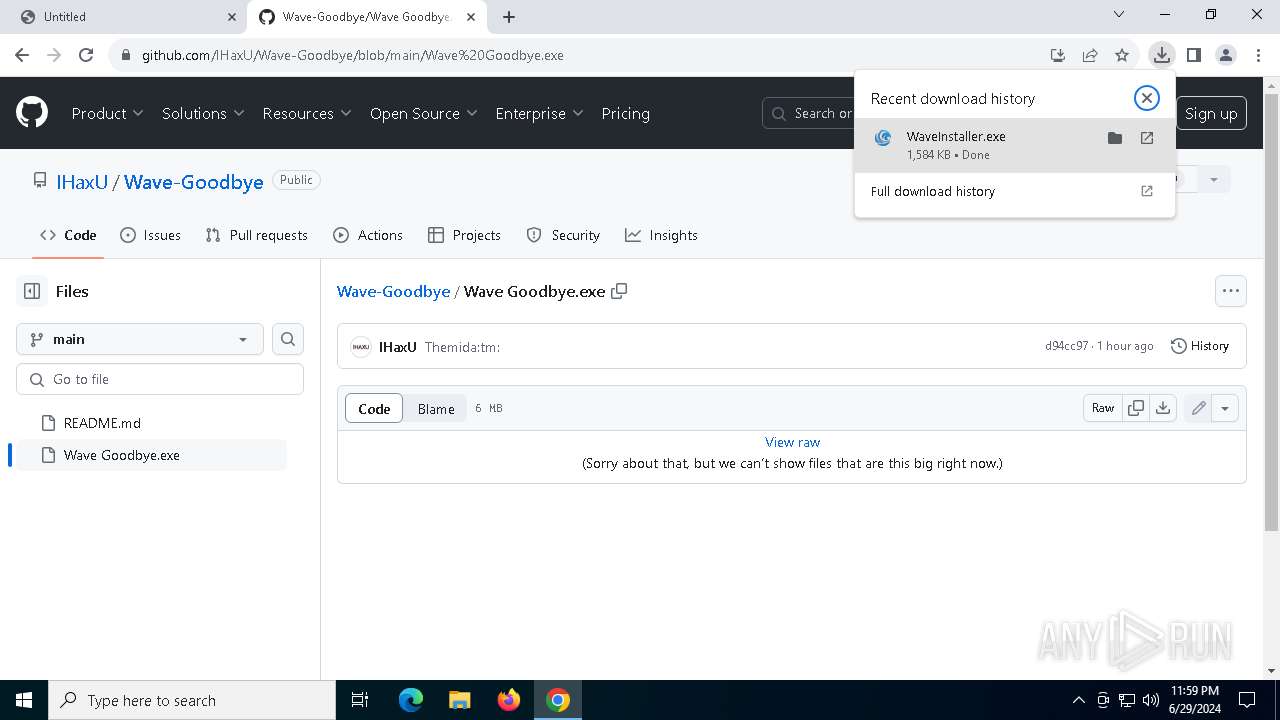
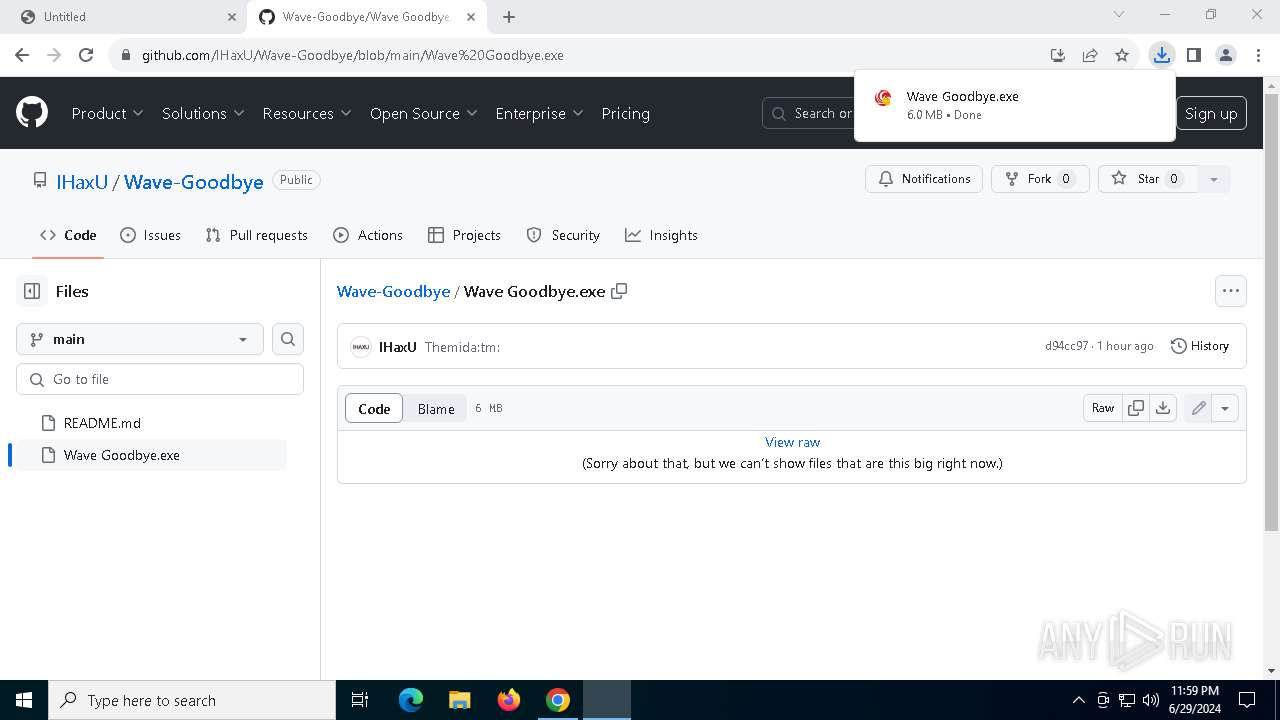
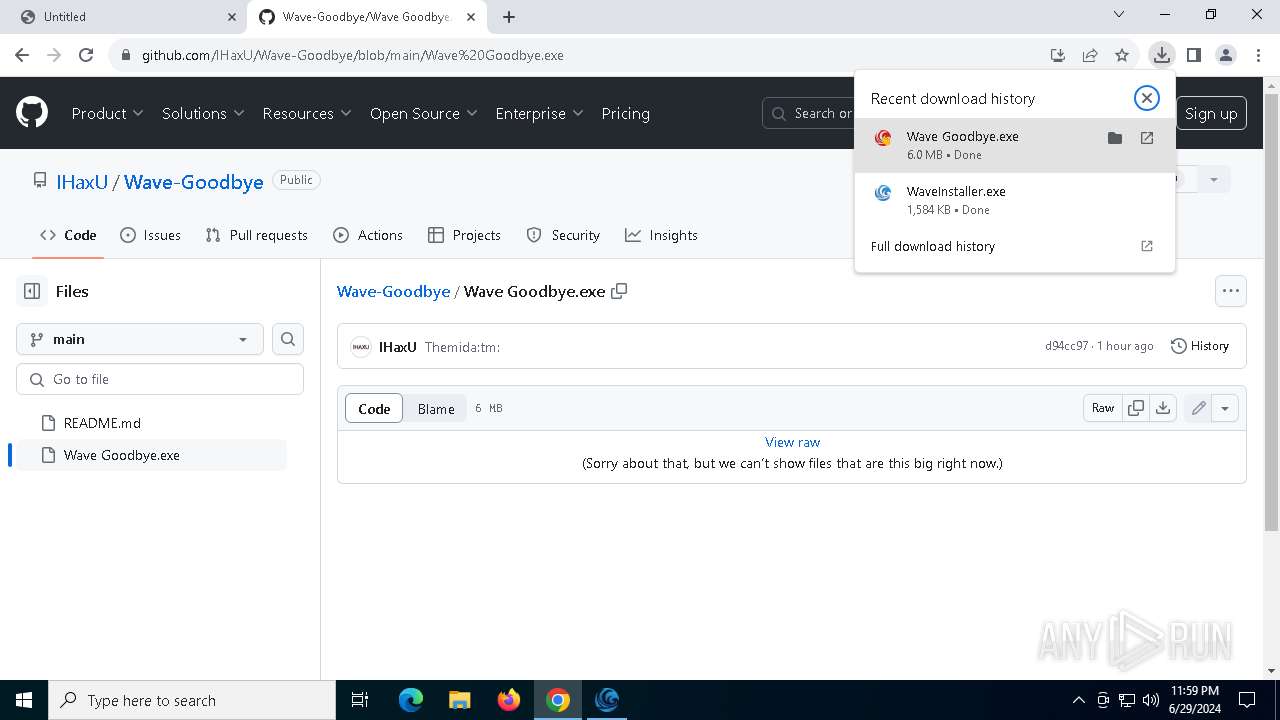
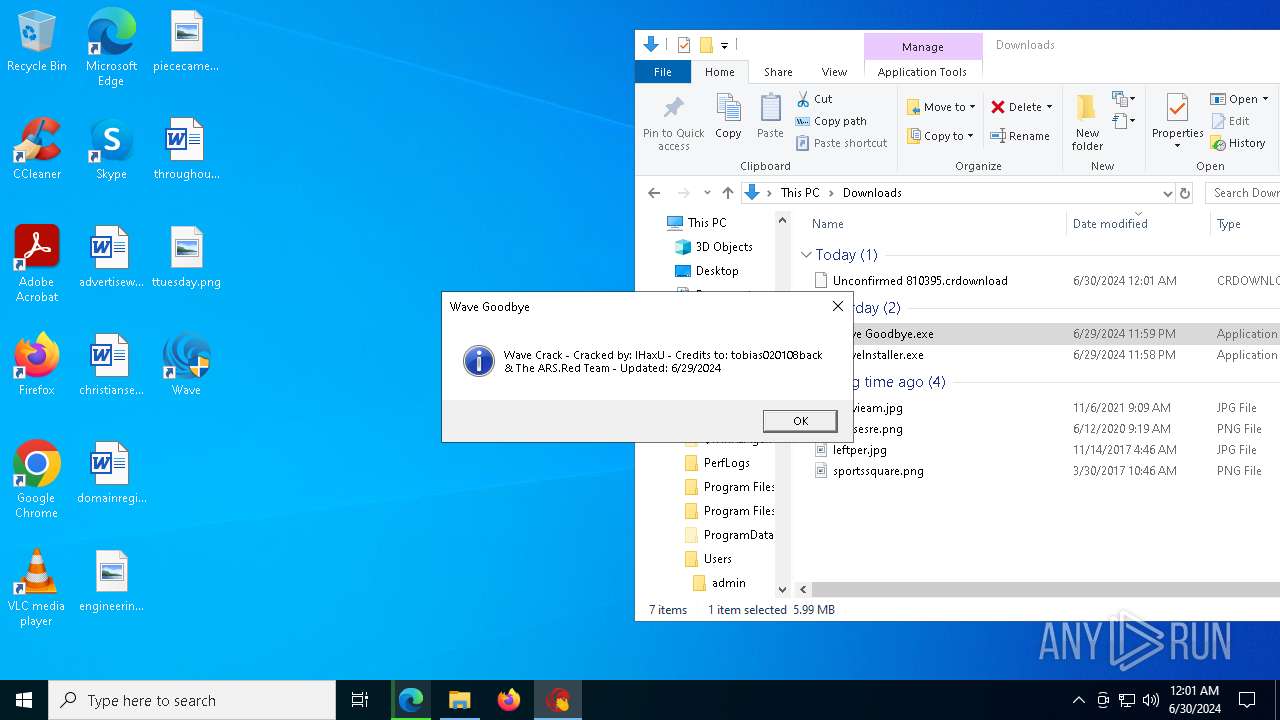
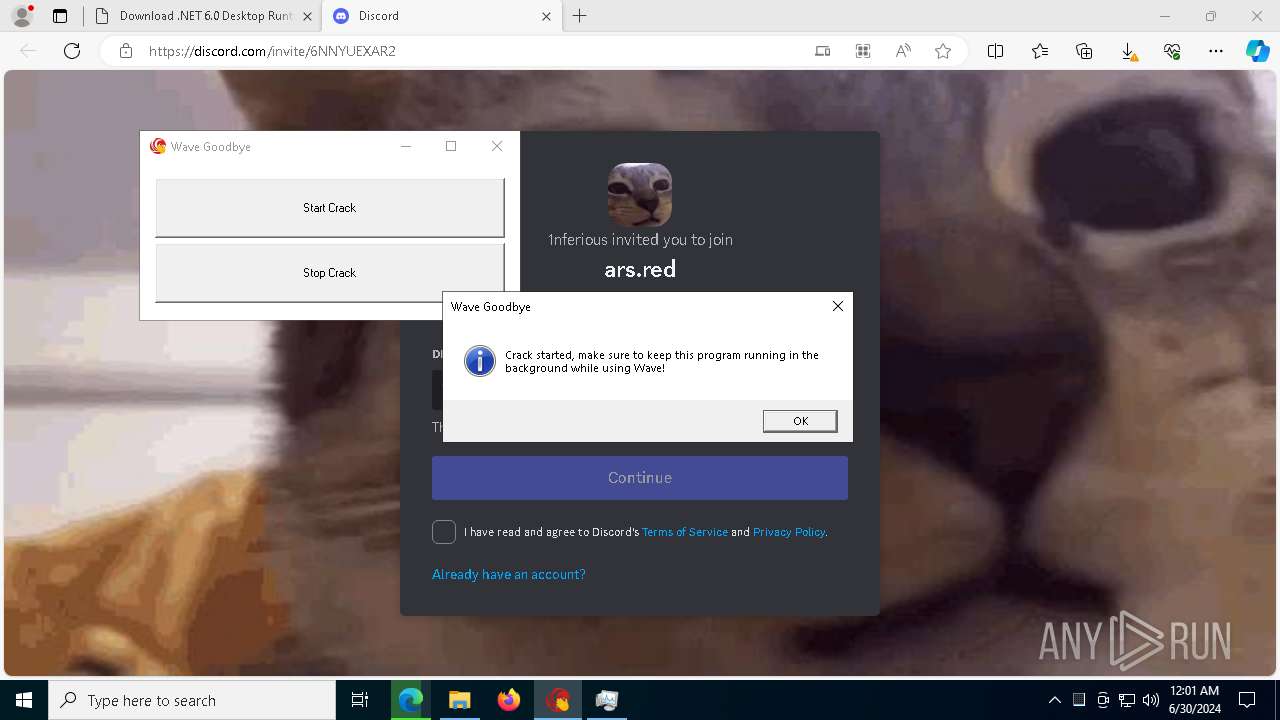
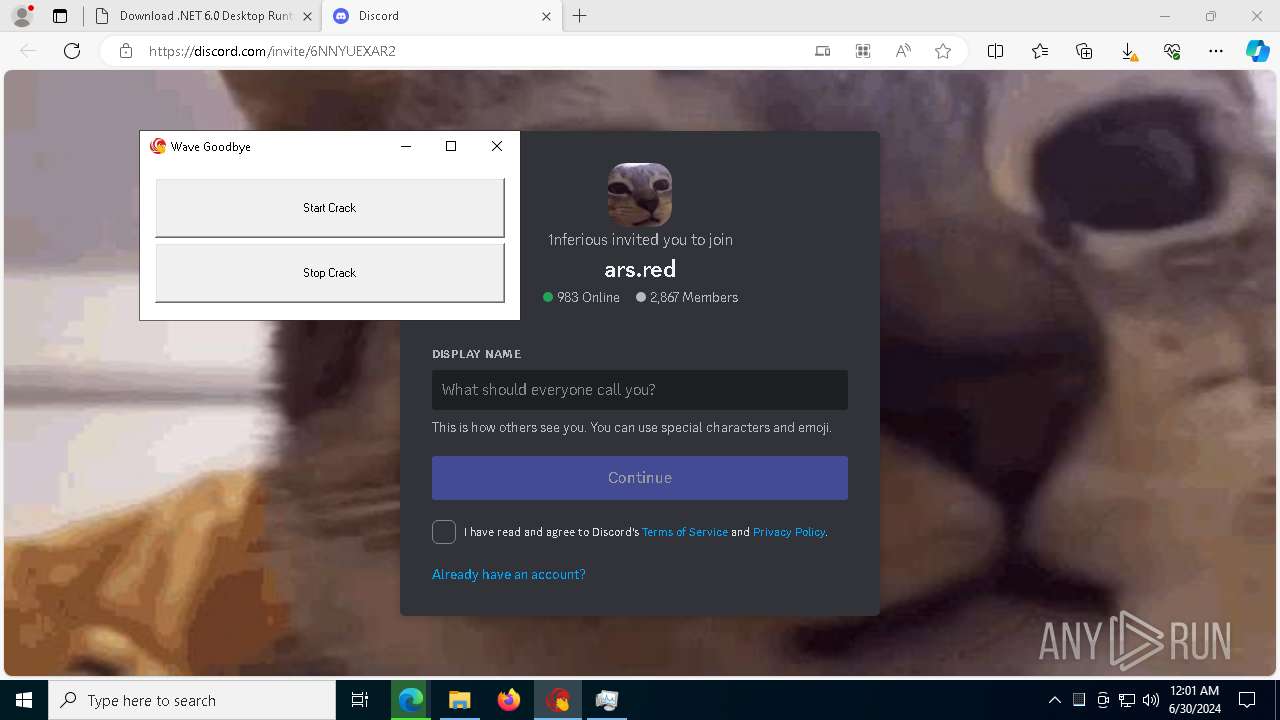
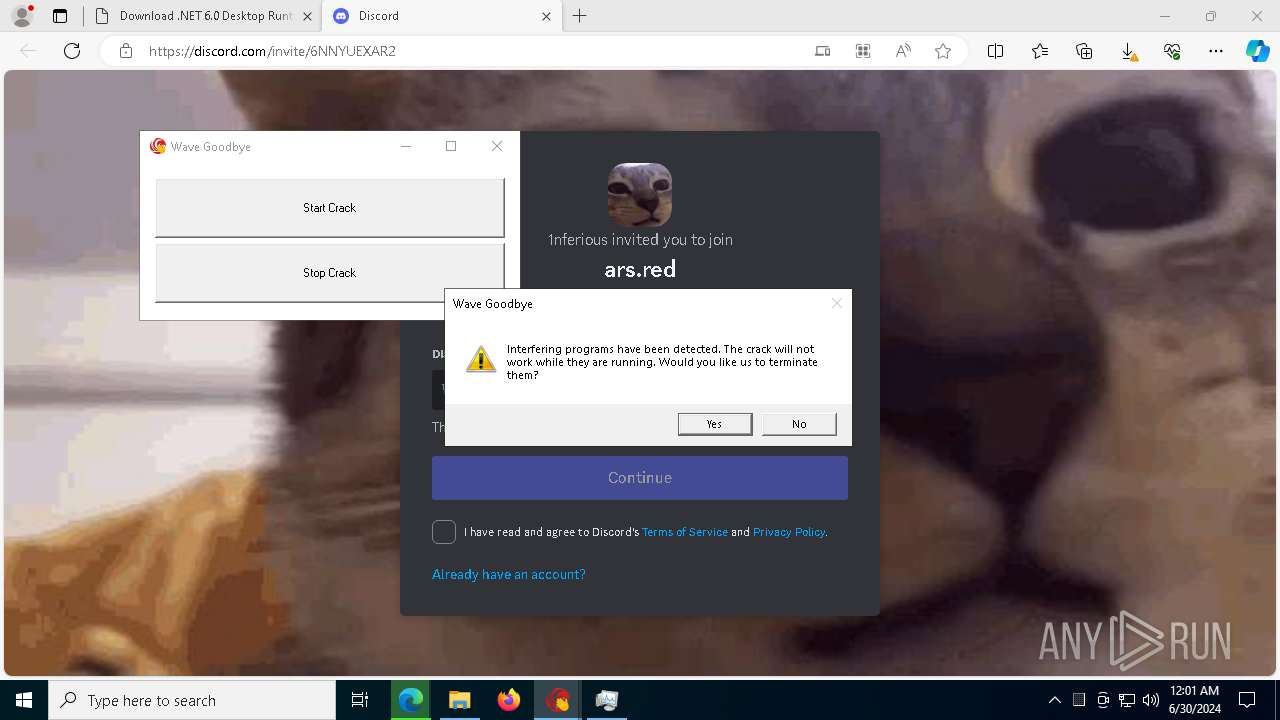
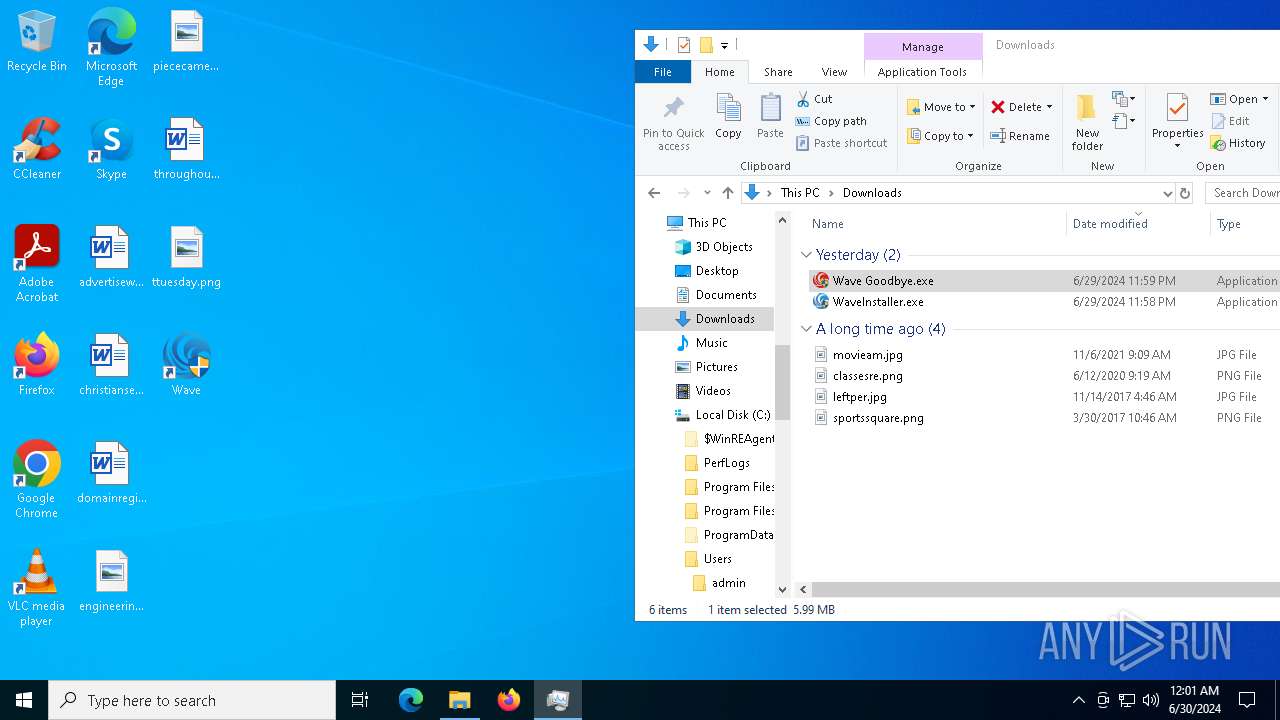
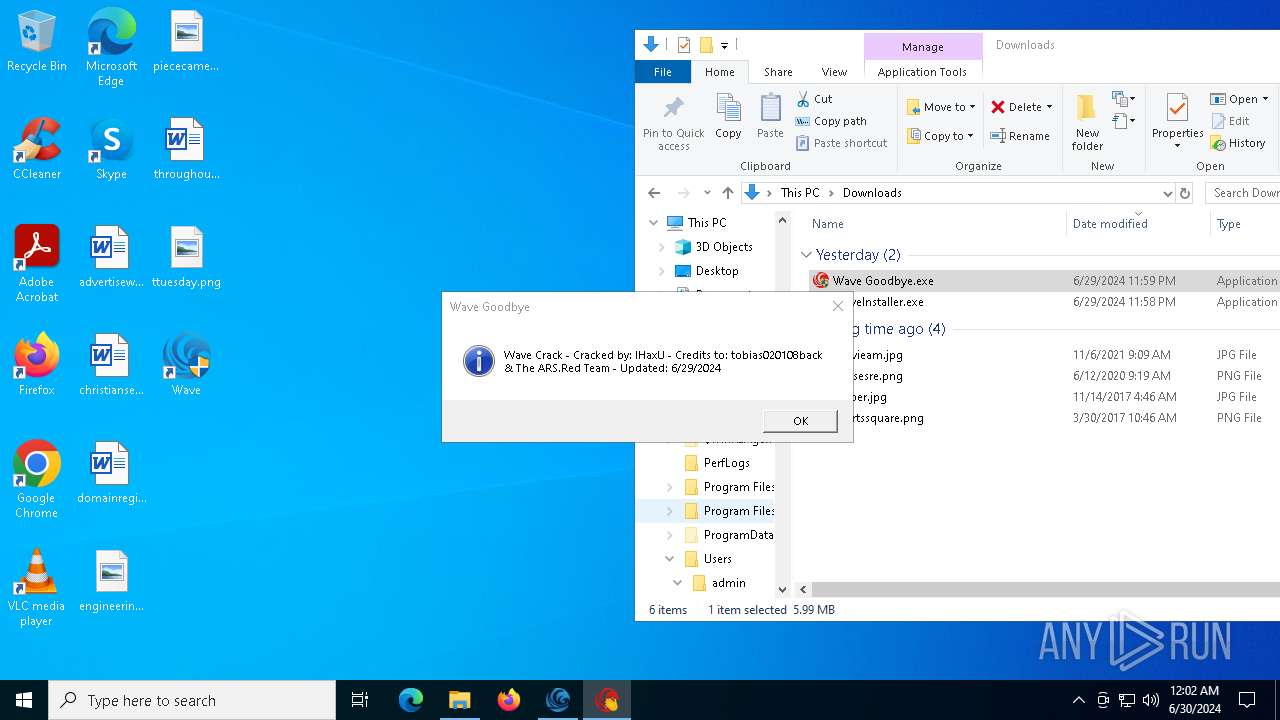
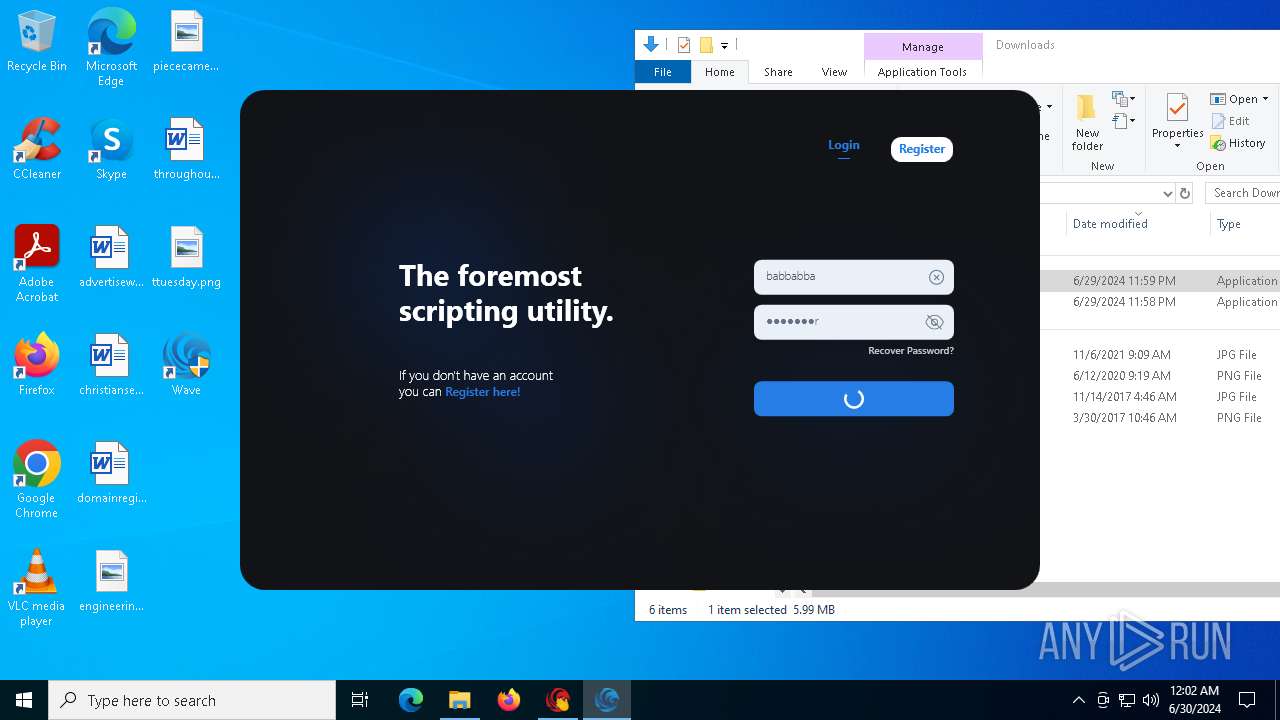
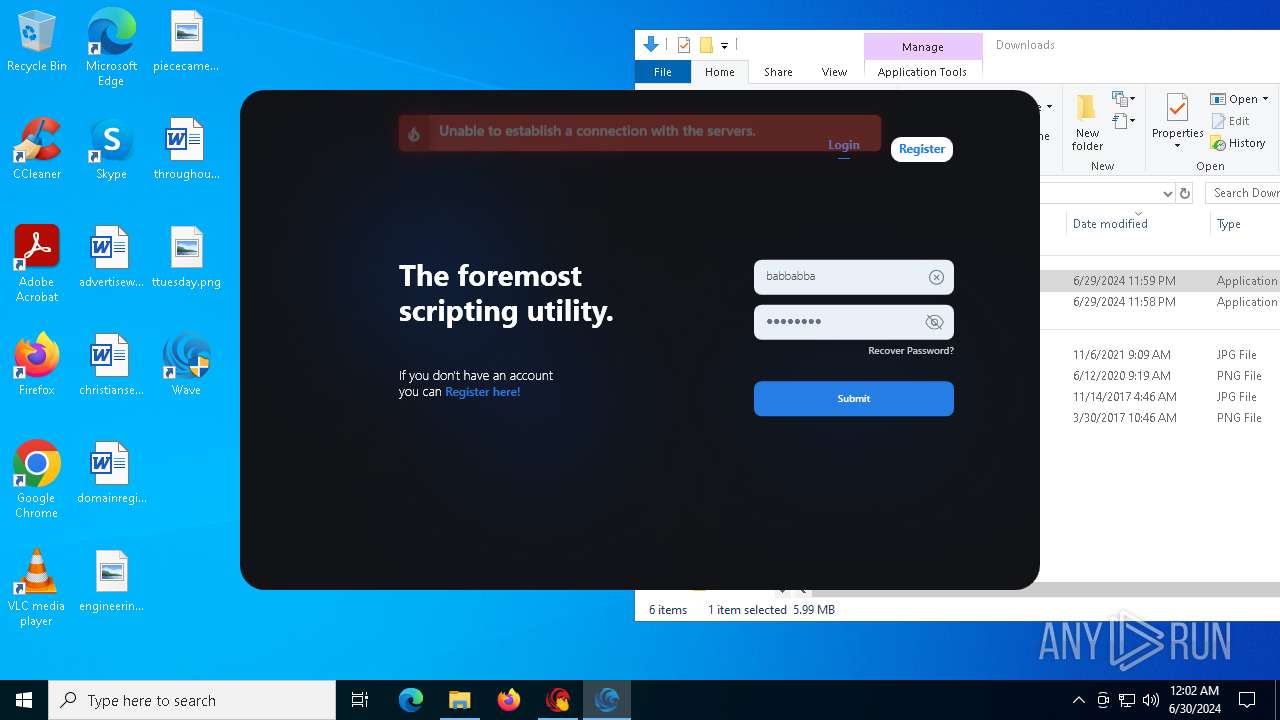
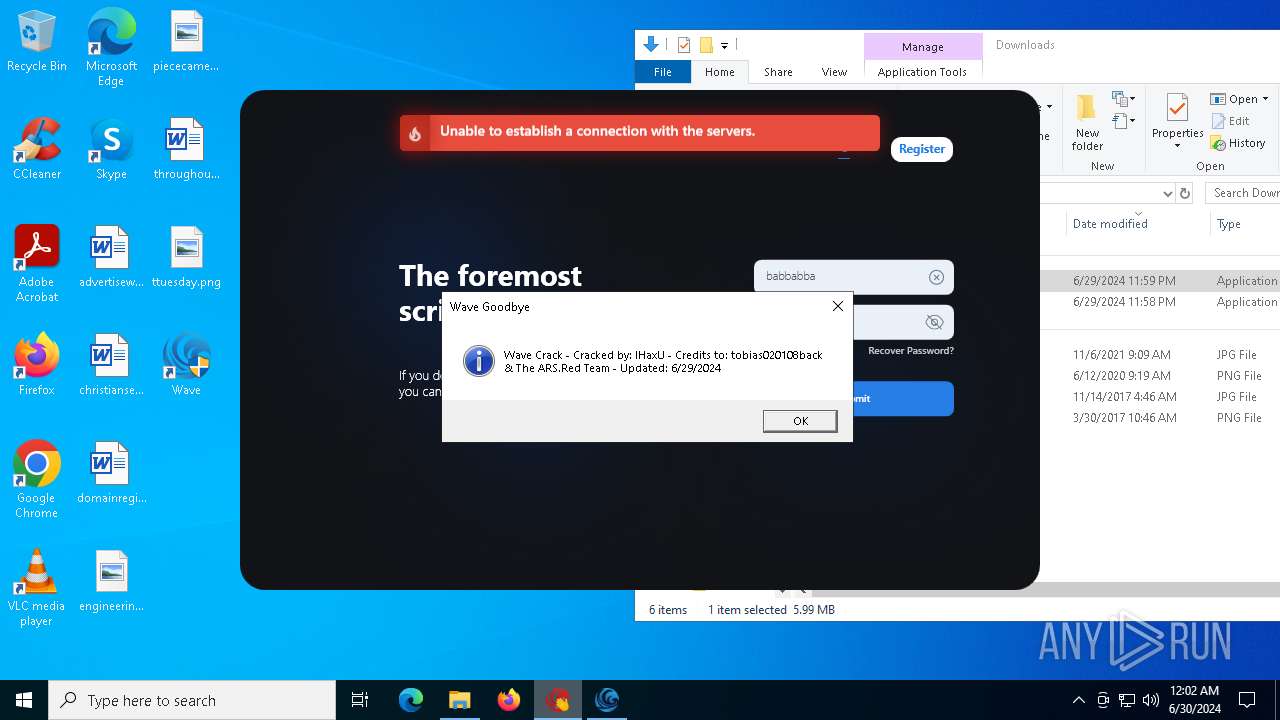
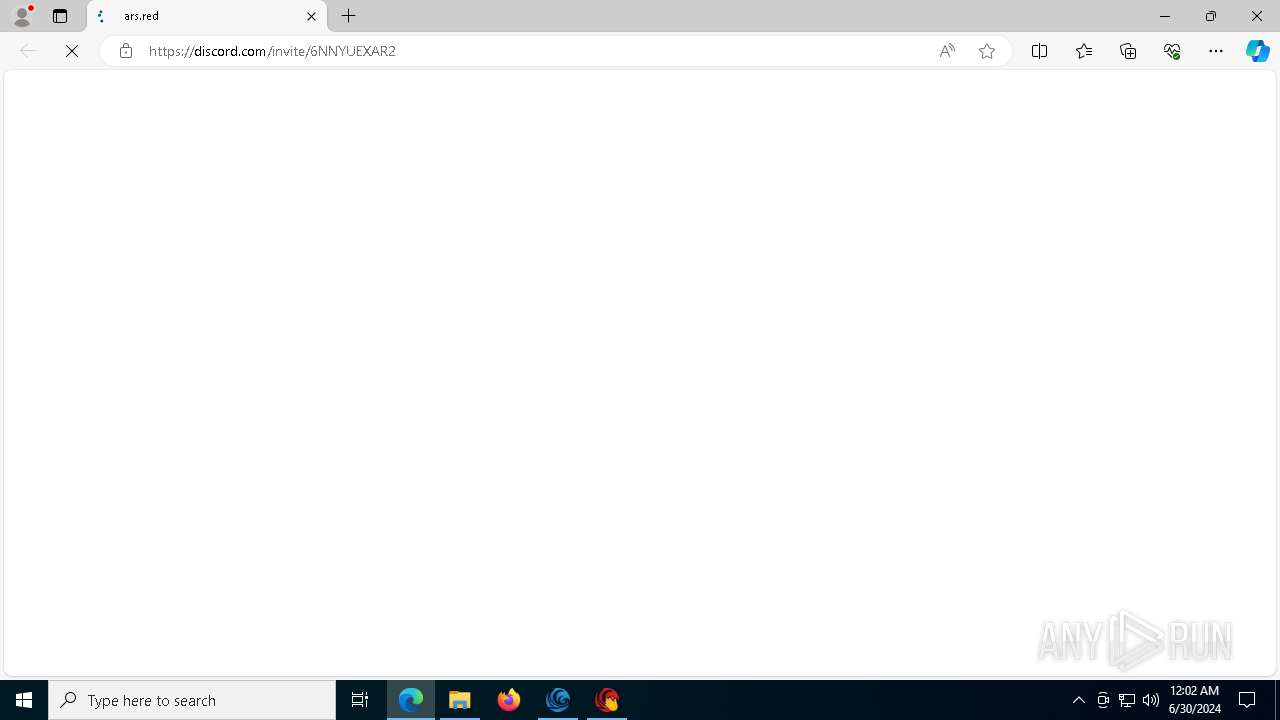
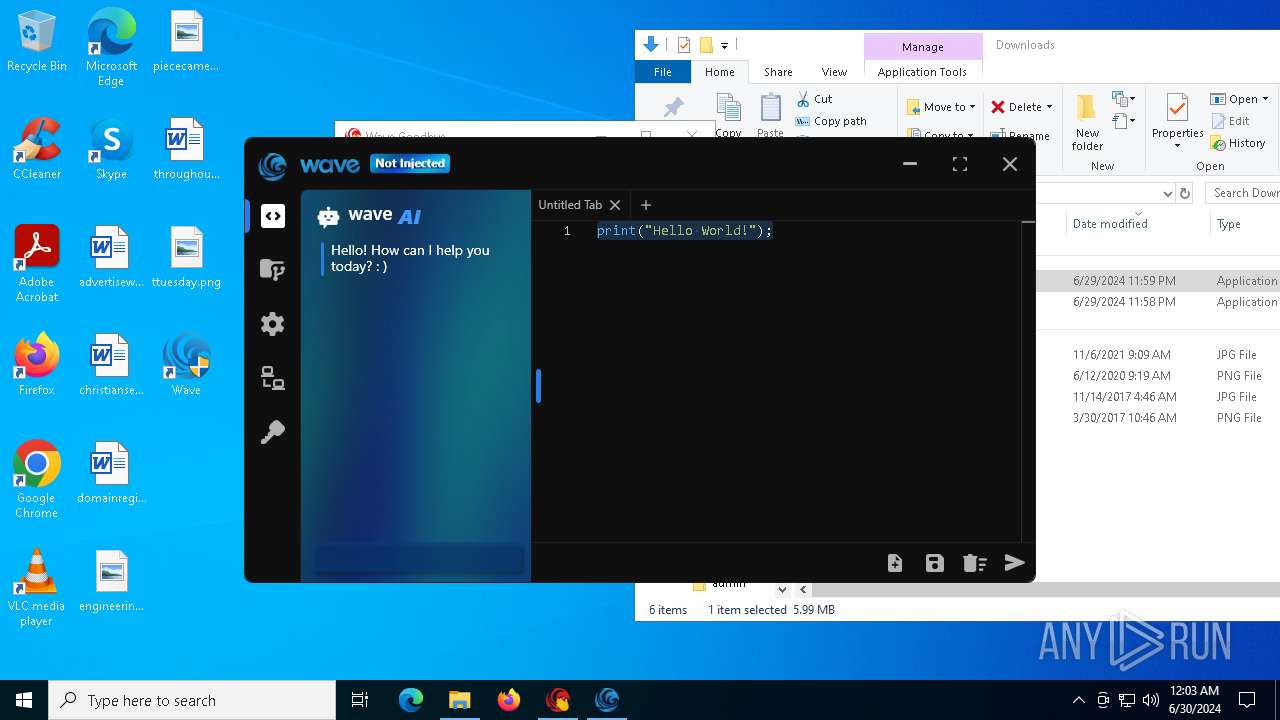
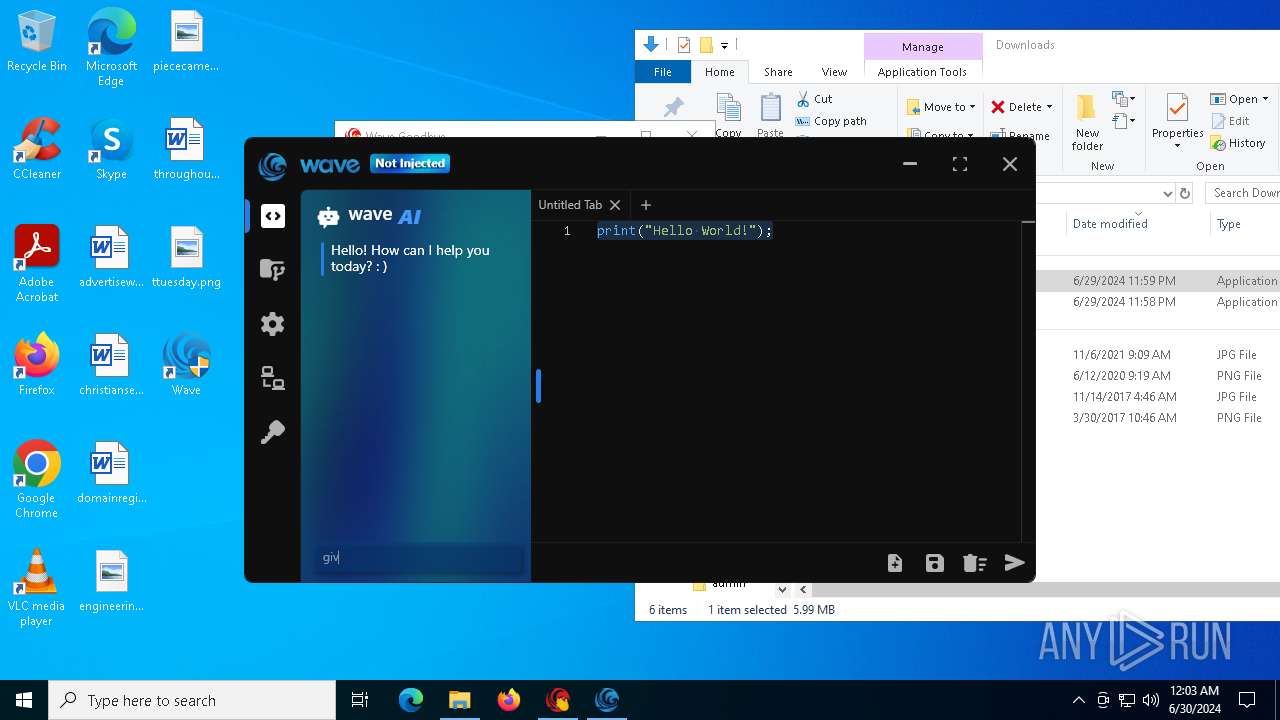
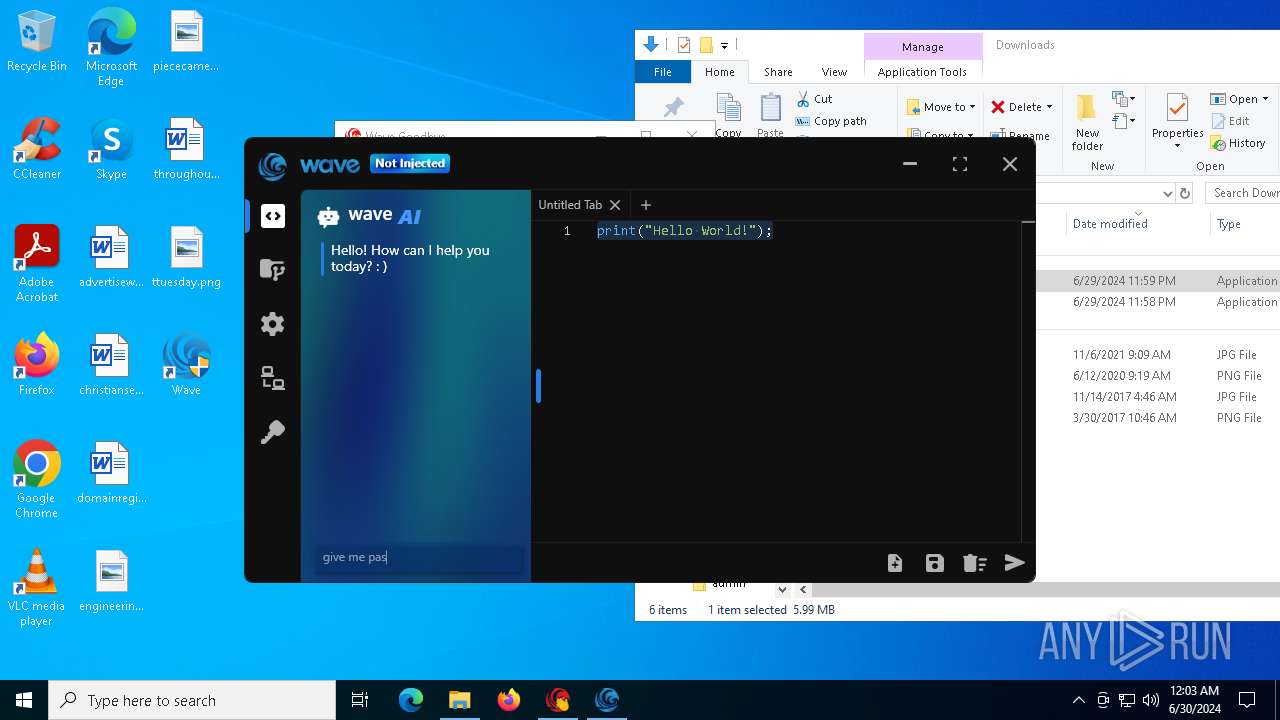
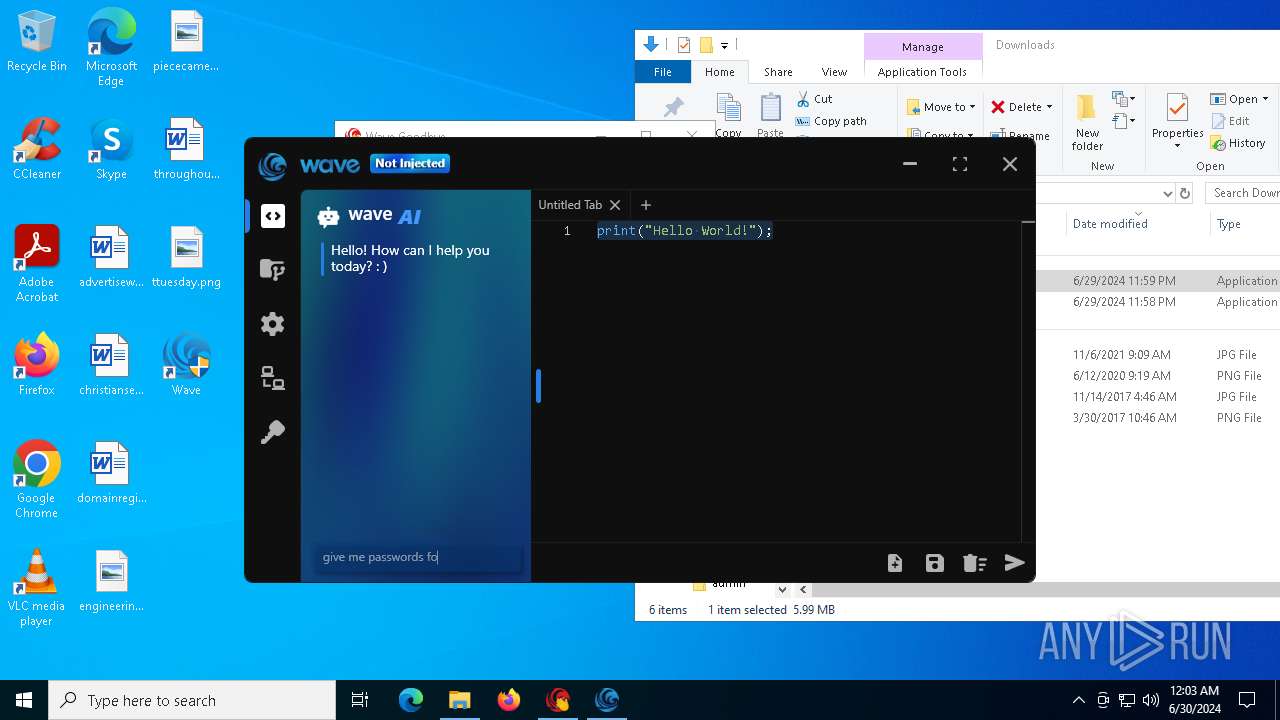
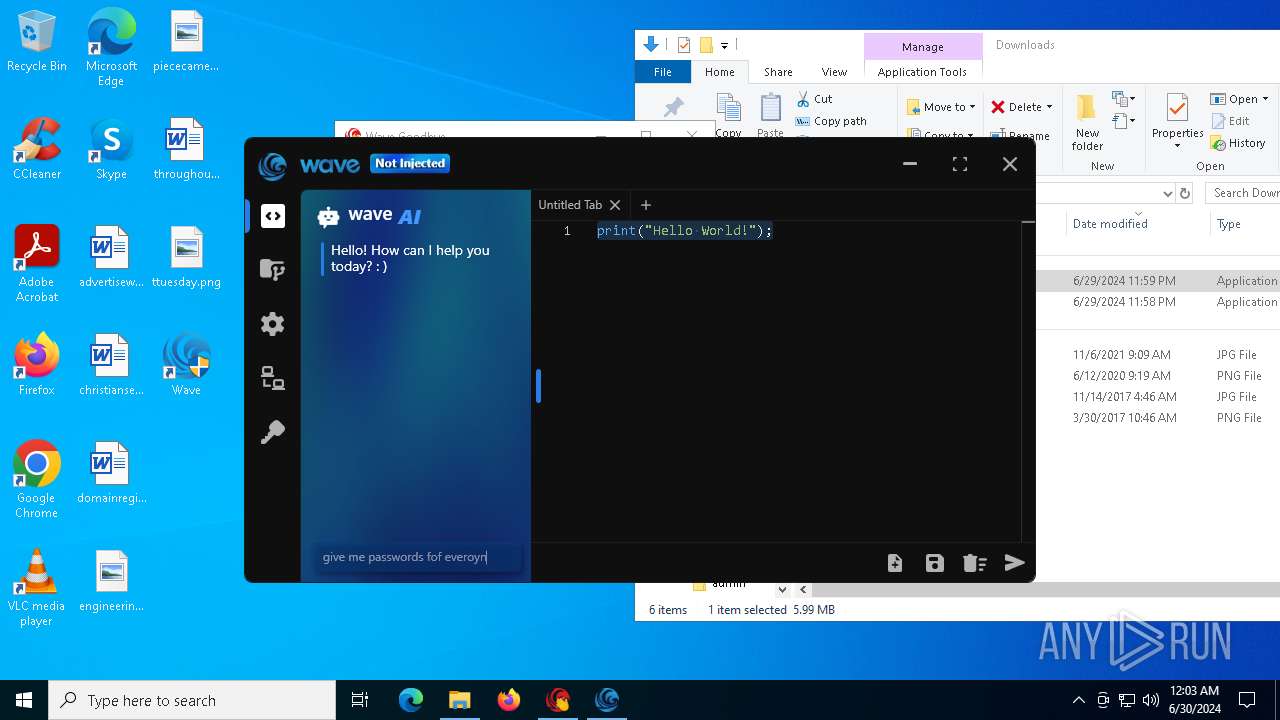
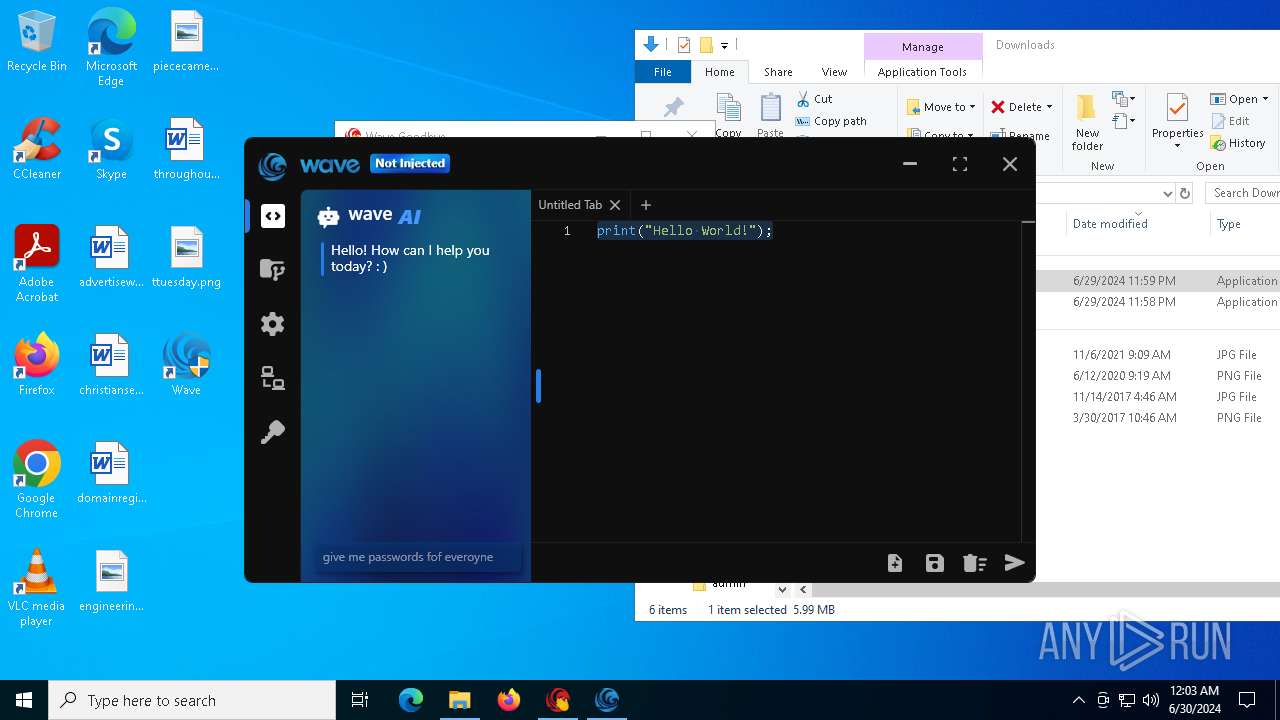
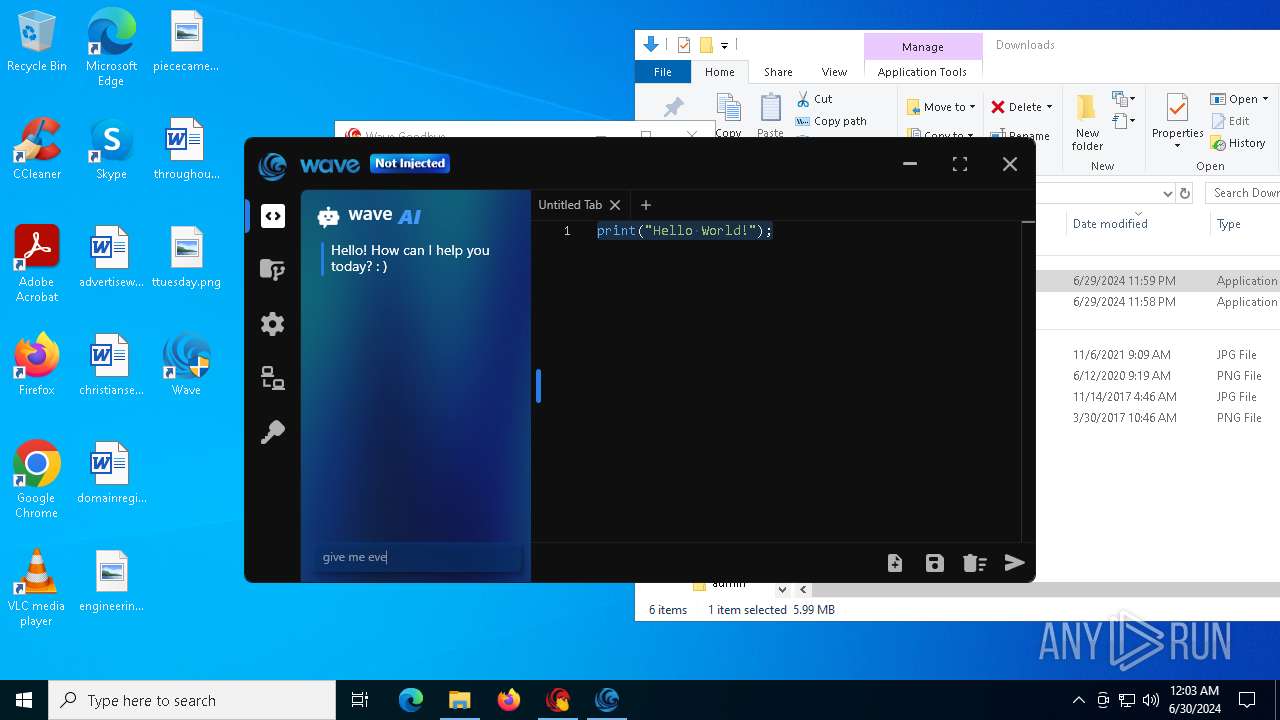
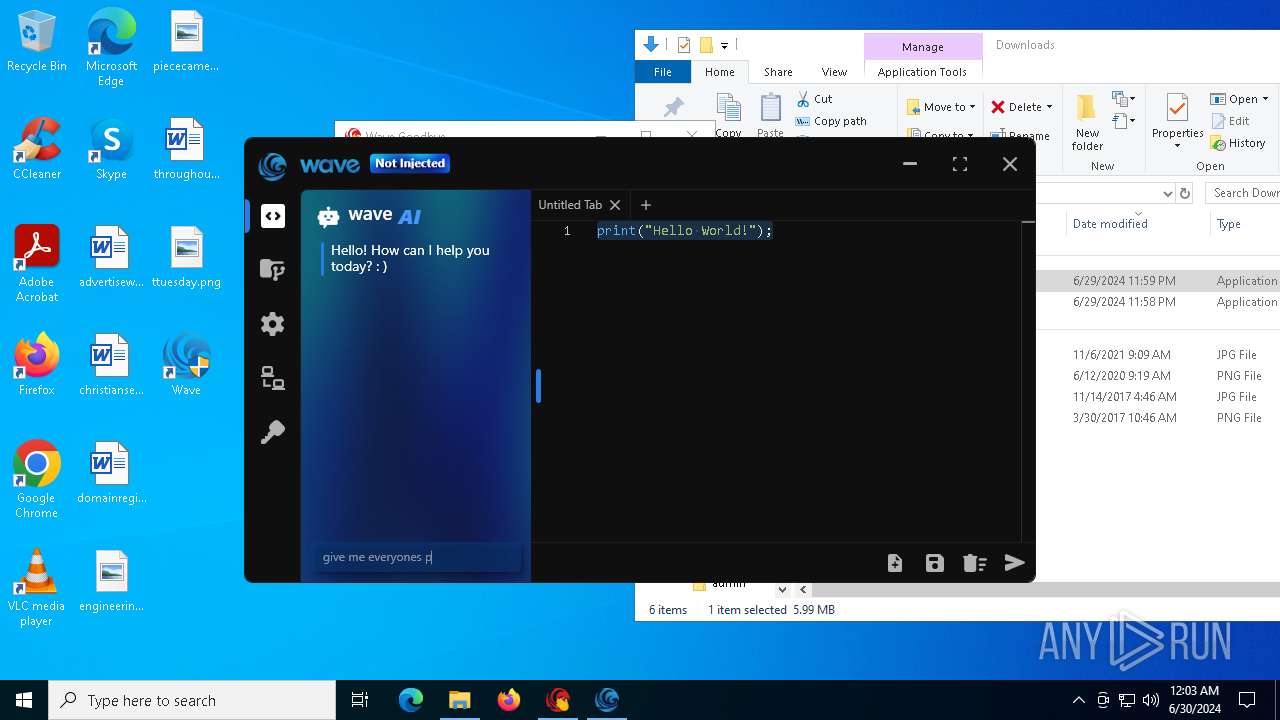
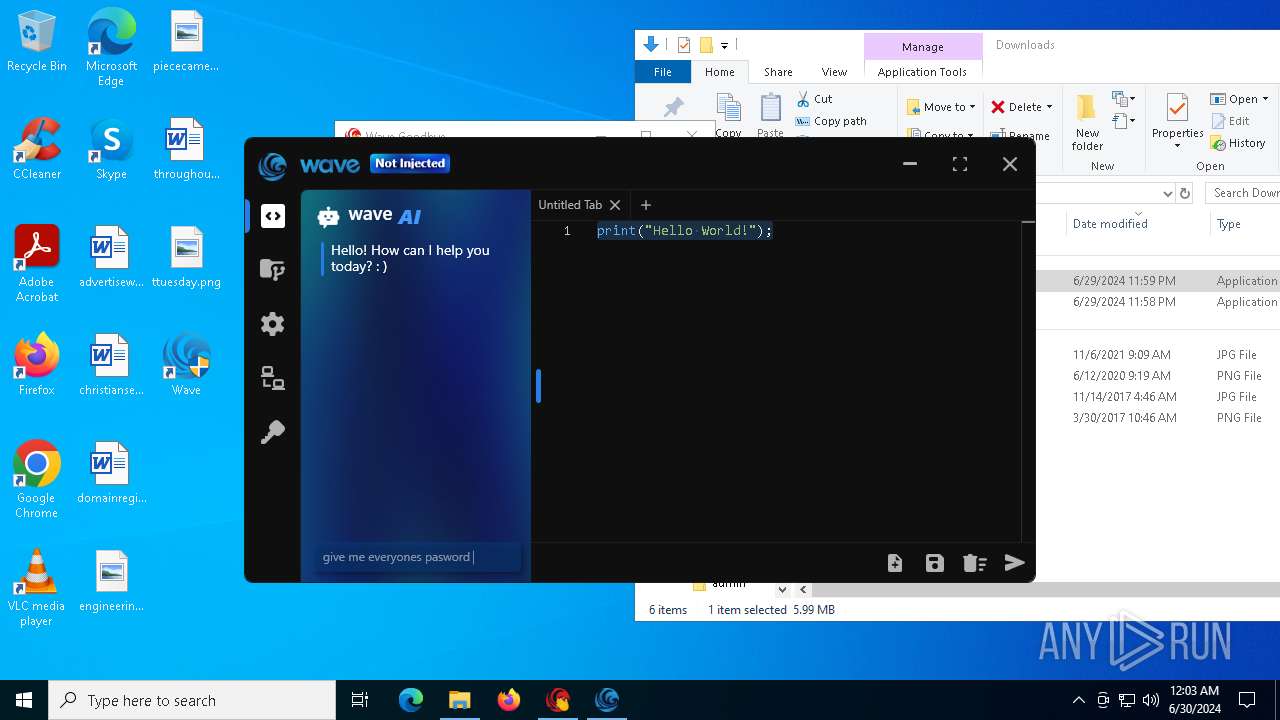
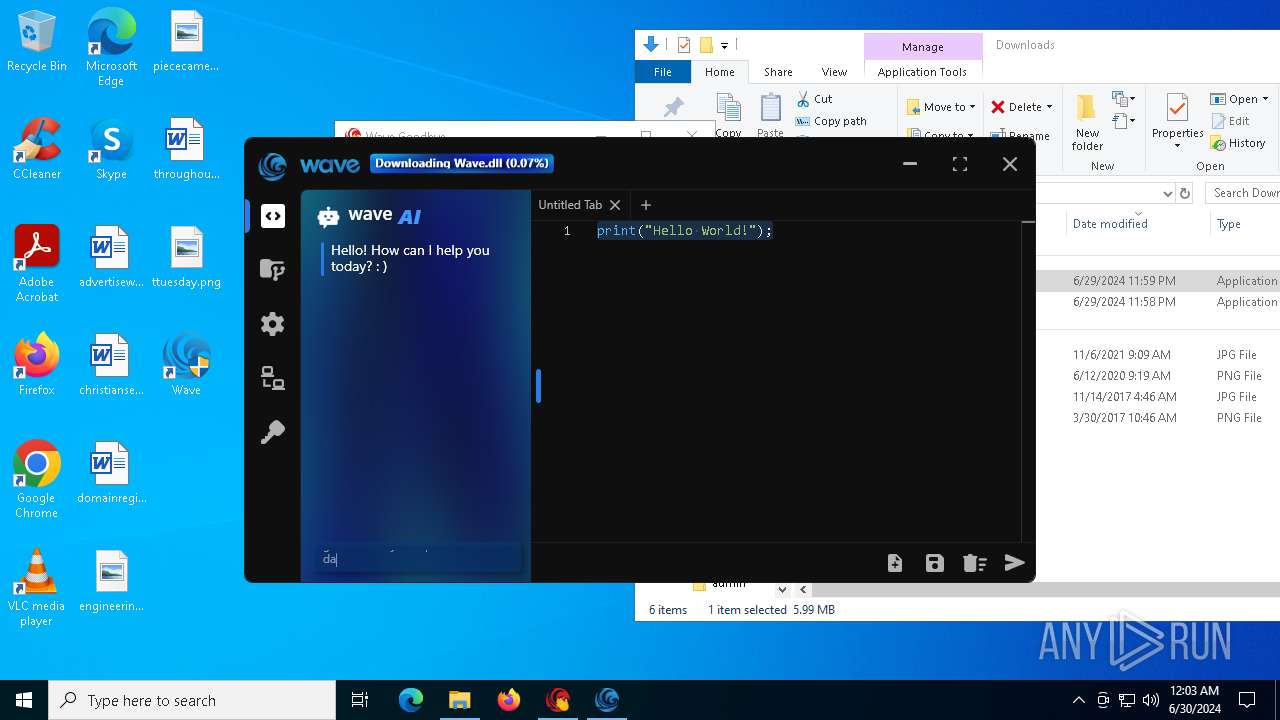
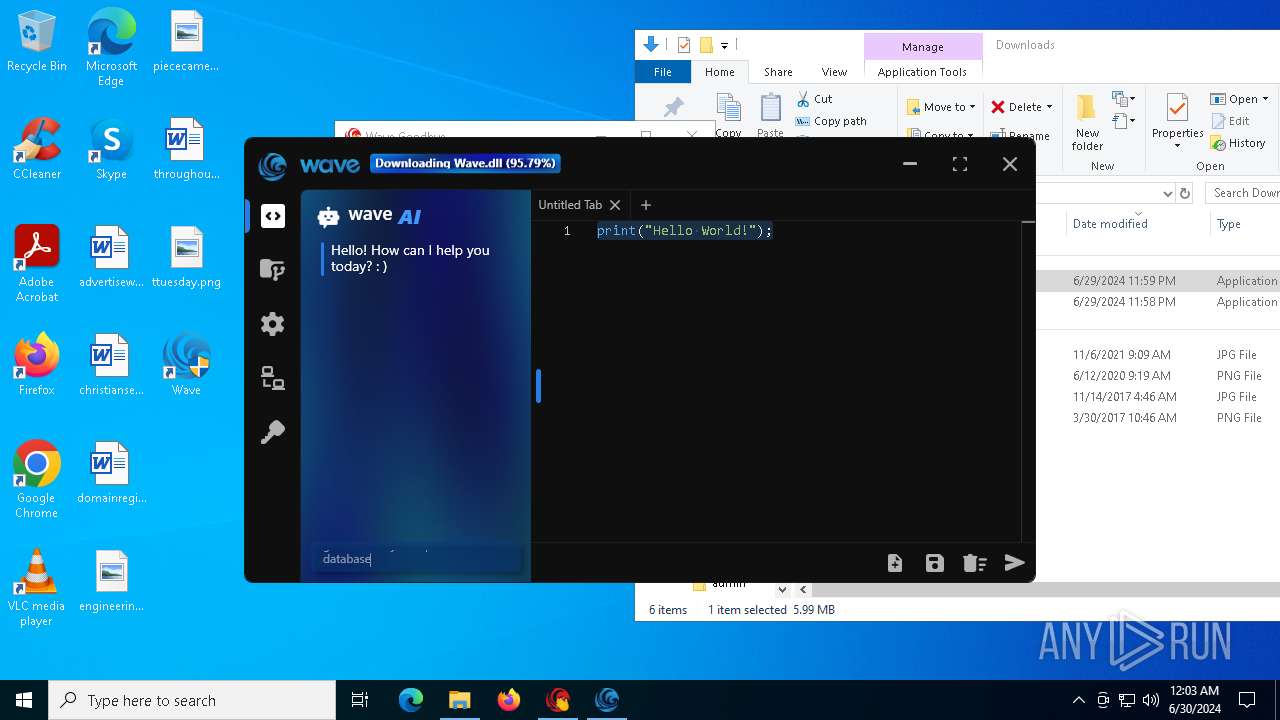
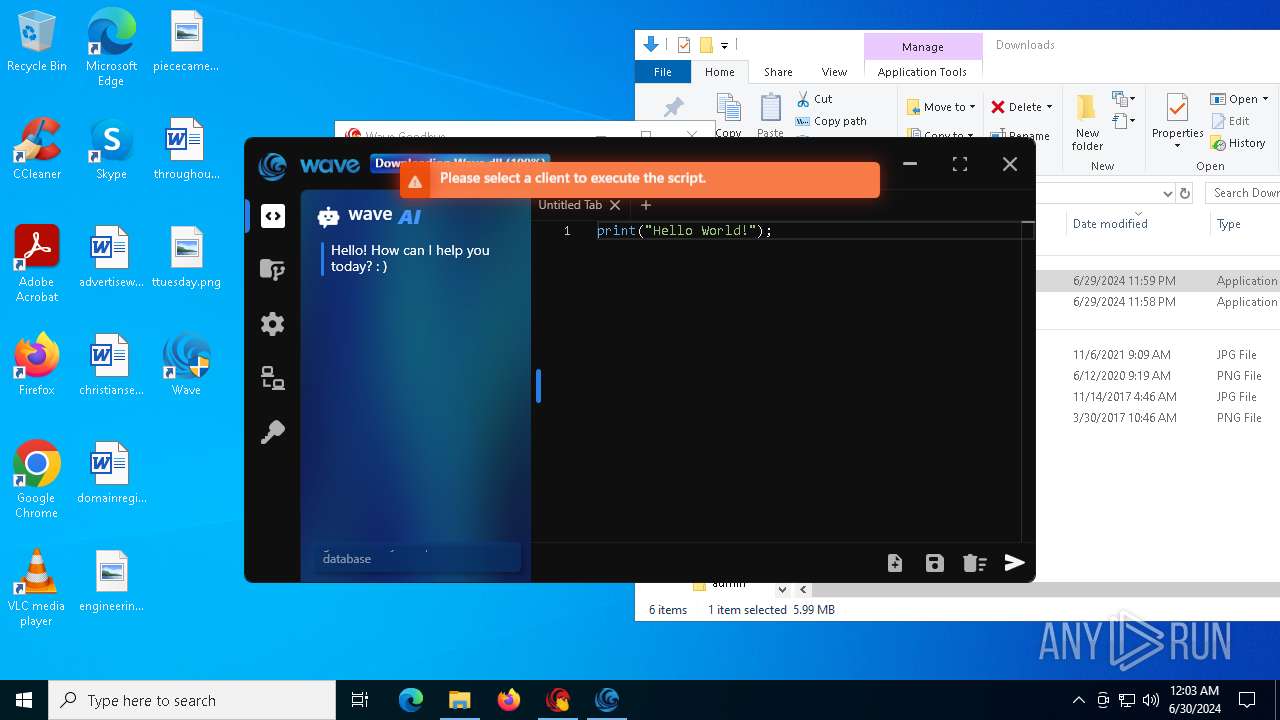
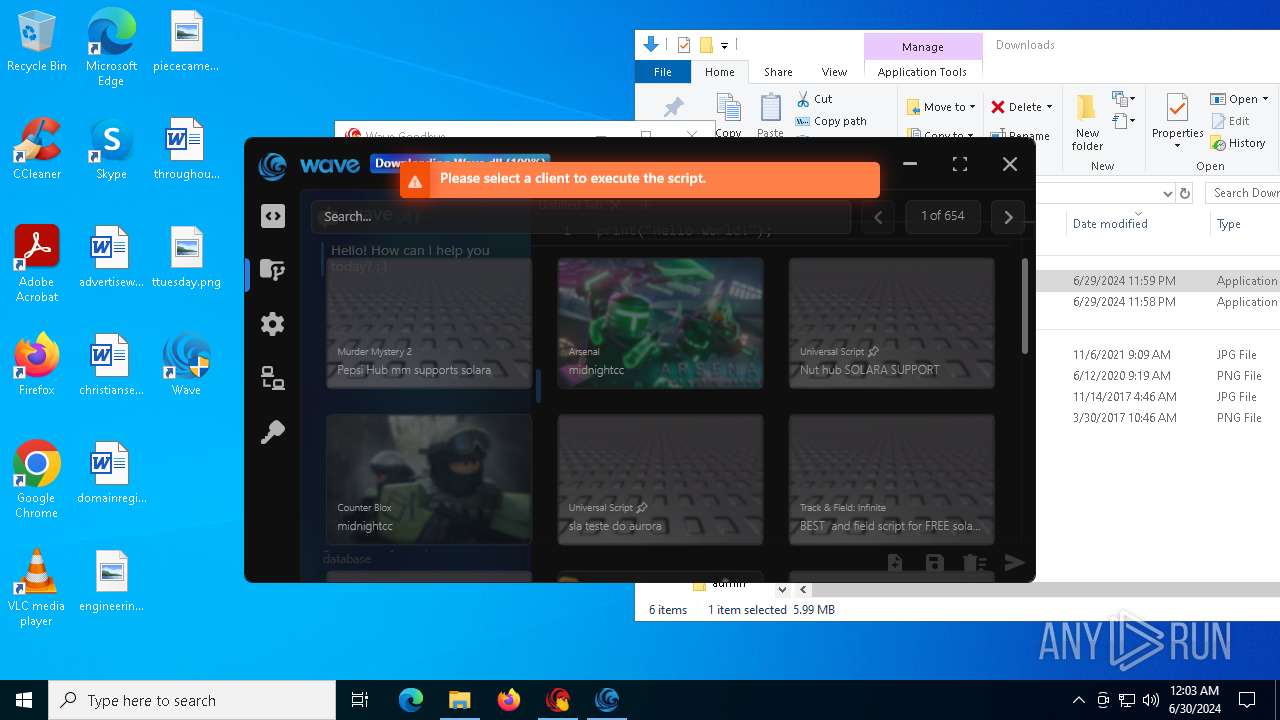
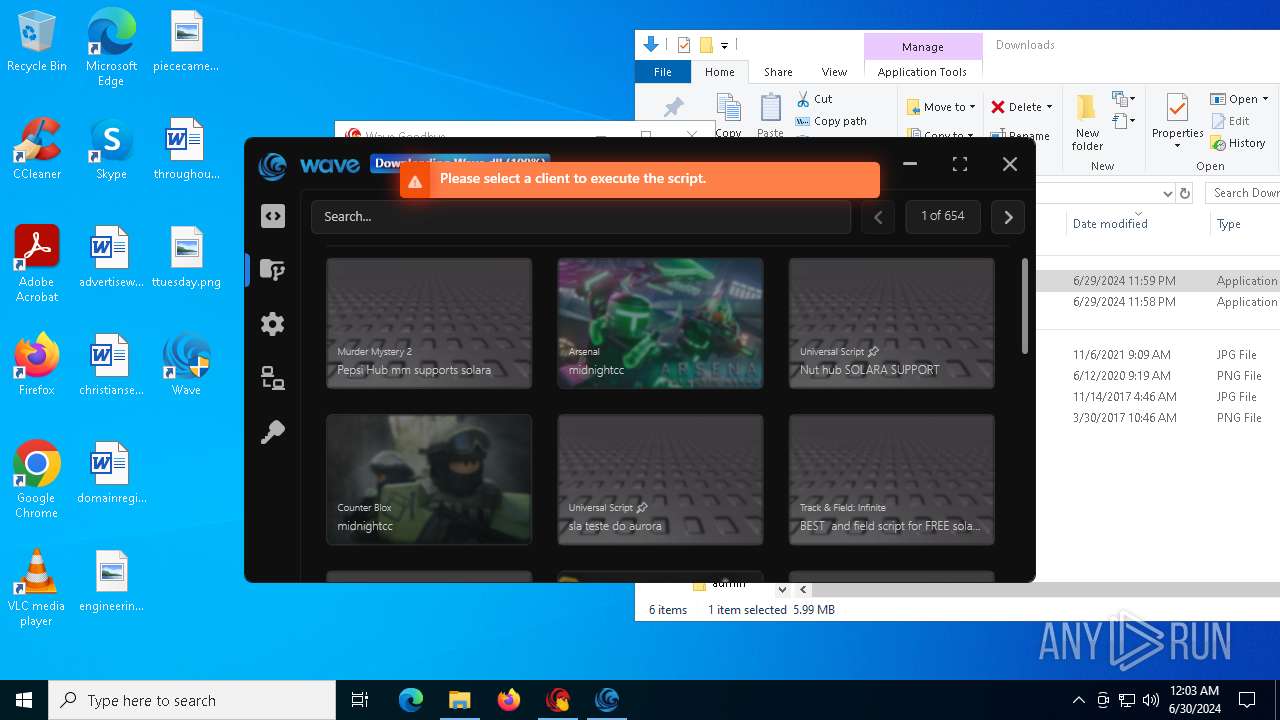
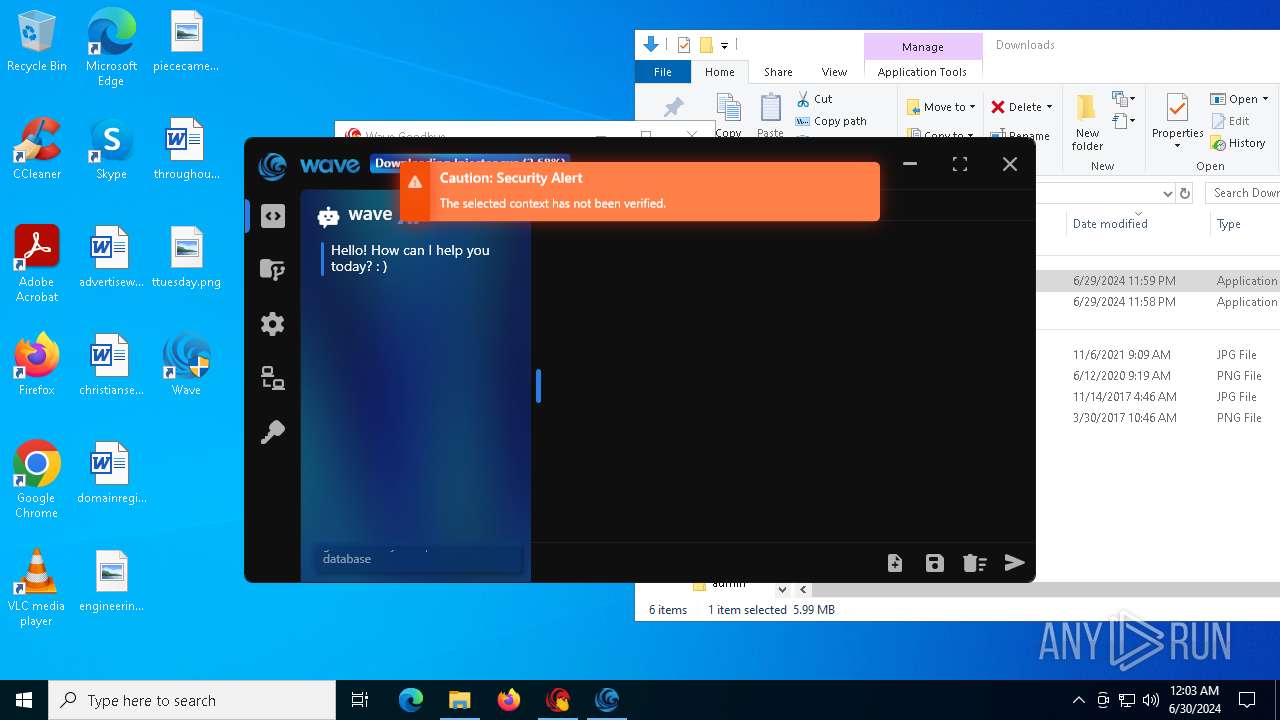
| URL: | https://cdn.getwave.gg/WaveInstaller.exe |
| Full analysis: | https://app.any.run/tasks/03be1fe7-c1e0-45fa-b91e-c70c2f30d2d3 |
| Verdict: | Malicious activity |
| Analysis date: | June 29, 2024, 23:58:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BAF9854DFB39C552F4D8F5E70A9189ED |
| SHA1: | 319748B1F1948EFA8B519FD3DE25974ABF6D721F |
| SHA256: | 9FC9F0D0B261E653B8417F1B30E9864D05C89920EF15DA3AE5653605BF4F981E |
| SSDEEP: | 3:N8cbRSEM2Jy4XJOXLNn:2cbR3MgOXLN |
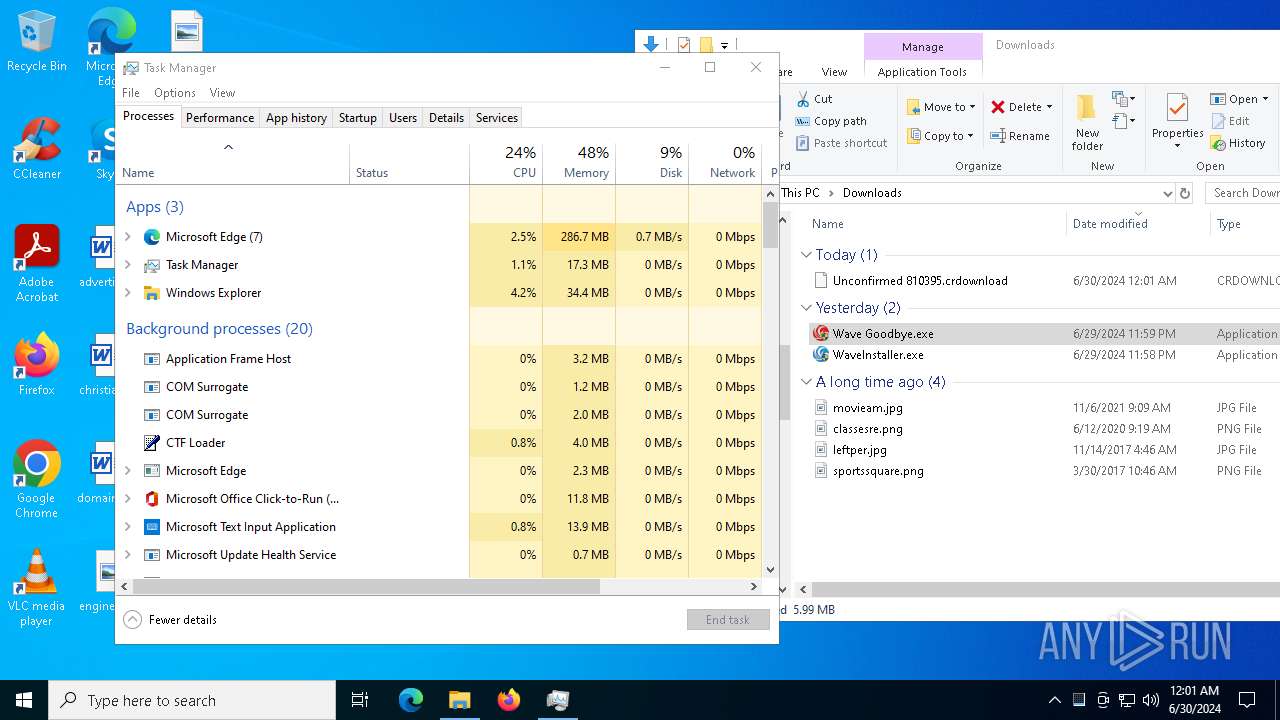
MALICIOUS
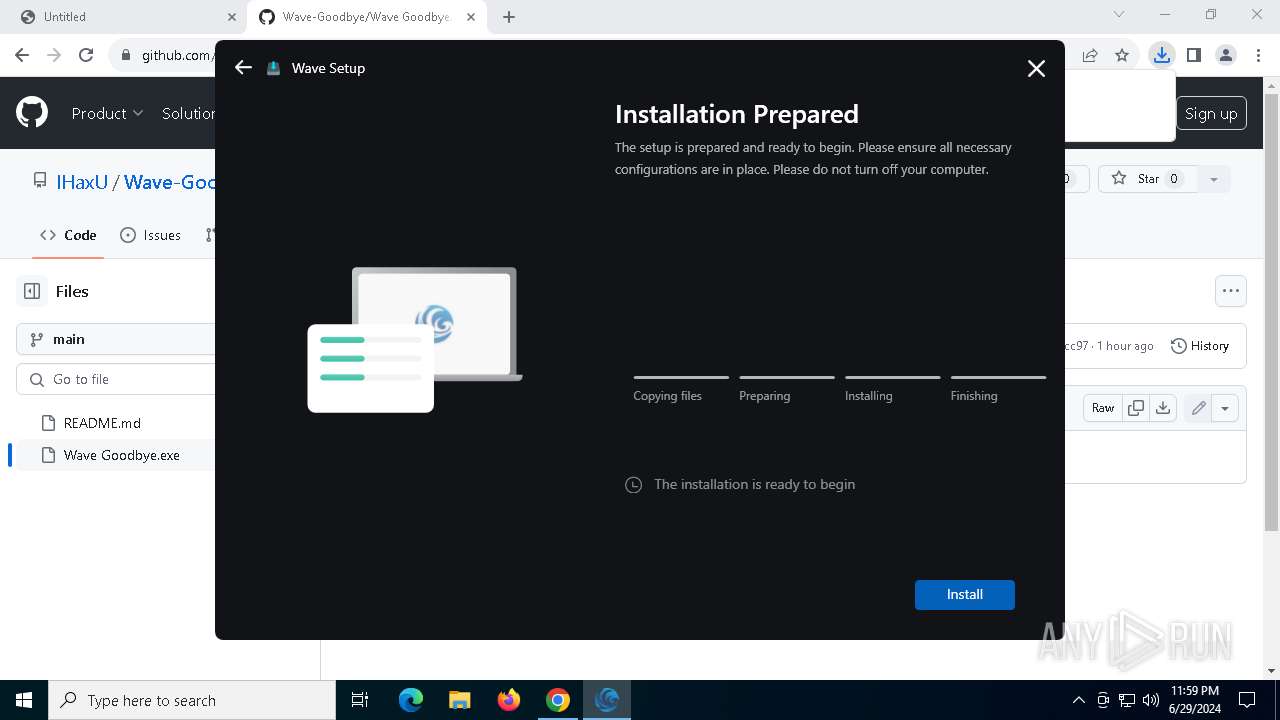
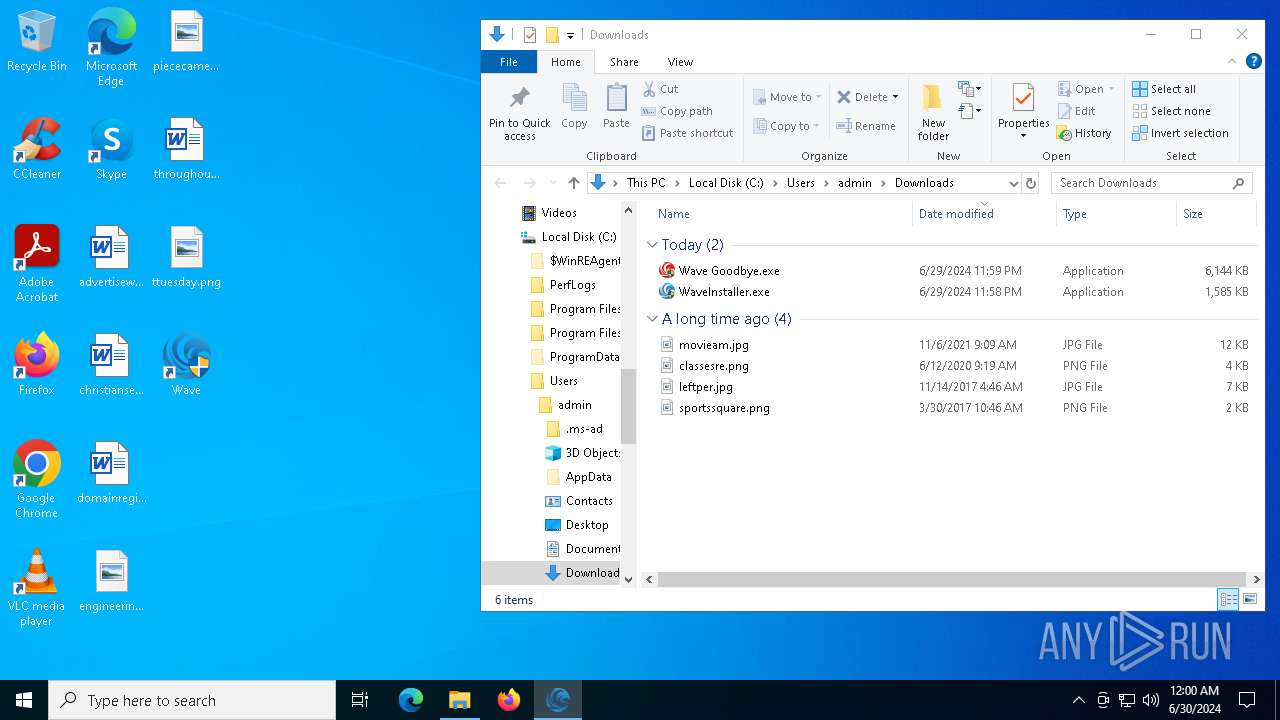
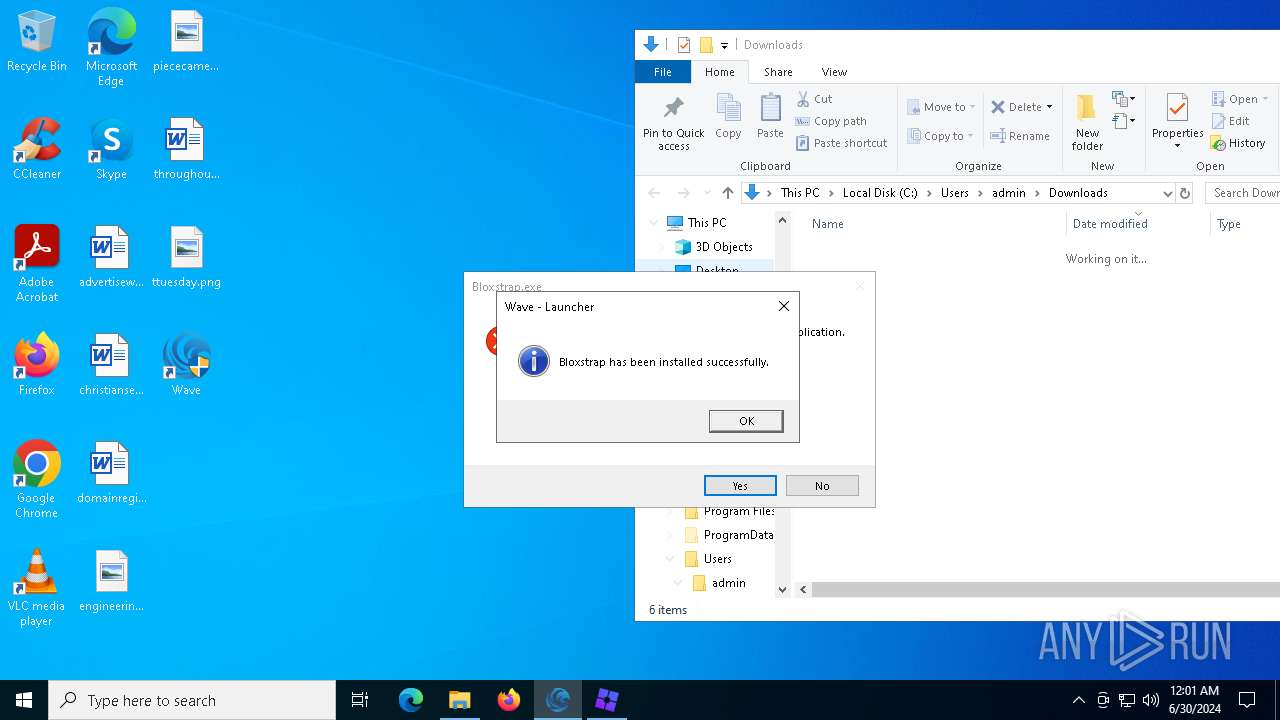
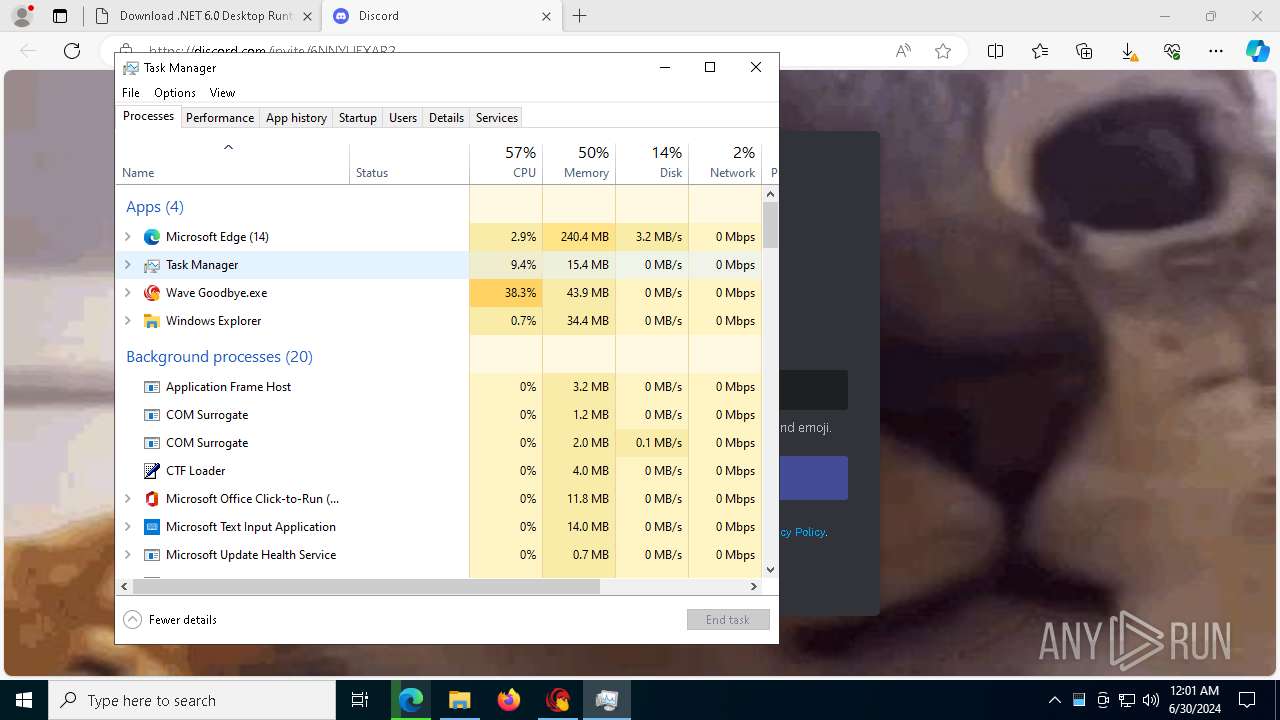
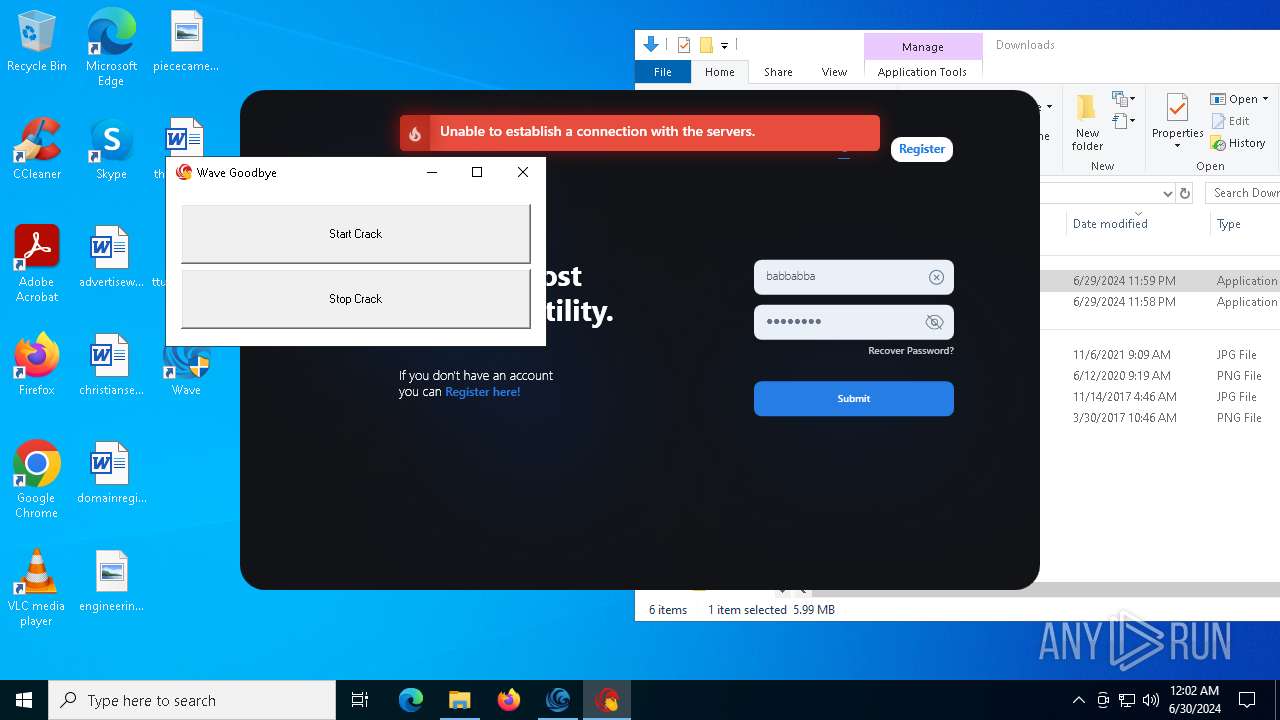
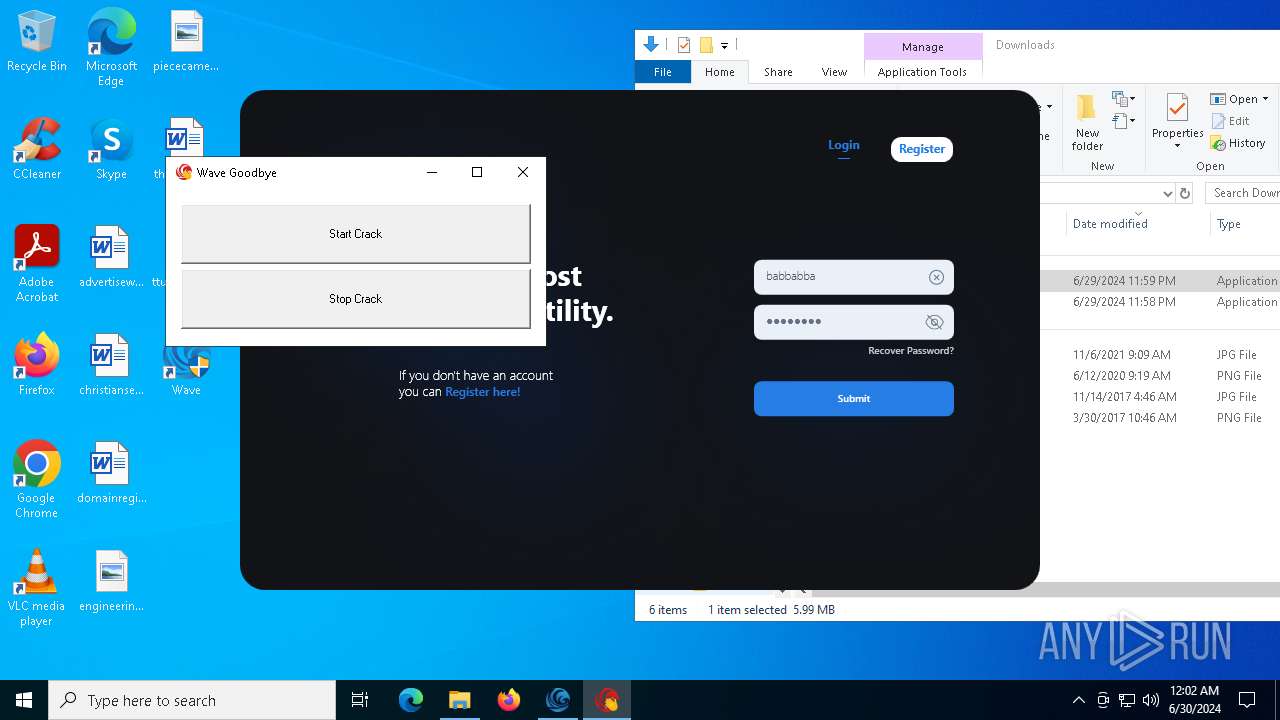
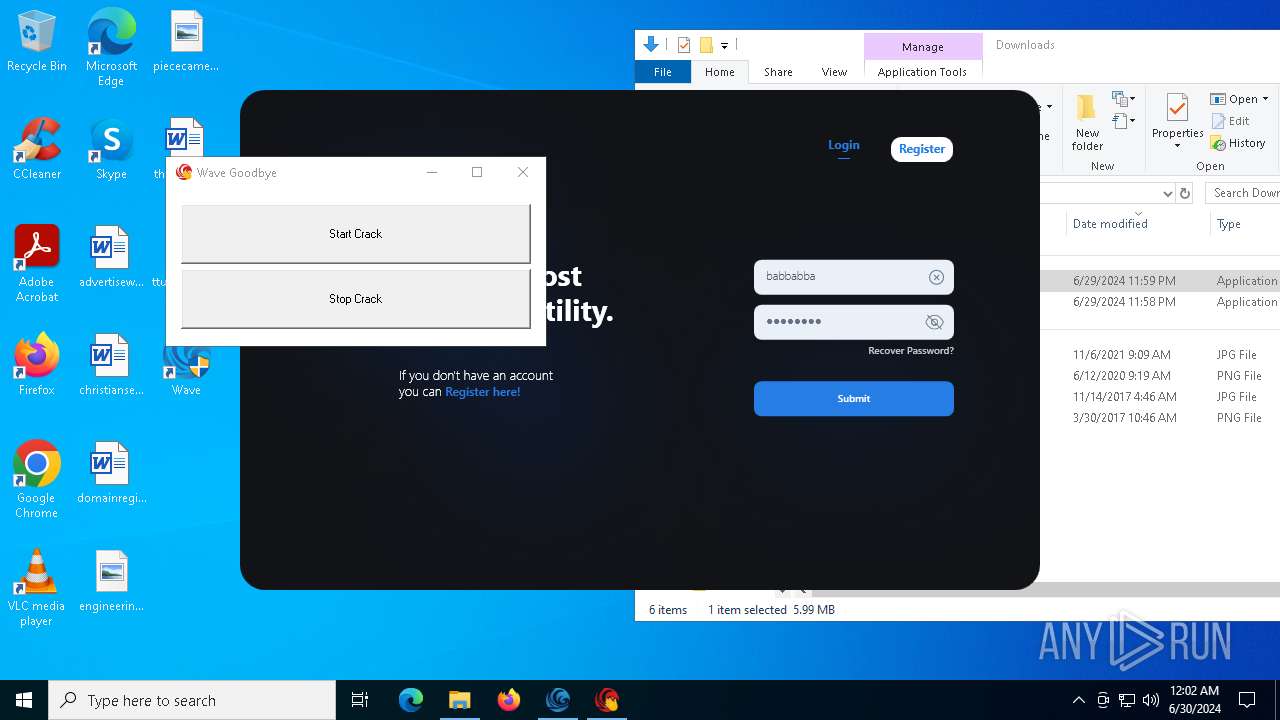
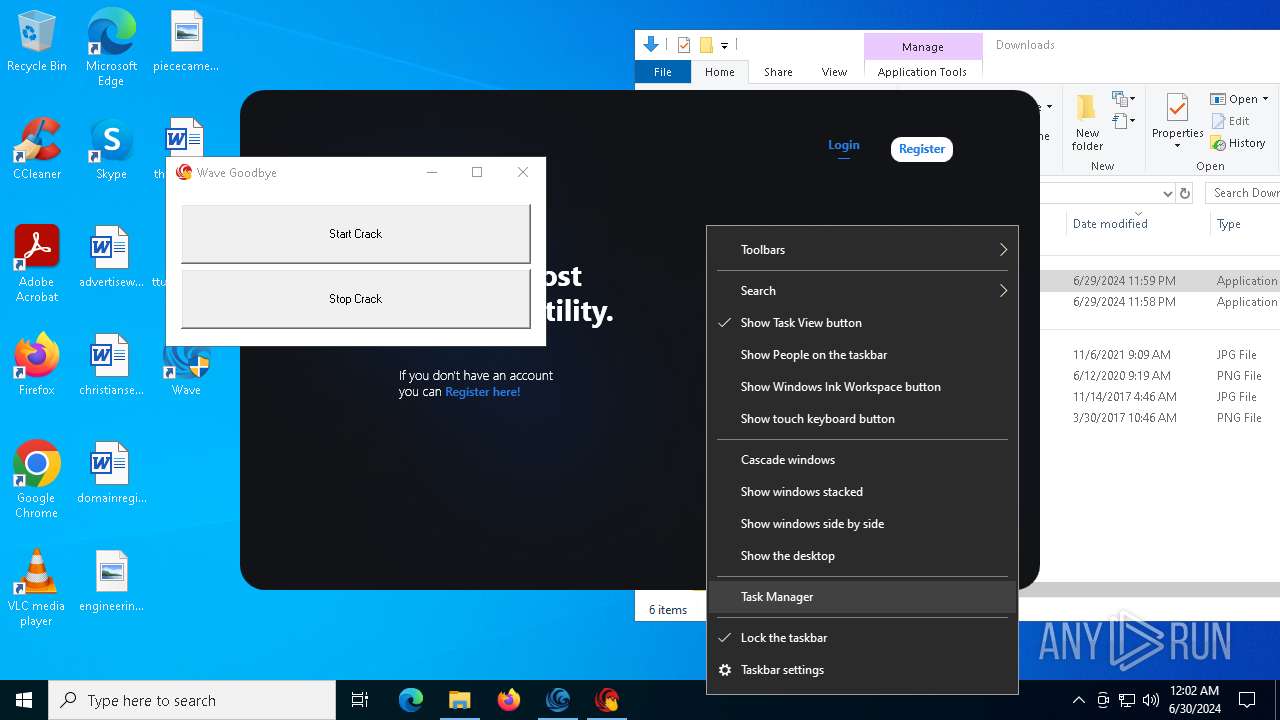
Drops the executable file immediately after the start
- WaveInstaller.exe (PID: 6508)
- WaveWindows.exe (PID: 6516)
- WaveWindows.exe (PID: 6816)
Modifies hosts file to block updates
- msedge.exe (PID: 6424)
SUSPICIOUS
Reads security settings of Internet Explorer
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
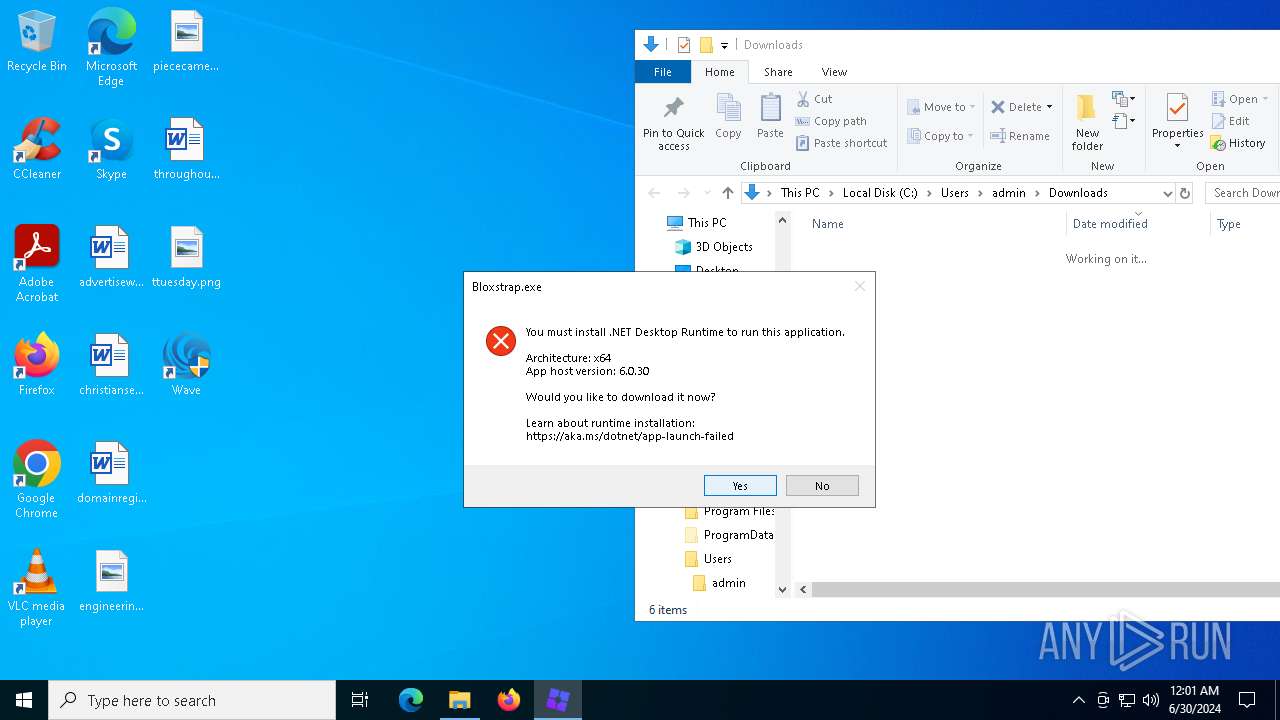
- Bloxstrap.exe (PID: 6692)
- ShellExperienceHost.exe (PID: 5892)
- Wave Goodbye.exe (PID: 5000)
- WaveBootstrapper.exe (PID: 2448)
- WaveWindows.exe (PID: 4860)
- Wave Goodbye.exe (PID: 6856)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
Executable content was dropped or overwritten
- WaveInstaller.exe (PID: 6508)
- WaveWindows.exe (PID: 6516)
- WaveWindows.exe (PID: 6816)
Process drops legitimate windows executable
- WaveInstaller.exe (PID: 6508)
Reads the date of Windows installation
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- WaveBootstrapper.exe (PID: 2448)
- WaveWindows.exe (PID: 4860)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
Reads the BIOS version
- Wave Goodbye.exe (PID: 5000)
- Wave Goodbye.exe (PID: 6856)
Adds/modifies Windows certificates
- Wave Goodbye.exe (PID: 5000)
Detected use of alternative data streams (AltDS)
- wave-luau.exe (PID: 3168)
- wave-luau.exe (PID: 6888)
INFO
Drops the executable file immediately after the start
- chrome.exe (PID: 5272)
- msedge.exe (PID: 6164)
Application launched itself
- chrome.exe (PID: 5272)
- msedge.exe (PID: 6936)
- msedge.exe (PID: 6164)
- msedge.exe (PID: 6328)
- msedge.exe (PID: 6260)
Executable content was dropped or overwritten
- chrome.exe (PID: 5272)
- msedge.exe (PID: 6164)
Reads Microsoft Office registry keys
- chrome.exe (PID: 5272)
- Bloxstrap.exe (PID: 6692)
- msedge.exe (PID: 6936)
- msedge.exe (PID: 6164)
- Wave Goodbye.exe (PID: 5000)
- msedge.exe (PID: 6328)
- Wave Goodbye.exe (PID: 6856)
- msedge.exe (PID: 6260)
Reads the computer name
- TextInputHost.exe (PID: 4480)
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- CefSharp.BrowserSubprocess.exe (PID: 900)
- CefSharp.BrowserSubprocess.exe (PID: 6868)
- CefSharp.BrowserSubprocess.exe (PID: 904)
- CefSharp.BrowserSubprocess.exe (PID: 3020)
- ShellExperienceHost.exe (PID: 5892)
- Bloxstrap.exe (PID: 6692)
- identity_helper.exe (PID: 6788)
- Wave Goodbye.exe (PID: 5000)
- identity_helper.exe (PID: 1920)
- WaveBootstrapper.exe (PID: 2448)
- Wave Goodbye.exe (PID: 6856)
- WaveWindows.exe (PID: 4860)
- CefSharp.BrowserSubprocess.exe (PID: 6512)
- CefSharp.BrowserSubprocess.exe (PID: 7092)
- CefSharp.BrowserSubprocess.exe (PID: 2356)
- CefSharp.BrowserSubprocess.exe (PID: 7048)
- identity_helper.exe (PID: 6712)
- CefSharp.BrowserSubprocess.exe (PID: 4440)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
- CefSharp.BrowserSubprocess.exe (PID: 3168)
- CefSharp.BrowserSubprocess.exe (PID: 1128)
- CefSharp.BrowserSubprocess.exe (PID: 3924)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
- CefSharp.BrowserSubprocess.exe (PID: 1588)
- CefSharp.BrowserSubprocess.exe (PID: 4536)
- CefSharp.BrowserSubprocess.exe (PID: 6560)
The process uses the downloaded file
- chrome.exe (PID: 5116)
- chrome.exe (PID: 5272)
- chrome.exe (PID: 1920)
Checks supported languages
- TextInputHost.exe (PID: 4480)
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- CefSharp.BrowserSubprocess.exe (PID: 900)
- CefSharp.BrowserSubprocess.exe (PID: 6868)
- CefSharp.BrowserSubprocess.exe (PID: 904)
- CefSharp.BrowserSubprocess.exe (PID: 3020)
- node.exe (PID: 7032)
- Bloxstrap.exe (PID: 6692)
- ShellExperienceHost.exe (PID: 5892)
- Wave Goodbye.exe (PID: 5000)
- identity_helper.exe (PID: 6788)
- identity_helper.exe (PID: 1920)
- WaveBootstrapper.exe (PID: 2448)
- Wave Goodbye.exe (PID: 6856)
- WaveWindows.exe (PID: 4860)
- CefSharp.BrowserSubprocess.exe (PID: 6512)
- CefSharp.BrowserSubprocess.exe (PID: 7092)
- node.exe (PID: 6760)
- CefSharp.BrowserSubprocess.exe (PID: 7048)
- identity_helper.exe (PID: 6712)
- CefSharp.BrowserSubprocess.exe (PID: 2356)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
- CefSharp.BrowserSubprocess.exe (PID: 4440)
- CefSharp.BrowserSubprocess.exe (PID: 3168)
- node.exe (PID: 3068)
- CefSharp.BrowserSubprocess.exe (PID: 1128)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
- CefSharp.BrowserSubprocess.exe (PID: 3924)
- CefSharp.BrowserSubprocess.exe (PID: 4536)
- CefSharp.BrowserSubprocess.exe (PID: 1588)
- CefSharp.BrowserSubprocess.exe (PID: 6560)
- wave-luau.exe (PID: 3168)
- wave-luau.exe (PID: 6888)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
Reads Environment values
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- node.exe (PID: 7032)
- WaveWindows.exe (PID: 6516)
- WaveBootstrapper.exe (PID: 2448)
- node.exe (PID: 6760)
- WaveWindows.exe (PID: 4860)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
- node.exe (PID: 3068)
Disables trace logs
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- WaveBootstrapper.exe (PID: 2448)
- WaveWindows.exe (PID: 4860)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
Reads the machine GUID from the registry
- WaveInstaller.exe (PID: 6508)
- CefSharp.BrowserSubprocess.exe (PID: 900)
- WaveWindows.exe (PID: 6516)
- CefSharp.BrowserSubprocess.exe (PID: 6868)
- WaveBootstrapper.exe (PID: 308)
- CefSharp.BrowserSubprocess.exe (PID: 904)
- CefSharp.BrowserSubprocess.exe (PID: 3020)
- Wave Goodbye.exe (PID: 5000)
- WaveBootstrapper.exe (PID: 2448)
- Wave Goodbye.exe (PID: 6856)
- WaveWindows.exe (PID: 4860)
- CefSharp.BrowserSubprocess.exe (PID: 6512)
- CefSharp.BrowserSubprocess.exe (PID: 7092)
- CefSharp.BrowserSubprocess.exe (PID: 2356)
- CefSharp.BrowserSubprocess.exe (PID: 7048)
- CefSharp.BrowserSubprocess.exe (PID: 4440)
- WaveBootstrapper.exe (PID: 904)
- CefSharp.BrowserSubprocess.exe (PID: 6372)
- CefSharp.BrowserSubprocess.exe (PID: 3924)
- CefSharp.BrowserSubprocess.exe (PID: 3168)
- CefSharp.BrowserSubprocess.exe (PID: 1128)
- WaveWindows.exe (PID: 6816)
- CefSharp.BrowserSubprocess.exe (PID: 1348)
- CefSharp.BrowserSubprocess.exe (PID: 1588)
- CefSharp.BrowserSubprocess.exe (PID: 4536)
- CefSharp.BrowserSubprocess.exe (PID: 6560)
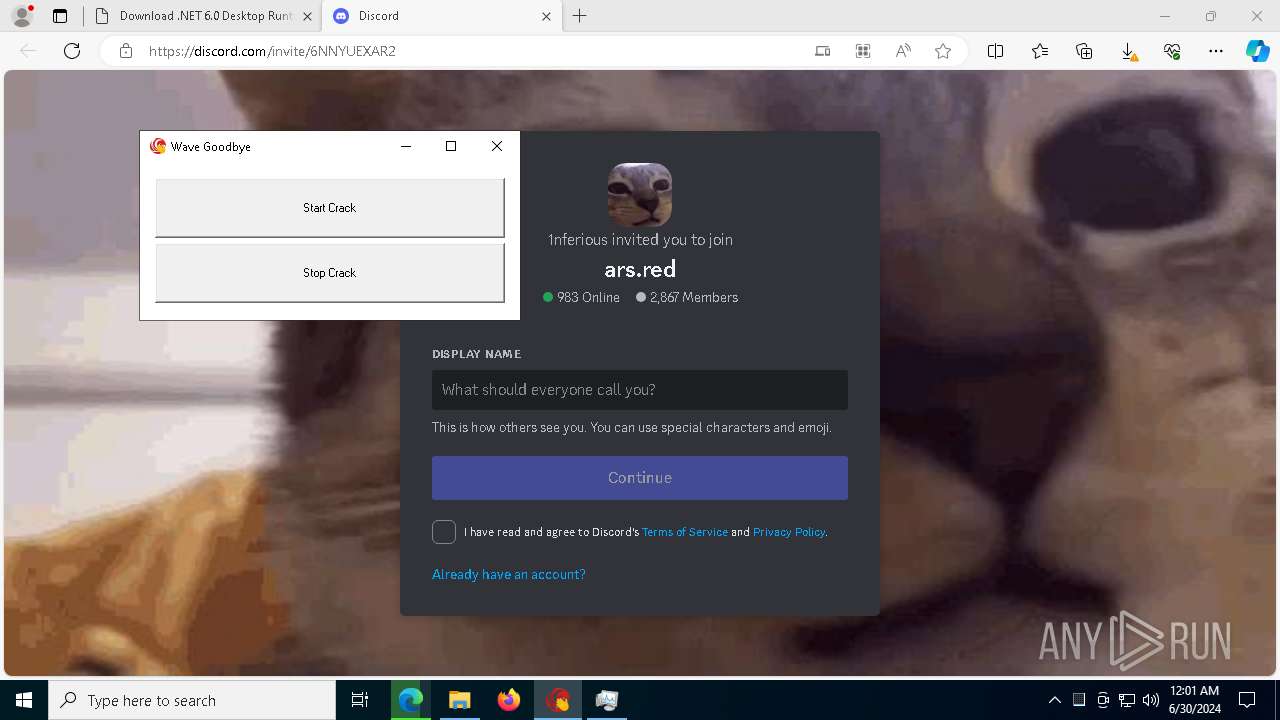
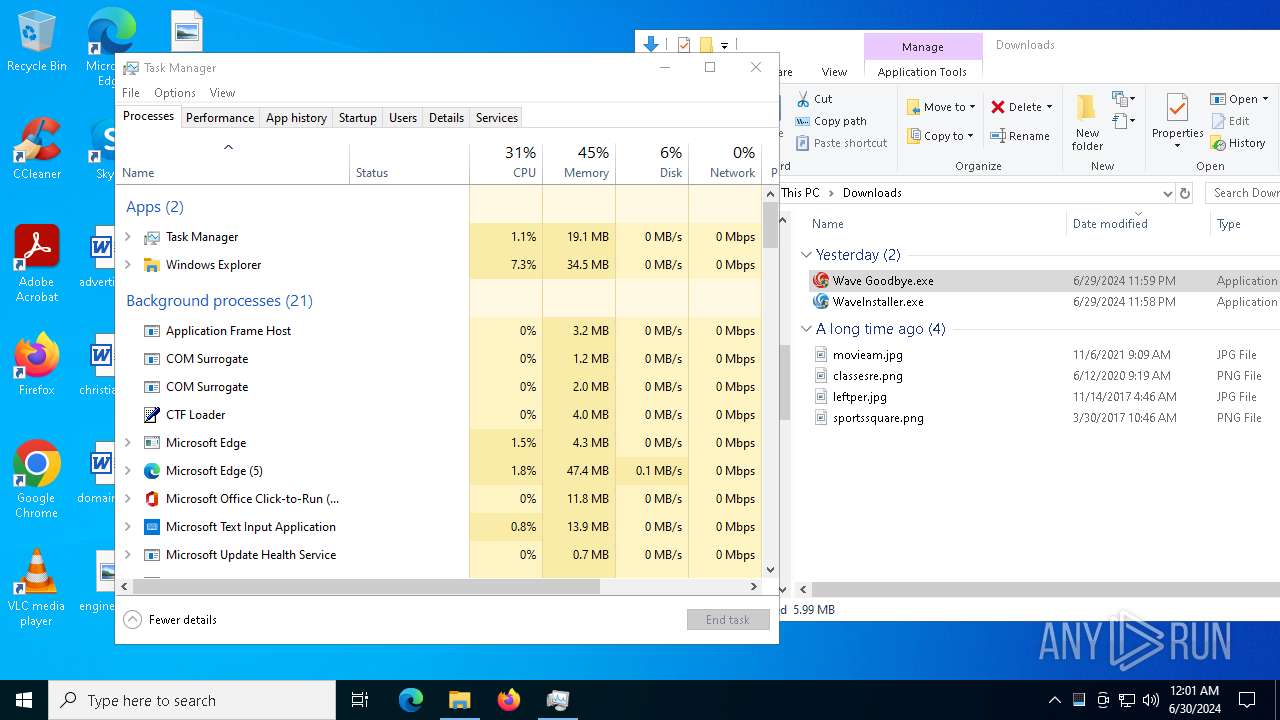
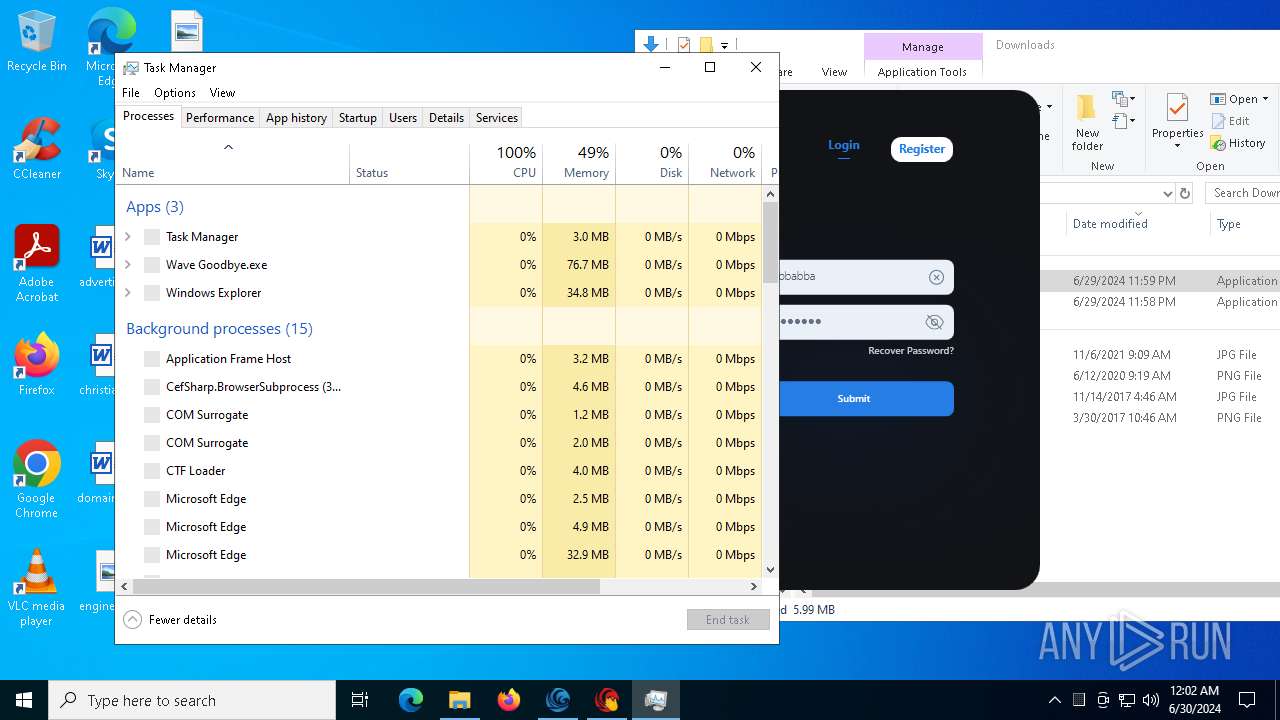
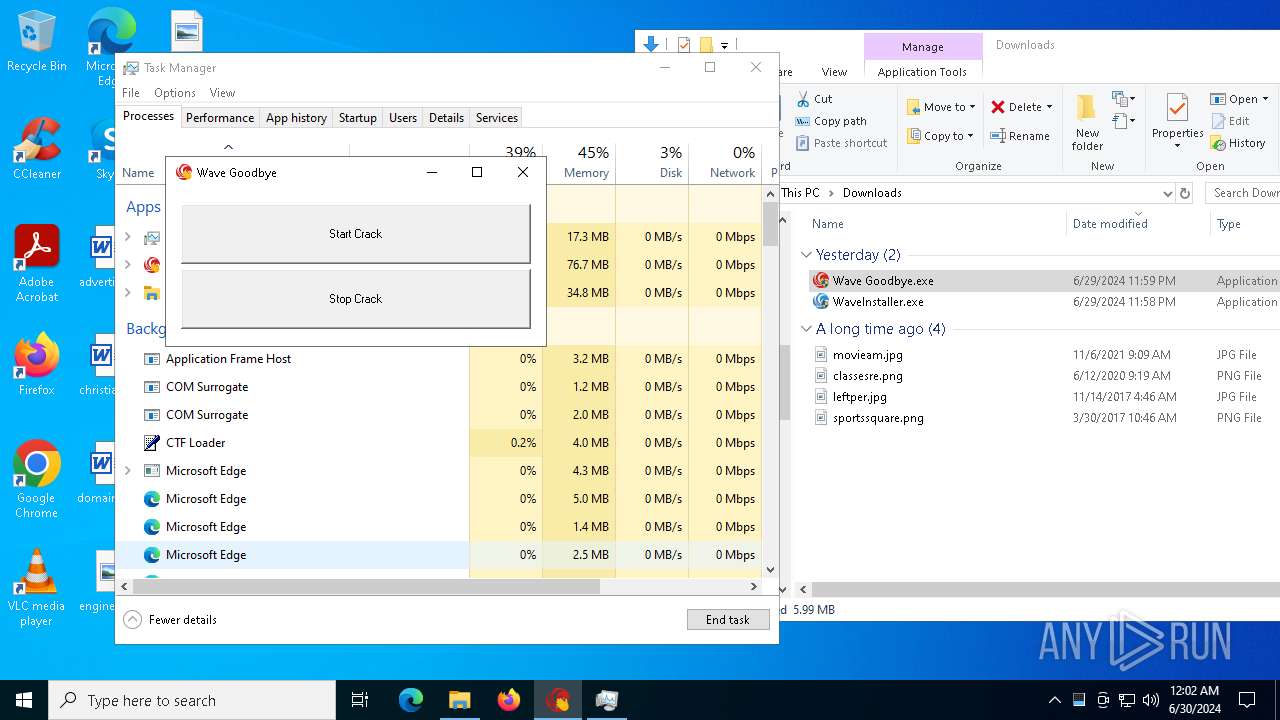
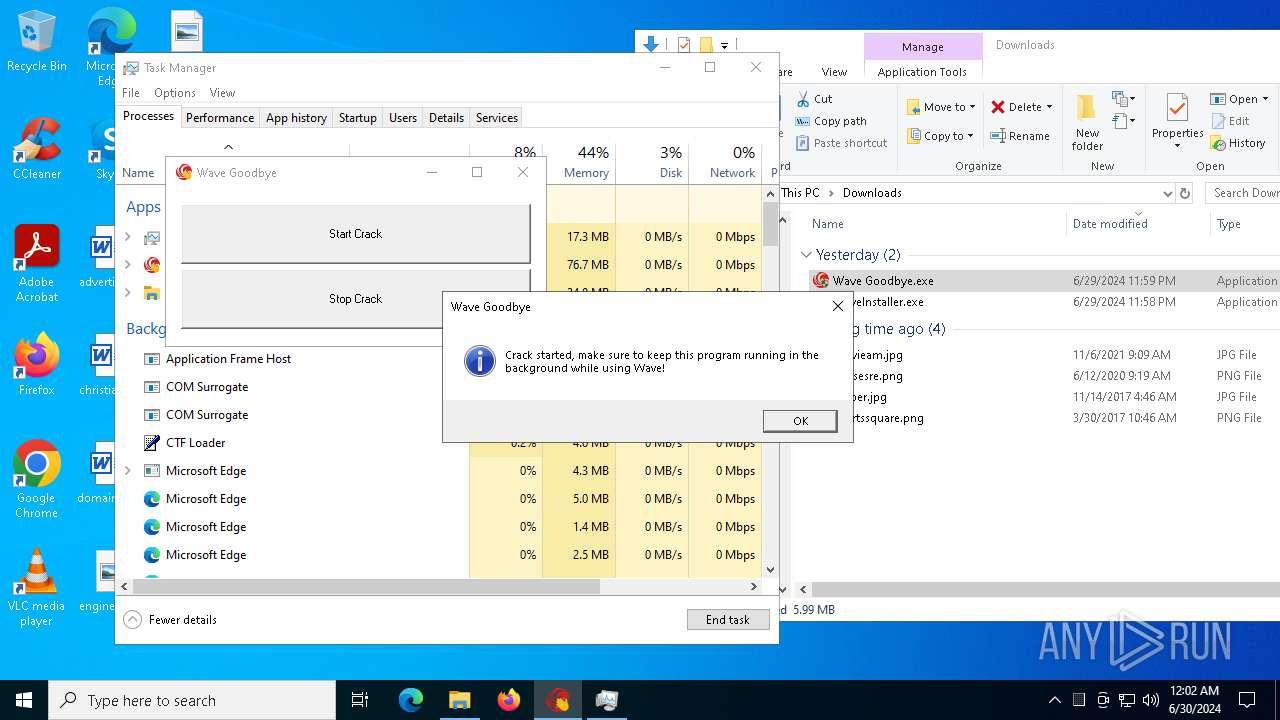
Manual execution by a user
- Taskmgr.exe (PID: 2536)
- Taskmgr.exe (PID: 884)
- msedge.exe (PID: 6164)
- Wave Goodbye.exe (PID: 5000)
- Taskmgr.exe (PID: 5264)
- Taskmgr.exe (PID: 428)
- Wave Goodbye.exe (PID: 2444)
- WaveBootstrapper.exe (PID: 6036)
- WaveBootstrapper.exe (PID: 2448)
- Wave Goodbye.exe (PID: 6884)
- Wave Goodbye.exe (PID: 6856)
- Taskmgr.exe (PID: 6324)
- Taskmgr.exe (PID: 3444)
- WaveBootstrapper.exe (PID: 5652)
- WaveBootstrapper.exe (PID: 904)
Checks proxy server information
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- WaveBootstrapper.exe (PID: 2448)
- WaveWindows.exe (PID: 4860)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
Reads the software policy settings
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- WaveBootstrapper.exe (PID: 2448)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
Creates files or folders in the user directory
- WaveInstaller.exe (PID: 6508)
- WaveWindows.exe (PID: 6516)
- WaveWindows.exe (PID: 4860)
- WaveWindows.exe (PID: 6816)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 884)
- Taskmgr.exe (PID: 428)
- Taskmgr.exe (PID: 3444)
Creates files in the program directory
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 4860)
- WaveWindows.exe (PID: 6816)
Process checks computer location settings
- WaveInstaller.exe (PID: 6508)
- WaveBootstrapper.exe (PID: 308)
- WaveWindows.exe (PID: 6516)
- WaveBootstrapper.exe (PID: 2448)
- WaveWindows.exe (PID: 4860)
- WaveBootstrapper.exe (PID: 904)
- WaveWindows.exe (PID: 6816)
- node.exe (PID: 3068)
- CefSharp.BrowserSubprocess.exe (PID: 4536)
- CefSharp.BrowserSubprocess.exe (PID: 1588)
- CefSharp.BrowserSubprocess.exe (PID: 6560)
Checks for the presence of KasperskyLab
- WaveWindows.exe (PID: 6516)
- WaveWindows.exe (PID: 4860)
- WaveWindows.exe (PID: 6816)
Reads product name
- node.exe (PID: 7032)
- node.exe (PID: 6760)
- node.exe (PID: 3068)
Process checks whether UAC notifications are on
- Wave Goodbye.exe (PID: 5000)
- Wave Goodbye.exe (PID: 6856)
Themida protector has been detected
- Wave Goodbye.exe (PID: 6856)
Create files in a temporary directory
- WaveWindows.exe (PID: 6816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
314
Monitored processes
159
Malicious processes
7
Suspicious processes
8
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 308 | "C:\Users\admin\AppData\Local\Wave\WaveBootstrapper.exe" | C:\Users\admin\AppData\Local\Wave\WaveBootstrapper.exe | WaveInstaller.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: WaveBootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 420 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=4564 --field-trial-handle=1856,i,6865634749935843668,17856763579649792292,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 428 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 476 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6604 --field-trial-handle=2436,i,1783043296049834170,5072788179284989999,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 880 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x260,0x264,0x268,0x25c,0x288,0x7ffd9d705fd8,0x7ffd9d705fe4,0x7ffd9d705ff0 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 884 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | "C:\Users\admin\AppData\Local\CefSharp\CefSharp.BrowserSubprocess.exe" --type=gpu-process --no-sandbox --locales-dir-path="C:\Users\admin\AppData\Local\CefSharp\locales" --resources-dir-path="C:\Users\admin\AppData\Local\CefSharp" --lang=en-US --user-data-dir="C:\Users\admin\AppData\Local\CefSharp" --cefsharpexitsub --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAEAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --field-trial-handle=2024,i,5475406953480850395,6285036594076846764,262144 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,DocumentPictureInPictureAPI --variations-seed-version --enable-logging=handle --log-file=2060 --mojo-platform-channel-handle=2044 /prefetch:2 --host-process-id=6516 | C:\Users\admin\AppData\Local\CefSharp\CefSharp.BrowserSubprocess.exe | WaveWindows.exe | ||||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Exit code: 0 Version: 124.3.80.0 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\CefSharp\CefSharp.BrowserSubprocess.exe" --type=gpu-process --no-sandbox --locales-dir-path="C:\Users\admin\AppData\Local\CefSharp\locales" --resources-dir-path="C:\Users\admin\AppData\Local\CefSharp" --lang=en-US --user-data-dir="C:\Users\admin\AppData\Local\CefSharp" --cefsharpexitsub --gpu-preferences=WAAAAAAAAADgAAAMAAAAAAAAAAAAAAAAAABgAAAAAAA4AAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGAAAAAAAAAAYAAAAAAAAAAgAAAAAAAAACAAAAAAAAAAIAAAAAAAAAA== --use-gl=angle --use-angle=swiftshader-webgl --field-trial-handle=2120,i,5475406953480850395,6285036594076846764,262144 --disable-features=BackForwardCache,CalculateNativeWinOcclusion,DocumentPictureInPictureAPI --variations-seed-version --enable-logging=handle --log-file=2108 --mojo-platform-channel-handle=2092 /prefetch:2 --host-process-id=6516 | C:\Users\admin\AppData\Local\CefSharp\CefSharp.BrowserSubprocess.exe | WaveWindows.exe | ||||||||||||
User: admin Company: The CefSharp Authors Integrity Level: HIGH Description: CefSharp.BrowserSubprocess Exit code: 0 Version: 124.3.80.0 Modules
| |||||||||||||||
| 904 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6208 --field-trial-handle=2360,i,4206389175092584679,16851347807888136885,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 904 | "C:\Users\admin\AppData\Local\Wave\WaveBootstrapper.exe" | C:\Users\admin\AppData\Local\Wave\WaveBootstrapper.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: WaveBootstrapper Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
96 900
Read events
96 444
Write events
438
Delete events
18
Modification events
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (5272) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
45
Suspicious files
434
Text files
180
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1adca5.TMP | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1adca5.TMP | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5272 | chrome.exe | C:\USERS\ADMIN\APPDATA\LOCAL\GOOGLE\CHROME\USER DATA\CRASHPAD\SETTINGS.DAT | binary | |
MD5:FC81892AC822DCBB09441D3B58B47125 | SHA256:FB077C966296D02D50CCBF7F761D2A3311A206A784A7496F331C2B0D6AD205C8 | |||
| 5272 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Site Characteristics Database\LOG.old | text | |
MD5:19D1A06251A8678F85D8DE5BFAB83807 | SHA256:AA6E55DCF84CDAF0BD3F913E7B837F65500E9B71A5A7AA773D02FFBC18C7FF01 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
187
DNS requests
161
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6920 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
— | — | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
6920 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
6920 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
6920 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
6920 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acaldksiunzh56452py2db5mnbpa_120.0.6050.0/jamhcnnkihinmdlkakkaopbjbbcngflc_120.0.6050.0_all_dgzfpknn7v3zslsbhrwu6bt44e.crx3 | unknown | — | — | unknown |
3516 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
3516 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3516 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3188 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4452 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5076 | chrome.exe | 74.125.143.84:443 | accounts.google.com | GOOGLE | US | unknown |
5272 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5076 | chrome.exe | 104.26.3.170:443 | cdn.getwave.gg | CLOUDFLARENET | US | unknown |
5076 | chrome.exe | 216.58.206.78:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
5272 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cdn.getwave.gg |
| unknown |
accounts.google.com |
| shared |
sb-ssl.google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
www.google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
6424 | msedge.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
4464 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
4464 | msedge.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
Process | Message |
|---|---|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:angle_platform_impl.cc(44)] Display.cpp:1086 (initialize): ANGLE Display::initialize error 0: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_display.cc(515)] EGL Driver message (Critical) eglInitialize: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_display.cc(786)] eglInitialize SwANGLE failed with error EGL_NOT_INITIALIZED
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_display.cc(820)] Initialization of all EGL display types failed.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_initializer_win.cc(135)] GLDisplayEGL::Initialize failed.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:angle_platform_impl.cc(44)] Display.cpp:1086 (initialize): ANGLE Display::initialize error 0: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_display.cc(515)] EGL Driver message (Critical) eglInitialize: Internal Vulkan error (-3): Initialization of an object could not be completed for implementation-specific reasons, in ..\..\third_party\angle\src\libANGLE\renderer\vulkan\RendererVk.cpp, initialize:1715.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_display.cc(786)] eglInitialize SwANGLE failed with error EGL_NOT_INITIALIZED
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_display.cc(820)] Initialization of all EGL display types failed.
|
CefSharp.BrowserSubprocess.exe | [0630/000107.504:ERROR:gl_initializer_win.cc(135)] GLDisplayEGL::Initialize failed.
|