| File name: | paco.exe |
| Full analysis: | https://app.any.run/tasks/de762b61-2bb9-4d34-9431-533fc0a0de41 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2025, 05:36:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | 33EEEB25F834E0B180F960ECB9518EA0 |
| SHA1: | 61F73E692E9549AD8BC9B965E25D2DA683D56DC1 |
| SHA256: | 9F6A696876FEE8B811DB8889BF4933262F4472AD41DAEA215D2E39BD537CF32F |
| SSDEEP: | 98304:ODQPps2E6S1RNJ31LawGx8lh6fPEXPYKzUyvtHLjAJ7MY2E8OilEHUXBAcbp5y4m:HhBAyBgh8 |
MALICIOUS
Known privilege escalation attack
- dllhost.exe (PID: 6148)
Changes the autorun value in the registry
- ELPACO-team.exe (PID: 6732)
Executing a file with an untrusted certificate
- DC.exe (PID: 5720)
- DC.exe (PID: 6744)
Changes image file execution options
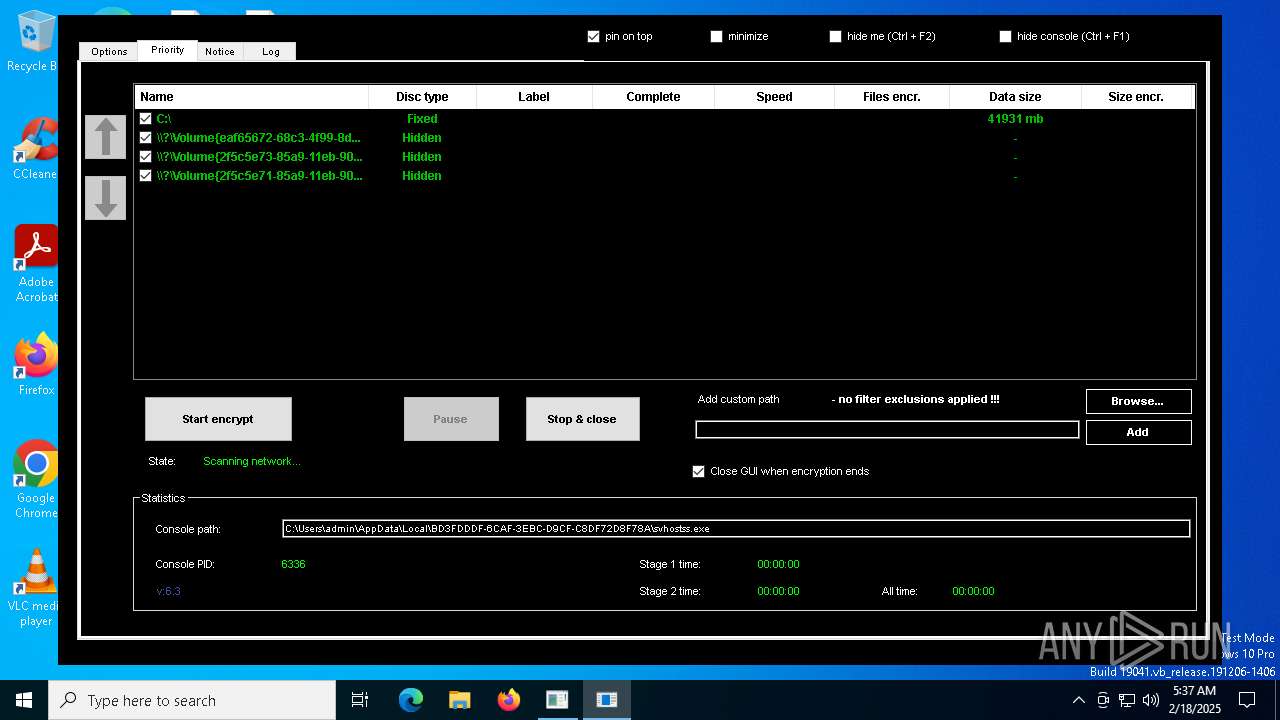
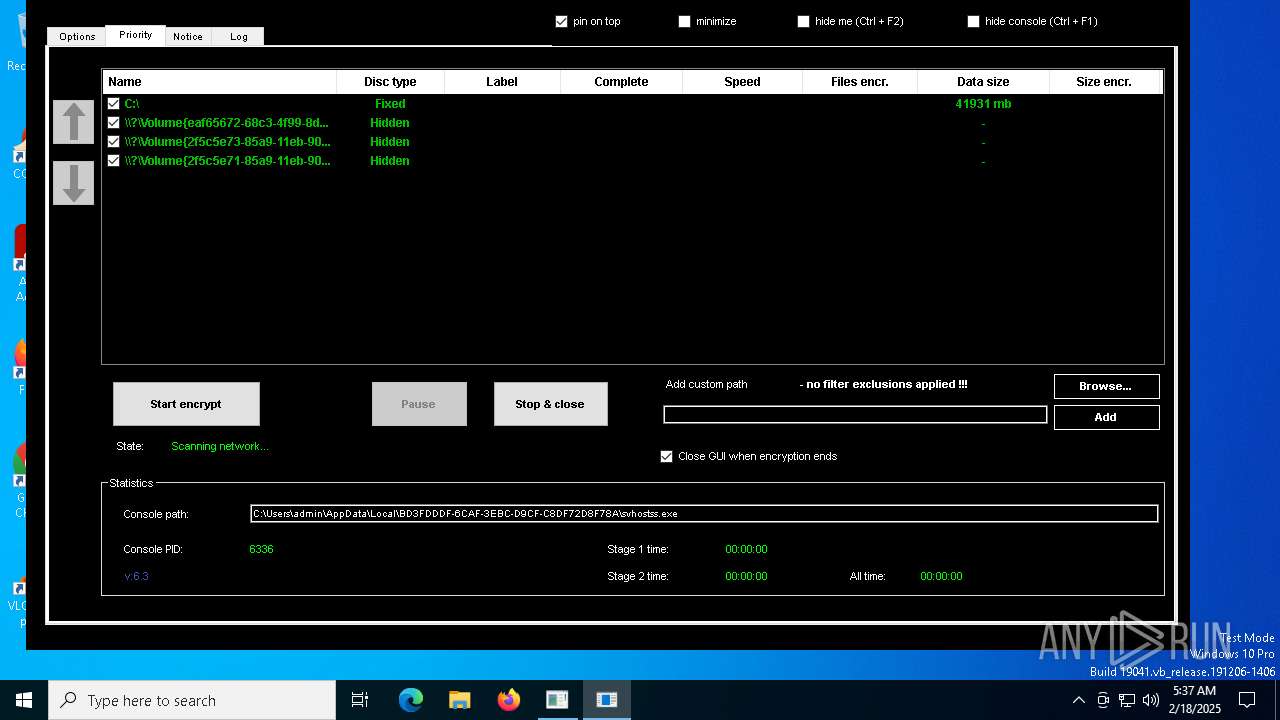
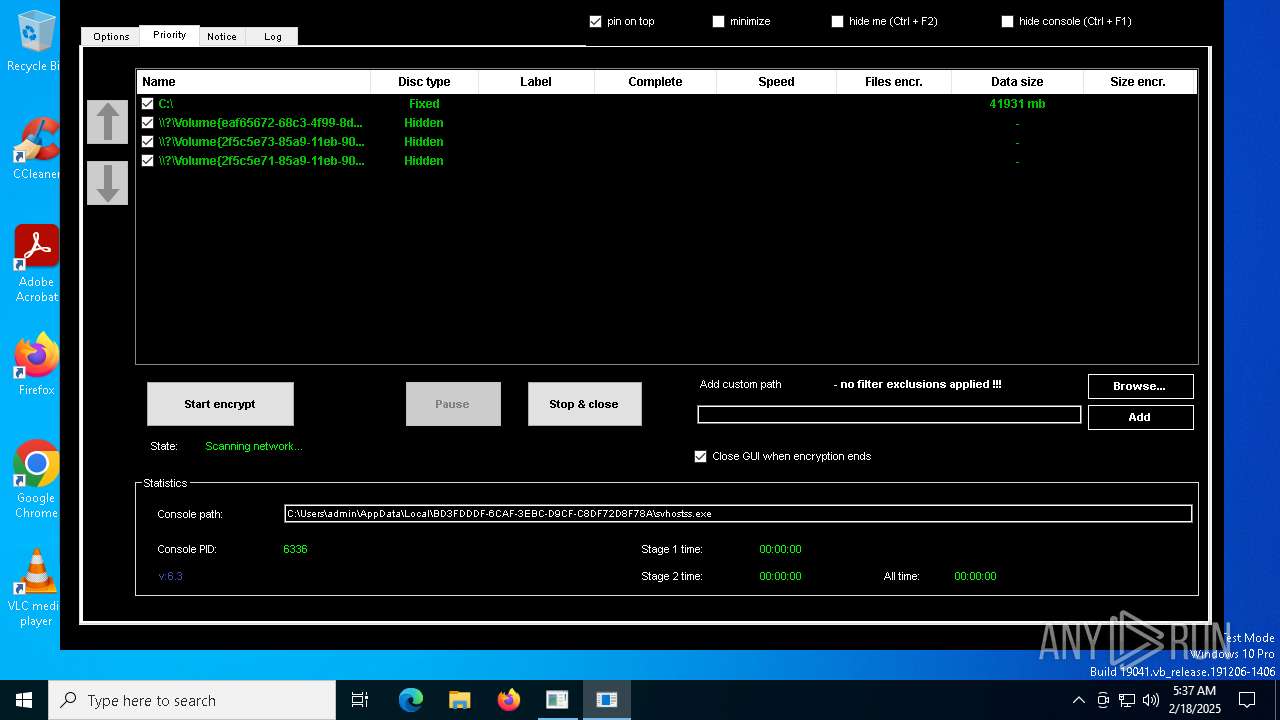
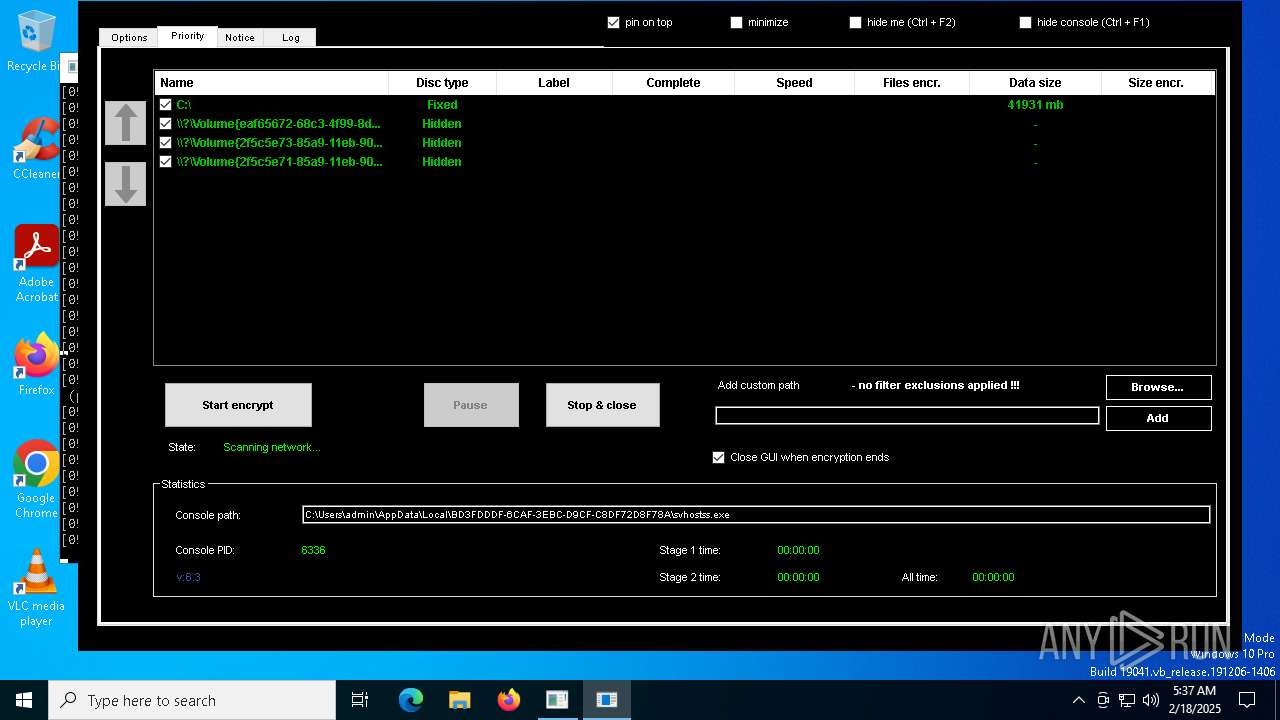
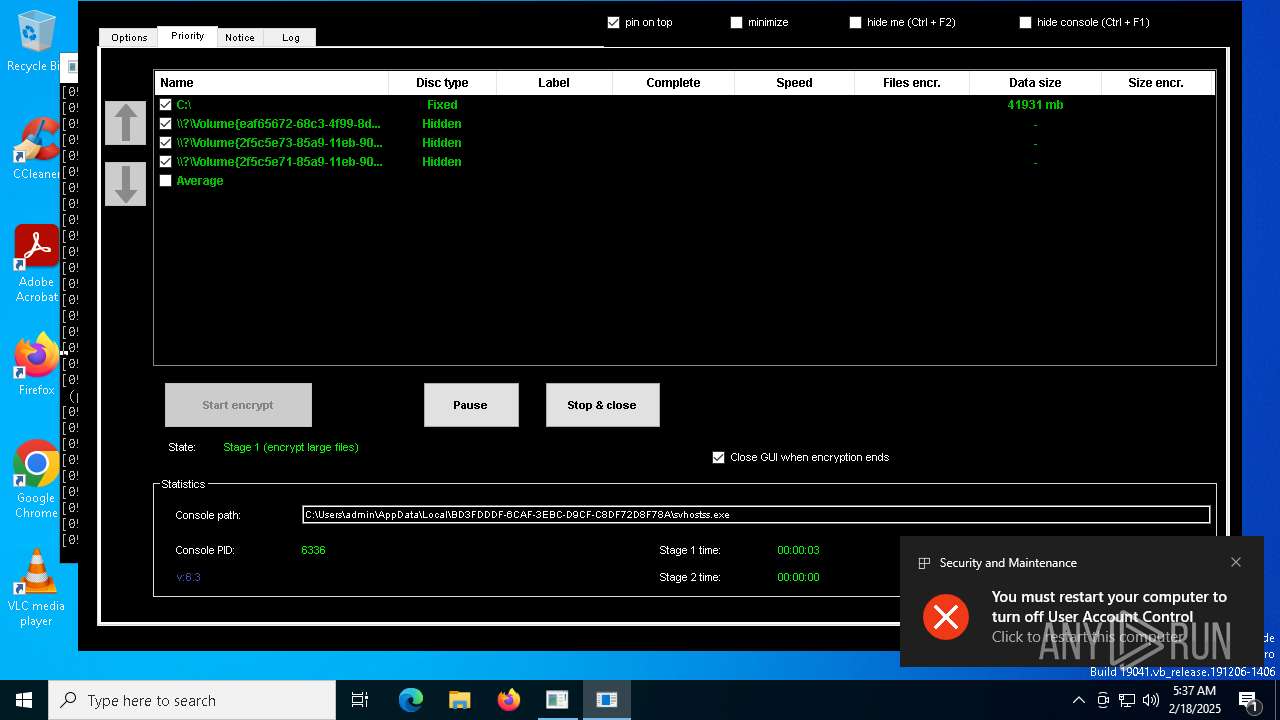
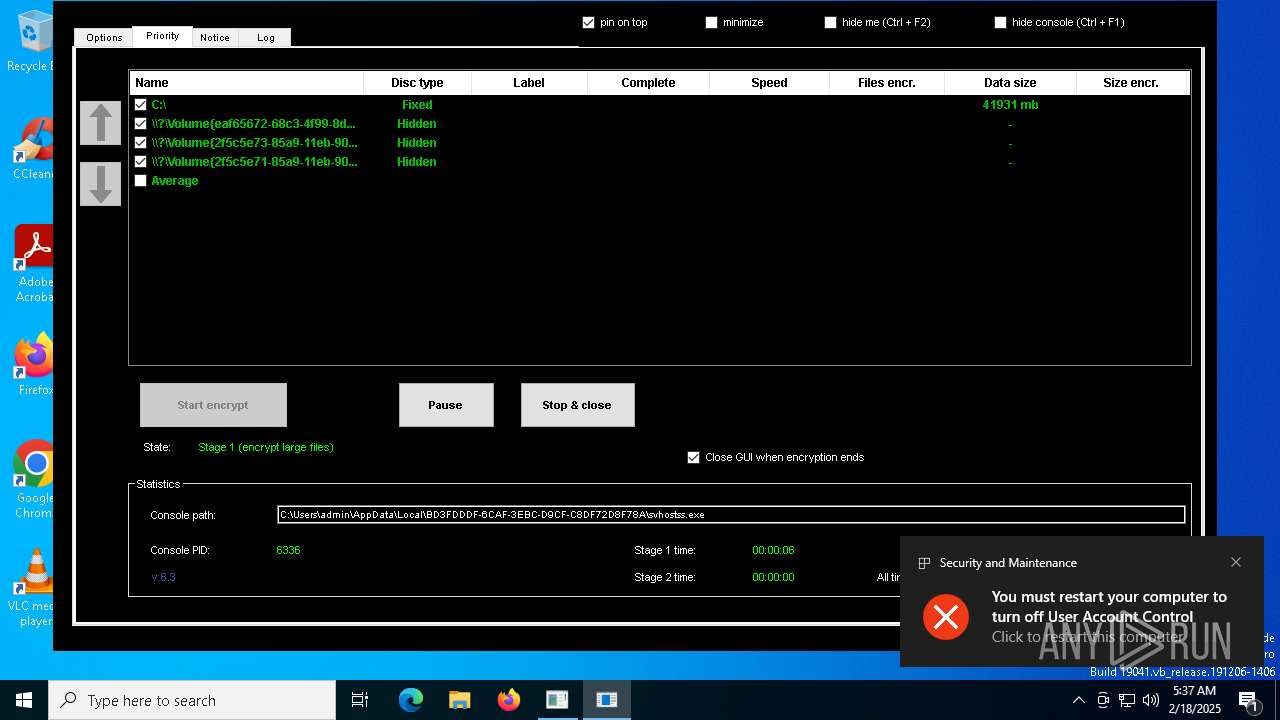
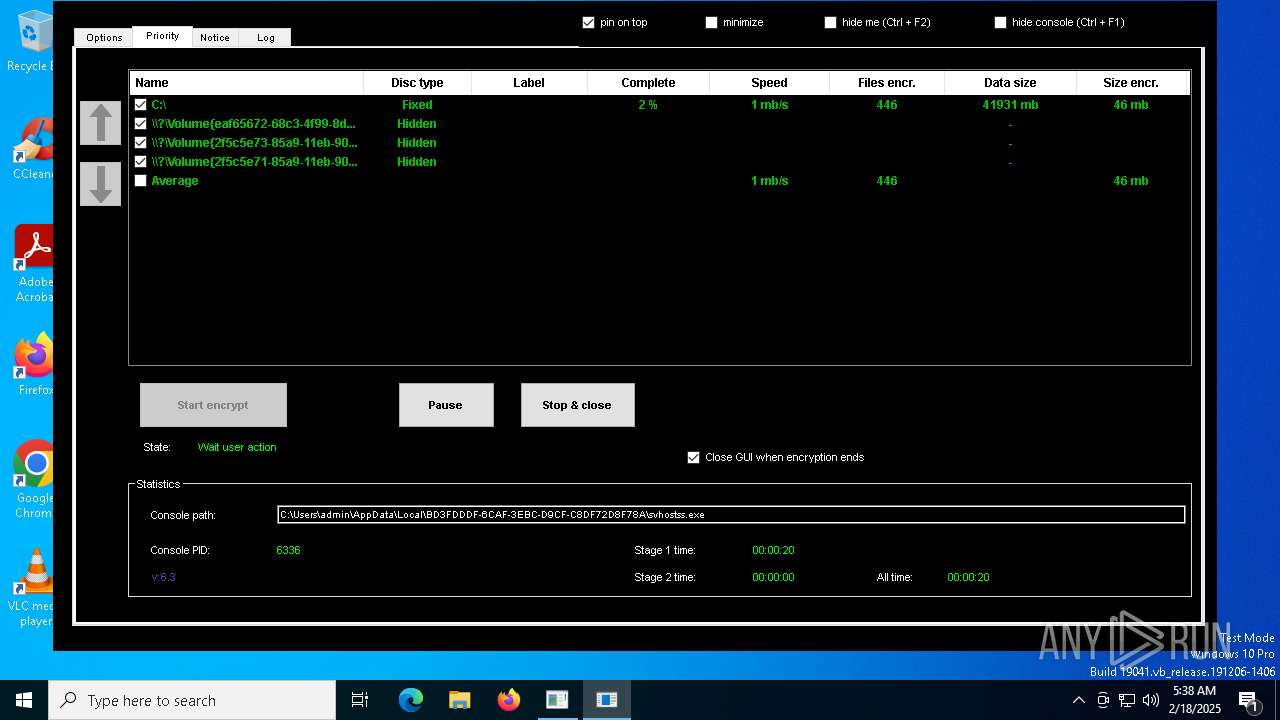
- svhostss.exe (PID: 6336)
Disables Windows Defender
- DC.exe (PID: 5720)
- DC.exe (PID: 6384)
- DC.exe (PID: 6744)
UAC/LUA settings modification
- svhostss.exe (PID: 6336)
Bypass execution policy to execute commands
- powershell.exe (PID: 1804)
- powershell.exe (PID: 3724)
- powershell.exe (PID: 4984)
Disables the Shutdown in the Start menu
- svhostss.exe (PID: 6336)
Changes powershell execution policy (Bypass)
- svhostss.exe (PID: 6336)
Creates or modifies Windows services
- DC.exe (PID: 6744)
SUSPICIOUS
Executable content was dropped or overwritten
- 7za.exe (PID: 6620)
- ELPACO-team.exe (PID: 6732)
- paco.exe (PID: 6488)
- svhostss.exe (PID: 6336)
Drops 7-zip archiver for unpacking
- paco.exe (PID: 6488)
- ELPACO-team.exe (PID: 6732)
Reads security settings of Internet Explorer
- paco.exe (PID: 6488)
- ShellExperienceHost.exe (PID: 4160)
Starts CMD.EXE for commands execution
- paco.exe (PID: 6488)
- svhostss.exe (PID: 6336)
Application launched itself
- svhostss.exe (PID: 6336)
- DC.exe (PID: 5720)
- DC.exe (PID: 6384)
Executing commands from ".cmd" file
- paco.exe (PID: 6488)
Creates or modifies Windows services
- svhostss.exe (PID: 6336)
The executable file from the user directory is run by the CMD process
- DC.exe (PID: 5720)
Uses powercfg.exe to modify the power settings
- svhostss.exe (PID: 6336)
Starts POWERSHELL.EXE for commands execution
- svhostss.exe (PID: 6336)
There is functionality for taking screenshot (YARA)
- paco.exe (PID: 6488)
INFO
Checks supported languages
- paco.exe (PID: 6488)
- 7za.exe (PID: 6552)
- 7za.exe (PID: 6620)
- Everything.exe (PID: 2380)
- svhostss.exe (PID: 6336)
- gui40.exe (PID: 6412)
- svhostss.exe (PID: 4384)
- svhostss.exe (PID: 4528)
- svhostss.exe (PID: 3820)
- ELPACO-team.exe (PID: 6732)
- DC.exe (PID: 5720)
- DC.exe (PID: 6384)
- DC.exe (PID: 6744)
- ShellExperienceHost.exe (PID: 4160)
Reads the computer name
- paco.exe (PID: 6488)
- 7za.exe (PID: 6620)
- 7za.exe (PID: 6552)
- ELPACO-team.exe (PID: 6732)
- gui40.exe (PID: 6412)
- svhostss.exe (PID: 6336)
- Everything.exe (PID: 2380)
- svhostss.exe (PID: 4528)
- svhostss.exe (PID: 3820)
- DC.exe (PID: 5720)
- svhostss.exe (PID: 4384)
- ShellExperienceHost.exe (PID: 4160)
- DC.exe (PID: 6744)
Create files in a temporary directory
- paco.exe (PID: 6488)
- 7za.exe (PID: 6620)
- DC.exe (PID: 5720)
The sample compiled with english language support
- paco.exe (PID: 6488)
- 7za.exe (PID: 6620)
- ELPACO-team.exe (PID: 6732)
- svhostss.exe (PID: 6336)
Process checks computer location settings
- paco.exe (PID: 6488)
Creates files or folders in the user directory
- ELPACO-team.exe (PID: 6732)
- svhostss.exe (PID: 6336)
- gui40.exe (PID: 6412)
Reads the machine GUID from the registry
- gui40.exe (PID: 6412)
- ELPACO-team.exe (PID: 6732)
Reads mouse settings
- DC.exe (PID: 5720)
- DC.exe (PID: 6384)
- DC.exe (PID: 6744)
Reads security settings of Internet Explorer
- dllhost.exe (PID: 6148)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1804)
- powershell.exe (PID: 4984)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3724)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2012:12:31 00:38:51+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 8 |
| CodeSize: | 101888 |
| InitializedDataSize: | 87040 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1942f |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
213
Monitored processes
70
Malicious processes
6
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1476 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | svhostss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | powershell.exe -ExecutionPolicy Bypass "Get-VM | Select-Object vmid | Get-VHD | %{Get-DiskImage -ImagePath $_.Path; Get-DiskImage -ImagePath $_.ParentPath} | Dismount-DiskImage" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | svhostss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2088 | C:\WINDOWS\System32\Systray.exe "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\System32\systray.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Systray .exe stub Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
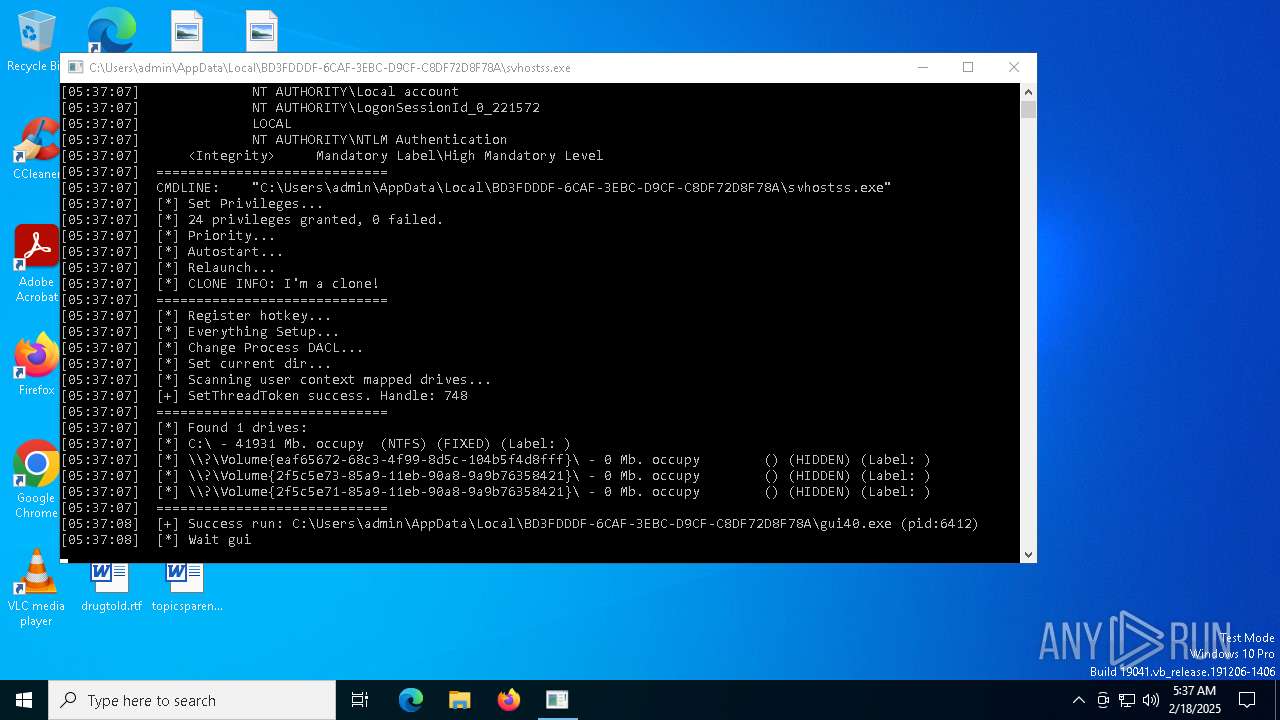
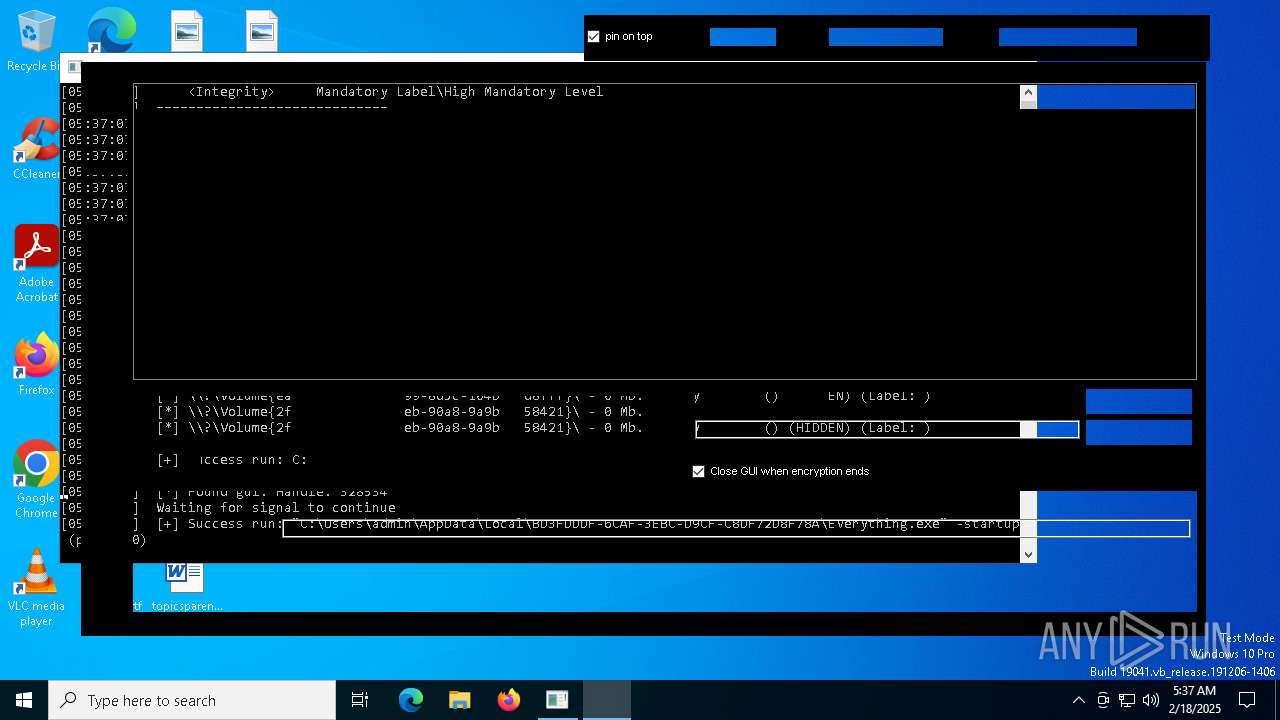
| 2380 | "C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\Everything.exe" -startup | C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\Everything.exe | — | svhostss.exe | |||||||||||
User: admin Company: voidtools Integrity Level: HIGH Description: Everything Version: 1.4.1.1015 Modules
| |||||||||||||||
| 2792 | C:\WINDOWS\System32\Systray.exe "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\System32\systray.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Systray .exe stub Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2796 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powercfg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2940 | powercfg.exe -S e9a42b02-d5df-448d-aa00-03f14749eb61 | C:\Windows\System32\powercfg.exe | — | svhostss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Power Settings Command-Line Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
21 391
Read events
21 349
Write events
40
Delete events
2
Modification events
| (PID) Process: | (6732) ELPACO-team.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | svhostss |
Value: "C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\svhostss.exe" | |||
| (PID) Process: | (6148) dllhost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\SDRSVC |
| Operation: | write | Name: | Start |
Value: 4 | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\wbengine |
| Operation: | write | Name: | Start |
Value: 4 | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchIndexer.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\System32\Systray.exe | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\searchprotocolhost.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\System32\Systray.exe | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SearchApp.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\System32\Systray.exe | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CompatTelRunner.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\System32\Systray.exe | |||
| (PID) Process: | (6336) svhostss.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wsqmcons.exe |
| Operation: | write | Name: | Debugger |
Value: C:\WINDOWS\System32\Systray.exe | |||
| (PID) Process: | (5720) DC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
Executable files
26
Suspicious files
981
Text files
288
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6488 | paco.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\7za.exe | executable | |
MD5:B93EB0A48C91A53BDA6A1A074A4B431E | SHA256:AB15A9B27EE2D69A8BC8C8D1F5F40F28CD568F5CBB28D36ED938110203F8D142 | |||
| 6620 | 7za.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\ELPACO-team.exe | executable | |
MD5:B951E50264F9C5244592DFB0A859EC41 | SHA256:E160D7D21C917344F010E58DCFC1E19BEC6297C294647A06CE60EFC7420D3B13 | |||
| 6620 | 7za.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\gui40.exe | executable | |
MD5:57850A4490A6AFD1EF682EB93EA45E65 | SHA256:31FEFF32D23728B39ED813C1E7DC5FE6A87DCD4D10AA995446A8C5EB5DA58615 | |||
| 6732 | ELPACO-team.exe | C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\ENC_default_default_2023-12-27_09-27-40=Telegram@datadecrypt.exe | executable | |
MD5:0BF7C0D8E3E02A6B879EFAB5DEAB013C | SHA256:B600E06F14E29B03F0B1456723A430B5024816518D704A831DDE2DC9597CE9C9 | |||
| 6732 | ELPACO-team.exe | C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\DC.exe | executable | |
MD5:AC34BA84A5054CD701EFAD5DD14645C9 | SHA256:C576F7F55C4C0304B290B15E70A638B037DF15C69577CD6263329C73416E490E | |||
| 6488 | paco.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Everything.exe | executable | |
MD5:C44487CE1827CE26AC4699432D15B42A | SHA256:4C83E46A29106AFBAF5279029D102B489D958781764289B61AB5B618A4307405 | |||
| 6732 | ELPACO-team.exe | C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\Everything.exe | executable | |
MD5:C44487CE1827CE26AC4699432D15B42A | SHA256:4C83E46A29106AFBAF5279029D102B489D958781764289B61AB5B618A4307405 | |||
| 6732 | ELPACO-team.exe | C:\Users\admin\AppData\Local\BD3FDDDF-6CAF-3EBC-D9CF-C8DF72D8F78A\7za.exe | executable | |
MD5:B93EB0A48C91A53BDA6A1A074A4B431E | SHA256:AB15A9B27EE2D69A8BC8C8D1F5F40F28CD568F5CBB28D36ED938110203F8D142 | |||
| 6620 | 7za.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Everything.ini | text | |
MD5:742C2400F2DE964D0CCE4A8DABADD708 | SHA256:2FEFB69E4B2310BE5E09D329E8CF1BEBD1F9E18884C8C2A38AF8D7EA46BD5E01 | |||
| 6620 | 7za.exe | C:\Users\admin\AppData\Local\Temp\7ZipSfx.000\Everything2.ini | text | |
MD5:51014C0C06ACDD80F9AE4469E7D30A9E | SHA256:89AD2164717BD5F5F93FBB4CEBF0EFEB473097408FDDFC7FC7B924D790514DC5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
41
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 104.119.109.218:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6828 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1876 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5564 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
488 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 104.119.109.218:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 23.15.178.208:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.160.66:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |