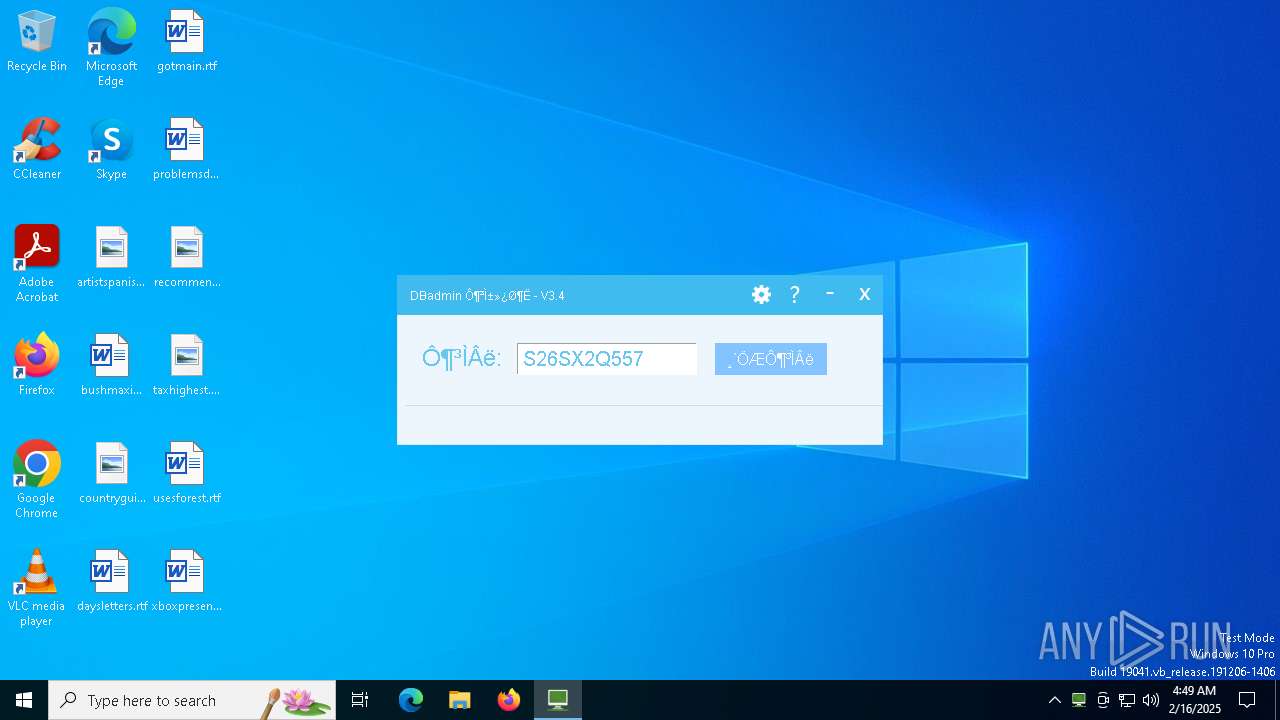
| File name: | DBadmin被控端.exe |
| Full analysis: | https://app.any.run/tasks/9511088b-d268-4931-ac0d-16411ea735b4 |
| Verdict: | Malicious activity |
| Analysis date: | February 16, 2025, 04:49:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | A81C0BC1B3DCD4A5386F81C3F013AFC0 |
| SHA1: | A2E0553D84F25859D3509D64ED58809A68104052 |
| SHA256: | 9FA13F87B3B7154C68C36FC9EC5CD3DEC4C5EE2A7D78F06EDD93539B1AC27AED |
| SSDEEP: | 49152:dOHy25KEkE+QSXkQtGxQn1VccQc+hd3bNMxddseacuwL534+LCowd9L9WsoHaoF5:dONXjQtG2A1RNcuY4+Wo69LHoHaoF5cb |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- DBadmin被控端.exe (PID: 6348)
Reads security settings of Internet Explorer
- DBadmin被控端.exe (PID: 6348)
Application launched itself
- DBremotes.exe (PID: 6528)
Potential Corporate Privacy Violation
- DBadmin被控端.exe (PID: 6348)
Connects to unusual port
- DBadmin被控端.exe (PID: 6348)
There is functionality for taking screenshot (YARA)
- DBadmin被控端.exe (PID: 6348)
- DBremotes.exe (PID: 6528)
- DBremotes.exe (PID: 6576)
INFO
Checks supported languages
- DBadmin被控端.exe (PID: 6348)
- DBremotes.exe (PID: 6500)
- DBremotes.exe (PID: 6528)
- DBremotes.exe (PID: 6576)
The sample compiled with chinese language support
- DBadmin被控端.exe (PID: 6348)
The sample compiled with english language support
- DBadmin被控端.exe (PID: 6348)
Reads the computer name
- DBadmin被控端.exe (PID: 6348)
- DBremotes.exe (PID: 6528)
Checks proxy server information
- DBadmin被控端.exe (PID: 6348)
Create files in a temporary directory
- DBadmin被控端.exe (PID: 6348)
- DBremotes.exe (PID: 6528)
UPX packer has been detected
- DBadmin被控端.exe (PID: 6348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (28.6) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (28) |
| .exe | | | Win32 EXE Yoda's Crypter (27.5) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.8) |
| .exe | | | Win32 Executable (generic) (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:04:23 13:26:41+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1363968 |
| InitializedDataSize: | 16384 |
| UninitializedDataSize: | 2342912 |
| EntryPoint: | 0x3893b0 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.3.2.0 |
| ProductVersionNumber: | 3.3.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Chinese (Simplified) |
| CharacterSet: | Unicode |
| FileVersion: | 3.3.2.0 |
| FileDescription: | DBadmin远程被控端 |
| ProductName: | DBadmin远程被控端 |
| ProductVersion: | 3.3.2.0 |
| CompanyName: | 定做技术支持邮箱: wgLm@qq.com |
| LegalCopyright: | 定做技术支持邮箱: wgLm@qq.com |
| Comments: | 定做技术支持邮箱: wgLm@qq.com |
Total processes
131
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6348 | "C:\Users\admin\AppData\Local\Temp\DBadmin被控端.exe" | C:\Users\admin\AppData\Local\Temp\DBadmin被控端.exe | explorer.exe | ||||||||||||
User: admin Company: 定做技术支持邮箱: wgLm@qq.com Integrity Level: MEDIUM Description: DBadmin远程被控端 Version: 3.3.2.0 Modules
| |||||||||||||||
| 6500 | C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe -setservicevncpass 0e74f08 -setservicereadpass 0e74f09 -setservicerfbport 49686 -setserviceremovedeskwall 1 -setservicetrayicon 0 -setapp | C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe | — | DBadmin被控端.exe | |||||||||||
User: admin Company: sLsup.com Integrity Level: MEDIUM Description: sLsup.com Exit code: 0 Version: 3, 2, 0, 0 Modules
| |||||||||||||||
| 6528 | "C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe" | C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe | — | DBadmin被控端.exe | |||||||||||
User: admin Company: sLsup.com Integrity Level: MEDIUM Description: sLsup.com Version: 3, 2, 0, 0 Modules
| |||||||||||||||
| 6576 | "C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe" -controlapp -slave | C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe | — | DBremotes.exe | |||||||||||
User: admin Company: sLsup.com Integrity Level: MEDIUM Description: sLsup.com Version: 3, 2, 0, 0 Modules
| |||||||||||||||
Total events
1 139
Read events
1 097
Write events
40
Delete events
2
Modification events
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | ExtraPorts |
Value: | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | QueryTimeout |
Value: 30 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | QueryAcceptOnTimeout |
Value: 0 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | LocalInputPriorityTimeout |
Value: 3 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | LocalInputPriority |
Value: 0 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | BlockRemoteInput |
Value: 0 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | BlockLocalInput |
Value: 0 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | IpAccessControl |
Value: | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | RfbPort |
Value: 49686 | |||
| (PID) Process: | (6500) DBremotes.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\NATVnc\Server |
| Operation: | write | Name: | HttpPort |
Value: 5800 | |||
Executable files
3
Suspicious files
0
Text files
16
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6348 | DBadmin被控端.exe | C:\Users\admin\AppData\Local\Temp\inc\16_rdpClient.log | text | |
MD5:6752C983D6AF1984155435155A60B712 | SHA256:487A157FE4337B98D87AE22F921A72E41FBAF8B192438BE96967626F24E80A8F | |||
| 6348 | DBadmin被控端.exe | C:\Users\admin\AppData\Local\Temp\inc\±»¿Ø¶Ë.log | text | |
MD5:17E62C52057A40E9790BECEE5F180A6D | SHA256:ECFFB5CB6D59179AA4B67B745A3DFBF9DEAD0624D424646FB6BD49D014C41818 | |||
| 6348 | DBadmin被控端.exe | C:\Users\admin\AppData\Local\Temp\inc\DBremotes.exe | executable | |
MD5:21097291AE55DC2565A4C0362348B7F1 | SHA256:DDA179F332180866998386FE447656E1432187C989E970FC19D41D30BE70ADEB | |||
| 6348 | DBadmin被控端.exe | C:\Users\admin\AppData\Local\Temp\inc\tsPairServer.dll | executable | |
MD5:C0755EC60B32BF59FB13758F958106E6 | SHA256:1560C0FA0CD5FCBFBBF0361AE3ECD647F5A75E3A699514B39F9255E7708E9288 | |||
| 6348 | DBadmin被控端.exe | C:\Users\admin\AppData\Local\Temp\inc\ToolTsClient.dll | executable | |
MD5:446C0A7734DB91342B8B10E57F3A6B09 | SHA256:619B73099FD5CD8DC931666FF8EFABAF3491A3D21F2AFB1B47F2D2E740E9700F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
13
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6348 | DBadmin被控端.exe | GET | 200 | 49.234.67.74:80 | http://serstate.slser.com/getServer.php?s=NewVer2 | unknown | — | — | unknown |
6348 | DBadmin被控端.exe | GET | 200 | 49.234.67.74:80 | http://serstate.slser.com/getServer.php?s=notice | unknown | — | — | unknown |
6184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7012 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6184 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5776 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6348 | DBadmin被控端.exe | 59.34.14.18:42800 | remoteser.slser.com | Chinanet | CN | unknown |
6348 | DBadmin被控端.exe | 49.234.67.74:80 | serstate.slser.com | Shenzhen Tencent Computer Systems Company Limited | CN | unknown |
2144 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1076 | svchost.exe | 184.30.18.9:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6348 | DBadmin被控端.exe | 59.34.14.18:42801 | remoteser.slser.com | Chinanet | CN | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
remoteser.slser.com |
| unknown |
serstate.slser.com |
| unknown |
settings-win.data.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6348 | DBadmin被控端.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
6348 | DBadmin被控端.exe | Potential Corporate Privacy Violation | ET INFO Unsupported/Fake Windows NT Version 5.0 |
6348 | DBadmin被控端.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] VNC negotiation has been detected (ProtocolVersion message) |
— | — | Misc activity | SUSPICIOUS [ANY.RUN] Sent Host Name in HTTP POST Body |
— | — | A Network Trojan was detected | ET MALWARE Generic - POST To .php w/Extended ASCII Characters |