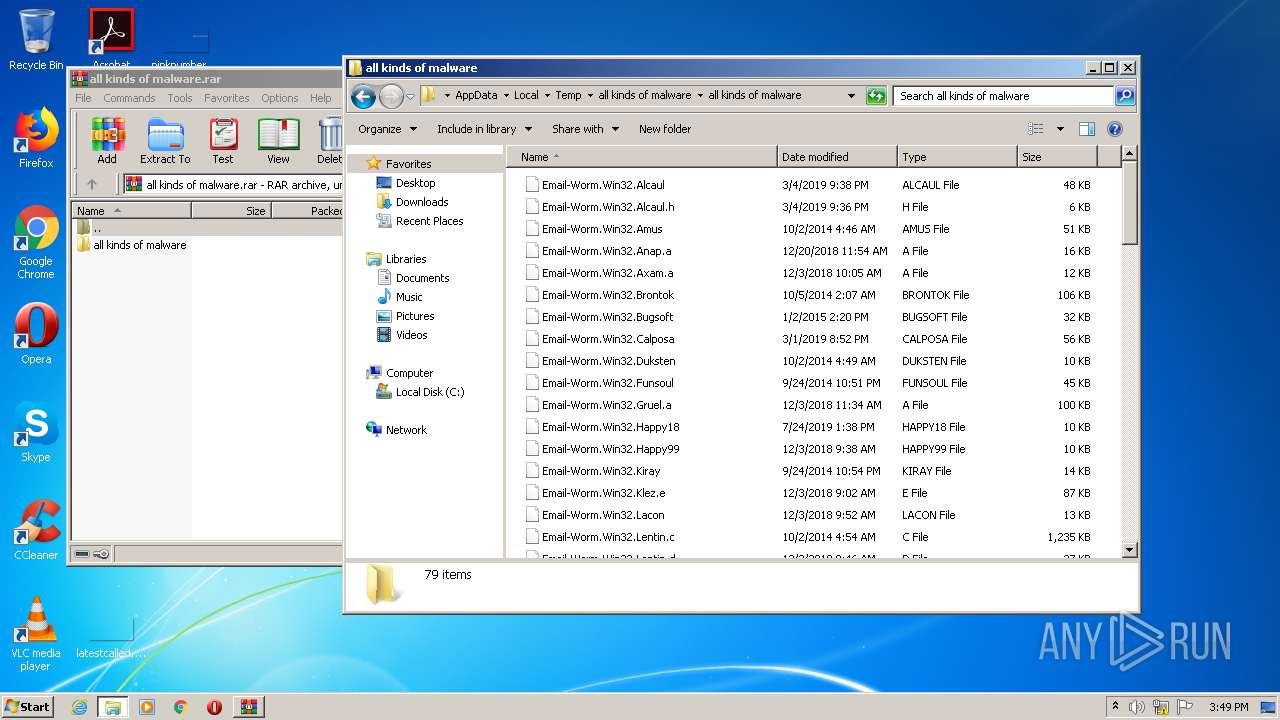
| File name: | all kinds of malware.rar |
| Full analysis: | https://app.any.run/tasks/52c21621-4deb-4caf-a3a9-f1b5322f0be0 |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 14:48:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E05E357F1533DA10E3E074AE6F3856FC |
| SHA1: | 9FBA9C014E83D2735D09B304D80668D736CA257C |
| SHA256: | A03D4D762D0099E1D55C252503A2EB5598CFF9B657EC9BF91E9D7173E660596B |
| SSDEEP: | 98304:H+oFIxSh4w9NnpTVf8JBwxgQ9Dr++rUBvBOstKXvsIQOFi:eoFywtTV0tQJ++QBzmsIQO0 |
MALICIOUS
Application was dropped or rewritten from another process
- Email-Worm.Win32.White.exe (PID: 2984)
- Trojan.Rootkit.exe (PID: 3396)
- Trojan.Win32.Malantern.exe (PID: 548)
- Virus.Win32.Rigel.exe (PID: 3440)
- Virus.Win32.Savior.exe (PID: 3492)
- Virus.Win32.Yerg.exe (PID: 944)
- Virus.Win32.Saynob.exe (PID: 1964)
- Virus.Win32.ZHymn.exe (PID: 2956)
- Virus.Win32.exe (PID: 2888)
- Virus.Win32.CTX.exe (PID: 2944)
- Email-Worm.Win32.ZippedFiles.exe (PID: 3888)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3452)
- cmd.exe (PID: 2624)
- Virus.Win32.Savior.exe (PID: 3492)
- Virus.Win32.exe (PID: 2888)
Removes files from Windows directory
- Trojan.Win32.Malantern.exe (PID: 548)
Creates files in the program directory
- Email-Worm.Win32.ZippedFiles.exe (PID: 3888)
INFO
Manual execution by user
- cmd.exe (PID: 2624)
- Email-Worm.Win32.White.exe (PID: 2984)
- Trojan.Rootkit.exe (PID: 3396)
- rundll32.exe (PID: 1072)
- Virus.Win32.Rigel.exe (PID: 3440)
- Virus.Win32.Savior.exe (PID: 3492)
- Trojan.Win32.Malantern.exe (PID: 548)
- Virus.Win32.Yerg.exe (PID: 944)
- Virus.Win32.Saynob.exe (PID: 1964)
- Virus.Win32.ZHymn.exe (PID: 2956)
- Virus.Win32.exe (PID: 2888)
- ntvdm.exe (PID: 3544)
- Virus.Win32.CTX.exe (PID: 2944)
- Email-Worm.Win32.ZippedFiles.exe (PID: 3888)
- taskmgr.exe (PID: 3200)
Reads Microsoft Office registry keys
- Email-Worm.Win32.ZippedFiles.exe (PID: 3888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
68
Monitored processes
17
Malicious processes
10
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 548 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Trojan.Win32.Malantern.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Trojan.Win32.Malantern.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IE Security Patch Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 944 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.Yerg.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.Yerg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Paintbrush Exit code: 0 Version: 4.10.1998 Modules
| |||||||||||||||
| 1072 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Trojan.Win32.DesktopPuzzle | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1964 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.Saynob.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.Saynob.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2624 | cmd /c ""C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\rename and runall.bat" " | C:\Windows\system32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2888 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.exe | explorer.exe | ||||||||||||
User: admin Company: littlepeter.com Integrity Level: MEDIUM Description: littlepeter mines Exit code: 0 Version: 1.0.0 Modules
| |||||||||||||||
| 2944 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.CTX.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.CTX.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2956 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.ZHymn.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Virus.Win32.ZHymn.exe | explorer.exe | ||||||||||||
User: admin Company: Корпорация Microsoft Integrity Level: MEDIUM Description: Текстовый редактор "Блокнот" Exit code: 3221225477 Version: 4.10.1998 Modules
| |||||||||||||||
| 2984 | "C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.White.exe" | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.White.exe | — | explorer.exe | |||||||||||
User: admin Company: [P54C]-133mhz Integrity Level: MEDIUM Exit code: 0 Version: 1.01 Modules
| |||||||||||||||
| 3200 | "C:\Windows\system32\taskmgr.exe" /4 | C:\Windows\system32\taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Task Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 053
Read events
1 926
Write events
127
Delete events
0
Modification events
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\all kinds of malware.rar | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3452) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\all kinds of malware | |||
| (PID) Process: | (944) Virus.Win32.Yerg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
165
Suspicious files
14
Text files
4
Unknown types
69
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Calposa | executable | |
MD5:492CB47D844368063828CD74C5185A1F | SHA256:2DA40E5D2F7D2174E4F1558BEDC7FBDBF46714813D94C5DE8D77D6CFE1843A38 | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Amus | executable | |
MD5:47ABD68080EEE0EA1B95AE31968A3069 | SHA256:B5FC4FD50E4BA69F0C8C8E5C402813C107C605CAB659960AC31B3C8356C4E0EC | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Axam.a | executable | |
MD5:0FBF8022619BA56C545B20D172BF3B87 | SHA256:4AE7D63EC497143C2ACDE1BA79F1D9EED80086A420B6F0A07B1E2917DA0A6C74 | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Alcaul.h | executable | |
MD5:B994A4BAC6126F3C09DC202AB98ACF1E | SHA256:0CAE69E5A68182AB60562F5ED565FC453E85C0DED1D9D70BF7E285A9CCEEBD3C | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Alcaul | executable | |
MD5:D74CF2CA9982E477D22CF32FE5DA49DC | SHA256:EC82B3817A7BEAA6DB6AB3274F0B20F82392E16CD8A7F4A303AF5776DD077FB9 | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Duksten | executable | |
MD5:900EBFF3E658825F828AB95B30FAD2E7 | SHA256:CAEC6E664B3CFF5717DD2EFEA8DCD8715ABDCFE7F611456BE7009771F22A8F50 | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Klez.e | executable | |
MD5:F2DB87B351770E5995E9FCAAD47D9591 | SHA256:3113FA9A3CF00ED423A2C686A2FFB19586F6A047747DE65A93436A7DCA8FCFA7 | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Funsoul | executable | |
MD5:A13A4DB860D743A088EF7AB9BACB4DDA | SHA256:69EE59CEE5A1D39739D935701CFA917F75787B29E0B9BDA9ADA9E2642ADE434C | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Magistr.a | executable | |
MD5:9890349FE3C68F5923B29347BBA021A4 | SHA256:068F2EE28AF7645DBF2A1684F0A5FC5CCB6AA1027F71DA4468E0CBA56C65E058 | |||
| 3452 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\all kinds of malware\all kinds of malware\Email-Worm.Win32.Lentin.d | executable | |
MD5:D9CE0273F791DA275ED2A69446413A87 | SHA256:AA2E8D70654E30CF11E2B57E92CEA72A9823A048F75FC9029DA04E1E4D8A9810 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
Trojan.Rootkit.exe | sssssssssss |