| File name: | 8A6EA674E75372008949C4F1E04303D4265638FE.exe |
| Full analysis: | https://app.any.run/tasks/727b187f-e162-4111-a5f9-4ca4c5693a71 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 14:35:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | D3344DA029B2296761359F8E1DBB1C49 |
| SHA1: | 8A6EA674E75372008949C4F1E04303D4265638FE |
| SHA256: | A0919D2A455417657A4CAD342725A536A7B780651DF720F2D2AC77FD91BE8DB2 |
| SSDEEP: | 3072:MJ7mYROZdkz9fjqOvi5la+Jt5swoT+CRjWCBk6/0Dg4HLBNC4l3Xo6kldN:MQlkdqQAat6CRjWI1dELyso68 |
MALICIOUS
Changes the autorun value in the registry
- 8A6EA674E75372008949C4F1E04303D4265638FE.exe (PID: 3732)
- svchost.exe (PID: 584)
Uses SVCHOST.EXE for hidden code execution
- 8A6EA674E75372008949C4F1E04303D4265638FE.exe (PID: 3732)
SUSPICIOUS
Starts Internet Explorer
- 8A6EA674E75372008949C4F1E04303D4265638FE.exe (PID: 3732)
Application launched itself
- 8A6EA674E75372008949C4F1E04303D4265638FE.exe (PID: 2524)
Executable content was dropped or overwritten
- 8A6EA674E75372008949C4F1E04303D4265638FE.exe (PID: 3732)
Creates files in the user directory
- 8A6EA674E75372008949C4F1E04303D4265638FE.exe (PID: 3732)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2668)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 960)
Creates files in the user directory
- iexplore.exe (PID: 2668)
- WINWORD.EXE (PID: 960)
Manual execution by user
- WINWORD.EXE (PID: 960)
- msinfo32.exe (PID: 2720)
- explorer.exe (PID: 3836)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (30.7) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (30.1) |
| .exe | | | Win32 EXE Yoda's Crypter (29.5) |
| .exe | | | Win32 Executable (generic) (5) |
| .exe | | | Generic Win/DOS Executable (2.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:05:30 04:30:05+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 163840 |
| InitializedDataSize: | 32768 |
| UninitializedDataSize: | 92274688 |
| EntryPoint: | 0x5827e90 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 11.0.55321.0 |
| ProductVersionNumber: | 11.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Private build |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| CompanyName: | TeamViewer GmbH |
| FileDescription: | TeamViewer 11 |
| FileVersion: | 11.0.55321.0 |
| InternalName: | TeamViewer |
| LegalCopyright: | TeamViewer GmbH |
| LegalTrademarks: | TeamViewer |
| OriginalFileName: | TeamViewer.exe |
| PrivateBuild: | TeamViewer Remote Control Application |
| ProductName: | TeamViewer |
| ProductVersion: | 11 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 30-May-2007 02:30:05 |
| Detected languages: |
|
| CompanyName: | TeamViewer GmbH |
| FileDescription: | TeamViewer 11 |
| FileVersion: | 11.0.55321.0 |
| InternalName: | TeamViewer |
| LegalCopyright: | TeamViewer GmbH |
| LegalTrademarks: | TeamViewer |
| OriginalFilename: | TeamViewer.exe |
| PrivateBuild: | TeamViewer Remote Control Application |
| ProductName: | TeamViewer |
| ProductVersion: | 11.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 30-May-2007 02:30:05 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x05800000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x05801000 | 0x00028000 | 0x00027200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.71396 |
.rsrc | 0x05829000 | 0x00008000 | 0x00007E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.81263 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.35697 | 884 | Latin 1 / Western European | English - United States | RT_VERSION |
2 | 6.88627 | 296 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
3 | 5.79022 | 296 | Latin 1 / Western European | Chinese - PRC | RT_ICON |
7 | 5.97605 | 116 | Latin 1 / Western European | Chinese - PRC | RT_STRING |
103 | 6.48301 | 254 | Latin 1 / Western European | Chinese - PRC | RT_DIALOG |
107 | 4.82997 | 34 | Latin 1 / Western European | Chinese - PRC | RT_GROUP_ICON |
108 | 4.32193 | 20 | Latin 1 / Western European | Chinese - PRC | RT_GROUP_ICON |
109 | 3.875 | 16 | Latin 1 / Western European | Chinese - PRC | RT_ACCELERATOR |
Imports
GDI32.dll |
KERNEL32.DLL |
USER32.dll |
Total processes
51
Monitored processes
7
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 584 | svchost.exe | C:\Windows\system32\svchost.exe | 8A6EA674E75372008949C4F1E04303D4265638FE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 960 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Documents\bsoftware.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2524 | "C:\Users\admin\AppData\Local\Temp\8A6EA674E75372008949C4F1E04303D4265638FE.exe" | C:\Users\admin\AppData\Local\Temp\8A6EA674E75372008949C4F1E04303D4265638FE.exe | — | explorer.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer 11 Exit code: 0 Version: 11.0.55321.0 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Internet Explorer\iexplore.exe" | C:\Program Files\Internet Explorer\iexplore.exe | — | 8A6EA674E75372008949C4F1E04303D4265638FE.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2720 | "C:\Windows\system32\msinfo32.exe" | C:\Windows\system32\msinfo32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: System Information Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3732 | "C:\Users\admin\AppData\Local\Temp\8A6EA674E75372008949C4F1E04303D4265638FE.exe" | C:\Users\admin\AppData\Local\Temp\8A6EA674E75372008949C4F1E04303D4265638FE.exe | 8A6EA674E75372008949C4F1E04303D4265638FE.exe | ||||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer 11 Exit code: 0 Version: 11.0.55321.0 Modules
| |||||||||||||||
| 3836 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 424
Read events
1 048
Write events
235
Delete events
141
Modification events
| (PID) Process: | (3732) 8A6EA674E75372008949C4F1E04303D4265638FE.exe | Key: | HKEY_CURRENT_USER\Software\We7qCrQnw |
| Operation: | write | Name: | ServerStarted |
Value: 12/6/2019 14:36:35 PM | |||
| (PID) Process: | (3732) 8A6EA674E75372008949C4F1E04303D4265638FE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | HKLM |
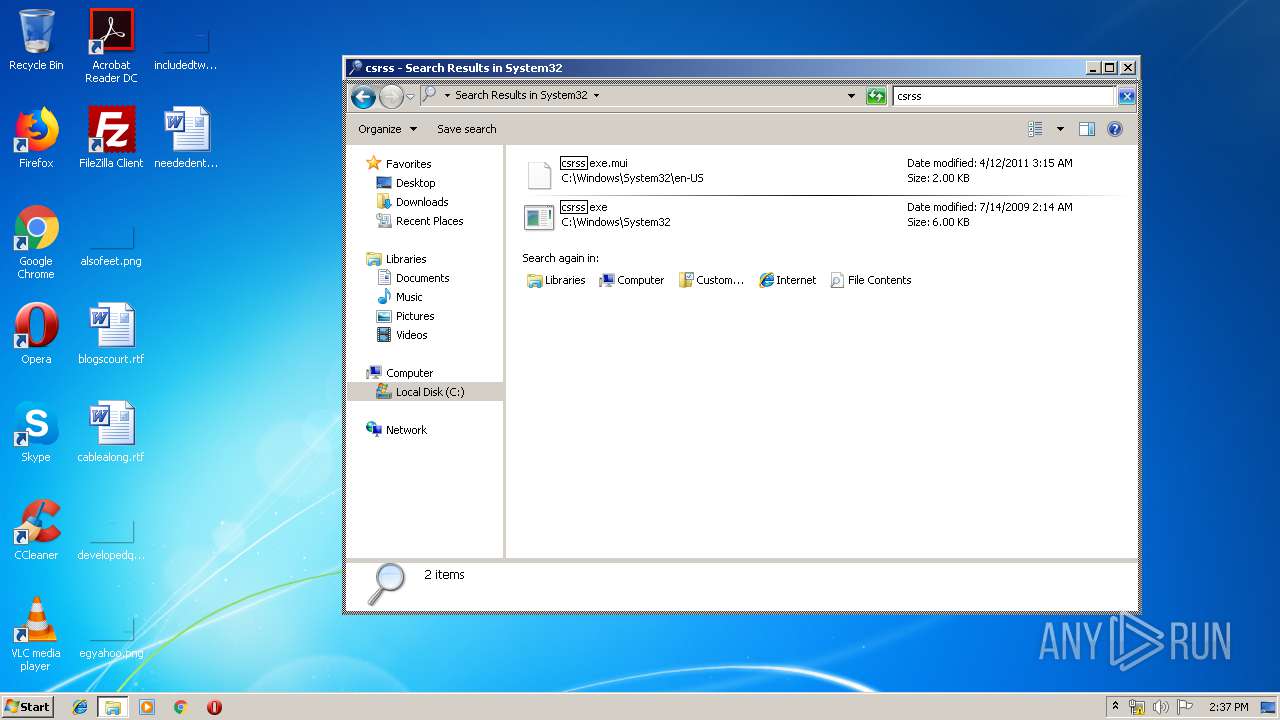
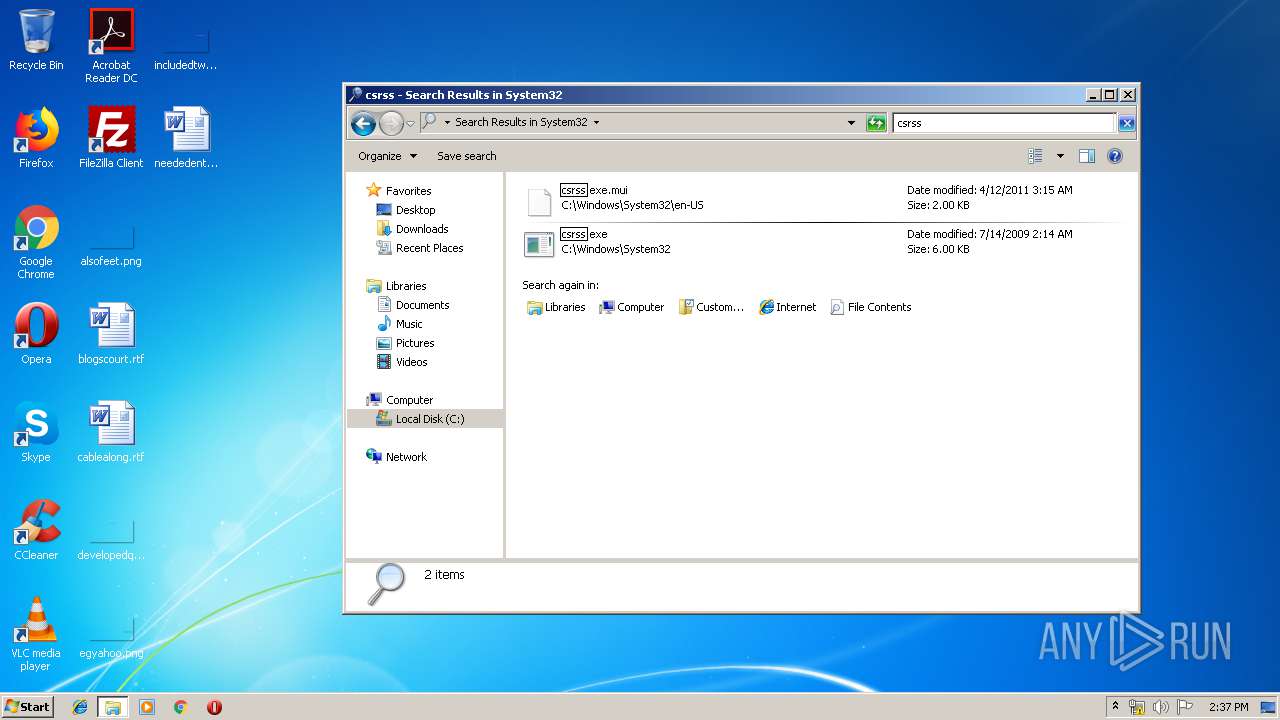
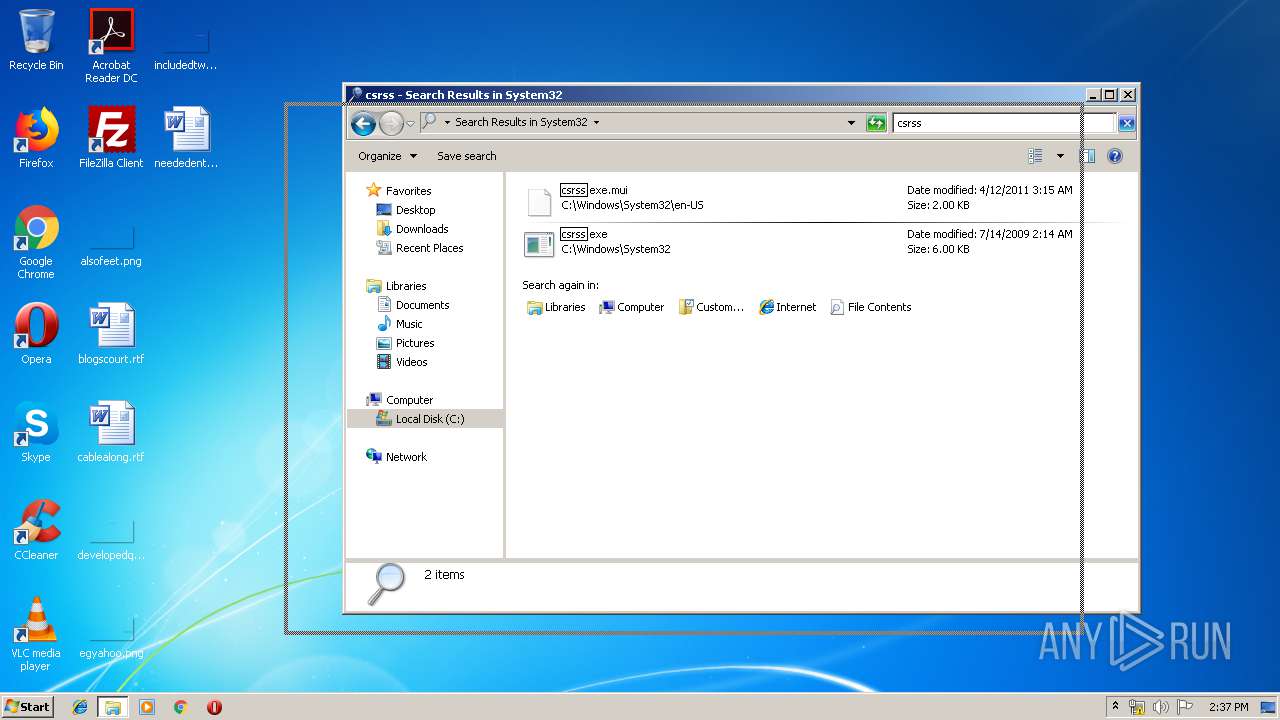
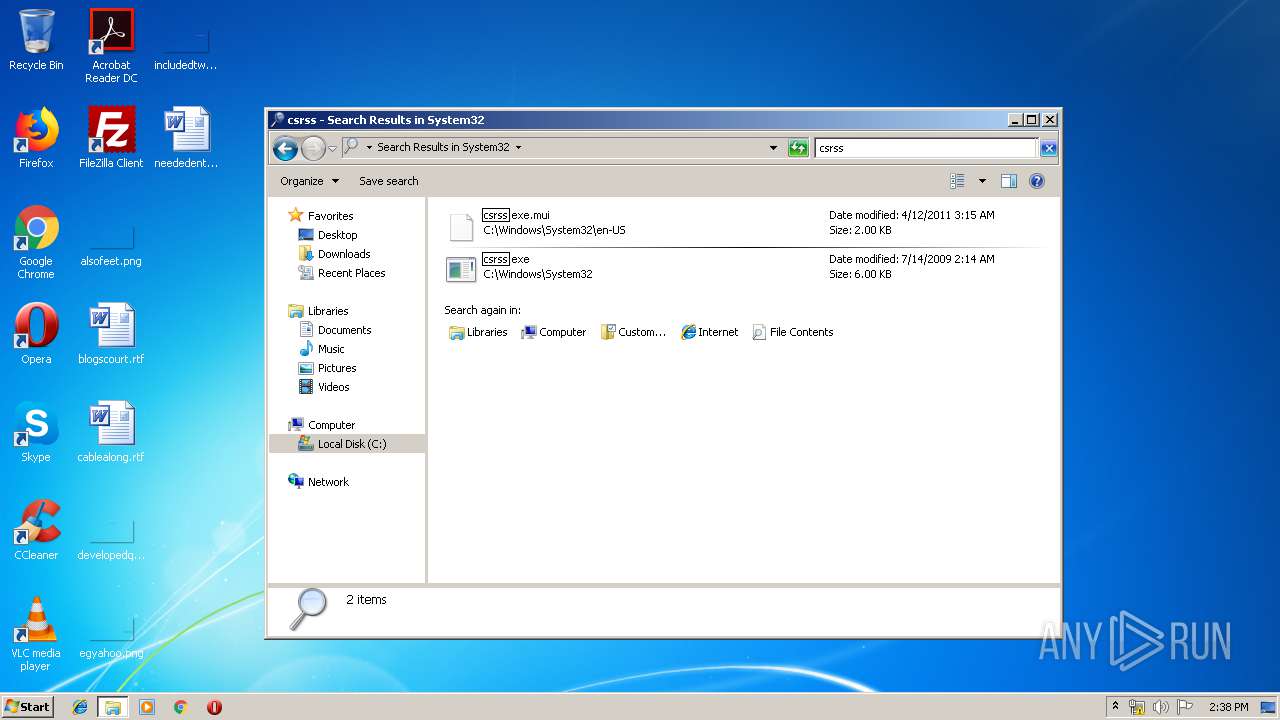
Value: C:\Users\admin\AppData\Roaming\System32\csrss.exe | |||
| (PID) Process: | (3732) 8A6EA674E75372008949C4F1E04303D4265638FE.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | HKCU |
Value: C:\Users\admin\AppData\Roaming\System32\csrss.exe | |||
| (PID) Process: | (3732) 8A6EA674E75372008949C4F1E04303D4265638FE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Active Setup\Installed Components\{5460C4DF-B266-909E-CB58-E32B79832EB2} |
| Operation: | write | Name: | StubPath |
Value: C:\Users\admin\AppData\Roaming\System32\csrss.exe restart | |||
| (PID) Process: | (3732) 8A6EA674E75372008949C4F1E04303D4265638FE.exe | Key: | HKEY_CURRENT_USER\Software\We7qCrQnw |
| Operation: | write | Name: | InstalledServer |
Value: C:\Users\admin\AppData\Roaming\System32\csrss.exe | |||
| (PID) Process: | (2668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000093000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2668) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (584) svchost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | HKCU |
Value: C:\Users\admin\AppData\Roaming\System32\csrss.exe | |||
Executable files
1
Suspicious files
1
Text files
2
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE527.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{172B7881-D969-450D-A461-CFD28AF0FA81}.tmp | — | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{A3CD98EC-F5C2-4957-9591-5B17846EFE09}.tmp | — | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRF{B33A1157-B2FE-4E58-BC6D-C75CFBEED4E8}.tmp | — | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\Documents\~$oftware.rtf | pgc | |
MD5:— | SHA256:— | |||
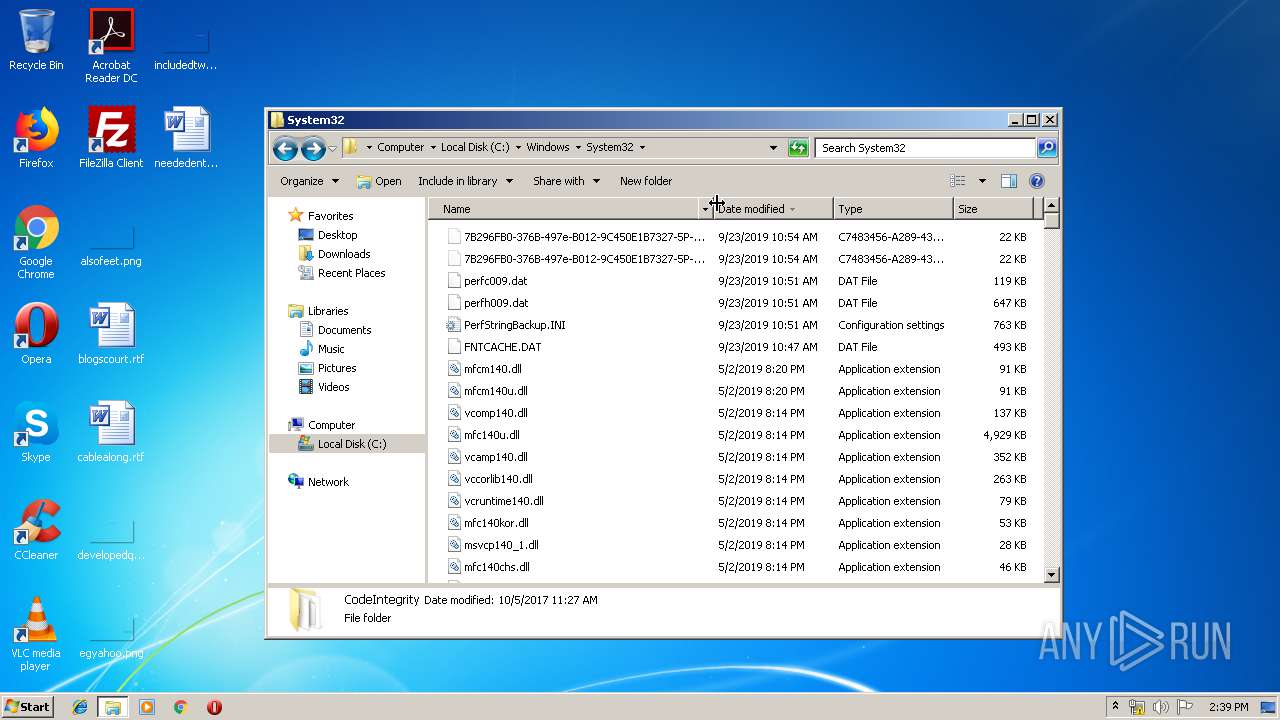
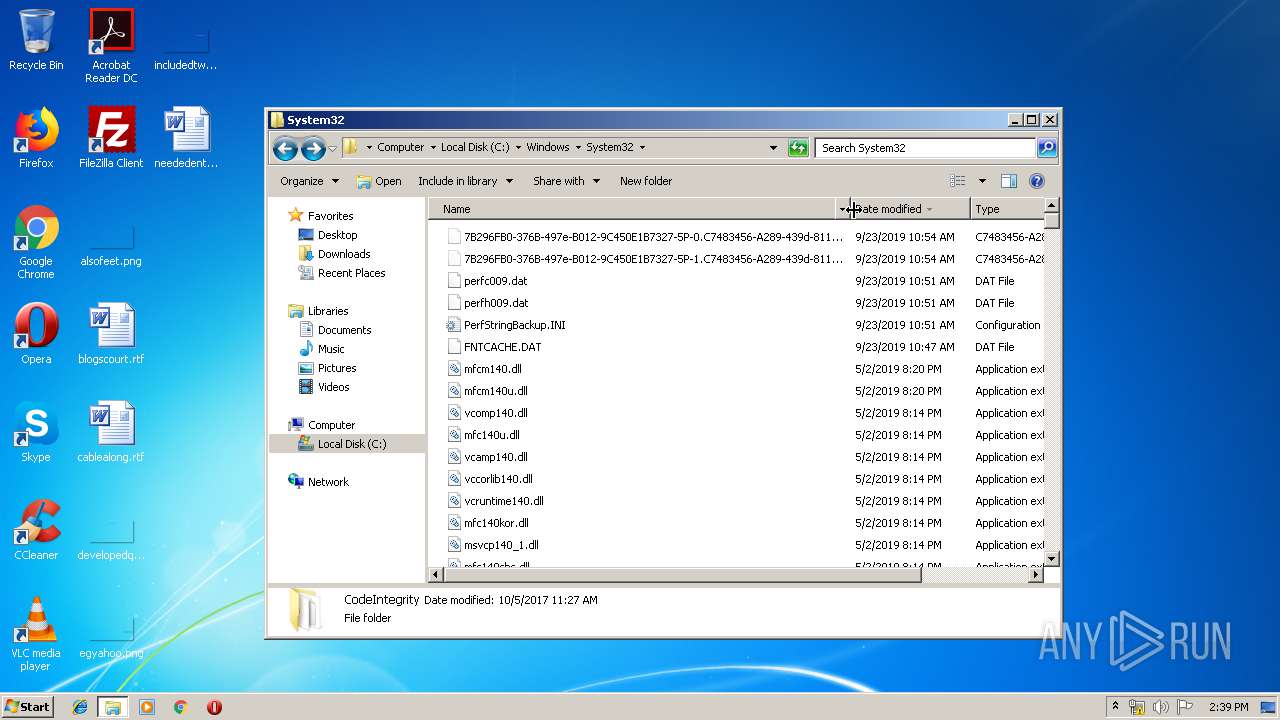
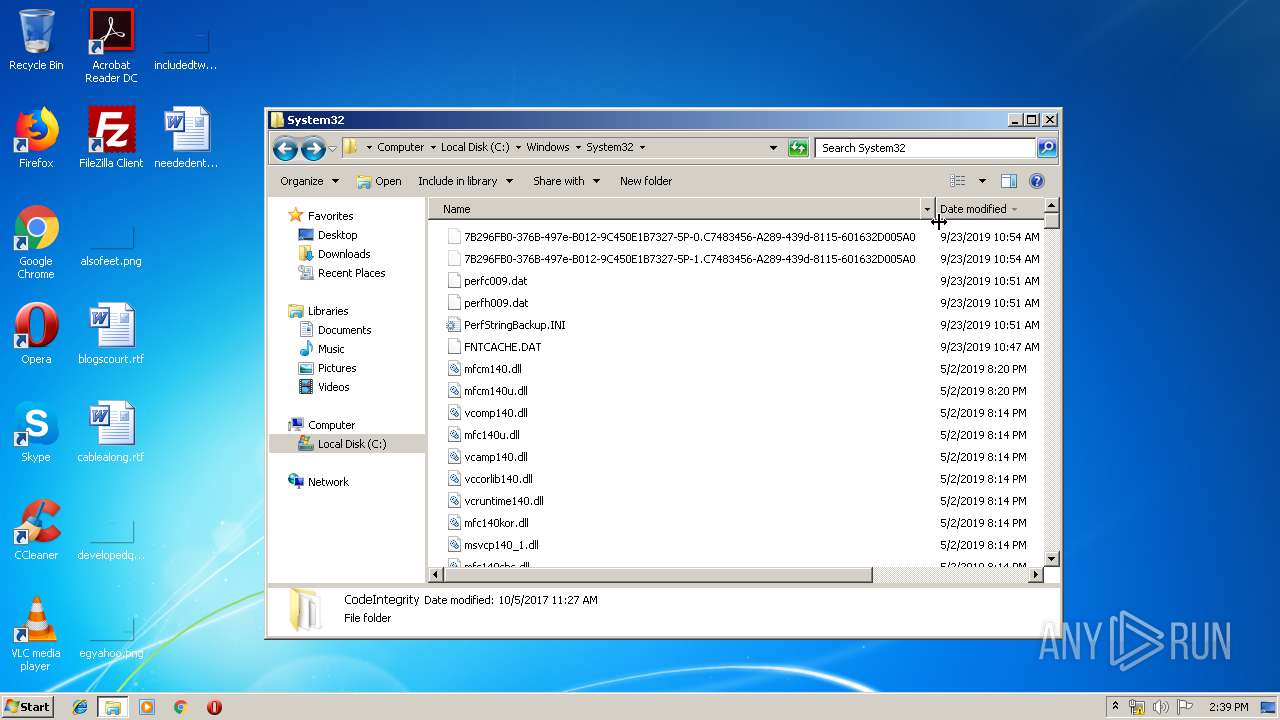
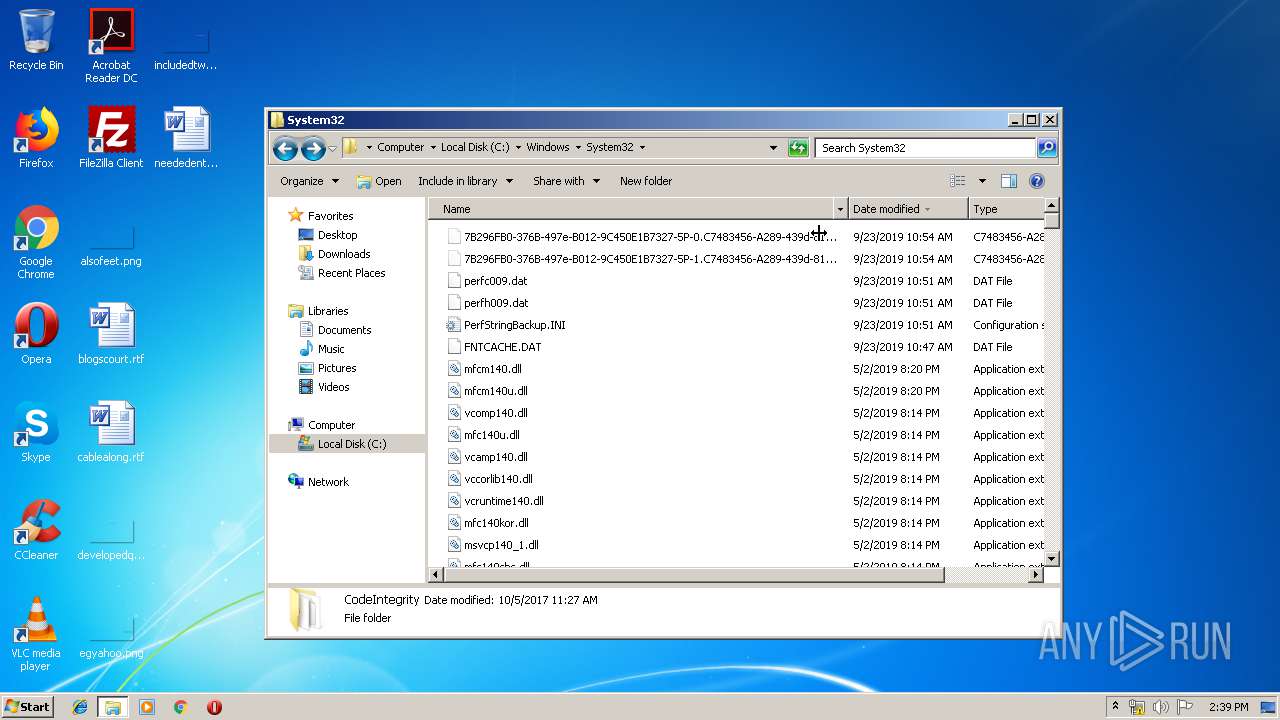
| 3732 | 8A6EA674E75372008949C4F1E04303D4265638FE.exe | C:\Users\admin\AppData\Roaming\System32\csrss.exe | executable | |
MD5:— | SHA256:— | |||
| 3732 | 8A6EA674E75372008949C4F1E04303D4265638FE.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\We7qCrQnw.cfg | binary | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\bsoftware.rtf.LNK | lnk | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 960 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
1
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Domain | IP | Reputation |
|---|---|---|
clarityz.no-ip.biz |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DYNAMIC_DNS Query to a Suspicious no-ip Domain |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |