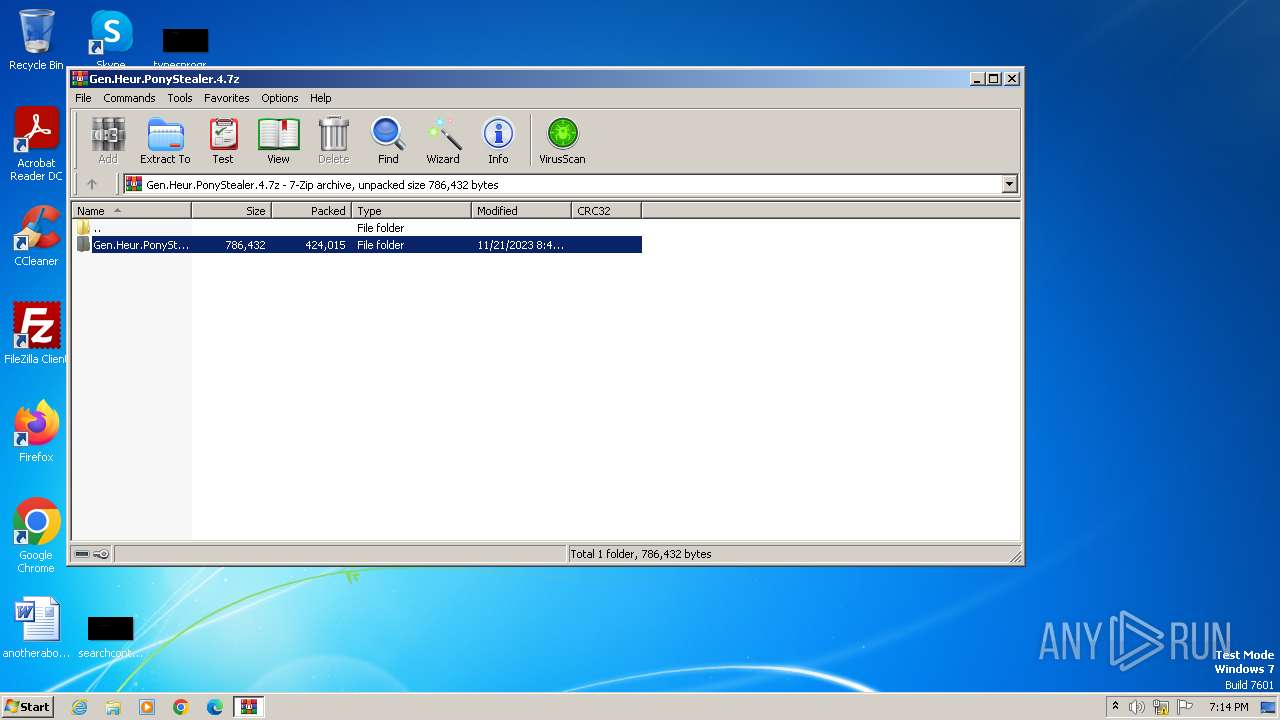
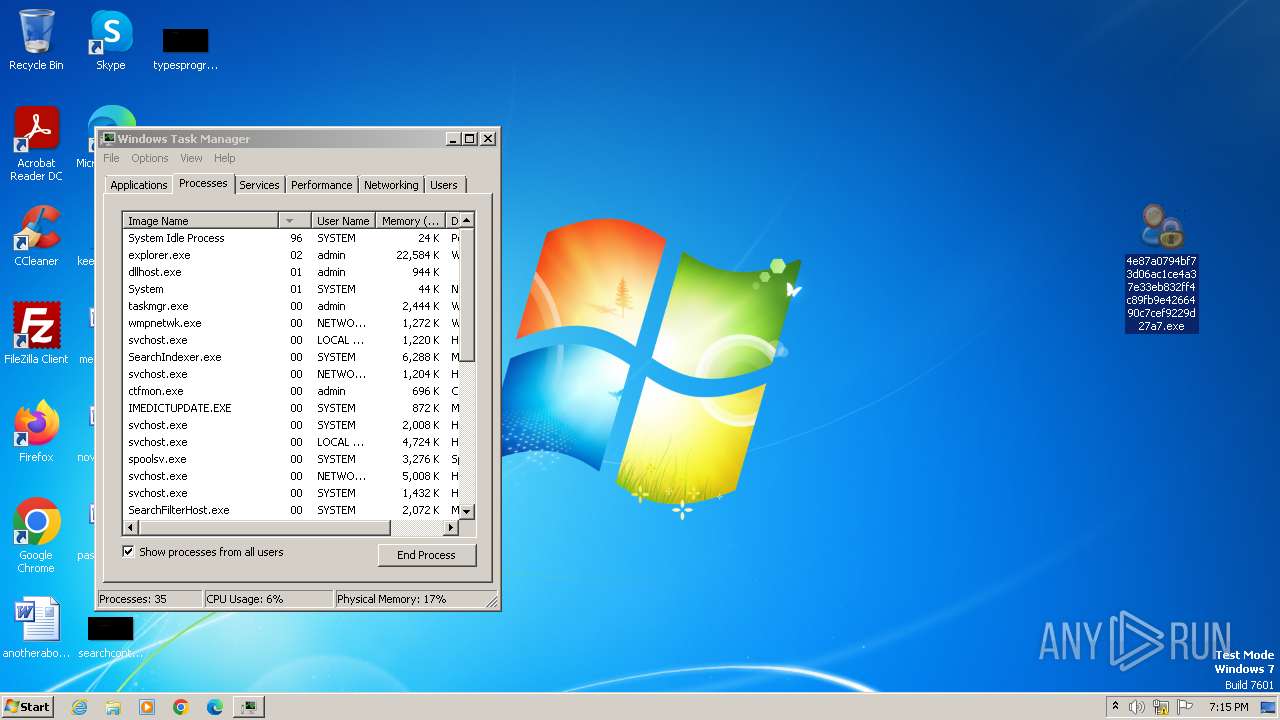
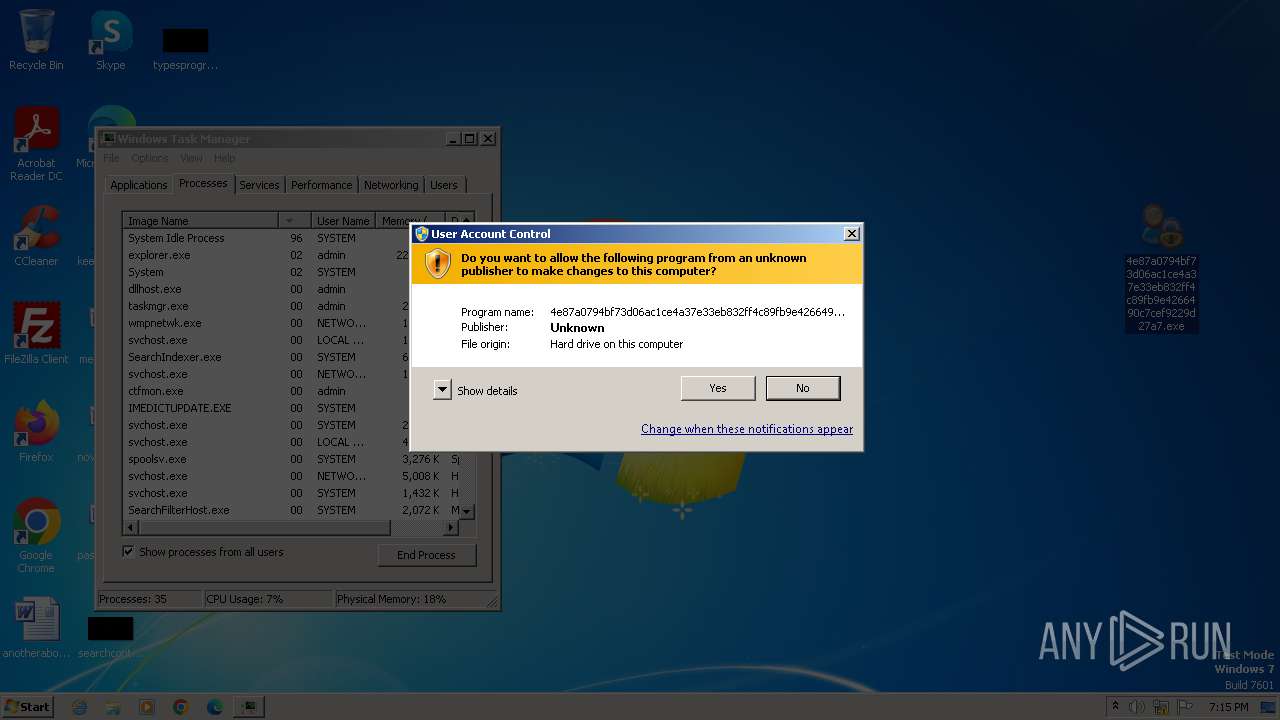
| File name: | Gen.Heur.PonyStealer.4.7z |
| Full analysis: | https://app.any.run/tasks/4f24695a-1495-47cb-a984-edcfb8ef2ac7 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2023, 19:14:33 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 3CDEFC17F658FE68242A489D1526CD53 |
| SHA1: | A74FB9F87855E399C5DCA208EC9F2E65D8647804 |
| SHA256: | 9FB54D7E9E5E01EA93007A6AE9681E9EEA02443CADAE1584248F3E52B113792D |
| SSDEEP: | 12288:vARp77VoGj/FNV3Lgub6+BOwNZfGvU4dppvZDkmmgIv3h:4RR7VoG7ffbzOwNZfGM4dpphDkmmg43h |
MALICIOUS
Uses Task Scheduler to run other applications
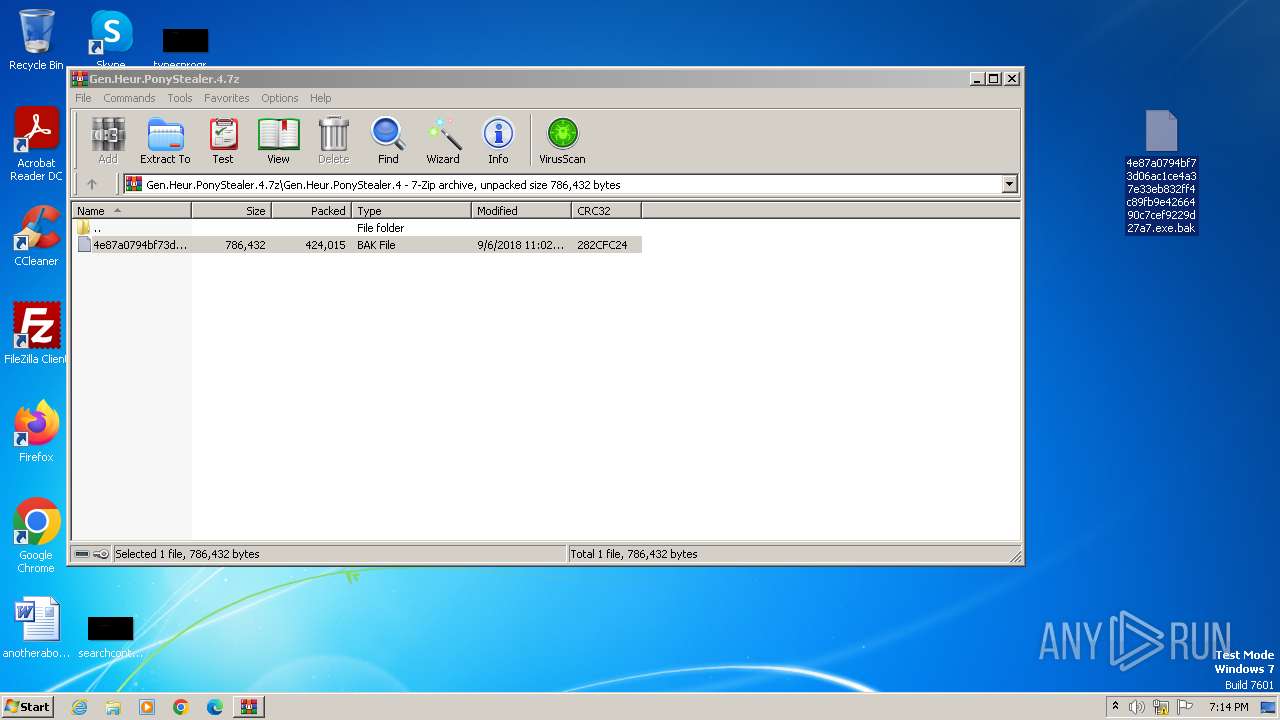
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
Drops the executable file immediately after the start
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
SUSPICIOUS
Application launched itself
- taskmgr.exe (PID: 3228)
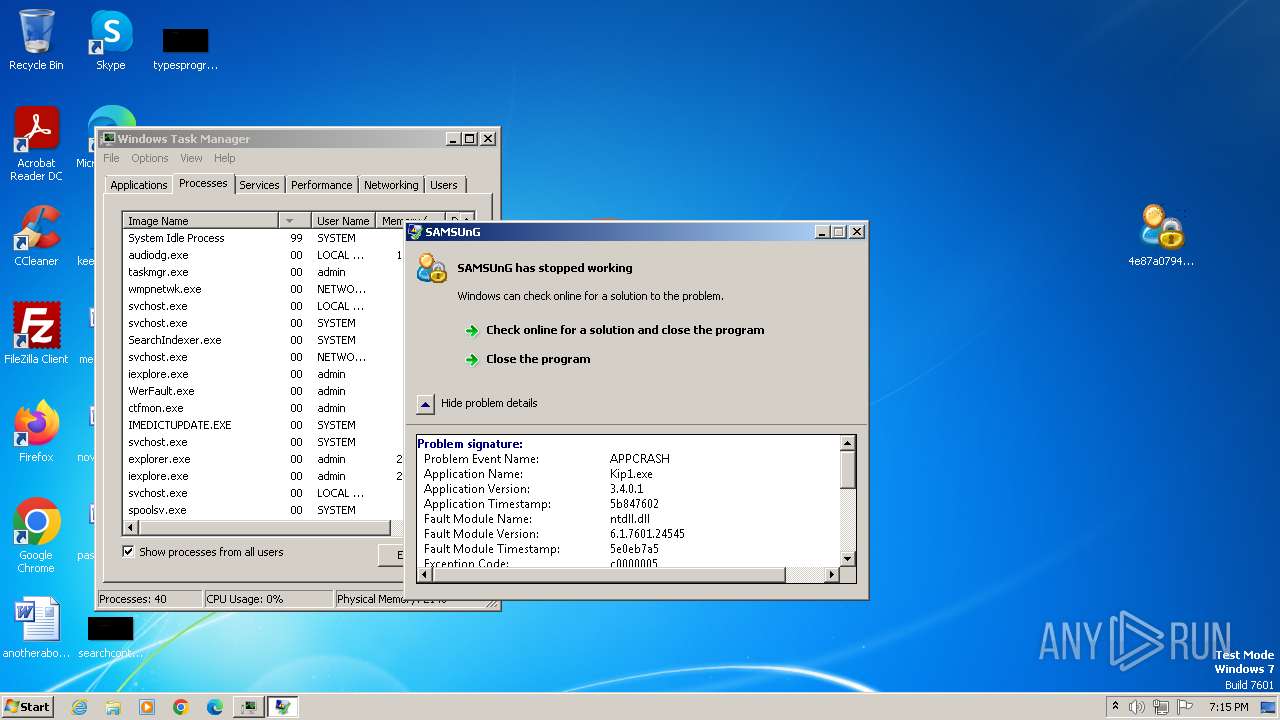
- Kip1.exe (PID: 1852)
Reads the Internet Settings
- taskmgr.exe (PID: 3228)
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
The process executes via Task Scheduler
- Kip1.exe (PID: 1852)
The process checks if it is being run in the virtual environment
- Kip1.exe (PID: 1032)
INFO
Manual execution by a user
- taskmgr.exe (PID: 3228)
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
- wmpnscfg.exe (PID: 1116)
- wmpnscfg.exe (PID: 536)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3128)
Checks supported languages
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
- Kip1.exe (PID: 1852)
- Kip1.exe (PID: 1032)
- wmpnscfg.exe (PID: 536)
- wmpnscfg.exe (PID: 1116)
Reads the computer name
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
- Kip1.exe (PID: 1032)
- wmpnscfg.exe (PID: 536)
- wmpnscfg.exe (PID: 1116)
Creates files in the program directory
- 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe (PID: 756)
Create files in a temporary directory
- Kip1.exe (PID: 1032)
Reads the machine GUID from the registry
- Kip1.exe (PID: 1032)
- wmpnscfg.exe (PID: 1116)
- wmpnscfg.exe (PID: 536)
Application launched itself
- iexplore.exe (PID: 1892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
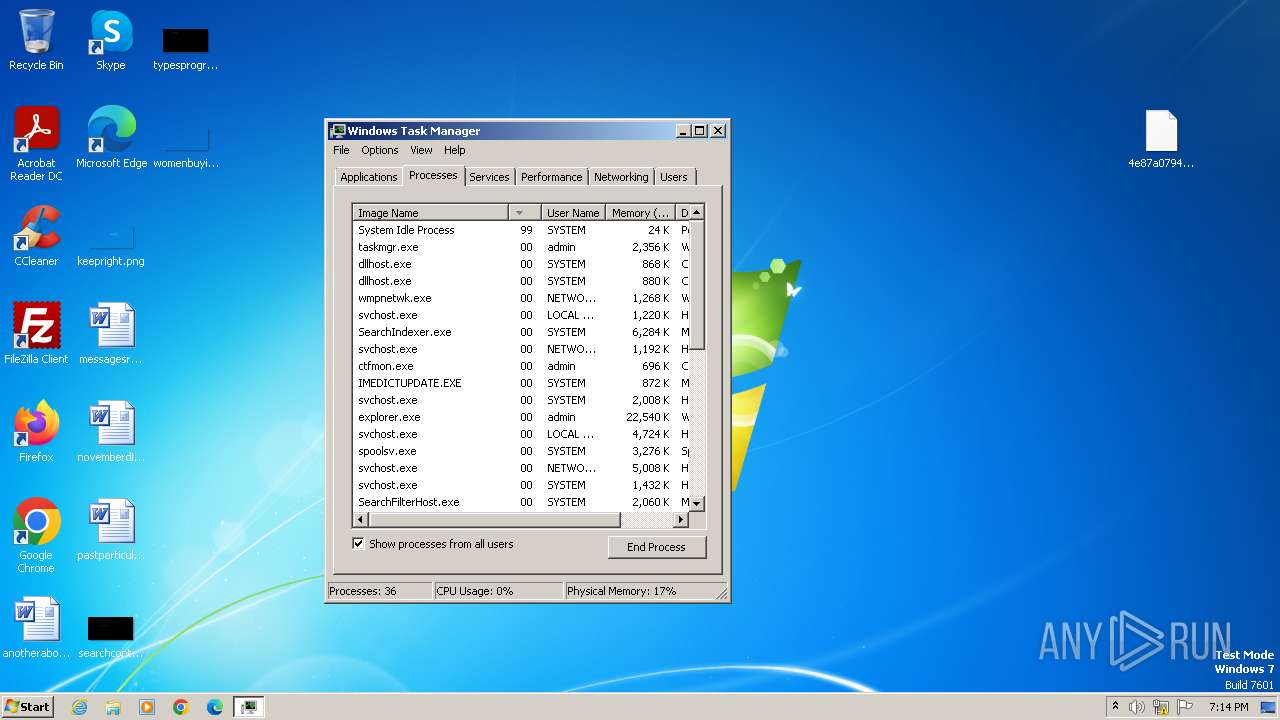
Total processes
59
Monitored processes
12
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
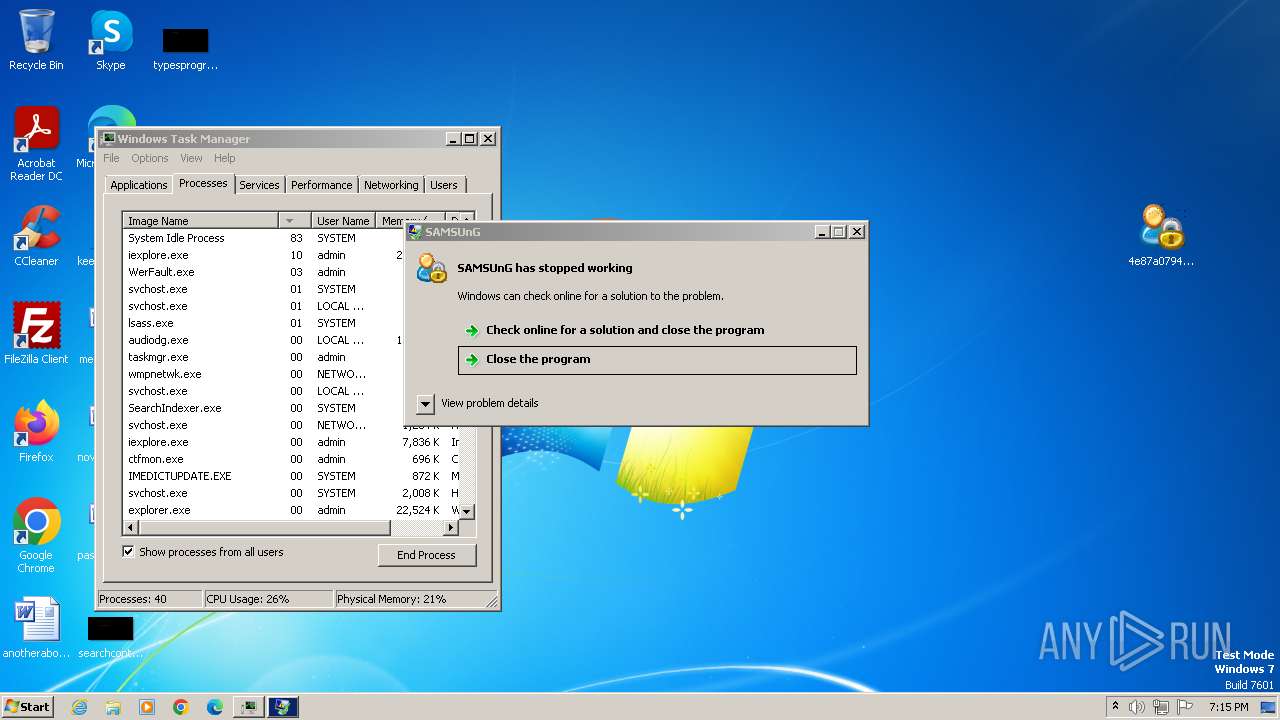
| 756 | "C:\Users\admin\Desktop\4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe" | C:\Users\admin\Desktop\4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe | explorer.exe | ||||||||||||
User: admin Company: SAMSUnG Integrity Level: HIGH Description: SAMSUnG Exit code: 0 Version: 3.04.0001 Modules
| |||||||||||||||
| 908 | "C:\Windows\System32\schtasks.exe" /run /tn "Eburin" | C:\Windows\System32\schtasks.exe | — | 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | "C:\Windows\System32\schtasks.exe" /Create /SC MINUTE /TN "Eburin" /TR "\"C:\ProgramData\Kip1.exe\"" | C:\Windows\System32\schtasks.exe | — | 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1032 | C:\ProgramData\Kip1.exe | C:\ProgramData\Kip1.exe | Kip1.exe | ||||||||||||
User: admin Company: SAMSUnG Integrity Level: MEDIUM Description: SAMSUnG Exit code: 3221225477 Version: 3.04.0001 Modules
| |||||||||||||||
| 1116 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1356 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1892 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1852 | C:\ProgramData\Kip1.exe | C:\ProgramData\Kip1.exe | — | taskeng.exe | |||||||||||
User: admin Company: SAMSUnG Integrity Level: MEDIUM Description: SAMSUnG Exit code: 0 Version: 3.04.0001 Modules
| |||||||||||||||
| 1892 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3128 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Gen.Heur.PonyStealer.4.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 133
Read events
14 035
Write events
90
Delete events
8
Modification events
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (3128) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
2
Suspicious files
26
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F2DDCD2B5F37625B82E81F4976CEE400_8FF5BE4204C5F704E3914BEF4952C317 | binary | |
MD5:6EDD0E9A9922AF6DBEE9A625B80418CE | SHA256:D56E0CA91953761993C249EE1A66E92A91F4707414A723C553019E97B0D41E17 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:03415E519A8043D3F51316A5244CB9F0 | SHA256:FA414E78A7D0B80C3FA0EC5D32923CDBB28EAD746D47A517854AEB024BA0C216 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:4A581734C4C4B57E4CD8C47760F235E7 | SHA256:53EFE452518AC06FF2DC2838DB46499962498A7733310BC0858C0431ADD6013A | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:E256374EA3DFDE87D87BFAC86B5BC807 | SHA256:4F23C530BD7F3001D8C65847C7528A3C67AB33AFFBC4F6FD1BAED5A9DF478923 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | binary | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F2DDCD2B5F37625B82E81F4976CEE400_8FF5BE4204C5F704E3914BEF4952C317 | binary | |
MD5:E5B9CD833FC898634A7423D66BE26BB3 | SHA256:890BEA85B914EB5C41149A1DEB76816EDFE7D3AA97399C1FE34DF0DABD4331EF | |||
| 756 | 4e87a0794bf73d06ac1ce4a37e33eb832ff4c89fb9e4266490c7cef9229d27a7.exe | C:\ProgramData\Kip1.exe | executable | |
MD5:B211348F8784EA450E1364C053046A6C | SHA256:CA11B8FFBC782DF697F34A26DF930970B1CED2EFBF89A34C506AE80A1CDC43BF | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:AB1CCF3D45926C982B7DB4640ECE9CE5 | SHA256:16C93D85FE838520DB4ACB2C7E7D169D3011EB851D59EDB738F3CC290BCAA558 | |||
| 1356 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\px[1].js | text | |
MD5:D2183968F9080B37BABFEBA3CCF10DF2 | SHA256:4D9B83714539F82372E1E0177924BCB5180B75148E22D6725468FD2FB6F96BCC | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
25
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1356 | iexplore.exe | GET | 200 | 8.241.11.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?82eb57de9b37ba1f | unknown | compressed | 4.66 Kb | unknown |
1356 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
1356 | iexplore.exe | GET | 302 | 5.79.79.211:80 | http://seeyouonlineservice.com/config.php | unknown | text | 11 b | unknown |
1356 | iexplore.exe | GET | 200 | 3.33.243.145:80 | http://ww1.seeyouonlineservice.com/px.js?ch=1&abp=1 | unknown | text | 476 b | unknown |
1356 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
1356 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQCLPpgizFvtXApe3cL6kC3u | unknown | binary | 472 b | unknown |
1356 | iexplore.exe | GET | 200 | 142.250.74.195:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEF2rtEA6xK7GEl4nbt8ZZfk%3D | unknown | binary | 471 b | unknown |
1356 | iexplore.exe | GET | 200 | 3.33.243.145:80 | http://ww1.seeyouonlineservice.com/ | unknown | html | 1.15 Kb | unknown |
1356 | iexplore.exe | GET | 200 | 3.33.243.145:80 | http://ww1.seeyouonlineservice.com/px.js?ch=2&abp=1 | unknown | text | 476 b | unknown |
1892 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1356 | iexplore.exe | 172.217.23.110:443 | google.com | GOOGLE | US | whitelisted |
1356 | iexplore.exe | 5.79.79.211:80 | seeyouonlineservice.com | LeaseWeb Netherlands B.V. | NL | unknown |
1356 | iexplore.exe | 8.241.11.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | unknown |
1356 | iexplore.exe | 142.250.74.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1356 | iexplore.exe | 3.33.243.145:80 | ww1.seeyouonlineservice.com | AMAZON-02 | US | unknown |
1356 | iexplore.exe | 142.250.185.196:443 | www.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
seeyouonlineservice.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ww1.seeyouonlineservice.com |
| unknown |
www.google.com |
| whitelisted |
img1.wsimg.com |
| whitelisted |
ocsp.starfieldtech.com |
| whitelisted |