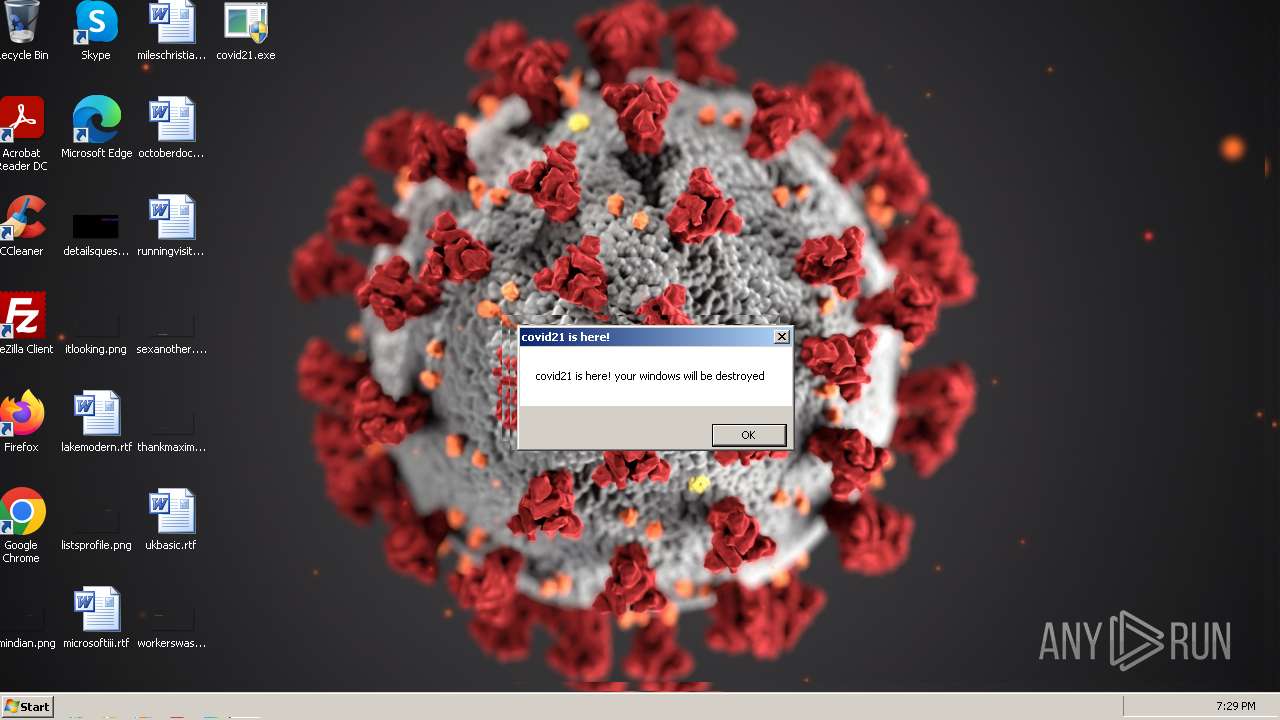
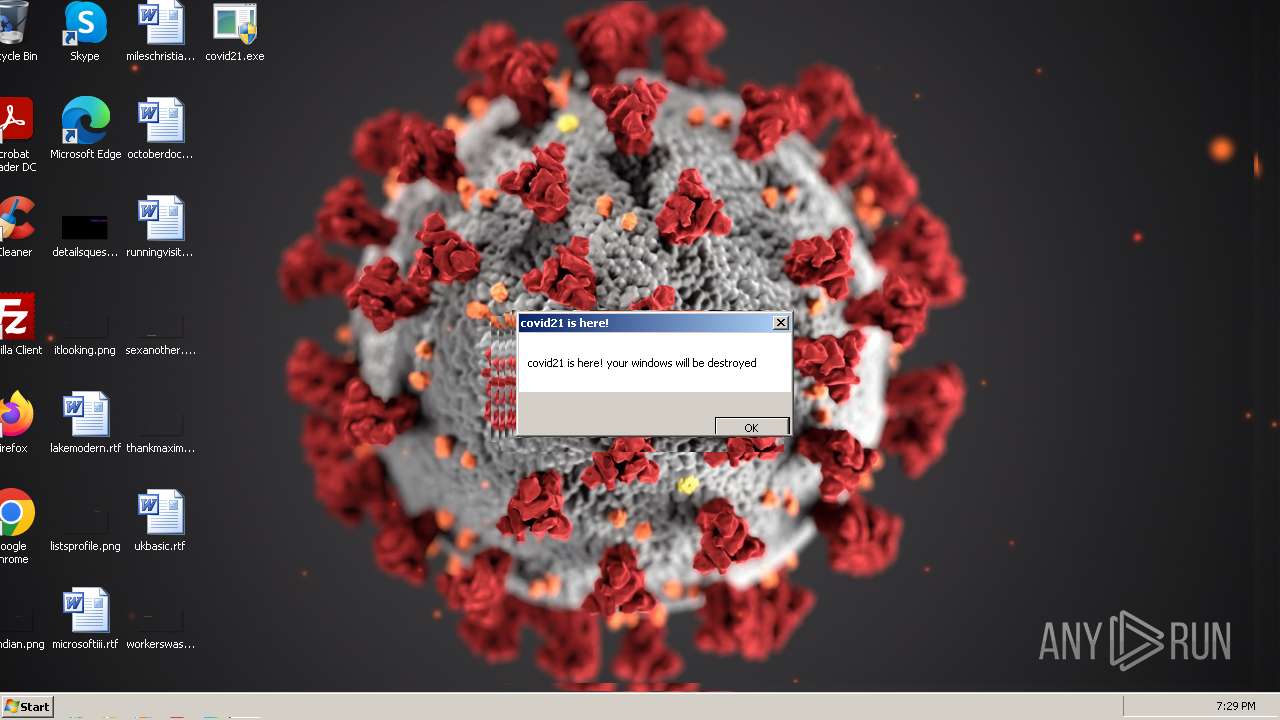
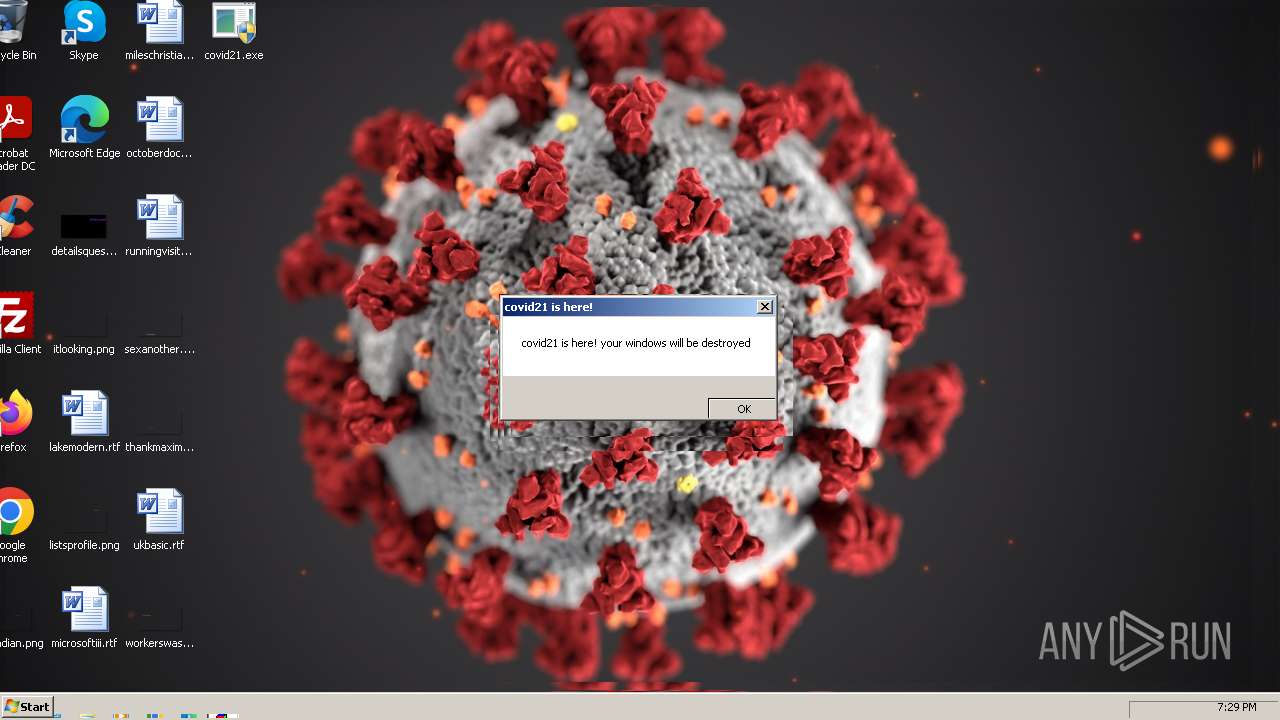
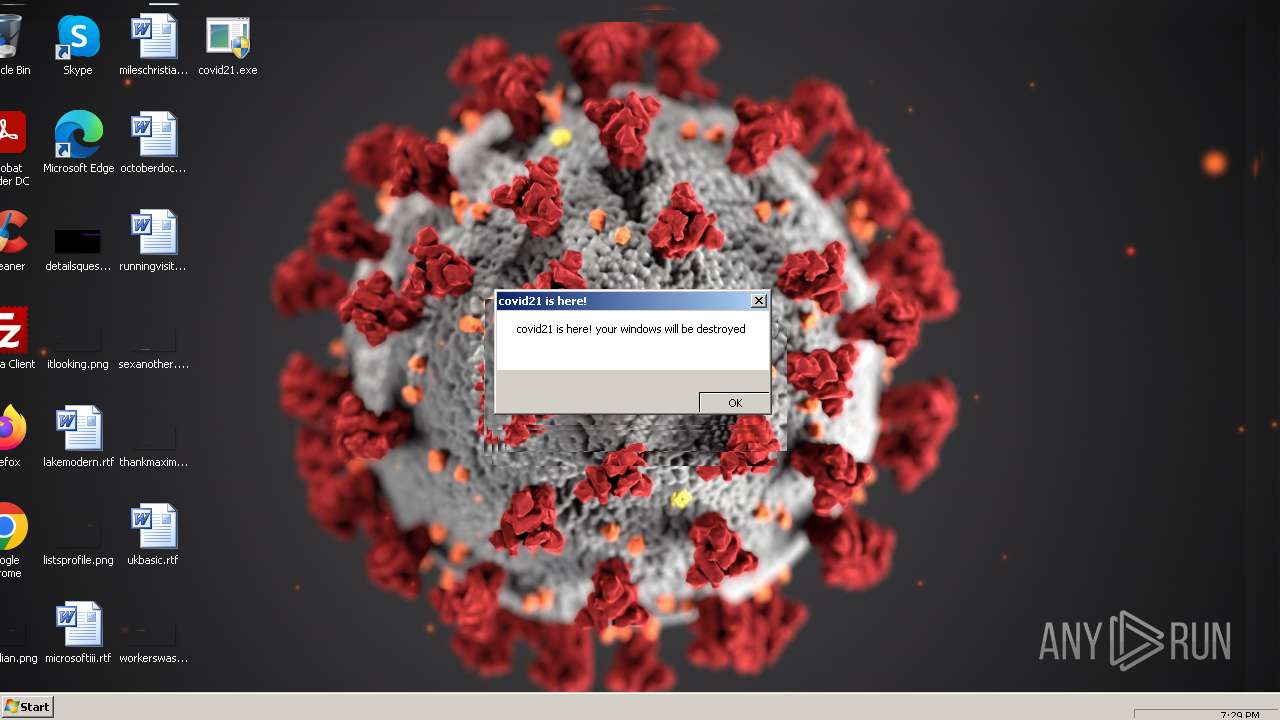
| File name: | covid21.exe |
| Full analysis: | https://app.any.run/tasks/6ff77764-37ee-4152-9eb0-c2ff987a47f3 |
| Verdict: | Malicious activity |
| Analysis date: | February 22, 2024, 19:29:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | 1A2E2D295E04F74437652DC9B8A2D03C |
| SHA1: | E3565983EE402856C2CF4EEC2AC6FF9636443FE9 |
| SHA256: | A078251C61A4F90BF60DA47D99CEA465BE5D44057684D681FB3D94A20D2025BD |
| SSDEEP: | 98304:+4vFOFeH129yvv9K1gNDV/62i1zoxyBVNvHrKiGCMplhu3pyK8huj4ioaYT3X26Q:bzH |
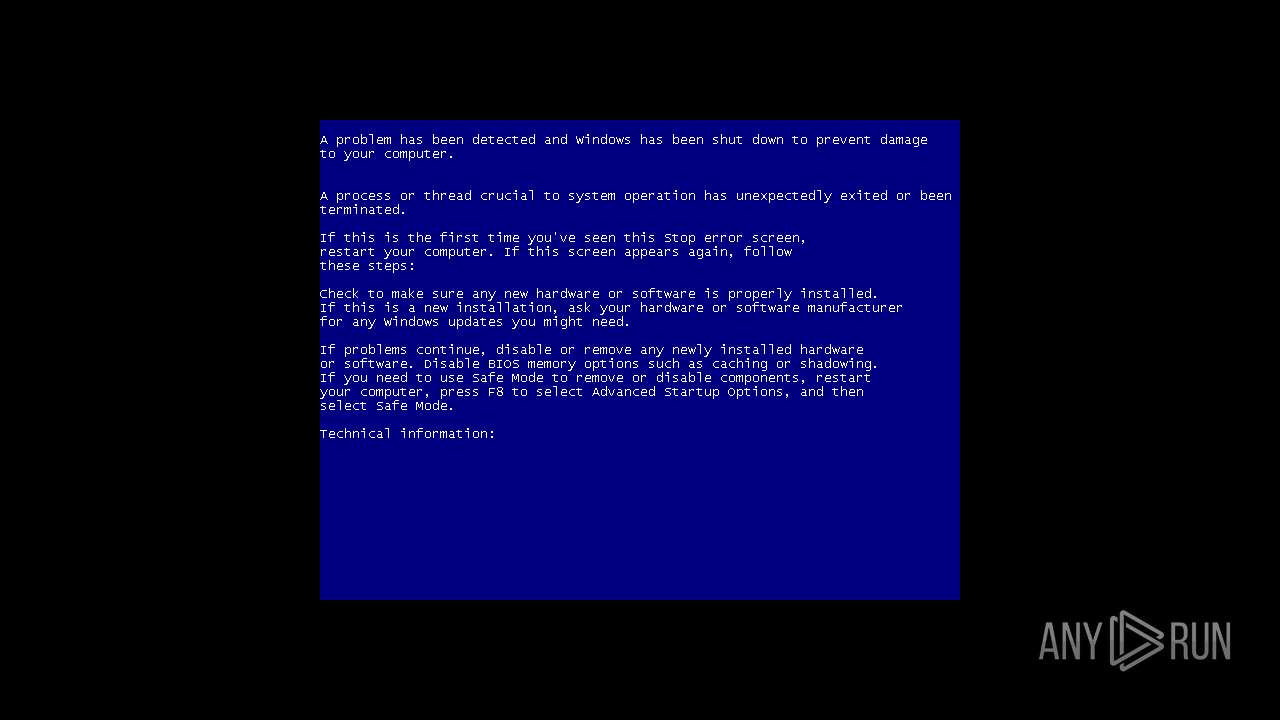
MALICIOUS
Drops the executable file immediately after the start
- covid21.exe (PID: 2844)
SUSPICIOUS
Reads the Internet Settings
- covid21.exe (PID: 2844)
- cmd.exe (PID: 2840)
Executing commands from a ".bat" file
- covid21.exe (PID: 2844)
Starts CMD.EXE for commands execution
- covid21.exe (PID: 2844)
The executable file from the user directory is run by the CMD process
- CLWCP.exe (PID: 1876)
- screenscrew.exe (PID: 4000)
- PayloadGDI.exe (PID: 2856)
- PayloadMBR.exe (PID: 3980)
Reads security settings of Internet Explorer
- covid21.exe (PID: 2844)
Executable content was dropped or overwritten
- covid21.exe (PID: 2844)
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 2840)
The process executes VB scripts
- cmd.exe (PID: 2840)
INFO
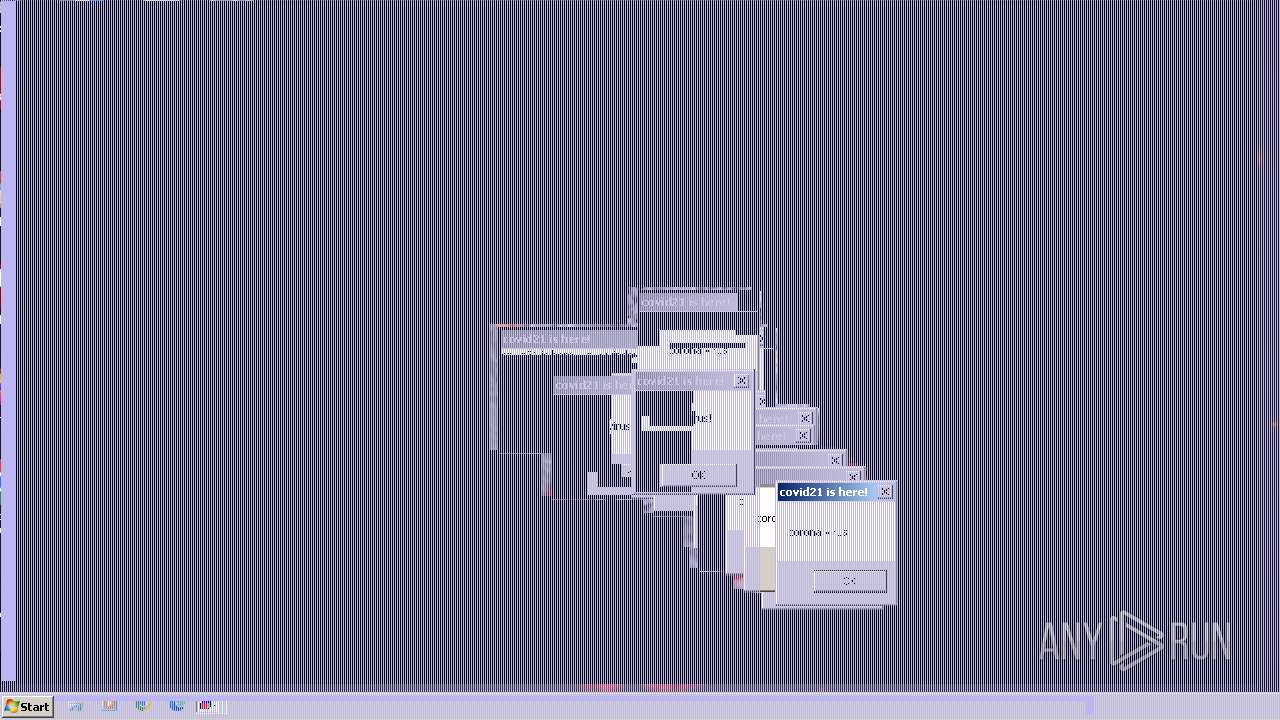
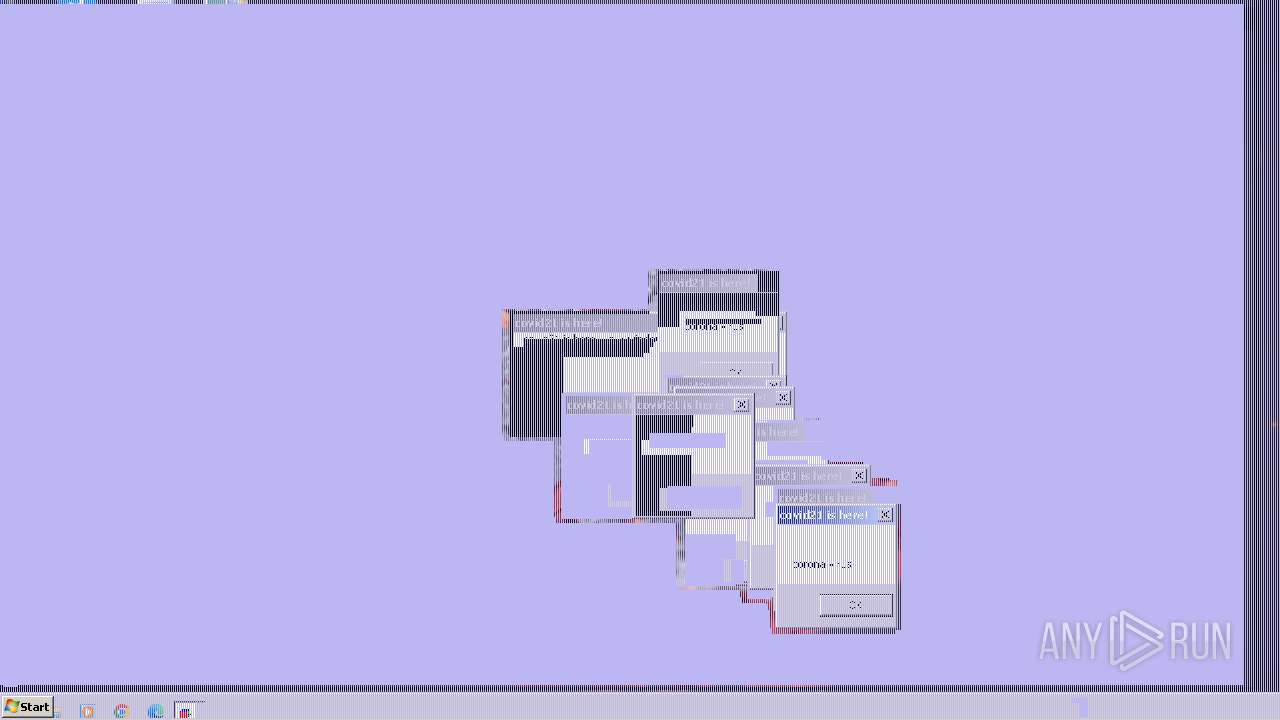
Drops a (possible) Coronavirus decoy
- covid21.exe (PID: 2844)
- cmd.exe (PID: 2840)
Checks supported languages
- covid21.exe (PID: 2844)
- CLWCP.exe (PID: 1876)
- PayloadGDI.exe (PID: 2856)
- screenscrew.exe (PID: 4000)
Reads the computer name
- covid21.exe (PID: 2844)
Create files in a temporary directory
- covid21.exe (PID: 2844)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2010:11:08 13:12:07+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 2117632 |
| InitializedDataSize: | 4096 |
| UninitializedDataSize: | 5320704 |
| EntryPoint: | 0x717d80 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
75
Monitored processes
35
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 120 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\F79E.tmp\covid.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 680 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\F79E.tmp\corona.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 696 | timeout 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 748 | timeout 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1336 | timeout 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1816 | timeout /3 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\F79E.tmp\covid21.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1876 | clwcp c:\covid21\covid.bmp | C:\Users\admin\AppData\Local\Temp\F79E.tmp\CLWCP.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2060 | timeout 1 /nobreak | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2184 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\F79E.tmp\corona.vbs" | C:\Windows\System32\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
Total events
8 124
Read events
8 012
Write events
112
Delete events
0
Modification events
| (PID) Process: | (2844) covid21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2844) covid21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2844) covid21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2844) covid21.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (2840) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2840) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2840) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2840) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
4
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2844 | covid21.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\covid.bmp | — | |
MD5:— | SHA256:— | |||
| 2840 | cmd.exe | C:\covid21\covid.bmp | — | |
MD5:— | SHA256:— | |||
| 2844 | covid21.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\covid21.bat | text | |
MD5:CB71400420494F3DD91D5CD070B01B3F | SHA256:25034DCCDB96D86E3B797B7DB7DD7786D74B51120196C44340A03B3291B3C9AC | |||
| 2844 | covid21.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\screenscrew.exe | executable | |
MD5:E87A04C270F98BB6B5677CC789D1AD1D | SHA256:E03520794F00FB39EF3CFFF012F72A5D03C60F89DE28DBE69016F6ED151B5338 | |||
| 2840 | cmd.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\corona.vbs | text | |
MD5:F4DE606815F3BD1BF38B83C91AC66C35 | SHA256:AAC0328F3782AEFD5BB8A2DF87B65DCC545A0F2CB4A0052F9068B53BA6D4E0D3 | |||
| 2844 | covid21.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\CLWCP.exe | executable | |
MD5:E62EE6F1EFC85CB36D62AB779DB6E4EC | SHA256:13B4EC59785A1B367EFB691A3D5C86EB5AAF1CA0062521C4782E1BAAC6633F8A | |||
| 2844 | covid21.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\PayloadGDI.exe | executable | |
MD5:A7CE5BEE03C197F0A99427C4B590F4A0 | SHA256:0C53A3EC2B432A9013546F92416109D7E8F64CEA26AC2491635B4CF2A310D852 | |||
| 2844 | covid21.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\PayloadMBR.exe | executable | |
MD5:D917AF256A1D20B4EAC477CDB189367B | SHA256:E40F57F6693F4B817BEB50DE68027AABBB0376CA94A774F86E3833BAF93DC4C0 | |||
| 2840 | cmd.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\covid21.vbs | text | |
MD5:87AAEBE24D9CC38CB0357E9723CCE915 | SHA256:0AA36C0A57C3F2C57EE9D674CEFCCD86970C239233F571718D434472C0F6FFBA | |||
| 2840 | cmd.exe | C:\Users\admin\AppData\Local\Temp\F79E.tmp\covid.vbs | text | |
MD5:6B29DA2D6D7BAC4E365D7BFDDB4B5428 | SHA256:23C3C72DB728EB062DB9336E1C8E7840D4C554720D056CFF41E2339B07879F75 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |