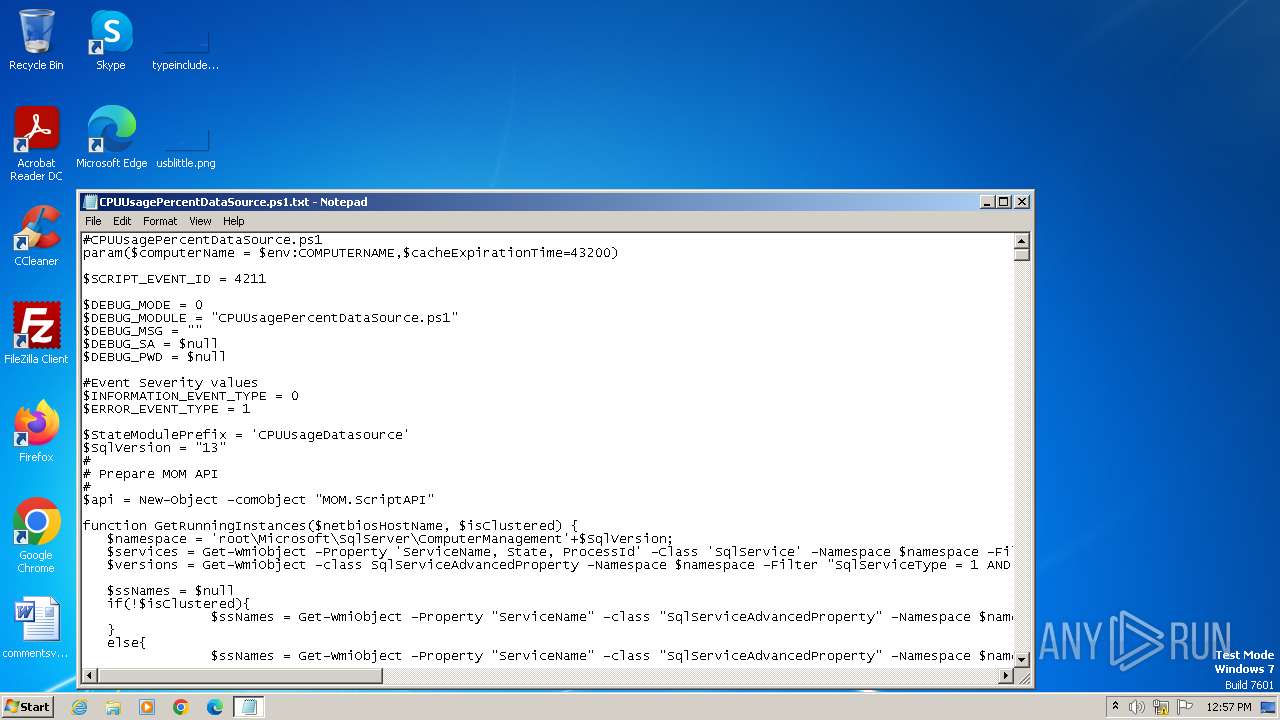
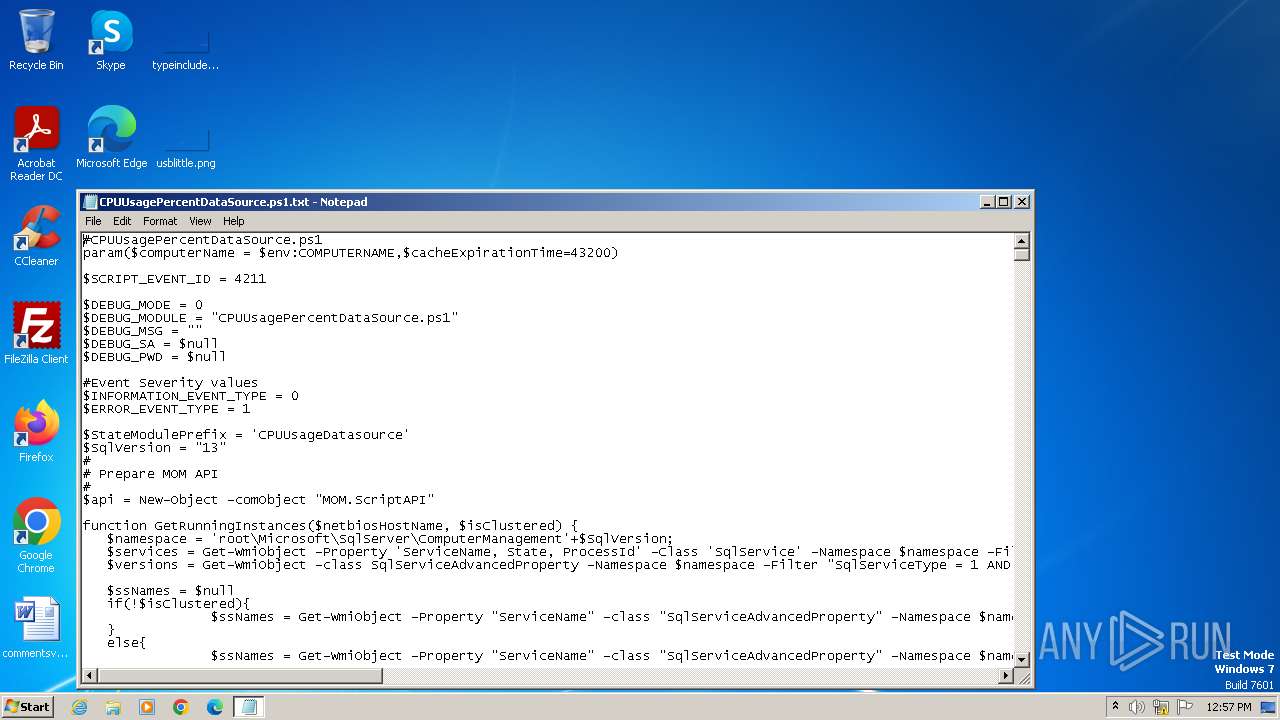
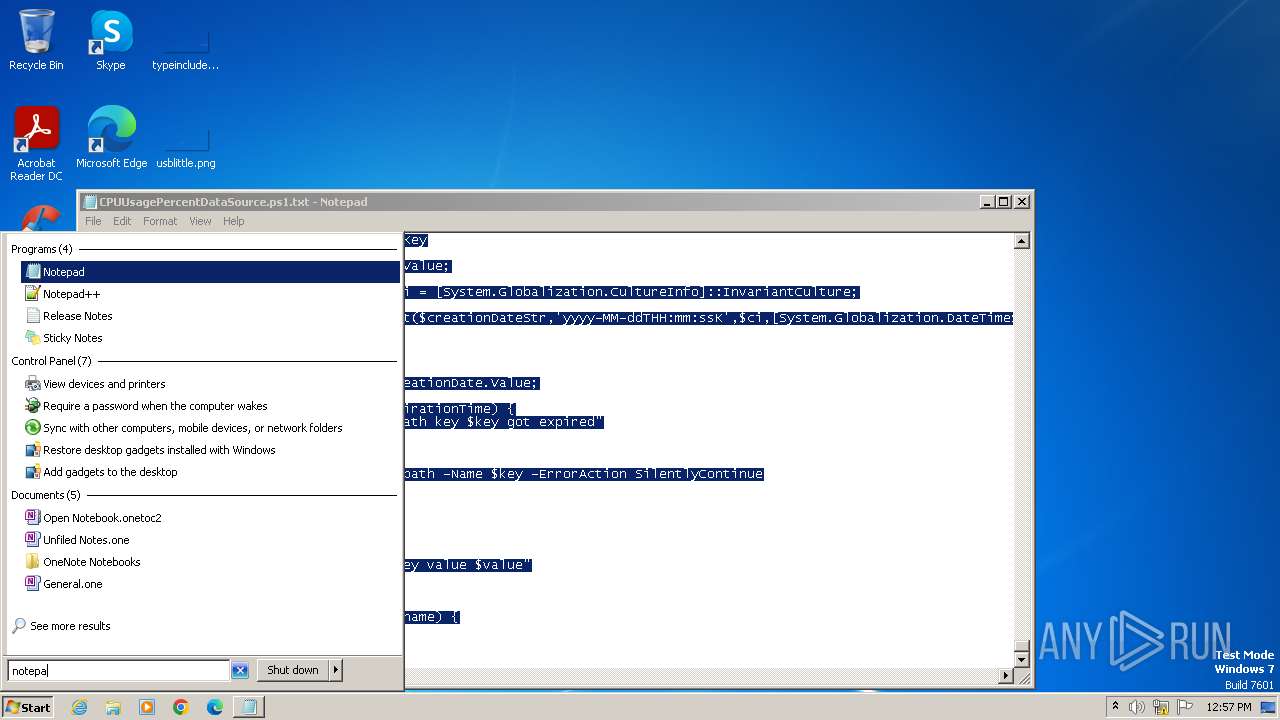
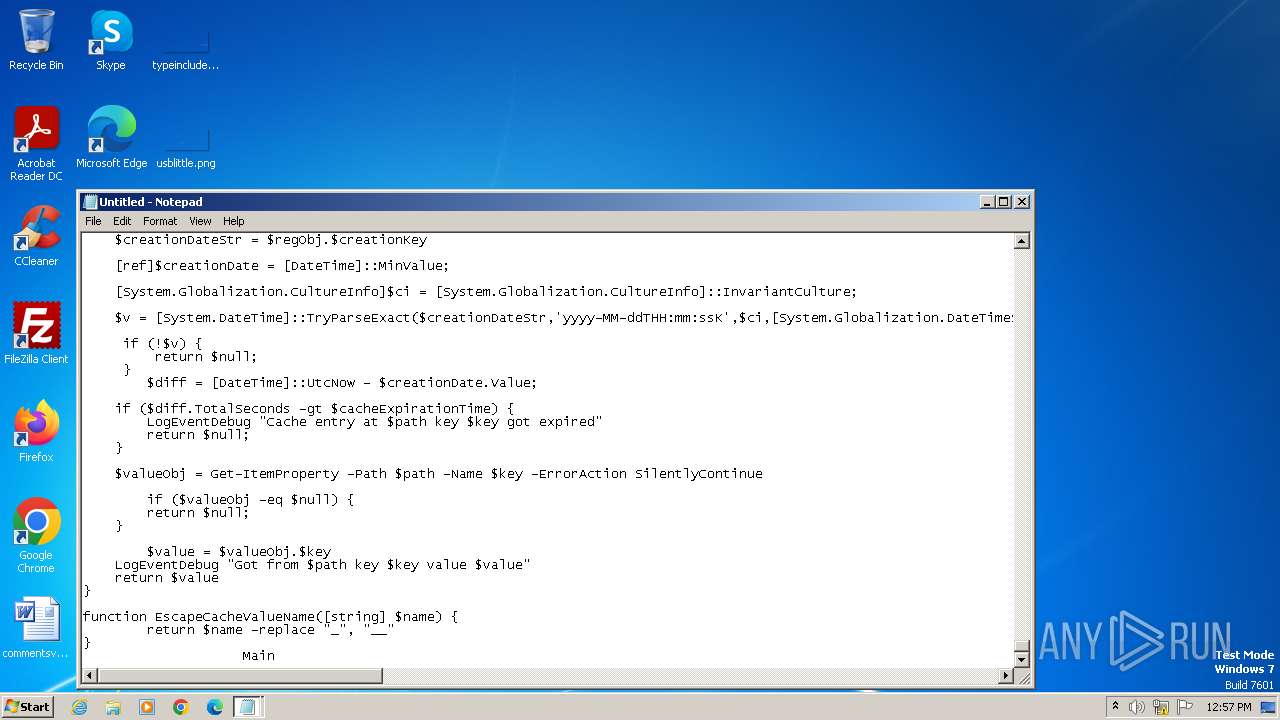
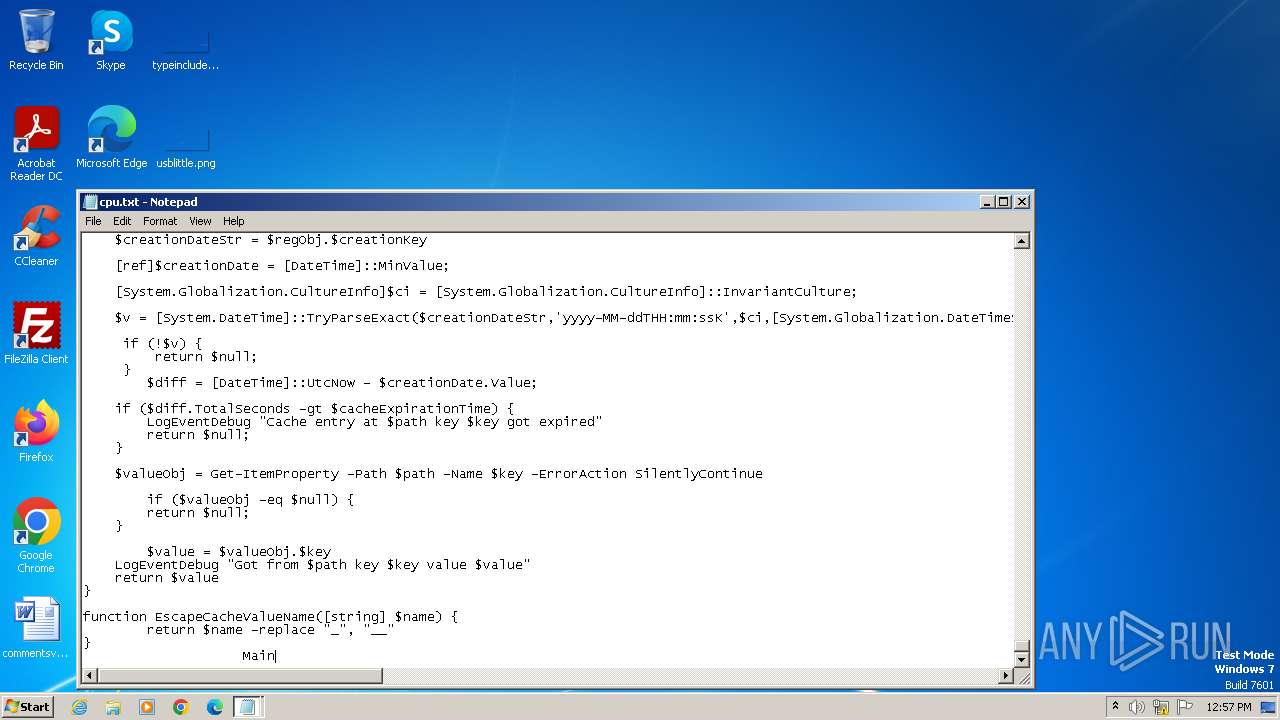
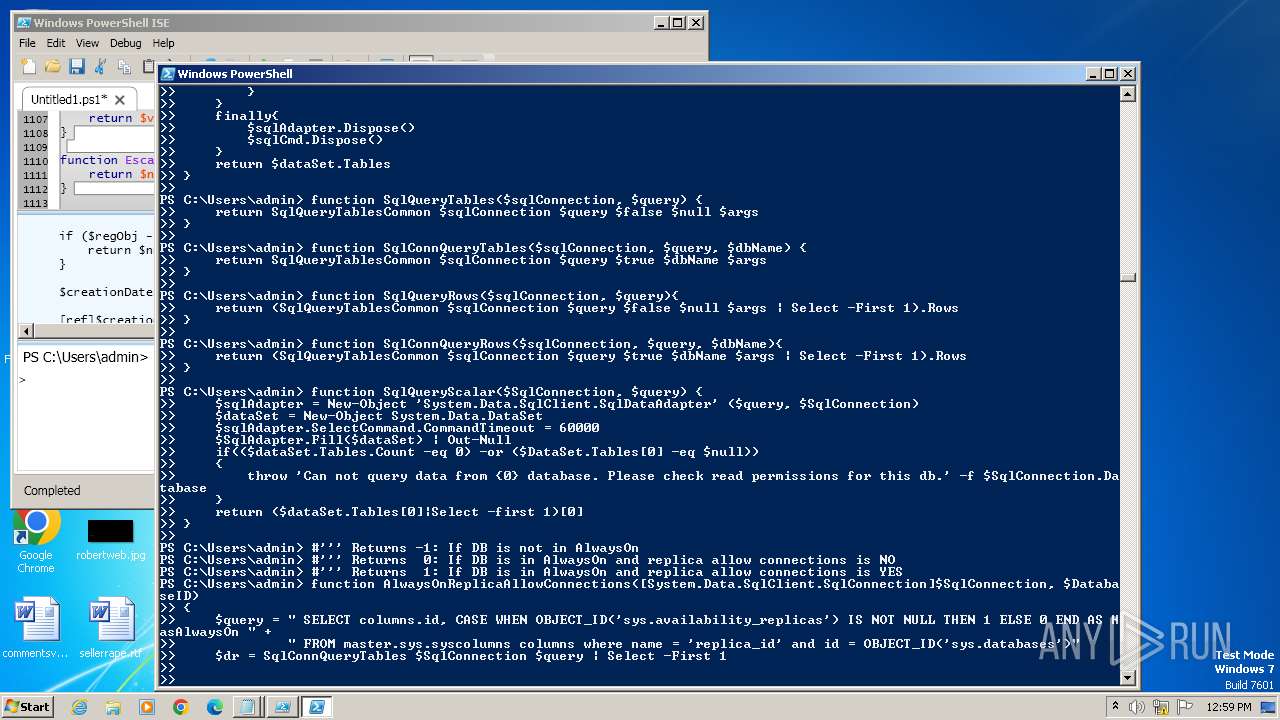
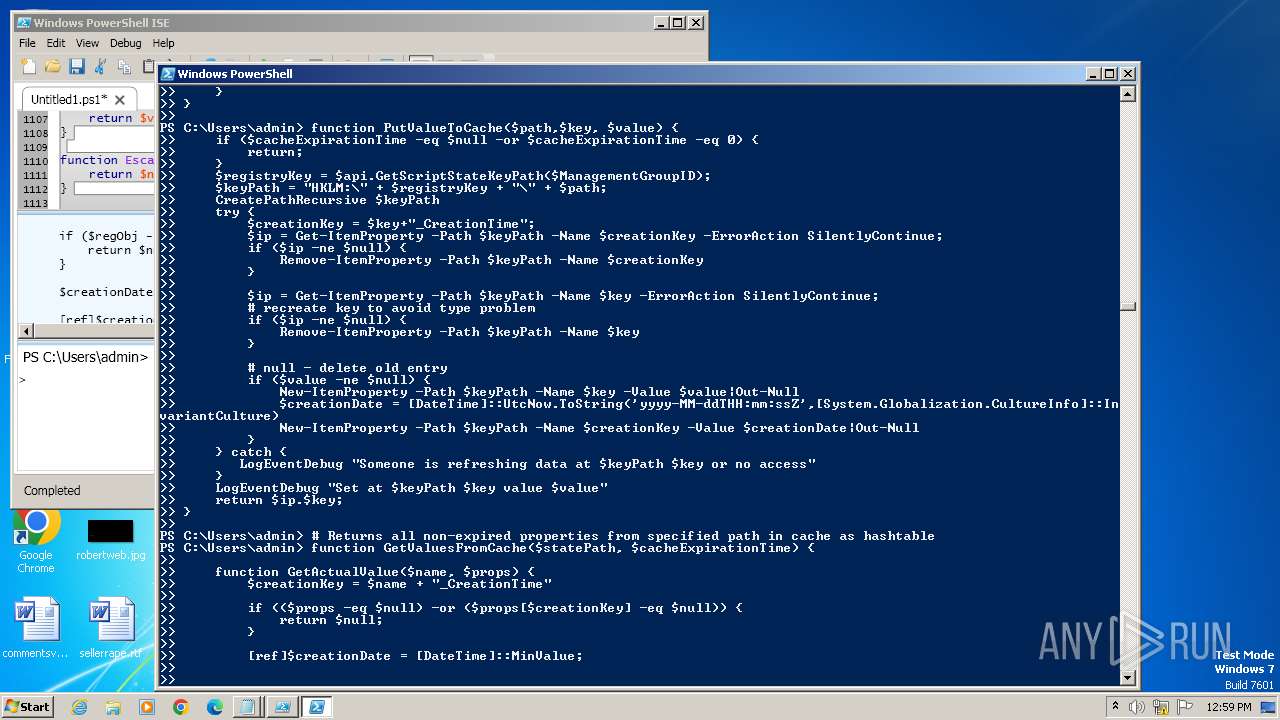
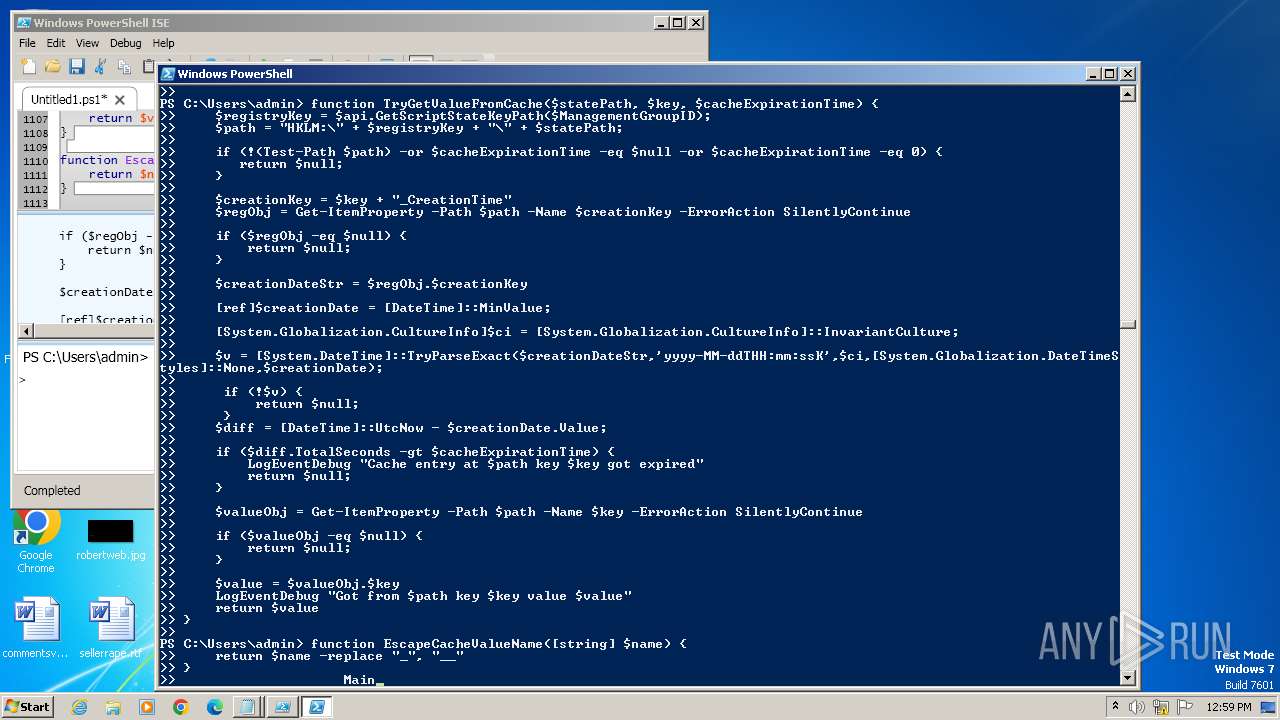
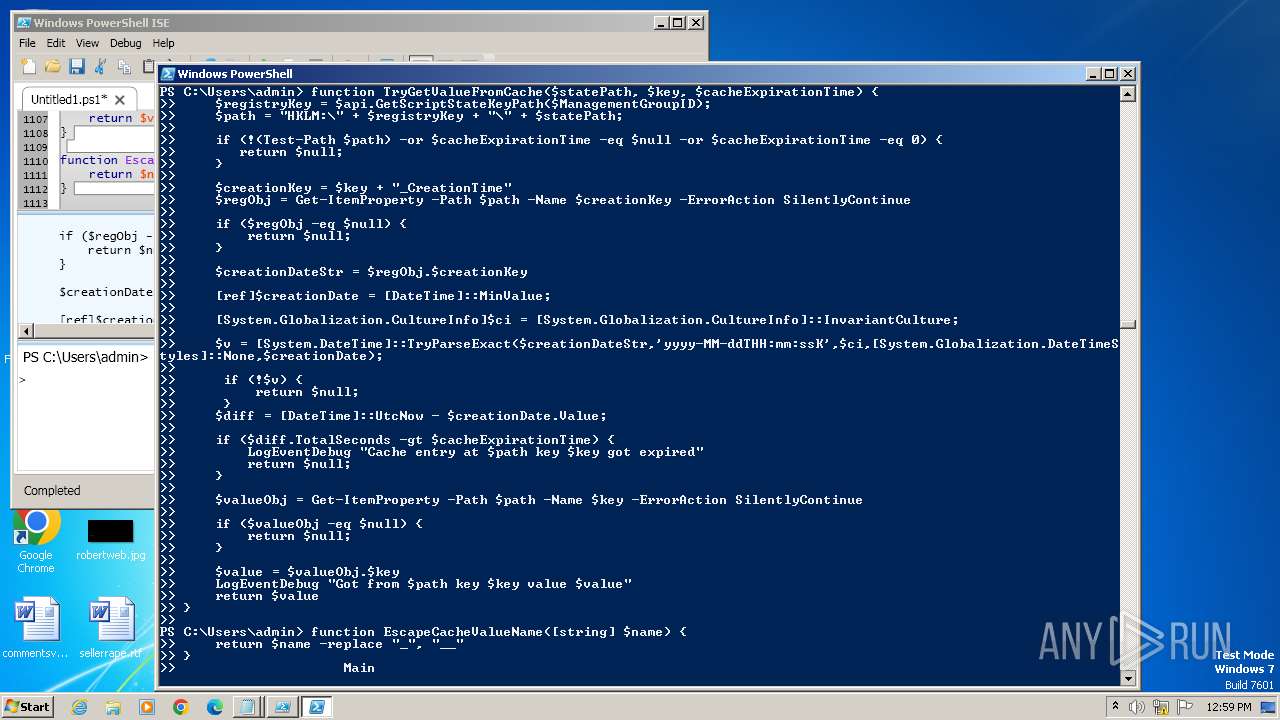
| File name: | CPUUsagePercentDataSource.ps1 |
| Full analysis: | https://app.any.run/tasks/75aa3d1a-b271-4459-bb7e-ce9063d35877 |
| Verdict: | Malicious activity |
| Analysis date: | November 02, 2023, 12:57:05 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Little-endian UTF-16 Unicode text, with very long lines, with CRLF line terminators |
| MD5: | A3957B3EB5628D8669DC1207D89A82DD |
| SHA1: | 1115A9E1F1CCFF858D2D9A20752B1A6EB391F790 |
| SHA256: | 9FAC67A4F44358311474C1ABF2207B4BD7D75D0C244863BFD77B43A2EB687F51 |
| SSDEEP: | 768:3p3e4yF7nRZthRhZAfGXu5u8jRjvr1JhkHh4I0MftbbyfVRZthRhZAAuYvYKiIj1:wJmzuHb02XRKiIjirNGeiJ1n |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads the Internet Settings
- notepad.exe (PID: 3512)
- PowerShell_ISE.exe (PID: 3944)
Executes as Windows Service
- PresentationFontCache.exe (PID: 3908)
Powershell version downgrade attack
- powershell.exe (PID: 4048)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3460)
- notepad.exe (PID: 3512)
- PowerShell_ISE.exe (PID: 3944)
- explorer.exe (PID: 3528)
- powershell.exe (PID: 4048)
Checks supported languages
- wmpnscfg.exe (PID: 3460)
- PresentationFontCache.exe (PID: 3908)
Reads the computer name
- wmpnscfg.exe (PID: 3460)
- PresentationFontCache.exe (PID: 3908)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3460)
- PresentationFontCache.exe (PID: 3908)
Creates files or folders in the user directory
- PowerShell_ISE.exe (PID: 3944)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
45
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3428 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\AppData\Local\Temp\CPUUsagePercentDataSource.ps1.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3460 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3512 | "C:\Windows\system32\notepad.exe" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3528 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3908 | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | C:\Windows\Microsoft.Net\Framework\v3.0\WPF\PresentationFontCache.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: PresentationFontCache.exe Exit code: 0 Version: 3.0.6920.4902 built by: NetFXw7 Modules
| |||||||||||||||
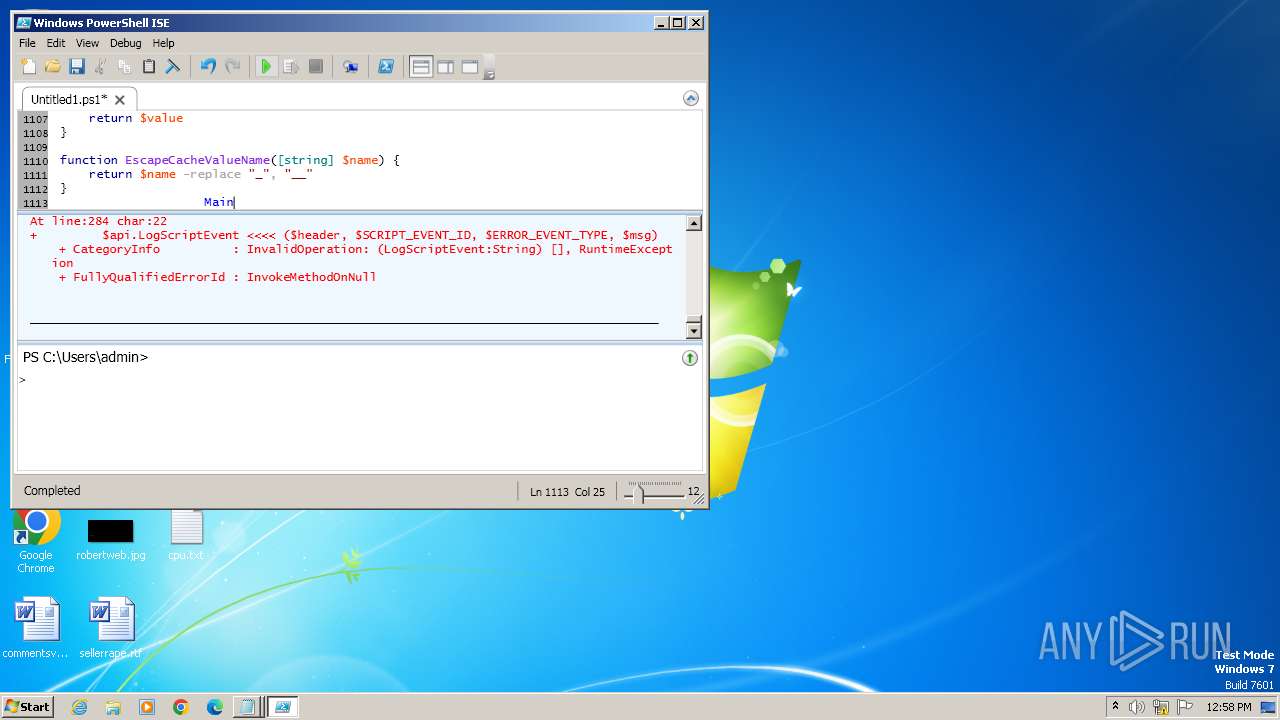
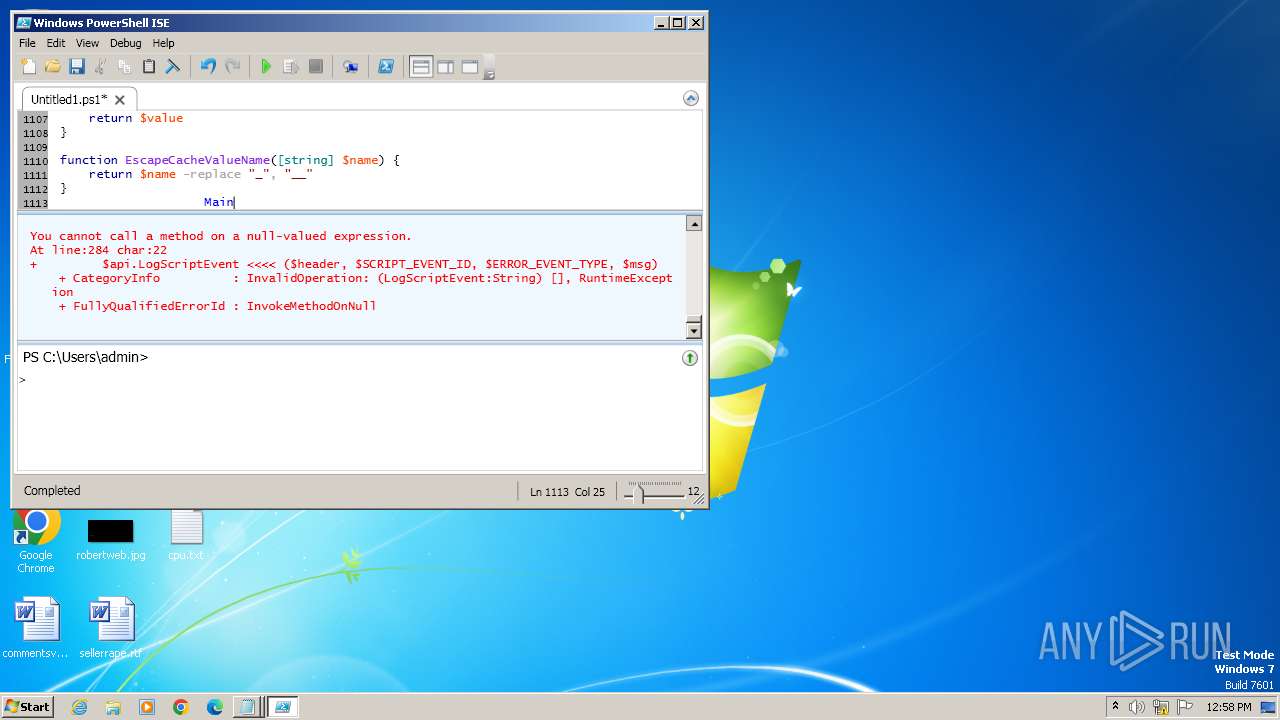
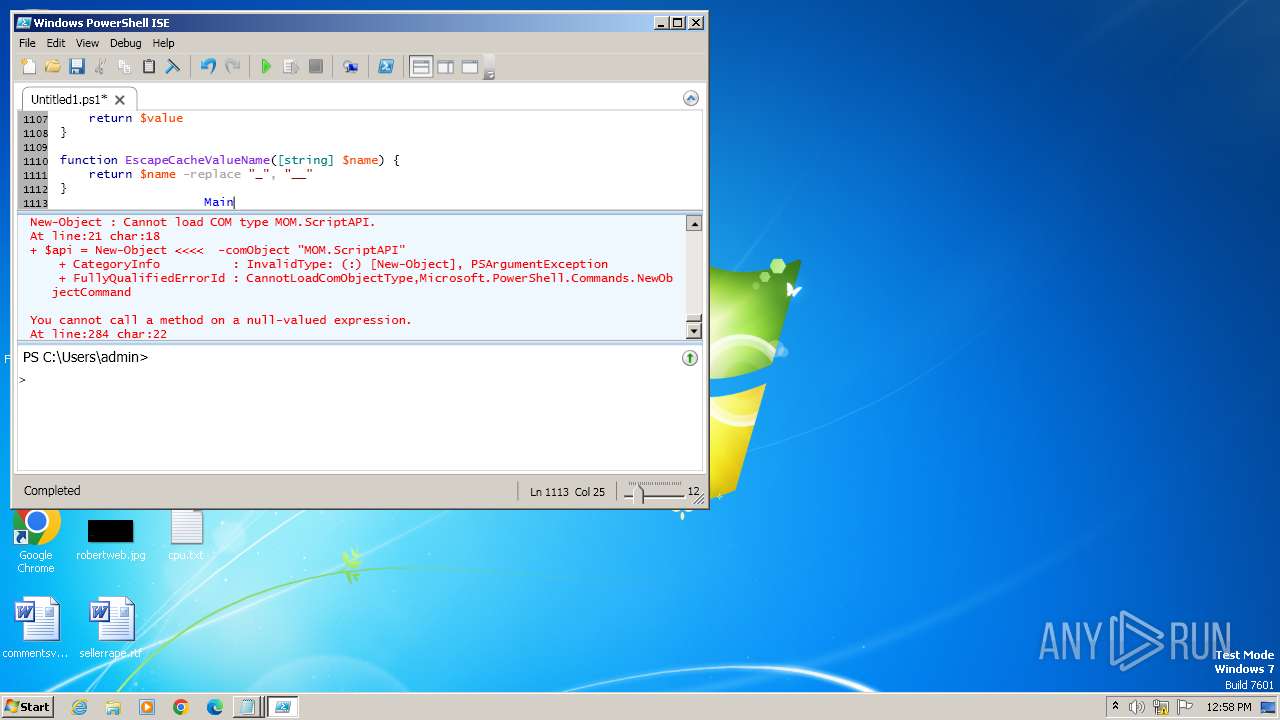
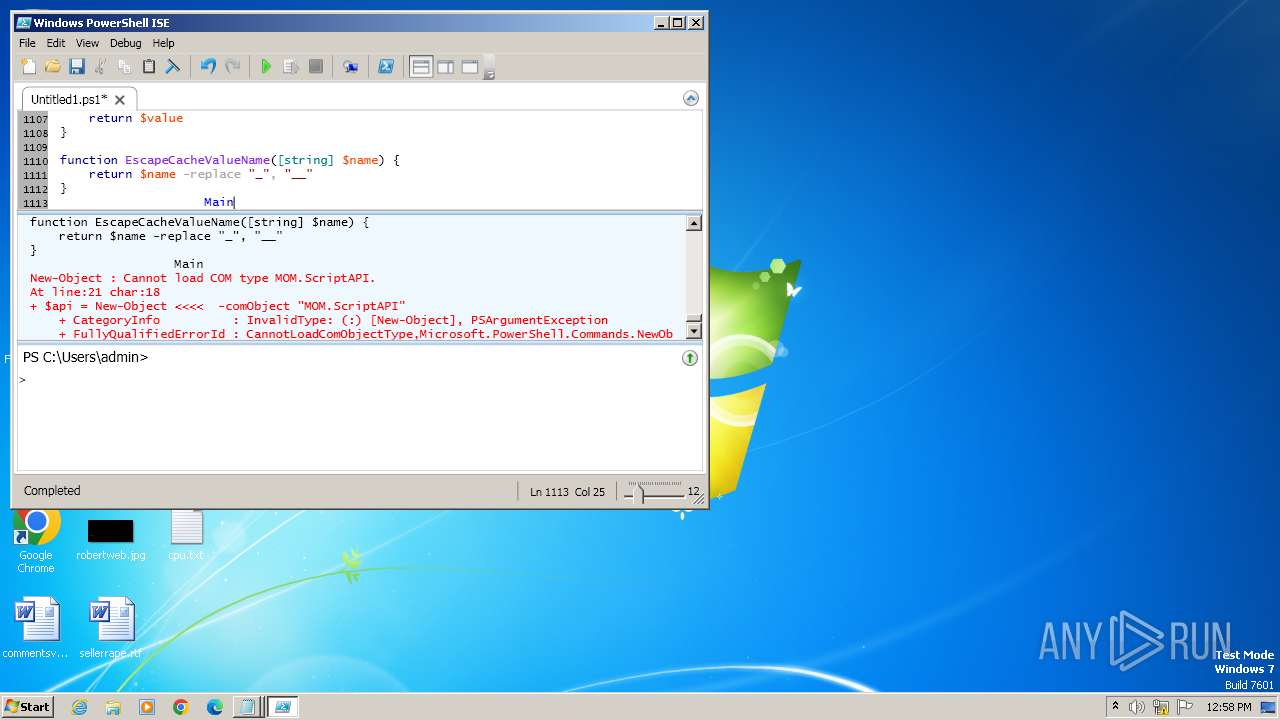
| 3944 | "C:\Windows\system32\WindowsPowerShell\v1.0\PowerShell_ISE.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\PowerShell_ISE.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell ISE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4048 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 316
Read events
5 204
Write events
107
Delete events
5
Modification events
| (PID) Process: | (3460) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{EB8C13BE-6828-4EF0-AF7B-F5A324CC6E41}\{6798FEA9-3EAD-4B24-8ED3-2799CB14B3FC} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3460) wmpnscfg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Media Player NSS\3.0\Events\{EB8C13BE-6828-4EF0-AF7B-F5A324CC6E41} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3460) wmpnscfg.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\MediaPlayer\Health\{86897002-B53B-49B9-92F1-910CA3D85C6E} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 01000000020000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 02000000010000000700000000000000060000000C0000000B0000000D0000000A0000000900000008000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (3512) notepad.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\H4G1FWGQ0YMV2IV6OOP4.temp | binary | |
MD5:855CA43939AE71B2832C68E9F2977F93 | SHA256:C67D06695A80DB87DC94A28811140D14A1A0A9796B48B8485272763B51EEDFE6 | |||
| 3944 | PowerShell_ISE.exe | C:\Users\admin\AppData\Local\microsoft\PowerShell_ISE\S-1-5-5-0-69763\PowerShellISEPipeName_0_d7a465cc-903f-4dc3-89c1-f5a73bfa3d5c | text | |
MD5:A5EA0AD9260B1550A14CC58D2C39B03D | SHA256:F1B2F662800122BED0FF255693DF89C4487FBDCF453D3524A42D4EC20C3D9C04 | |||
| 4048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF180b07.TMP | binary | |
MD5:C681106A4168B935996B10134404F885 | SHA256:89AB4ECFBB5C1FD07CF99465E36B1A08F51E2512AA60DDD616D4A37753FC112D | |||
| 3512 | notepad.exe | C:\Users\admin\Desktop\cpu.txt | text | |
MD5:6203E04476472AF15B58C0B0136E72BE | SHA256:096DDF7DD5CD72245CE3AAFBFB96440D711B3A7558F5D8339E42701205BB3E09 | |||
| 4048 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms | binary | |
MD5:855CA43939AE71B2832C68E9F2977F93 | SHA256:C67D06695A80DB87DC94A28811140D14A1A0A9796B48B8485272763B51EEDFE6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Threats
Process | Message |
|---|---|
PowerShell_ISE.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
PowerShell_ISE.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
PowerShell_ISE.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
PowerShell_ISE.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
PowerShell_ISE.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
PowerShell_ISE.exe |
*** HR propagated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\enumidentityattribute.cpp, line 144
|
PowerShell_ISE.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
PowerShell_ISE.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
PowerShell_ISE.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|
PowerShell_ISE.exe |
*** HR originated: -2147024774
*** Source File: d:\iso_whid\x86fre\base\isolation\com\copyout.cpp, line 1302
|