 7116)
- Ibot.exe (PID: 8064)
Uses NETSH.EXE to add a firewall rule or allowed programs
- JeuxNul.exe (PID: 6744)
- ctfmon.exe (PID: 6956)
- csrss.exe (PID: 5208)
The process creates files with name similar to system file names
- stub.exe (PID: 6884)
- ctfmon.exe (PID: 6956)
- CS GO Skin Generator.exe (PID: 7116)
There is functionality for VM detection antiVM strings (YARA)
- Email Hacker.exe (PID: 6732)
INFO
The process uses the downloaded file
- WinRAR.exe (PID: 828)
- autorun.exe (PID: 4076)
- wscript.exe (PID: 6228)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- Ibot.exe (PID: 8064)
- njRAT Start.exe (PID: 8160)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 828)
Manual execution by a user
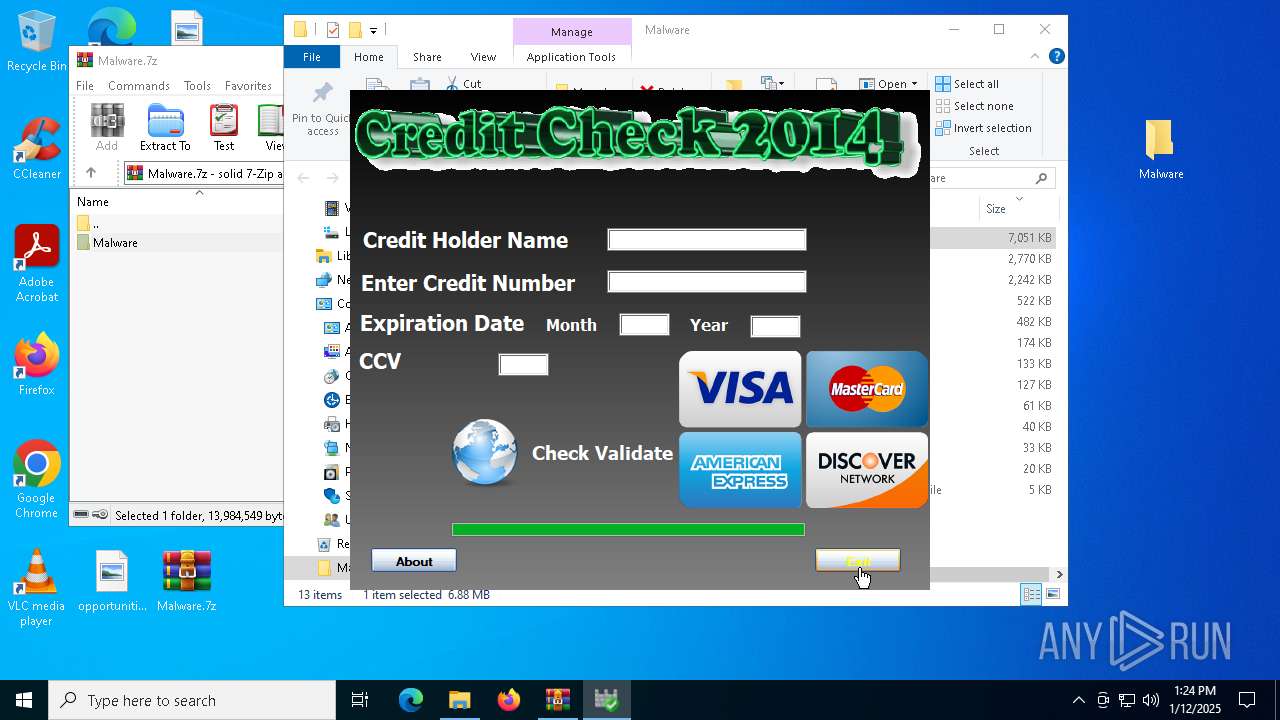
- Credit Card Checker 2014.exe (PID: 4504)
- Credit Card Checker 2014.exe (PID: 2088)
- Email Hacker.exe (PID: 6500)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- loginServer.exe (PID: 7656)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7404)
- Paypal-adder.exe (PID: 7736)
- Paypal-adder.exe (PID: 7856)
- VAC³ Status Changer.exe (PID: 8004)
- Ibot.exe (PID: 8064)
- njRAT Start.exe (PID: 8160)
- stub.exe (PID: 6884)
- CS GO Skin Generator.exe (PID: 7116)
- njrat 0.6.exe (PID: 7156)
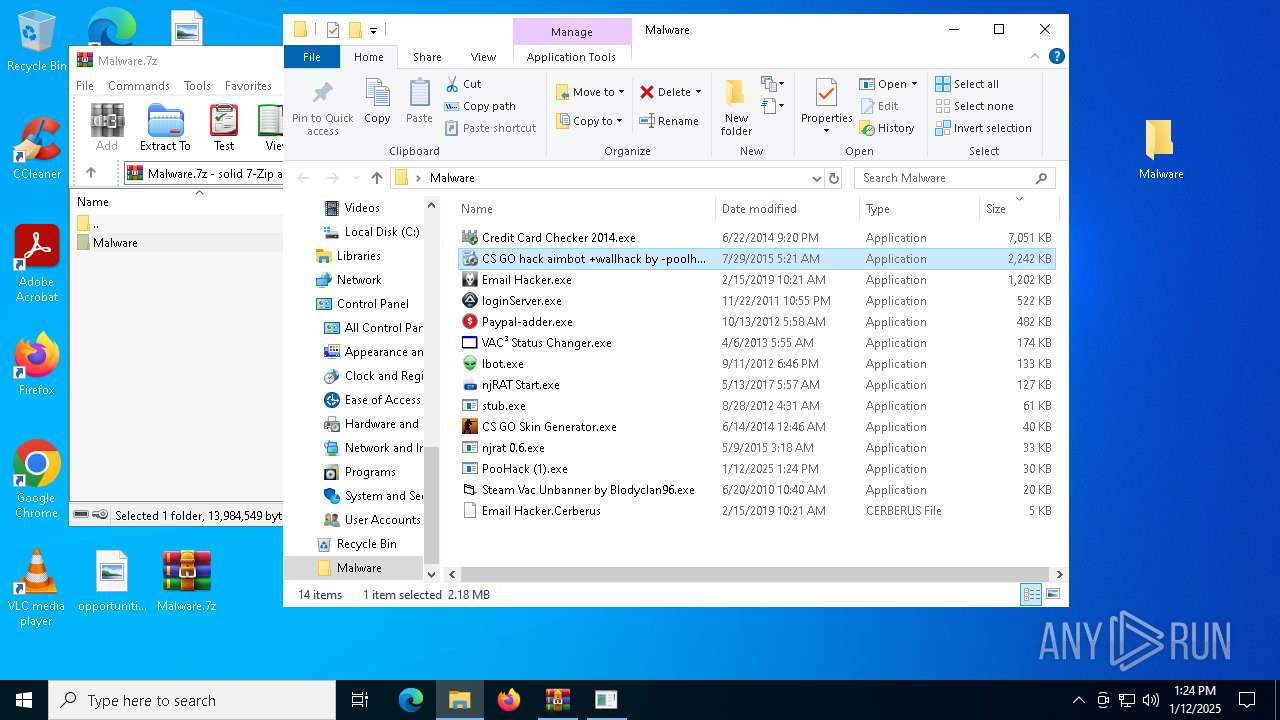
- PooHack (1).exe (PID: 3912)
- Steam Vac Unbanner by Blodyclan96.exe (PID: 4876)
The sample compiled with english language support
- WinRAR.exe (PID: 828)
- Credit Card Checker 2014.exe (PID: 4504)
- loginServer.exe (PID: 7656)
Checks supported languages
- Credit Card Checker 2014.exe (PID: 4504)
- autorun.exe (PID: 4076)
- Email Hacker.exe (PID: 6500)
- VaporLoader.exe (PID: 6644)
- Email Hacker.exe (PID: 6684)
- Email Hacker.exe (PID: 6732)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- loginServer.exe (PID: 7656)
- PooHack (1).exe (PID: 7512)
- BLE.exe (PID: 7492)
- LOGINS~1.EXE (PID: 7692)
- Paypal-adder.exe (PID: 7736)
- Paypal-adder.exe (PID: 7856)
- VAC³ Status Changer.exe (PID: 8004)
- Ibot.exe (PID: 8064)
- mstwain32.exe (PID: 8108)
- njRAT Start.exe (PID: 8160)
- JeuxNul.exe (PID: 6744)
- stub.exe (PID: 6884)
- ctfmon.exe (PID: 6956)
- CS GO Skin Generator.exe (PID: 7116)
- PooHack (1).exe (PID: 3912)
- google.exe (PID: 3464)
- Steam Vac Unbanner by Blodyclan96.exe (PID: 4876)
- csrss.exe (PID: 5208)
- njrat 0.6.exe (PID: 7156)
Create files in a temporary directory
- Credit Card Checker 2014.exe (PID: 4504)
- autorun.exe (PID: 4076)
- Email Hacker.exe (PID: 6500)
- loginServer.exe (PID: 7656)
- njRAT Start.exe (PID: 8160)
- stub.exe (PID: 6884)
- ctfmon.exe (PID: 6956)
- JeuxNul.exe (PID: 6744)
The sample compiled with french language support
- WinRAR.exe (PID: 828)
Reads the computer name
- autorun.exe (PID: 4076)
- Email Hacker.exe (PID: 6500)
- Email Hacker.exe (PID: 6684)
- VaporLoader.exe (PID: 6644)
- Credit Card Checker 2014.exe (PID: 4504)
- Email Hacker.exe (PID: 6732)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- PooHack (1).exe (PID: 7512)
- loginServer.exe (PID: 7656)
- LOGINS~1.EXE (PID: 7692)
- Paypal-adder.exe (PID: 7736)
- Paypal-adder.exe (PID: 7856)
- Ibot.exe (PID: 8064)
- VAC³ Status Changer.exe (PID: 8004)
- stub.exe (PID: 6884)
- JeuxNul.exe (PID: 6744)
- BLE.exe (PID: 7492)
- PooHack (1).exe (PID: 3912)
- njrat 0.6.exe (PID: 7156)
- google.exe (PID: 3464)
- Steam Vac Unbanner by Blodyclan96.exe (PID: 4876)
- CS GO Skin Generator.exe (PID: 7116)
- ctfmon.exe (PID: 6956)
Process checks computer location settings
- autorun.exe (PID: 4076)
- Ibot.exe (PID: 8064)
- stub.exe (PID: 6884)
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
The process uses Lua
- autorun.exe (PID: 4076)
Checks proxy server information
- wscript.exe (PID: 6280)
- VaporLoader.exe (PID: 6644)
- BLE.exe (PID: 7492)
Reads the machine GUID from the registry
- Email Hacker.exe (PID: 6500)
- VaporLoader.exe (PID: 6644)
- Paypal-adder.exe (PID: 7736)
- Paypal-adder.exe (PID: 7856)
- VAC³ Status Changer.exe (PID: 8004)
- njRAT Start.exe (PID: 8160)
- JeuxNul.exe (PID: 6744)
- ctfmon.exe (PID: 6956)
Disables trace logs
- VaporLoader.exe (PID: 6644)
Failed to create an executable file in Windows directory
- Email Hacker.exe (PID: 6732)
- njrat 0.6.exe (PID: 7156)
- google.exe (PID: 3464)
Creates files or folders in the user directory
- Email Hacker.exe (PID: 6732)
- Ibot.exe (PID: 8064)
- mstwain32.exe (PID: 8108)
- JeuxNul.exe (PID: 6744)
- ctfmon.exe (PID: 6956)
- njrat 0.6.exe (PID: 7156)
- CS GO Skin Generator.exe (PID: 7116)
Reads the software policy settings
- VaporLoader.exe (PID: 6644)
- Paypal-adder.exe (PID: 7736)
- Paypal-adder.exe (PID: 7856)
Creates files in the program directory
- CS GO hack aimbot +wallhack by -poolhax.exe (PID: 7452)
- BLE.exe (PID: 7492)
Reads mouse settings
- LOGINS~1.EXE (PID: 7692)
Process checks whether UAC notifications are on
- Ibot.exe (PID: 8064)
Sends debugging messages
- njrat 0.6.exe (PID: 7156)
- google.exe (PID: 3464)
UPX packer has been detected
- mstwain32.exe (PID: 8108)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
NjRat
(PID) Process(6744) JeuxNul.exe
C2hacker45.ddns.net
Ports1604
BotnetHacKed
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\691e59f102743330f16e52374a9fedec
Splitter|'|'|
Version0.6.4
(PID) Process(5208) csrss.exe
C2keygen1gg.zapto.org
Ports1177
Botnethacked
Options
Auto-run registry keySoftware\Microsoft\Windows\CurrentVersion\Run\9ebc89cb70ae8d1246bcd119aeec0d85
Splitter|'|'|
Version0.7d
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2025:01:12 13:22:58+00:00 |
| ArchivedFileName: | Malware |
Total processes
167
Monitored processes
46
Malicious processes
18
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 828 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Malware.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
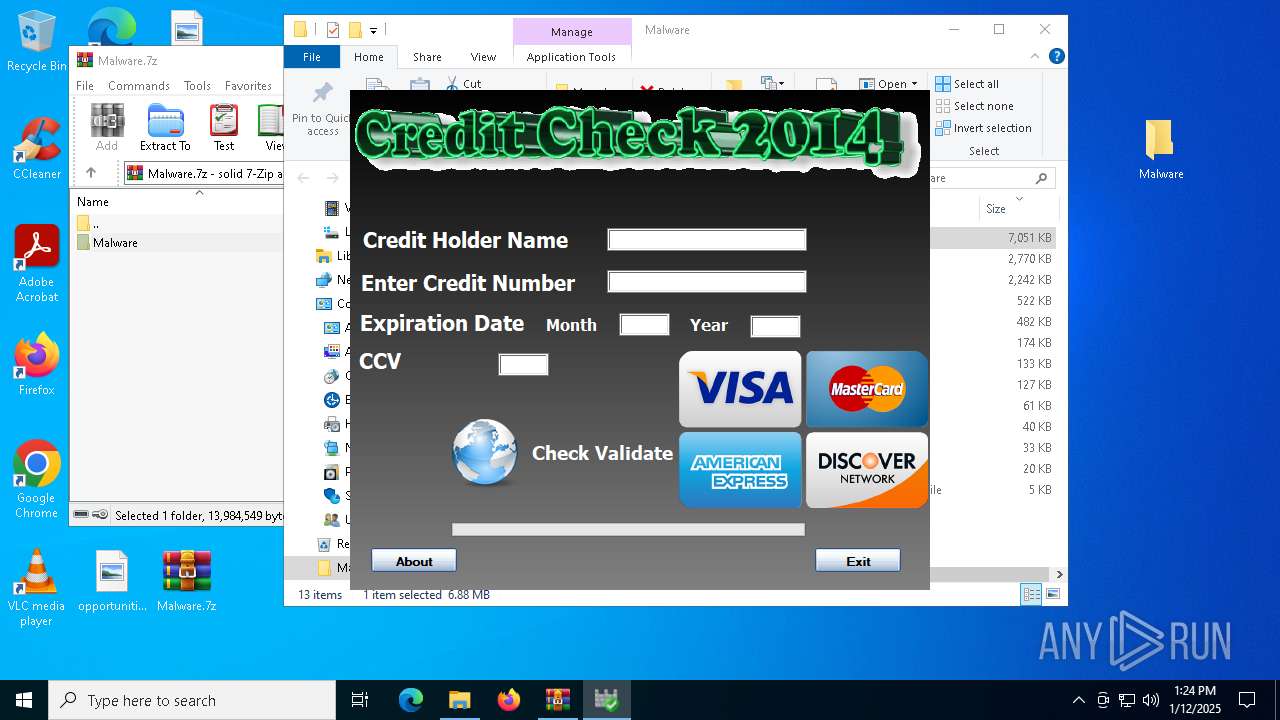
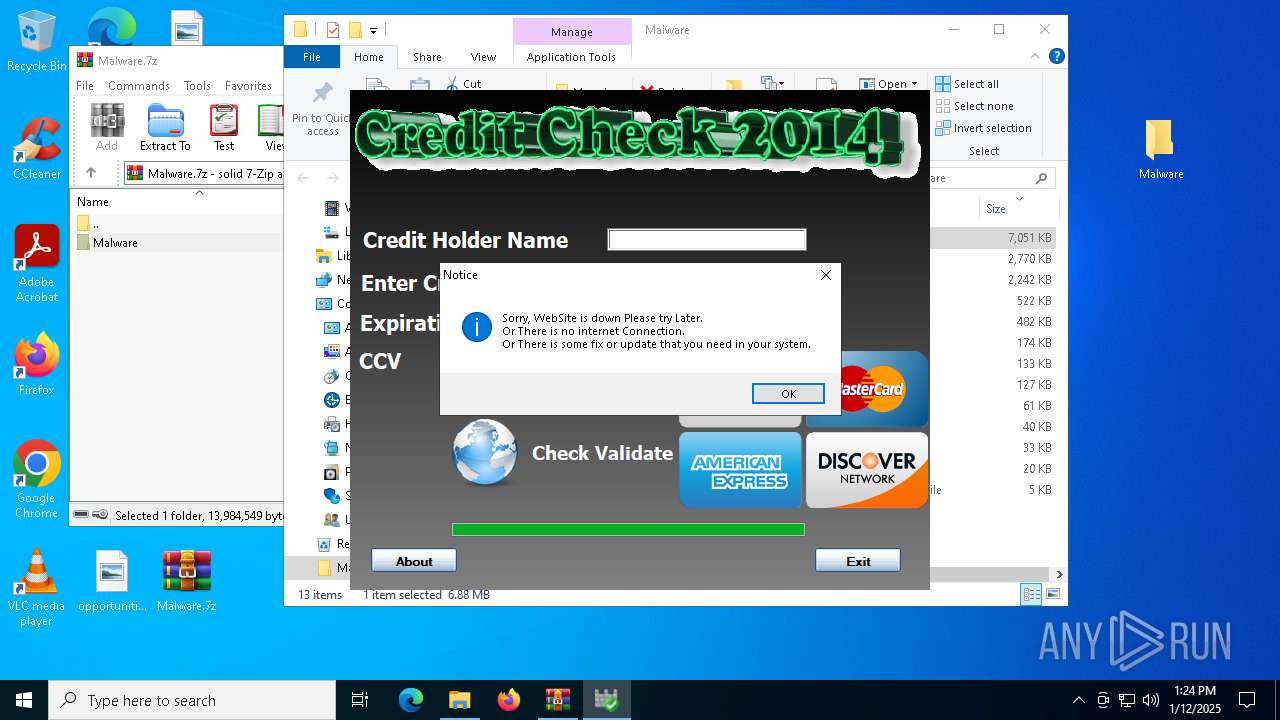
| 2088 | "C:\Users\admin\Desktop\Malware\Credit Card Checker 2014.exe" | C:\Users\admin\Desktop\Malware\Credit Card Checker 2014.exe | — | explorer.exe | |||||||||||
User: admin Company: Powered by Credit Checker 2014 Integrity Level: MEDIUM Description: http://creditcheck2014.blogspot.com/ Exit code: 3221226540 Version: 2.1.3.5 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\appdata\local\google.exe" | C:\Users\admin\AppData\Local\google.exe | njrat 0.6.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 3912 | "C:\Users\admin\Desktop\Malware\PooHack (1).exe" | C:\Users\admin\Desktop\Malware\PooHack (1).exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: SimpleRadar Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4076 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4076 | "C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\autorun.exe" "SFXSOURCE:C:\Users\admin\Desktop\Malware\Credit Card Checker 2014.exe" | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\autorun.exe | — | Credit Card Checker 2014.exe | |||||||||||
User: admin Company: Powered by Credit Checker 2014 Integrity Level: HIGH Description: http://creditcheck2014.blogspot.com/ Exit code: 0 Version: 2.1.3.5 Modules
| |||||||||||||||
| 4504 | "C:\Users\admin\Desktop\Malware\Credit Card Checker 2014.exe" | C:\Users\admin\Desktop\Malware\Credit Card Checker 2014.exe | explorer.exe | ||||||||||||
User: admin Company: Powered by Credit Checker 2014 Integrity Level: HIGH Description: http://creditcheck2014.blogspot.com/ Exit code: 0 Version: 2.1.3.5 Modules
| |||||||||||||||
| 4592 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | PooHack (1).exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4876 | "C:\Users\admin\Desktop\Malware\Steam Vac Unbanner by Blodyclan96.exe" | C:\Users\admin\Desktop\Malware\Steam Vac Unbanner by Blodyclan96.exe | — | explorer.exe | |||||||||||
User: admin Company: Blodyclan96 Integrity Level: MEDIUM Description: Steam Vac Unbanner by Blodyclan96 Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
15 820
Read events
15 167
Write events
651
Delete events
2
Modification events
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Malware.7z | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (828) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4076) autorun.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\MediaResources\DirectSound\Speaker Configuration |
| Operation: | write | Name: | Speaker Configuration |
Value: 4 | |||
| (PID) Process: | (6228) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | msg |
Value: wscript.exe //B "C:\Users\admin\AppData\Local\Temp\msg.vbs" | |||
Executable files
41
Suspicious files
24
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa828.3947\Malware\stub.exe | executable | |
MD5:A35523B624C9E25669643A9D7C9999A1 | SHA256:40823ED33D1A420BA675BCB6D880D951A89FB78E256A43DA1C32EFB6E8A81D16 | |||
| 828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa828.3947\Malware\njrat 0.6.exe | executable | |
MD5:7D4190B1EE0E4C41CED4664B9B8A4A21 | SHA256:2A0EE1701FDB3D2DFF2C25BEDFD41925699F5B80A7D4C3C75365CDAE8FD2E1E4 | |||
| 828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa828.3947\Malware\Email Hacker.exe | executable | |
MD5:07A66A43588311B6045004B0759D47F2 | SHA256:DBFB0C6855D91233890D8E47C8F9906D6EF73CD92E2CF109ADC669D9F4286A24 | |||
| 828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa828.3947\Malware\loginServer.exe | executable | |
MD5:4E65CAB63599F2BBAAEE0C06BAD441AB | SHA256:6B1E8666CCCBDF703D7B2427A71B5E28C22967A3CDC053A87E998DE7D335A933 | |||
| 4504 | Credit Card Checker 2014.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\Click1.ogg | binary | |
MD5:93270C4FA492E4E4EDEE872A2B961DDE | SHA256:25D49CBBD65D48AD462455F1143F73EE997DF8F747E7D2213DAAB18E321C028B | |||
| 4504 | Credit Card Checker 2014.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Buttons\0002-royale.btn | compressed | |
MD5:0B933456BBFFD11B50F14F391A4B0695 | SHA256:89786C6CC4CBF430C9AEE1F8131EFEFF8A4ADF6617535AADE525FA909441A38F | |||
| 4504 | Credit Card Checker 2014.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Buttons\0001-windows-7.btn | compressed | |
MD5:967FDFE0A01C083804673B4976AD6730 | SHA256:72EDA9D49BCD0CD3B540F75C4215714378AFBB1CE40AFCBB7A0B246AB2A44F21 | |||
| 828 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa828.3947\Malware\Paypal-adder.exe | executable | |
MD5:E237A341D0201E7D69A2E4D58E4F990D | SHA256:28FF33F8A31454EA52BCC719882087DA985EFE9DF7EC2560D69943F8BACDAF7D | |||
| 4504 | Credit Card Checker 2014.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Audio\APOCALYPTiCA - Guitarz 6.5crk.ogg | binary | |
MD5:C832B9274CCD5DC90119F676EFDEA6CC | SHA256:8E5986C7E72B4E3506FB5F313D5F20950E419B33697D2A1085D3FB428EFAC20F | |||
| 4504 | Credit Card Checker 2014.exe | C:\Users\admin\AppData\Local\Temp\ir_ext_temp_0\AutoPlay\Buttons\button-documentation.btn | compressed | |
MD5:F10D0E454B29CA2579BED4C18CD10561 | SHA256:0A76A2620FE34E874E4DBA8268240D3BE75392157D284AAA190F389AD0CCD4B3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
61
DNS requests
181
Threats
160
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6424 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4264 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6424 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3568 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.204.157:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
1176 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
google-chrome.servehttp.com |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a *.dyndns-ip .com Domain |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
2192 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.servehttp .com |
Process | Message |
|---|---|
njrat 0.6.exe | BILGE:TONYUKUK:BEN:ÖZÜM:TABGAC:ILINGE:KILINDIM:TÜRK:BODUNU:TABGACKA:KÖRÜK:ERTI |
google.exe | BILGE:TONYUKUK:BEN:ÖZÜM:TABGAC:ILINGE:KILINDIM:TÜRK:BODUNU:TABGACKA:KÖRÜK:ERTI |