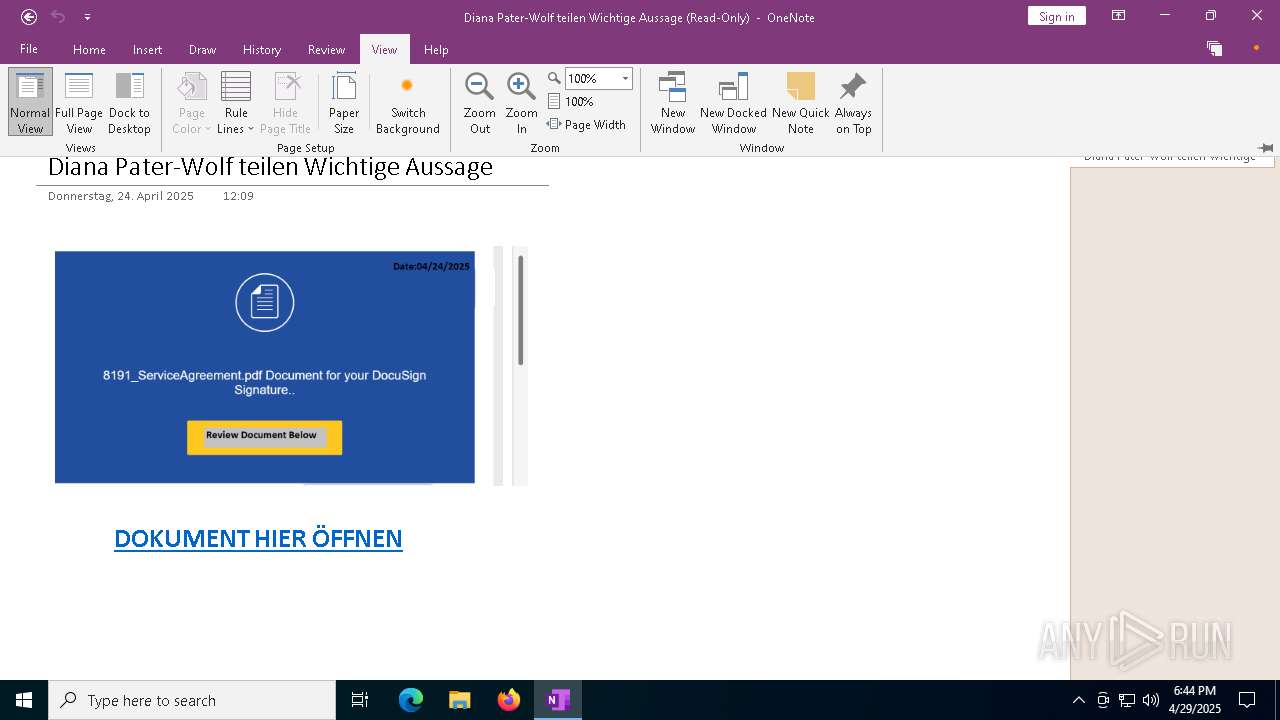
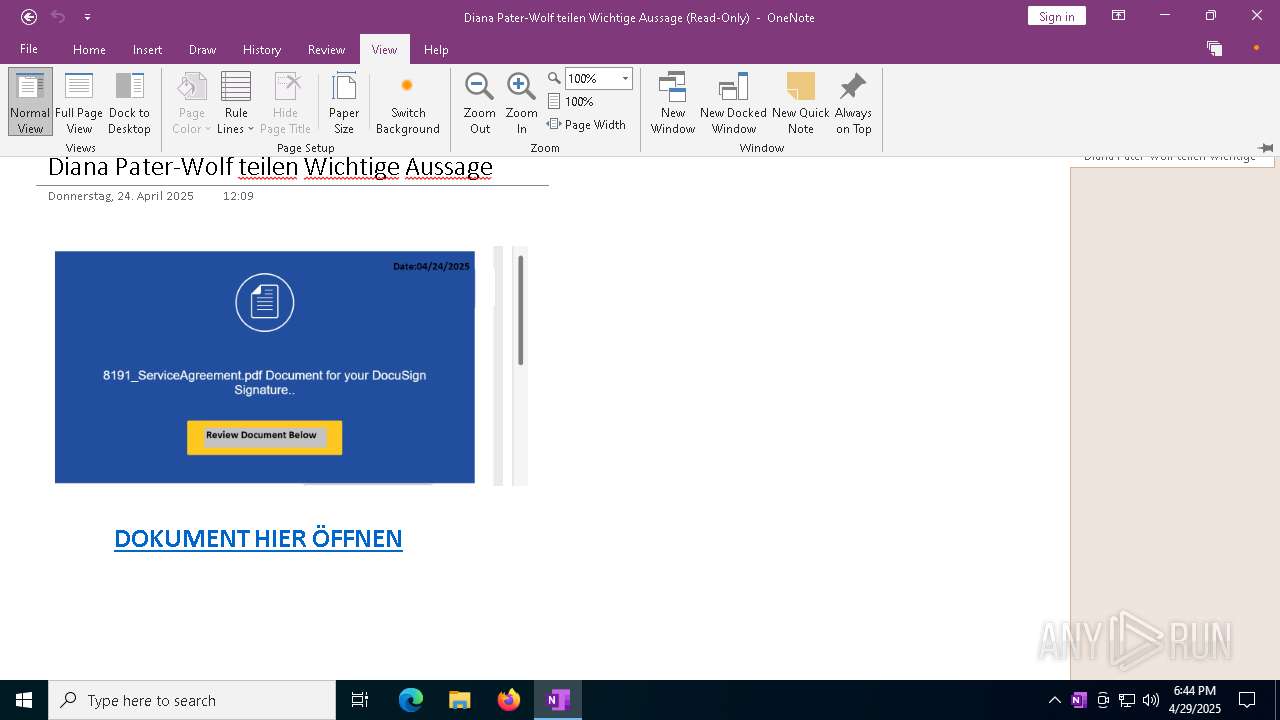
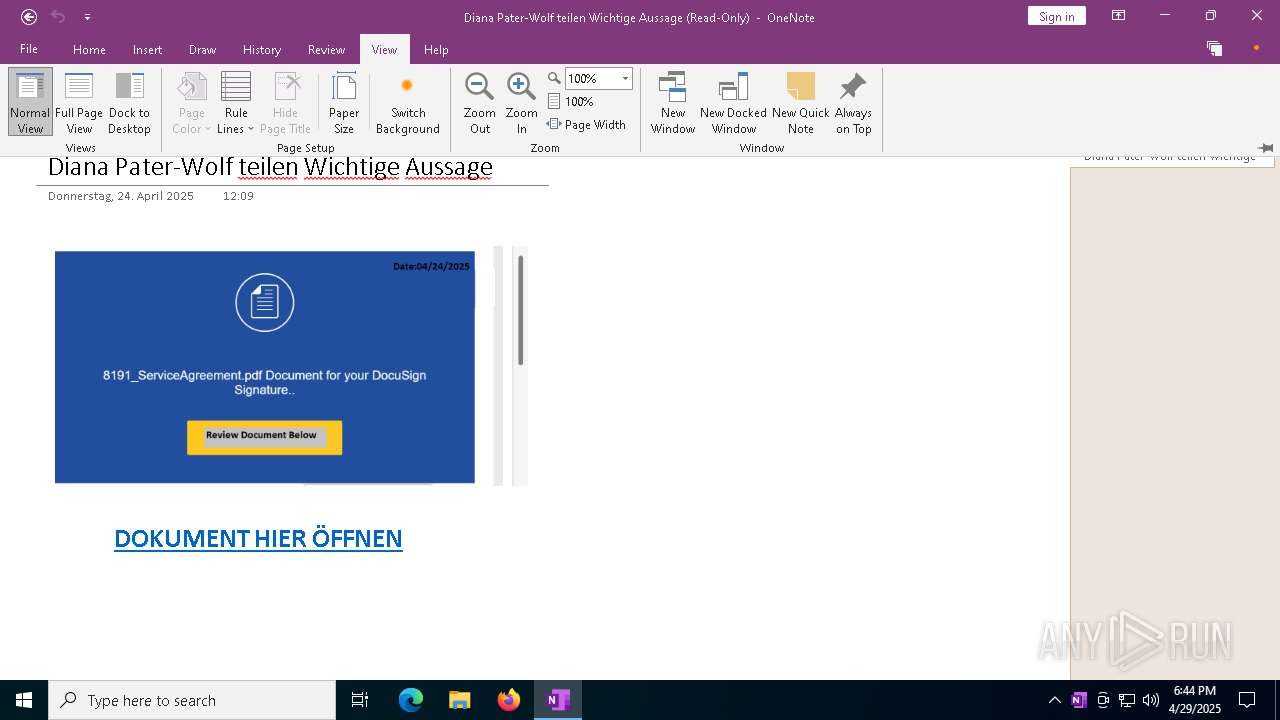
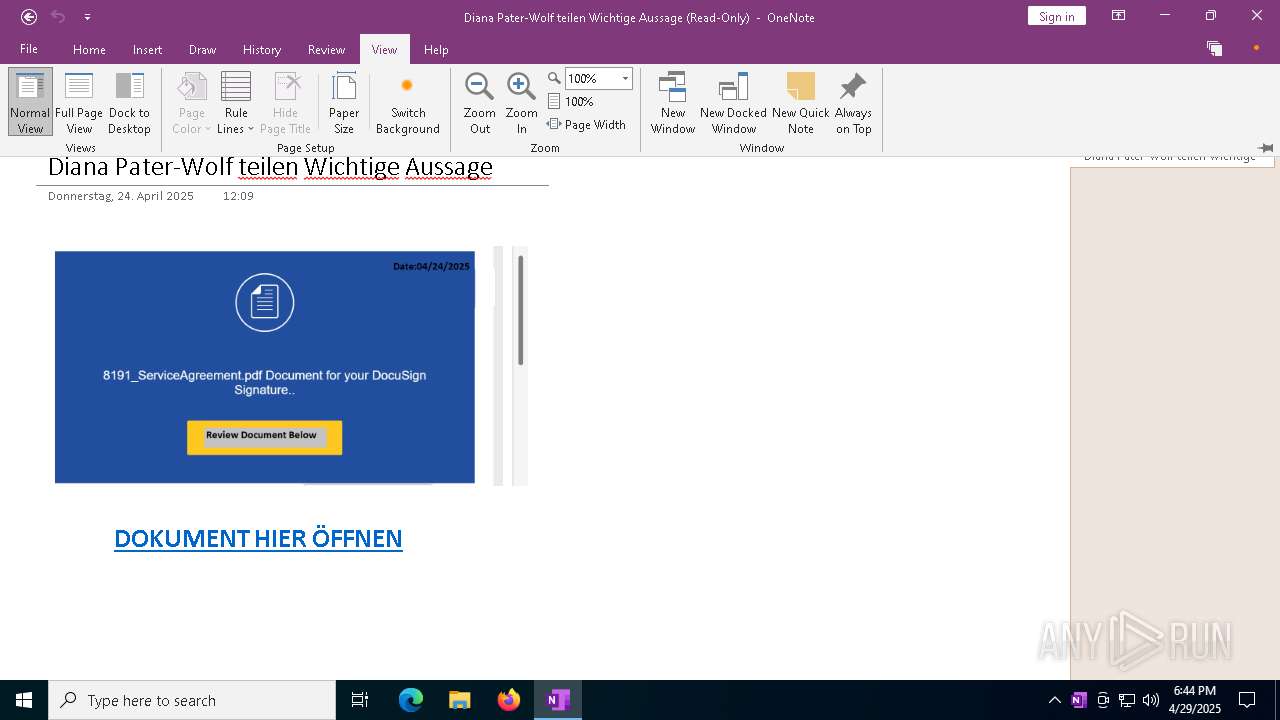
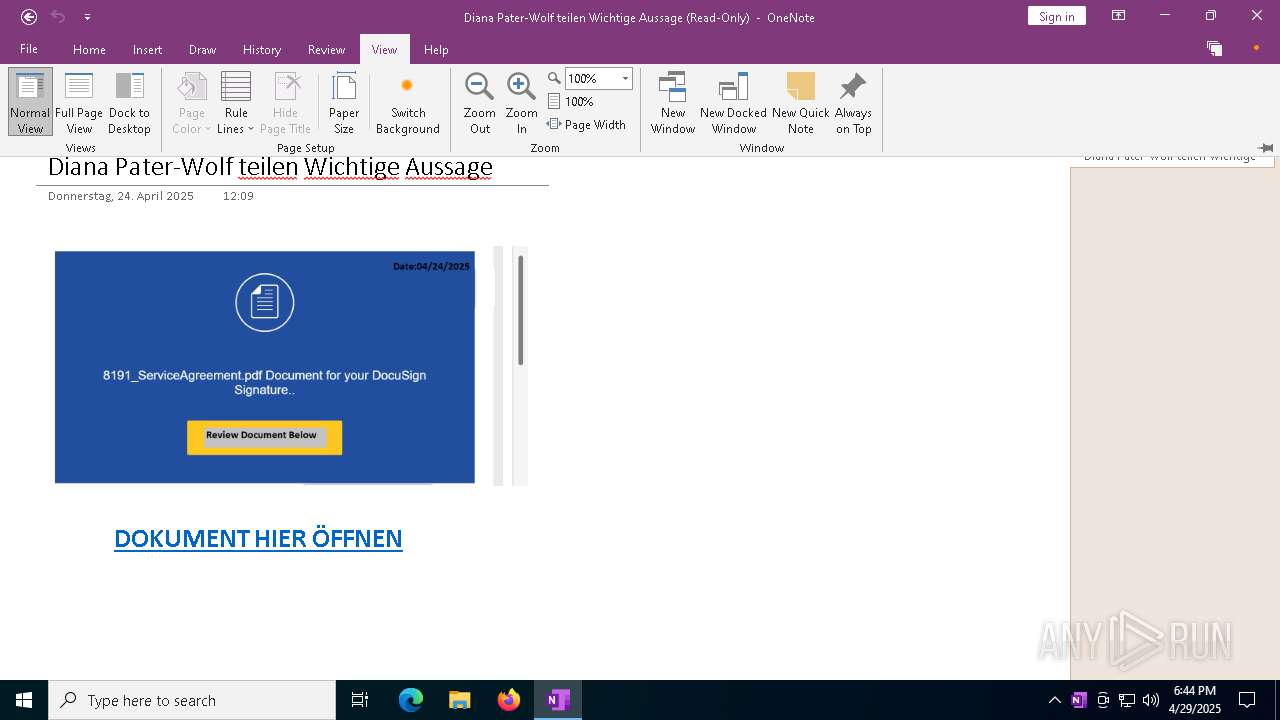
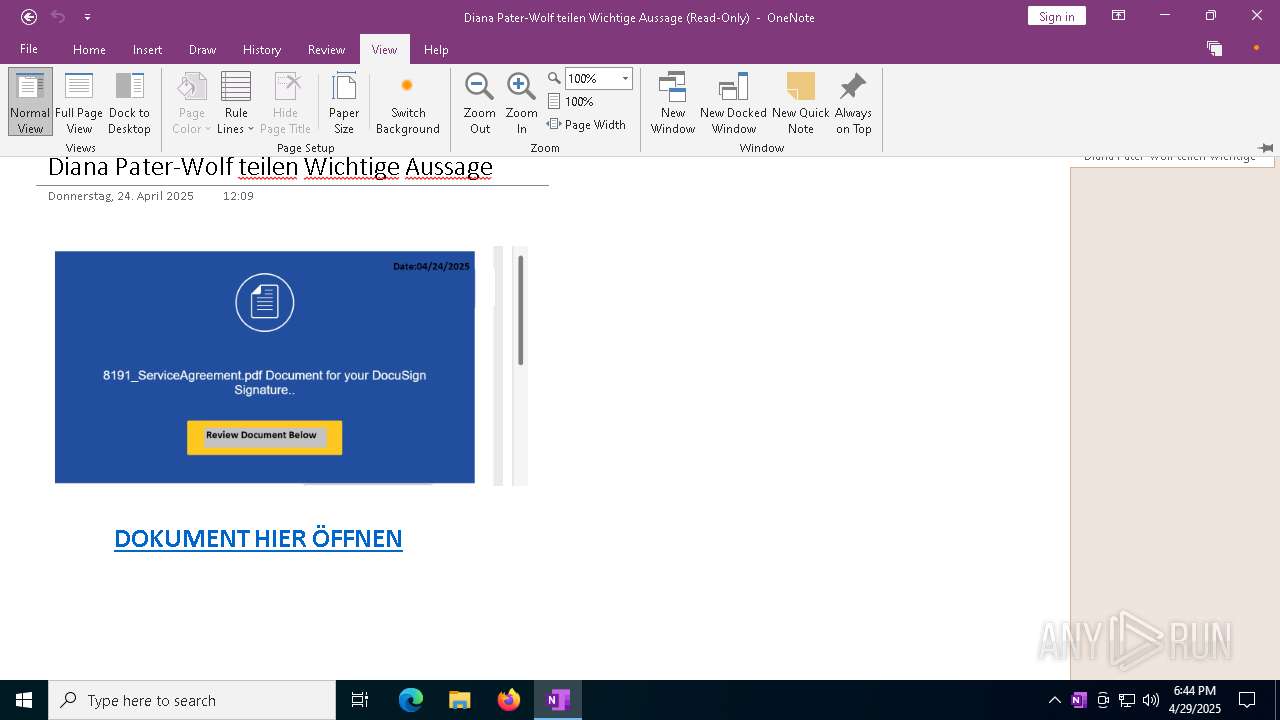
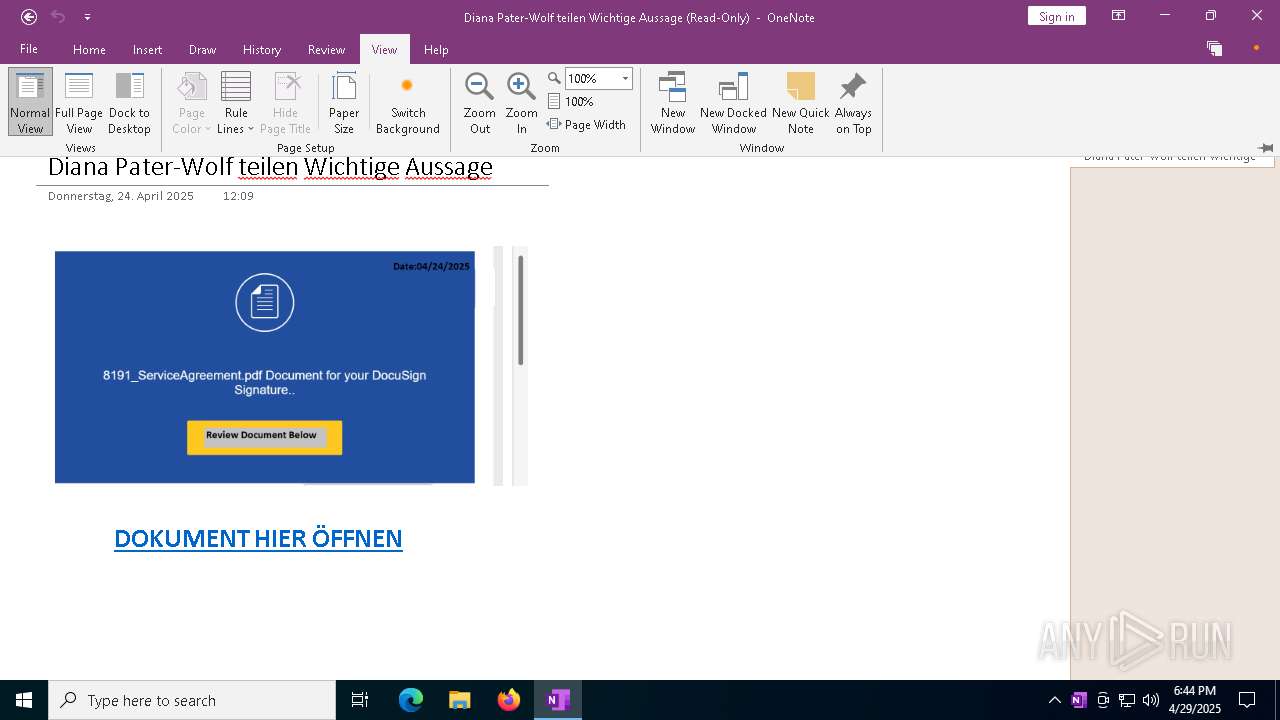
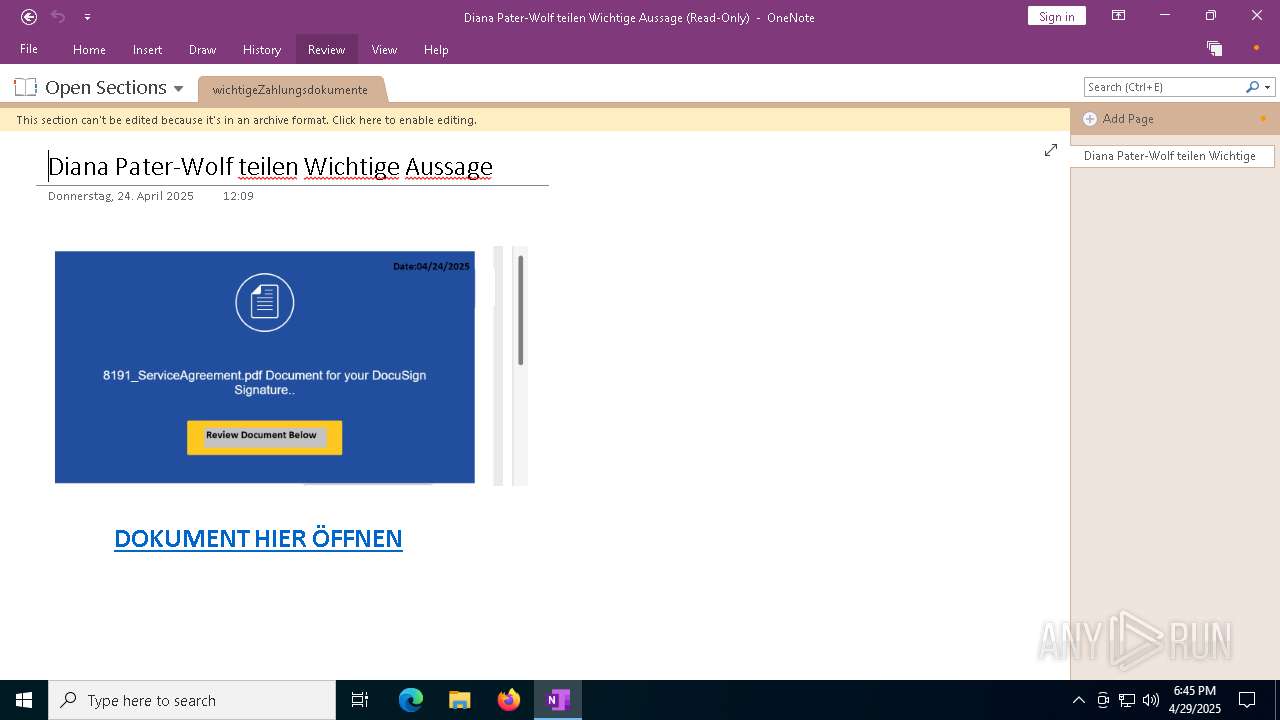
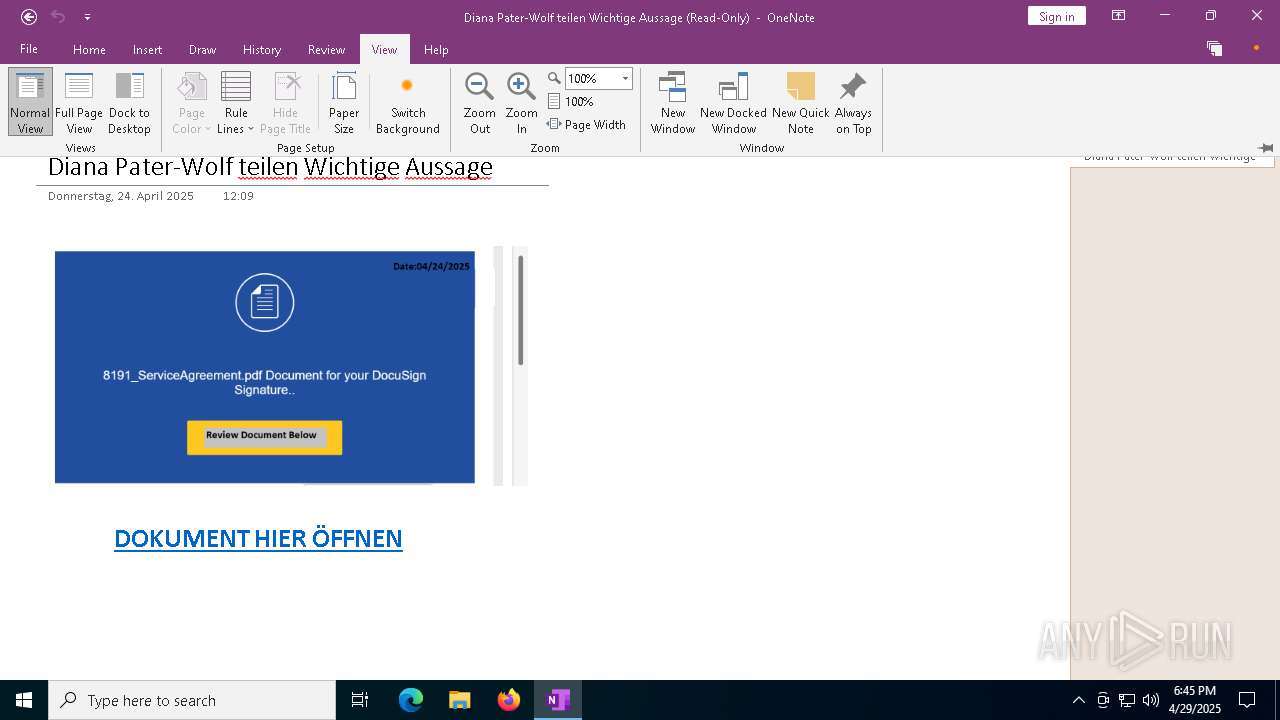
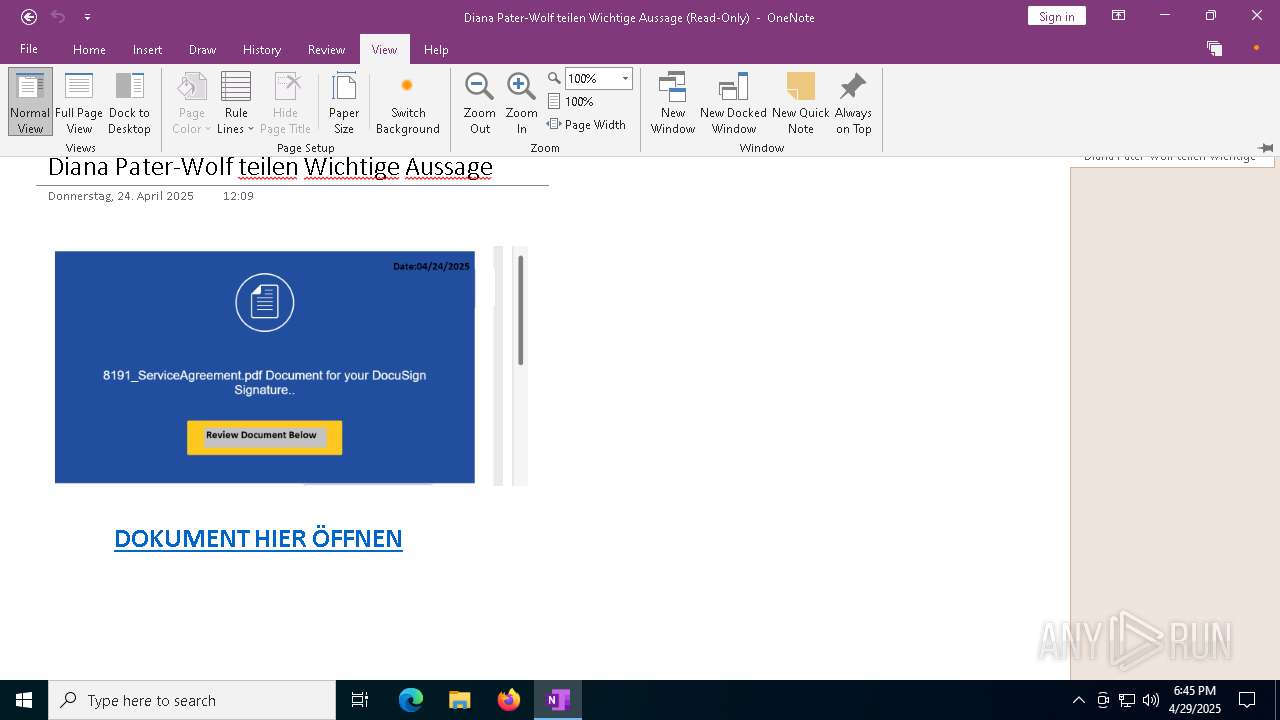
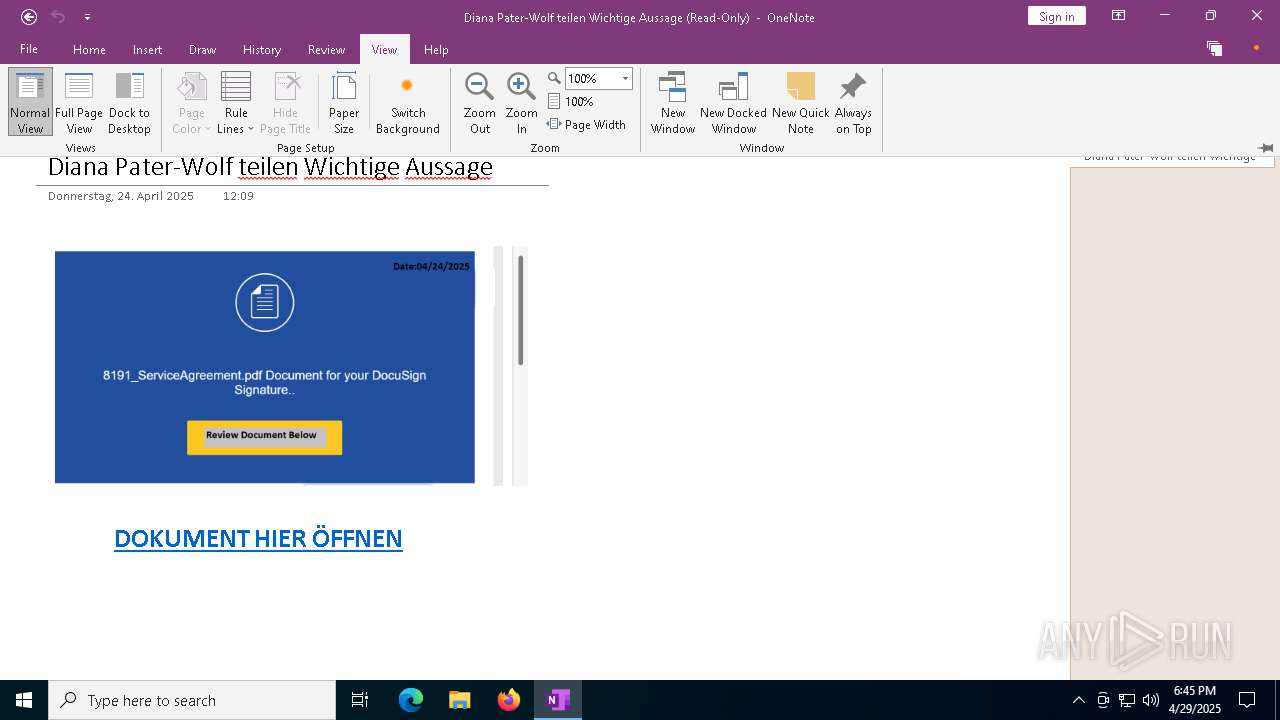
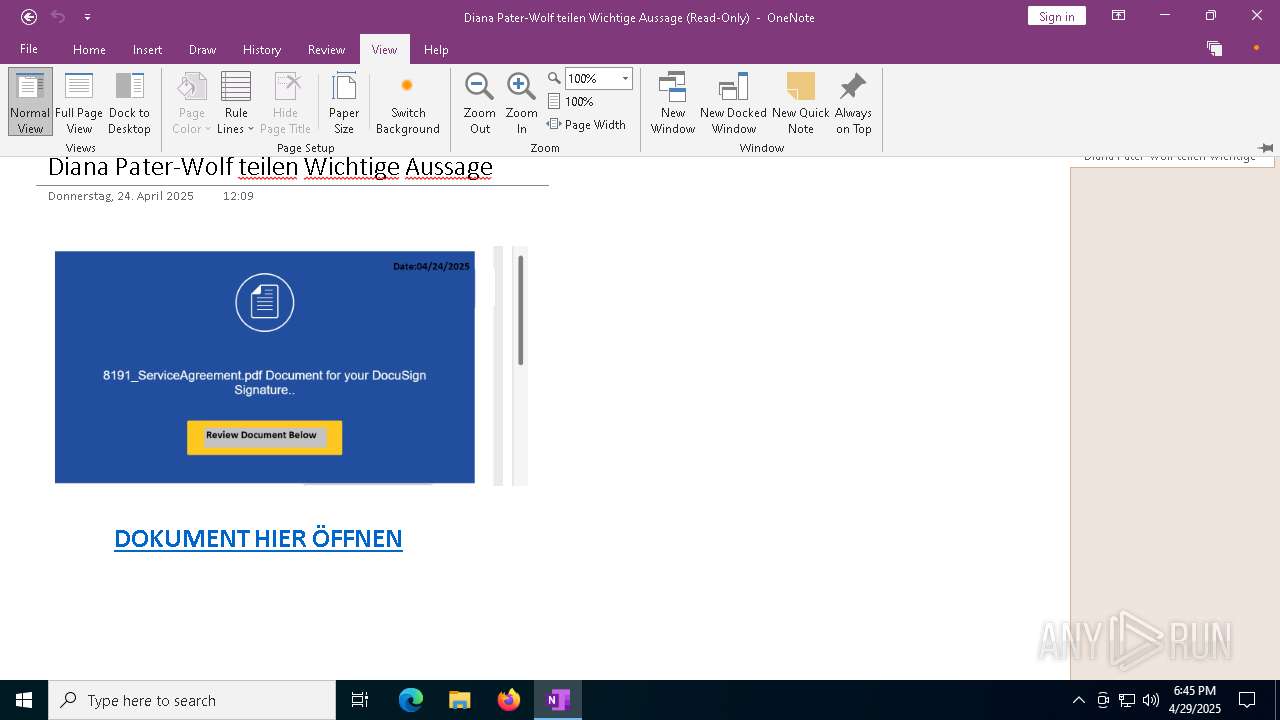
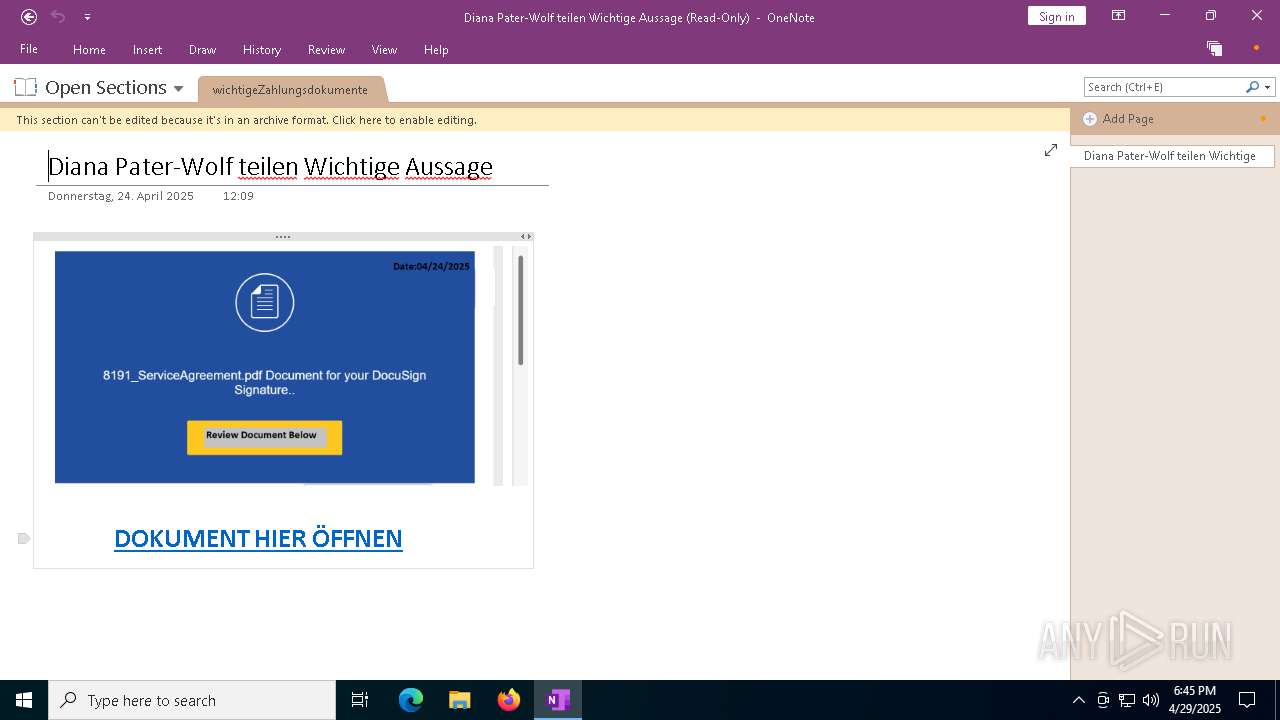
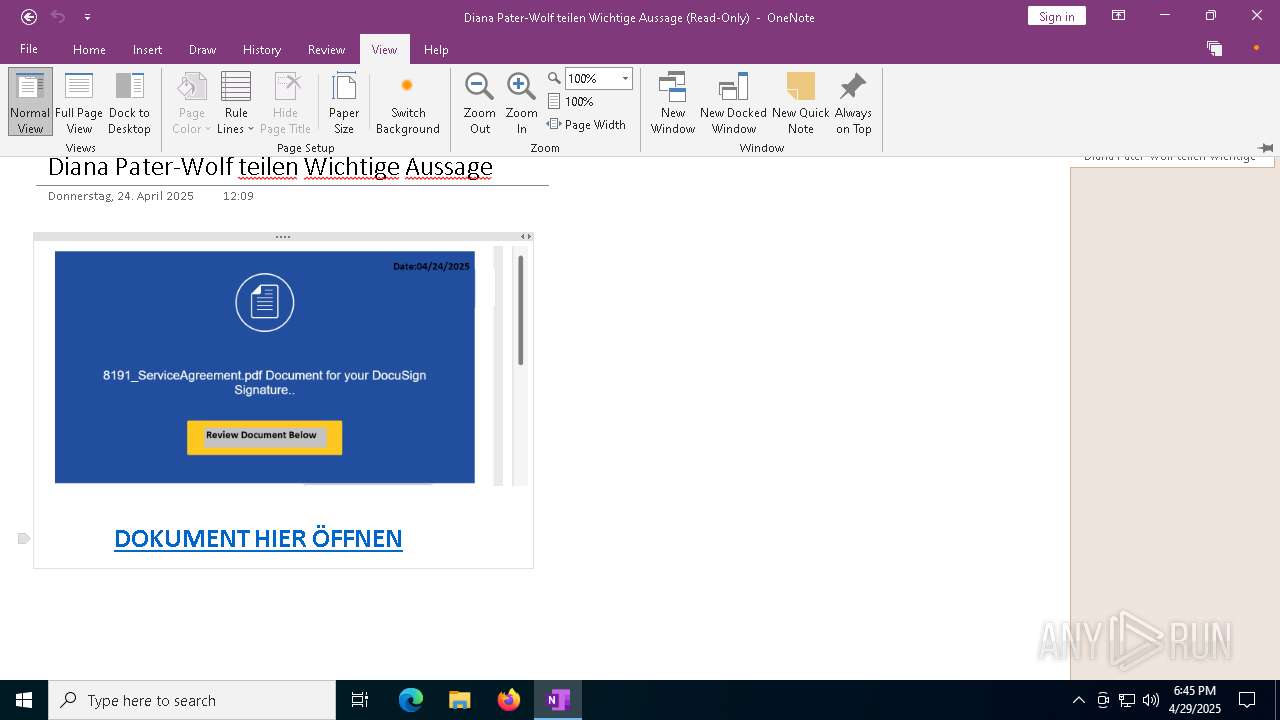
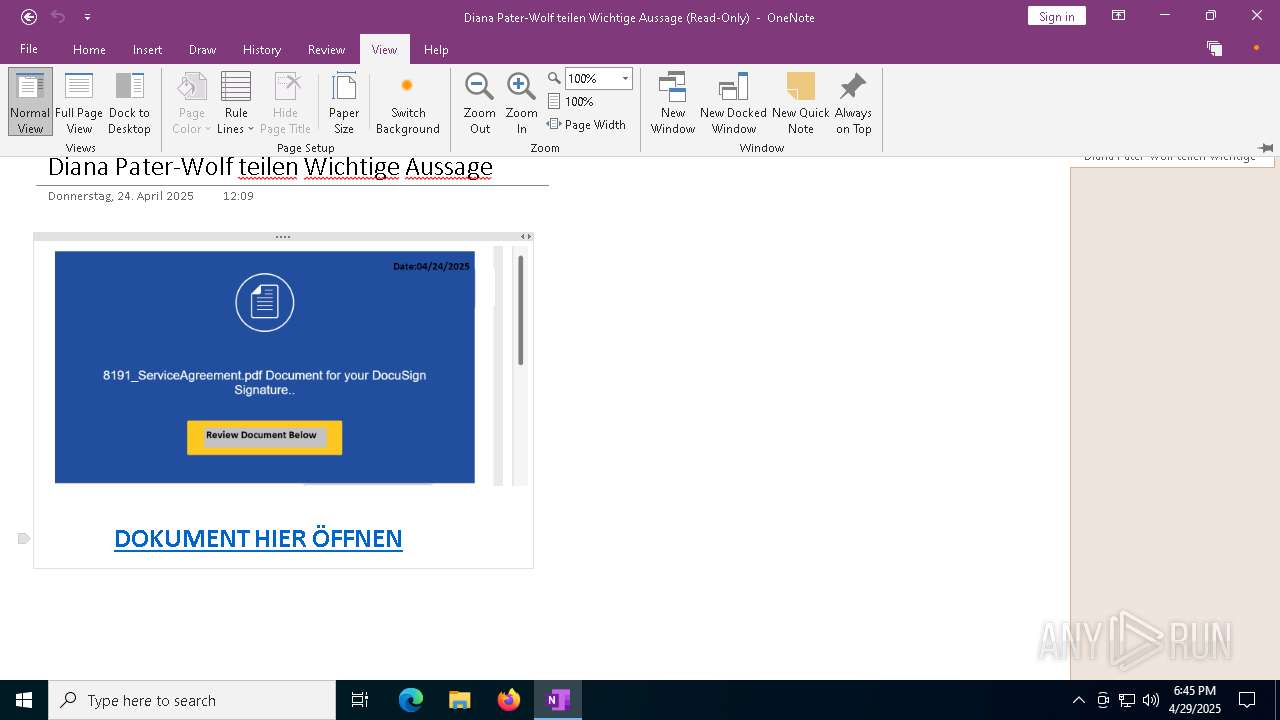
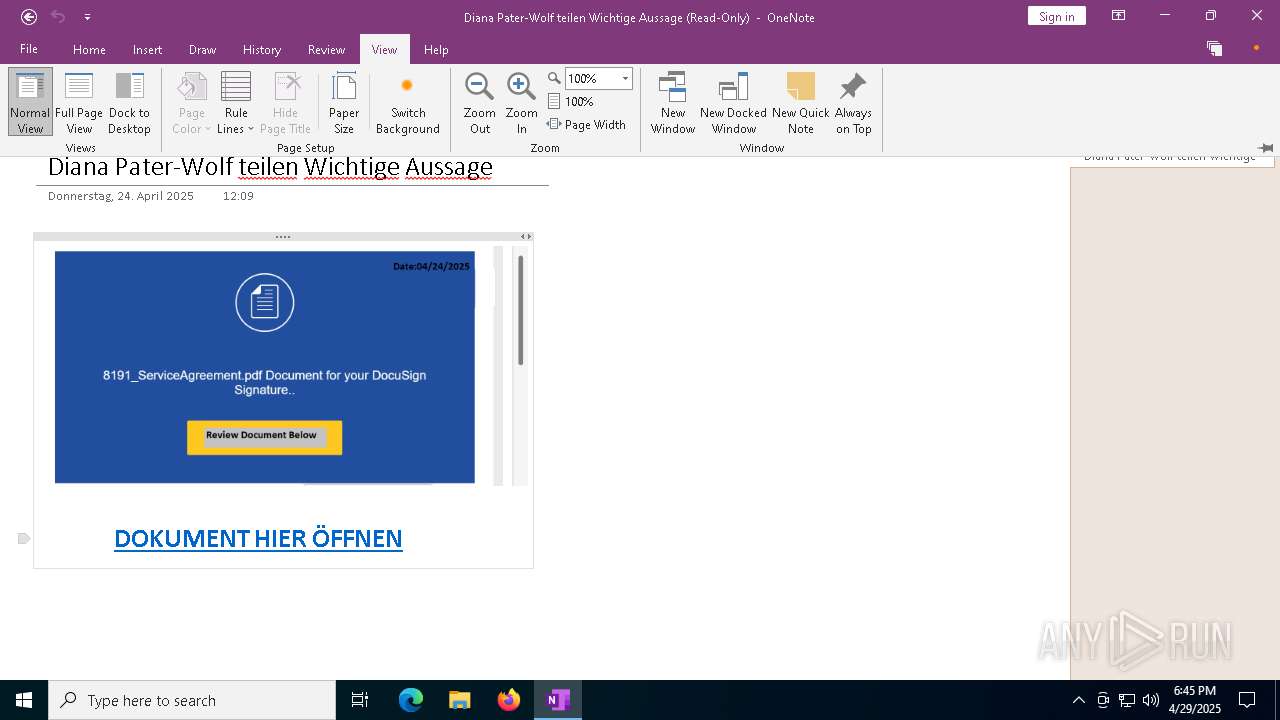
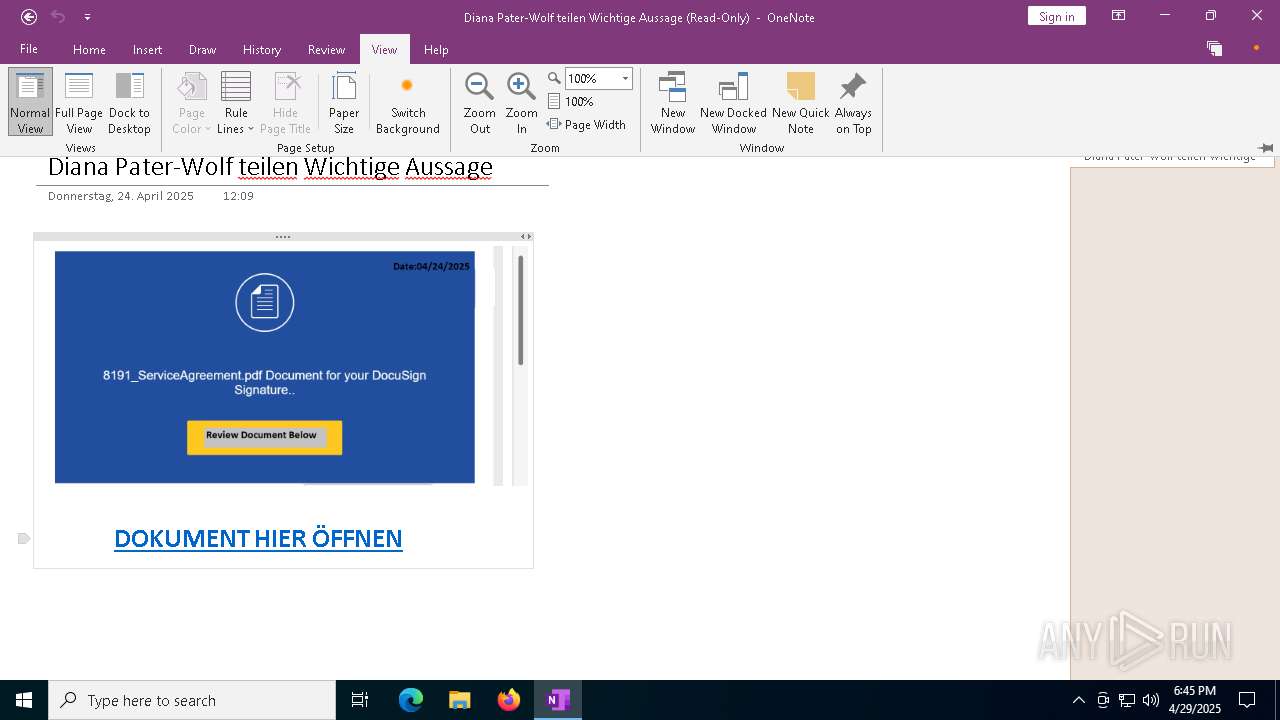
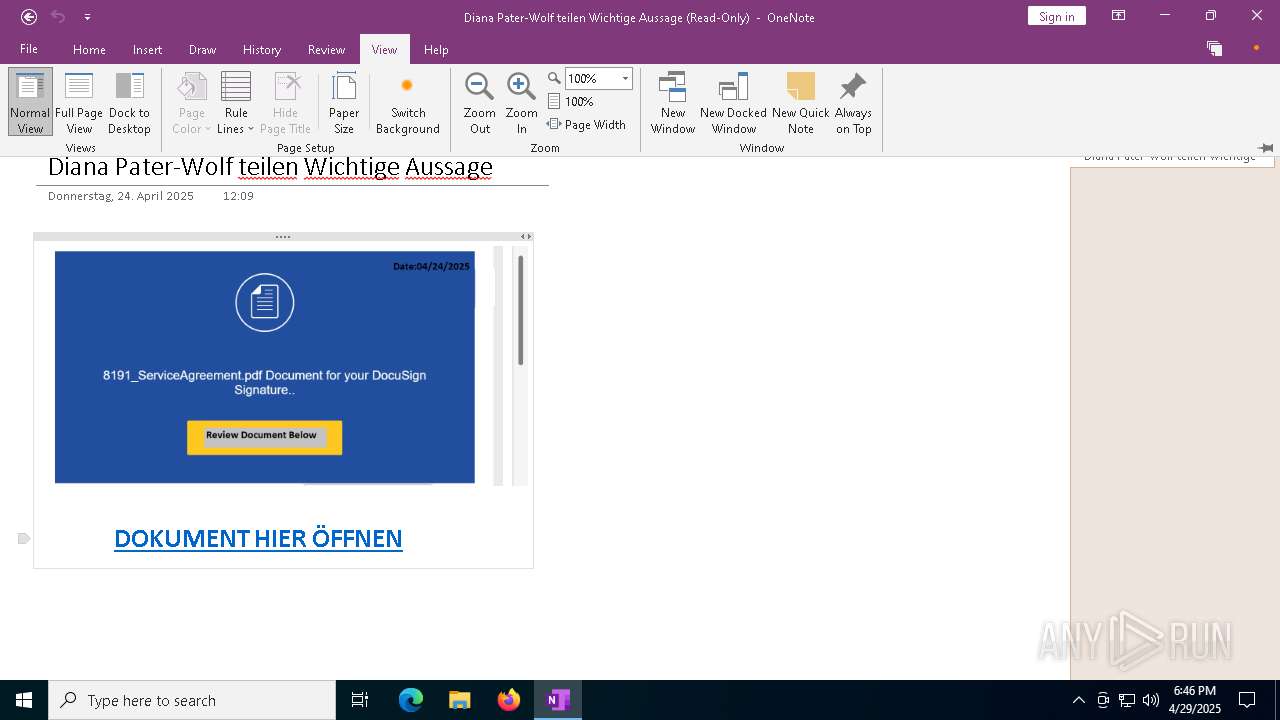
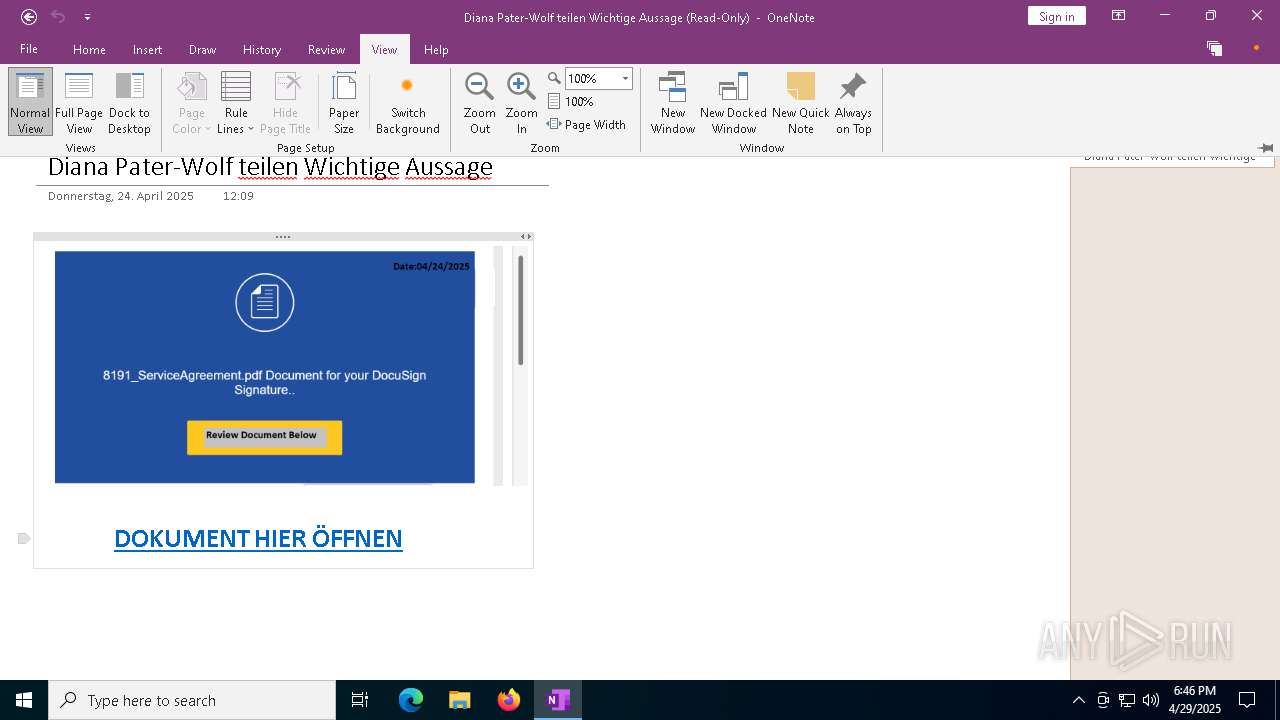
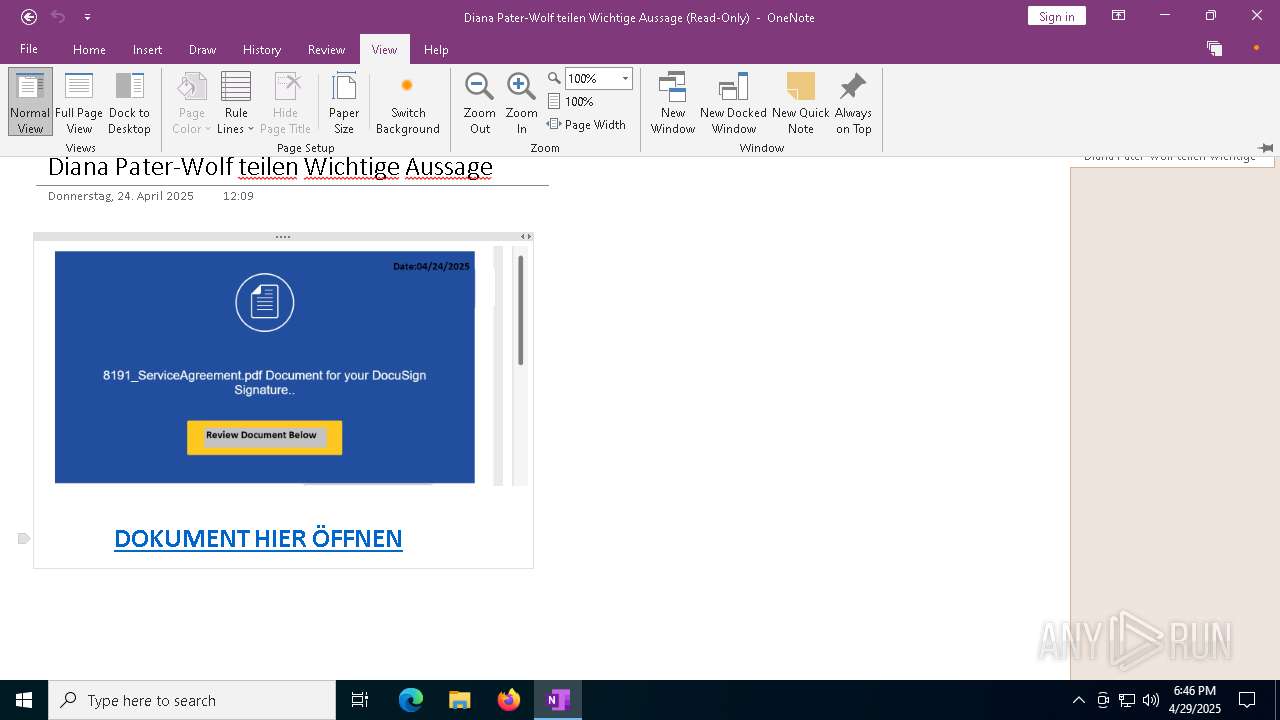
| File name: | wichtigeZahlungsdokumente.one |
| Full analysis: | https://app.any.run/tasks/48a5d146-2606-4156-9181-ec322608fcf6 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 18:43:40 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/onenote |
| File info: | Microsoft OneNote |
| MD5: | B7D8F312C66F9523F31AE4CF5B2ECBA3 |
| SHA1: | 6E2B6A672FDE3748623B062075D69901B080A1CA |
| SHA256: | 9F6639BB4778AD4089DB097F4DF4E4B1DD20D0550E9F9533614DB9793A42D4E3 |
| SSDEEP: | 3072:kA+R2lZsz1Ui9XwUerNBGMb0107u9euQwdiGBAaMLgY5:kHWC19gUeX0y7uReLg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 7000)
Creates file in the systems drive root
- ONENOTE.EXE (PID: 7000)
INFO
Checks supported languages
- ONENOTEM.EXE (PID: 5720)
Reads Microsoft Office registry keys
- ONENOTEM.EXE (PID: 5720)
Reads the computer name
- ONENOTEM.EXE (PID: 5720)
Reads the software policy settings
- slui.exe (PID: 736)
Checks proxy server information
- slui.exe (PID: 736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
EXIF
JFIF
| JFIFVersion: | 1.01 |
|---|---|
| ResolutionUnit: | inches |
| XResolution: | 96 |
| YResolution: | 96 |
EXIF
| Orientation: | Horizontal (normal) |
|---|
Composite
| ImageSize: | 1225x613 |
|---|---|
| Megapixels: | 0.751 |
Total processes
132
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 736 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | /tsr | C:\Program Files\Microsoft Office\root\Office16\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Send to OneNote Tool Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7000 | "C:\Program Files\Microsoft Office\Root\Office16\ONENOTE.EXE" C:\Users\admin\Desktop\wichtigeZahlungsdokumente.one | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
13 171
Read events
12 918
Write events
224
Delete events
29
Modification events
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 12 |
Value: 012C19000000001000B24E9A3E02000000000000000200000000000000 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\ONENOTE\7000 |
| Operation: | write | Name: | 0 |
Value: 0B0E10863DF3E2A78BD64EB09328FC2E5EF7532300469389DDC6EAA6EEED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E225763446C494E41384C537237784C67357549303451703444396E4730426B415A4C6B6C6361656270562B303D22CA0DC2190000C91003783634C511D836D2120B6F006E0065006E006F00740065002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (7000) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
10
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:D2A36389970D5F420B8269E69150AF00 | SHA256:065DB01421A23304065562216740082E48300461A40FBA427C6DC115E8A36F5E | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\946DCB8A-5EB5-49CB-A304-732DC59FFA32 | xml | |
MD5:FA43BDF4F74D8FAB8E63E612CE118028 | SHA256:4264EA949B672019AE92A686F5F6EF7B349226281B366087551A3DB08878E785 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\Send to OneNote.lnk | binary | |
MD5:4B8B5999ECAD688516E3E7E3C3FB7BC2 | SHA256:7C6444146D35EEAB85D6385B863172D3027A49470BF269672512C520B909B092 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryGE0407.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1bc9bbbe61f14501.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\0000000A.bin | binary | |
MD5:7E753FCB02782D8E8BC4369496E6E206 | SHA256:D2641D3408B4907A6B5FF43EB1FFF73AC256CFD8E7C857BCD9E3BAC0878874CD | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\U46M73YZ9YHFKJ9AUOKQ.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\0000000B.bin | binary | |
MD5:257C2B6A8C0FC1C49819A04408EBFF15 | SHA256:50D229746BA83FA623FC007B6118CAD840DEF0F9130D0AF6B6AE3C97E86BC0A6 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1bc9bbbe61f14501.customDestinations-ms~RF112596.TMP | binary | |
MD5:C32BC52A21EFE066C95CF6C4935220D7 | SHA256:0635BCDAD77D46DF9604BBAE323D88772F55AB176C3224E110B4154660DA3916 | |||
| 7000 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\0000000C.bin | binary | |
MD5:7E753FCB02782D8E8BC4369496E6E206 | SHA256:D2641D3408B4907A6B5FF43EB1FFF73AC256CFD8E7C857BCD9E3BAC0878874CD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
49
TCP/UDP connections
68
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 200 | 40.126.31.130:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.159.68:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 52.109.89.18:443 | https://officeclient.microsoft.com/config16/?lcid=1033&syslcid=1033&uilcid=1033&build=16.0.16026&crev=3 | unknown | xml | 179 Kb | whitelisted |
— | — | POST | 200 | 13.107.6.156:443 | https://roaming.officeapps.live.com/rs/RoamingSoapService.svc | unknown | — | — | whitelisted |
— | — | POST | 400 | 20.190.159.75:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 20.190.159.2:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | GET | 200 | 52.123.128.14:443 | https://ecs.office.com/config/v2/Office/onenote/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=onenote&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=onenote.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=OneNoteFreeRetail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bE2F33D86-8BA7-4ED6-B093-28FC2E5EF753%7d&LabMachine=false | unknown | tss | 368 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
— | — | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 23.53.40.178:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6544 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
7000 | ONENOTE.EXE | 52.109.89.18:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |