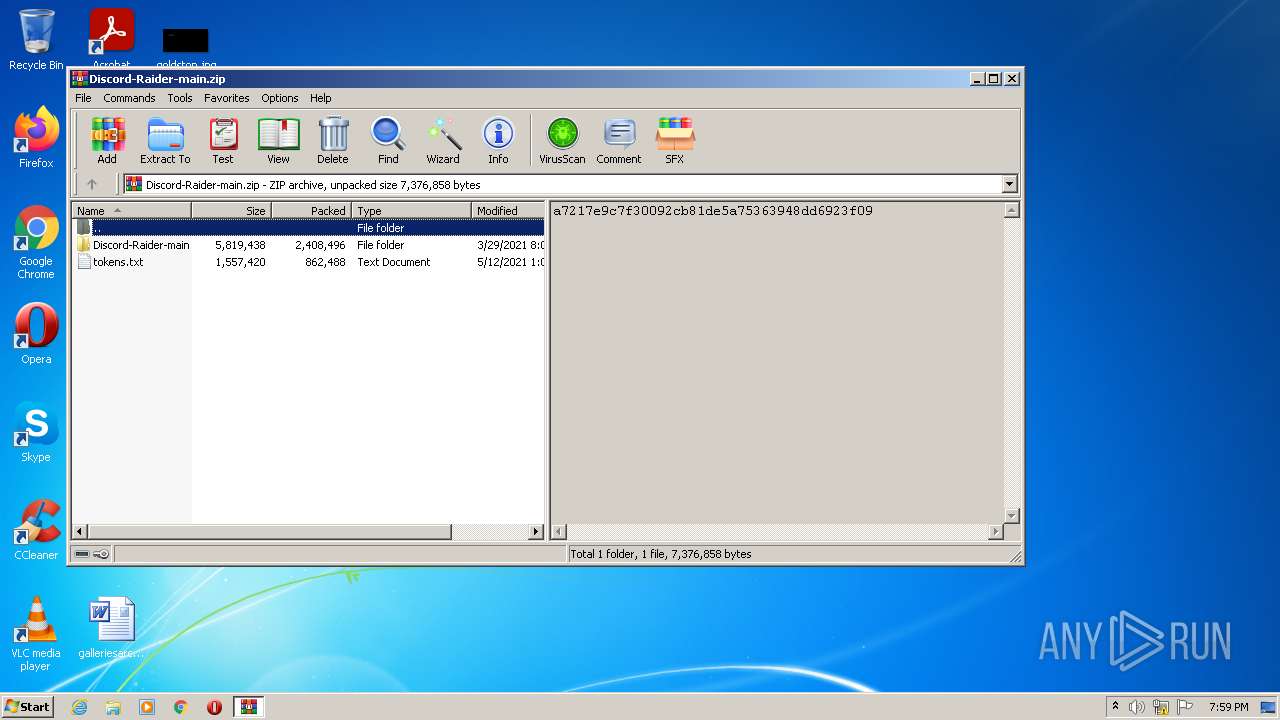
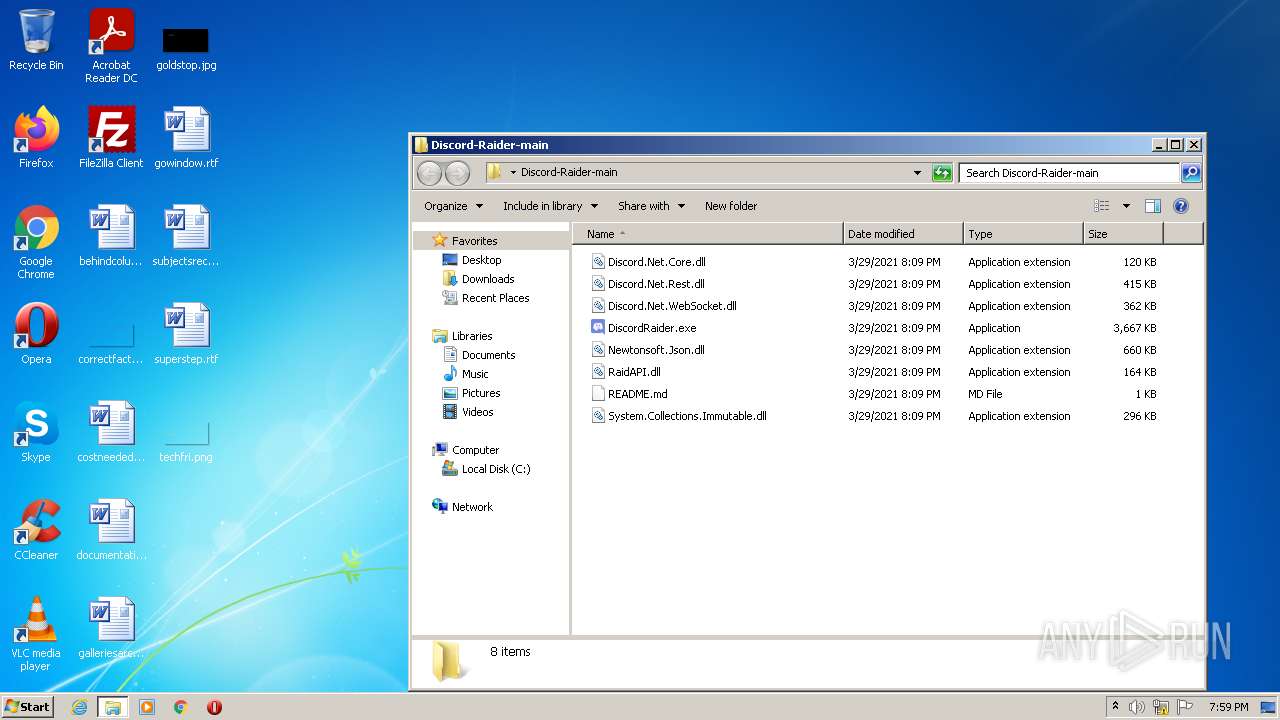
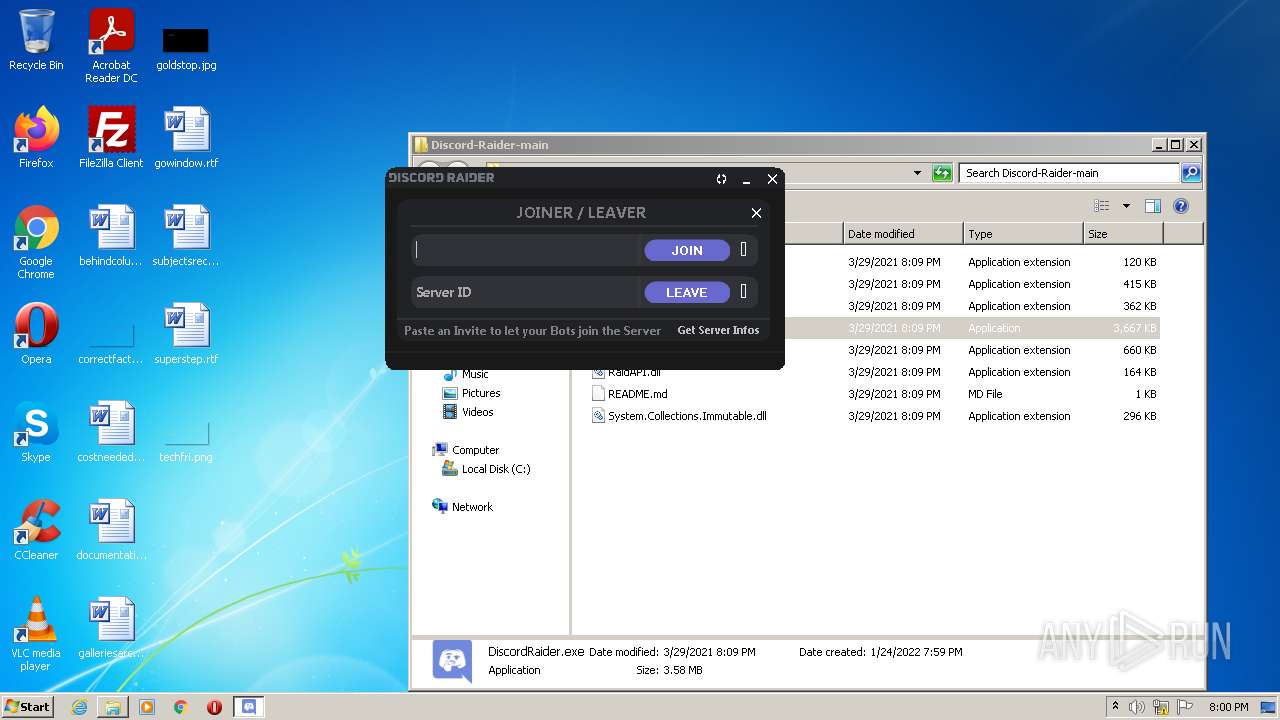
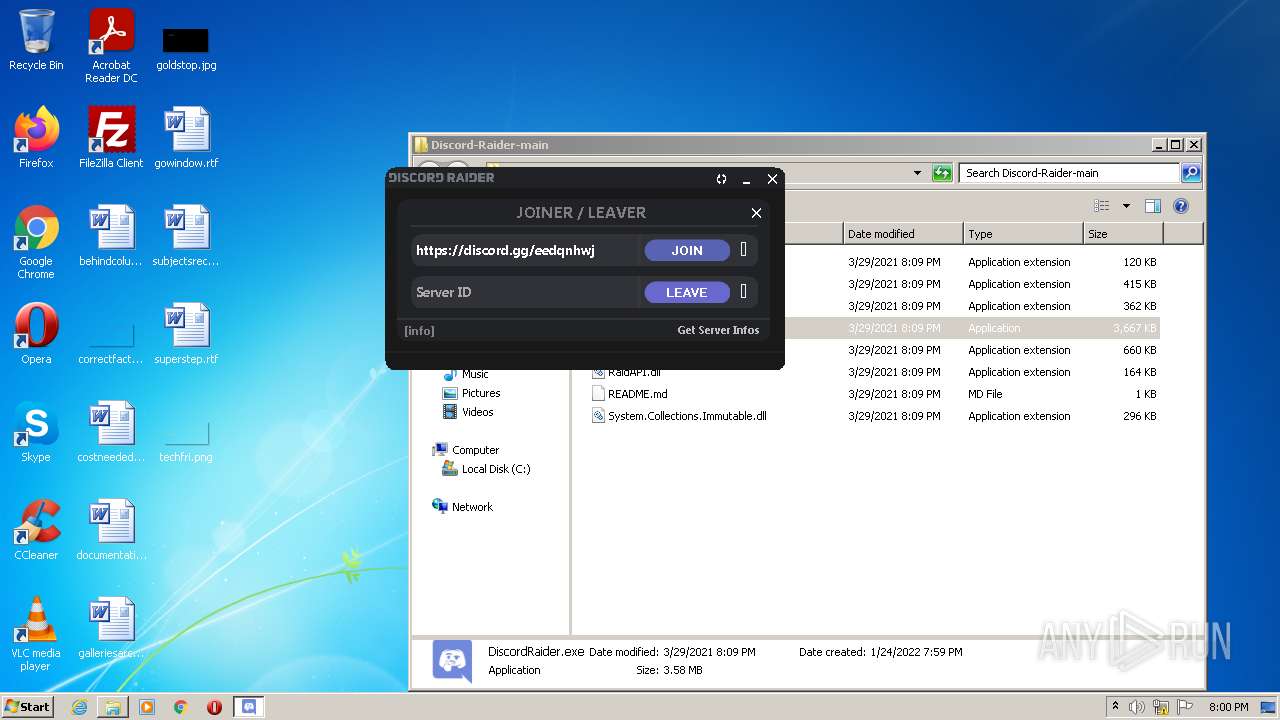
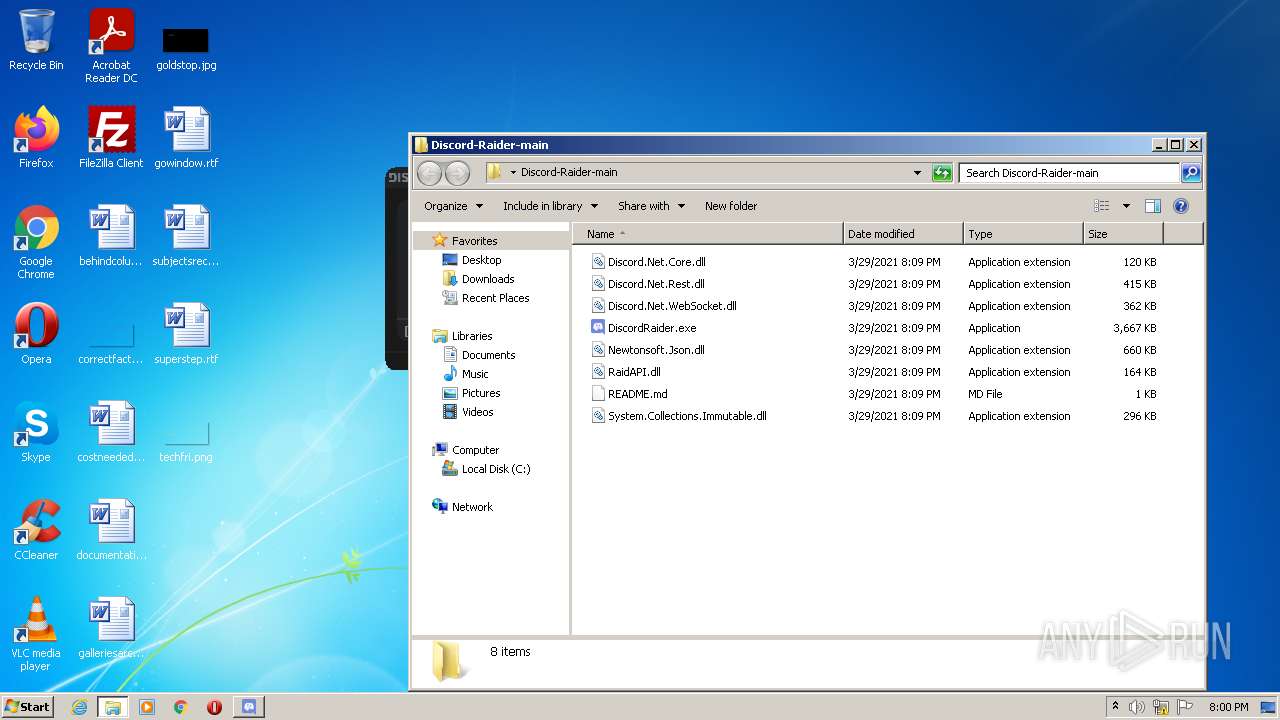
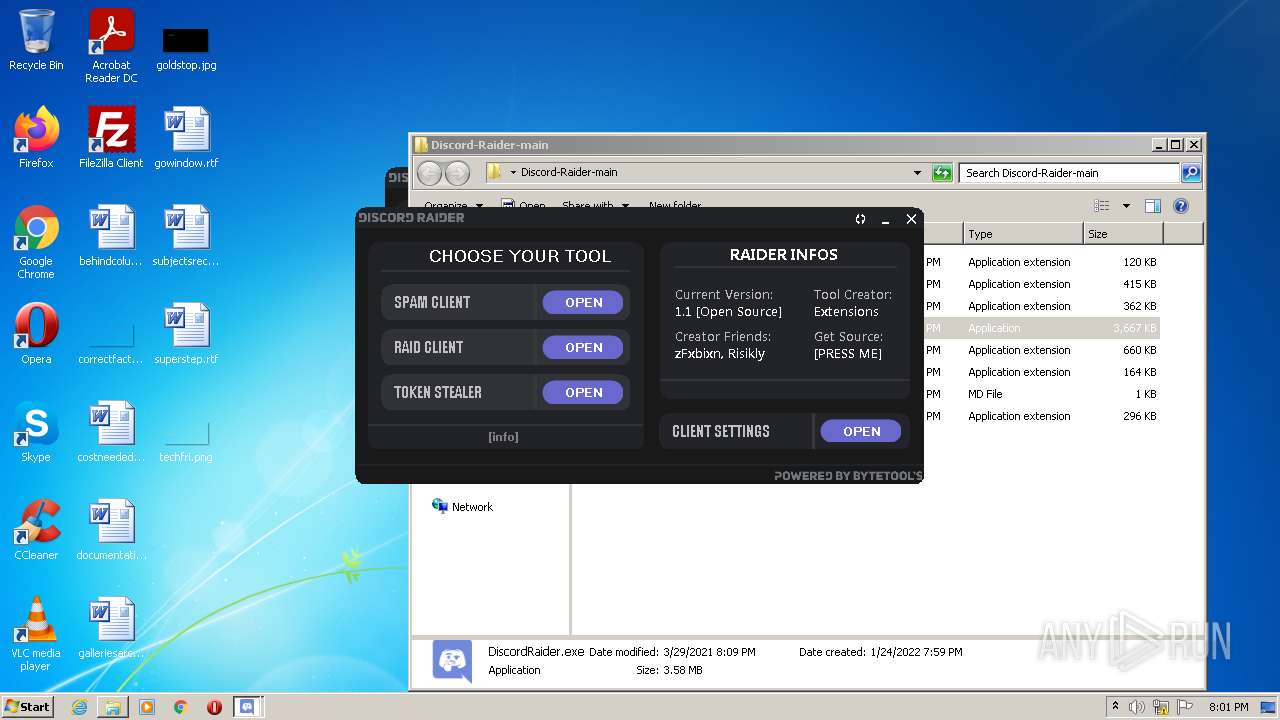
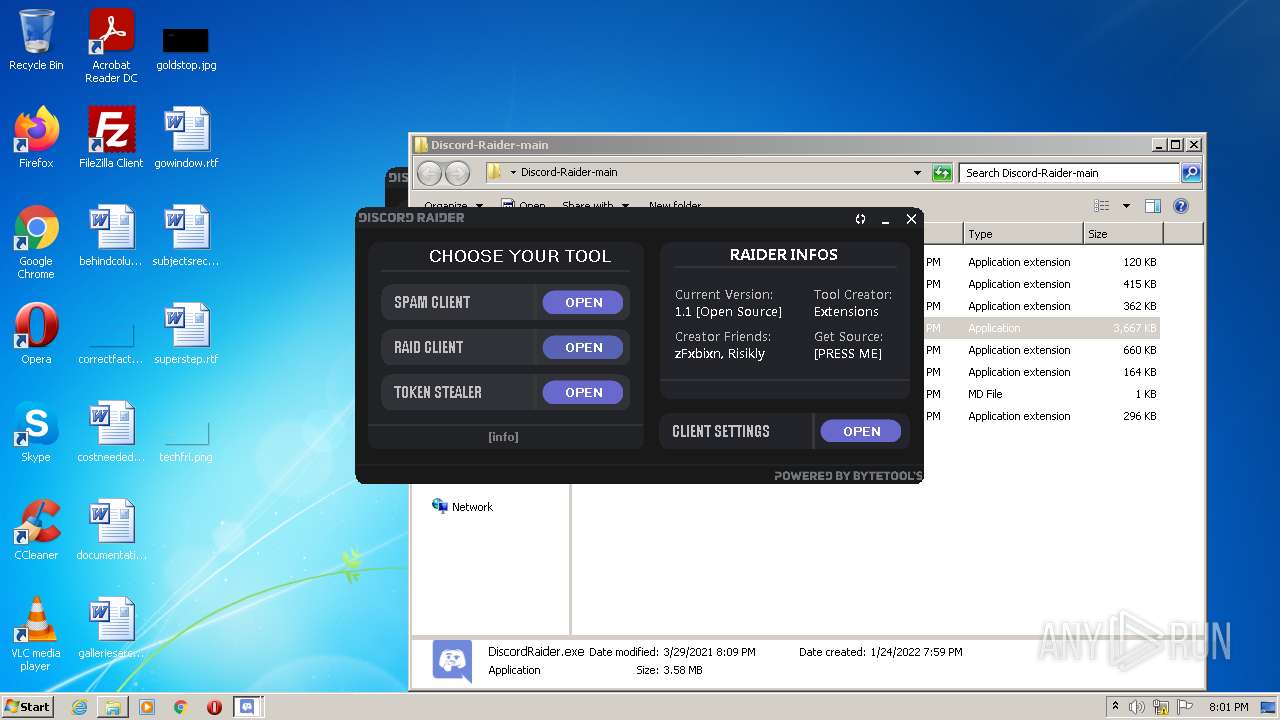
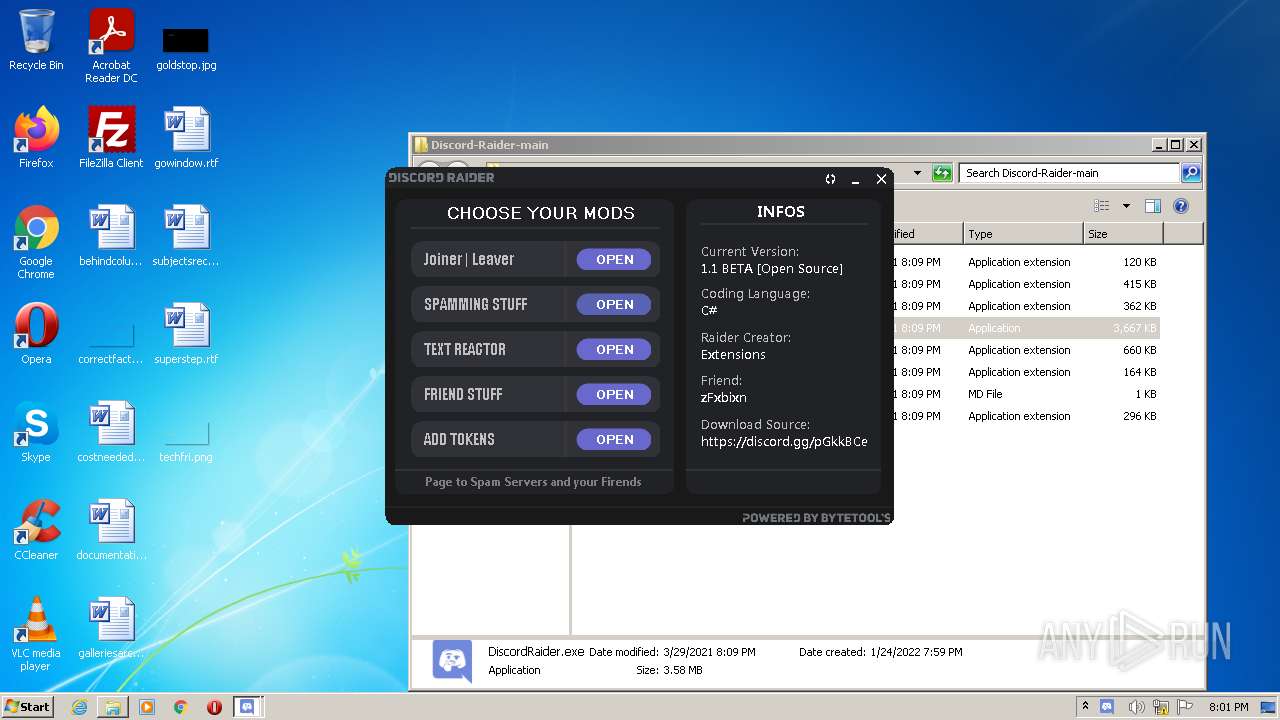
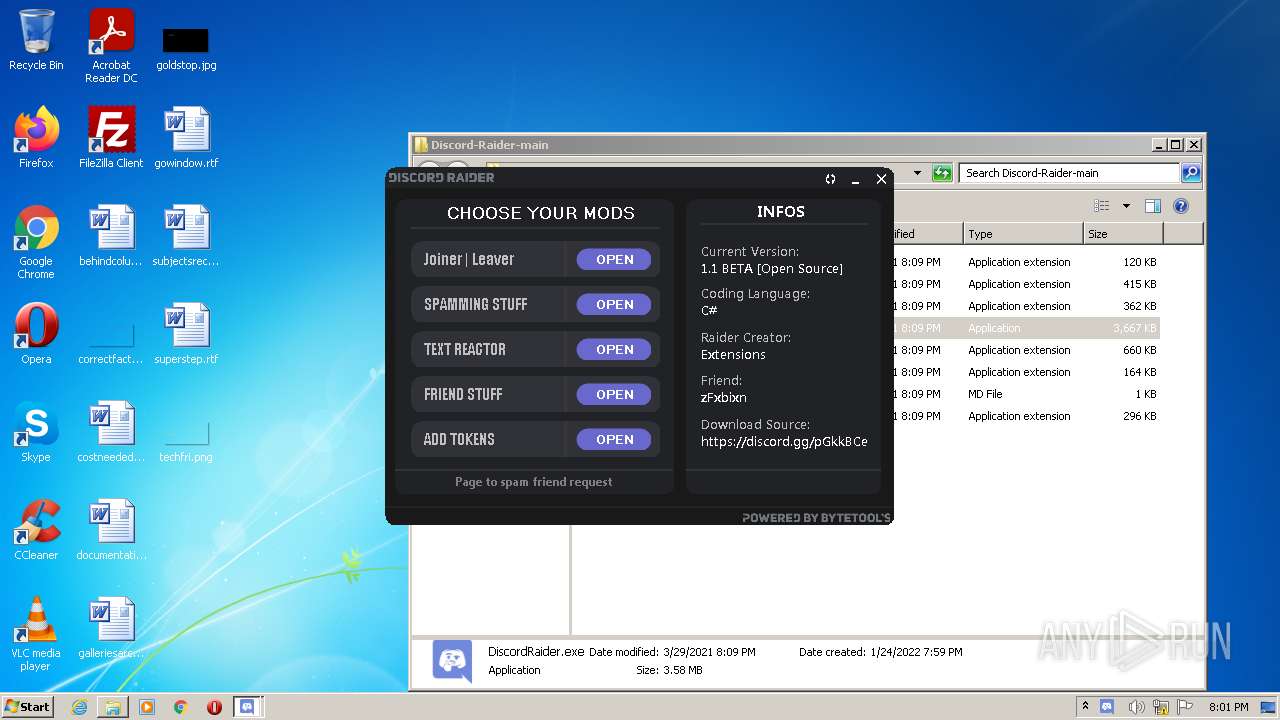
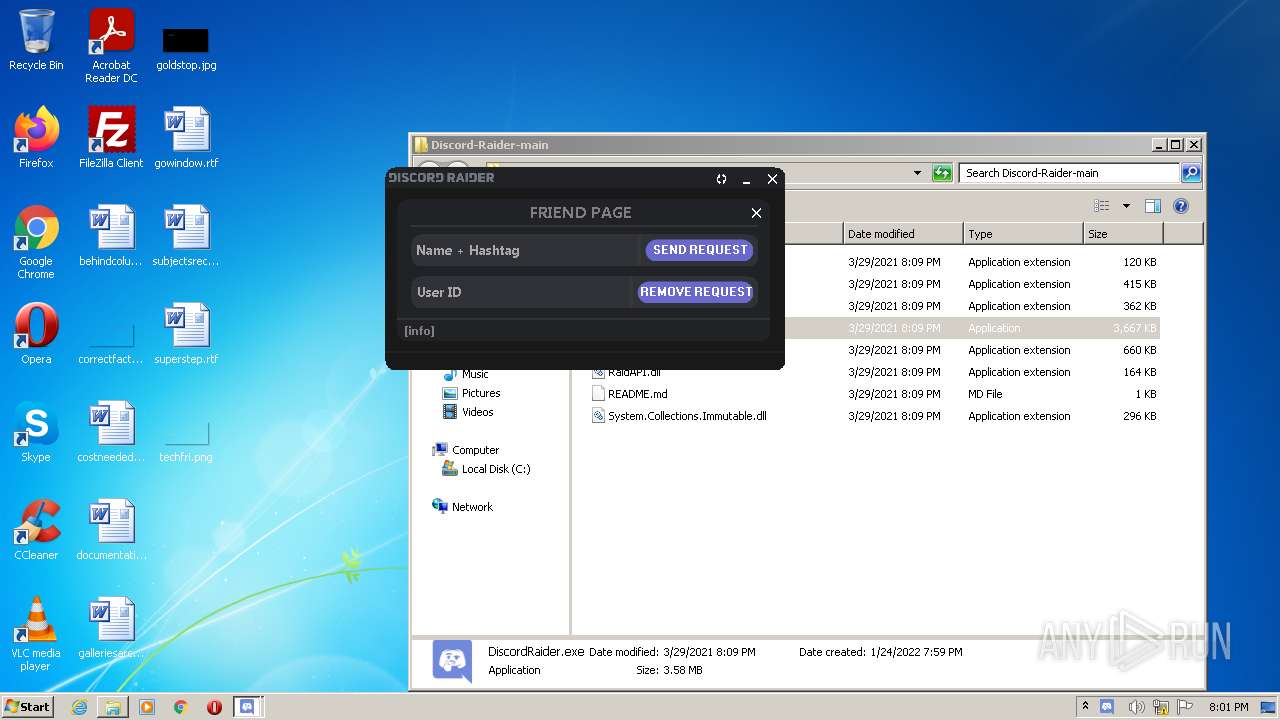
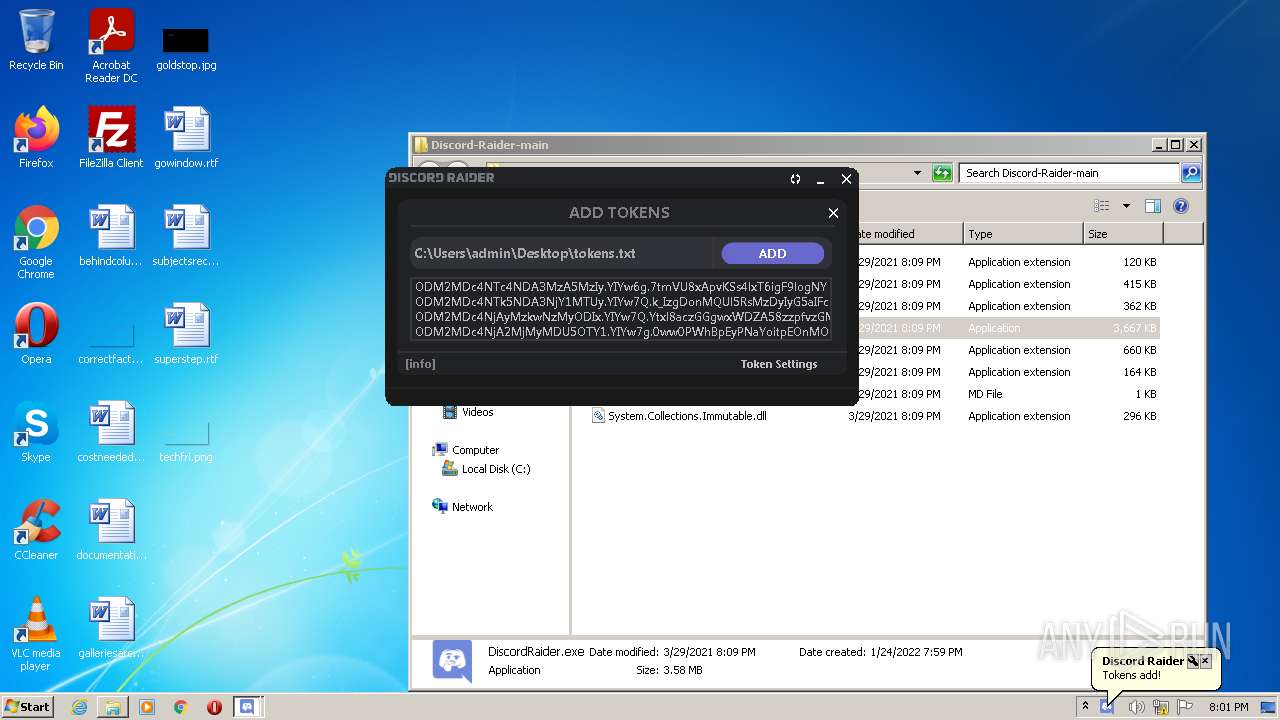
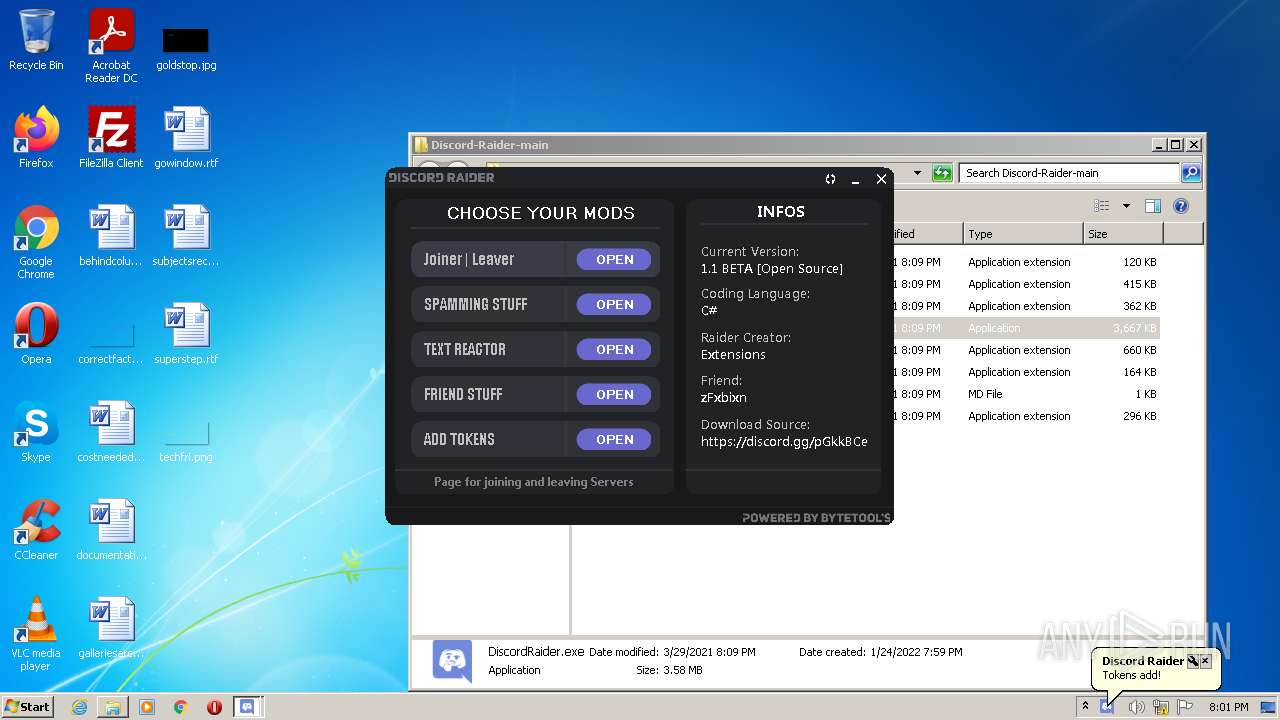
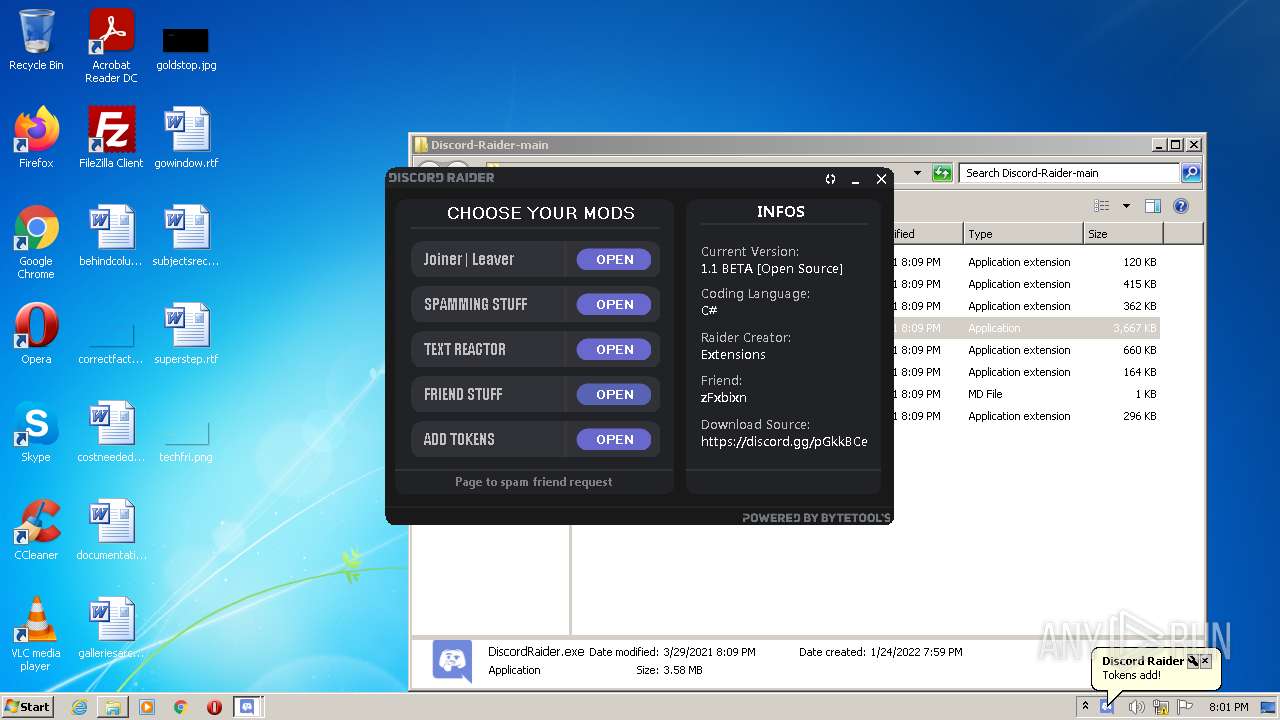
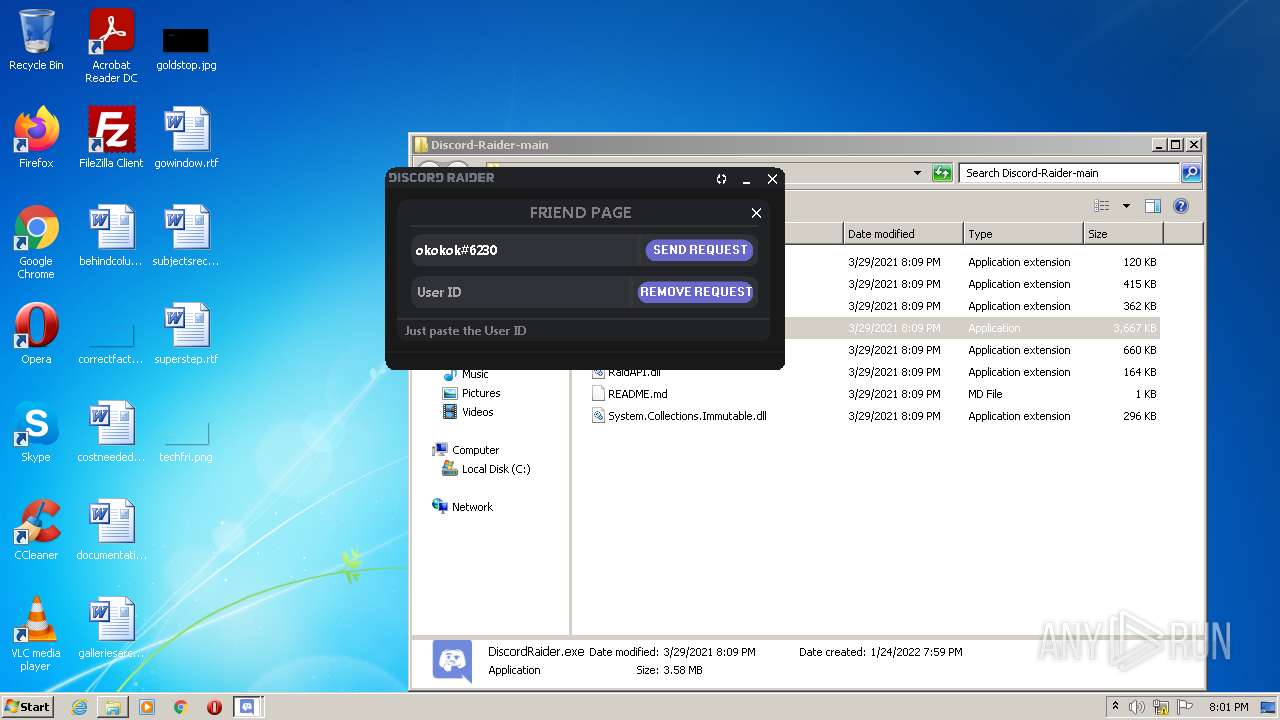
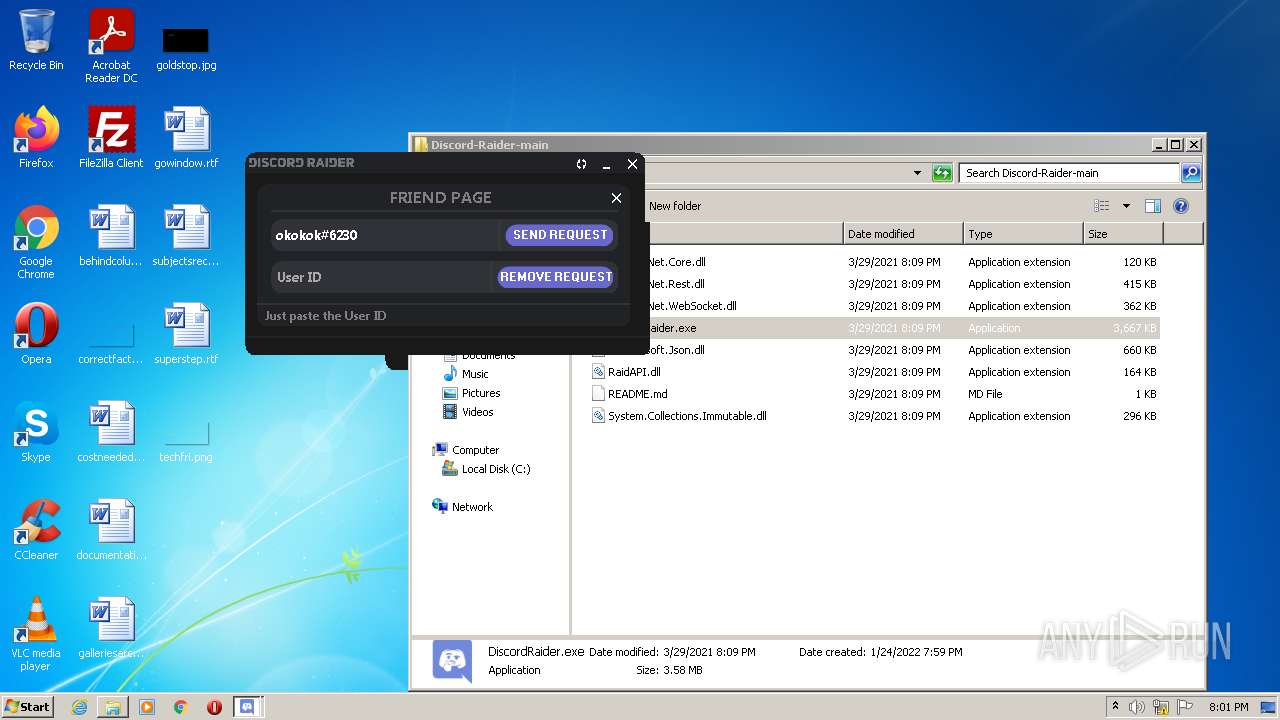
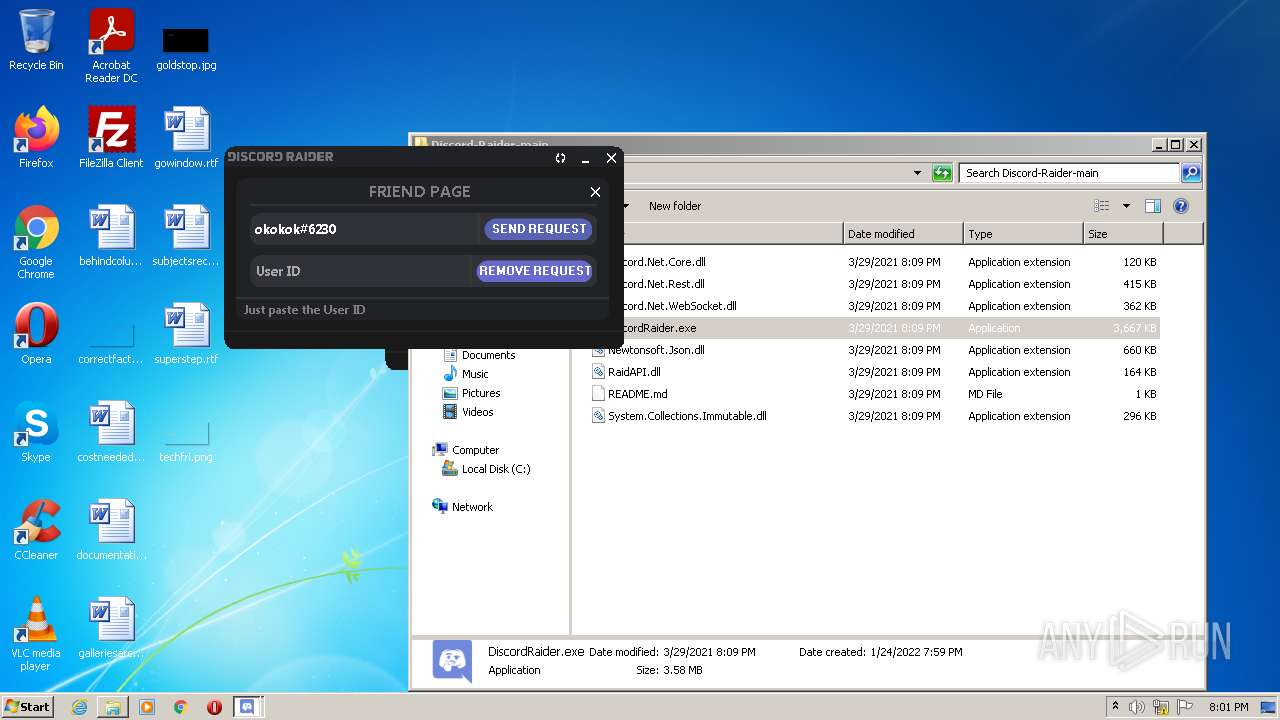
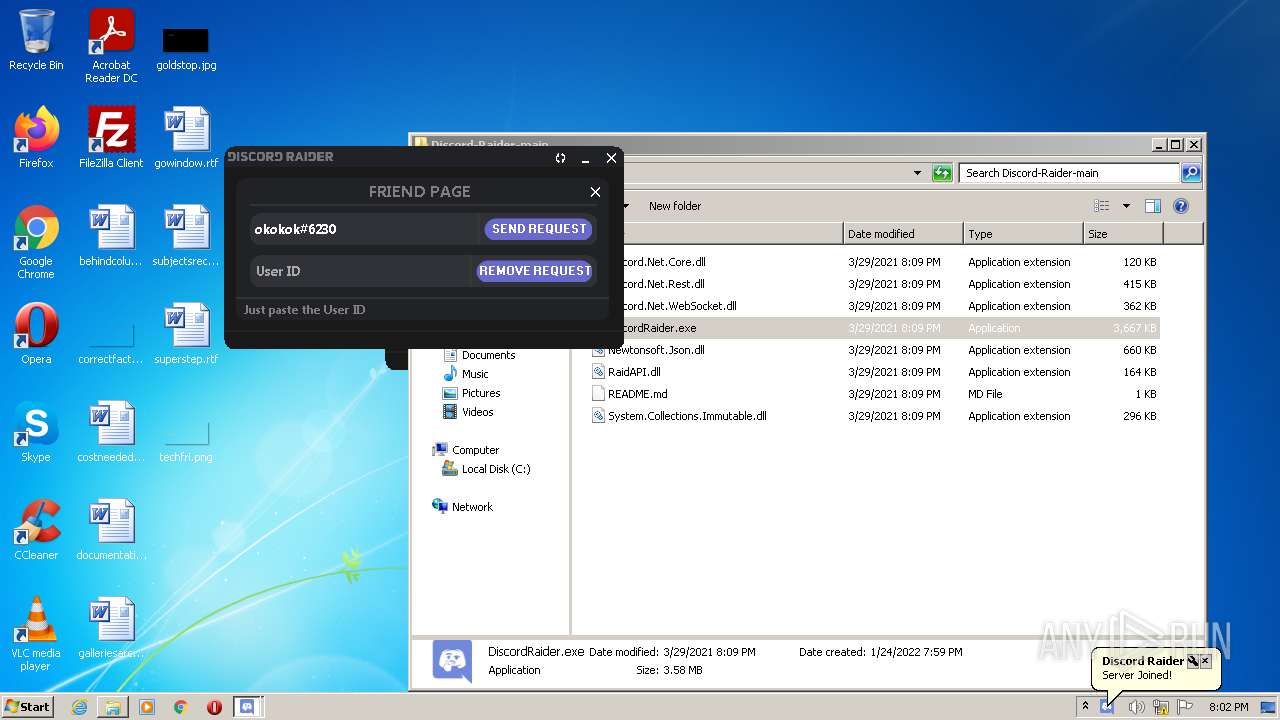
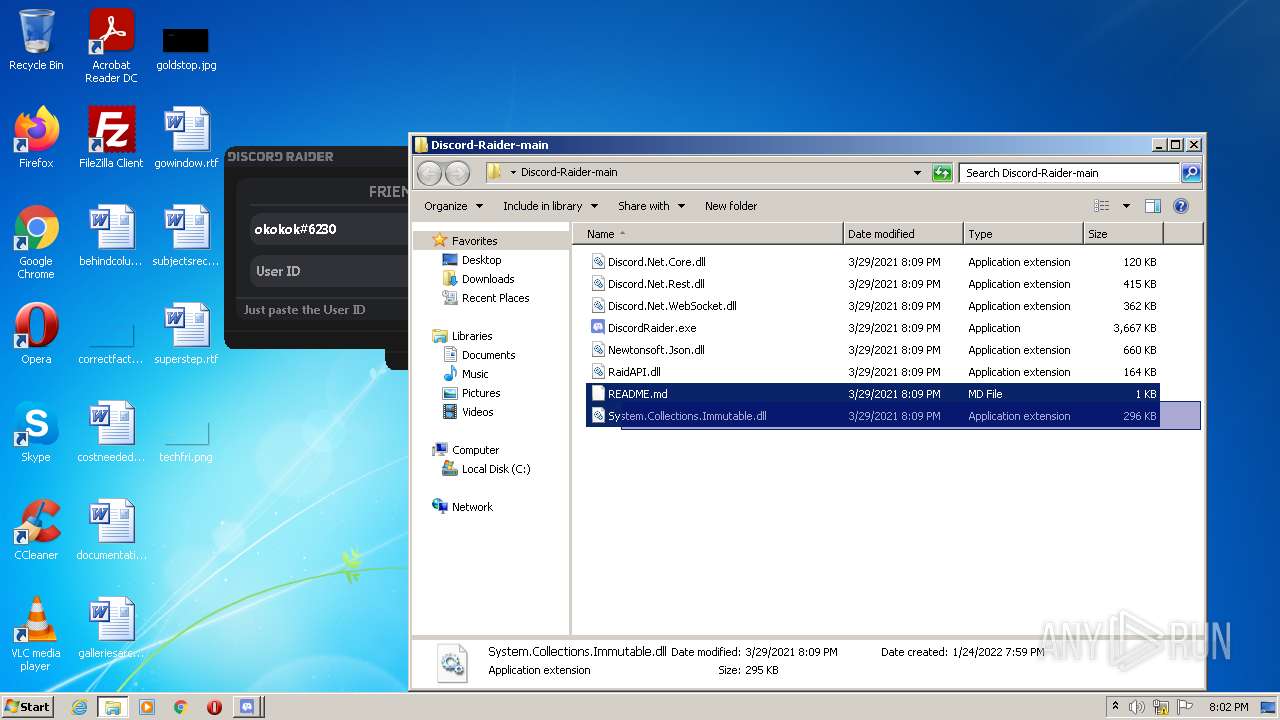
| File name: | Discord-Raider-main.zip |
| Full analysis: | https://app.any.run/tasks/73862477-bac1-4347-8c50-550c88dd2c50 |
| Verdict: | Malicious activity |
| Analysis date: | January 24, 2022, 19:59:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | 6C78D24848BFEE1842E883B3D4E62DE9 |
| SHA1: | 51505E8E30E5DF6051789F3BA8194D88424226BE |
| SHA256: | A0F14704B7DF5C28FD35548EEC3D04E66EAE1B5730C57592F6A5EED61A9E16EF |
| SSDEEP: | 98304:wAjVZHG51MnvQATiTeNVYy2Jo2vG13PVXVjelms9/:p+ATiTe+y2JFvGbds9/ |
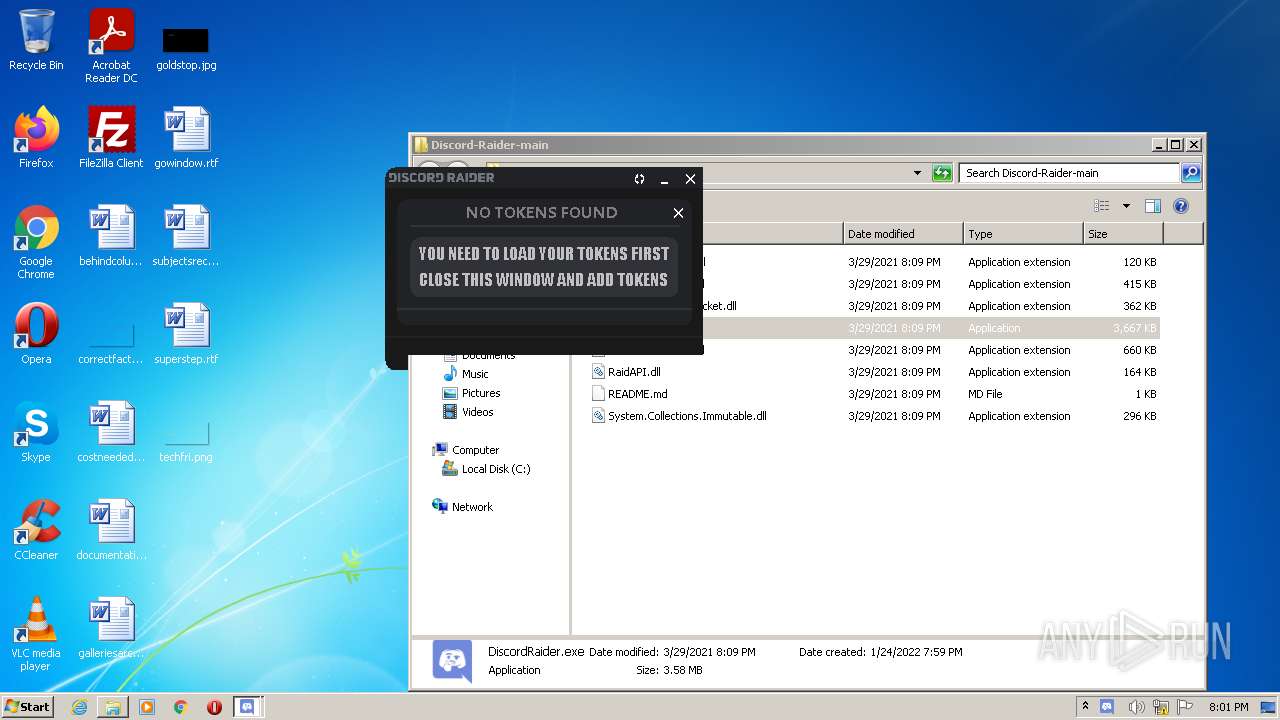
MALICIOUS
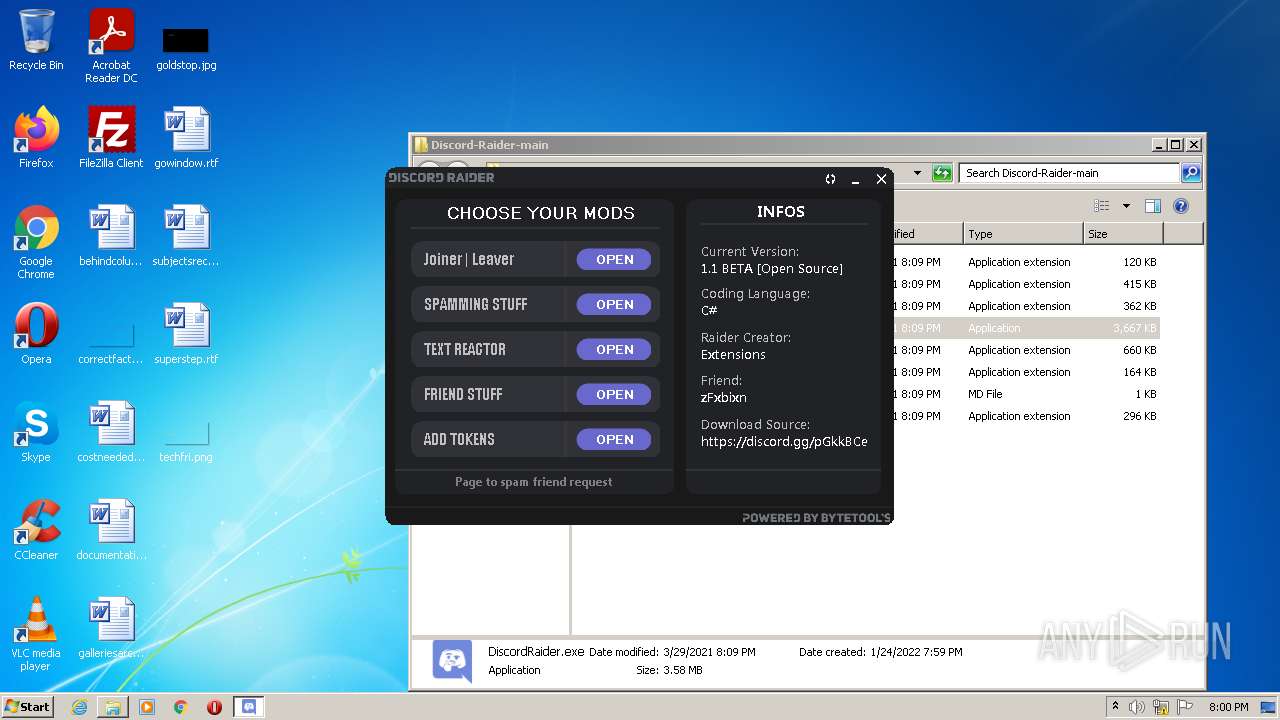
Drops executable file immediately after starts
- Explorer.EXE (PID: 1656)
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3836)
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
- Explorer.EXE (PID: 1656)
Application was dropped or rewritten from another process
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1408)
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
Checks supported languages
- WinRAR.exe (PID: 1408)
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 1408)
- Explorer.EXE (PID: 1656)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1408)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1408)
- Explorer.EXE (PID: 1656)
Reads Environment values
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
Creates files in the user directory
- Explorer.EXE (PID: 1656)
INFO
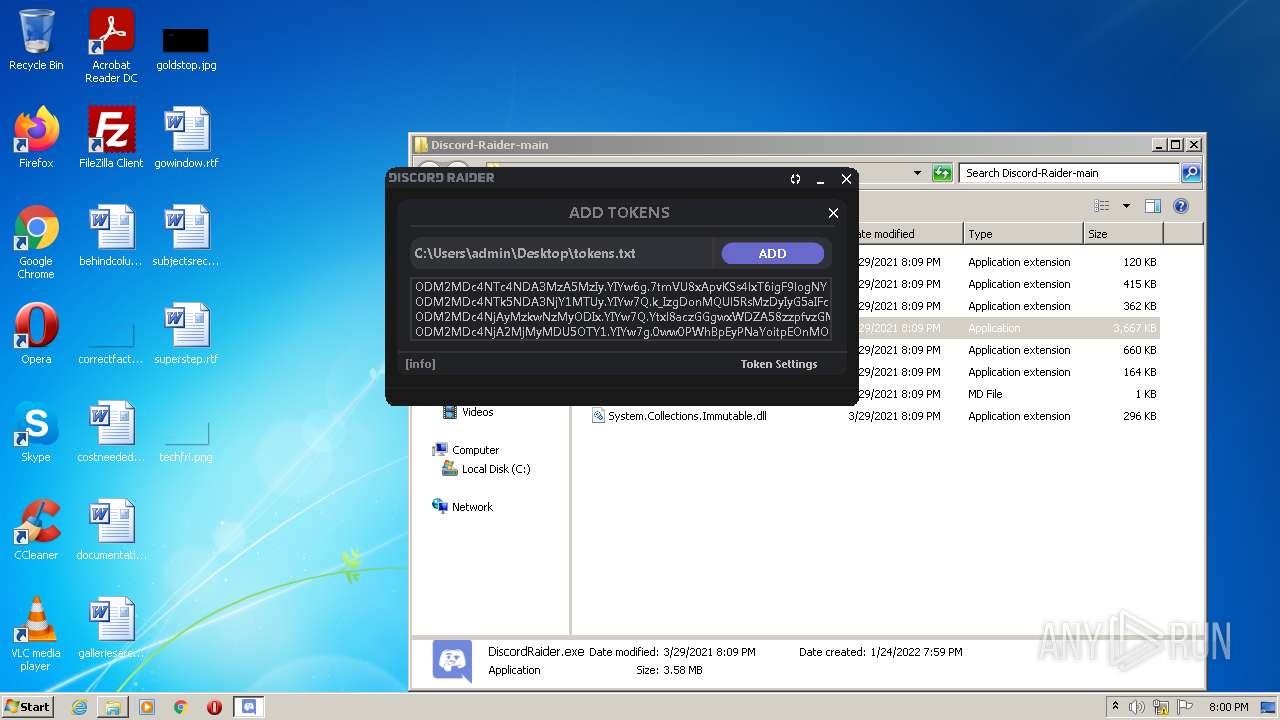
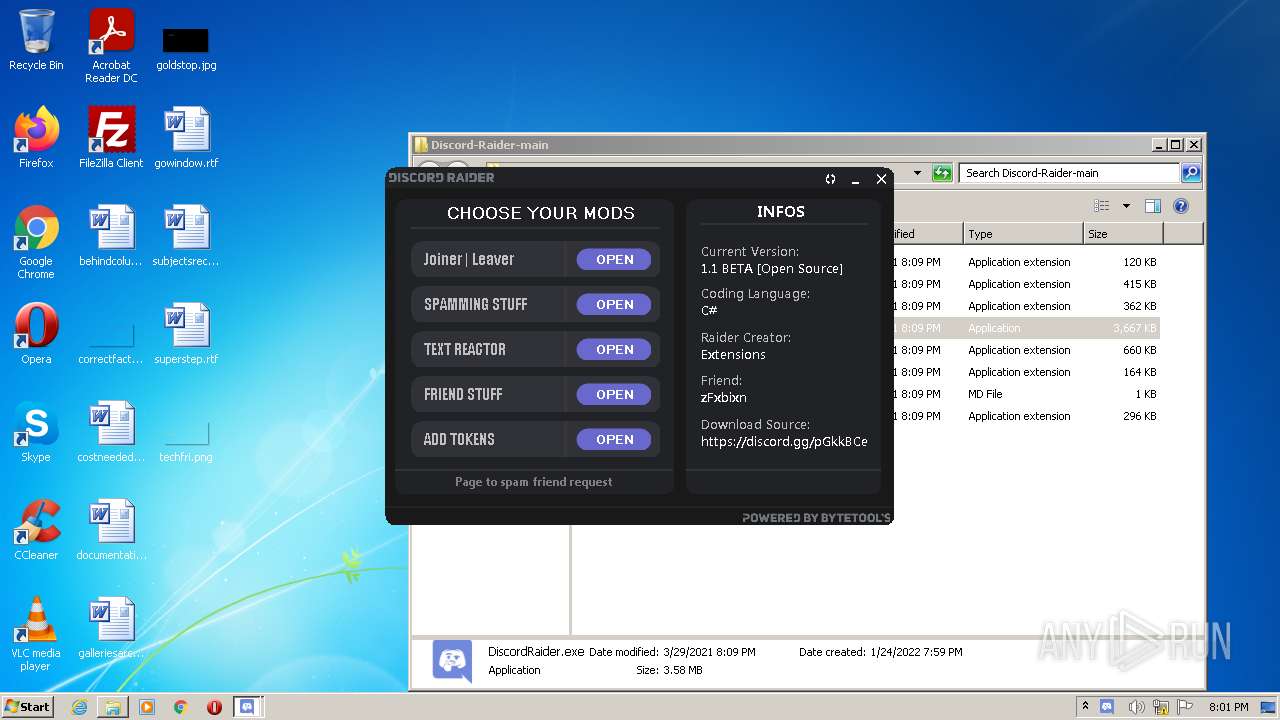
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1408)
- Explorer.EXE (PID: 1656)
Manual execution by user
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
Reads settings of System Certificates
- DiscordRaider.exe (PID: 2512)
- DiscordRaider.exe (PID: 984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Discord-Raider-main/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:03:29 12:09:28 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 10 |
Total processes
41
Monitored processes
5
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 984 | "C:\Users\admin\Desktop\Discord-Raider-main\DiscordRaider.exe" | C:\Users\admin\Desktop\Discord-Raider-main\DiscordRaider.exe | Explorer.EXE | ||||||||||||
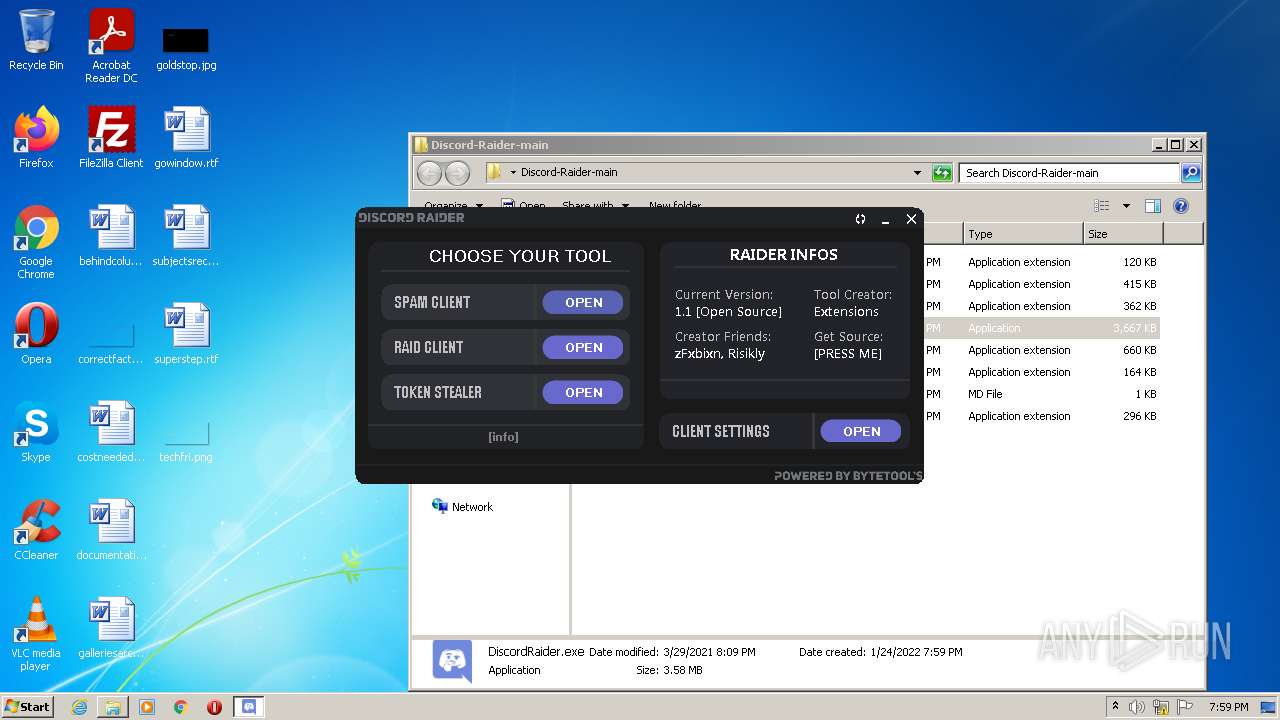
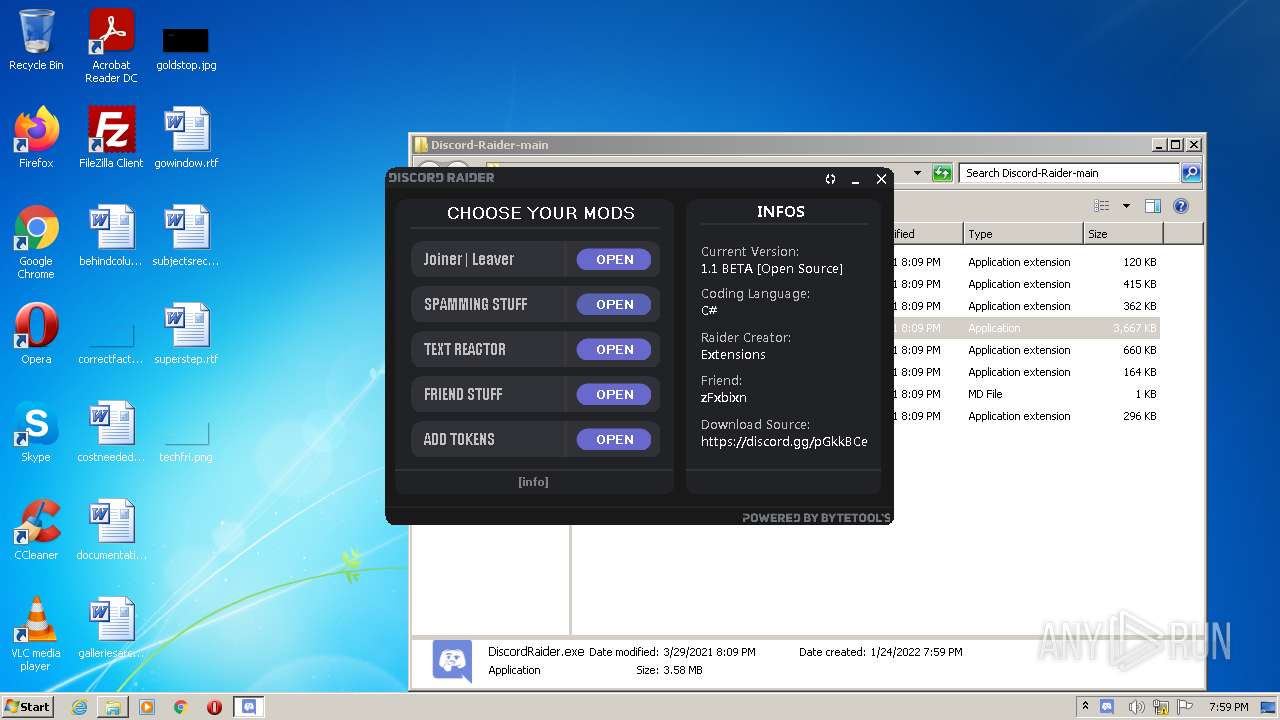
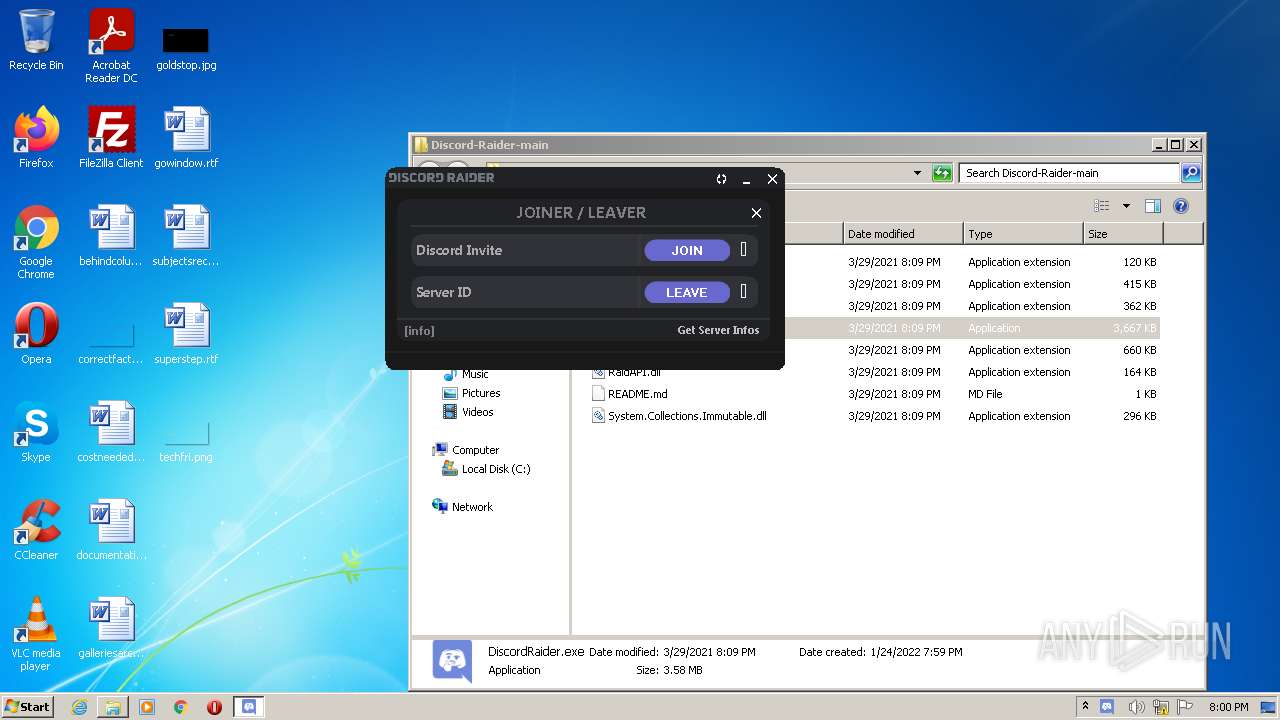
User: admin Integrity Level: MEDIUM Description: Discord Raider By Extensions Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1408 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Discord-Raider-main.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1656 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\Desktop\Discord-Raider-main\DiscordRaider.exe" | C:\Users\admin\Desktop\Discord-Raider-main\DiscordRaider.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Discord Raider By Extensions Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3836 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe3_ Global\UsGthrCtrlFltPipeMssGthrPipe3 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
19 414
Read events
19 076
Write events
330
Delete events
8
Modification events
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Discord-Raider-main.zip | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1408) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
14
Suspicious files
0
Text files
8
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
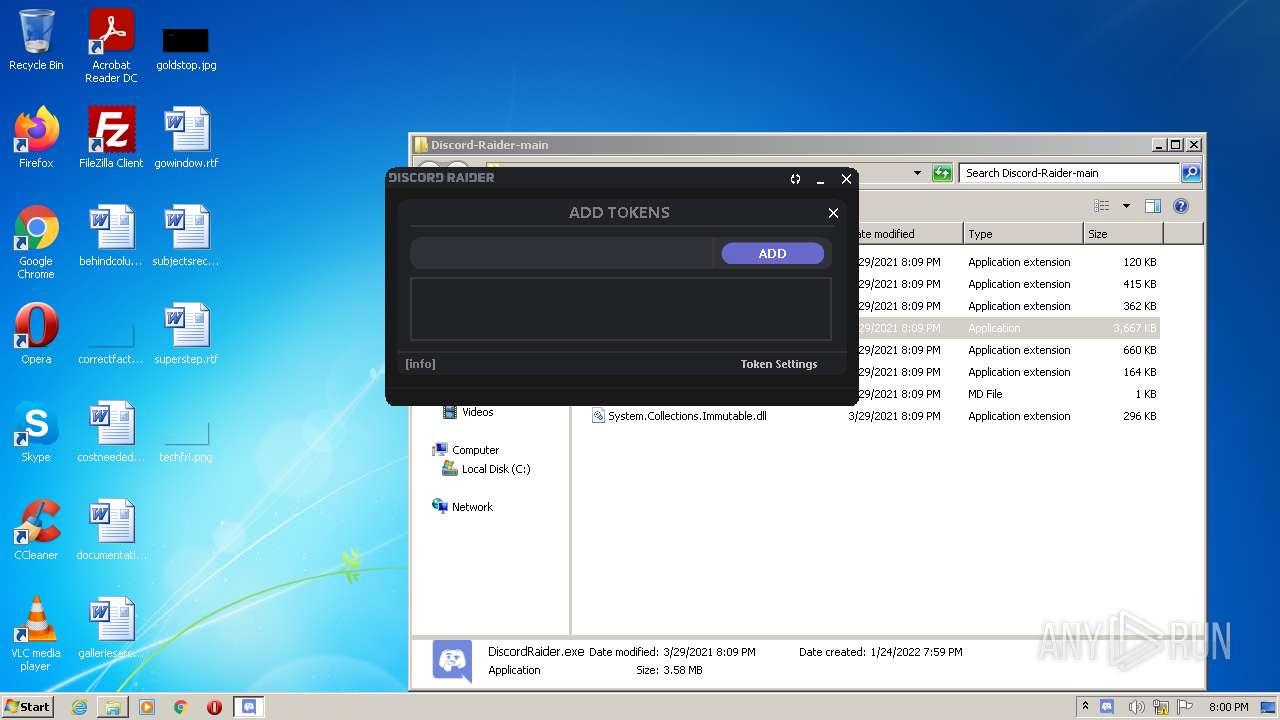
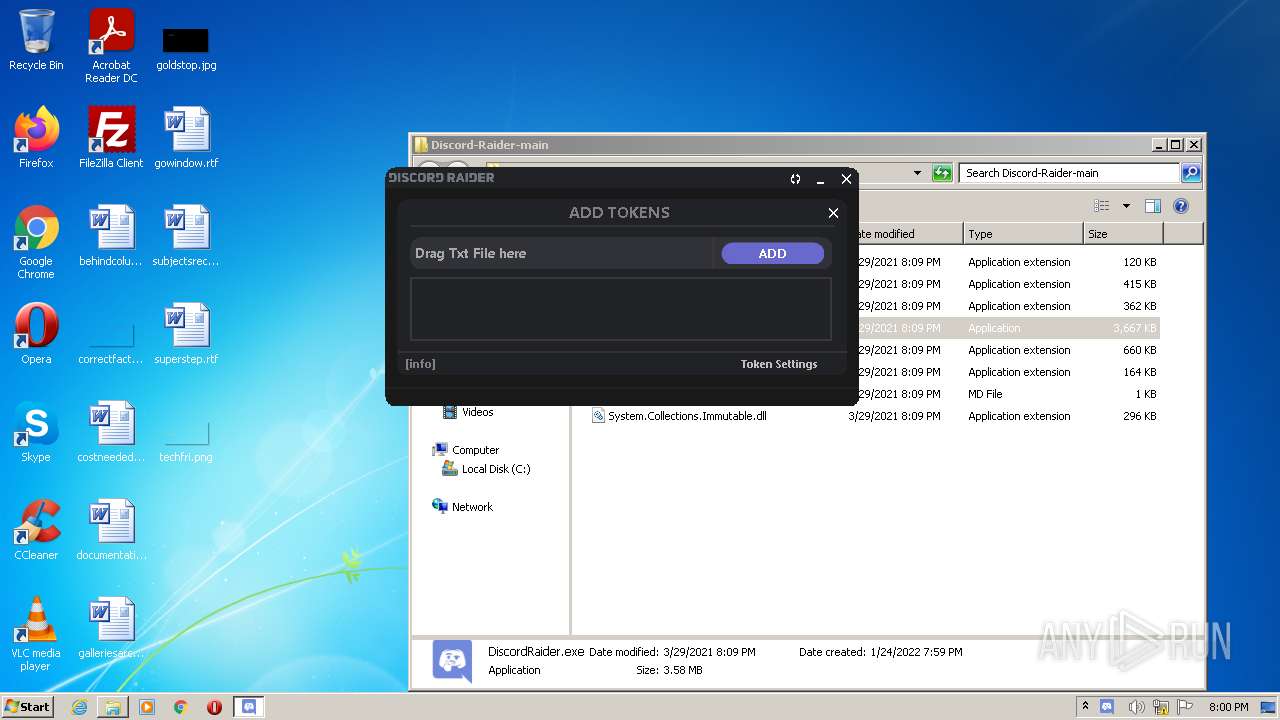
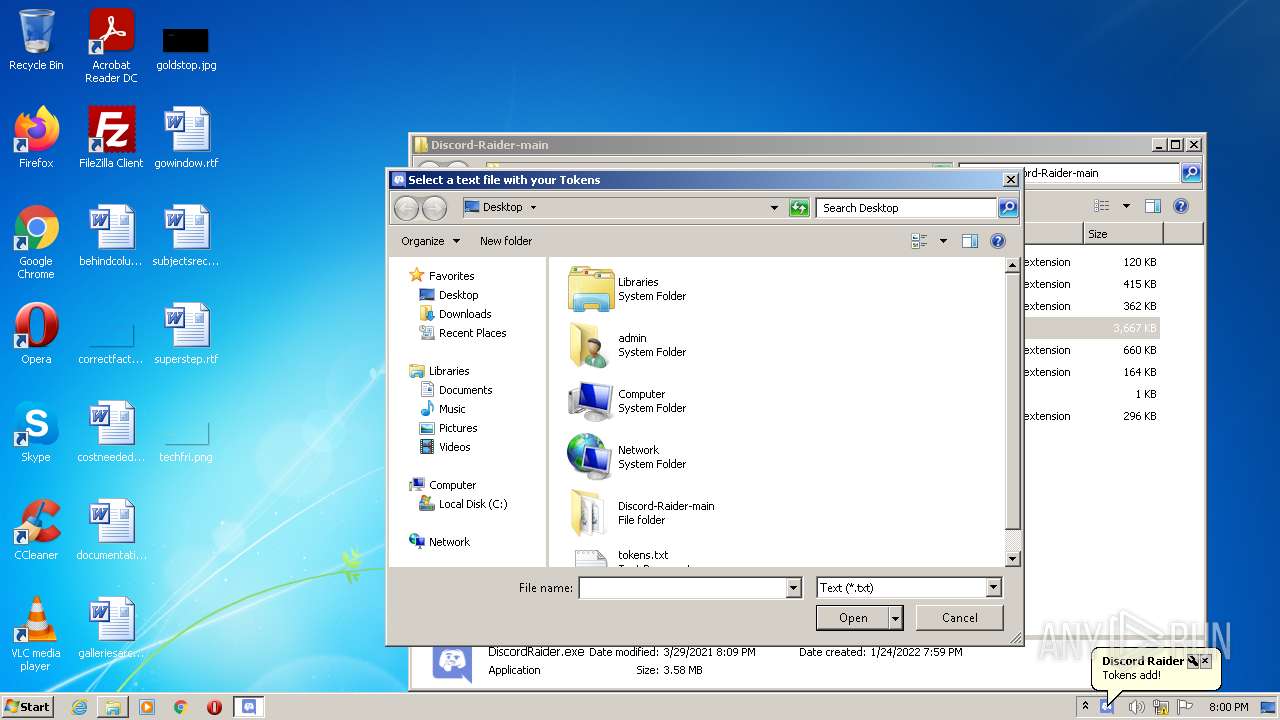
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\tokens.txt | text | |
MD5:— | SHA256:— | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\Newtonsoft.Json.dll | executable | |
MD5:4DF6C8781E70C3A4912B5BE796E6D337 | SHA256:3598CCCAD5B535FEA6F93662107A4183BFD6167BF1D0F80260436093EDC2E3AF | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\Discord.Net.Rest.dll | executable | |
MD5:360B5CEC575080F52030BDCD8D02A5A3 | SHA256:99265D78C4E55267ED476A9861C226D5471CEF29FFCE6B00E1BCF5544073670B | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\README.md | text | |
MD5:04B81692C02EF9EFE3B94536AE70B508 | SHA256:ED39BD8E777F36710500C25B530E0B244B23067BC9EEF46FA7A4379F88990163 | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\Discord.Net.Core.dll | executable | |
MD5:D00FE9035E5936A65AD44D819CA7B392 | SHA256:F812A1DA84B579BE1032ACB06F13546220E1D26B79D9008659B5B4694353045D | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\RaidAPI.dll | executable | |
MD5:CB32F0166833761B9009C32DC122964E | SHA256:F3C37C3D71573368F463F053E6B5A90C5073DCE79559C8975E12E010E1FB5836 | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\System.Collections.Immutable.dll | executable | |
MD5:D8203AEDAABEAC1E606CD0E2AF397D01 | SHA256:2F05A2C489C2D30A6CCA346D4CE184323D70EB4F5AFA6BED34D5800274444E57 | |||
| 1656 | Explorer.EXE | C:\Users\admin\Desktop\Discord-Raider-main\Discord.Net.Core.dll | executable | |
MD5:D00FE9035E5936A65AD44D819CA7B392 | SHA256:F812A1DA84B579BE1032ACB06F13546220E1D26B79D9008659B5B4694353045D | |||
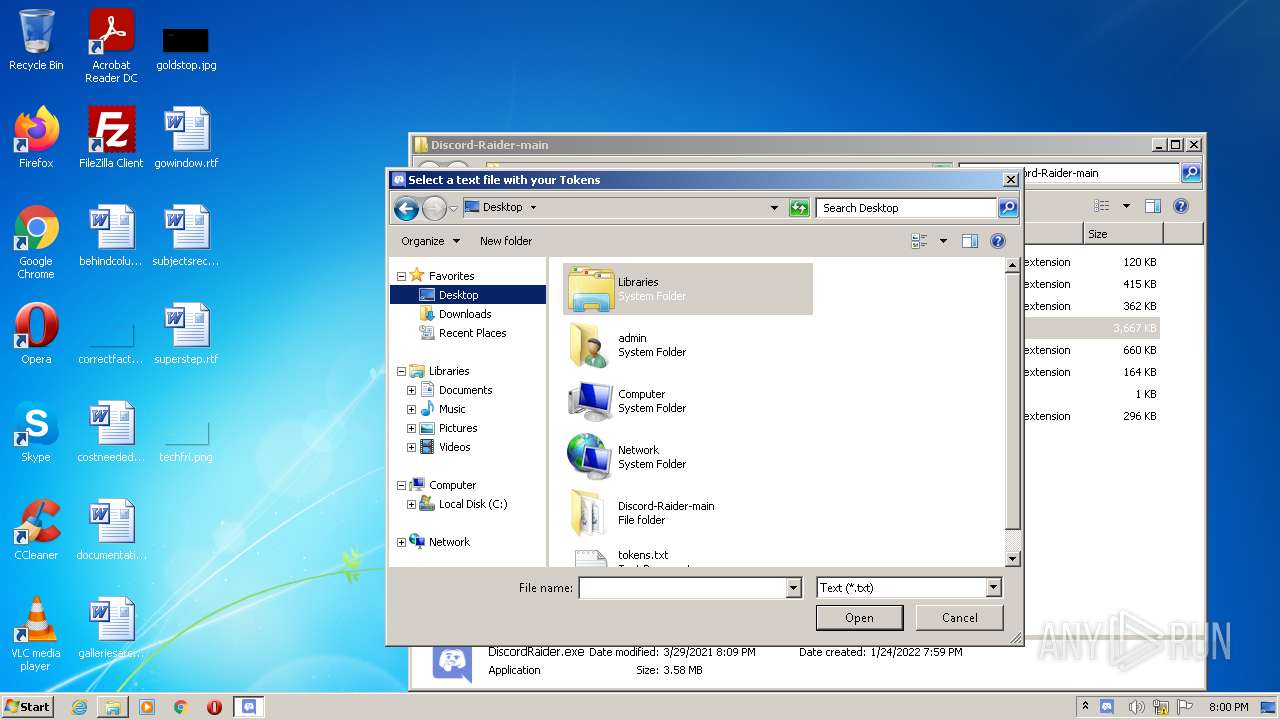
| 1656 | Explorer.EXE | C:\Users\admin\Desktop\tokens.txt | text | |
MD5:— | SHA256:— | |||
| 1408 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1408.4619\Discord-Raider-main\Discord.Net.WebSocket.dll | executable | |
MD5:B1C42560370899C48A9607C34B84A498 | SHA256:B2440A1938B9EE0E44499AD2FCE68DB0D35C0A51BCFC46CC44D9EE102363A9F6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
35 648
DNS requests
4
Threats
6
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2512 | DiscordRaider.exe | 162.159.129.233:443 | discordapp.com | Cloudflare Inc | — | shared |
2512 | DiscordRaider.exe | 162.159.133.233:443 | discordapp.com | Cloudflare Inc | — | shared |
— | — | 162.159.133.233:443 | discordapp.com | Cloudflare Inc | — | shared |
984 | DiscordRaider.exe | 162.159.133.233:443 | discordapp.com | Cloudflare Inc | — | shared |
984 | DiscordRaider.exe | 162.159.129.233:443 | discordapp.com | Cloudflare Inc | — | shared |
— | — | 162.159.129.233:443 | discordapp.com | Cloudflare Inc | — | shared |
984 | DiscordRaider.exe | 162.159.130.233:443 | discordapp.com | Cloudflare Inc | — | shared |
— | — | 162.159.130.233:443 | discordapp.com | Cloudflare Inc | — | shared |
— | — | 162.159.134.233:443 | discordapp.com | Cloudflare Inc | — | shared |
— | — | 162.159.135.233:443 | discordapp.com | Cloudflare Inc | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discordapp.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
984 | DiscordRaider.exe | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK with wrong ack |
— | — | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK with wrong ack |
— | — | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK with wrong ack |
— | — | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK with wrong ack |
— | — | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK with wrong ack |
— | — | Generic Protocol Command Decode | SURICATA STREAM 3way handshake SYNACK with wrong ack |