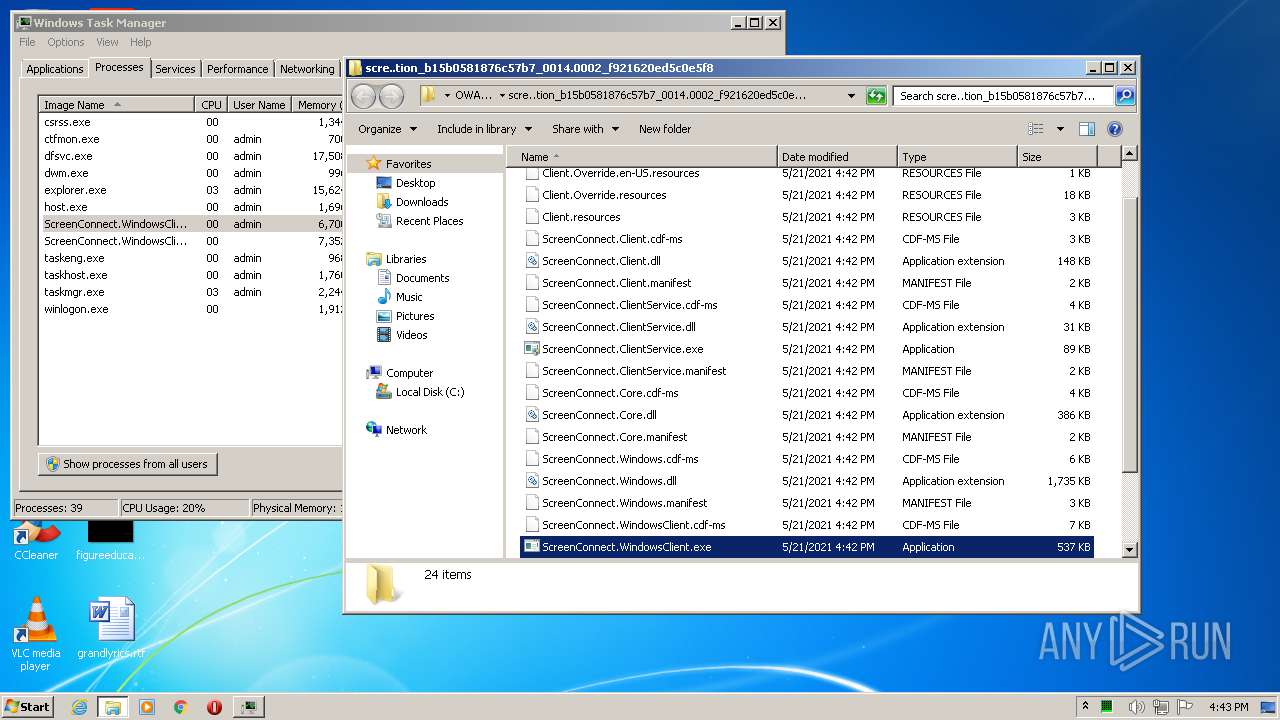
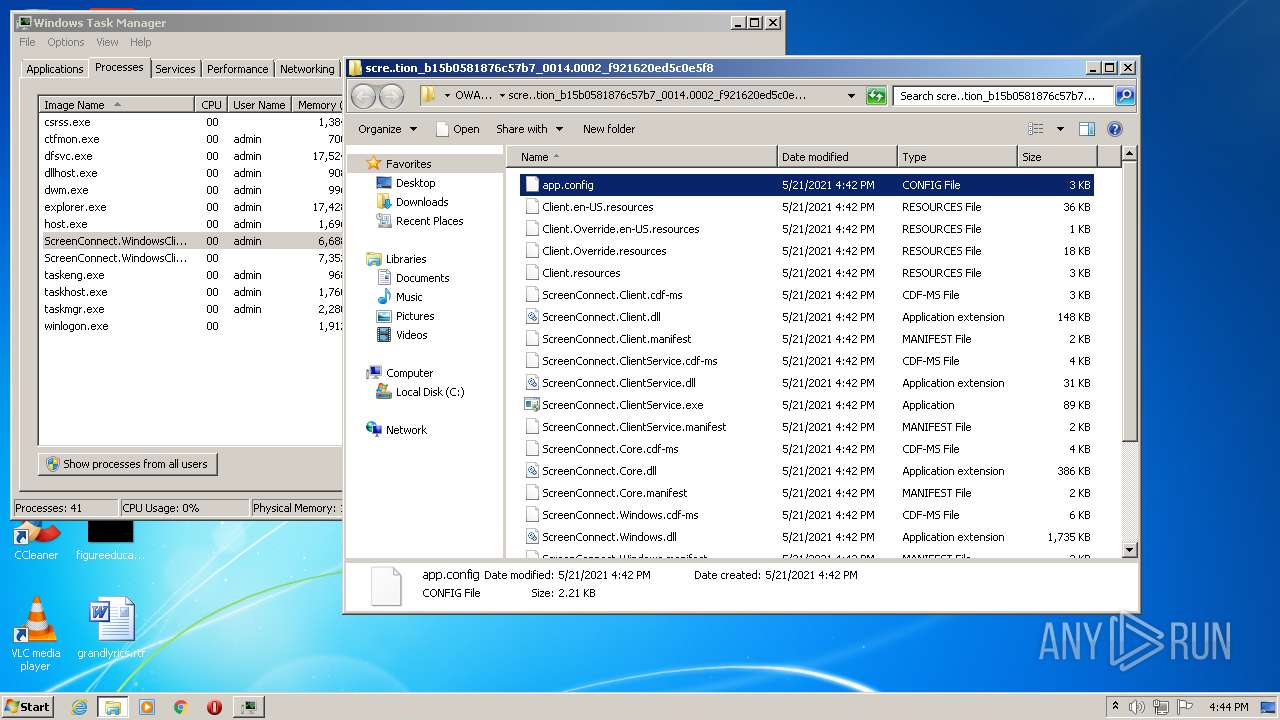
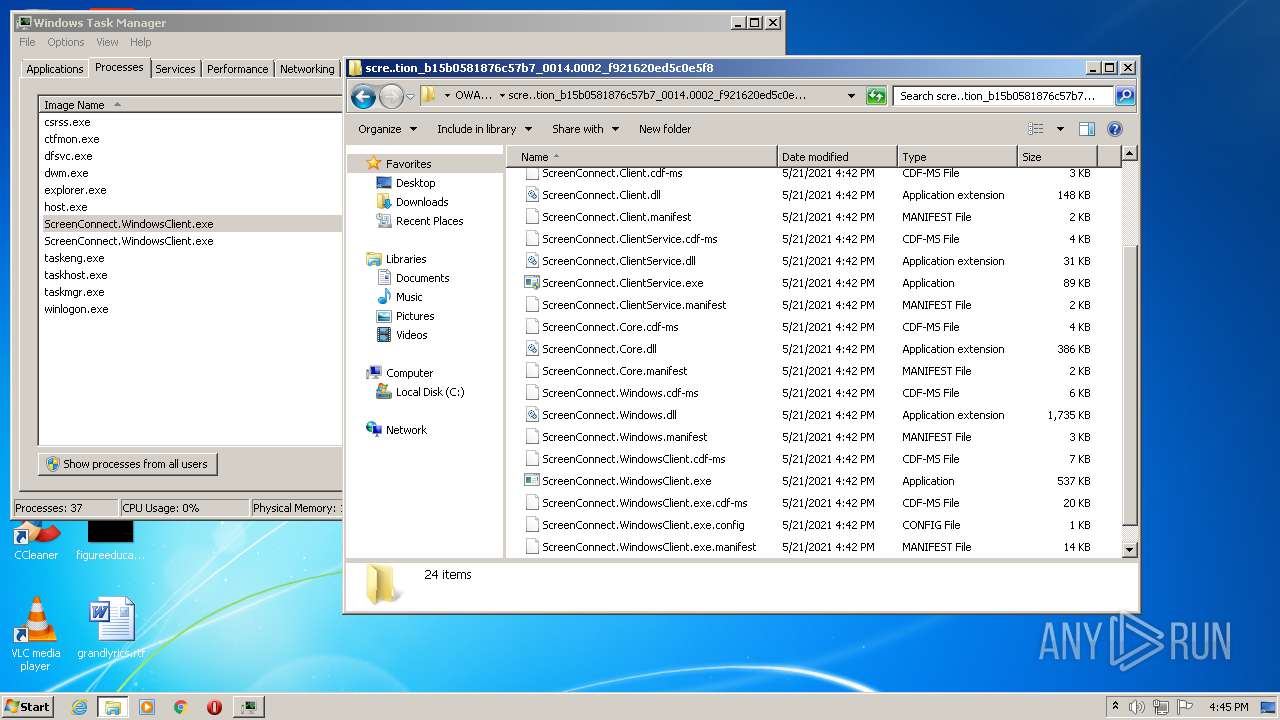
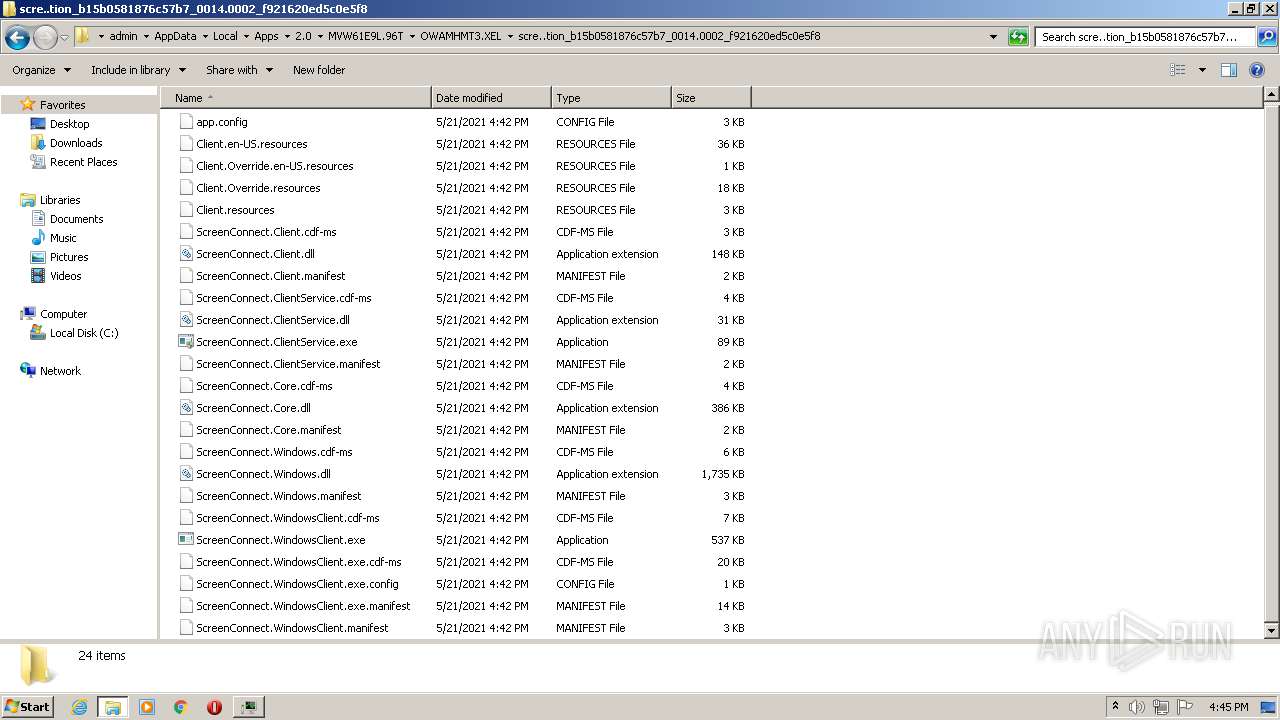
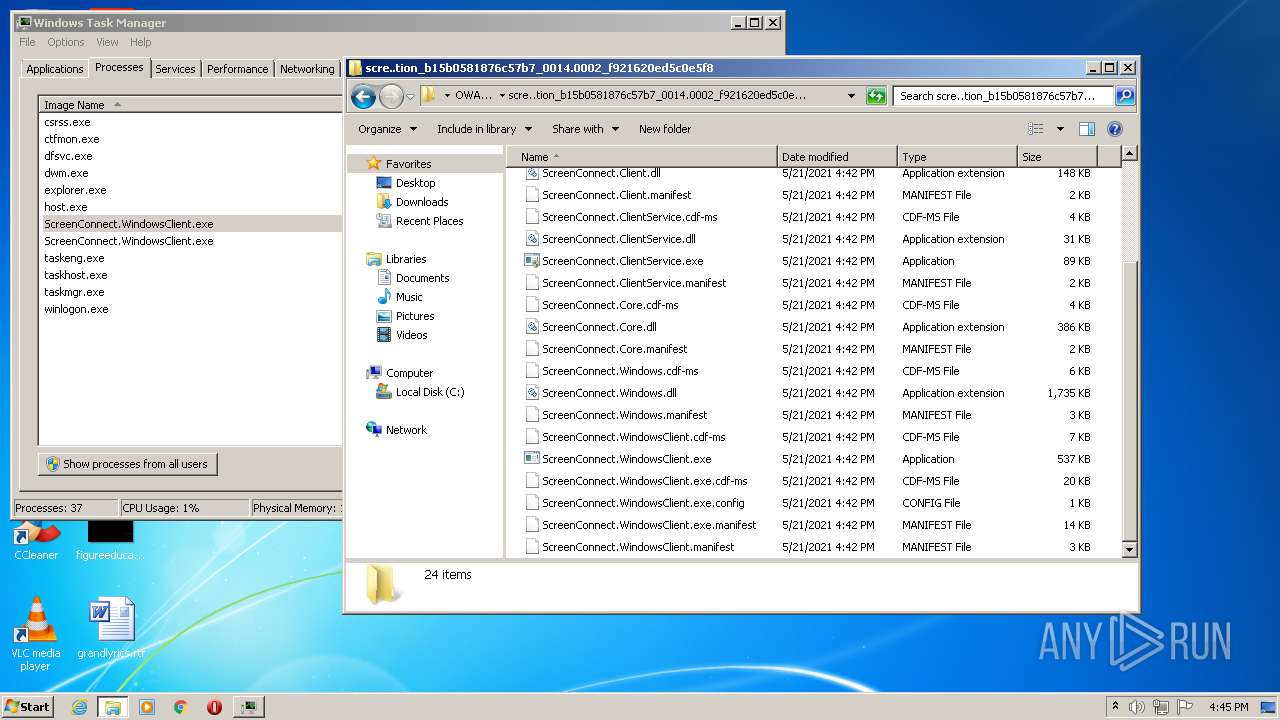
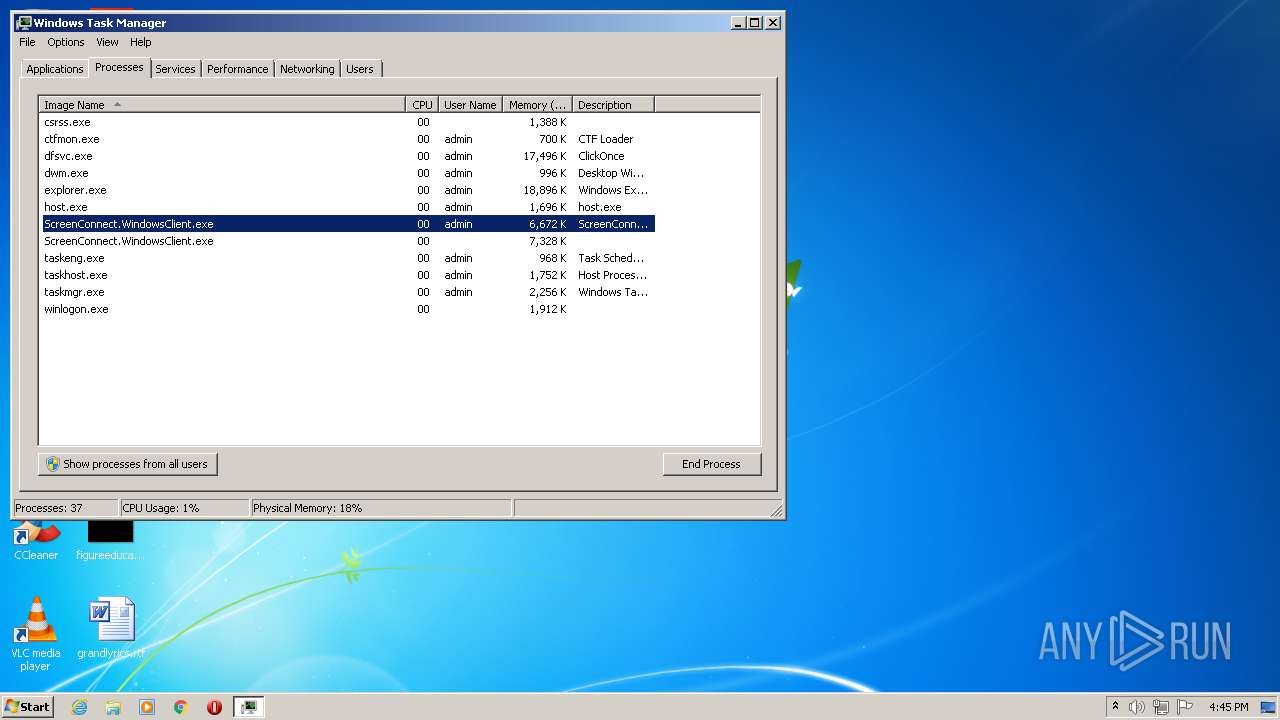
| File name: | support.Client.exe |
| Full analysis: | https://app.any.run/tasks/e96f7b1d-cd7b-4321-bb37-b54bc0448b6e |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2021, 15:41:48 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | F7B04C9F29262196DAC463E6164A2A8F |
| SHA1: | B145491B802B7EDE3CC5FC4D1CBDBAFA95152690 |
| SHA256: | A041D228CFEB88ABE07E575DF0C3FF4253BFB1B59544BA89CA82F0CD31006172 |
| SSDEEP: | 1536:TXn1JYSnExFkcgKKjxfmqshiKW5Xs/iYQqQJtsWFcdfRMvb+xWvI:jE3x5KBDYiKWm/iSw0fRMvygQ |
MALICIOUS
Changes settings of System certificates
- dfsvc.exe (PID: 3560)
- support.Client.exe (PID: 1592)
Loads dropped or rewritten executable
- dfsvc.exe (PID: 3560)
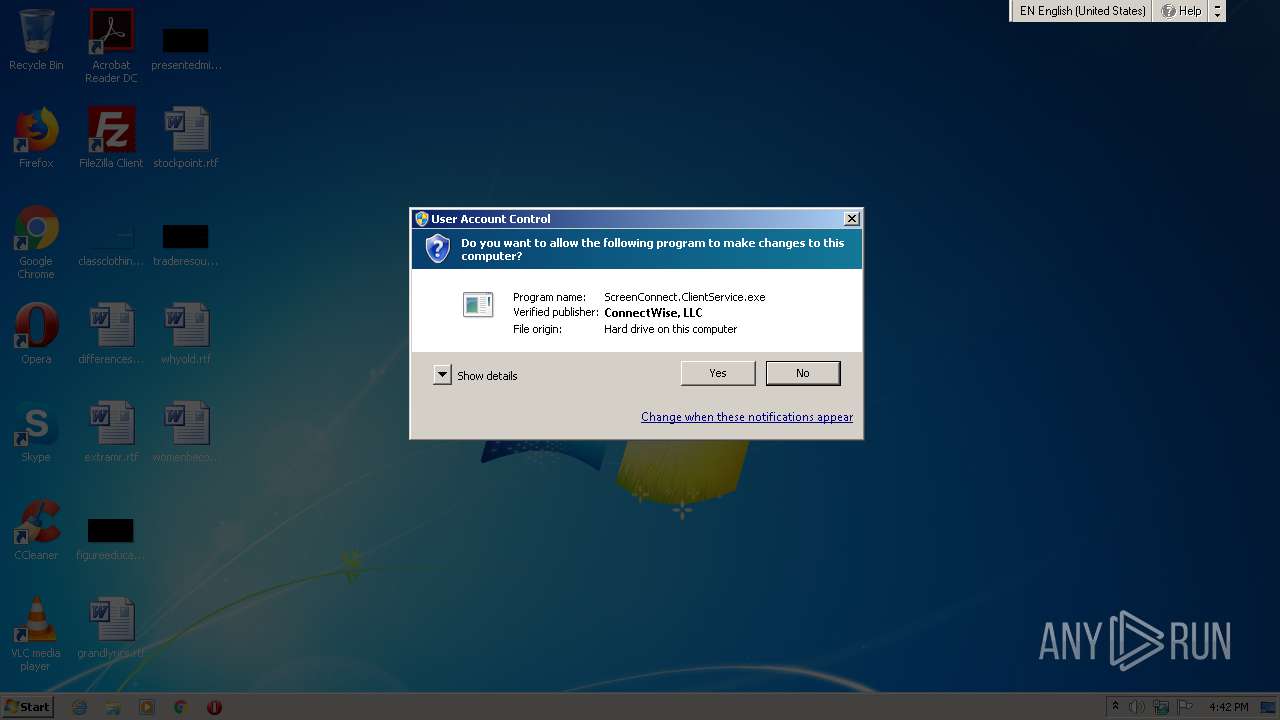
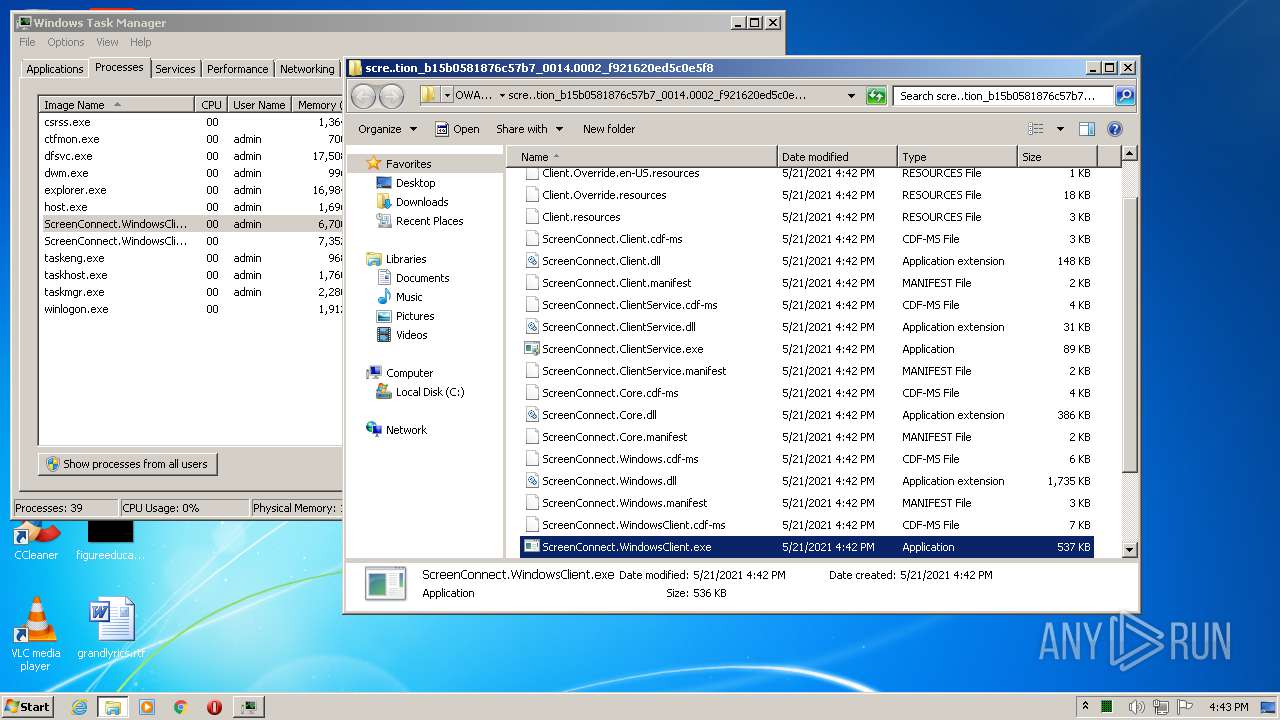
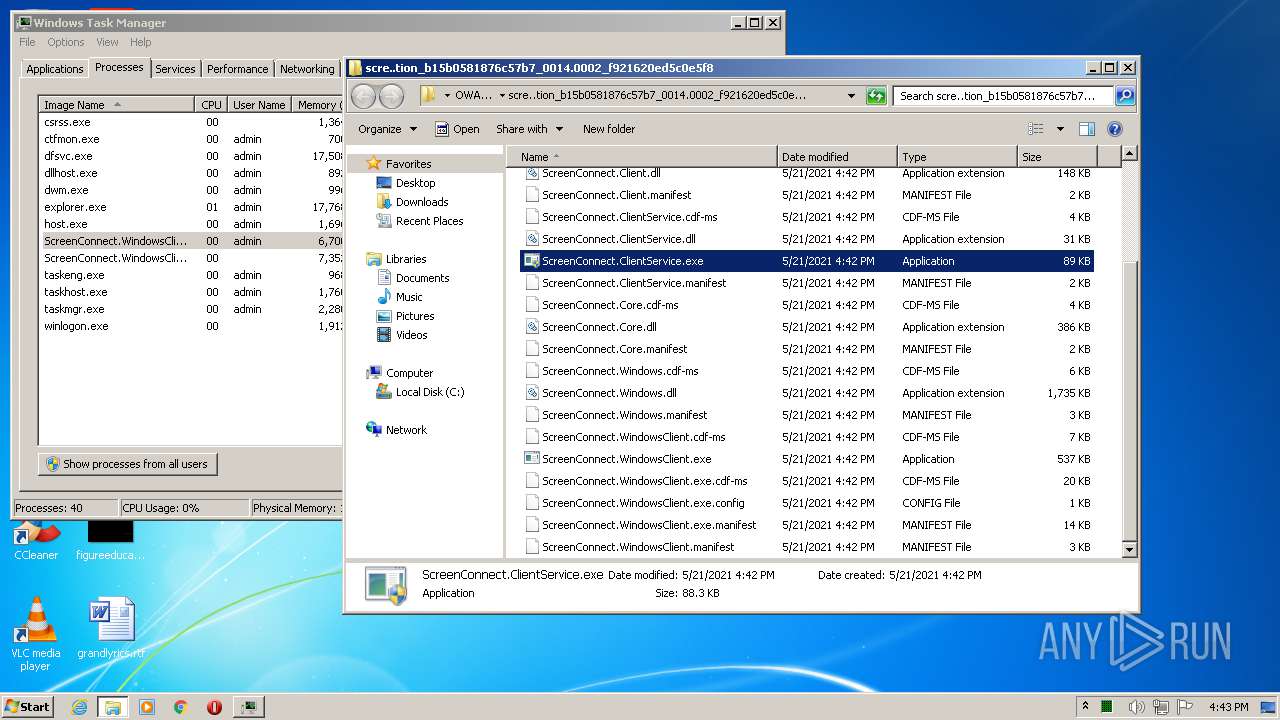
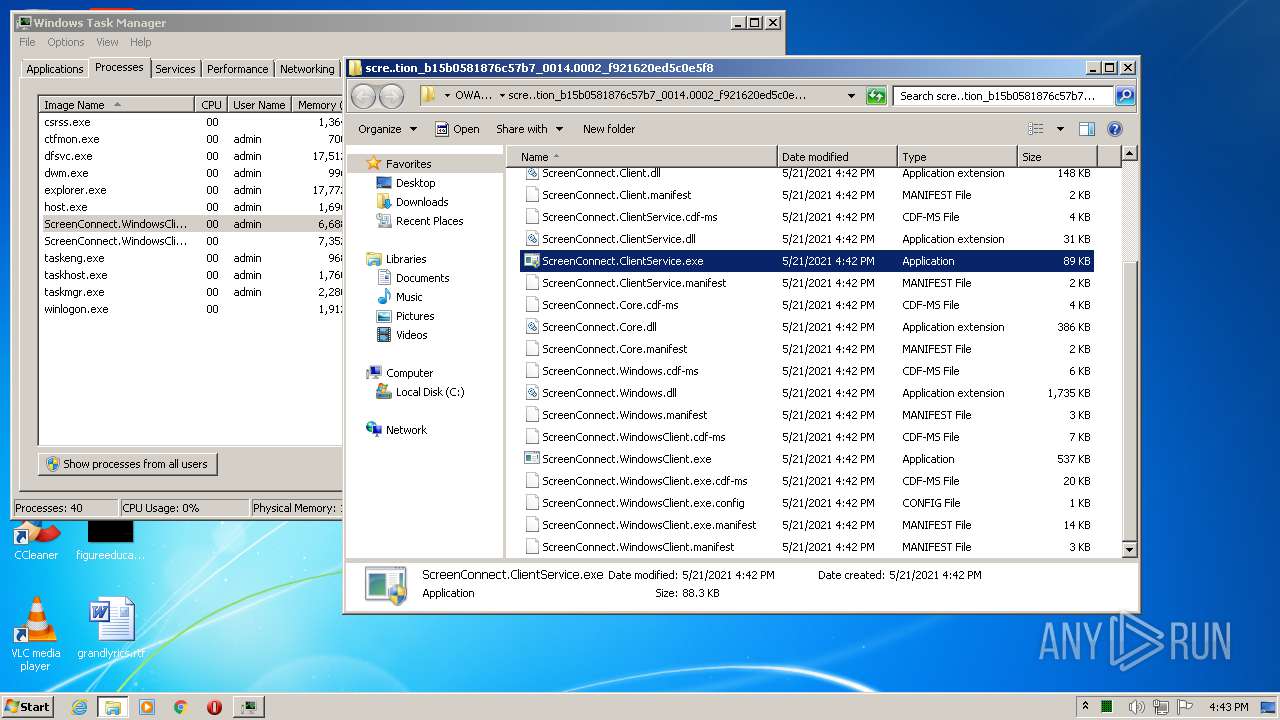
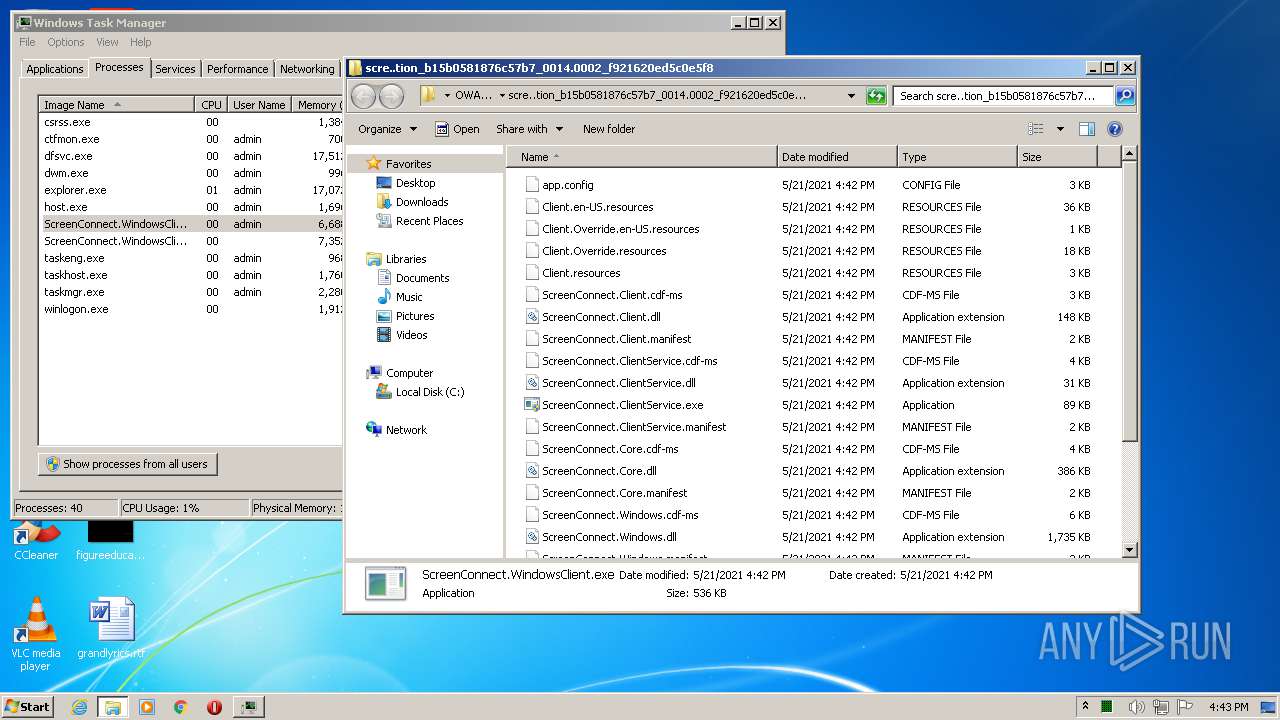
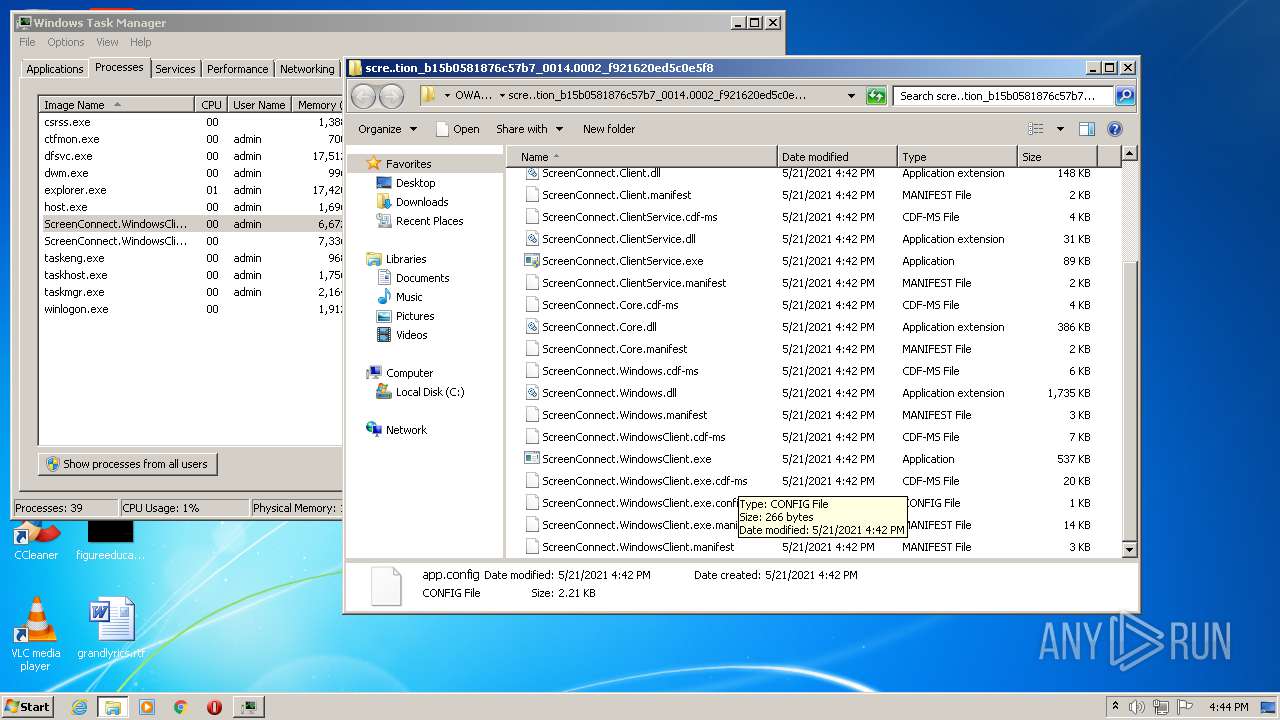
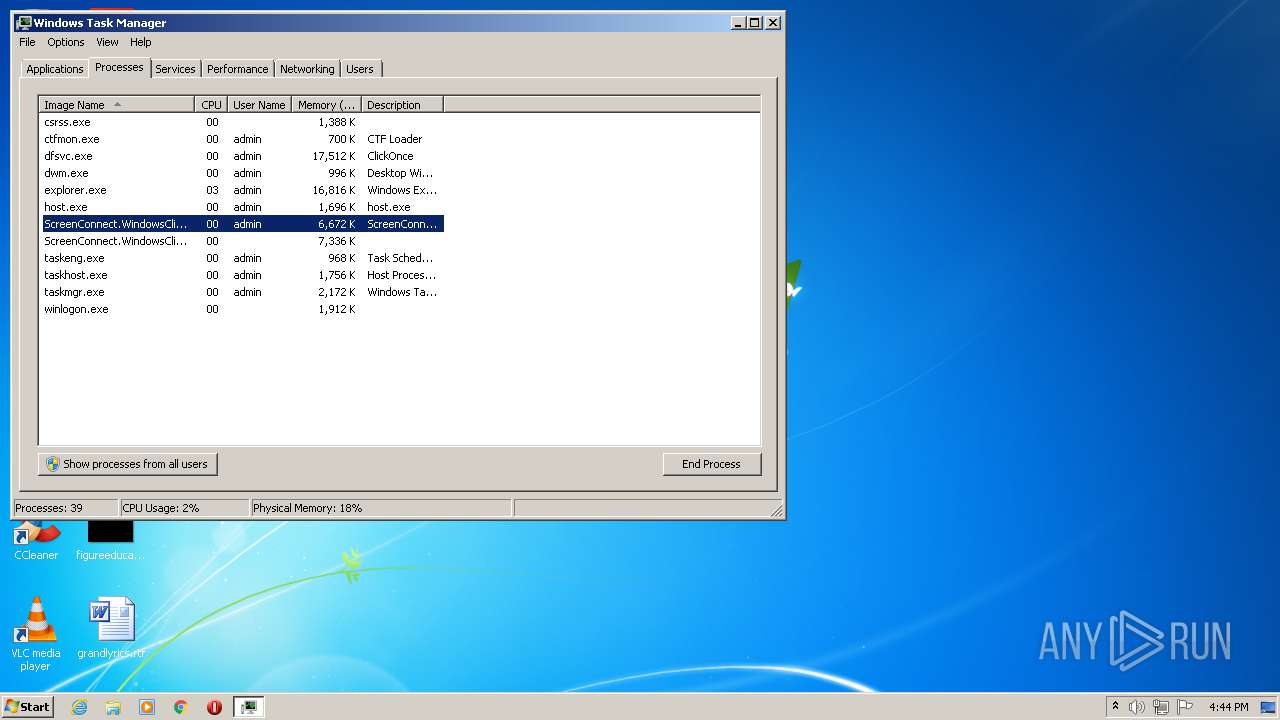
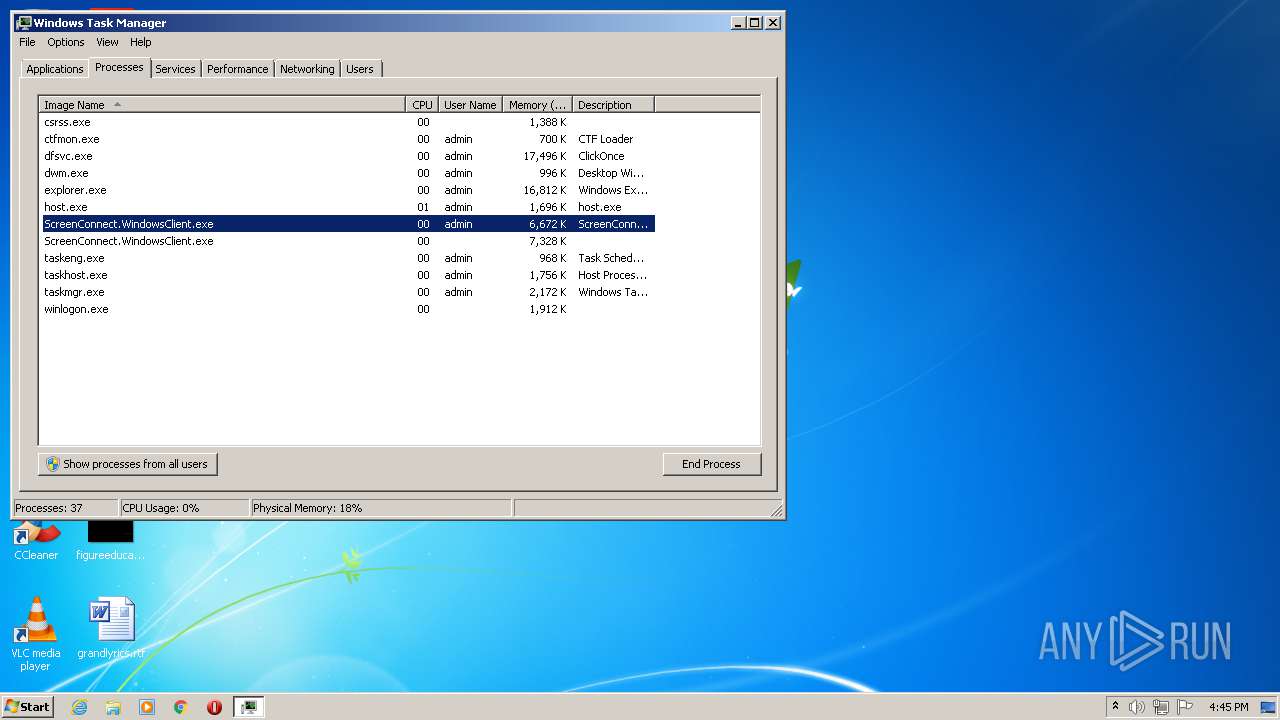
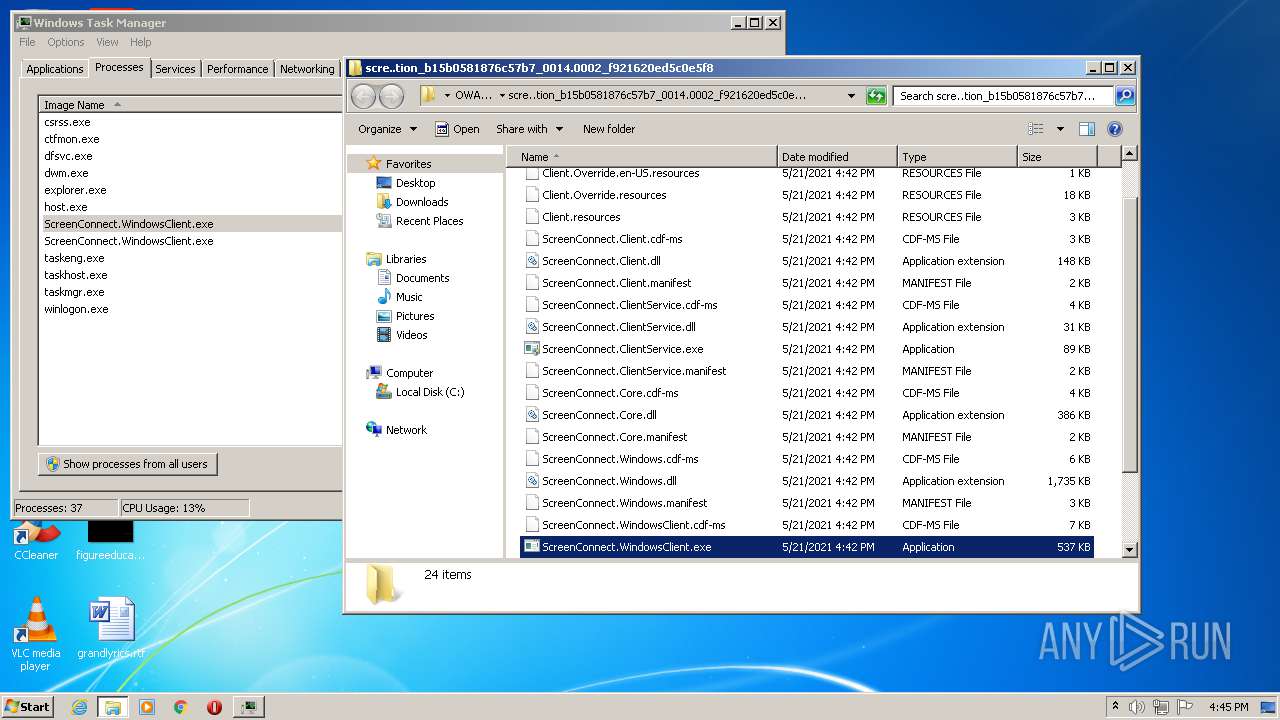
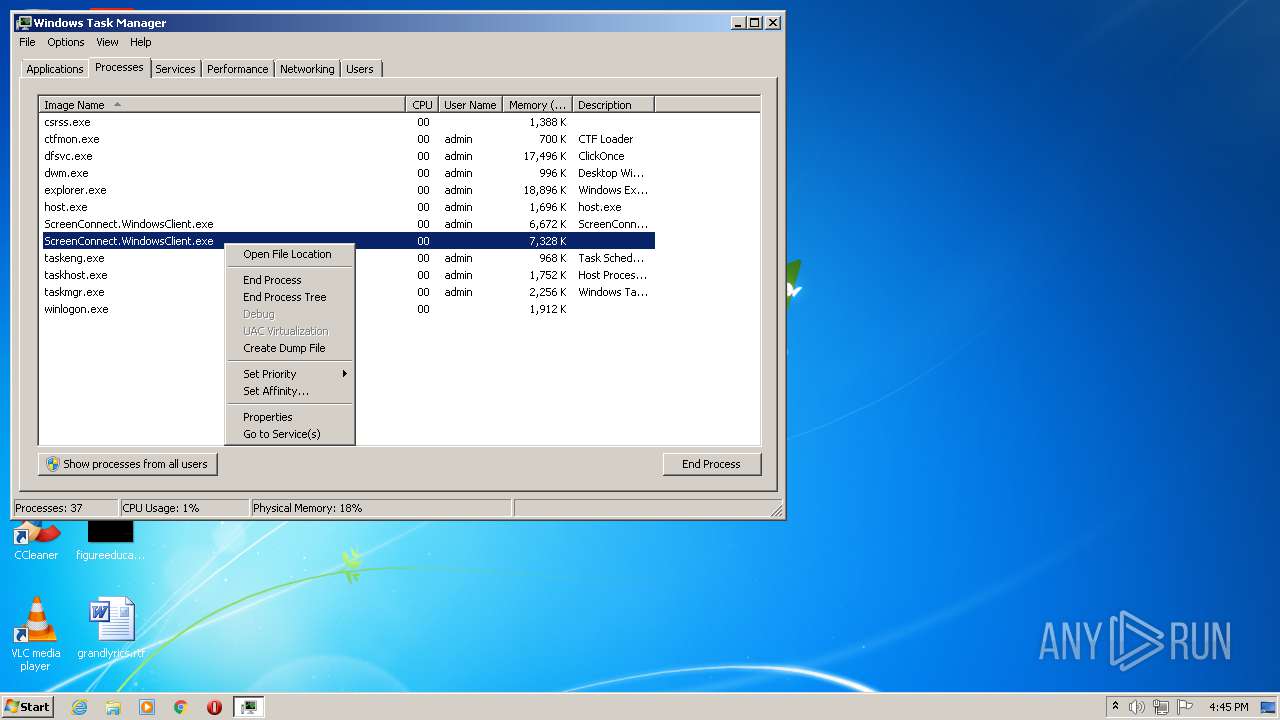
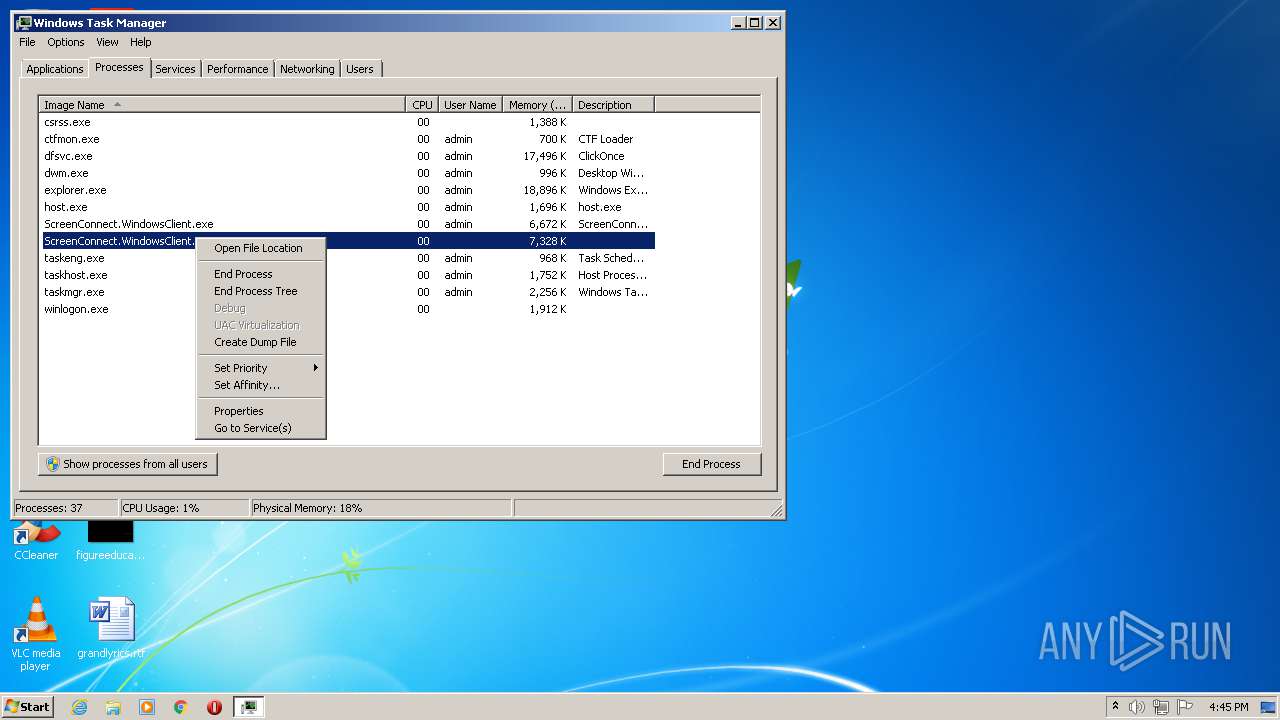
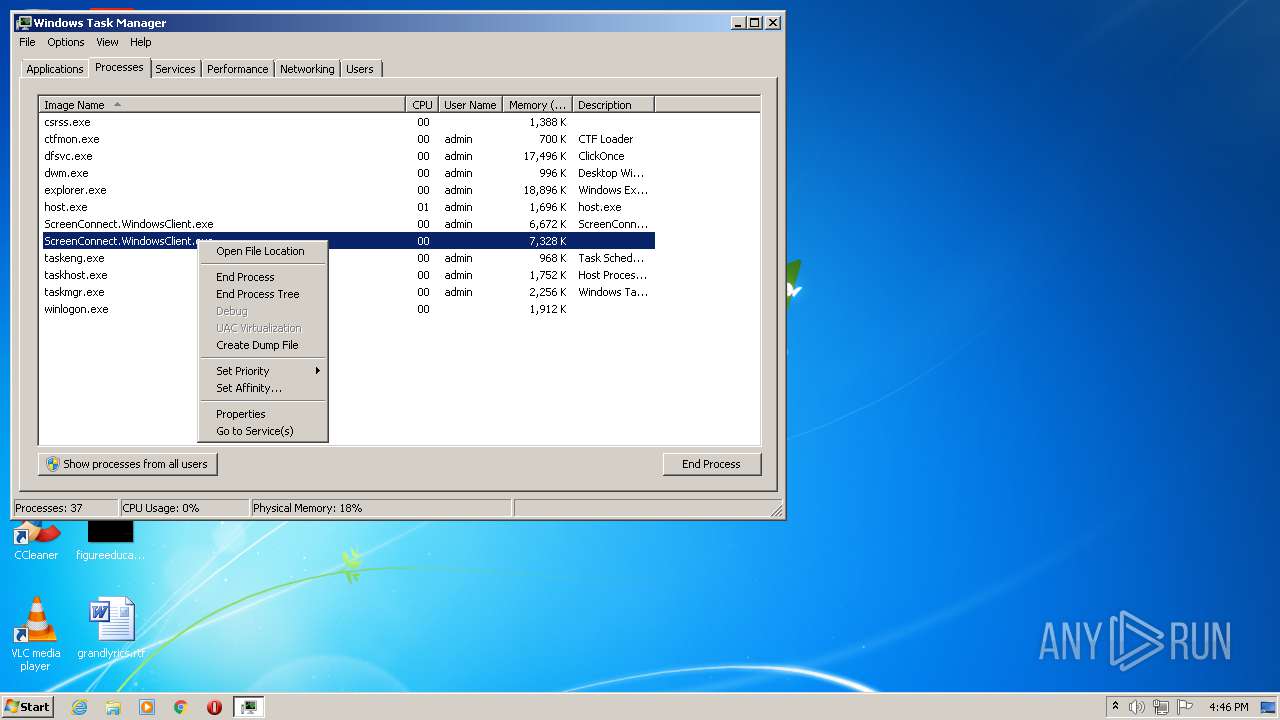
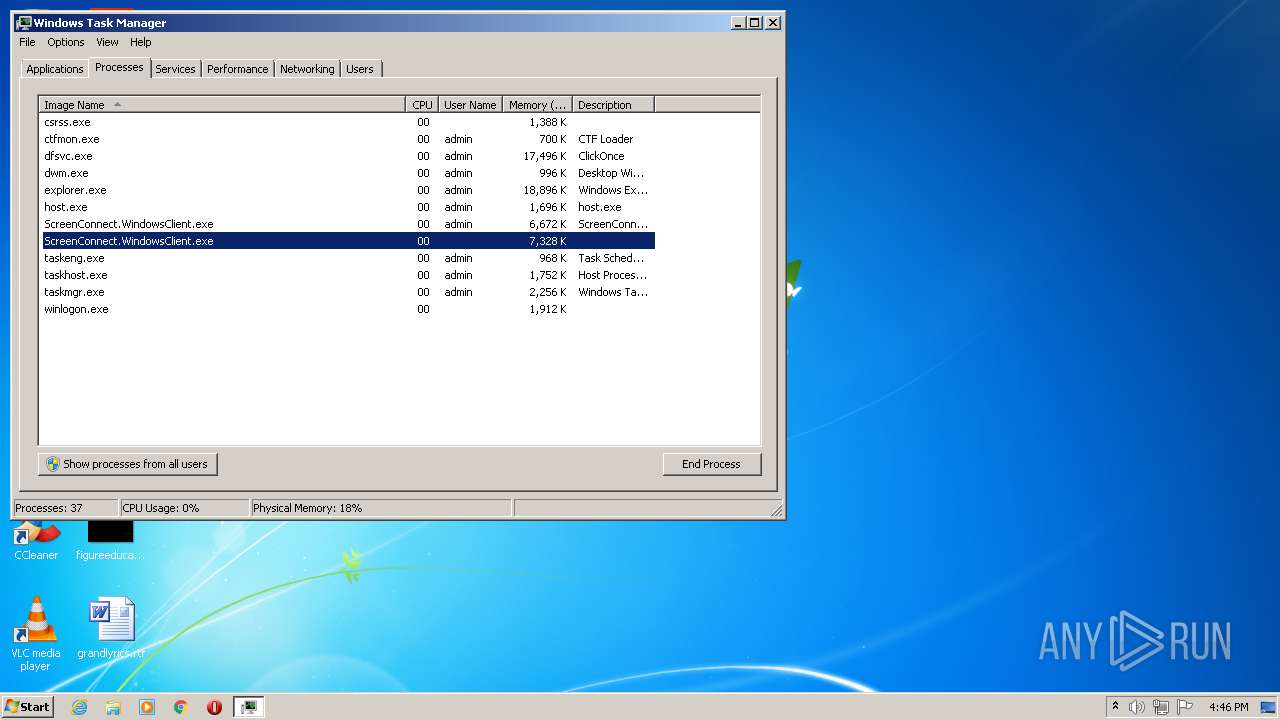
- ScreenConnect.WindowsClient.exe (PID: 1868)
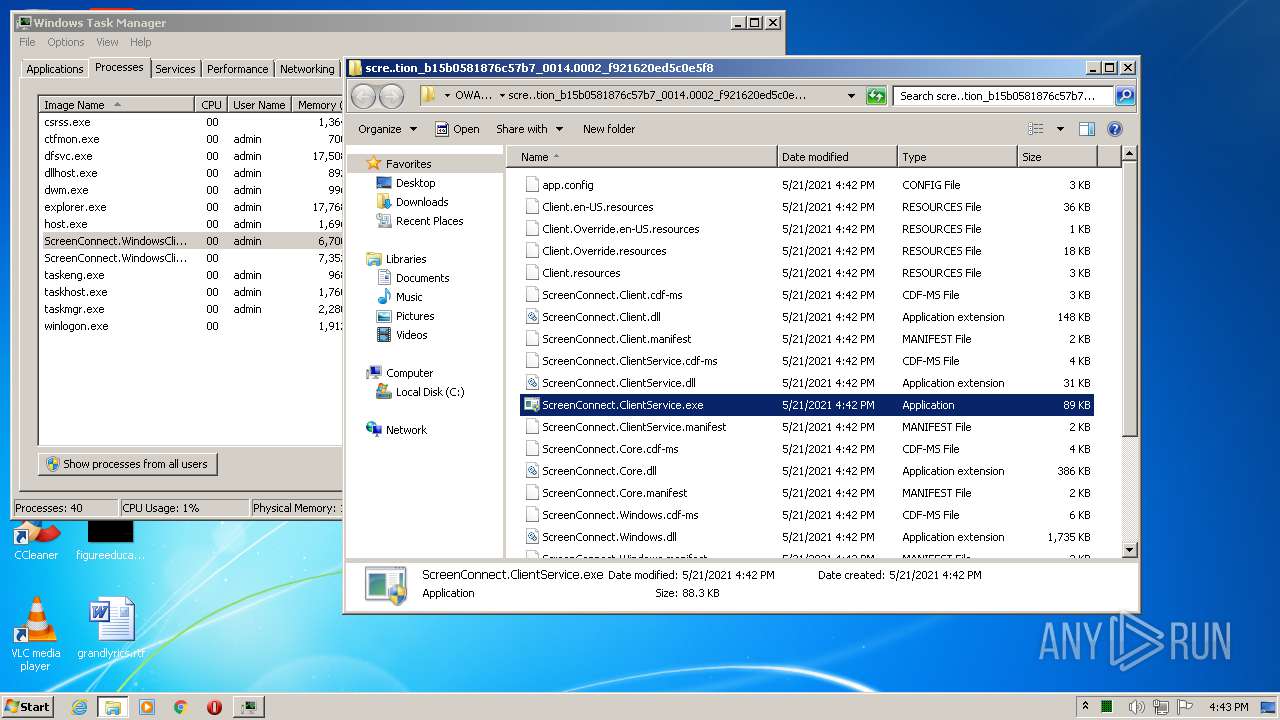
- ScreenConnect.ClientService.exe (PID: 4088)
- ScreenConnect.ClientService.exe (PID: 3504)
- ScreenConnect.WindowsClient.exe (PID: 888)
- ScreenConnect.WindowsClient.exe (PID: 3552)
- explorer.exe (PID: 560)
Application was dropped or rewritten from another process
- ScreenConnect.WindowsClient.exe (PID: 1868)
- ScreenConnect.ClientService.exe (PID: 4088)
- ScreenConnect.ClientService.exe (PID: 3504)
- ScreenConnect.WindowsClient.exe (PID: 888)
- ScreenConnect.WindowsClient.exe (PID: 3552)
SUSPICIOUS
Reads Environment values
- dfsvc.exe (PID: 3560)
- ScreenConnect.WindowsClient.exe (PID: 3552)
Reads internet explorer settings
- dfsvc.exe (PID: 3560)
Creates files in the user directory
- dfsvc.exe (PID: 3560)
Executable content was dropped or overwritten
- dfsvc.exe (PID: 3560)
Drops a file that was compiled in debug mode
- dfsvc.exe (PID: 3560)
Drops a file with too old compile date
- dfsvc.exe (PID: 3560)
Executed as Windows Service
- ScreenConnect.ClientService.exe (PID: 3504)
Reads CPU info
- ScreenConnect.WindowsClient.exe (PID: 3552)
Reads default file associations for system extensions
- explorer.exe (PID: 560)
INFO
Manual execution by user
- taskmgr.exe (PID: 3412)
- notepad++.exe (PID: 1588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| Subsystem: | Windows GUI |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x16e7 |
| UninitializedDataSize: | - |
| InitializedDataSize: | 33280 |
| CodeSize: | 44032 |
| LinkerVersion: | 14 |
| PEType: | PE32 |
| TimeStamp: | 2016:05:18 18:07:24+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 18-May-2016 16:07:24 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 18-May-2016 16:07:24 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000AA97 | 0x0000AC00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.6143 |
.rdata | 0x0000C000 | 0x00005AE8 | 0x00005C00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.90769 |
.data | 0x00012000 | 0x000011E0 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.12918 |
.gfids | 0x00014000 | 0x000000B4 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 1.4773 |
.rsrc | 0x00015000 | 0x000001E0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.70468 |
.reloc | 0x00016000 | 0x00000E10 | 0x00001000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.16675 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91161 | 381 | UNKNOWN | English - United States | RT_MANIFEST |
Imports
ADVAPI32.dll |
CRYPT32.dll |
KERNEL32.dll |
Total processes
56
Monitored processes
11
Malicious processes
7
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | C:\Windows\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
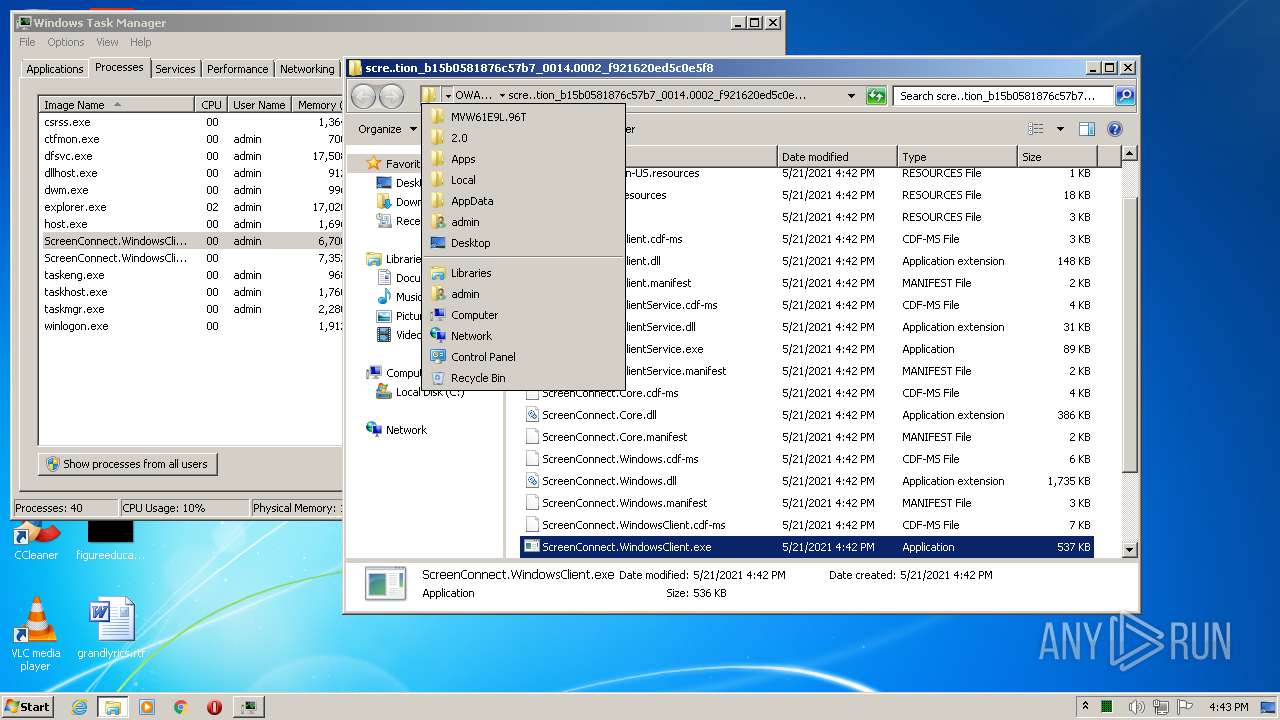
| 888 | "C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.WindowsClient.exe" "RunRole" "bebdaae9-6970-414e-89aa-b8bcb0e34fa9" "User" | C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 20.2.27450.7387 Modules
| |||||||||||||||
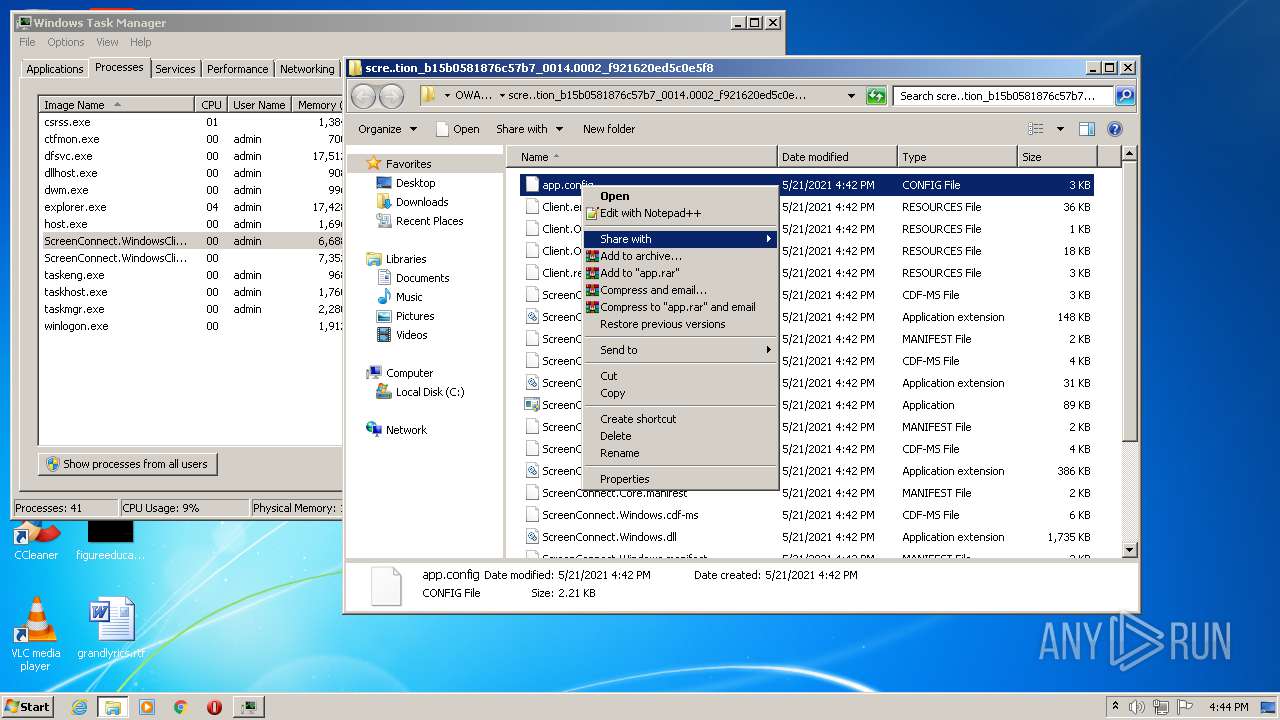
| 1588 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\app.config" | C:\Program Files\Notepad++\notepad++.exe | — | explorer.exe | |||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\AppData\Local\Temp\support.Client.exe" | C:\Users\admin\AppData\Local\Temp\support.Client.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1868 | "C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.WindowsClient.exe" | C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.WindowsClient.exe | — | dfsvc.exe | |||||||||||
User: admin Company: ScreenConnect Software Integrity Level: MEDIUM Description: ScreenConnect Client Exit code: 0 Version: 20.2.27450.7387 Modules
| |||||||||||||||
| 3412 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3504 | "C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.ClientService.exe" "?y=Guest&h=tssupport.us&p=8041&s=c9f1e86a-7044-45de-9c19-6a5861609c22&k=BgIAAACkAABSU0ExAAgAAAEAAQCDJtWgqekzRVo8dGHl%2b4mRD4X509o6naFSX5ri6oKCh58u0KquANoKWXMagEwL636P9aw93EvW0cVgYiuGFWOzeeLuKHfehoyQcNZQ4AjJTFpf86ktD%2f5VREGlwYw7BgH1thDidPfqCd8S3BYZtGzor8PYM66rjMPJqEg%2f0LhiWlOLw3ceA9oZwt%2bkB3S1L74J8meAoME4LMzwt%2fC4i5vKBFycaNtWYBgDPG1SqtOTkayxqBqQuDoy6aOUVAW1oIP%2fhJlhMwUBCCRO3raSWCe%2fHtcL1CAJlGFuAEwijdPF2UJHAjs%2bCyMWFeTDgHcSjvbWXWYN3nc3njHrjWMtoOXI&r=&i=Untitled%20Session" "1" | C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.ClientService.exe | services.exe | ||||||||||||
User: SYSTEM Integrity Level: SYSTEM Exit code: 0 Version: 20.2.27450.7387 Modules
| |||||||||||||||
| 3552 | "C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.WindowsClient.exe" "RunRole" "0bfd8a99-6134-4adf-81fb-a28d0dd11245" "System" | C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\scre..tion_b15b0581876c57b7_0014.0002_f921620ed5c0e5f8\ScreenConnect.WindowsClient.exe | — | ScreenConnect.ClientService.exe | |||||||||||
User: SYSTEM Company: ScreenConnect Software Integrity Level: SYSTEM Description: ScreenConnect Client Exit code: 0 Version: 20.2.27450.7387 Modules
| |||||||||||||||
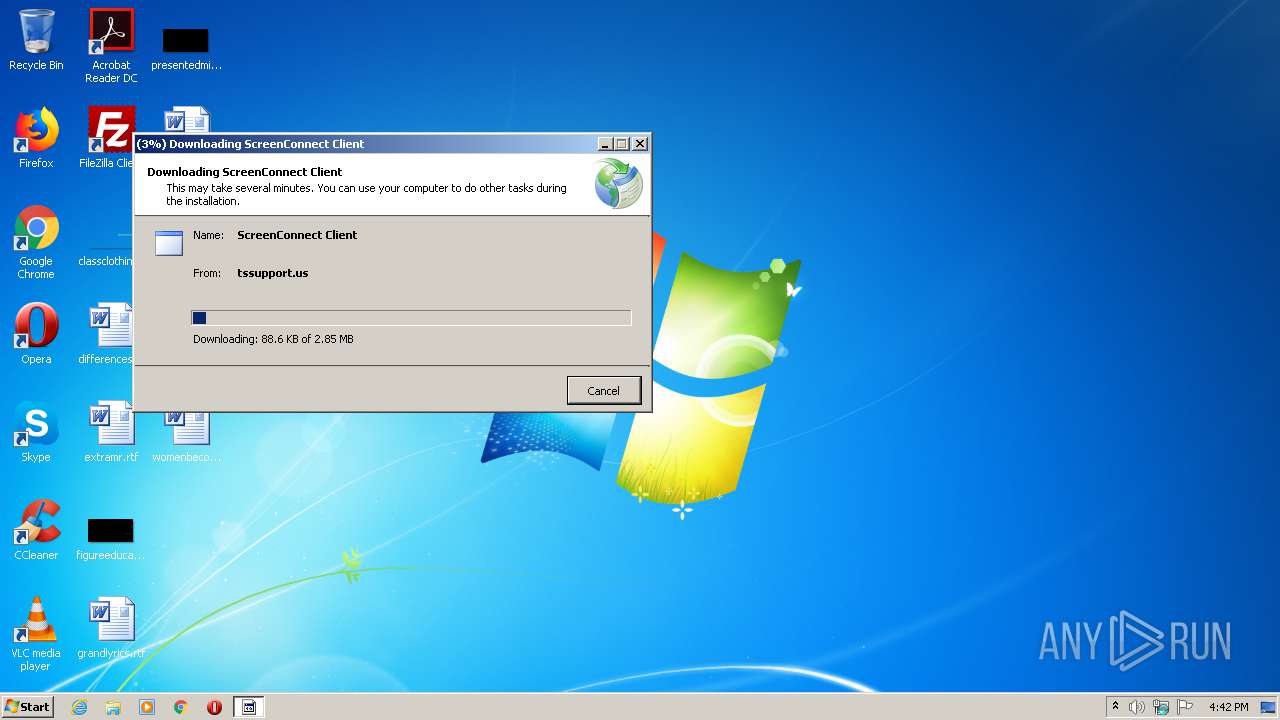
| 3560 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe | support.Client.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 3828 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
Total events
2 157
Read events
1 703
Write events
426
Delete events
28
Modification events
| (PID) Process: | (1592) support.Client.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13D\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1592) support.Client.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\TrustedPublisher\Certificates\D4D75FDE705713CC3D28AABB99DA6BA16B3DFCDE |
| Operation: | write | Name: | Blob |
Value: 030000000100000014000000D4D75FDE705713CC3D28AABB99DA6BA16B3DFCDE20000000010000002C0500003082052830820410A0030201020210085DFB7228E907CF98022C52C511BC66300D06092A864886F70D01010B05003072310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3131302F0603550403132844696769436572742053484132204173737572656420494420436F6465205369676E696E67204341301E170D3139313032323030303030305A170D3232313032363132303030305A3065310B30090603550406130255533110300E06035504081307466C6F72696461310E300C0603550407130554616D706131193017060355040A1310436F6E6E656374576973652C204C4C433119301706035504031310436F6E6E656374576973652C204C4C4330820122300D06092A864886F70D01010105000382010F003082010A0282010100AFF44932097C6F6581818041BEB0983E68F9AF594959E60ADB9948991D0CB693BD3E6FEBC4E08D0895D3B77970B3EA171C377224B71A12B163385F1480F498CD0EAE93B0E6EED61DBDBDFBFB5E3B4A9C7B63F52BF30E027CEFE53B449160EA09969E6F474A3BA8B9EC92DF855F3031F42EED4813CF5B31080F7677DF2941BE2157134683184629972BFAA24A8184E6AEEE5F4485A4C86E1342118FD4D203C3537B91931279DE62DDF5FC6F378F1371E0D987CE9A1DAA873F8C9EAC570F684CC150C11195F9E66EA6A7579574EAF1C635A247B19A74E9853EF8AEB2F9985E37A6591CAAE42453745C4E4F67D55472E67A8B4566913E978D351A9C53277A51A5ED0203010001A38201C5308201C1301F0603551D230418301680145AC4B97B2A0AA3A5EA7103C060F92DF665750E58301D0603551D0E04160414A6B7FAEEC29169953F10837D11E48F3C596BD80B300E0603551D0F0101FF04040302078030130603551D25040C300A06082B0601050507030330770603551D1F0470306E3035A033A031862F687474703A2F2F63726C332E64696769636572742E636F6D2F736861322D617373757265642D63732D67312E63726C3035A033A031862F687474703A2F2F63726C342E64696769636572742E636F6D2F736861322D617373757265642D63732D67312E63726C304C0603551D2004453043303706096086480186FD6C0301302A302806082B06010505070201161C68747470733A2F2F7777772E64696769636572742E636F6D2F4350533008060667810C01040130818406082B0601050507010104783076302406082B060105050730018618687474703A2F2F6F6373702E64696769636572742E636F6D304E06082B060105050730028642687474703A2F2F636163657274732E64696769636572742E636F6D2F446967694365727453484132417373757265644944436F64655369676E696E6743412E637274300C0603551D130101FF04023000300D06092A864886F70D01010B05000382010100693660B45165355D831C324C3AE47A4960602E321C9BD34546DD87D86D9AF9E78D39BD42972273587FFA2EA32F4C7FD35D9A1B8C901A7422E322810E84E1BFDA958363DE1E32F4700D9B0867EADC5B018C71F5F2DD0238194E42F6D744C7F65F2EDDB04740B85AD62F821ECC9C9DDB474B6EE71035EF99251518183E8CB0F7FAB4BAC08BBAD55522B23ED20E065F917956F6B24DF8F89AF1A32901512DB2FBE1783EA37B645AAD71E15BD4E5522B83BAE0696744F7EC21143BEFD856AFCA78C62F9D989A0BC67C1E33204A1EA4154940B7078DE53FE15A71D6F0DEA3957A099AA65C4C4C33F4316B2DB58CB221D712D10C177CAE393427529E04346D029B2D24 | |||
| (PID) Process: | (1592) support.Client.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\SystemCertificates\TrustedPublisher\Certificates\92C1588E85AF2201CE7915E8538B492F605B80C6 |
| Operation: | write | Name: | Blob |
Value: 03000000010000001400000092C1588E85AF2201CE7915E8538B492F605B80C62000000001000000340500003082053030820418A00302010202100409181B5FD5BB66755343B56F955008300D06092A864886F70D01010B05003065310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D312430220603550403131B4469676943657274204173737572656420494420526F6F74204341301E170D3133313032323132303030305A170D3238313032323132303030305A3072310B300906035504061302555331153013060355040A130C446967694365727420496E6331193017060355040B13107777772E64696769636572742E636F6D3131302F0603550403132844696769436572742053484132204173737572656420494420436F6465205369676E696E6720434130820122300D06092A864886F70D01010105000382010F003082010A0282010100F8D3B31C7F0E11AF677707D30B314919CFD0FB4599B13ADB44F57FE5A89DDB32D771EA769D052EB78FFA9243C0A5F989D43719D7B6AAF09C86A5D825AC0E79283A7EE9D167D3C6FB2927C7D37B2394E4912396907782F9A18423661254335074B12826BB2469C2C252F214678A8945D42DA1A3E9882C2095AE1C4A8708DF0CF5E24D6018BEAAC4B2AE70316633713EAC70A2ABCE7FE97CCB92A1E53B311CCFEAF20AE457BB4AB5E974E62BFE6CCB7E7439360D90EFE4B54EA4A9EA6A0AAB84F3AC674EB5C4F78CD1202523EB08643E5296C1F20F12F4C58E0FC1A2E82C51F773BCBD85B1628373418207E4388B6A7320D00F64733C9E9FA633A9FD19DF2593D10203010001A38201CD308201C930120603551D130101FF040830060101FF020100300E0603551D0F0101FF04040302018630130603551D25040C300A06082B06010505070303307906082B06010505070101046D306B302406082B060105050730018618687474703A2F2F6F6373702E64696769636572742E636F6D304306082B060105050730028637687474703A2F2F636163657274732E64696769636572742E636F6D2F4469676943657274417373757265644944526F6F7443412E6372743081810603551D1F047A3078303AA038A0368634687474703A2F2F63726C342E64696769636572742E636F6D2F4469676943657274417373757265644944526F6F7443412E63726C303AA038A0368634687474703A2F2F63726C332E64696769636572742E636F6D2F4469676943657274417373757265644944526F6F7443412E63726C304F0603551D20044830463038060A6086480186FD6C000204302A302806082B06010505070201161C68747470733A2F2F7777772E64696769636572742E636F6D2F435053300A06086086480186FD6C03301D0603551D0E041604145AC4B97B2A0AA3A5EA7103C060F92DF665750E58301F0603551D2304183016801445EBA2AFF492CB82312D518BA7A7219DF36DC80F300D06092A864886F70D01010B050003820101003EEC0D5A24B3F322D115C82C7C252976A81D5D1C2D3A1AC4EF3061D77E0B60FDC33D0FC4AF8BFDEF2ADF205537B0E1F6D192750F51B46EA58E5AE25E24814E10A4EE3F718E630E134BADD75F4479F33614068AF79C464E5CFF90B11B070E9115FBBAAFB551C28D24AE24C6C7272AA129281A3A7128023C2E91A3C02511E29C1447A17A6868AF9BA75C205CD971B10C8FBBA8F8C512689FCF40CB4044A513F0E6640C25084232B2368A2402FE2F727E1CD7494596E8591DE9FA74646BB2EB6643DAB3B08CD5E90DDDF60120CE9931633D081A18B3819B4FC6931006FC0781FA8BDAF98249F7626EA153FA129418852E9291EA686C4432B266A1E718A49A6451EF | |||
| (PID) Process: | (560) explorer.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Action Center\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000CEDED634E1F87E438182DF4170E861EF00000000020000000000106600000001000020000000E4CDCEF078519ADEE92F2E48985EB771683E122032AE502B166BDF1F63D67536000000000E800000000200002000000089DAC2A18EEB7FFF252521770D4053A2A50B43C9DB4ABB3AAFEB10CB445C7B913000000011CD2449F5D1CE1C2E7921AE253DA5D1324384C6F9D78824BC0C90B5FA2503FD4EE886523E65323BD06484A9036BDFC340000000C831FDC69FB5D1002F3BD23B00FF3FAD3BE235484D48BE6B5032063F47DDFBF0B363941F5D00933A7B220CC21DAF84D18DDC2CF2CF6A372245C4B9AE0FD6AAB5 | |||
| (PID) Process: | (3560) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | write | Name: | ComponentStore_RandomString |
Value: T00TLP7DM8JBXM2BZO3NOW83 | |||
| (PID) Process: | (3560) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | delete value | Name: | ComponentStore_RandomString |
Value: T00TLP7DM8JBXM2BZO3NOW83 | |||
| (PID) Process: | (3560) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3560) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0 |
| Operation: | write | Name: | ComponentStore_RandomString |
Value: MVW61E9L96TOWAMHMT3XELK0 | |||
| (PID) Process: | (3560) dfsvc.exe | Key: | HKEY_CLASSES_ROOT\Software\Microsoft\Windows\CurrentVersion\Deployment\SideBySide\2.0\StateManager |
| Operation: | write | Name: | StateStore_RandomString |
Value: VOTMEE4V5K8RO8LO4KRGJMVO | |||
| (PID) Process: | (3560) dfsvc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\dfsvc_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
Executable files
12
Suspicious files
12
Text files
15
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\74WDZ4ZN.QNV\N3VK2P6Y.YZB\ScreenConnect.Windows.dll.genman | — | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\74WDZ4ZN.QNV\N3VK2P6Y.YZB\ScreenConnect.ClientService.dll.genman | — | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\74WDZ4ZN.QNV\N3VK2P6Y.YZB\ScreenConnect.Client.dll.genman | — | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\74WDZ4ZN.QNV\N3VK2P6Y.YZB\ScreenConnect.WindowsClient.exe.genman | — | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\74WDZ4ZN.QNV\N3VK2P6Y.YZB\ScreenConnect.Core.dll.genman | — | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\manifests\scre..tion_b15b0581876c57b7_0014.0002_none_c0293d15f4b866b6.cdf-ms | binary | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Apps\2.0\MVW61E9L.96T\OWAMHMT3.XEL\manifests\scre..tion_b15b0581876c57b7_0014.0002_none_c0293d15f4b866b6.manifest | xml | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Local\Temp\Deployment\HPHTBJKG.8QC\A4NTQZ02.OCX.application | xml | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2989C0A878FE45C610C8177194428257 | binary | |
MD5:— | SHA256:— | |||
| 3560 | dfsvc.exe | C:\Users\admin\AppData\Roaming\Microsoft\Crypto\RSA\S-1-5-21-1302019708-1500728564-335382590-1000\932a2db58c237abd381d22df4c63a04a_90059c37-1320-41a4-b58d-2b75a9850d2f | dbf | |
MD5:D2DED43CE07BFCE4D1C101DFCAA178C8 | SHA256:8EEE9284E733B9D4F2E5C43F71B81E27966F5CD8900183EB3BB77A1F1160D050 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
3560 | dfsvc.exe | GET | 200 | 104.18.11.39:80 | http://cacerts.digicert.com/DigiCertSHA2AssuredIDCodeSigningCA.crt | US | der | 1.30 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3560 | dfsvc.exe | 107.173.192.146:443 | tssupport.us | ColoCrossing | US | unknown |
3504 | ScreenConnect.ClientService.exe | 107.173.192.146:8041 | tssupport.us | ColoCrossing | US | unknown |
3560 | dfsvc.exe | 104.18.11.39:80 | cacerts.digicert.com | Cloudflare Inc | US | shared |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3828 | gup.exe | 104.21.26.128:443 | notepad-plus-plus.org | Cloudflare Inc | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
tssupport.us |
| unknown |
cacerts.digicert.com |
| whitelisted |
notepad-plus-plus.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |