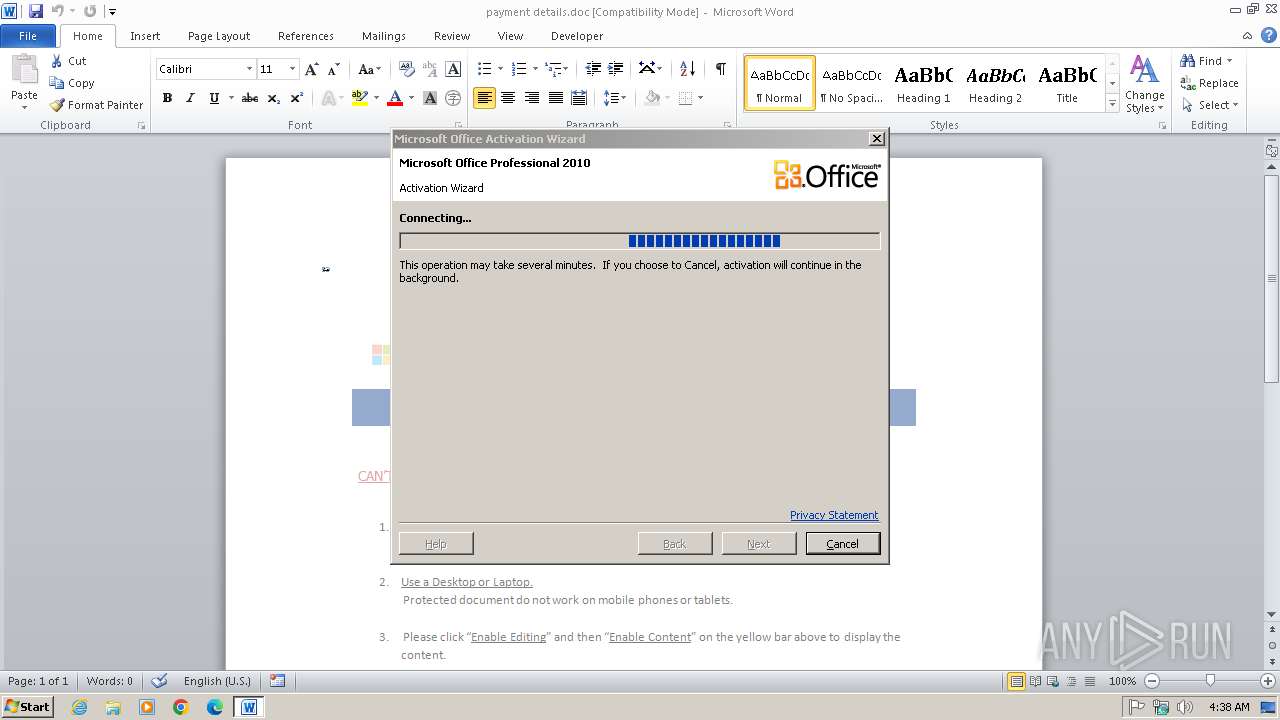
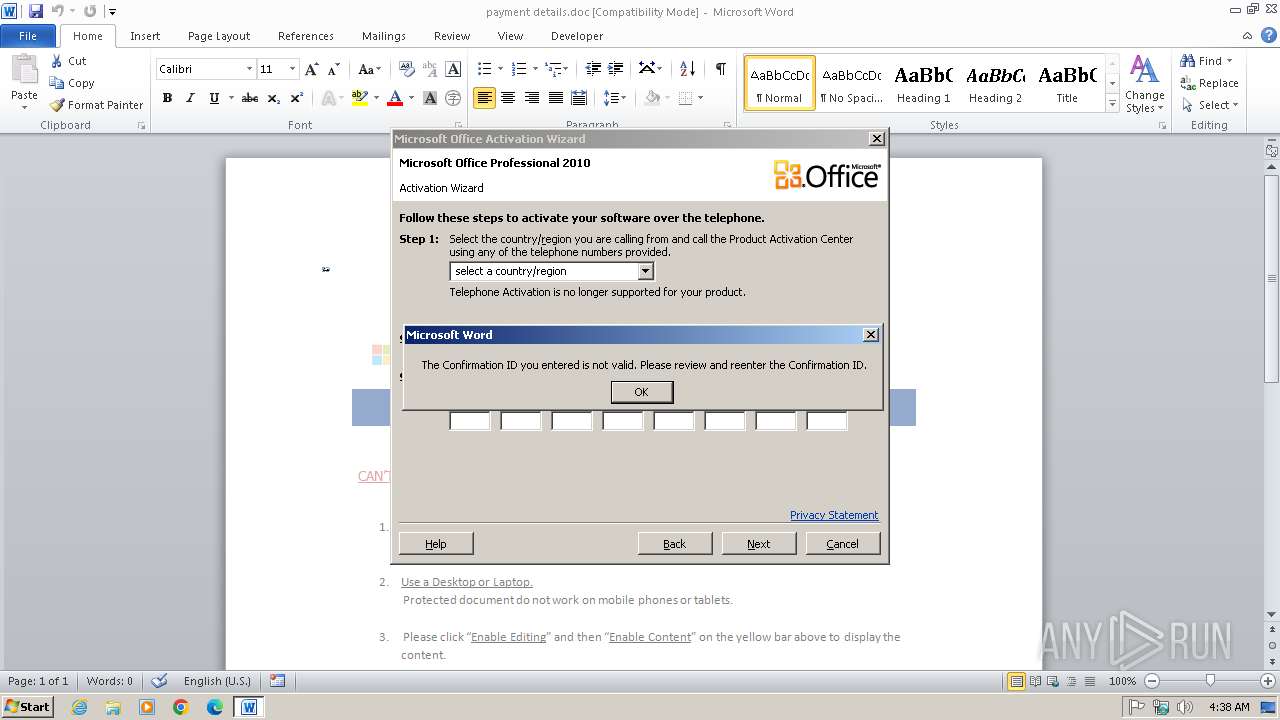
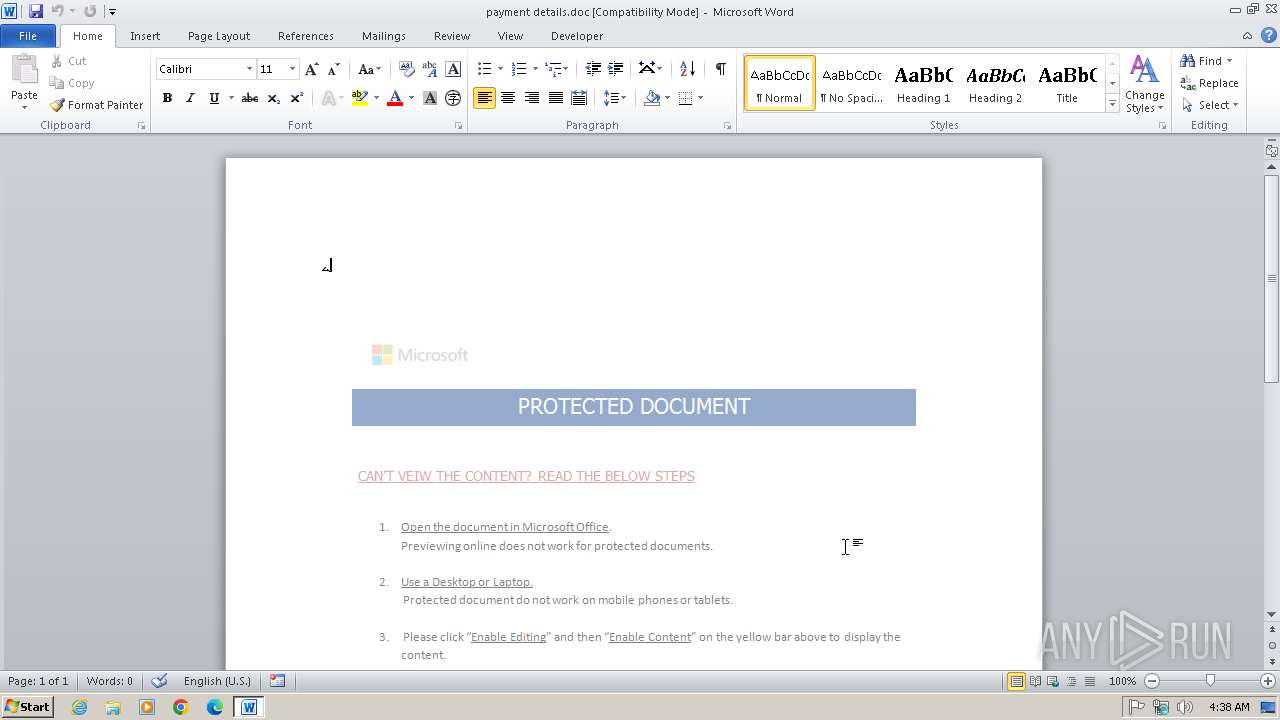
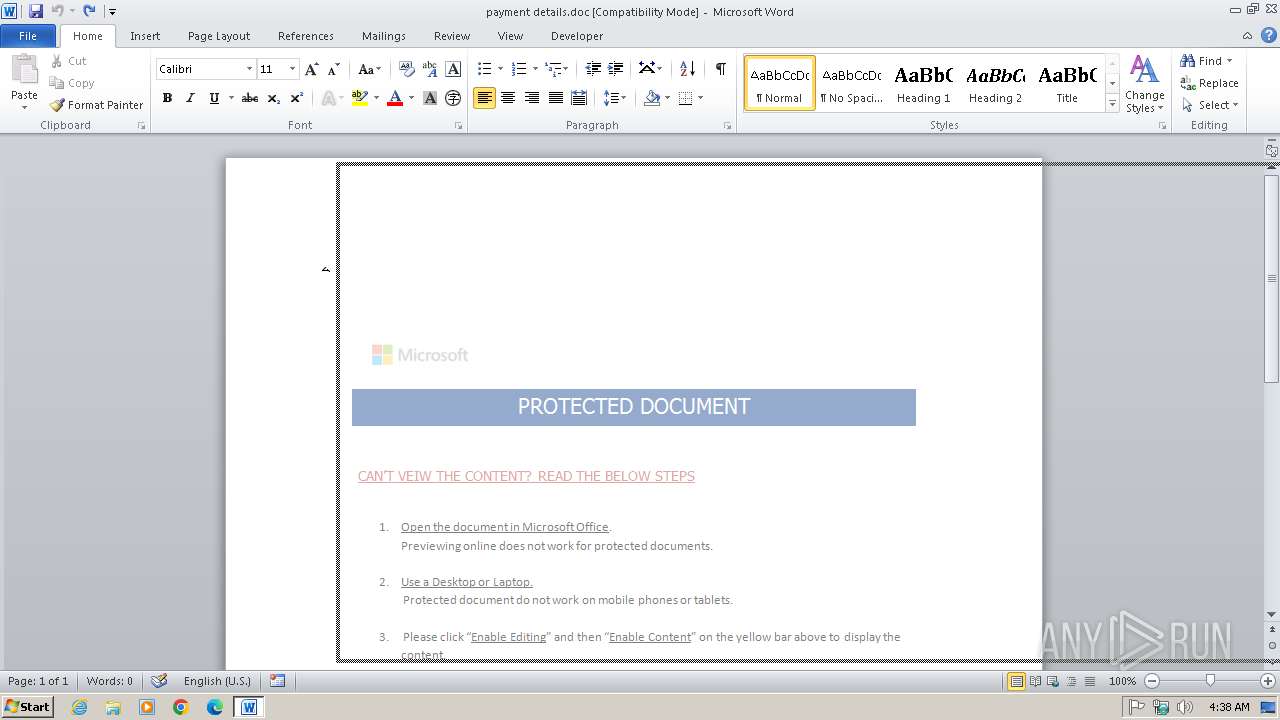
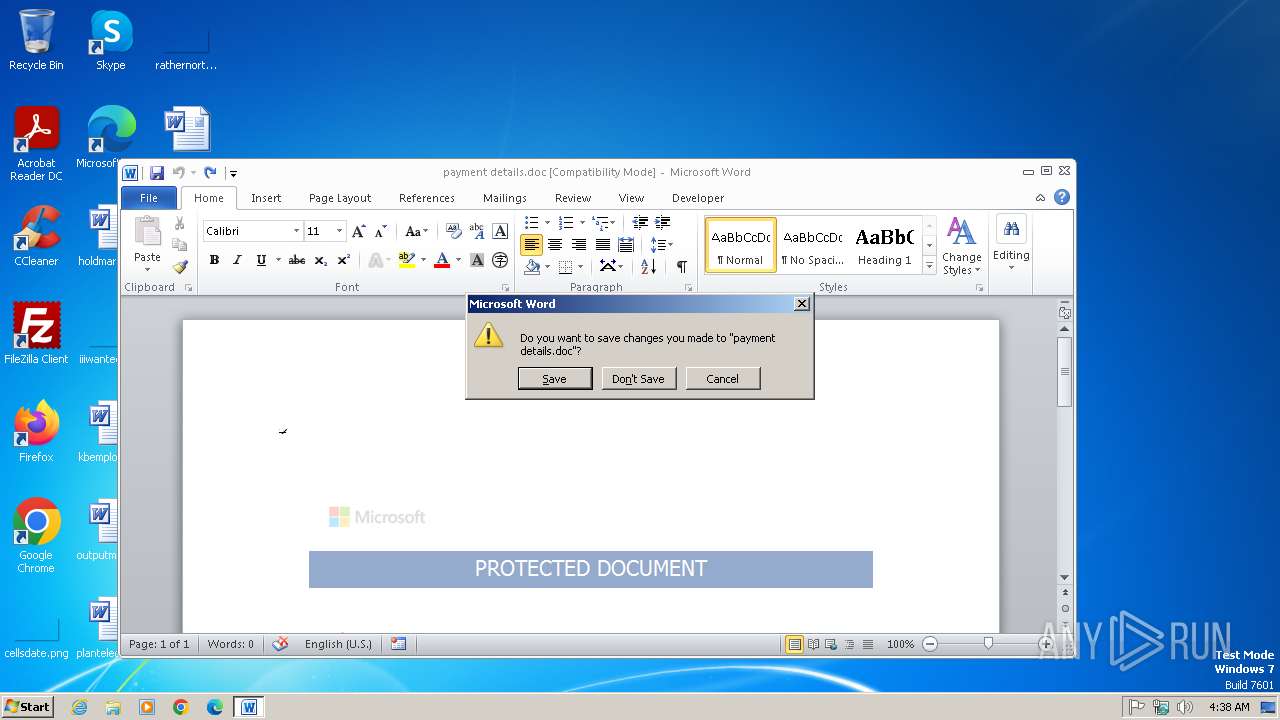
| File name: | payment details.doc |
| Full analysis: | https://app.any.run/tasks/00908c38-c299-4608-a5c9-5c111f2599c4 |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 03:38:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, Code page: 1252, Author: Windows User, Template: Normal.dotm, Last Saved By: MATRIX, Revision Number: 8, Name of Creating Application: Microsoft Office Word, Total Editing Time: 03:00, Create Time/Date: Fri Feb 28 03:49:00 2020, Last Saved Time/Date: Wed May 25 14:58:00 2022, Number of Pages: 1, Number of Words: 3, Number of Characters: 18, Security: 0 |
| MD5: | A3AC96A5B997A546855538E67072FCF1 |
| SHA1: | 03BFD25A4A775563228A85DD861DD621B61F8FE7 |
| SHA256: | A0BF6F09F394949C603B878AB42B001155D347E5812B59F09A2AB9D387D548F6 |
| SSDEEP: | 12288:6dffGZFF0UGe1famHsB17GXWwnJDygrfQC:OeRbH81ymwnJegTQC |
MALICIOUS
Unusual execution from MS Office
- WINWORD.EXE (PID: 2840)
Executable content was dropped or overwritten
- WINWORD.EXE (PID: 2840)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- WINWORD.EXE (PID: 2840)
INFO
Checks supported languages
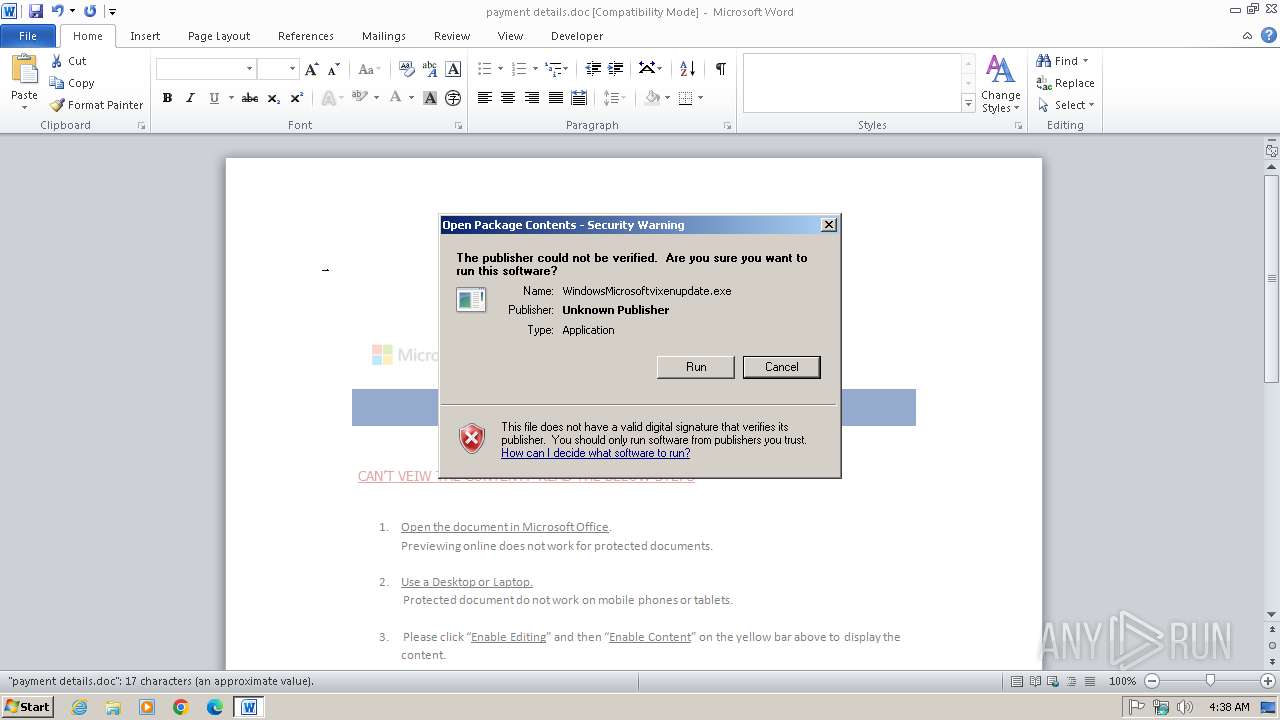
- WindowsMicrosoftvixenupdate.exe (PID: 2568)
Reads the computer name
- WindowsMicrosoftvixenupdate.exe (PID: 2568)
Reads the machine GUID from the registry
- WindowsMicrosoftvixenupdate.exe (PID: 2568)
.NET Reactor protector has been detected
- WindowsMicrosoftvixenupdate.exe (PID: 2568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | Windows User |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | MATRIX |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:02:28 03:49:00 |
| ModifyDate: | 2022:05:25 14:58:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 20 |
| AppVersion: | 14 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 8 |
| TotalEditTime: | 3 minutes |
| Words: | 3 |
| Characters: | 18 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2568 | "C:\Users\admin\AppData\Local\Temp\WindowsMicrosoftvixenupdate.exe" | C:\Users\admin\AppData\Local\Temp\WindowsMicrosoftvixenupdate.exe | — | WINWORD.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: CarRace Game Version: 4.2.0.1 Modules
| |||||||||||||||
| 2840 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\payment details.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
9 945
Read events
9 348
Write events
267
Delete events
330
Modification events
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: 180B0000CCD35F1FDDC6DB0100000000 | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\Themes\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\WordDocParts\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LCCache\SmartArt\1033 |
| Operation: | delete value | Name: | NextUpdate |
Value: | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | :6# |
Value: 3A362300180B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | :6# |
Value: 㘺#ଘ | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2840) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
2
Suspicious files
7
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR16DE.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2840 | WINWORD.EXE | C:\Users\admin\Desktop\~$yment details.doc | binary | |
MD5:D8E2154D1A9E29788C1EA60886EAF145 | SHA256:40D5B4307847409604F329226F415F2FCF2A824DFEC3C299829411CC28B41D7F | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\452FF749.emf | binary | |
MD5:A4914739C85710A71845BEDB4ED8690A | SHA256:C03DDBB289A46CDD9332AFE3569434F6F8095CCEA990390DC5DCCE94C152412F | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\payment details.doc.LNK | binary | |
MD5:D10C570C3A48BBC9E46100D0A1EAABA8 | SHA256:8E867A6E4D4E664165B128734F8E3A48180121FB2CBCFF83E2F68CF8FF91251A | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:CB78209A5D41936EF14AC2EE99593CC3 | SHA256:592323C4E1D21B4F4D29AD6BA44F520A299E12F60BE1DDAEC9930750FCE2E3BD | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\WindowsMicrosoftvixenupdate.exe:Zone.Identifier | text | |
MD5:FBCCF14D504B7B2DBCB5A5BDA75BD93B | SHA256:EACD09517CE90D34BA562171D15AC40D302F0E691B439F91BE1B6406E25F5913 | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\WindowsMicrosoftvixenupdate.exe | executable | |
MD5:208C18D5B375125E95CC9CCF582C2B9E | SHA256:F2354328324B94918311EF7A13E9C207B75F848BCAADEBE7F4753F3D5FCFC63D | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~DF442F319D16C6172A.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{9DE9F707-2E21-403C-8688-DD01FA3D2D8F}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
| 2840 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:7EE3F336A9C82E5FBE967D53FFA1594F | SHA256:B020B32E2EB3AD286F78AA23875ACECB651B2AA8706852638EDF80FEEFF1A41F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2840 | WINWORD.EXE | POST | 302 | 2.19.106.8:80 | http://go.microsoft.com/fwlink/?LinkID=120750 | unknown | — | — | whitelisted |
2840 | WINWORD.EXE | POST | 302 | 2.19.106.8:80 | http://go.microsoft.com/fwlink/?LinkID=120751 | unknown | — | — | whitelisted |
2840 | WINWORD.EXE | POST | 302 | 2.19.106.8:80 | http://go.microsoft.com/fwlink/?LinkID=120752 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2840 | WINWORD.EXE | 2.19.106.8:80 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
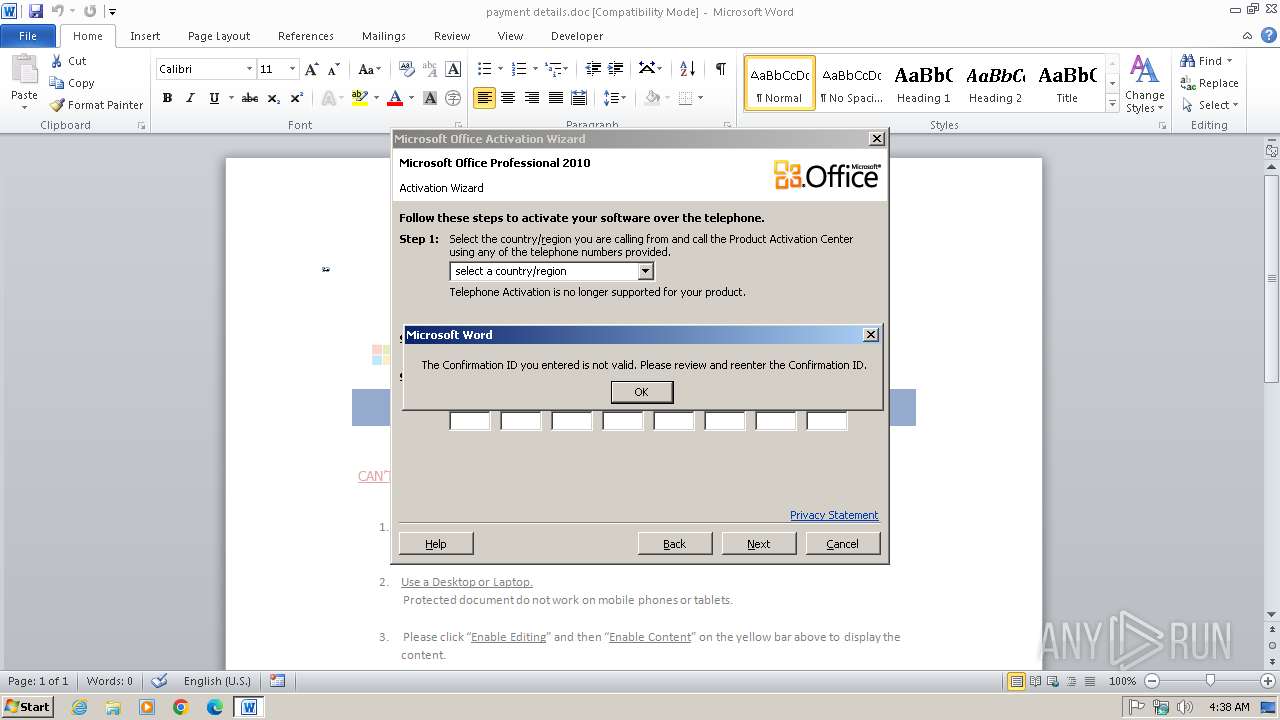
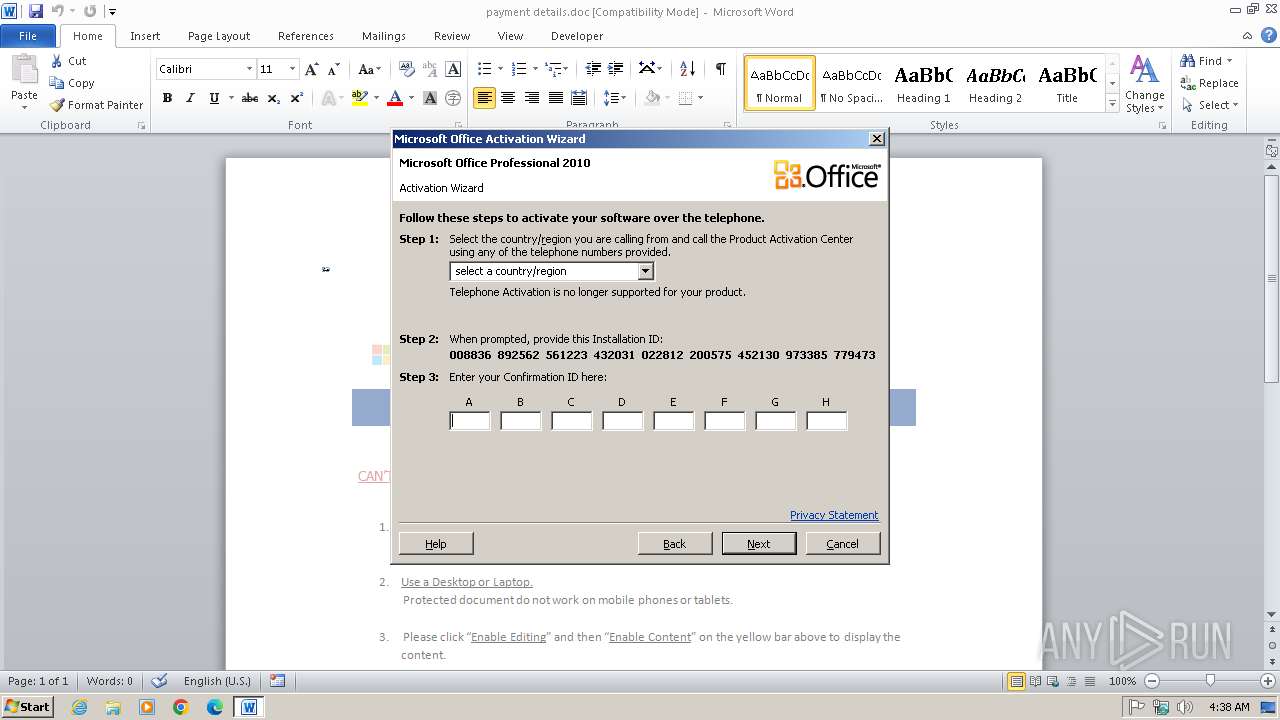
2840 | WINWORD.EXE | 40.91.76.224:443 | activation.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |