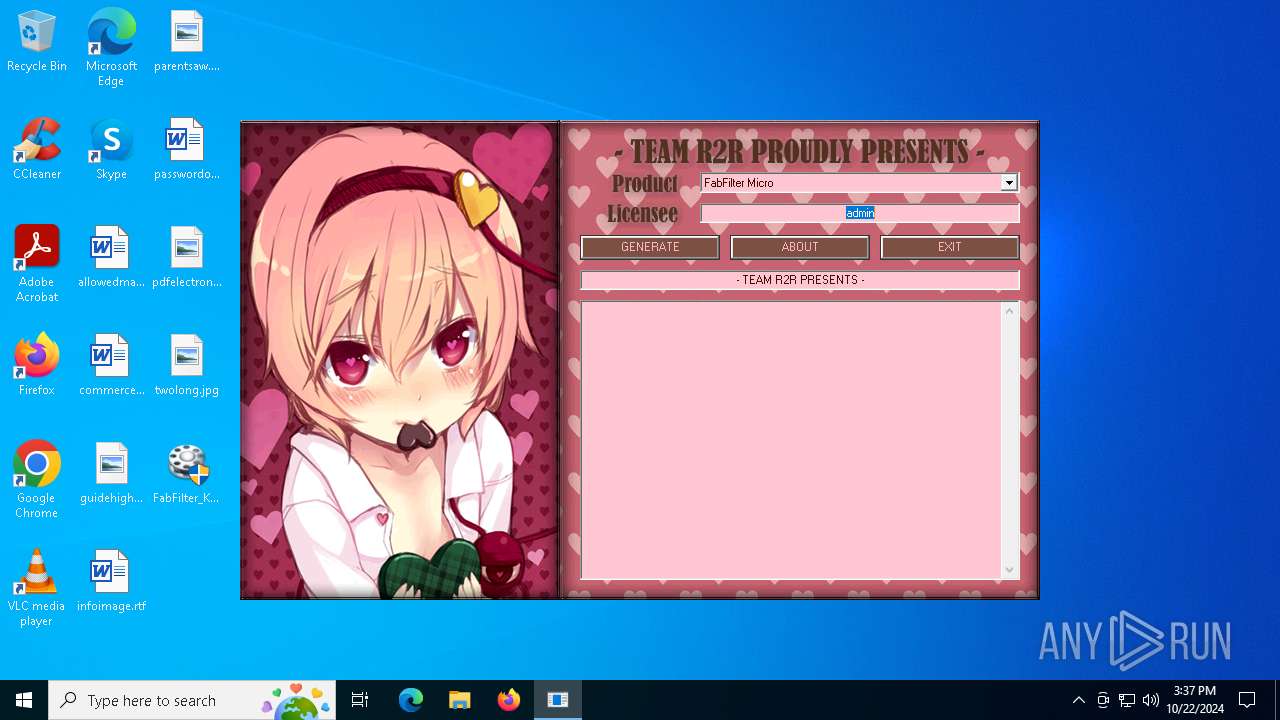
| File name: | FabFilter_KeyGen.exe |
| Full analysis: | https://app.any.run/tasks/90ff8f92-1ce6-4153-8337-e404e195bc47 |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2024, 15:37:16 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 3466AE073E7F90070C92EC029D2EFC2A |
| SHA1: | B60E83B94A07F0C69E01A768F24E785EB807B87A |
| SHA256: | 9F79FD90D7DE8680CCE1CDFCFFBB95892E9DFD5159239BC732BC6AECA80E92D0 |
| SSDEEP: | 98304:n+fgB8UfO3xqEzRqFJx45jfG3R3L5i+sIAmXOu+6EdqgSQkQktJeNqh3NcluzQGL:Rxsz45x |
MALICIOUS
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 6684)
Adds extension to the Windows Defender exclusion list
- cmd.exe (PID: 6684)
SUSPICIOUS
Executable content was dropped or overwritten
- FabFilter_KeyGen.exe (PID: 6588)
- FabFilter_KeyGen.exe (PID: 6664)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6684)
Process drops legitimate windows executable
- FabFilter_KeyGen.exe (PID: 6588)
Starts CMD.EXE for commands execution
- FabFilter_KeyGen.exe (PID: 6588)
Executing commands from a ".bat" file
- FabFilter_KeyGen.exe (PID: 6588)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 6684)
Script adds exclusion extension to Windows Defender
- cmd.exe (PID: 6684)
Drops a system driver (possible attempt to evade defenses)
- FabFilter_KeyGen.exe (PID: 6588)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Delphi generic (37.4) |
|---|---|---|
| .scr | | | Windows screen saver (34.5) |
| .exe | | | Win32 Executable (generic) (11.9) |
| .exe | | | Win16/32 Executable Delphi generic (5.4) |
| .exe | | | Generic Win/DOS Executable (5.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 148992 |
| InitializedDataSize: | 166400 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x25468 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| Comments: | - |
| CompanyName: | FabFilter KeyGen |
| FileDescription: | FabFilter KeyGen 1.0 Installation |
| FileVersion: | 1.0 |
| LegalCopyright: | FabFilter KeyGen |
Total processes
139
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 512 | powershell.exe Add-MpPreference -ExclusionPath C:\Windows\WinS | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3648 | C:\Users\admin\AppData\Local\Temp\keygen.exe | C:\Users\admin\AppData\Local\Temp\keygen.exe | — | FabFilter_KeyGen.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4208 | powershell.exe Add-MpPreference -ExclusionPath C:\ | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4448 | powershell.exe Add-MpPreference -ExclusionExtension ".zip" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5736 | powershell.exe Add-MpPreference -ExclusionExtension ".bat" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6380 | powershell.exe Add-MpPreference -ExclusionExtension ".sys" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6472 | powershell.exe Add-MpPreference -ExclusionExtension ".exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6540 | "C:\Users\admin\Desktop\FabFilter_KeyGen.exe" | C:\Users\admin\Desktop\FabFilter_KeyGen.exe | — | explorer.exe | |||||||||||
User: admin Company: FabFilter KeyGen Integrity Level: MEDIUM Description: FabFilter KeyGen 1.0 Installation Exit code: 3221226540 Version: 1.0 Modules
| |||||||||||||||
| 6588 | "C:\Users\admin\Desktop\FabFilter_KeyGen.exe" | C:\Users\admin\Desktop\FabFilter_KeyGen.exe | explorer.exe | ||||||||||||
User: admin Company: FabFilter KeyGen Integrity Level: HIGH Description: FabFilter KeyGen 1.0 Installation Exit code: 0 Version: 1.0 Modules
| |||||||||||||||
| 6660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
31 635
Read events
31 573
Write events
62
Delete events
0
Modification events
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | Type |
Value: 16 | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | Start |
Value: 2 | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | ErrorControl |
Value: 1 | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | ImagePath |
Value: C:\Windows\WinS\wmpnetwk.exe | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | Description |
Value: WMI Providers | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | DisplayName |
Value: WMIs | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | ObjectName |
Value: LocalSystem | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | DelayedAutostart |
Value: 0 | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | FailureActionsOnNonCrashFailures |
Value: 1 | |||
| (PID) Process: | (6588) FabFilter_KeyGen.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\WMS |
| Operation: | write | Name: | FailureActions |
Value: 00000000000000000000000003000000140000000100000060EA00000100000060EA00000100000060EA0000 | |||
Executable files
7
Suspicious files
5
Text files
25
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6588 | FabFilter_KeyGen.exe | C:\Windows\WinS\wd.bat | text | |
MD5:479988FE0741BA53D6682562377FBEE6 | SHA256:490C8EF0D7AA7DAA4255FF0792E4BA8D5EDAD5E2F8AB032DA1AC77019A207146 | |||
| 6588 | FabFilter_KeyGen.exe | C:\Program Files (x86)\FabFilter KeyGen\FabFilter KeyGen\FabFilter_KeyGen.exe | executable | |
MD5:4BE8F03C51F006A7CA3542E571ACB6BB | SHA256:5C7D774313E58E4E3B93D7860126E9DF834EAD52E03C696A42C398D6DDD6A039 | |||
| 6664 | FabFilter_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\bgm.it | binary | |
MD5:5E3C083251880C635F5EA6A0A6ED8E76 | SHA256:9D460A48D7F7F461967C9065182456871606EEF1C27F21767335B7D81384E141 | |||
| 4208 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_1haalksl.u54.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 512 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_rndmc1ph.czv.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6588 | FabFilter_KeyGen.exe | C:\Windows\WinS\WinRing0x64.sys | executable | |
MD5:0C0195C48B6B8582FA6F6373032118DA | SHA256:11BD2C9F9E2397C9A16E0990E4ED2CF0679498FE0FD418A3DFDAC60B5C160EE5 | |||
| 512 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dl3zxhqb.bnu.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 512 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:FBEA534931CA19F79F75FA855D8BA061 | SHA256:70F7077F6DCA2708032ED777848AB99E00173C24733758C8F7257BE3DD25BF86 | |||
| 6664 | FabFilter_KeyGen.exe | C:\Users\admin\AppData\Local\Temp\R2RFBFKG.dll | executable | |
MD5:62695F6FA2A85FC9993F57DFCBDC2749 | SHA256:1AB33027C4965B027298651781A1C780C272818DA189E2C3A8101AC578069260 | |||
| 6588 | FabFilter_KeyGen.exe | C:\Windows\WinS\xcopy.exe | executable | |
MD5:0991DCEC346F1FC78202217F6BCF516E | SHA256:08652A35530AB52E938DAB3478332C2E74A08D48E9E1C200F08B6F44A2094F06 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6908 | RUXIMICS.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6908 | RUXIMICS.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 2.23.9.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6908 | RUXIMICS.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6908 | RUXIMICS.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
5488 | MoUsoCoreWorker.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
6944 | svchost.exe | 2.23.9.218:80 | www.microsoft.com | AKAMAI-AS | CZ | whitelisted |
6944 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |