| File name: | Web Blocked as Usual ( May 2023 ).doc |
| Full analysis: | https://app.any.run/tasks/a75b06ef-2a10-4a0f-a47f-65f5b2ba415e |
| Verdict: | Malicious activity |
| Analysis date: | May 22, 2023, 02:46:01 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 949, Author: user, Template: Normal, Last Saved By: user, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Total Editing Time: 02:00, Create Time/Date: Thu Apr 27 06:46:00 2023, Last Saved Time/Date: Thu Apr 27 06:48:00 2023, Number of Pages: 1, Number of Words: 25, Number of Characters: 146, Security: 0 |
| MD5: | 6C0D2E720A5DEC59C583683C2EC70F84 |
| SHA1: | FDFACAAC3057AE5600B9580BFB6F32616CA52FE5 |
| SHA256: | A0D72FFE6347F08D58A5EFF7E056628831F061966CBAF7BBB04A7E94DC2B1F1C |
| SSDEEP: | 3072:ea3Sd+iVWFBvEgVDN2mpNSAjQ5brISvCU54zaOb5i/a0gcB:eaQ8BvEkDQQjQ9ISqU2WOcN |
MALICIOUS
Connection from MS Office application
- WINWORD.EXE (PID: 3940)
SUSPICIOUS
No suspicious indicators.INFO
Reads Internet Explorer settings
- WINWORD.EXE (PID: 3940)
Application launched itself
- iexplore.exe (PID: 3292)
Create files in a temporary directory
- iexplore.exe (PID: 3292)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Lines: | 1 |
|---|---|
| Paragraphs: | 1 |
| Pages: | 1 |
| Characters: | 146 |
| Words: | 25 |
| TotalEditTime: | 2 minutes |
| RevisionNumber: | 1 |
| LastPrinted: | 0000:00:00 00:00:00 |
| CompObjUserType: | Microsoft Word 97-2003 ???? |
| CompObjUserTypeLen: | 28 |
| Hyperlinks: |
|
| CodePage: | Windows Korean (Unified Hangul Code) |
| HeadingPairs: |
|
| TitleOfParts: | - |
| HyperlinksChanged: | No |
| SharedDoc: | No |
| LinksUpToDate: | No |
| ScaleCrop: | No |
| AppVersion: | 16 |
| CharCountWithSpaces: | 170 |
| Company: | - |
| Security: | None |
| ModifyDate: | 2023:04:27 06:48:00 |
| CreateDate: | 2023:04:27 06:46:00 |
| Software: | Microsoft Office Word |
| LastModifiedBy: | user |
| Template: | Normal |
| Comments: | - |
| Keywords: | - |
| Author: | user |
| Subject: | - |
| Title: | - |
| Word97: | No |
| System: | Windows |
| DocFlags: | Has picture, 1Table, ExtChar, Far east |
| LanguageCode: | English (US) |
| Identification: | Word 8.0 |
Total processes
42
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2140 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3292 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2632 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3292 CREDAT:333058 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3292 | "C:\Program Files\Internet Explorer\iexplore.exe" -startmediumtab -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3940 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Web Blocked as Usual ( May 2023 ).doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
26 842
Read events
26 198
Write events
507
Delete events
137
Modification events
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: On | |||
| (PID) Process: | (3940) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: On | |||
Executable files
0
Suspicious files
72
Text files
72
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRC759.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$b Blocked as Usual ( May 2023 ).doc | binary | |
MD5:FFBE7B0AABAF91717A1A20E2D25E9F00 | SHA256:630FFDD63042B08AFFE0DA59145CA53F582D9A03065B7A4511A1961F71DFFF32 | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF1F325BBD8CA6277A.TMP | document | |
MD5:6C0D2E720A5DEC59C583683C2EC70F84 | SHA256:A0D72FFE6347F08D58A5EFF7E056628831F061966CBAF7BBB04A7E94DC2B1F1C | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:534C7488866F599D1D5B82A0241EBB6B | SHA256:3CB60B2C1FA22437B3308F1F579CA895AD68660C560FE19E8A6CC3F8ABAA897E | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 2632 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:335F1F65CC6DFA8FFEAC797DCE8F3991 | SHA256:FFFB9151839FDB5CCF0C35E7B2B8796F2D50FC3A8F0BD042E121AA02DEED6C4E | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:9E48A01B6A74AB0081669B40BEDB3385 | SHA256:84926FFB82572639F91E83B941DE30AAEDBFA4A0473CE3F227E9B4FBEF267923 | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1B1495DD322A24490E2BF2FAABAE1C61 | binary | |
MD5:DEC6BBE308EB44937F77160A25EE32DB | SHA256:68A71DE28F488586C2B169F4652347E0A1FD632D48A6D6725393607BFA18BC7E | |||
| 3940 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF9B0B72A34CD51606.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
109
DNS requests
52
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2632 | iexplore.exe | GET | — | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFRJdTSkekFdCkkVOnklDzo%3D | US | — | — | whitelisted |
2632 | iexplore.exe | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | GB | der | 717 b | whitelisted |
2632 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEHq7CHA9JeW1EONEhXHIKV8%3D | US | der | 471 b | whitelisted |
3940 | WINWORD.EXE | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?dc0615a02c683f1b | US | compressed | 62.3 Kb | whitelisted |
— | — | GET | 200 | 104.18.32.68:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 1.42 Kb | whitelisted |
3940 | WINWORD.EXE | GET | 200 | 23.201.254.55:80 | http://x2.c.lencr.org/ | CH | binary | 300 b | whitelisted |
2632 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | binary | 1.41 Kb | whitelisted |
2632 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | US | binary | 2.18 Kb | whitelisted |
2632 | iexplore.exe | GET | 200 | 108.138.2.10:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
2632 | iexplore.exe | GET | 200 | 172.217.18.3:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | binary | 724 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3372 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3940 | WINWORD.EXE | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
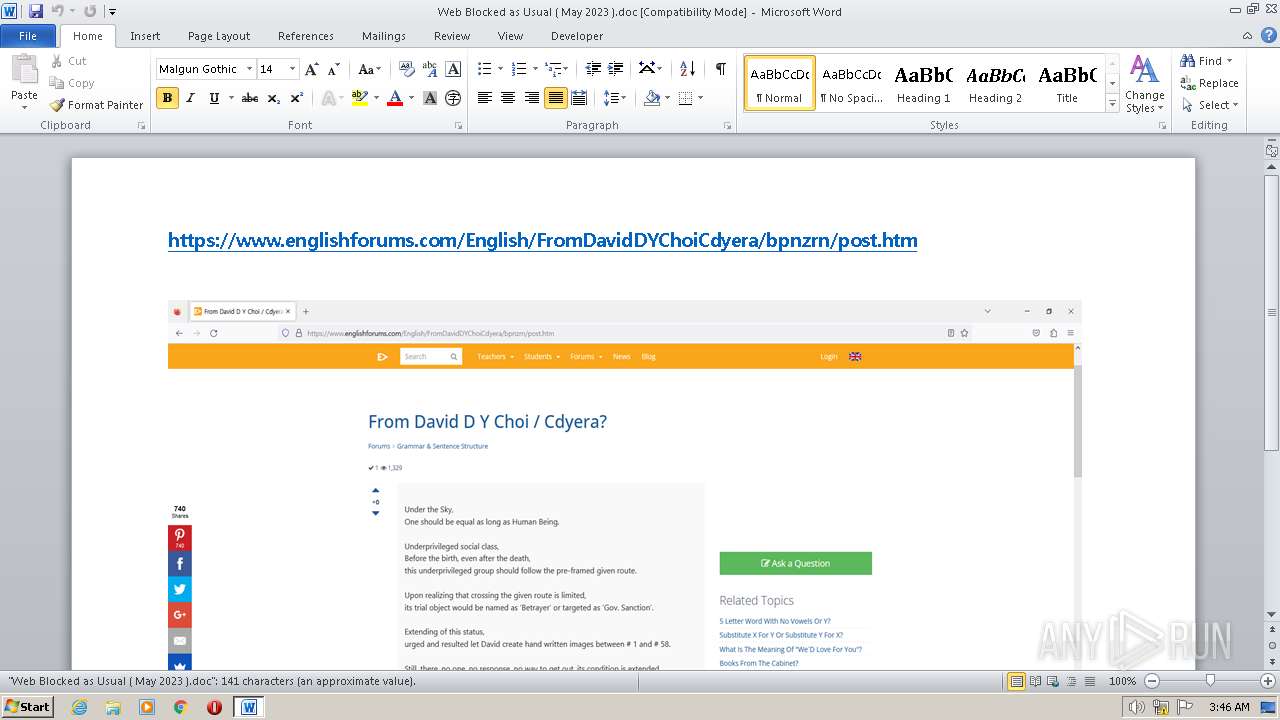
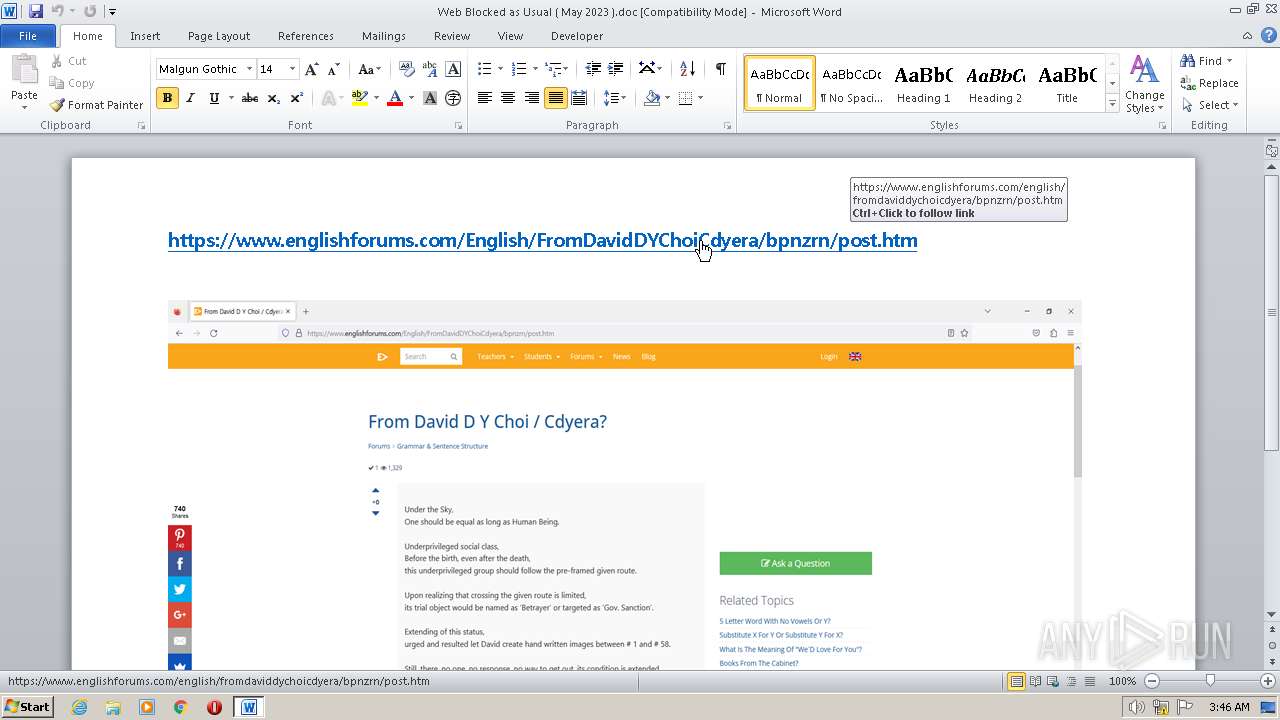
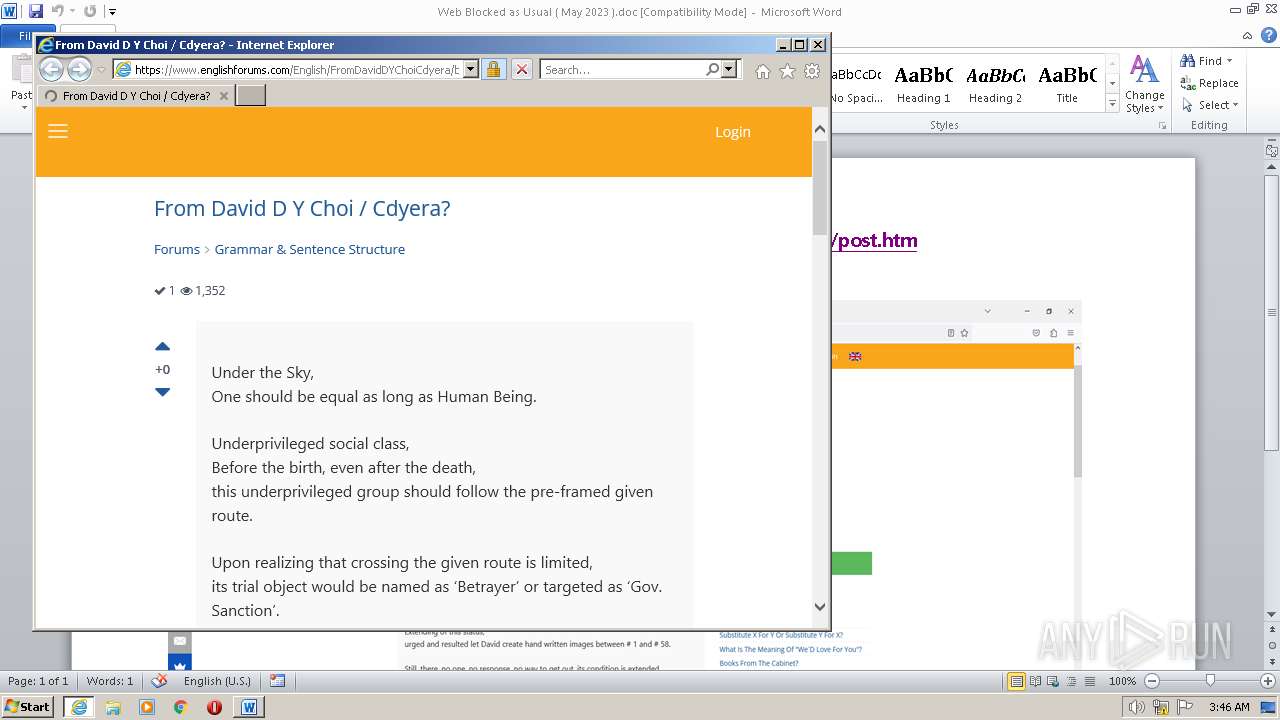
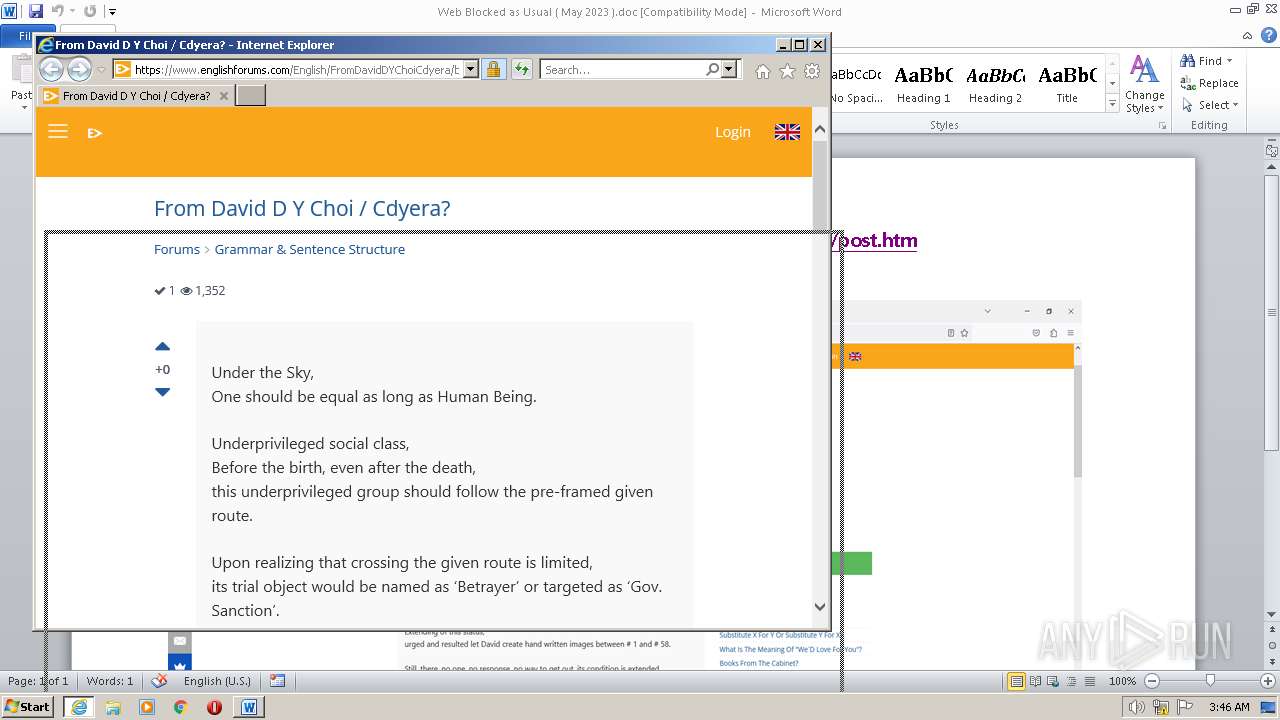
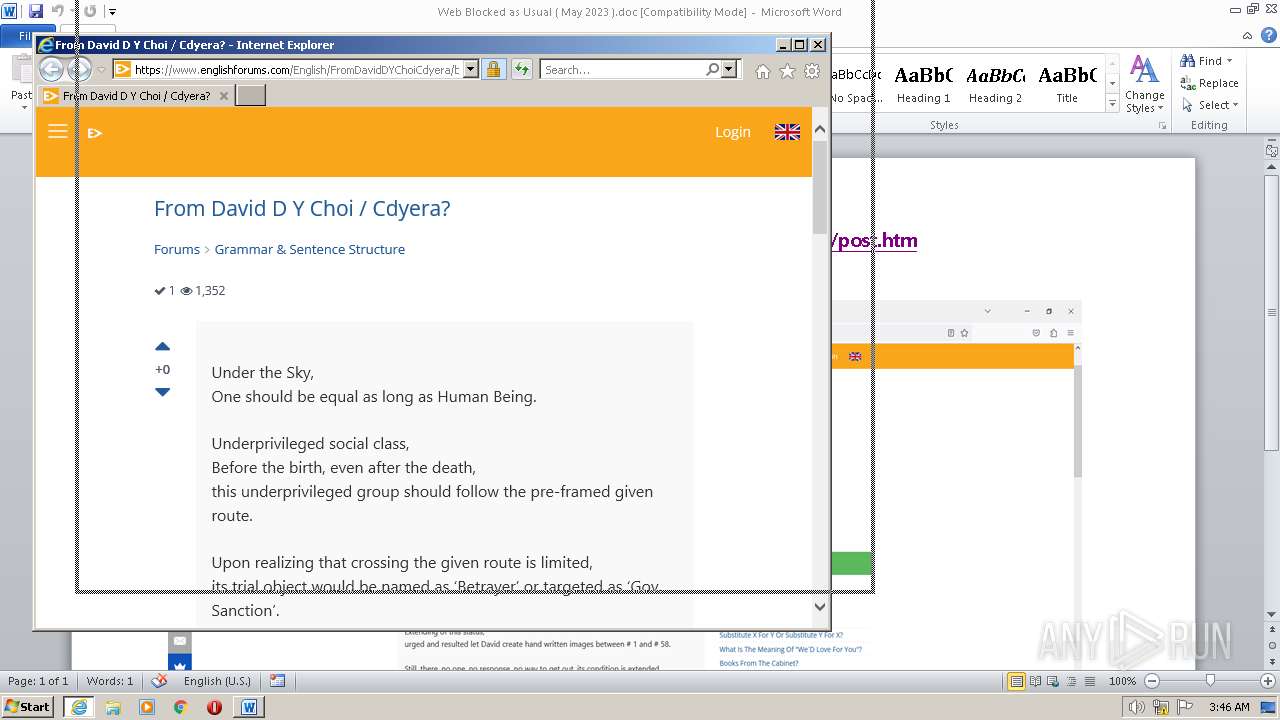
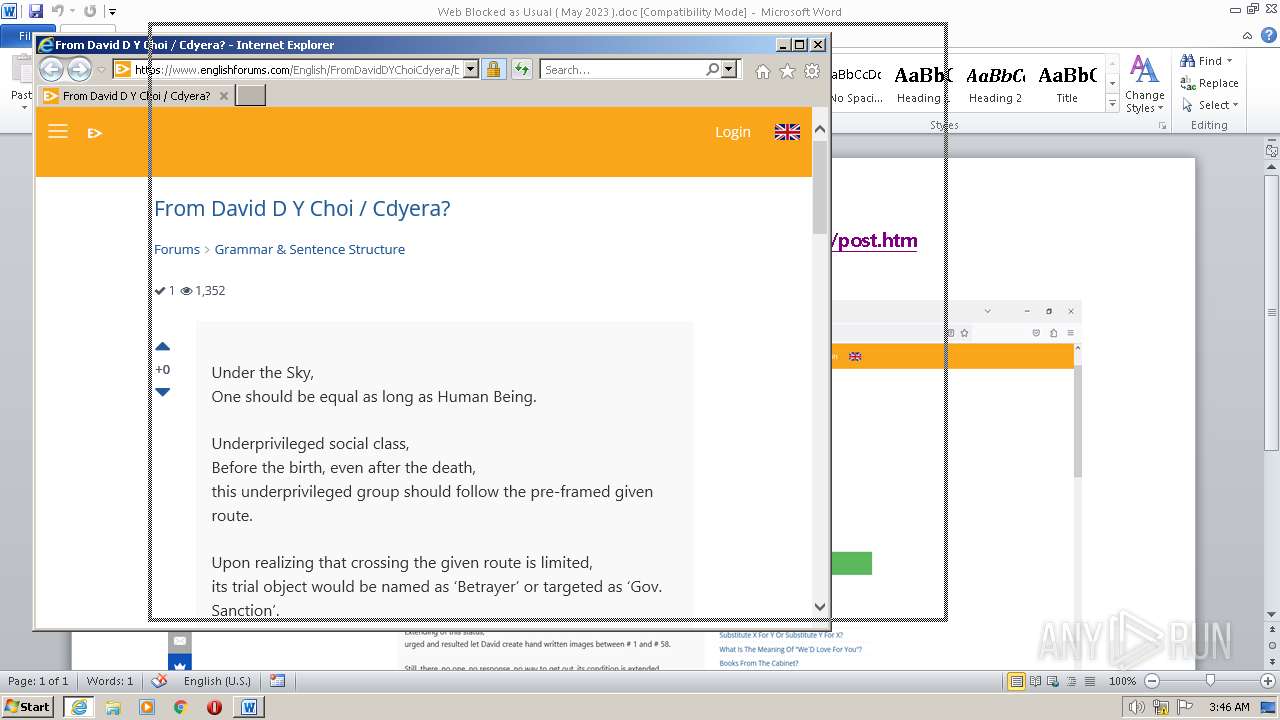
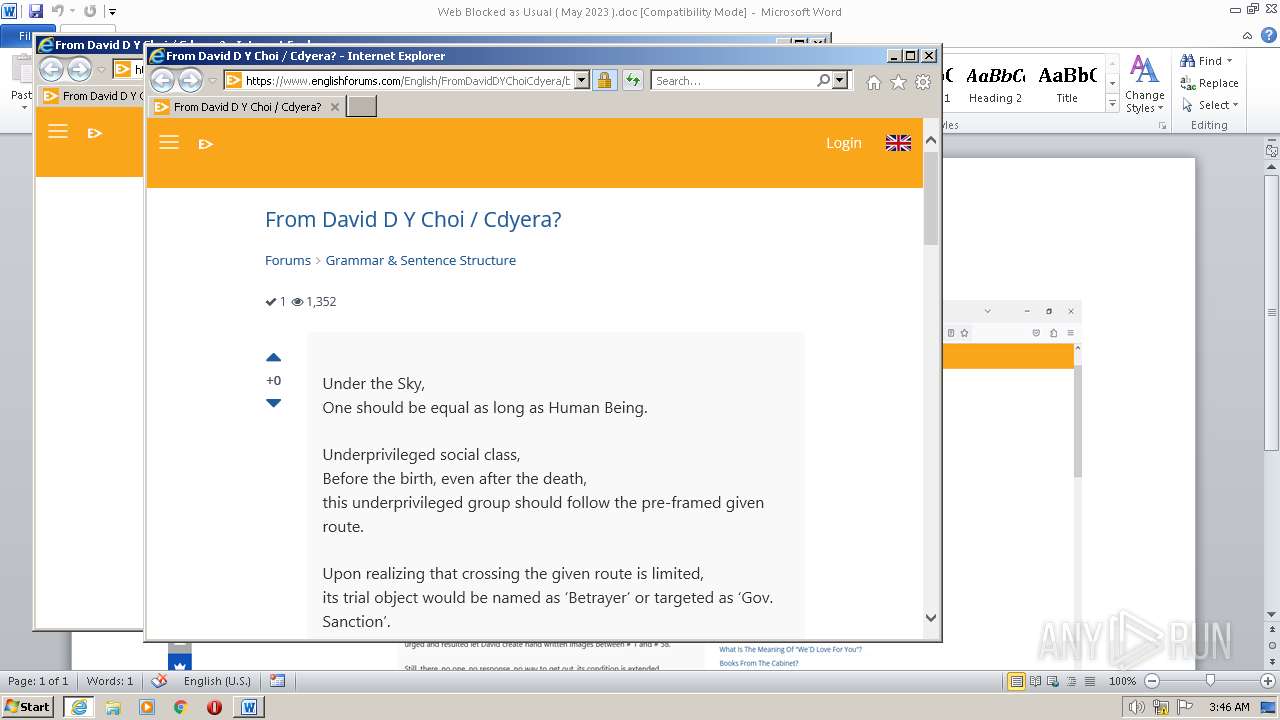
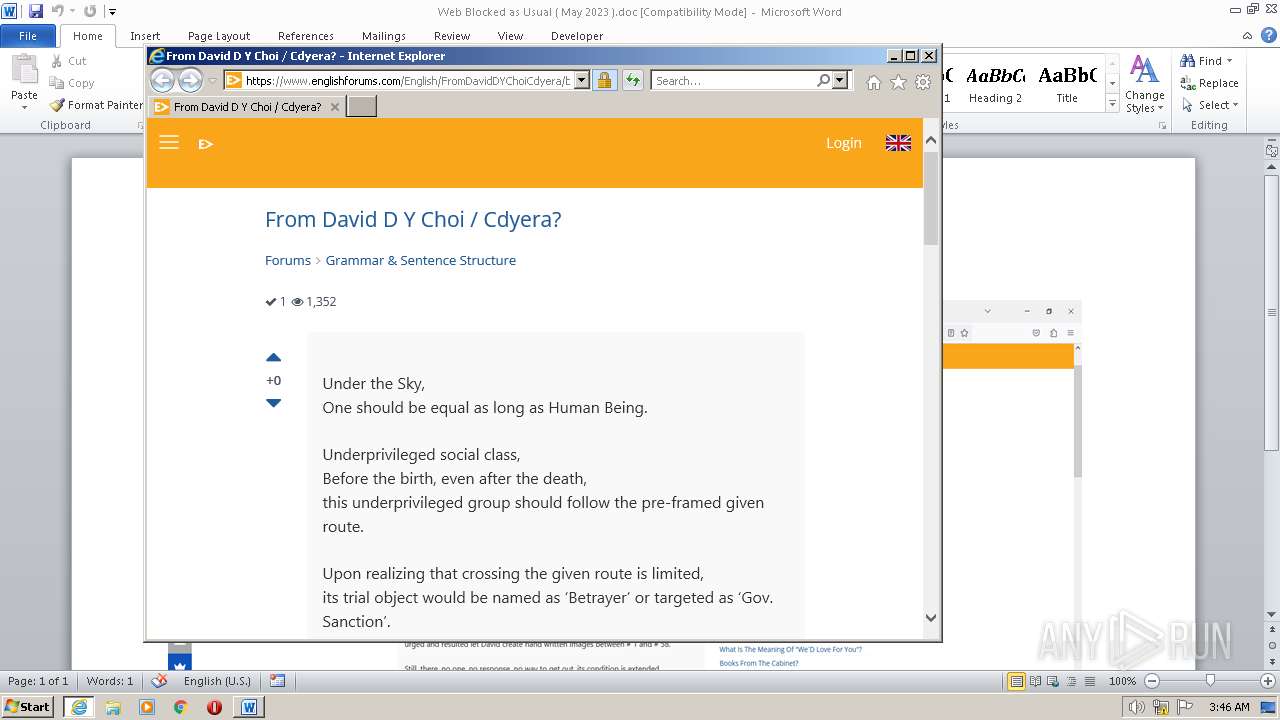
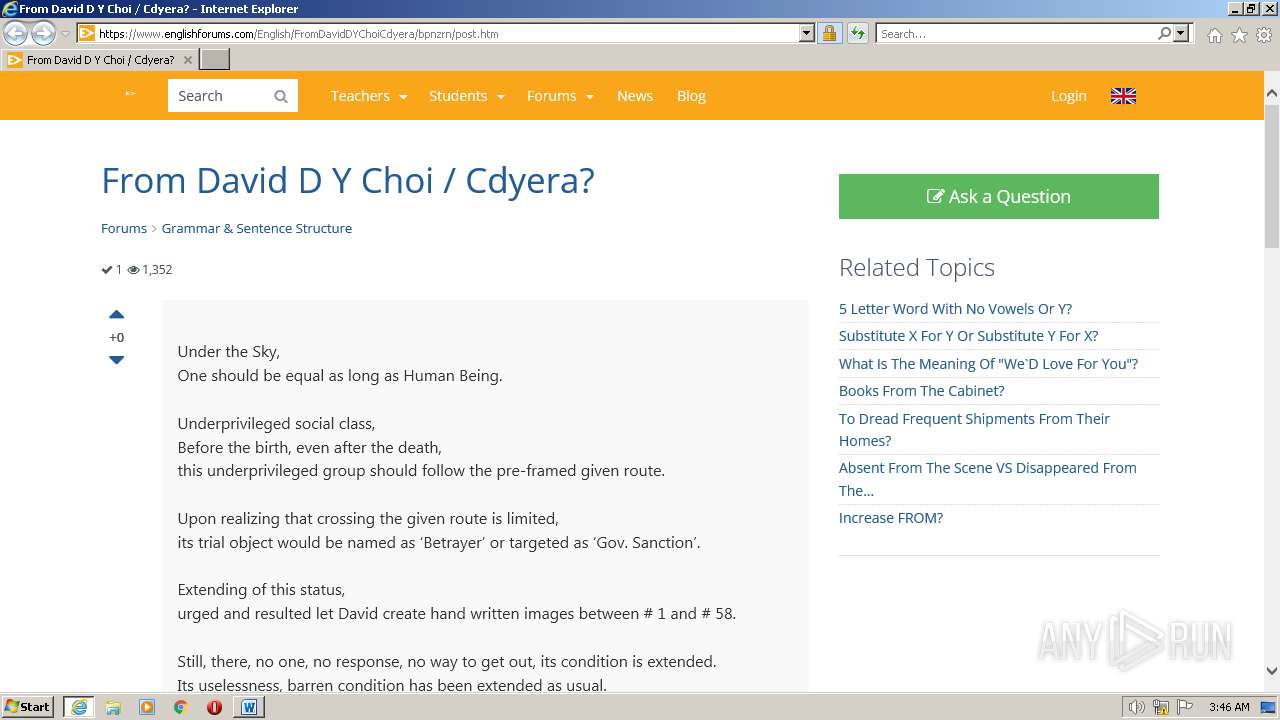
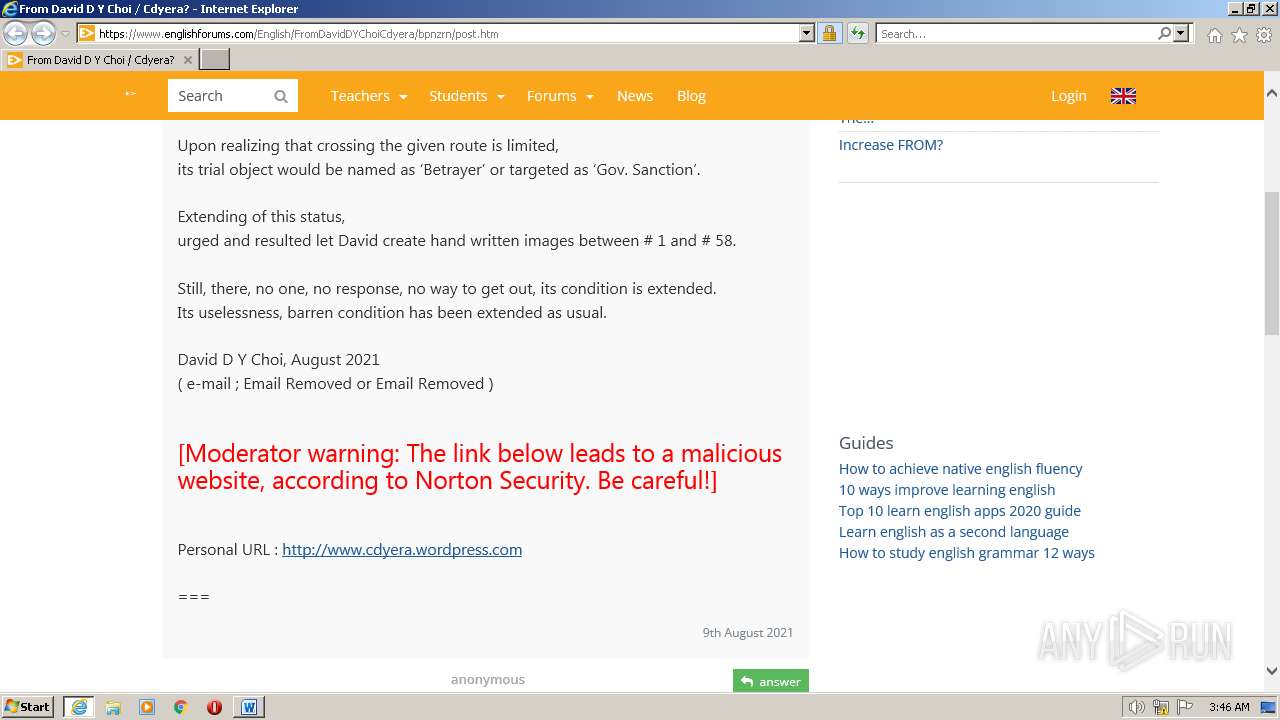
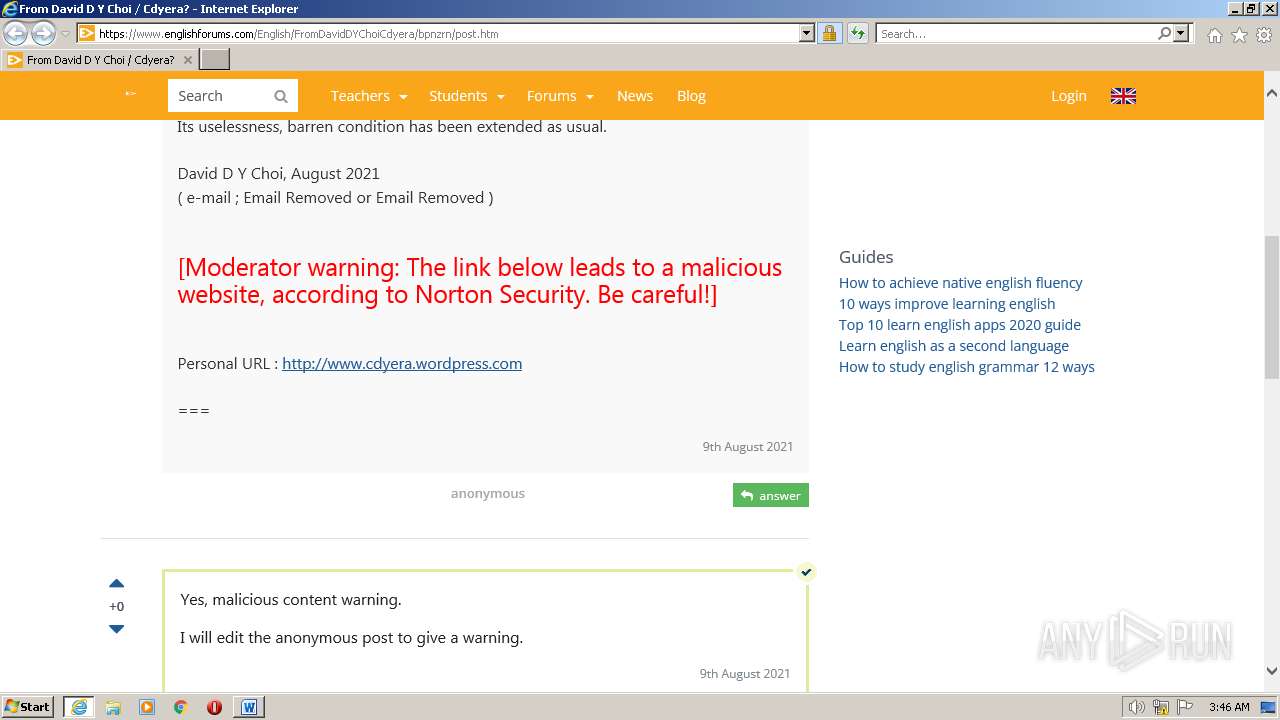
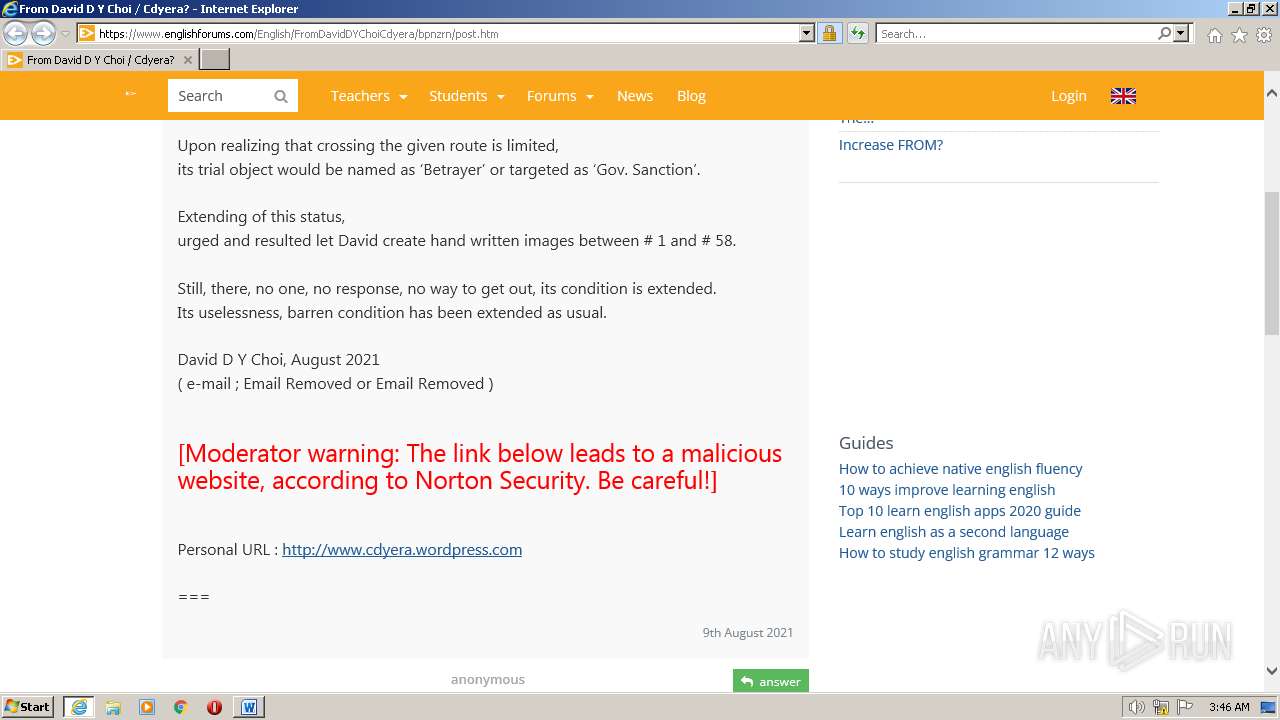
3940 | WINWORD.EXE | 188.114.96.3:443 | www.englishforums.com | CLOUDFLARENET | NL | malicious |
3940 | WINWORD.EXE | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | suspicious |
3940 | WINWORD.EXE | 23.201.254.55:80 | x2.c.lencr.org | AKAMAI-AS | CH | unknown |
2632 | iexplore.exe | 188.114.96.3:443 | www.englishforums.com | CLOUDFLARENET | NL | malicious |
2632 | iexplore.exe | 23.56.202.135:80 | x1.c.lencr.org | AKAMAI-AS | GB | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.englishforums.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
cdn.englishforums.com |
| malicious |
cdn.onesignal.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |