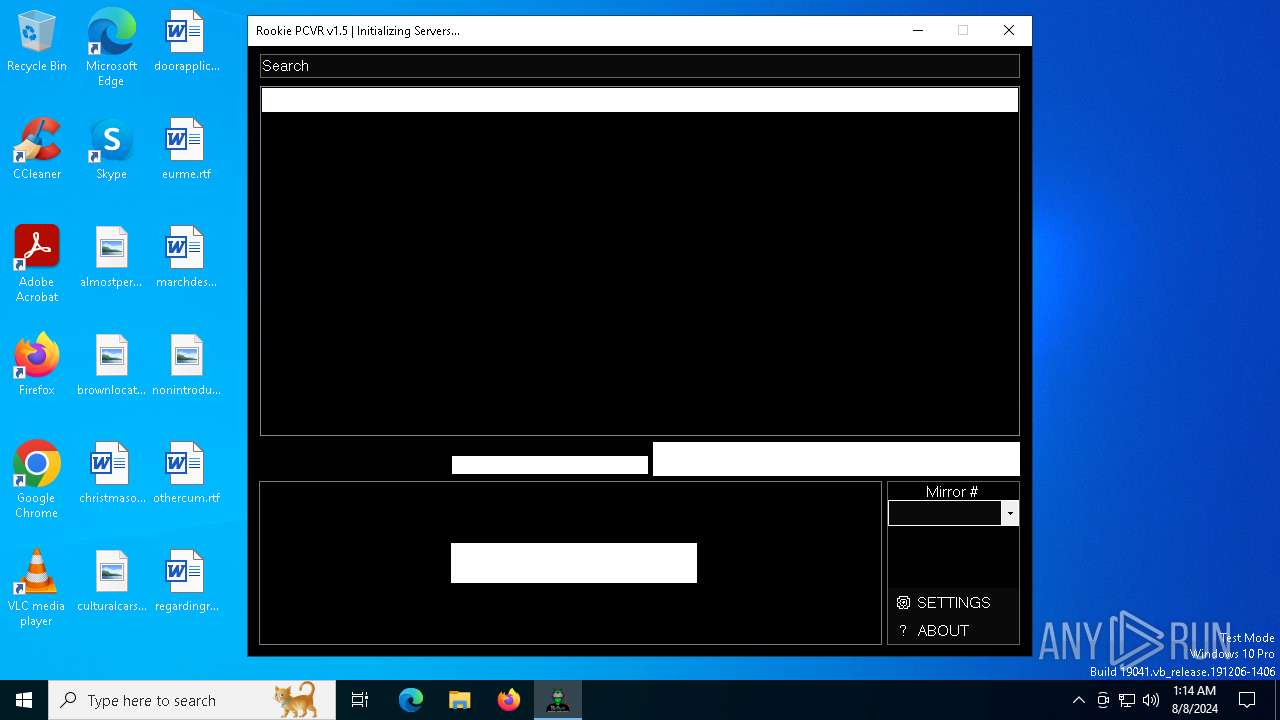
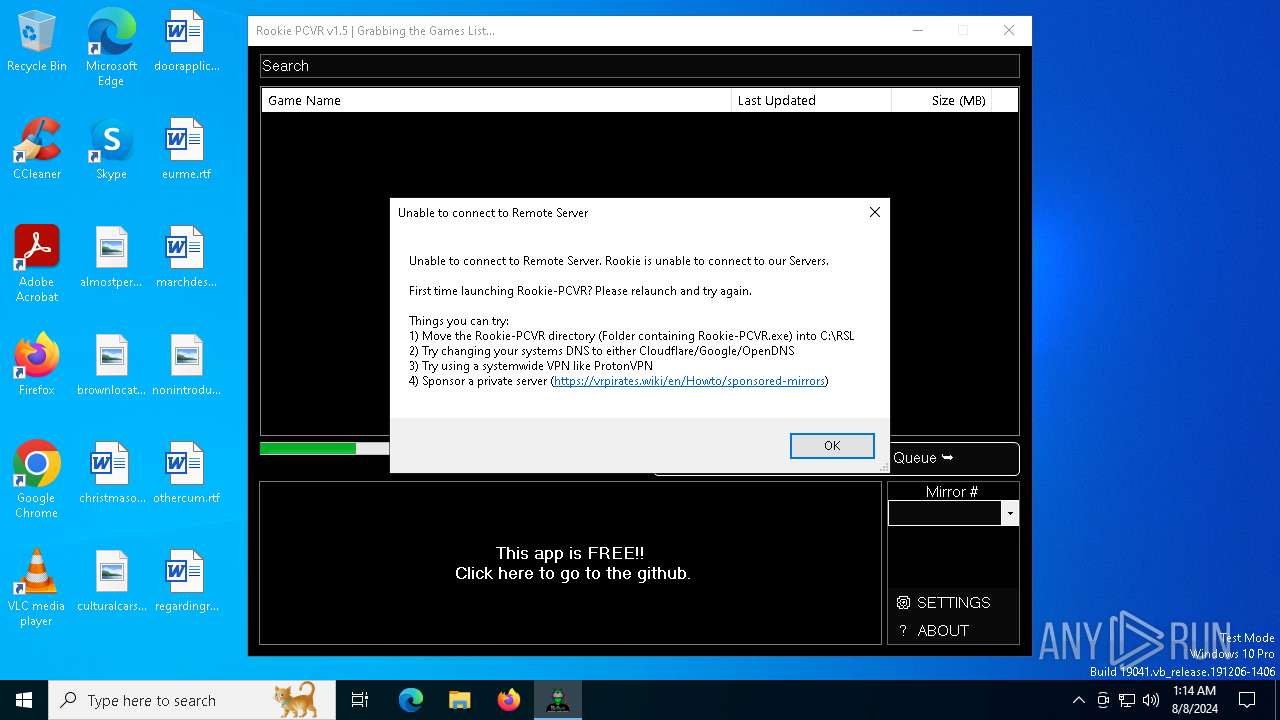
| File name: | PCVR-Rookie.exe |
| Full analysis: | https://app.any.run/tasks/da6e2bf7-4c41-41c5-9e18-2db40cd827e7 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2024, 01:13:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 7E660168665D26CD71ED031BBE6D76B7 |
| SHA1: | EA90944F7F589F92D0322C4E3EB4943CF449FE5F |
| SHA256: | 9F71F0C21498C7E2957E8BA80BDDEE5AC53C33E45FA2FB6D93C661955C3A318C |
| SSDEEP: | 24576:tlof8vpaSUHexvHrLMO9srQWGY65PsOutJ0dT5:Pof8vpaSUHexfrLMO9srQWGY+PsOuJ0T |
MALICIOUS
Drops the executable file immediately after the start
- PCVR-Rookie.exe (PID: 6620)
SUSPICIOUS
Executable content was dropped or overwritten
- PCVR-Rookie.exe (PID: 6620)
Reads security settings of Internet Explorer
- PCVR-Rookie.exe (PID: 6620)
Drops 7-zip archiver for unpacking
- PCVR-Rookie.exe (PID: 6620)
INFO
Checks supported languages
- PCVR-Rookie.exe (PID: 6620)
- 7z.exe (PID: 6856)
- rclone.exe (PID: 6828)
- rclone.exe (PID: 7024)
- rclone.exe (PID: 460)
- rclone.exe (PID: 4296)
- rclone.exe (PID: 4308)
- rclone.exe (PID: 2468)
- rclone.exe (PID: 6712)
- rclone.exe (PID: 6800)
- rclone.exe (PID: 2804)
- rclone.exe (PID: 6844)
- rclone.exe (PID: 5116)
- rclone.exe (PID: 1104)
- rclone.exe (PID: 4084)
Reads Environment values
- PCVR-Rookie.exe (PID: 6620)
Creates files or folders in the user directory
- PCVR-Rookie.exe (PID: 6620)
Reads the computer name
- PCVR-Rookie.exe (PID: 6620)
- 7z.exe (PID: 6856)
- rclone.exe (PID: 6828)
- rclone.exe (PID: 7024)
- rclone.exe (PID: 460)
- rclone.exe (PID: 4296)
- rclone.exe (PID: 2468)
- rclone.exe (PID: 6800)
- rclone.exe (PID: 6712)
- rclone.exe (PID: 4308)
- rclone.exe (PID: 2804)
- rclone.exe (PID: 6844)
- rclone.exe (PID: 4084)
- rclone.exe (PID: 5116)
- rclone.exe (PID: 1104)
Disables trace logs
- PCVR-Rookie.exe (PID: 6620)
Reads the software policy settings
- PCVR-Rookie.exe (PID: 6620)
Reads the machine GUID from the registry
- PCVR-Rookie.exe (PID: 6620)
Checks proxy server information
- PCVR-Rookie.exe (PID: 6620)
Create files in a temporary directory
- PCVR-Rookie.exe (PID: 6620)
- 7z.exe (PID: 6856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2096:08:05 23:25:58+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 528896 |
| InitializedDataSize: | 413184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8311e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Rookie Sideloader |
| CompanyName: | Rookie.WTF |
| FileDescription: | AndroidSideloader |
| FileVersion: | 2.0.0.0 |
| InternalName: | Rookie-PCVR.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | Rookie-PCVR.exe |
| ProductName: | AndroidSideloader |
| ProductVersion: | 2.0.0.0 |
| AssemblyVersion: | 2.0.0.0 |
Total processes
157
Monitored processes
29
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 460 | "C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe" cat ":PCVR Games/VRP-GameList.txt" --config vrp.download.config | C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe | — | PCVR-Rookie.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.66.0 Modules
| |||||||||||||||
| 1104 | "C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe" cat ":PCVR Games/VRP-GameList.txt" --config vrp.download.config | C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe | — | PCVR-Rookie.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.66.0 Modules
| |||||||||||||||
| 2468 | "C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe" cat ":PCVR Games/VRP-GameList.txt" --config vrp.download.config | C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe | — | PCVR-Rookie.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.66.0 Modules
| |||||||||||||||
| 2804 | "C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe" cat ":PCVR Games/VRP-GameList.txt" --config vrp.download.config | C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe | — | PCVR-Rookie.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.66.0 Modules
| |||||||||||||||
| 3292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3292 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4084 | "C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe" cat ":PCVR Games/VRP-GameList.txt" --config vrp.download.config | C:\Users\admin\AppData\Local\Temp\rclone\rclone.exe | — | PCVR-Rookie.exe | |||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 1 Version: 1.66.0 Modules
| |||||||||||||||
| 4192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4192 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
35 858
Read events
35 589
Write events
269
Delete events
0
Modification events
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\PCVR-Rookie_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\PCVR-Rookie_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\PCVR-Rookie_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\PCVR-Rookie_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (6620) PCVR-Rookie.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\PCVR-Rookie_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
Executable files
2
Suspicious files
1
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6856 | 7z.exe | C:\Users\admin\AppData\Local\Temp\rclone-v1.66.0-windows-amd64\rclone.exe | — | |
MD5:— | SHA256:— | |||
| 6620 | PCVR-Rookie.exe | C:\Users\admin\AppData\Local\Temp\rclone.zip | compressed | |
MD5:10BABE225D85F3DA58EE8CC260B63793 | SHA256:8E8BB13FB0D7BEB316487ECDE8EAD5426784CDCDBF8B4D8DD381C6FE8C7D92A0 | |||
| 6620 | PCVR-Rookie.exe | C:\Users\admin\AppData\Local\Temp\7z.exe | executable | |
MD5:1A7EAA1DAB7867E15D7800AE0B5AF5E3 | SHA256:356BEA8B6E9EB84DFA0DD8674E7C03428C641A47789DF605C5BEA0730DE4AED2 | |||
| 6620 | PCVR-Rookie.exe | C:\Users\admin\AppData\Local\Temp\7z.dll | executable | |
MD5:71EBAC040D32560BB9D76A552A7CB986 | SHA256:1AA51AA9BB50B26BB652D9C442208DB76546286B0DB169C8882DE97D1117029D | |||
| 6856 | 7z.exe | C:\Users\admin\AppData\Local\Temp\rclone-v1.66.0-windows-amd64\README.html | html | |
MD5:5DCCEDACC553BE80C9AFA46E51E9D246 | SHA256:9FA07BEDD060AC1E367C774DAC98F551A05BFF0A0B3348C8AD06A71CAE0CEDFA | |||
| 6856 | 7z.exe | C:\Users\admin\AppData\Local\Temp\rclone-v1.66.0-windows-amd64\git-log.txt | text | |
MD5:D1D8FE6F0BDE0342D206768762FF354A | SHA256:97F0028701D4043414BB18B460FD3F2DD2BAC9626E14A529A14E64DB523272CA | |||
| 6620 | PCVR-Rookie.exe | C:\Users\admin\AppData\Local\Rookie.WTF\PCVR-Rookie.exe_Url_xvschwsgakn2nagjsqlofr5vkuygxcxa\2.0.0.0\tfznqpjz.newcfg | xml | |
MD5:410AFDA4BDE459246A3CA55E2EE36BC3 | SHA256:4C28889E076FC03D80185C5CC0C85F26B4078E84C279CC2943C0B3CCAD0F9B4E | |||
| 6856 | 7z.exe | C:\Users\admin\AppData\Local\Temp\rclone-v1.66.0-windows-amd64\README.txt | text | |
MD5:6A54F7361DDB095EBA537B88109342BB | SHA256:B55306E1C65A924A193D5870D8C9D35BC9777E1CA58F0BC73A82E219410034A1 | |||
| 6620 | PCVR-Rookie.exe | C:\Users\admin\AppData\Local\Rookie.WTF\PCVR-Rookie.exe_Url_xvschwsgakn2nagjsqlofr5vkuygxcxa\2.0.0.0\user.config | xml | |
MD5:410AFDA4BDE459246A3CA55E2EE36BC3 | SHA256:4C28889E076FC03D80185C5CC0C85F26B4078E84C279CC2943C0B3CCAD0F9B4E | |||
| 6620 | PCVR-Rookie.exe | C:\Users\admin\AppData\Local\Rookie.WTF\PCVR-Rookie.exe_Url_xvschwsgakn2nagjsqlofr5vkuygxcxa\2.0.0.0\aucvfkc3.newcfg | xml | |
MD5:80FB0F0A5948978437AC75F5C13B722E | SHA256:C58BFDDB714A283BAE69704D4BF76B7BA673739E08245862F7157AFE6F2A7BE7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
51
DNS requests
21
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6360 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6332 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4016 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 2.23.209.133:443 | www.bing.com | Akamai International B.V. | GB | unknown |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4920 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5336 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
th.bing.com |
| whitelisted |
downloads.rclone.org |
| unknown |
fd.api.iris.microsoft.com |
| whitelisted |
github.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
6620 | PCVR-Rookie.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |