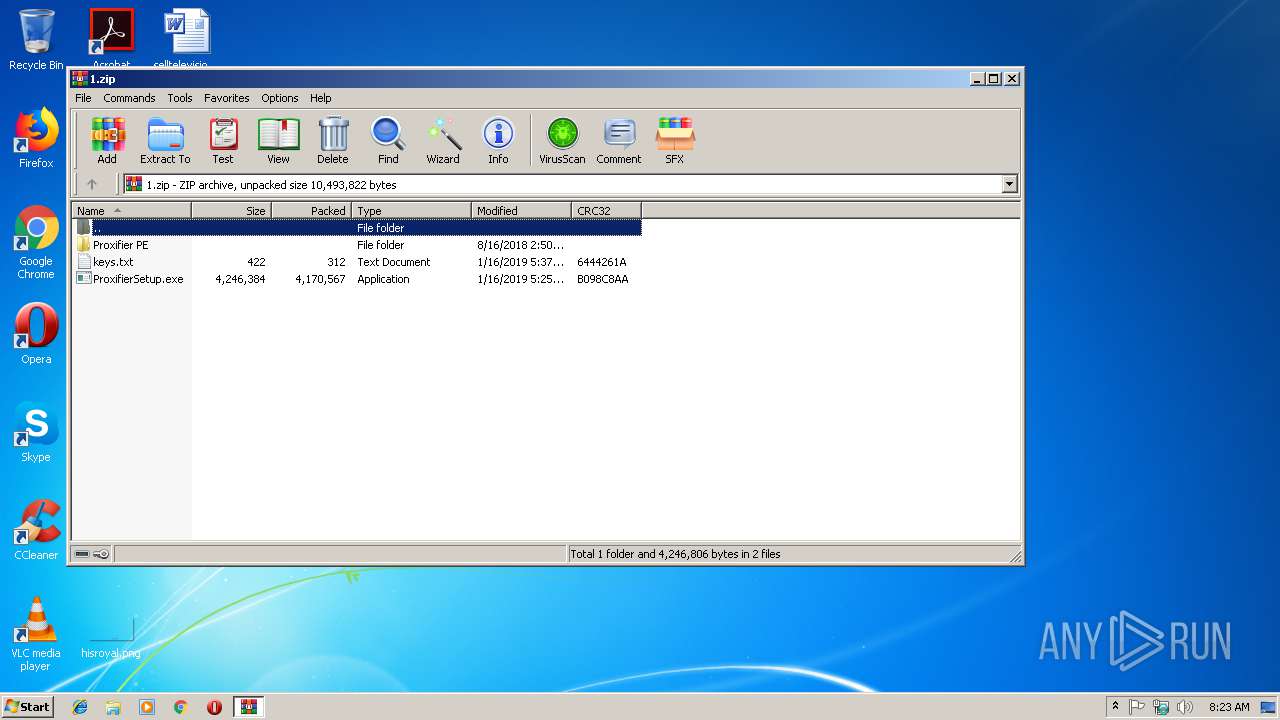
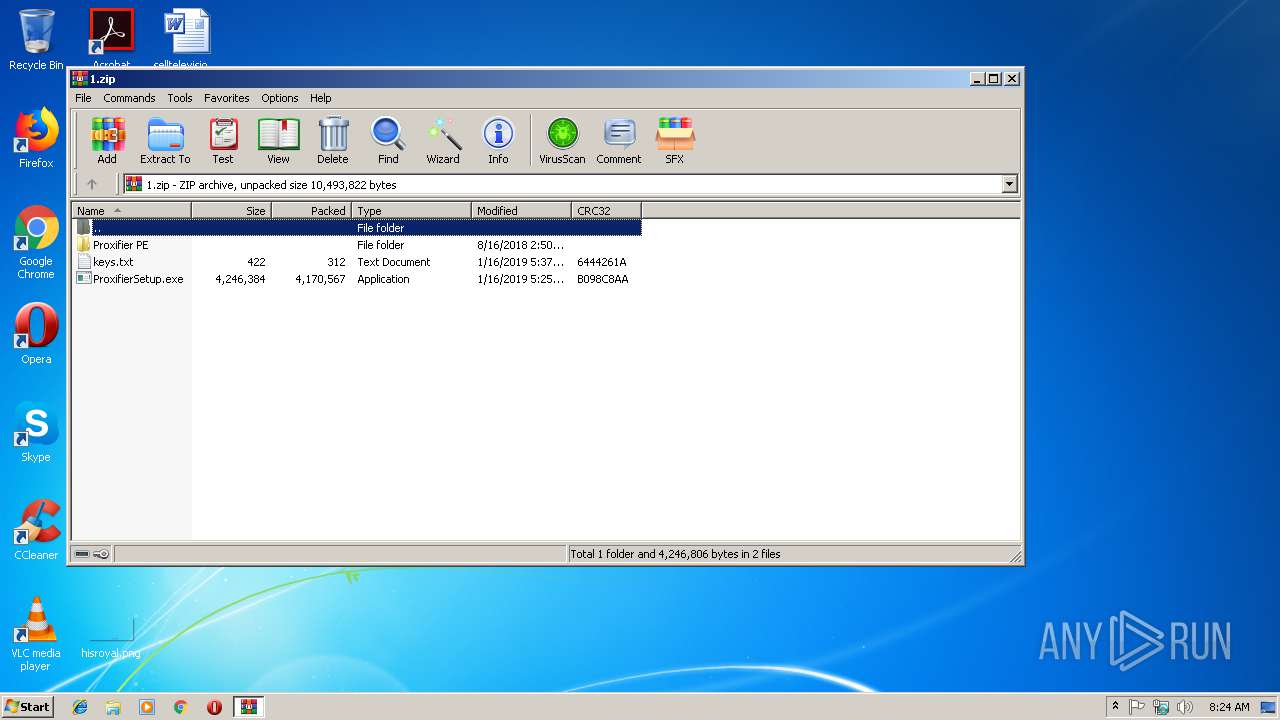
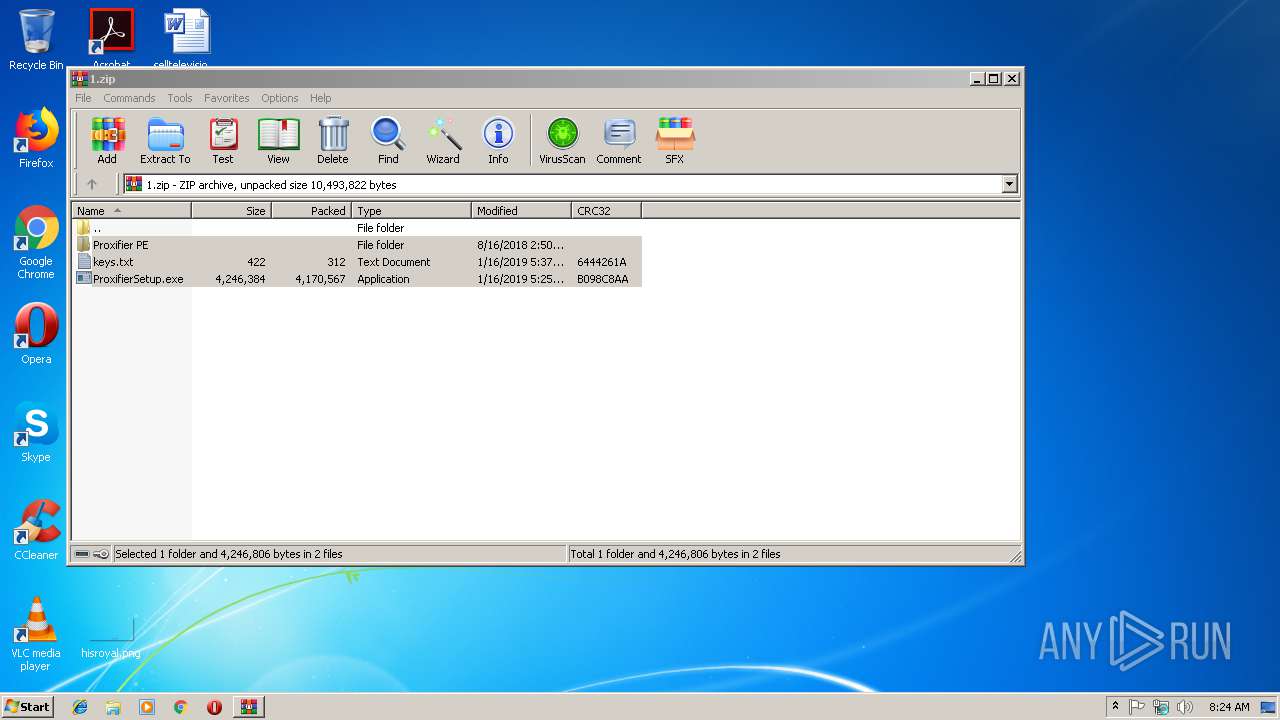
| File name: | 1.zip |
| Full analysis: | https://app.any.run/tasks/b25b233d-1028-4fa3-b38b-4a81746eefb7 |
| Verdict: | Malicious activity |
| Analysis date: | January 18, 2019, 08:23:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 2DBB5BF064F50628640A35CF6E9C5403 |
| SHA1: | 32EDBEF4EE21861360CCD525887CF6756ED966A1 |
| SHA256: | A0D7217133CF60DF5D74EEAA6AA4D4A77E0445DC12BE078BD3FBAFAB50BF792E |
| SSDEEP: | 98304:Q/yrlyYaoP4rM4ctXwL7ED6K5GI0nEPAl+L0HEnimPuupMknA5ZUA6lv0hP:QqrlyYhP4c67Et5QnE6zEim/OT56Ak0p |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 284)
- Proxifier.exe (PID: 3076)
- explorer.exe (PID: 2028)
- DllHost.exe (PID: 2556)
- opera.exe (PID: 960)
Application was dropped or rewritten from another process
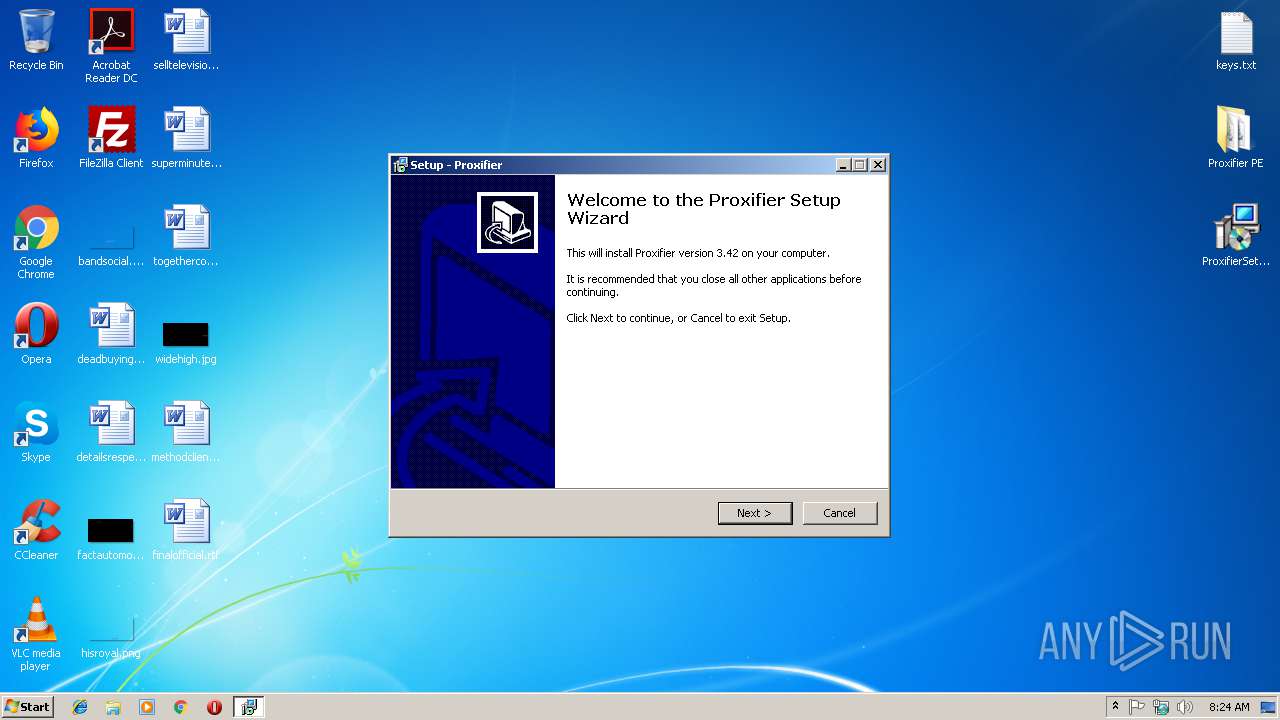
- ProxifierSetup.exe (PID: 3296)
- ProxifierSetup.exe (PID: 3632)
- Proxifier.exe (PID: 3076)
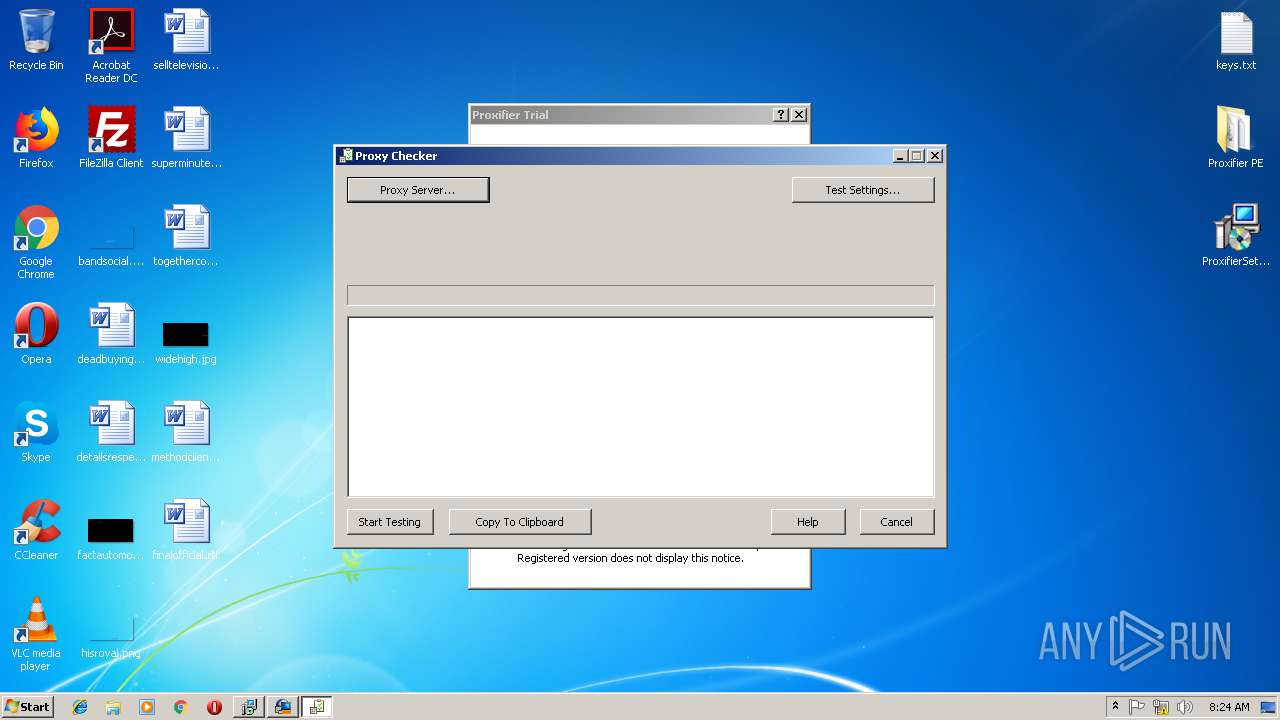
- ProxyChecker.exe (PID: 4008)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3128)
- ProxifierSetup.exe (PID: 3632)
- ProxifierSetup.exe (PID: 3296)
- explorer.exe (PID: 2028)
Reads Windows owner or organization settings
- ProxifierSetup.tmp (PID: 2240)
Reads the Windows organization settings
- ProxifierSetup.tmp (PID: 2240)
INFO
Application was dropped or rewritten from another process
- ProxifierSetup.tmp (PID: 2208)
- ProxifierSetup.tmp (PID: 2240)
Creates files in the user directory
- opera.exe (PID: 960)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:01:16 12:37:16 |
| ZipCRC: | 0x6444261a |
| ZipCompressedSize: | 312 |
| ZipUncompressedSize: | 422 |
| ZipFileName: | keys.txt |
Total processes
43
Monitored processes
11
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 960 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 2028 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2208 | "C:\Users\admin\AppData\Local\Temp\is-2M5E3.tmp\ProxifierSetup.tmp" /SL5="$4015A,3835417,121344,C:\Users\admin\Desktop\ProxifierSetup.exe" | C:\Users\admin\AppData\Local\Temp\is-2M5E3.tmp\ProxifierSetup.tmp | — | ProxifierSetup.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2240 | "C:\Users\admin\AppData\Local\Temp\is-I6GJG.tmp\ProxifierSetup.tmp" /SL5="$40164,3835417,121344,C:\Users\admin\Desktop\ProxifierSetup.exe" /SPAWNWND=$30162 /NOTIFYWND=$4015A | C:\Users\admin\AppData\Local\Temp\is-I6GJG.tmp\ProxifierSetup.tmp | — | ProxifierSetup.exe | |||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 2 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2556 | C:\Windows\system32\DllHost.exe /Processid:{AB8902B4-09CA-4BB6-B78D-A8F59079A8D5} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
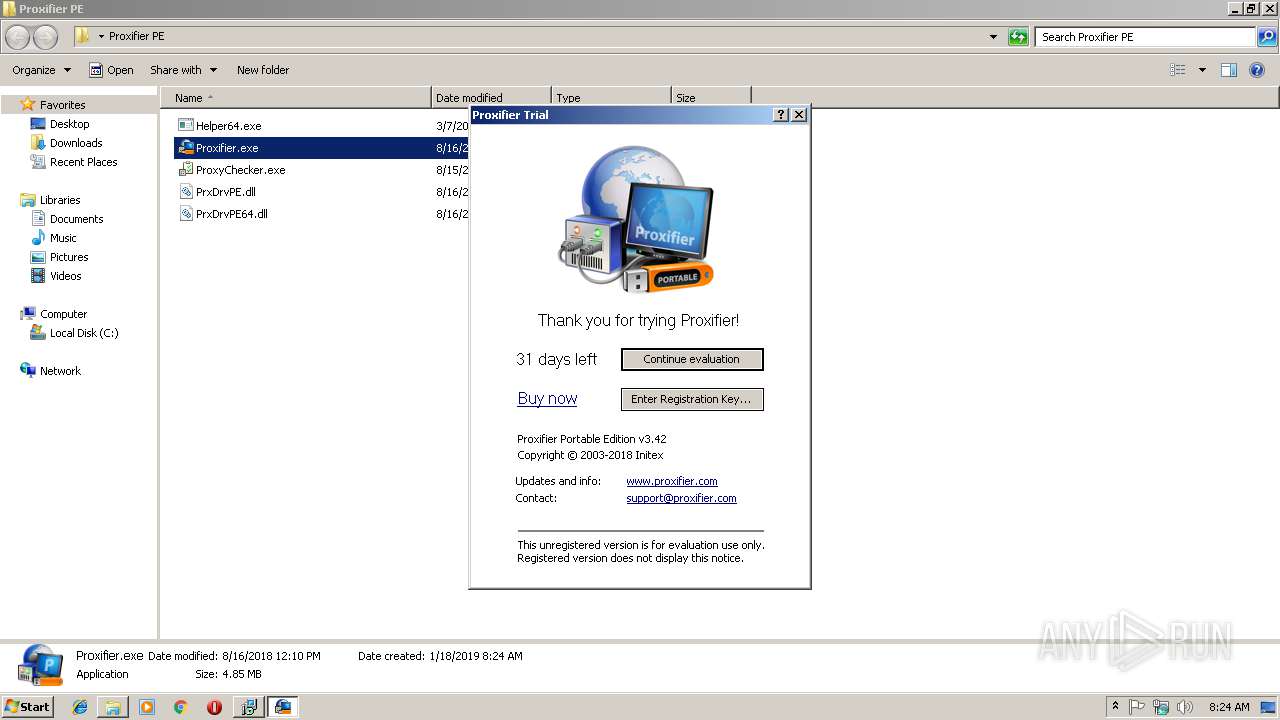
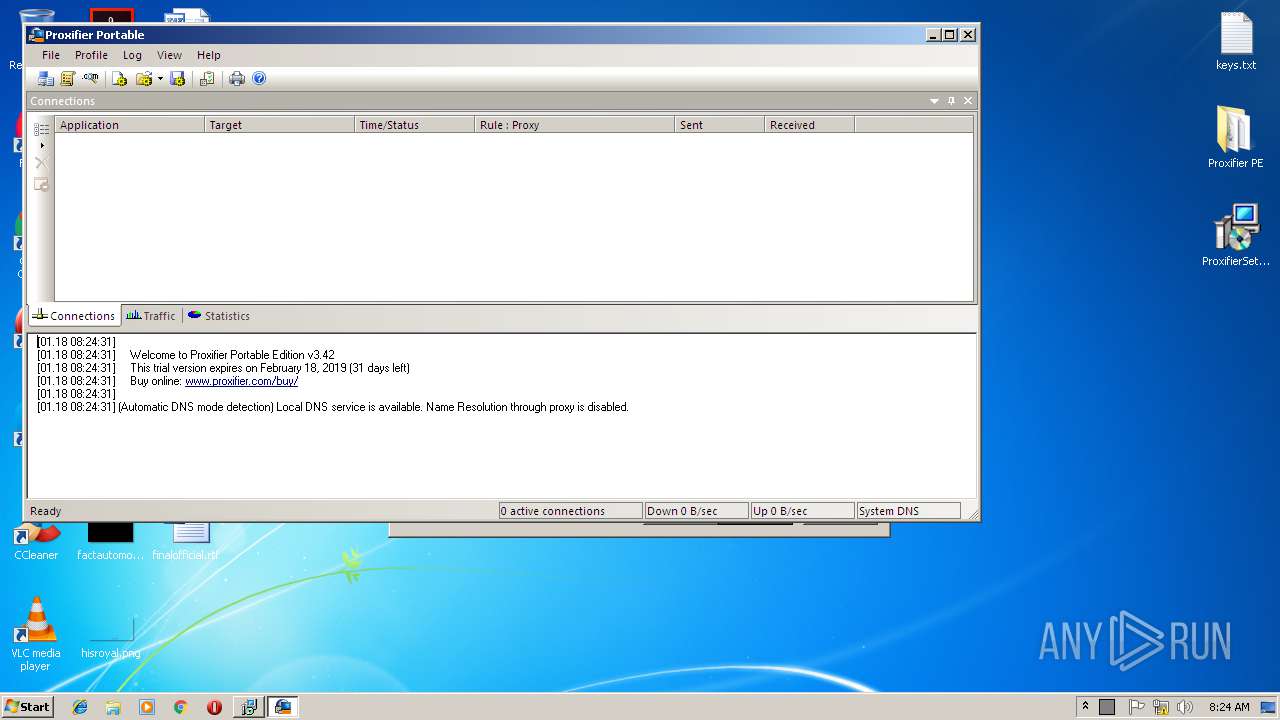
| 3076 | "C:\Users\admin\Desktop\Proxifier PE\Proxifier.exe" | C:\Users\admin\Desktop\Proxifier PE\Proxifier.exe | explorer.exe | ||||||||||||
User: admin Company: Initex Integrity Level: MEDIUM Description: Proxifier Portable Edition v3.42 Exit code: 0 Version: 3.42.0.1 Modules
| |||||||||||||||
| 3128 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\1.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3296 | "C:\Users\admin\Desktop\ProxifierSetup.exe" | C:\Users\admin\Desktop\ProxifierSetup.exe | explorer.exe | ||||||||||||
User: admin Company: Initex Integrity Level: MEDIUM Description: Proxifier Setup Exit code: 2 Version: 3.42.0.1 Modules
| |||||||||||||||
| 3632 | "C:\Users\admin\Desktop\ProxifierSetup.exe" /SPAWNWND=$30162 /NOTIFYWND=$4015A | C:\Users\admin\Desktop\ProxifierSetup.exe | ProxifierSetup.tmp | ||||||||||||
User: admin Company: Initex Integrity Level: HIGH Description: Proxifier Setup Exit code: 2 Version: 3.42.0.1 Modules
| |||||||||||||||
Total events
4 163
Read events
3 881
Write events
282
Delete events
0
Modification events
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | a |
Value: WinRAR.exe | |||
| (PID) Process: | (2028) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithList |
| Operation: | write | Name: | MRUList |
Value: a | |||
Executable files
9
Suspicious files
48
Text files
86
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2028 | explorer.exe | C:\Users\admin\Desktop\Proxifier PE | — | |
MD5:— | SHA256:— | |||
| 960 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr6AEB.tmp | — | |
MD5:— | SHA256:— | |||
| 960 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr6B3A.tmp | — | |
MD5:— | SHA256:— | |||
| 3128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3128.34669\keys.txt | text | |
MD5:— | SHA256:— | |||
| 2028 | explorer.exe | C:\Users\admin\Desktop\keys.txt | text | |
MD5:— | SHA256:— | |||
| 3076 | Proxifier.exe | C:\Users\admin\Desktop\Proxifier PE\Profiles\Default.ppx | xml | |
MD5:— | SHA256:— | |||
| 960 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 960 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
| 960 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opcacrt6.dat | binary | |
MD5:— | SHA256:— | |||
| 960 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
960 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3076 | Proxifier.exe | GET | 200 | 172.104.17.238:80 | http://www.proxifier.com/distr/last_versions/ProxifierPortable/?nocache=730939C9730939C99C | US | text | 47 b | suspicious |
960 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAOXQPQlVpLtFek%2BmcpabOk%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
960 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
960 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
960 | opera.exe | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3076 | Proxifier.exe | 172.104.17.238:80 | www.proxifier.com | Linode, LLC | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
www.proxifier.com |
| suspicious |
certs.opera.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |