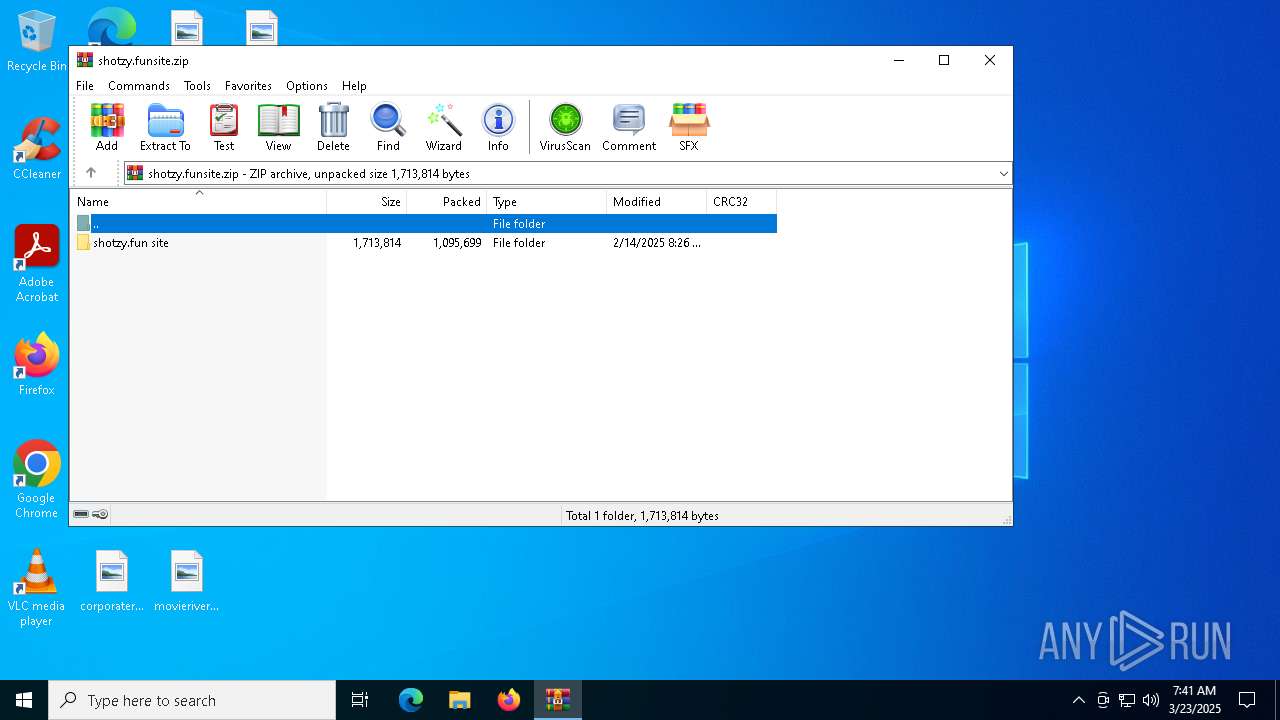
| File name: | shotzy.funsite.zip |
| Full analysis: | https://app.any.run/tasks/513a83b1-7736-4dfb-9aa1-02f87087ede9 |
| Verdict: | Malicious activity |
| Analysis date: | March 23, 2025, 07:41:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 060A6D3C842A12DAEA5956B898553D6B |
| SHA1: | D5258585B092F2E66EA186DC634177A2F33978C4 |
| SHA256: | A067AA086C9402197D9F4FC4D2F13B5D12D222C3BAF12A56E232565D6FF41EE8 |
| SSDEEP: | 49152:Ltd83/AuFURkWboqoLFf/6TxL6I7alJkAy9tG9FxS61aen460slwJHD61eBFGWio:Ltd8JUR/kqop/6TxLxalWRtWFn1a44Hd |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 7328)
SUSPICIOUS
Possible usage of Discord/Telegram API has been detected (YARA)
- wscript.exe (PID: 7560)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7328)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 7328)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 7328)
INFO
Manual execution by a user
- wscript.exe (PID: 7452)
- wscript.exe (PID: 7560)
- wscript.exe (PID: 7776)
- wscript.exe (PID: 7828)
- wscript.exe (PID: 7680)
- wscript.exe (PID: 7960)
- wscript.exe (PID: 7632)
- wscript.exe (PID: 7920)
- wscript.exe (PID: 7720)
- wscript.exe (PID: 7880)
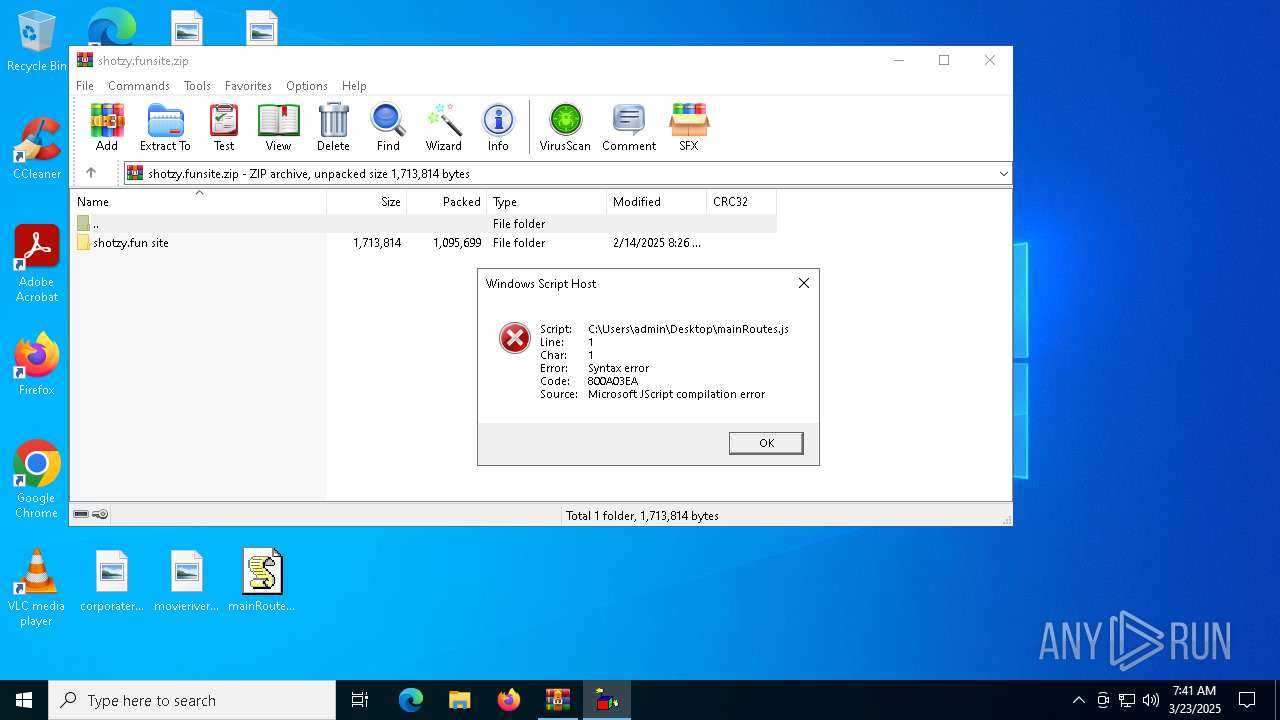
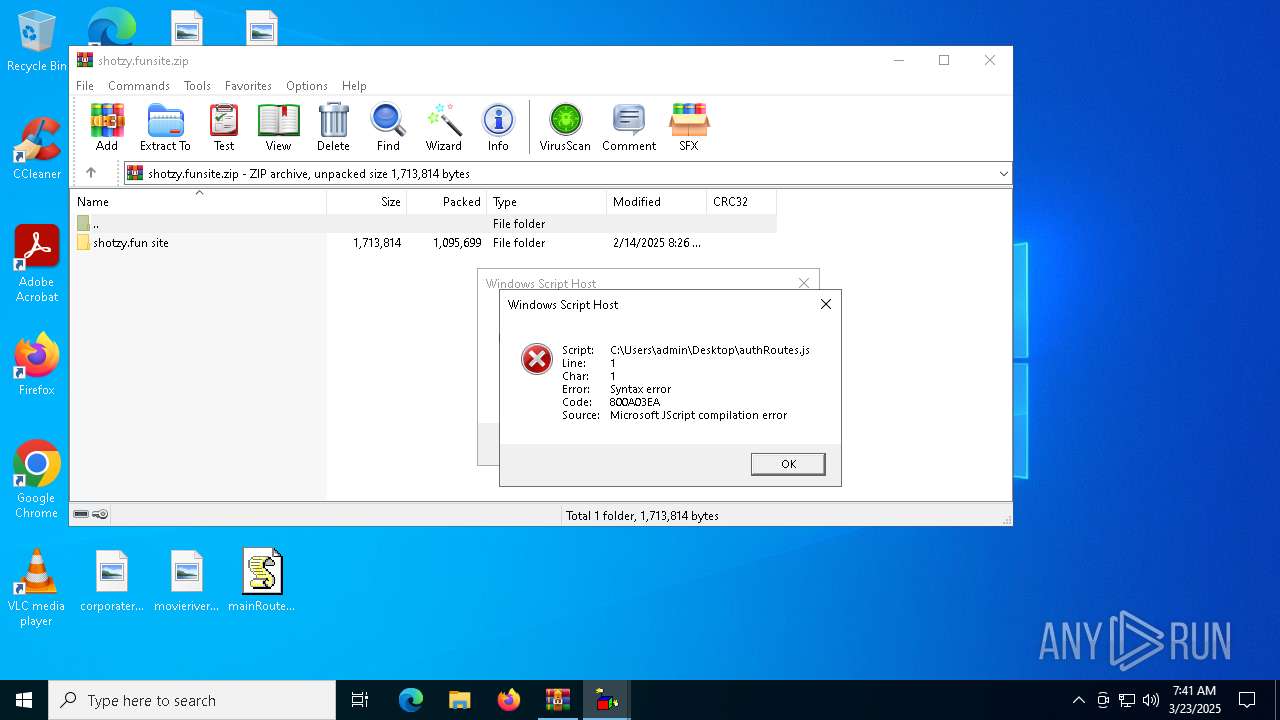
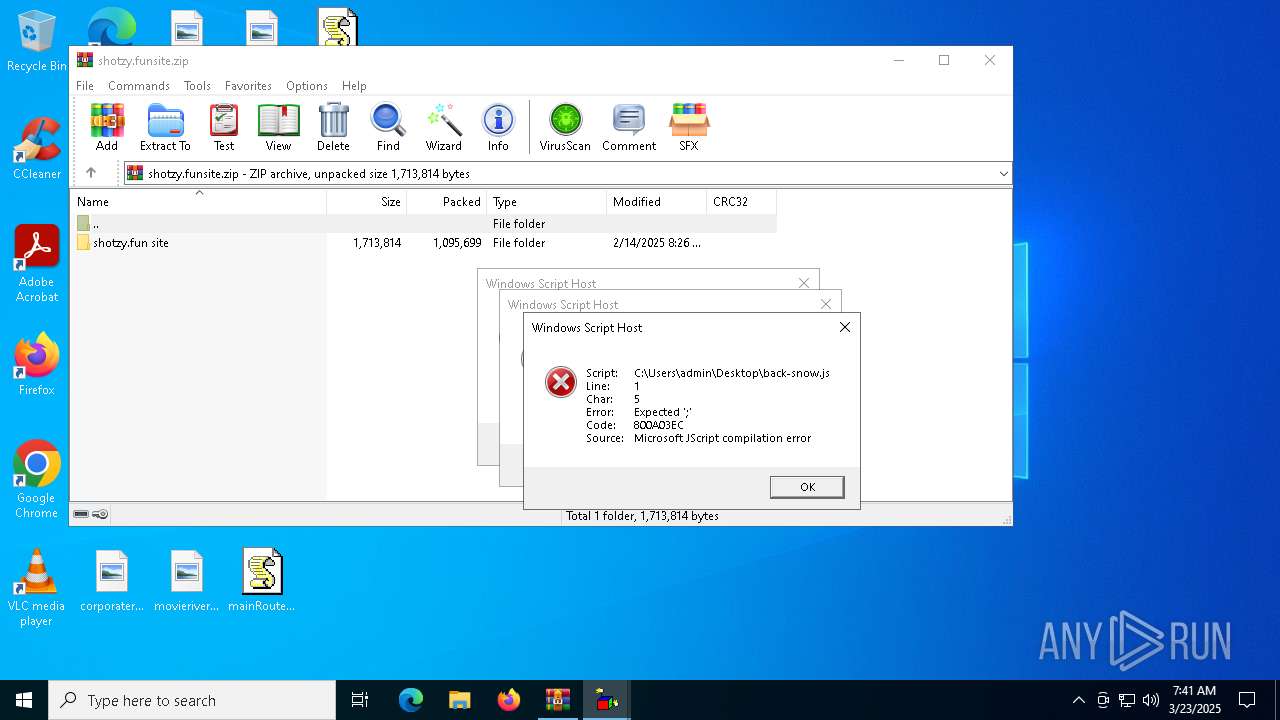
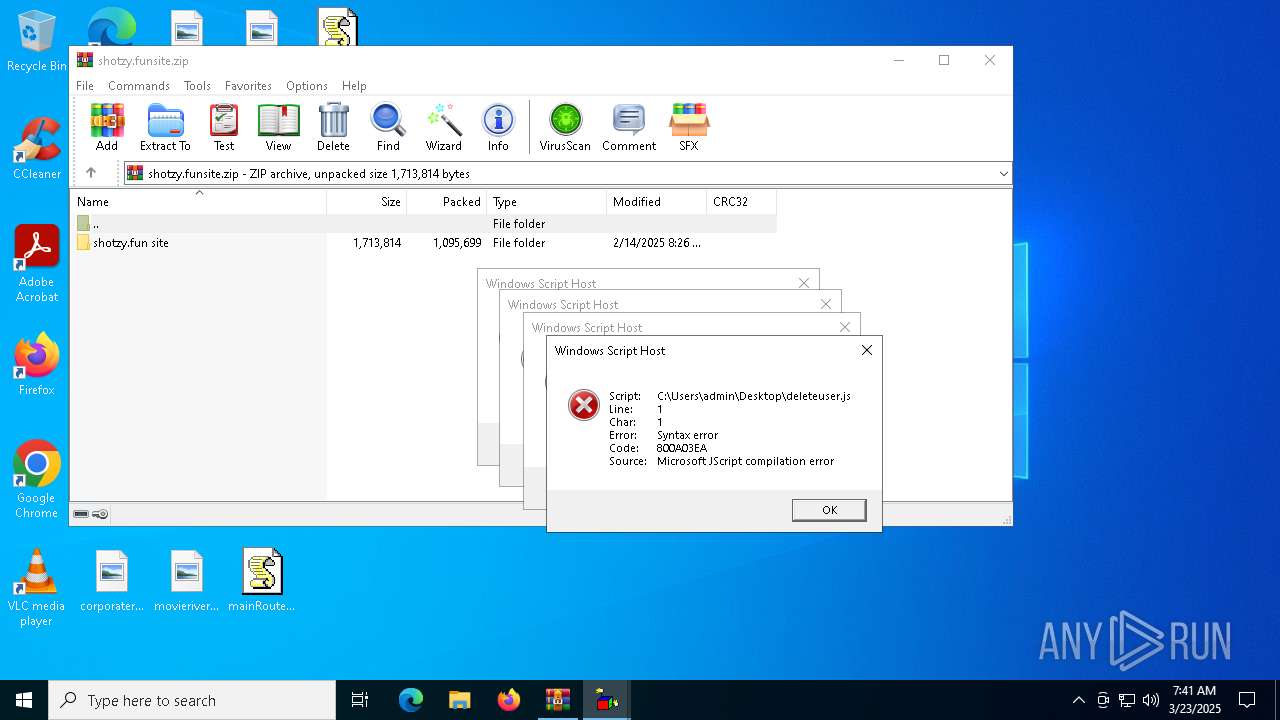
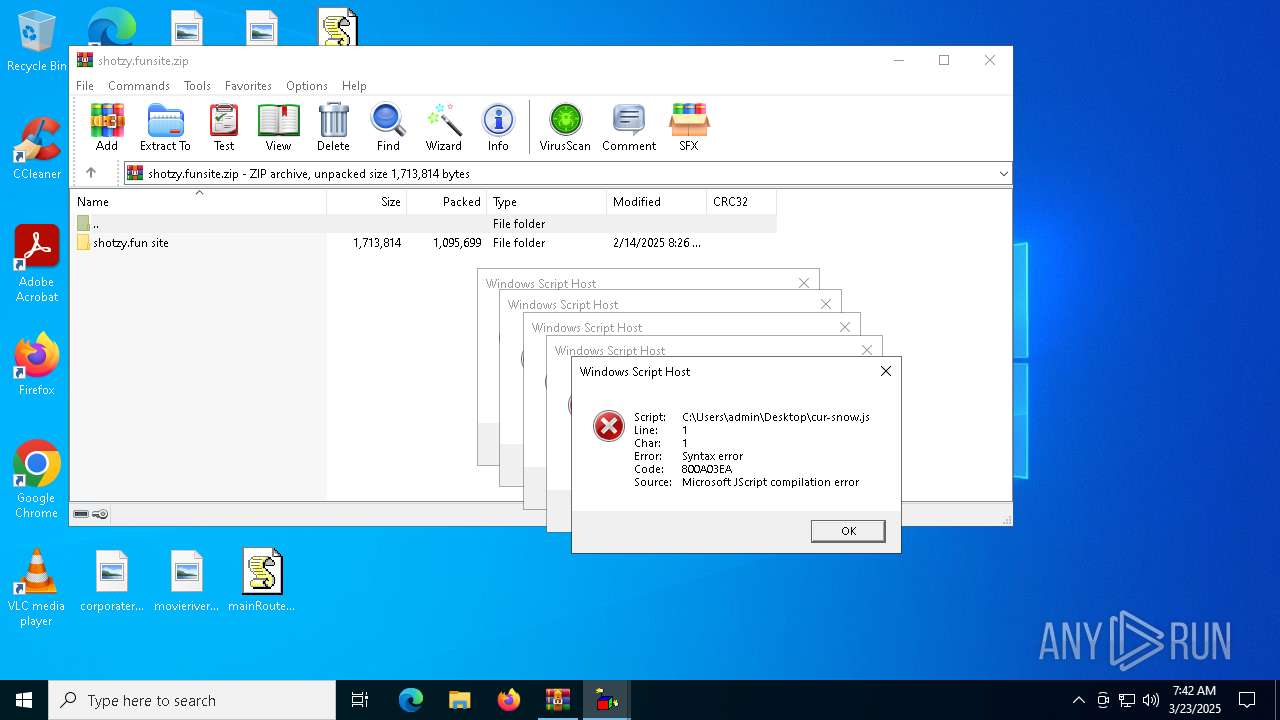
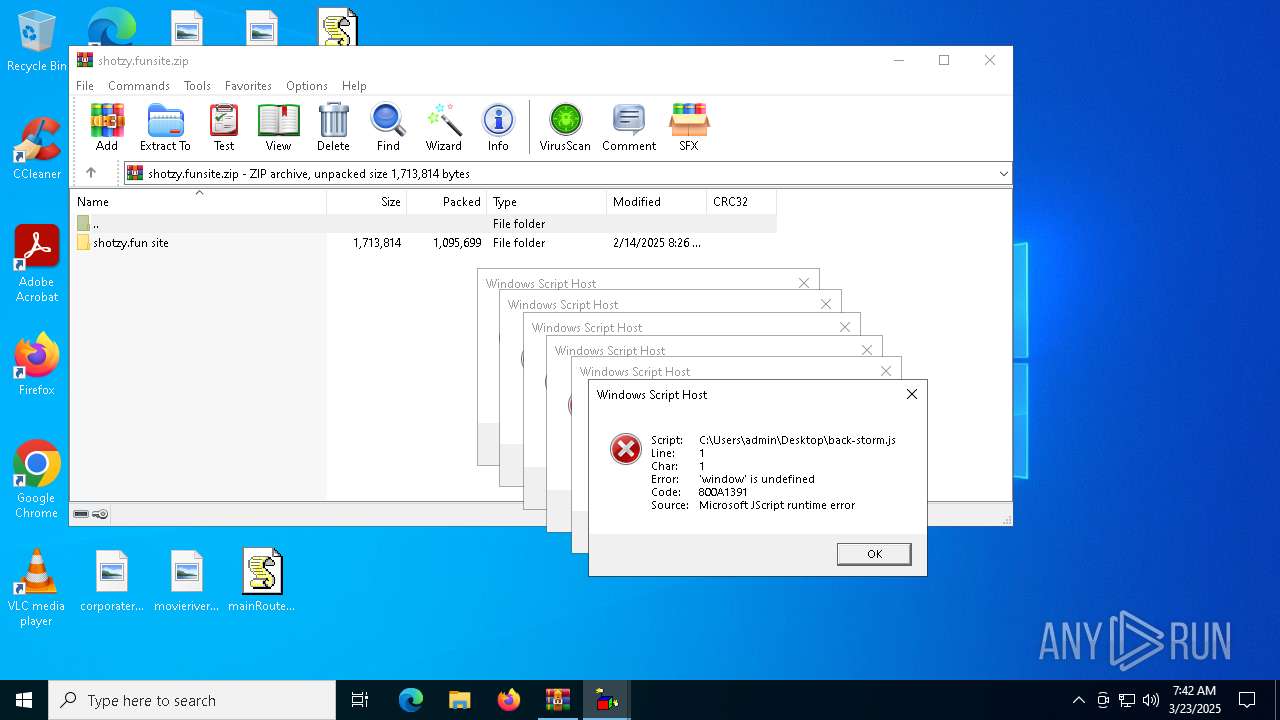
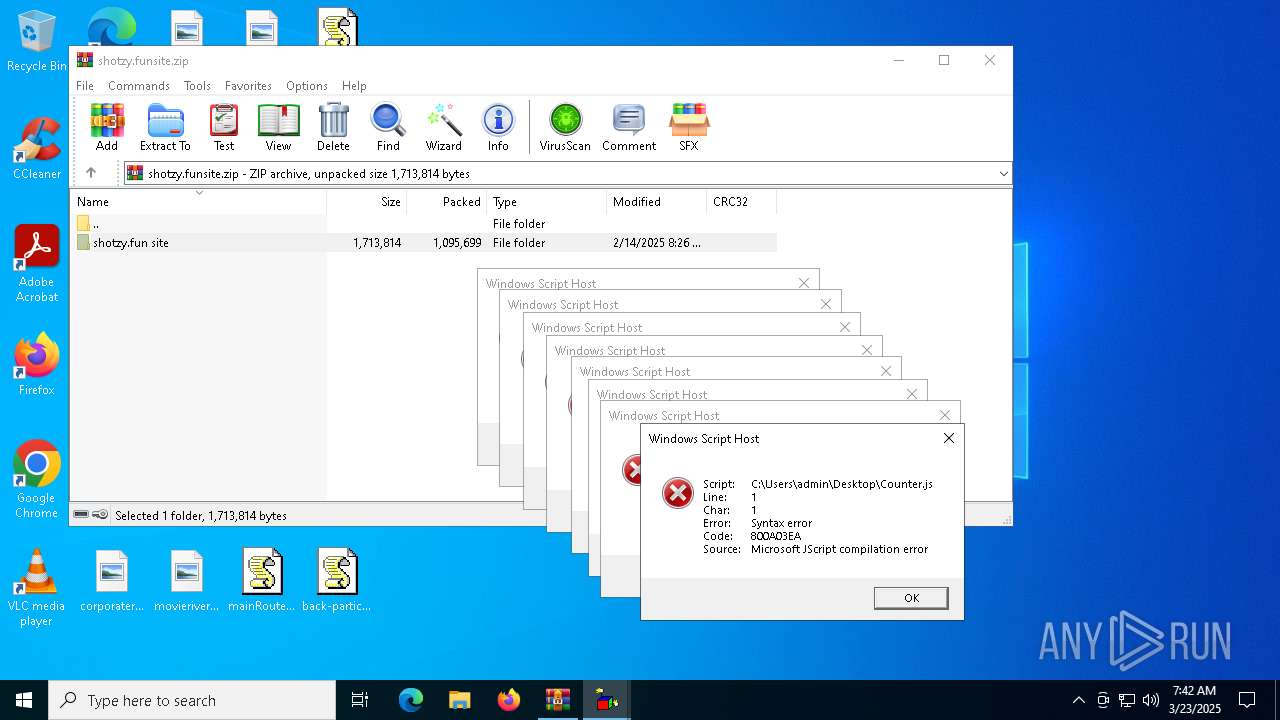
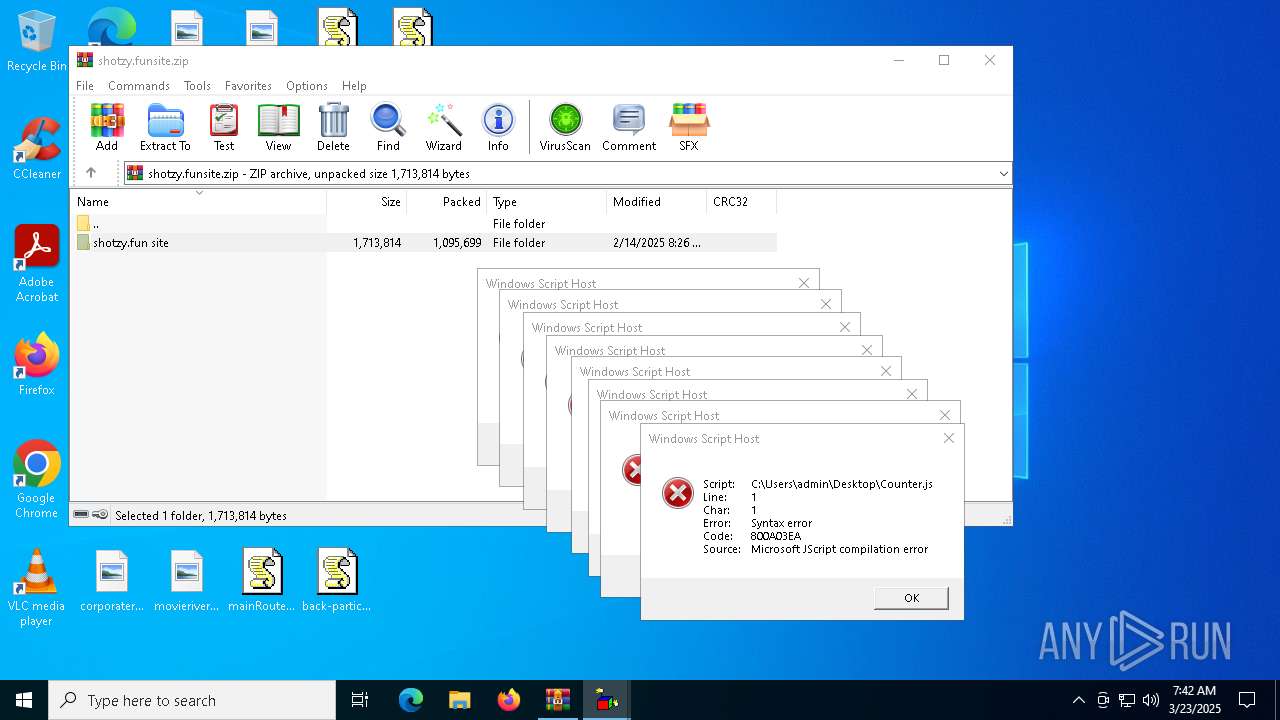
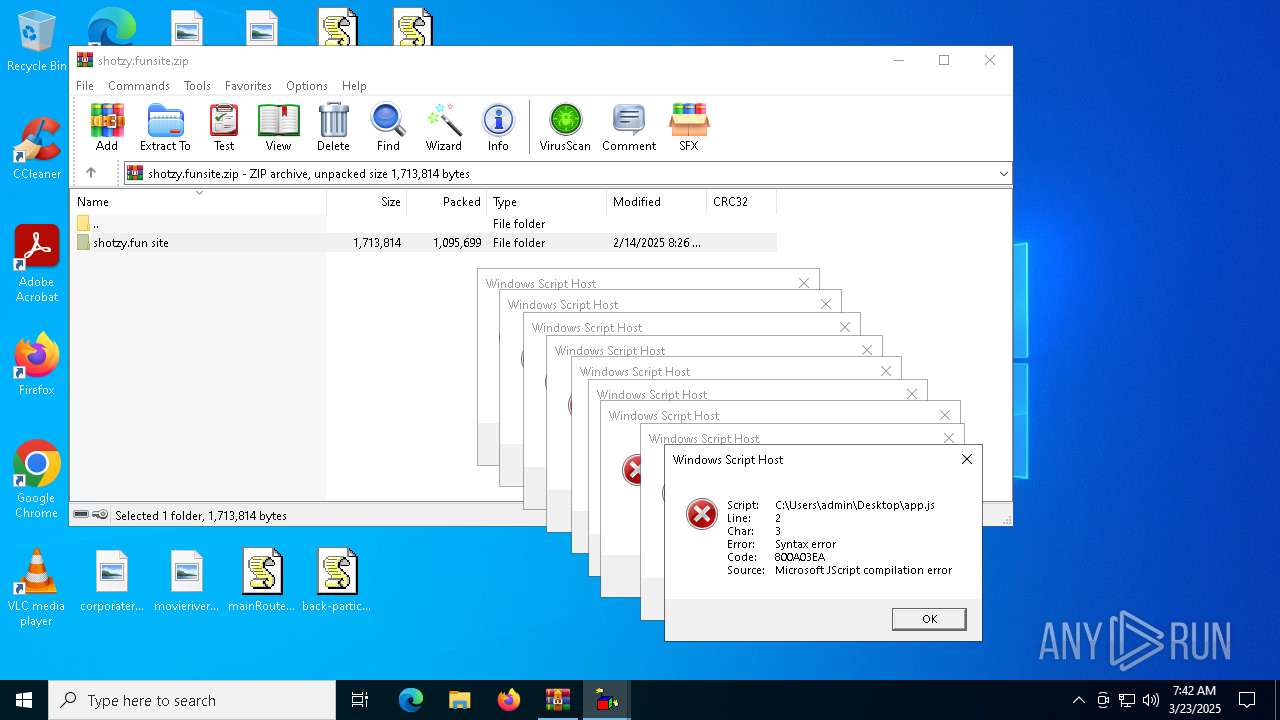
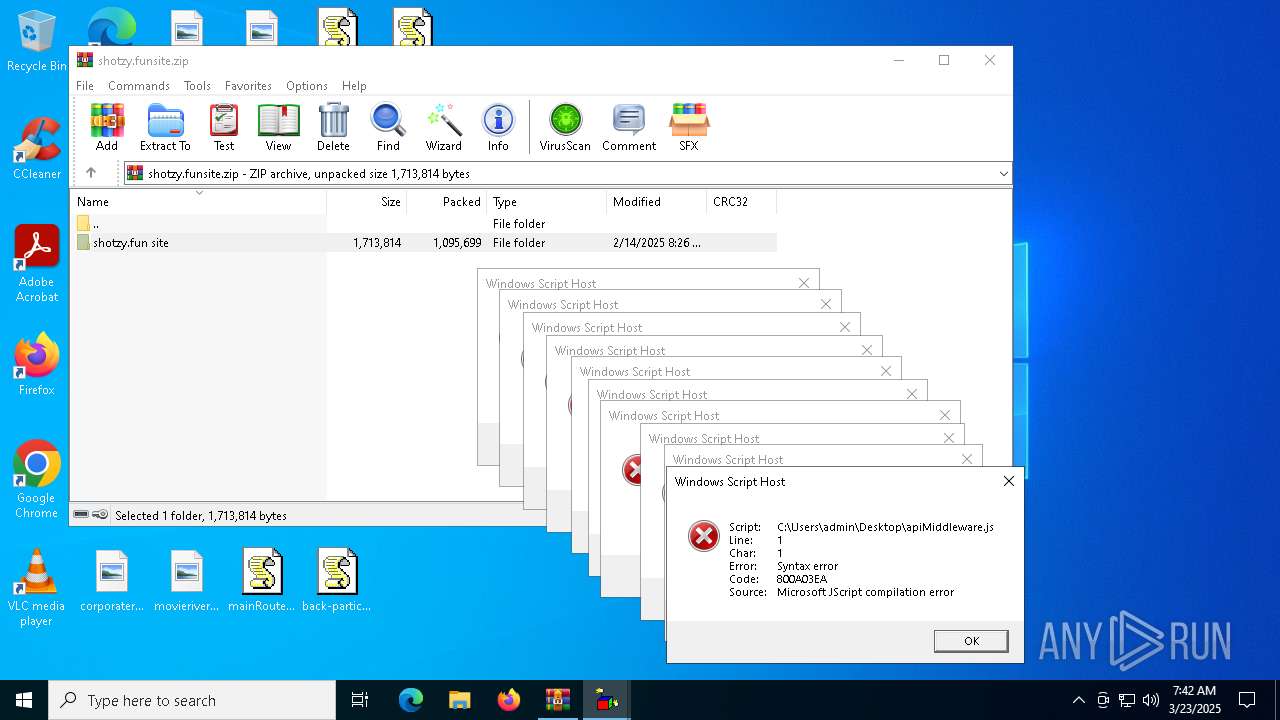
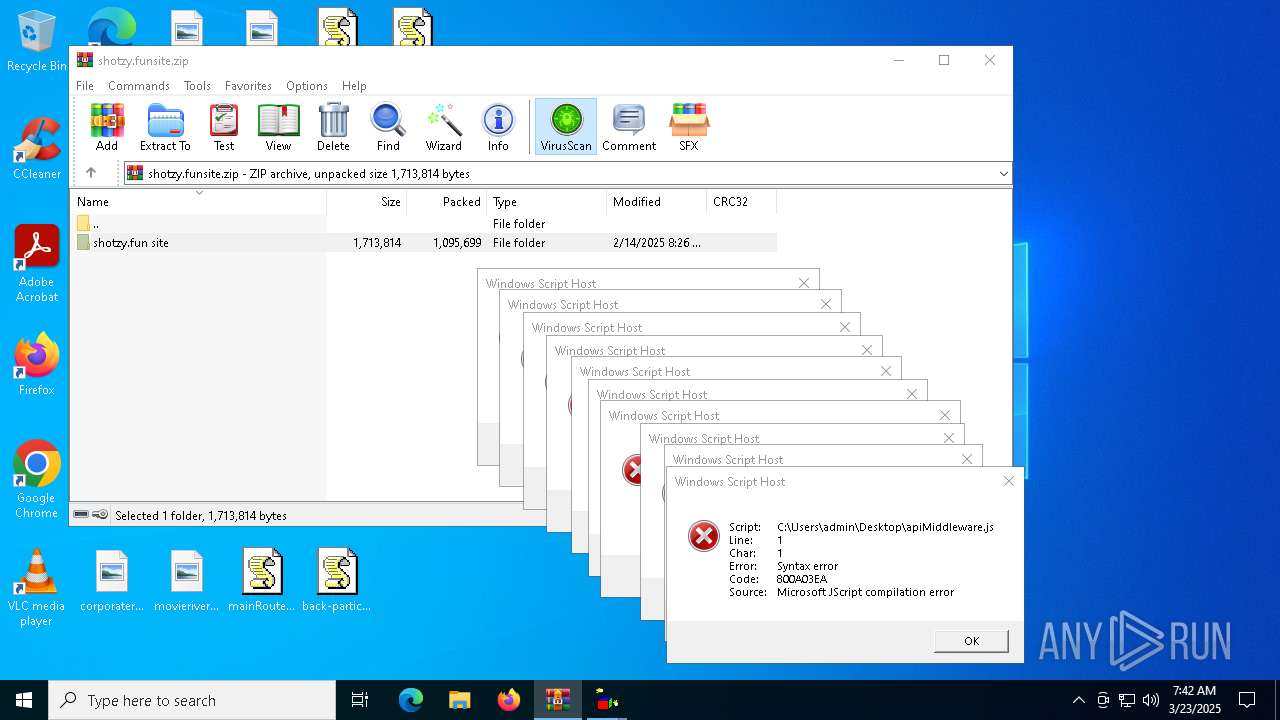
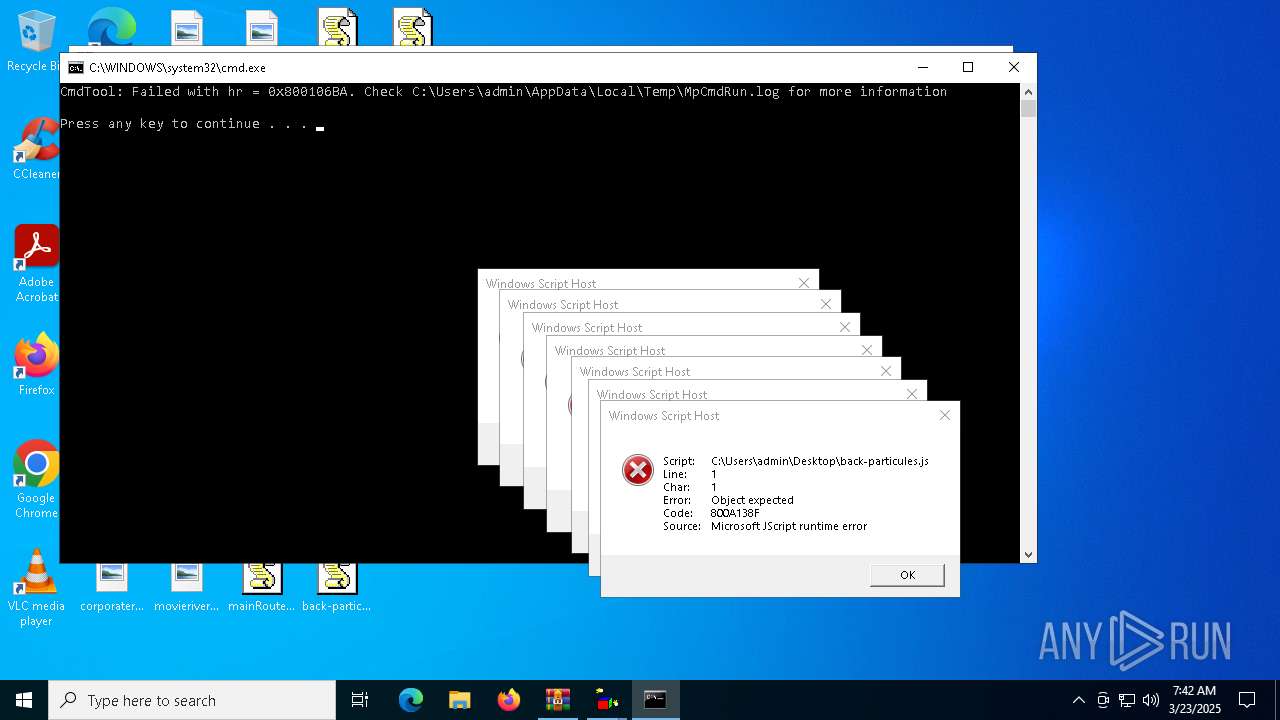
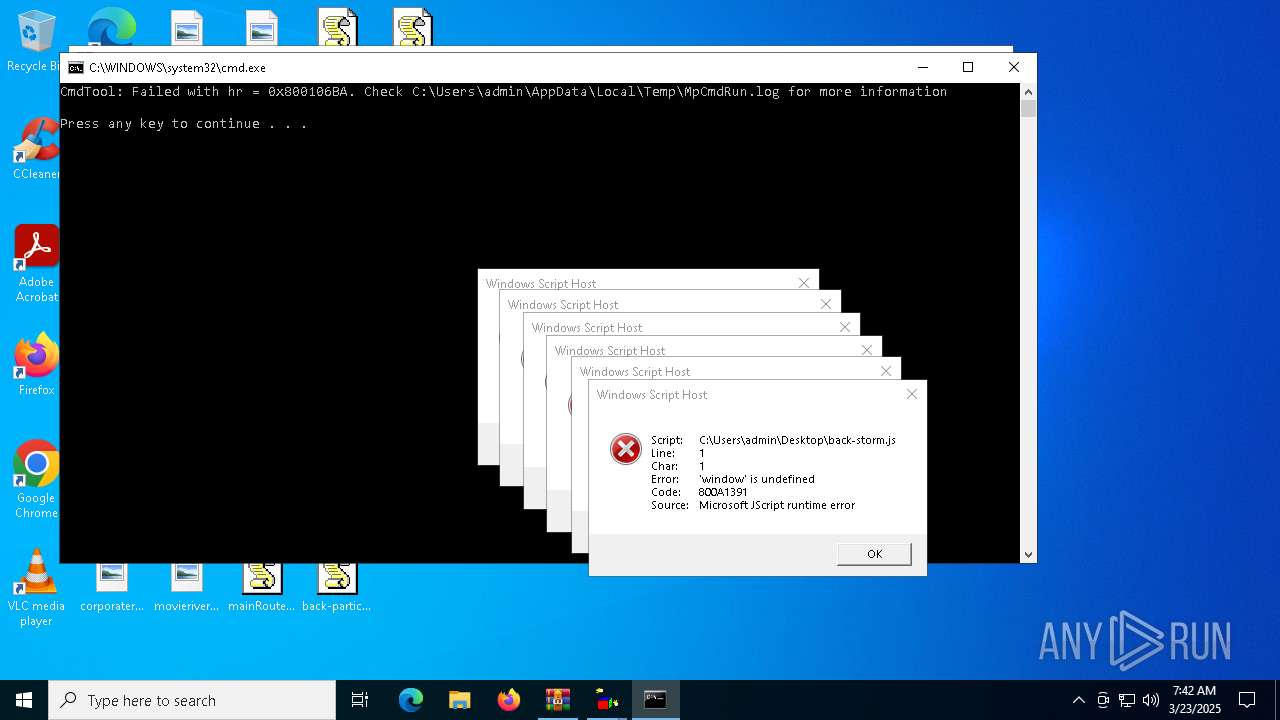
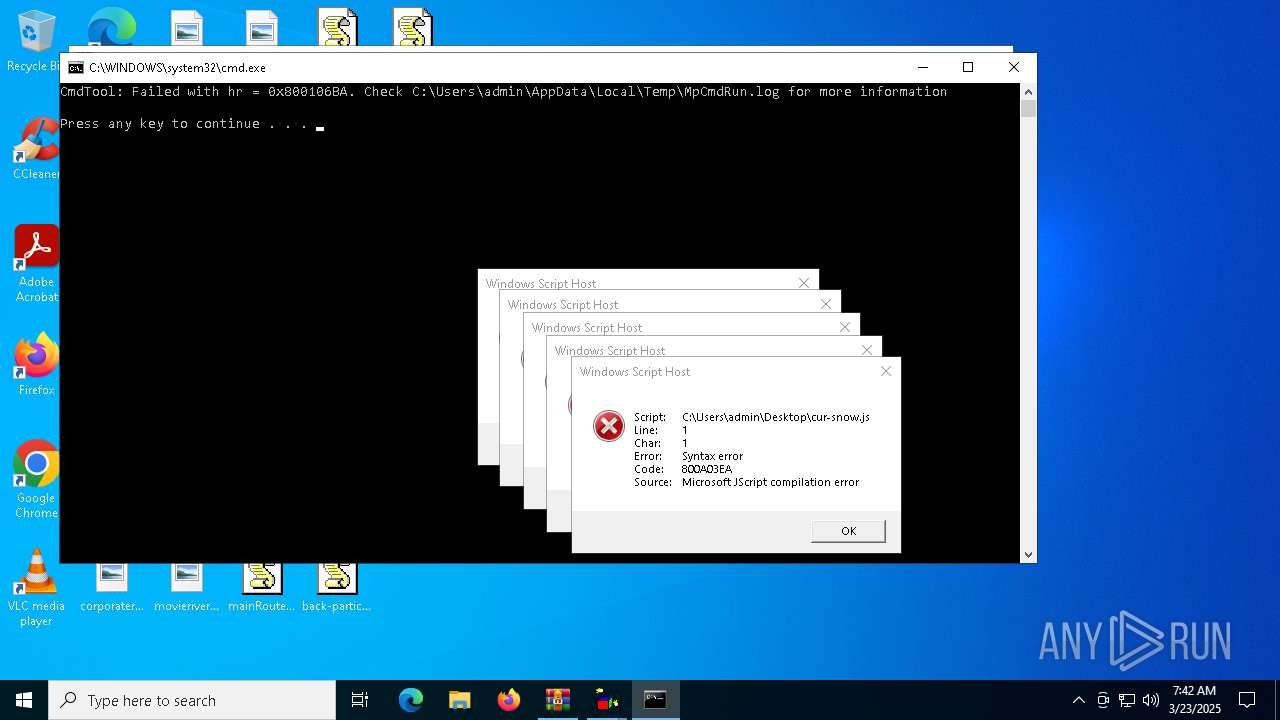
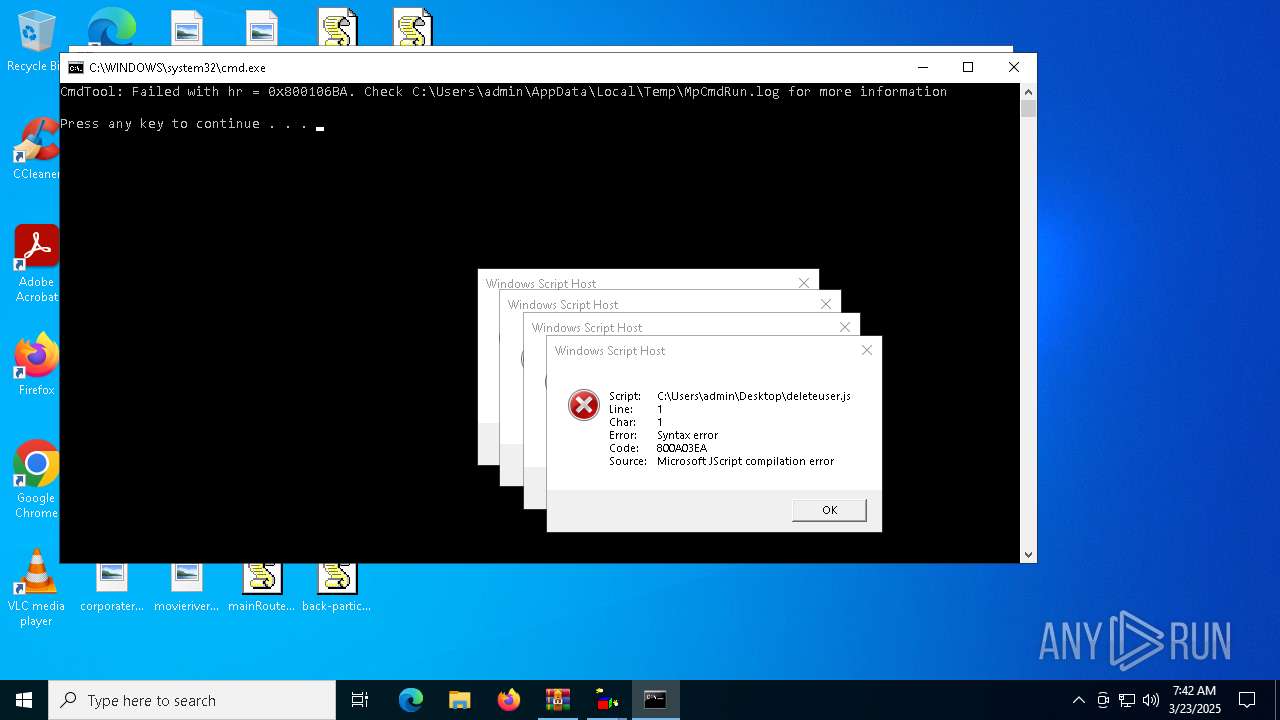
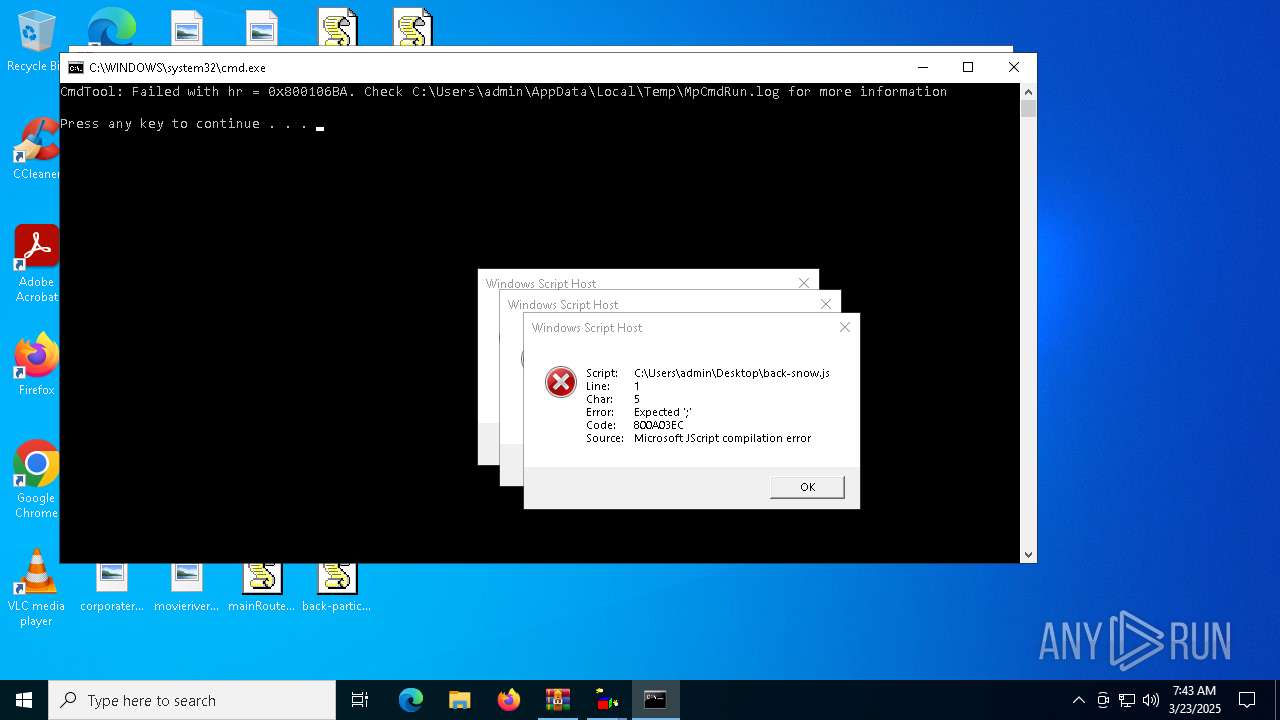
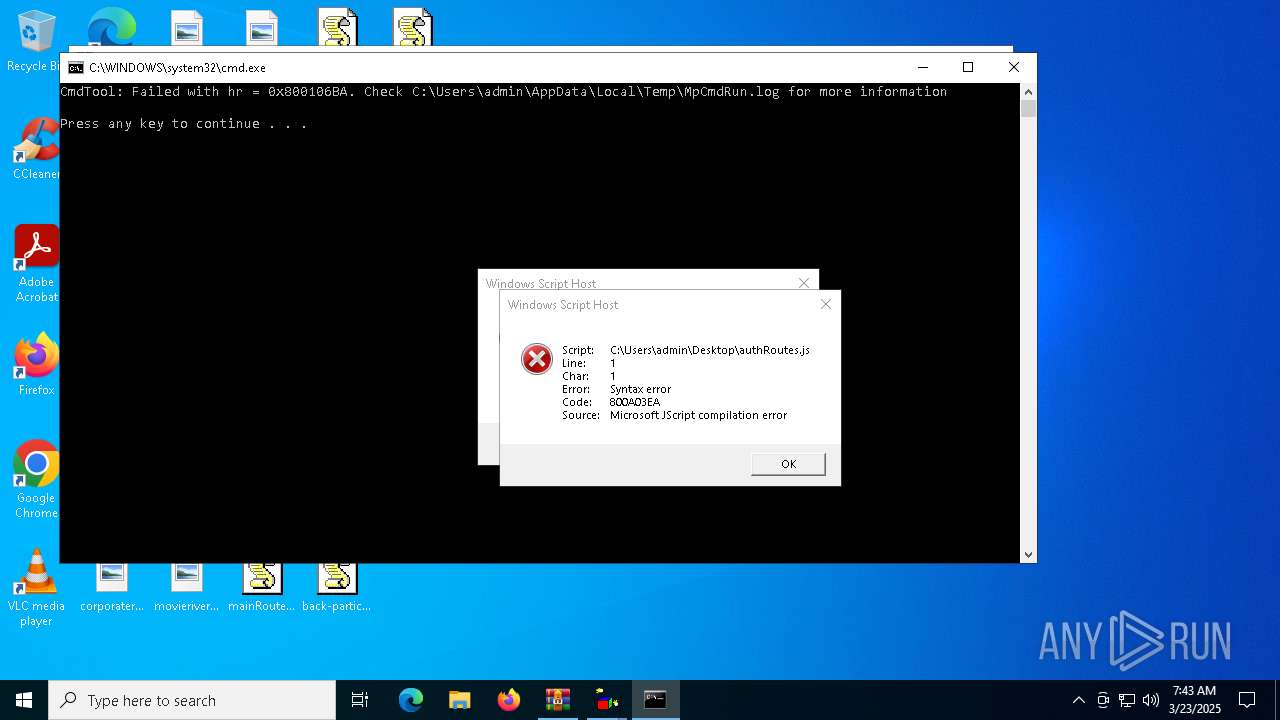
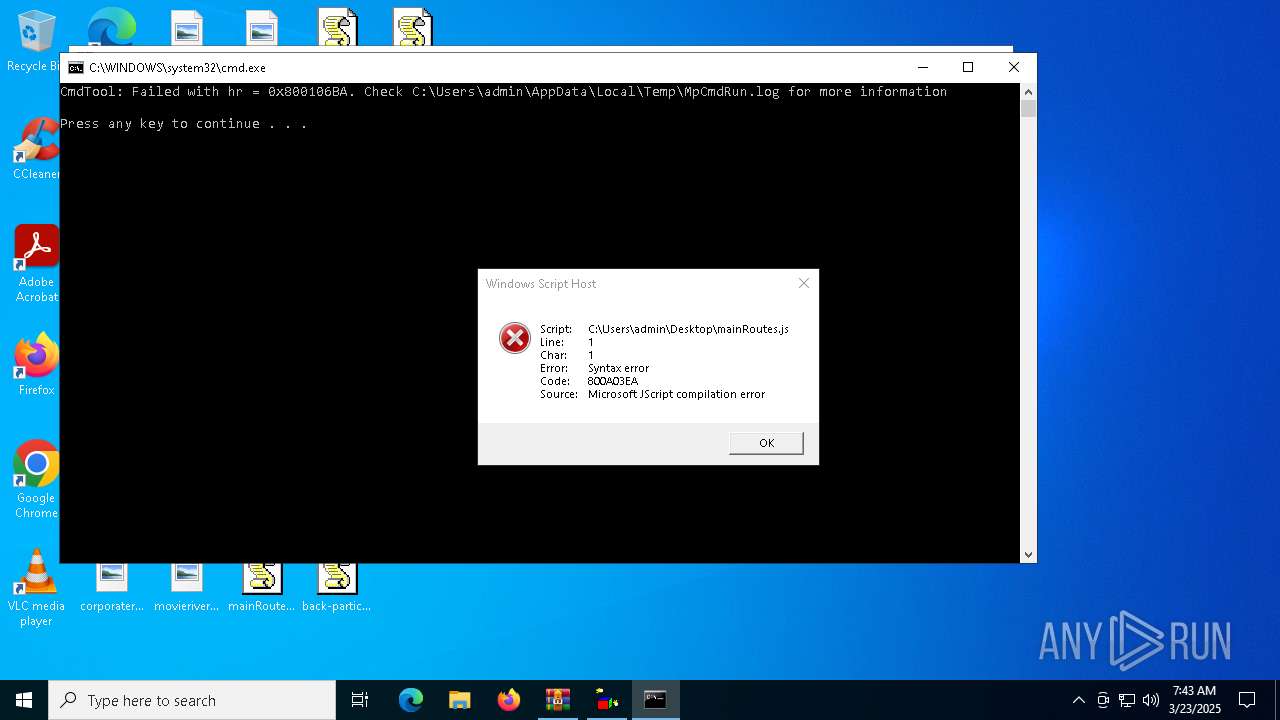
JScript runtime error (SCRIPT)
- wscript.exe (PID: 7776)
- wscript.exe (PID: 7828)
Checks proxy server information
- slui.exe (PID: 6476)
Reads the software policy settings
- slui.exe (PID: 6476)
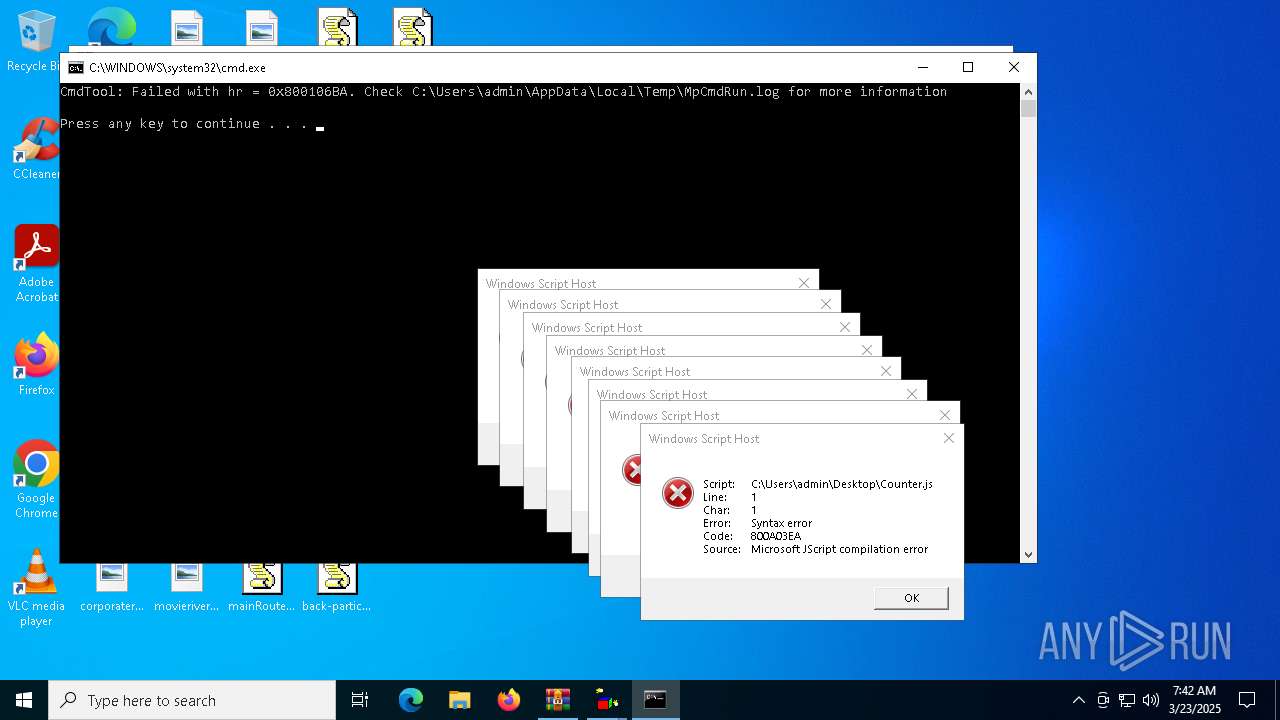
Create files in a temporary directory
- MpCmdRun.exe (PID: 4200)
Checks supported languages
- MpCmdRun.exe (PID: 4200)
Reads the computer name
- MpCmdRun.exe (PID: 4200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
ims-api
(PID) Process(7560) wscript.exe
Discord-Webhook-Tokens (1)1317569210360266862/KKWXoxBiJ1QMLTxPpHExbWMfSBc8HFeuhxuf5Xhtco24WcO_pEPAY12EadahmN8ZM-mH
Discord-Info-Links
1317569210360266862/KKWXoxBiJ1QMLTxPpHExbWMfSBc8HFeuhxuf5Xhtco24WcO_pEPAY12EadahmN8ZM-mH
Get Webhook Infohttps://discord.com/api/webhooks/1317569210360266862/KKWXoxBiJ1QMLTxPpHExbWMfSBc8HFeuhxuf5Xhtco24WcO_pEPAY12EadahmN8ZM-mH
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:02:14 21:26:02 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | shotzy.fun site/ |
Total processes
136
Monitored processes
15
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4200 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5332 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6476 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7328 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\shotzy.funsite.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 7452 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\mainRoutes.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7560 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\authRoutes.js | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
ims-api(PID) Process(7560) wscript.exe Discord-Webhook-Tokens (1)1317569210360266862/KKWXoxBiJ1QMLTxPpHExbWMfSBc8HFeuhxuf5Xhtco24WcO_pEPAY12EadahmN8ZM-mH Discord-Info-Links 1317569210360266862/KKWXoxBiJ1QMLTxPpHExbWMfSBc8HFeuhxuf5Xhtco24WcO_pEPAY12EadahmN8ZM-mH Get Webhook Infohttps://discord.com/api/webhooks/1317569210360266862/KKWXoxBiJ1QMLTxPpHExbWMfSBc8HFeuhxuf5Xhtco24WcO_pEPAY12EadahmN8ZM-mH | |||||||||||||||
| 7632 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\back-snow.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7680 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\deleteuser.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7720 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\cur-snow.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 7776 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\back-storm.js | C:\Windows\System32\wscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
6 215
Read events
6 203
Write events
12
Delete events
0
Modification events
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\shotzy.funsite.zip | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
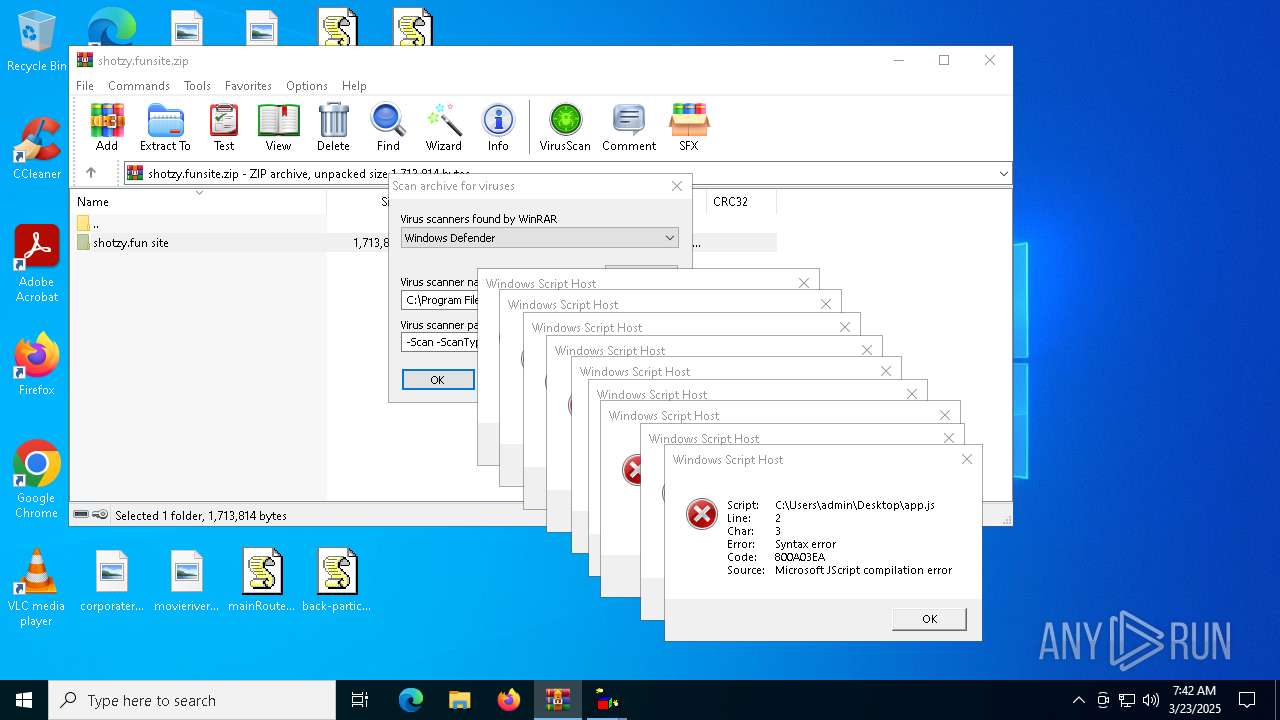
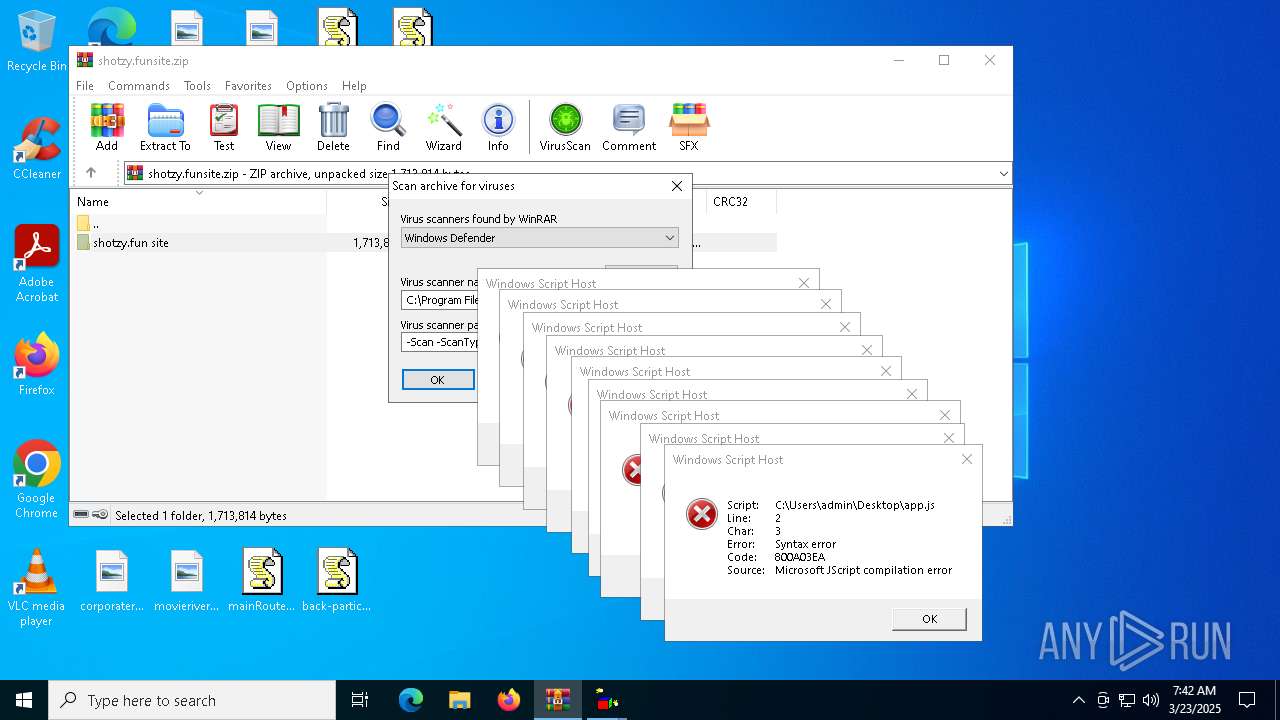
| (PID) Process: | (7328) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
0
Suspicious files
15
Text files
36
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\package-lock.json | — | |
MD5:— | SHA256:— | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\middlewares\apiMiddleware.js | binary | |
MD5:700E267EB8BCFA69C152A6B4D8C64B69 | SHA256:26335E97B38B0501F24C5781E0A612922717B89A6E3F19FF4129B7A4EF856E9D | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\controllers\authController.js | binary | |
MD5:62247345423B7829ED034B45293D631C | SHA256:6B4C4D4FC878D75EA590AF5C0BBEA713B8BC3CEC2234DE8A009A137DB84AA4EA | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\models\Counter.js | binary | |
MD5:560DD1A6A04B8595B02FE403B0856926 | SHA256:056F5E1139D3B806BC01D5EE0C489E9BF725F38249CD1499A61DBFA49EF0319B | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\controllers\mainController.js | binary | |
MD5:D9C5E60FEFBD70EC7CDF49A1AA497E12 | SHA256:87FC0257238085F8DDA602AE856172871E831EBB88163926D3DF6073DB260897 | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\models\ApiKey.js | binary | |
MD5:959A0DC4F40D65236D5E5C40F2C3B31C | SHA256:C1FC8E27D0D3564560084172F7F003FB18DAC3C73FB8CEA07A41159A1C221077 | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\package.json | binary | |
MD5:54CF4F53EFA0E65C4810D2D85F175C04 | SHA256:0CB16B2C7A93795F3FF321BA2CDCA4CF5A717407A7A301F444559C184A3E0132 | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\.env | text | |
MD5:1AD1CFBAA83AA17EE94E08D385B7127B | SHA256:889E2B0E65AEEB450FC139BA3620F3EE028D9184BE4DB1E80D2CCEAD0145515A | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\public\css\account.css | text | |
MD5:45E71A97FABC23EA1CD919351AD082A9 | SHA256:7FF9FFC99906AB1A95F8C204E9F1A436943F35DE7511CFD4174F162899CD2F52 | |||
| 7328 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR7328.6015\shotzy.funsite.zip\shotzy.fun site\public\img\featured-bio-banner.png | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
21
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7176 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6476 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |