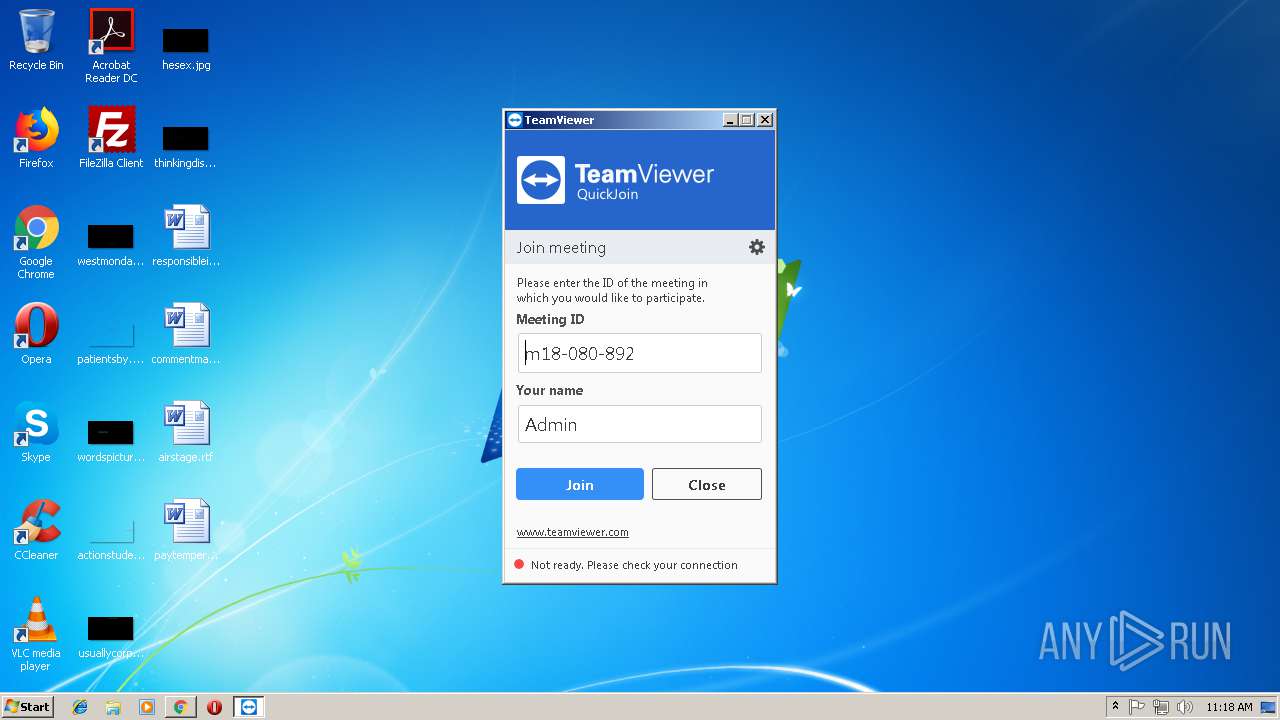
| URL: | https://dl.tvcdn.de/download/version_14x/teamviewerqj-idm18080892.exe |
| Full analysis: | https://app.any.run/tasks/a1071c8e-c7a5-4cfc-87fa-a4738e9da3b2 |
| Verdict: | Malicious activity |
| Analysis date: | March 01, 2019, 11:17:13 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | CD3663C49A34C5DC8784C799EE2DA95F |
| SHA1: | F73D8E06771F74A87377B9D634B6DE2CA8F754D7 |
| SHA256: | 9FD65413211213E583D3E636D2A3CCF74D4B08BFB6121BEBF7A3272F2FDA2B27 |
| SSDEEP: | 3:N8RJGBJvBKL1KQmJXXdE:2vGBbjJHdE |
MALICIOUS
Application was dropped or rewritten from another process
- teamviewerqj-idm18080892.exe (PID: 2420)
- TeamViewer.exe (PID: 4072)
- TeamViewer.exe (PID: 3648)
Loads dropped or rewritten executable
- TeamViewer.exe (PID: 3648)
- teamviewerqj-idm18080892.exe (PID: 2420)
- TeamViewer.exe (PID: 4072)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2856)
- teamviewerqj-idm18080892.exe (PID: 2420)
Application launched itself
- TeamViewer.exe (PID: 4072)
Connects to unusual port
- TeamViewer.exe (PID: 3648)
Creates files in the user directory
- TeamViewer.exe (PID: 4072)
INFO
Application launched itself
- chrome.exe (PID: 2856)
Reads Internet Cache Settings
- chrome.exe (PID: 2856)
Creates files in the user directory
- chrome.exe (PID: 2856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
11
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=916,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=B5BEC40E08977E96D81010F36B607E2B --mojo-platform-channel-handle=1744 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=916,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=E366619680F8F93D0EC4AB9435CD9FE1 --mojo-platform-channel-handle=2532 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2420 | "C:\Users\admin\Downloads\teamviewerqj-idm18080892.exe" | C:\Users\admin\Downloads\teamviewerqj-idm18080892.exe | chrome.exe | ||||||||||||
User: admin Company: TeamViewer Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --service-pipe-token=462F53C907EA550120CE6BD07EAAB4A4 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=462F53C907EA550120CE6BD07EAAB4A4 --renderer-client-id=4 --mojo-platform-channel-handle=1864 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2856 | "C:\Program Files\Google\Chrome\Application\chrome.exe" https://dl.tvcdn.de/download/version_14x/teamviewerqj-idm18080892.exe | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2876 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2860 --on-initialized-event-handle=304 --parent-handle=308 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3132 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=916,1112433181398300262,13346142530850764726,131072 --enable-features=PasswordImport --service-pipe-token=9762D8DE2D11AB440BDA7049356F36C0 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9762D8DE2D11AB440BDA7049356F36C0 --renderer-client-id=3 --mojo-platform-channel-handle=2136 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3604 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=68.0.3440.106 --initial-client-data=0x78,0x7c,0x80,0x74,0x84,0x6f6000b0,0x6f6000c0,0x6f6000cc | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 3648 | "C:\Users\admin\AppData\Local\Temp\TeamViewer\TeamViewer.exe" --dre | C:\Users\admin\AppData\Local\Temp\TeamViewer\TeamViewer.exe | TeamViewer.exe | ||||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: HIGH Description: TeamViewer 14 Exit code: 0 Version: 14.1.18533.0 Modules
| |||||||||||||||
| 4072 | "C:\Users\admin\AppData\Local\Temp\TeamViewer\TeamViewer.exe" | C:\Users\admin\AppData\Local\Temp\TeamViewer\TeamViewer.exe | — | teamviewerqj-idm18080892.exe | |||||||||||
User: admin Company: TeamViewer GmbH Integrity Level: MEDIUM Description: TeamViewer 14 Exit code: 0 Version: 14.1.18533.0 Modules
| |||||||||||||||
Total events
1 685
Read events
1 600
Write events
81
Delete events
4
Modification events
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2876) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2856-13195912659602625 |
Value: 259 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2856-13195912659602625 |
Value: 259 | |||
| (PID) Process: | (2856) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
46
Suspicious files
14
Text files
55
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\5c58e8b0-6630-4497-abec-d7f79b55b71c.tmp | — | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\83a50120-e38e-4287-a903-0d1e5a4242ad.tmp | — | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d764c61c-7cb9-44e5-8903-0ee2d9b0ed44.tmp | — | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF199502.TMP | text | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Service Worker\Database\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2856 | chrome.exe | C:\Users\admin\Downloads\f844aa9e-f09d-4544-8fa9-8e967014ef56.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
13
DNS requests
11
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 91.199.212.52:80 | http://crt.comodoca.com/COMODORSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2856 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 172.217.21.238:443 | sb-ssl.google.com | Google Inc. | US | whitelisted |
2856 | chrome.exe | 216.58.210.3:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3648 | TeamViewer.exe | 37.252.246.104:5938 | router16.teamviewer.com | ANEXIA Internetdienstleistungs GmbH | SK | suspicious |
3648 | TeamViewer.exe | 52.168.20.22:443 | client.teamviewer.com | Microsoft Corporation | US | whitelisted |
2856 | chrome.exe | 13.32.161.218:443 | dl.tvcdn.de | Amazon.com, Inc. | US | unknown |
3648 | TeamViewer.exe | 188.172.246.169:5938 | AT-VIE-ANX-R006.teamviewer.com | ANEXIA Internetdienstleistungs GmbH | AT | suspicious |
— | — | 91.199.212.52:80 | crt.comodoca.com | Comodo CA Ltd | GB | suspicious |
3648 | TeamViewer.exe | 185.188.32.1:5938 | master9.teamviewer.com | TeamViewer GmbH | DE | suspicious |
2856 | chrome.exe | 216.58.207.77:443 | accounts.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
dl.tvcdn.de |
| whitelisted |
www.gstatic.com |
| whitelisted |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
router16.teamviewer.com |
| suspicious |
master9.teamviewer.com |
| shared |
client.teamviewer.com |
| shared |
AT-VIE-ANX-R006.teamviewer.com |
| suspicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3648 | TeamViewer.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TeamViewer connection |
3648 | TeamViewer.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TeamViewer negotiation |
3648 | TeamViewer.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TeamViewer connection |
3648 | TeamViewer.exe | Potential Corporate Privacy Violation | POLICY [PTsecurity] TeamViewer negotiation |