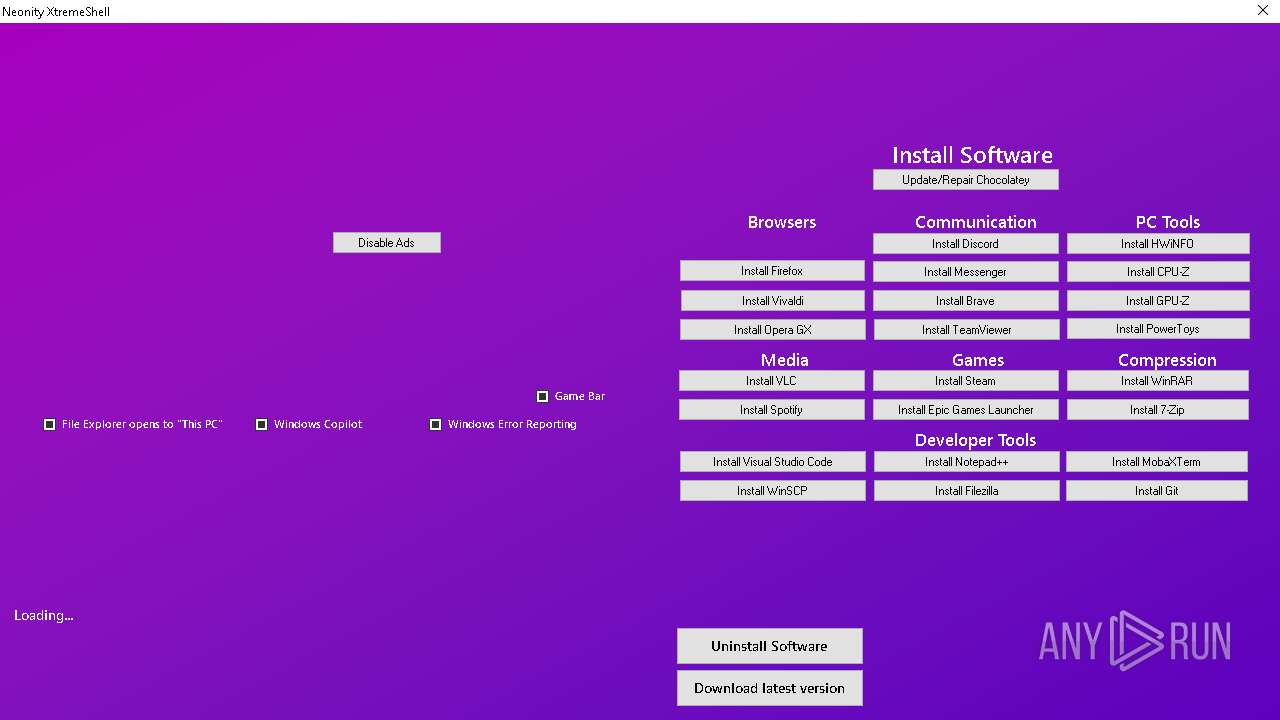
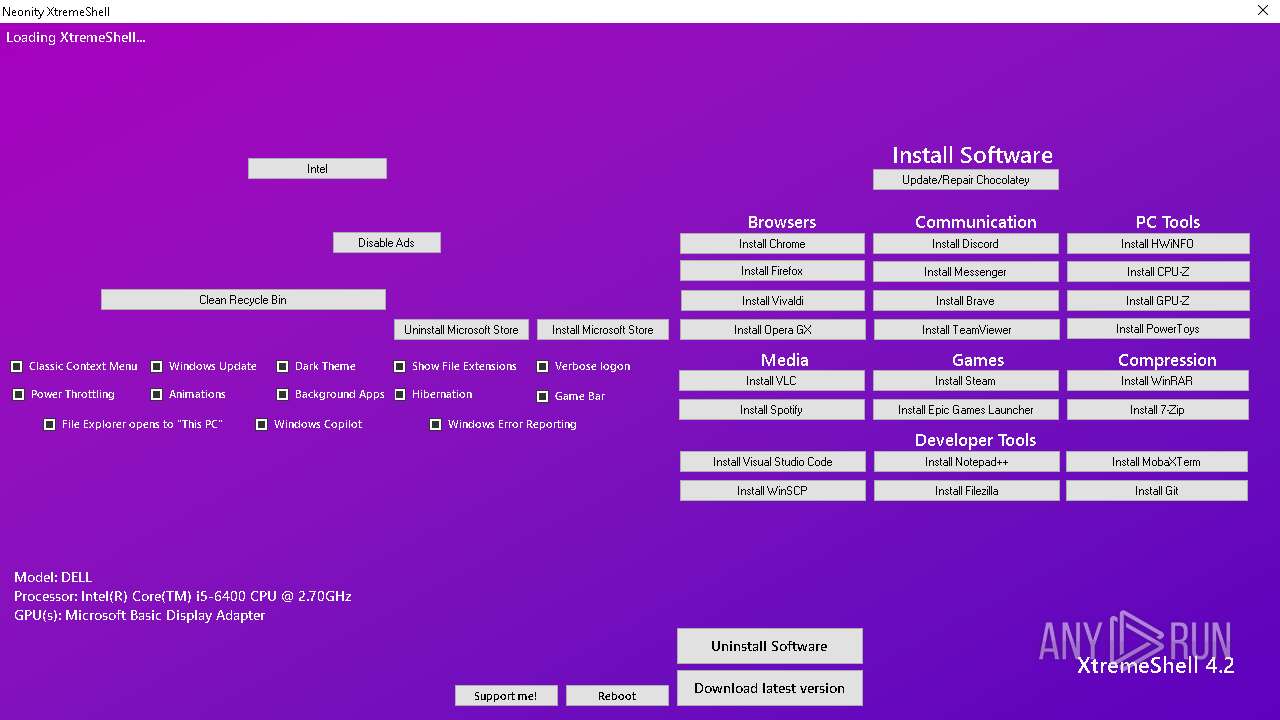
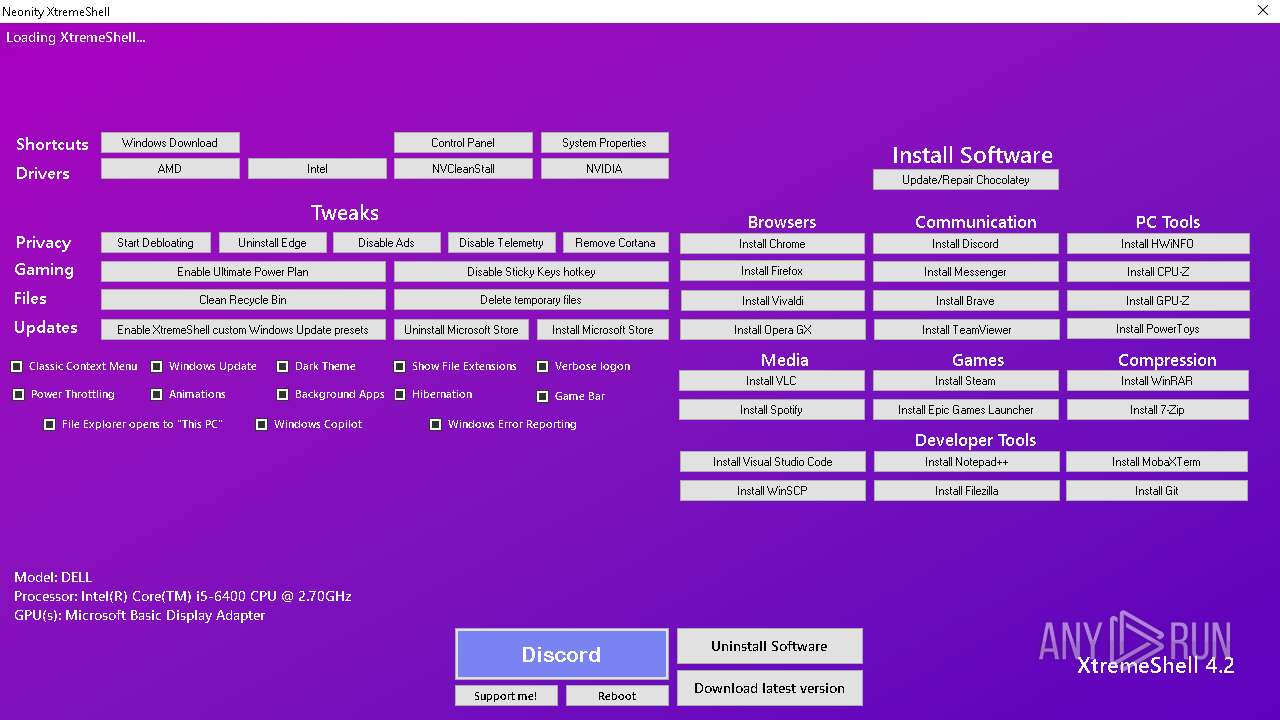
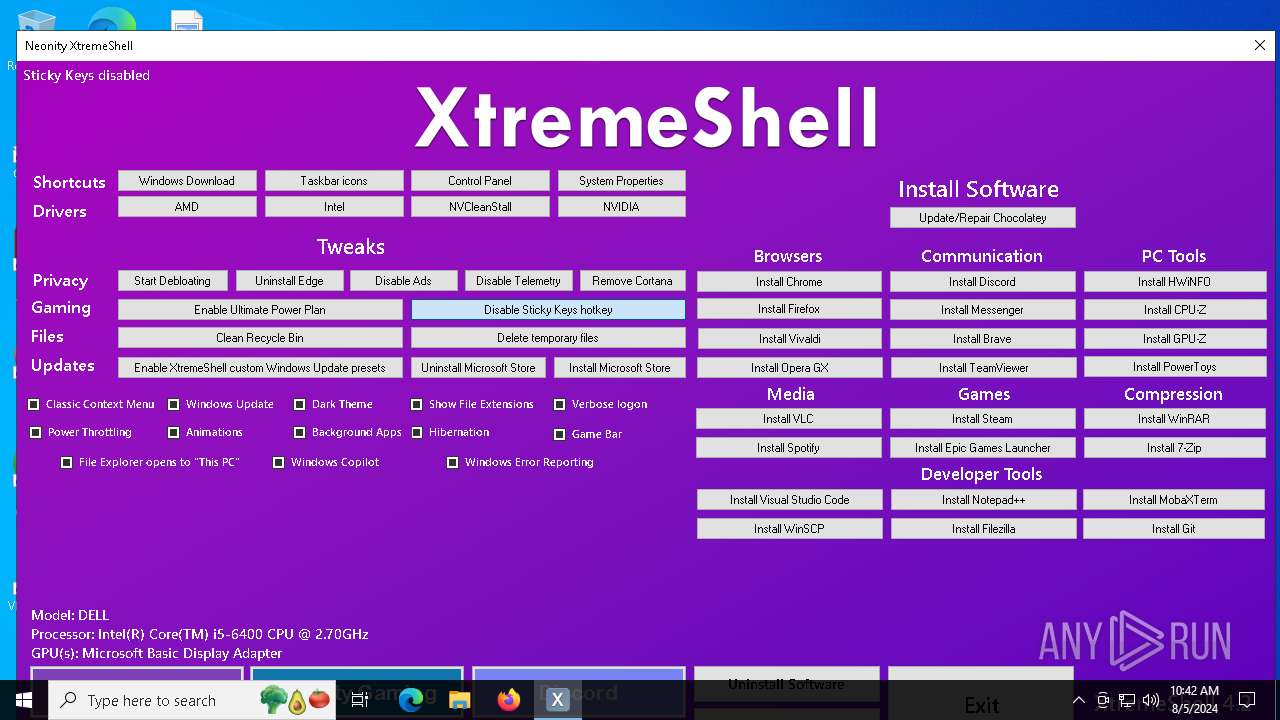
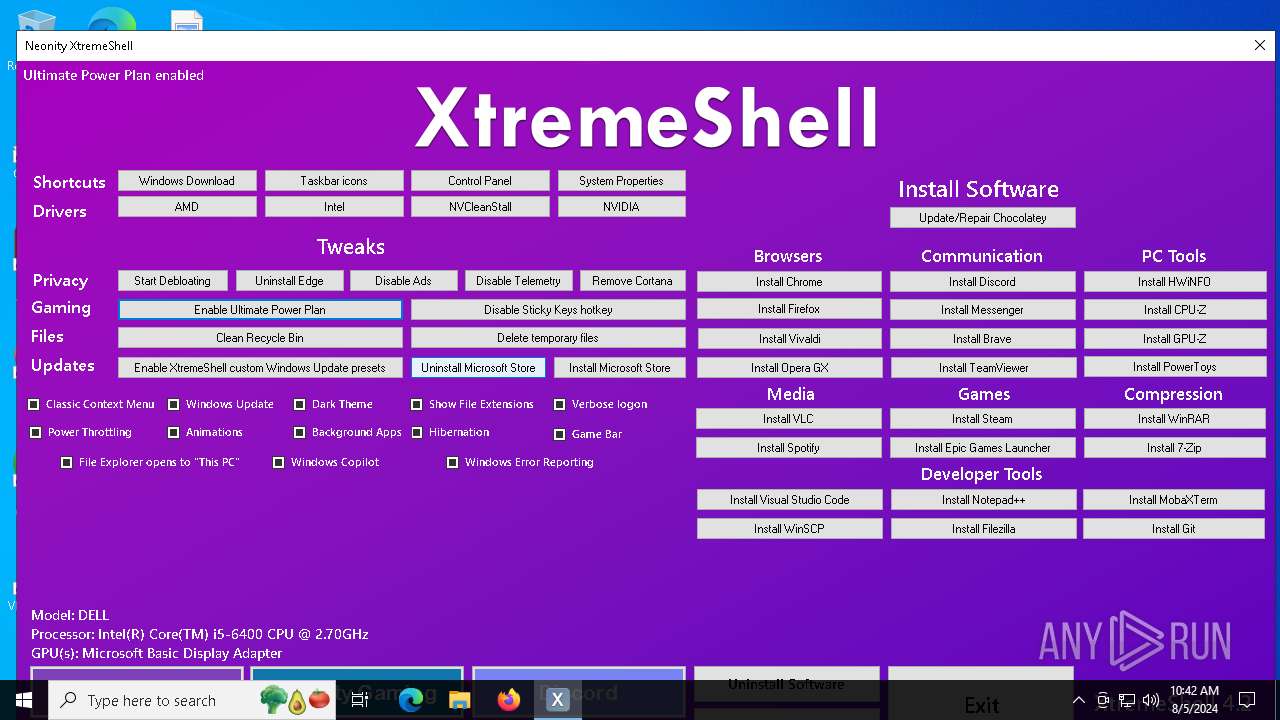
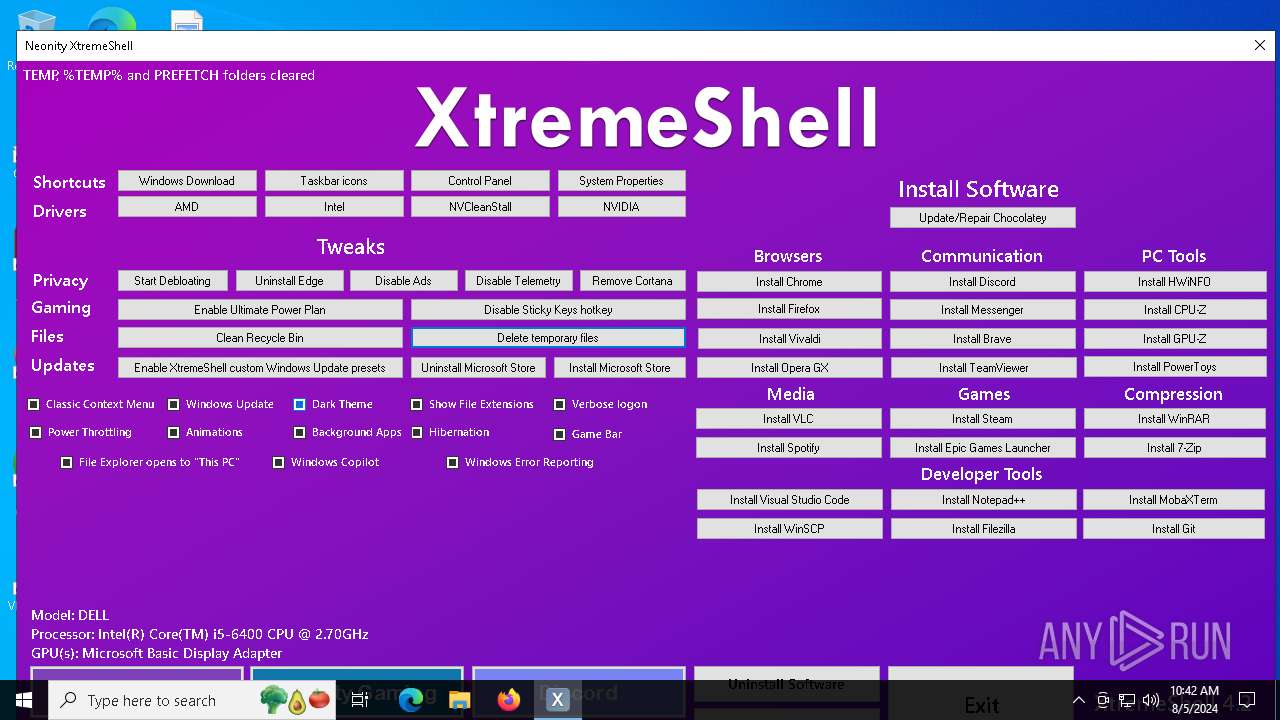
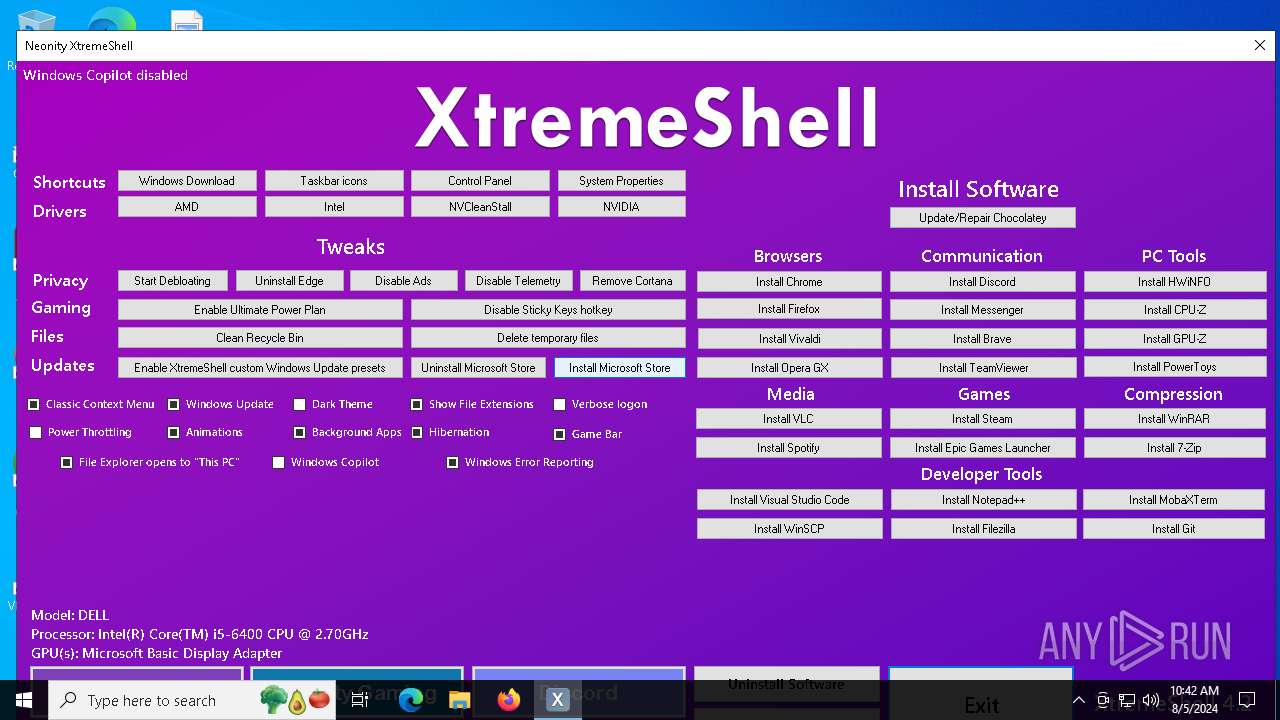
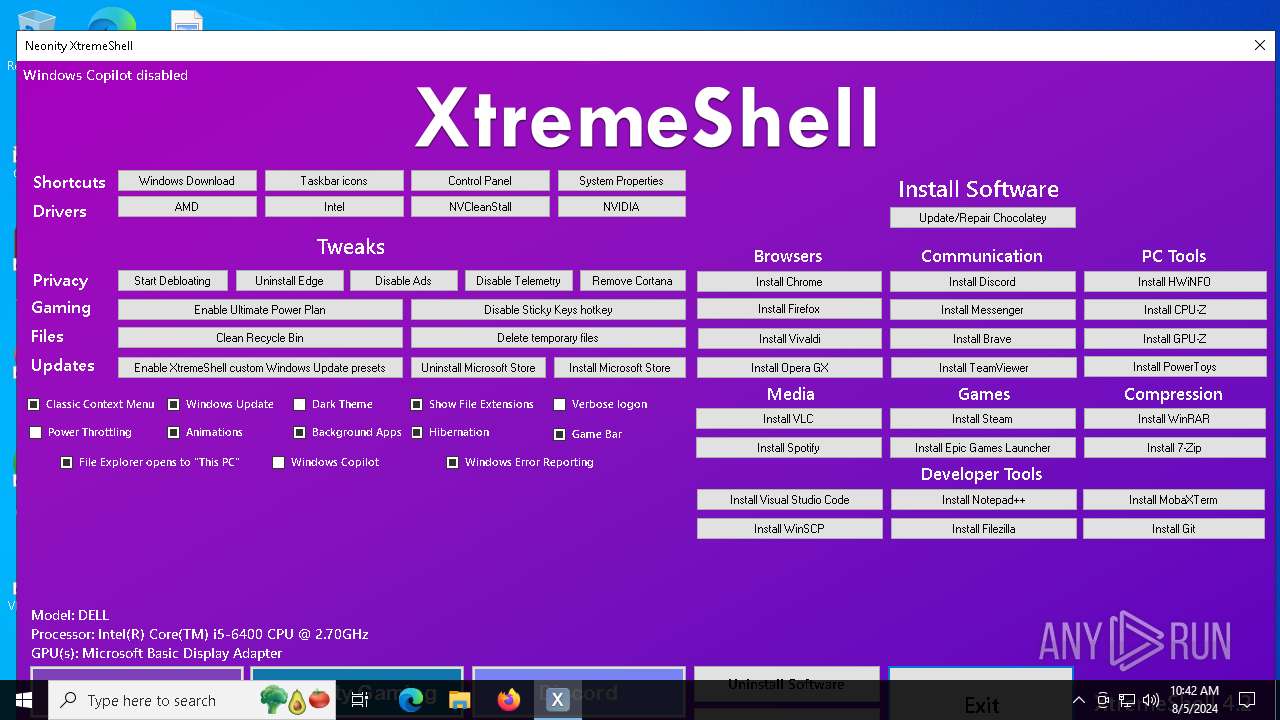
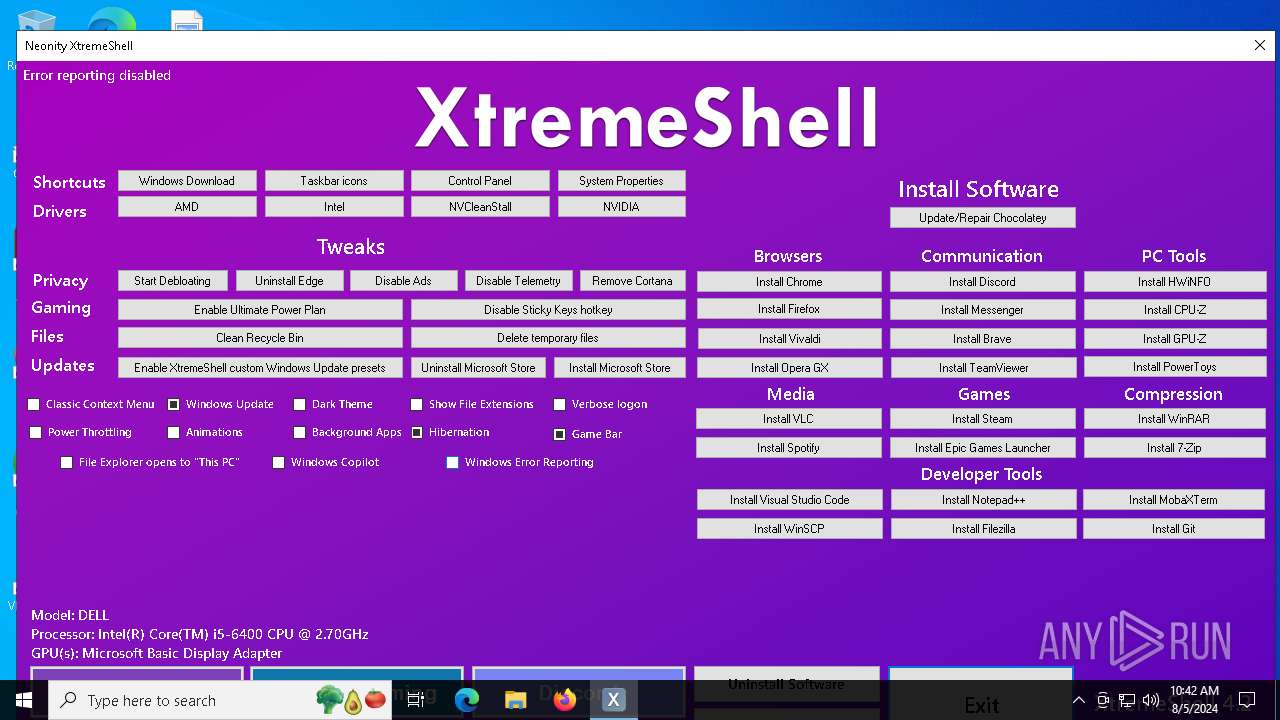
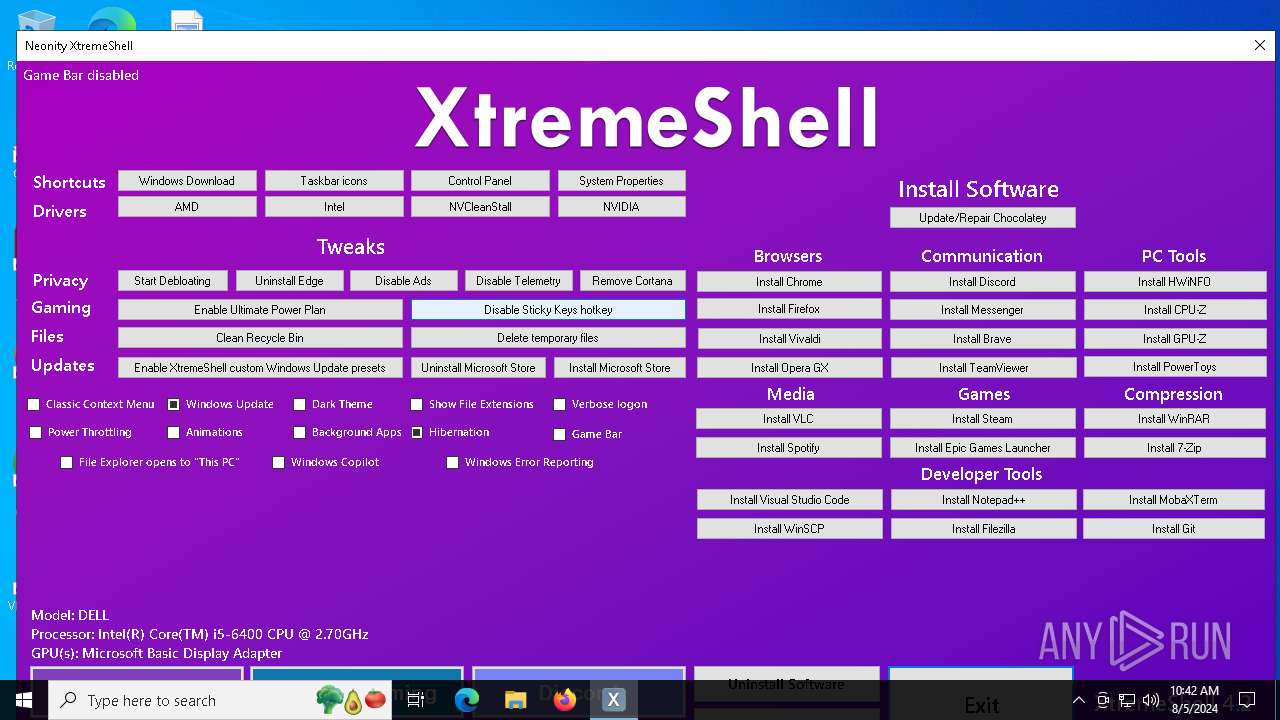
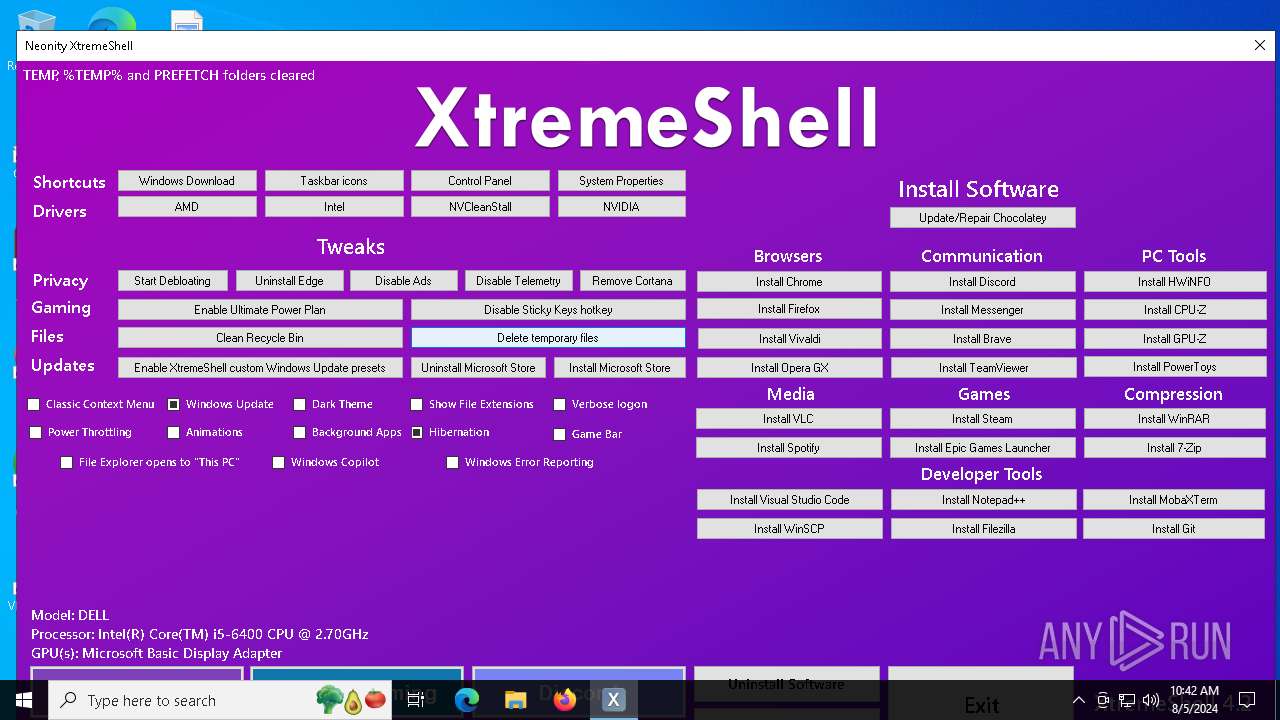
| File name: | XtremeShell.exe |
| Full analysis: | https://app.any.run/tasks/abc688c7-1f5b-49f7-895c-3e161bfc7bef |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2024, 10:41:25 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows |
| MD5: | 11F423BE9EED32E54700A19CCBFE72AE |
| SHA1: | 92FEC23E2ECD30FBDD38E52049E49439B6E63A1C |
| SHA256: | A0498C8372D9E0D1825F547FBDA4F8B7438C57F9139CC49314DE19E37F1A7A57 |
| SSDEEP: | 6144:N9idl3RwOLlQqH/vyomvclsA5Szl1MLewEEq8/Wfboi2Y8DYV6xWxWWi50NsRRjZ:4QRom5t4U+JTAKWF/chHToACQ |
MALICIOUS
Dynamically loads an assembly (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Downloads the requested resource (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Drops the executable file immediately after the start
- XtremeShell.exe (PID: 2080)
- csc.exe (PID: 7220)
Changes Windows Error Reporting flag
- reg.exe (PID: 8048)
SUSPICIOUS
Reads security settings of Internet Explorer
- XtremeShell.exe (PID: 2080)
- DismHost.exe (PID: 2636)
- DismHost.exe (PID: 6160)
- StartMenuExperienceHost.exe (PID: 2044)
Uses base64 encoding (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Gets or sets the security protocol (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Checks Windows Trust Settings
- XtremeShell.exe (PID: 2080)
Uses sleep to delay execution (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Extracts files to a directory (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Gets file extension (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Drops 7-zip archiver for unpacking
- XtremeShell.exe (PID: 2080)
Gets path to any of the special folders (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Creates a directory (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Process drops legitimate windows executable
- XtremeShell.exe (PID: 2080)
Detected use of alternative data streams (AltDS)
- XtremeShell.exe (PID: 2080)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 2396)
- DismHost.exe (PID: 5904)
- DismHost.exe (PID: 6160)
- DismHost.exe (PID: 2636)
Executable content was dropped or overwritten
- XtremeShell.exe (PID: 2080)
- csc.exe (PID: 7220)
The process creates files with name similar to system file names
- XtremeShell.exe (PID: 2080)
Uses REG/REGEDIT.EXE to modify registry
- XtremeShell.exe (PID: 2080)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 2044)
- XtremeShell.exe (PID: 2080)
Uses powercfg.exe to modify the power settings
- XtremeShell.exe (PID: 2080)
Uses TASKKILL.EXE to kill process
- XtremeShell.exe (PID: 2080)
The process executes via Task Scheduler
- explorer.exe (PID: 6608)
INFO
Reads the computer name
- XtremeShell.exe (PID: 2080)
- choco.exe (PID: 6536)
- DismHost.exe (PID: 2396)
- DismHost.exe (PID: 2636)
- DismHost.exe (PID: 5904)
- DismHost.exe (PID: 6160)
- TextInputHost.exe (PID: 2464)
- StartMenuExperienceHost.exe (PID: 2044)
- SearchApp.exe (PID: 4056)
Create files in a temporary directory
- XtremeShell.exe (PID: 2080)
- csc.exe (PID: 7220)
- cvtres.exe (PID: 6160)
Checks supported languages
- XtremeShell.exe (PID: 2080)
- choco.exe (PID: 6536)
- DismHost.exe (PID: 2396)
- DismHost.exe (PID: 2636)
- DismHost.exe (PID: 5904)
- DismHost.exe (PID: 6160)
- csc.exe (PID: 7220)
- cvtres.exe (PID: 6160)
- TextInputHost.exe (PID: 2464)
- StartMenuExperienceHost.exe (PID: 2044)
- SearchApp.exe (PID: 4056)
Reads Environment values
- XtremeShell.exe (PID: 2080)
- DismHost.exe (PID: 2636)
- DismHost.exe (PID: 5904)
- DismHost.exe (PID: 6160)
- DismHost.exe (PID: 2396)
- SearchApp.exe (PID: 4056)
Reads the machine GUID from the registry
- XtremeShell.exe (PID: 2080)
- choco.exe (PID: 6536)
- csc.exe (PID: 7220)
Checks whether the specified file exists (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Reads the software policy settings
- XtremeShell.exe (PID: 2080)
Disables trace logs
- XtremeShell.exe (PID: 2080)
Checks proxy server information
- XtremeShell.exe (PID: 2080)
- explorer.exe (PID: 6608)
- SearchApp.exe (PID: 4056)
Checks if a key exists in the options dictionary (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Script raised an exception (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Creates files in the program directory
- XtremeShell.exe (PID: 2080)
- choco.exe (PID: 6536)
Uses string replace method (POWERSHELL)
- XtremeShell.exe (PID: 2080)
Process checks computer location settings
- XtremeShell.exe (PID: 2080)
- StartMenuExperienceHost.exe (PID: 2044)
- SearchApp.exe (PID: 4056)
Reads Microsoft Office registry keys
- explorer.exe (PID: 6608)
Reads security settings of Internet Explorer
- explorer.exe (PID: 6608)
Process checks Internet Explorer phishing filters
- SearchApp.exe (PID: 4056)
Creates files or folders in the user directory
- explorer.exe (PID: 6608)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2022:07:20 04:57:19+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 48 |
| CodeSize: | 67584 |
| InitializedDataSize: | 9483776 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x0000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.2.0.1 |
| ProductVersionNumber: | 4.2.0.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | XtremeShell |
| FileVersion: | 4.2.0.1 |
| InternalName: | XtremeShell |
| LegalCopyright: | (c) 2023 All rights reserved |
| OriginalFileName: | XtremeShell |
| ProductVersion: | 4.2.0.1 |
| AssemblyVersion: | 5.0.36.0 |
| CompanyName: | Neonity |
| ProductName: | XtremeShell |
| Comments: | - |
Total processes
237
Monitored processes
98
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 888 | "C:\WINDOWS\system32\reg.exe" add HKCU\Software\Microsoft\Windows\CurrentVersion\Search /v BingSearchEnabled /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | XtremeShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1076 | "C:\WINDOWS\system32\reg.exe" add HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\SuggestedApps /v king.com.CandyCrushSodaSaga_kgqvnymyfvs32 /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | XtremeShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 2080 | "C:\Users\admin\AppData\Local\Temp\XtremeShell.exe" | C:\Users\admin\AppData\Local\Temp\XtremeShell.exe | explorer.exe | ||||||||||||
User: admin Company: Neonity Integrity Level: HIGH Description: XtremeShell Exit code: 0 Version: 4.2.0.1 Modules
| |||||||||||||||
| 2152 | "C:\WINDOWS\system32\reg.exe" add HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\SuggestedApps /v Expedia.ExpediaHotelsFlightsCarsActivities_0wbx8rnn4qk5c /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | XtremeShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2336 | "C:\WINDOWS\system32\reg.exe" add HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\SuggestedApps /v Fitbit.FitbitCoach_6mqt6hf9g46tw /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | XtremeShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2396 | C:\Users\admin\AppData\Local\Temp\F6821757-1E86-4DA4-94FE-82D7C8FBE886\dismhost.exe {5702BB3E-C035-4ED0-B74F-2A7D772FC859} | C:\Users\admin\AppData\Local\Temp\F6821757-1E86-4DA4-94FE-82D7C8FBE886\DismHost.exe | XtremeShell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2464 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 2580 | "C:\WINDOWS\system32\reg.exe" add HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\SuggestedApps /v AdobeSystemsIncorporated.PhotoshopElements2018_ynb6jyjzte8ga /t REG_DWORD /d 0 /f | C:\Windows\System32\reg.exe | — | XtremeShell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2636 | C:\Users\admin\AppData\Local\Temp\7C641D29-7C81-4068-8578-3836FA2AFF1C\dismhost.exe {41FA79B5-6F53-4014-86EA-11205BBE3CF4} | C:\Users\admin\AppData\Local\Temp\7C641D29-7C81-4068-8578-3836FA2AFF1C\DismHost.exe | XtremeShell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Dism Host Servicing Process Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
45 874
Read events
45 540
Write events
297
Delete events
37
Modification events
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (2080) XtremeShell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\XtremeShell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
216
Suspicious files
5
Text files
128
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_uu0eizbq.ov3.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\chocolatey.zip | compressed | |
MD5:95231E41829F1C3A5AE890B71BCEF1FA | SHA256:C73D4EDA9AB5CA89583EF90838C4B819A304C9AC5A8AD5A89DCB7EDB15AB5FCF | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall.ps1 | text | |
MD5:DB89FC7120818885D1A1E112AC7BE6C1 | SHA256:C46903CFED1D74620630D0653CE057B3079AF5789AFEB1A5F884298A8693B4EC | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ciff2414.5l3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_2uzkrjt3.2ao.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\CREDITS.txt | text | |
MD5:7677758586925BAF4E9D7573BF12F273 | SHA256:4387F7836591FD9B384D5A11C22685D5441ED8F56A15DD962C28174F60D1B35B | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\chocolatey.nuspec | xml | |
MD5:6F1D1A607FCF498C306BA60F4C49E0BB | SHA256:A2B9463494ED831C3A388C1867043FDA6D7B308125F1CE33E52C914DE5D35B99 | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\_rels\.rels | xml | |
MD5:BB9B566B51B59EF054CBC0D22DF193C4 | SHA256:DDDB65206BB1DE00C7EC48740C10C2ABC0B440F22C49FB1FD74AFEDA0D095528 | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\choco.exe | executable | |
MD5:76D8FE544353FB6DFC258FCFBE9264D9 | SHA256:9A058764417A634DCB53AF74C50F9552AF3BC0B873A562F383AF36FEEFC1496E | |||
| 2080 | XtremeShell.exe | C:\Users\admin\AppData\Local\Temp\chocolatey\chocoInstall\tools\chocolateyInstall\choco.exe.manifest | xml | |
MD5:1B3ED984F60915F976B02BE949E212CB | SHA256:D715D6071E5CDD6447D46ED8E903B9B3AD5952ACC7394EE17593D87A546C17FC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
44
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6720 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
2080 | XtremeShell.exe | GET | 302 | 142.250.186.132:80 | http://www.google.com/ | unknown | — | — | whitelisted |
2080 | XtremeShell.exe | GET | 429 | 142.250.186.132:80 | http://www.google.com/sorry/index?continue=http://www.google.com/&q=EgTYGNieGPDYwrUGIjBNrJ4EPa16-odDTCImyINfcwHiHcsvuh6etFScfCEFKDVS7tR5RJKg_xNSbMlP7GYyAXJKGVNPUlJZX0FCVVNJVkVfTkVUX01FU1NBR0VaAUM | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6764 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
876 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5336 | SearchApp.exe | 95.100.146.35:443 | www.bing.com | Akamai International B.V. | CZ | unknown |
— | — | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6720 | backgroundTaskHost.exe | 20.31.169.57:443 | fd.api.iris.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3844 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
arc.msn.com |
| whitelisted |
community.chocolatey.org |
| whitelisted |
packages.chocolatey.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2080 | XtremeShell.exe | Potentially Bad Traffic | ET INFO Observed Chocolatey Windows Package Management Domain (chocolatey .org in TLS SNI) |
2080 | XtremeShell.exe | A Network Trojan was detected | ET HUNTING Terse Unencrypted Request for Google - Likely Connectivity Check |
Process | Message |
|---|---|
XtremeShell.exe | PID=2080 TID=6156 DismApi.dll: - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 DismApi.dll: <----- Starting DismApi.dll session -----> - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 DismApi.dll: - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 DismApi.dll: Host machine information: OS Version=10.0.19045, Running architecture=amd64, Number of processors=4 - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 DismApi.dll: API Version 10.0.19041.3758 - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 DismApi.dll: Parent process command line: "C:\Users\admin\AppData\Local\Temp\XtremeShell.exe" - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 Enter DismInitializeInternal - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 Input parameters: LogLevel: 2, LogFilePath: C:\WINDOWS\Logs\DISM\dism.log, ScratchDirectory: (null) - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 Initialized GlobalConfig - DismInitializeInternal
|
XtremeShell.exe | PID=2080 TID=6156 Initialized SessionTable - DismInitializeInternal
|