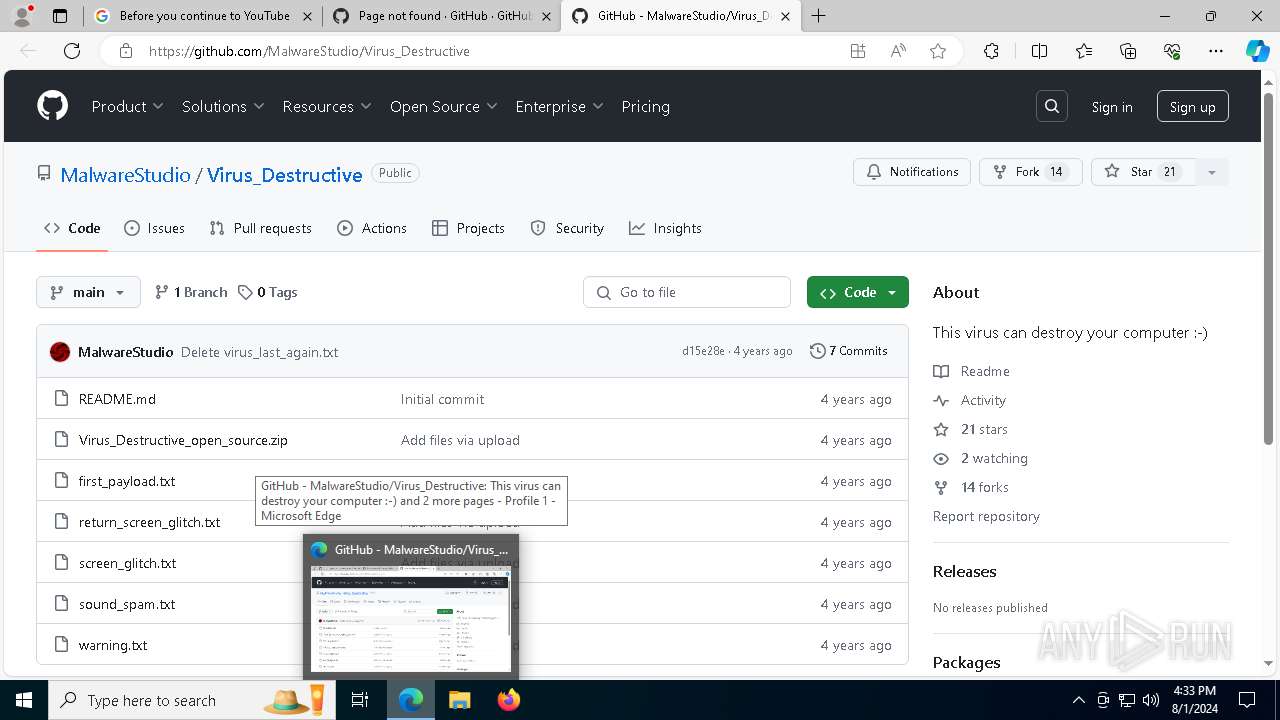
| File name: | Virus.exe |
| Full analysis: | https://app.any.run/tasks/ac517fcd-742e-4696-927b-46fe5fe2067d |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 16:32:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 739F0E4E9C89F704D553B6C1638A2630 |
| SHA1: | 07F3A108134F132310A93D98F909F492F9990FFF |
| SHA256: | A0EEEB8B83831D6FD9B7C042B8DA87E43DC75D35B6D552B00B08433CB78AC048 |
| SSDEEP: | 6144:hCpVej/t9JAy89+J9Wz0p/y7t6nS54dvQPs3J+VfMZYZnpw:VlP39i09QtudvQPs3JzaB+ |
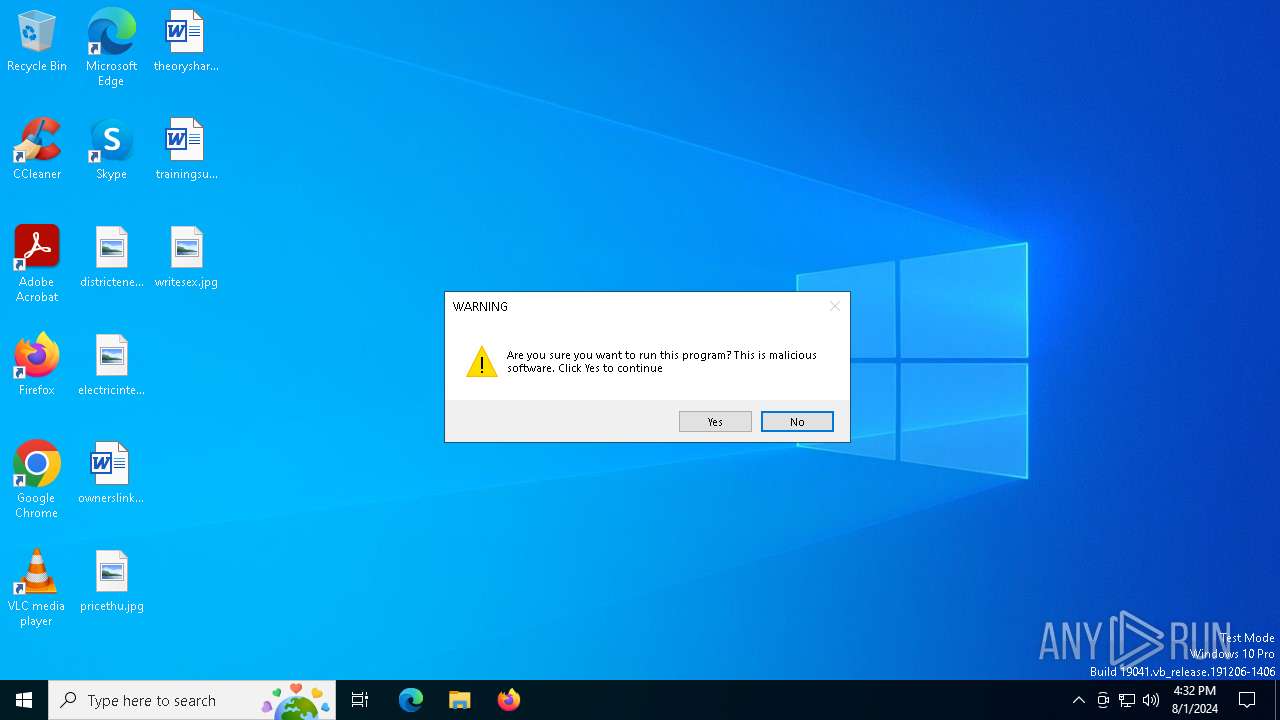
MALICIOUS
Drops the executable file immediately after the start
- Virus.exe (PID: 6320)
- Virus.exe (PID: 6464)
Uses Task Scheduler to run other applications
- MBR.exe (PID: 6892)
Changes the autorun value in the registry
- MBR.exe (PID: 6892)
SUSPICIOUS
Reads security settings of Internet Explorer
- Virus.exe (PID: 6320)
- Virus.exe (PID: 6464)
- Virus_Destructive.exe (PID: 6612)
Reads the date of Windows installation
- Virus.exe (PID: 6320)
- Virus.exe (PID: 6464)
- Virus_Destructive.exe (PID: 6612)
Application launched itself
- Virus.exe (PID: 6320)
Starts CMD.EXE for commands execution
- Virus.exe (PID: 6464)
- Virus_Destructive.exe (PID: 6612)
Executing commands from ".cmd" file
- Virus.exe (PID: 6464)
Executable content was dropped or overwritten
- Virus.exe (PID: 6464)
Probably fake Windows Update
- schtasks.exe (PID: 6912)
Uses TASKKILL.EXE to kill process
- Virus_Destructive.exe (PID: 6612)
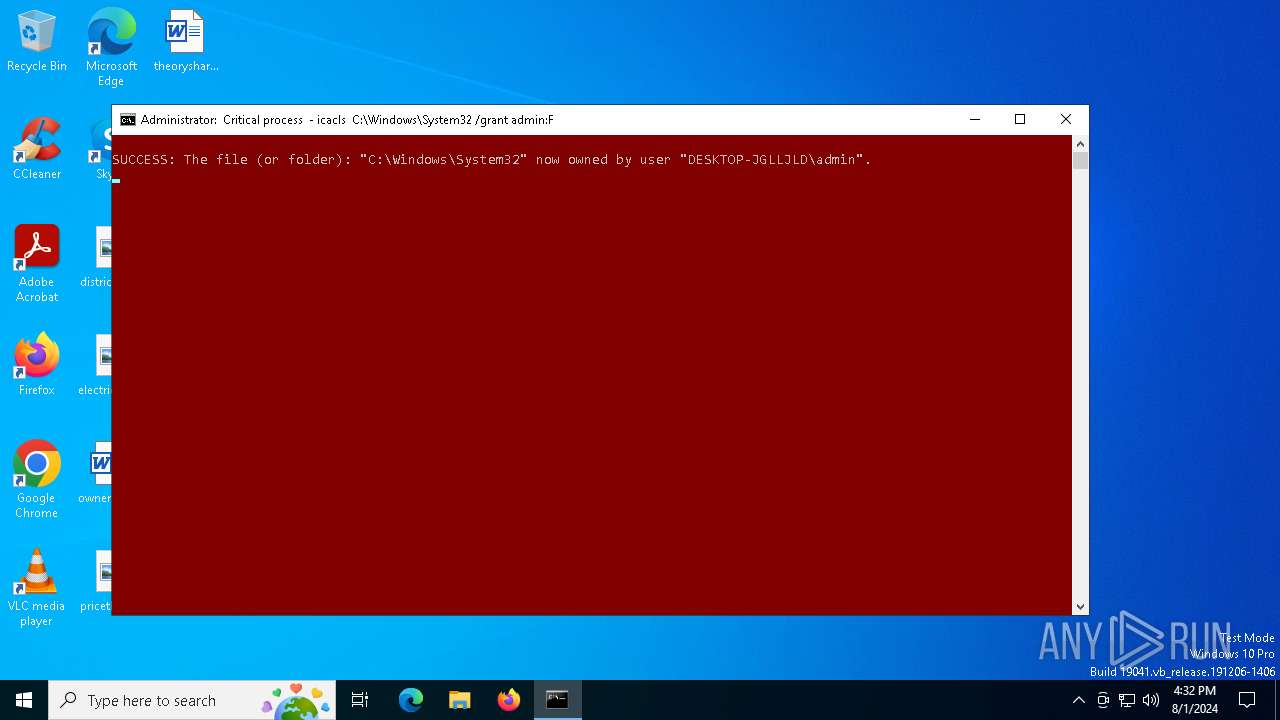
Takes ownership (TAKEOWN.EXE)
- cmd.exe (PID: 6988)
The process checks if it is being run in the virtual environment
- icacls.exe (PID: 6444)
- icacls.exe (PID: 7160)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 6988)
INFO
Checks supported languages
- Virus.exe (PID: 6320)
- Virus.exe (PID: 6464)
- Virus_Destructive.exe (PID: 6612)
- MBR.exe (PID: 6892)
- identity_helper.exe (PID: 7636)
- TextInputHost.exe (PID: 7524)
Reads the computer name
- Virus.exe (PID: 6464)
- Virus.exe (PID: 6320)
- Virus_Destructive.exe (PID: 6612)
- identity_helper.exe (PID: 7636)
- TextInputHost.exe (PID: 7524)
Process checks computer location settings
- Virus.exe (PID: 6320)
- Virus.exe (PID: 6464)
- Virus_Destructive.exe (PID: 6612)
Create files in a temporary directory
- Virus.exe (PID: 6464)
Reads the machine GUID from the registry
- Virus_Destructive.exe (PID: 6612)
Reads Microsoft Office registry keys
- msedge.exe (PID: 6280)
- msedge.exe (PID: 6932)
- Virus_Destructive.exe (PID: 6612)
Application launched itself
- msedge.exe (PID: 6280)
- msedge.exe (PID: 6932)
Manual execution by a user
- msedge.exe (PID: 6932)
Reads Environment values
- identity_helper.exe (PID: 7636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:04:02 22:14:34+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 114176 |
| InitializedDataSize: | 39424 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1c35f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| CompanyName: | Vichingo455 |
| LegalCopyright: | Copyright © 2021-22 Vichingo455 |
| OriginalFileName: | Virus.exe |
| Comments: | Trojan that destroys the system |
| FileVersion: | 2.0.0.0 |
| ProductName: | Trojan that destroys the system |
| ProductVersion: | 2.0.0.0 |
| InternalName: | Virus.exe |
| FileDescription: | Virus |
| Created: | 7z SFX Constructor v4.5.0.0 (http://usbtor.ru/viewtopic.php?t=798) |
| Builder: | Asus 11:46:51 28/12/2021 |
Total processes
230
Monitored processes
92
Malicious processes
6
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 568 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6452 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=8176 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1420 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x298,0x29c,0x2a0,0x28c,0x2a8,0x7fffd4055fd8,0x7fffd4055fe4,0x7fffd4055ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1812 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://github.com/MalwareStudio/Virus_Destructive | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | Virus_Destructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6408 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2132 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8612 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2248 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6112 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2628 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8164 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2900 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=42 --mojo-platform-channel-handle=7192 --field-trial-handle=2404,i,17496096914210099861,18318527014503637774,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 3648 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --single-argument https://github.com/MalwareStudio/Virus_Destructive | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | Virus_Destructive.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
33 560
Read events
33 174
Write events
320
Delete events
66
Modification events
| (PID) Process: | (6320) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6320) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6320) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6320) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6464) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6464) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6464) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6464) Virus.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6612) Virus_Destructive.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6612) Virus_Destructive.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
16
Suspicious files
415
Text files
107
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6892 | MBR.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 6552 | ReAgentc.exe | C:\Windows\System32\Recovery\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 6464 | Virus.exe | C:\Users\admin\AppData\Local\Temp\Virus\MBR.exe | executable | |
MD5:80EA4F98FD895104F8013828FBD5B036 | SHA256:73F1BBEF3C790F9017CBE4A403D0FD9DC9C1501E8322FD97AE52BC1FB20CE2AF | |||
| 6552 | ReAgentc.exe | C:\Windows\Logs\ReAgent\ReAgent.log | text | |
MD5:0EEC8DCBECB086A33EFB6625E2BF31C5 | SHA256:F9E8E5FB1DFAB673ED50EA5DFD46566B9FF2E4C6510F23359E983A0795D95EE7 | |||
| 6552 | ReAgentc.exe | C:\Windows\Panther\UnattendGC\diagerr.xml | text | |
MD5:3A8D2D92D67445734789F82D6E6D90A6 | SHA256:E80AA5A43C517844228A67E8A49E30EE8CF68979E54BA0A3FE660C80978808C6 | |||
| 6552 | ReAgentc.exe | \\?\Volume{2f5c5e71-85a9-11eb-90a8-9a9b76358421}\EFI\Microsoft\Recovery\BCD | binary | |
MD5:A43757247EF2EDA312D9D1D748B3A20A | SHA256:50B573A67EB41C534E46C9CCAAACB9F7724625EFB92E6B35B9F0AB070B6A4816 | |||
| 6464 | Virus.exe | C:\Users\admin\AppData\Local\Temp\Virus\Virus_Destructive.exe.config | xml | |
MD5:CEBFE157098995082112604CA8730110 | SHA256:DFDF5ECD6291CB0D74B89746B733BC8B1F6E74F00A253DEE15D14891A2CF5BA0 | |||
| 6932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RFeab9d.TMP | — | |
MD5:— | SHA256:— | |||
| 6932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFeab9d.TMP | — | |
MD5:— | SHA256:— | |||
| 6932 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFeab9d.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
181
DNS requests
185
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
7692 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/369e8e41-5ce3-4eb8-9826-427d58ae27b0?P1=1723132343&P2=404&P3=2&P4=ZHizZLMu%2fYEoyHsVnIAniM8B5fSzGRryDN2zXHJPVg%2f9BCCBO3w7OnRVJ5l%2fxU5FXoluR09za44fdBmIJsZywQ%3d%3d | unknown | — | — | whitelisted |
2456 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6436 | msedge.exe | GET | 304 | 195.138.255.24:80 | http://apps.identrust.com/roots/dstrootcax3.p7c | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4056 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1184 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5336 | SearchApp.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2456 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3260 | svchost.exe | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.youtube.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6436 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
6436 | msedge.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |