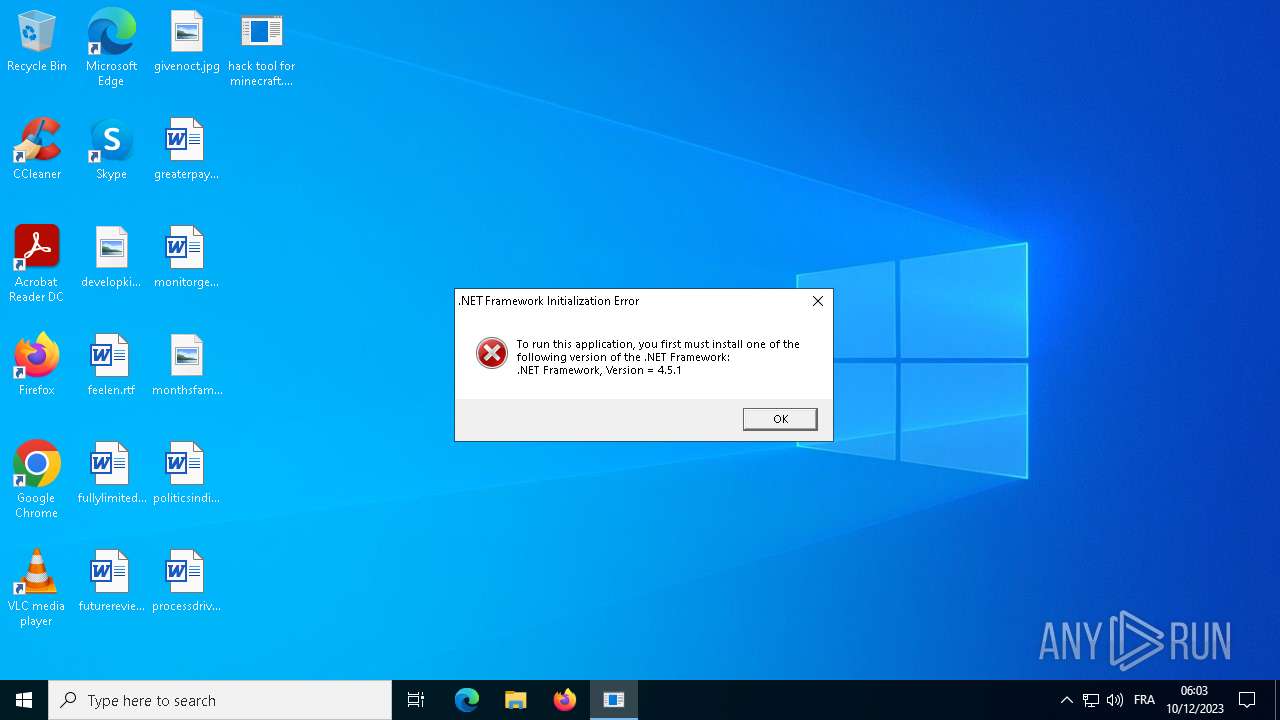
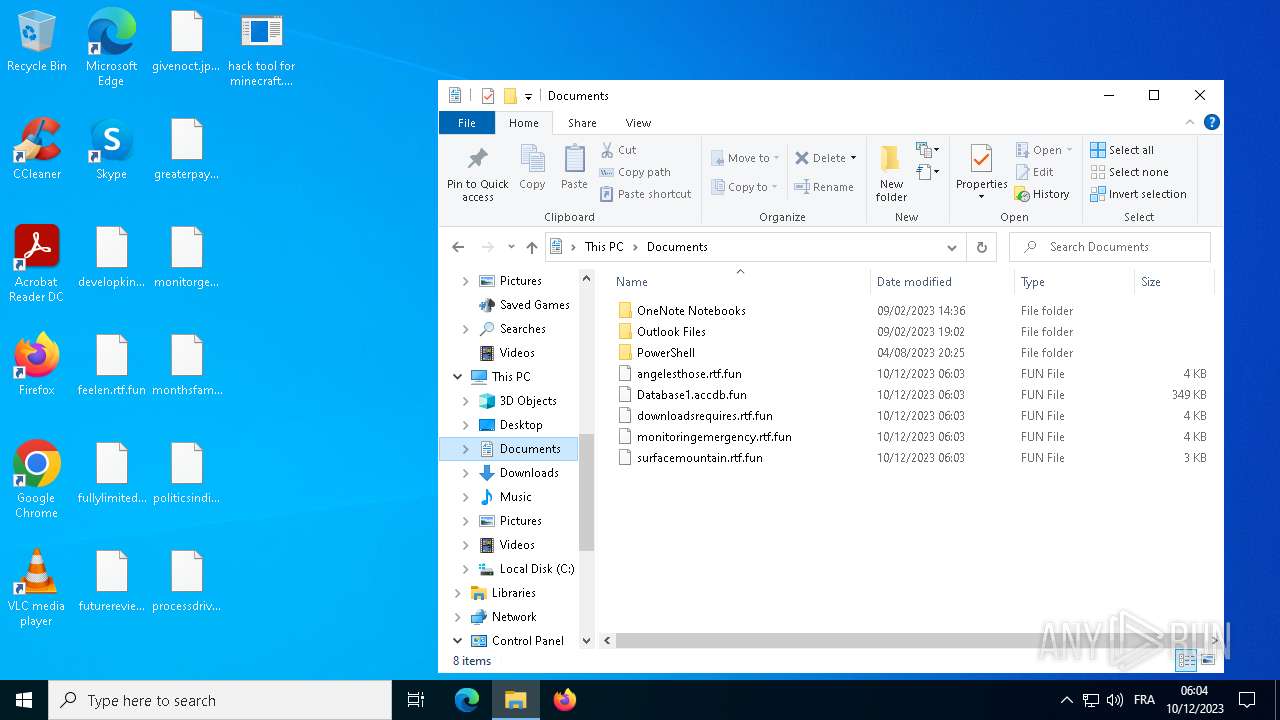
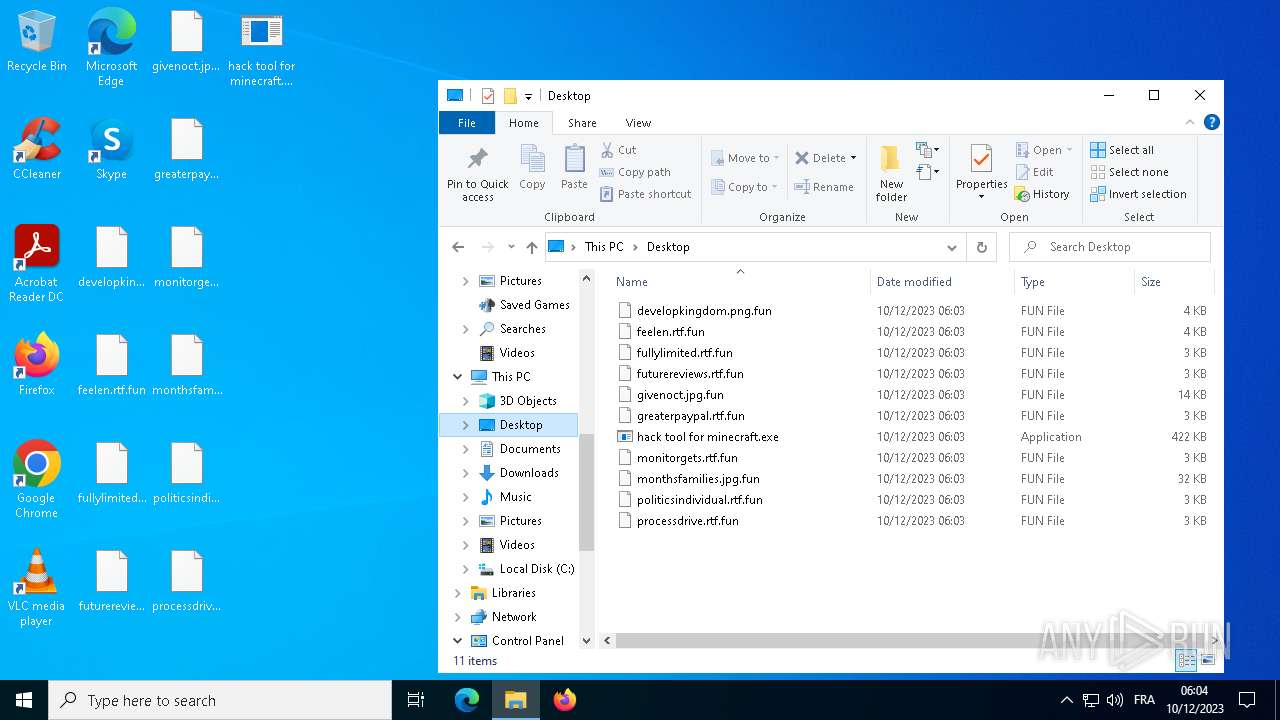
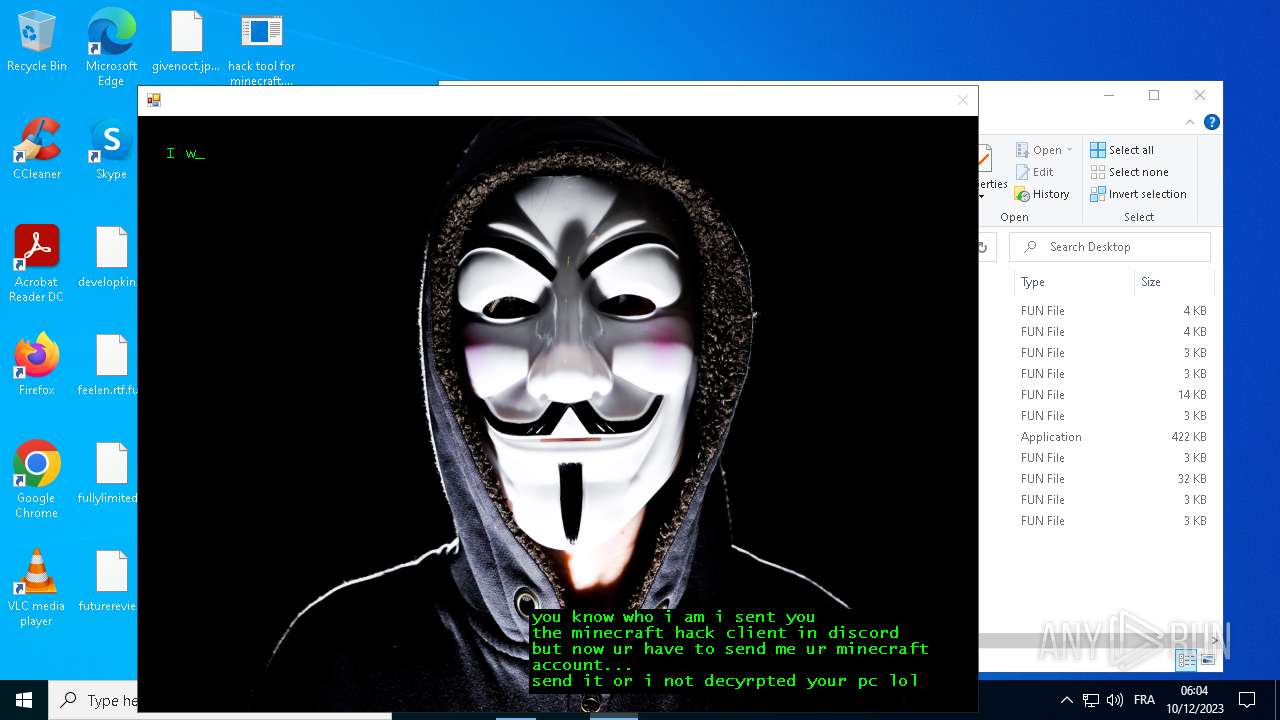
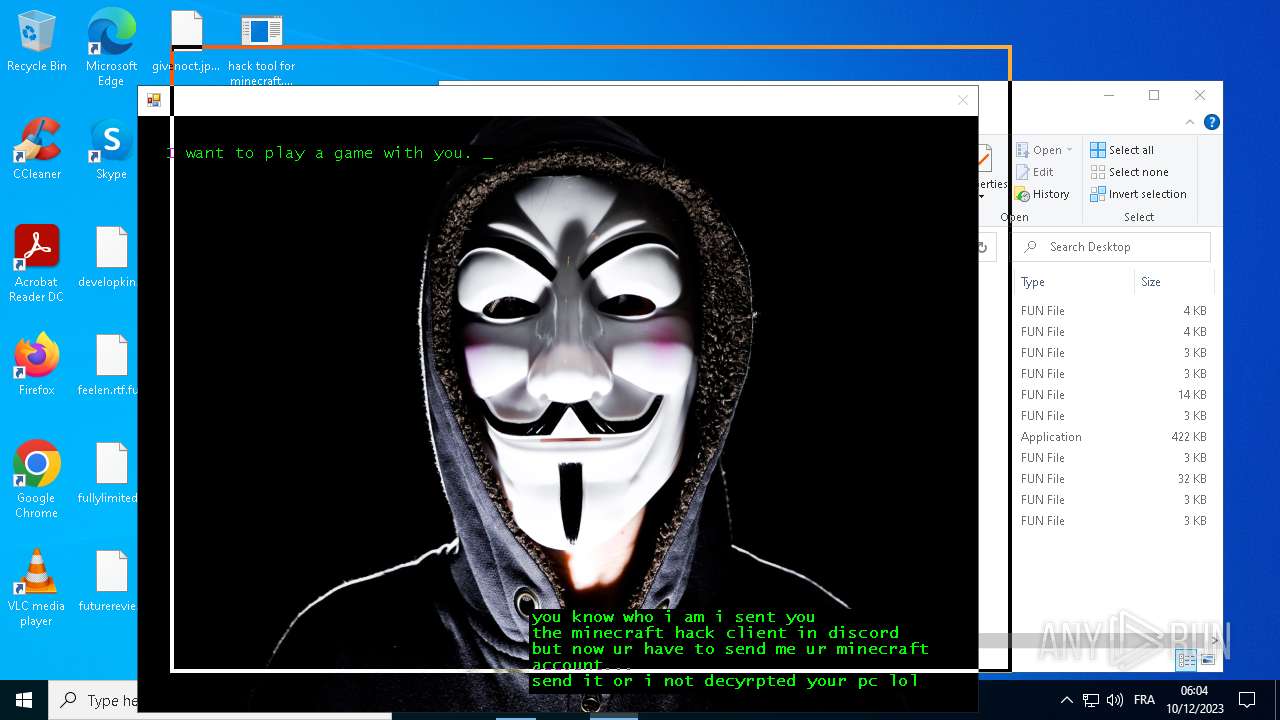
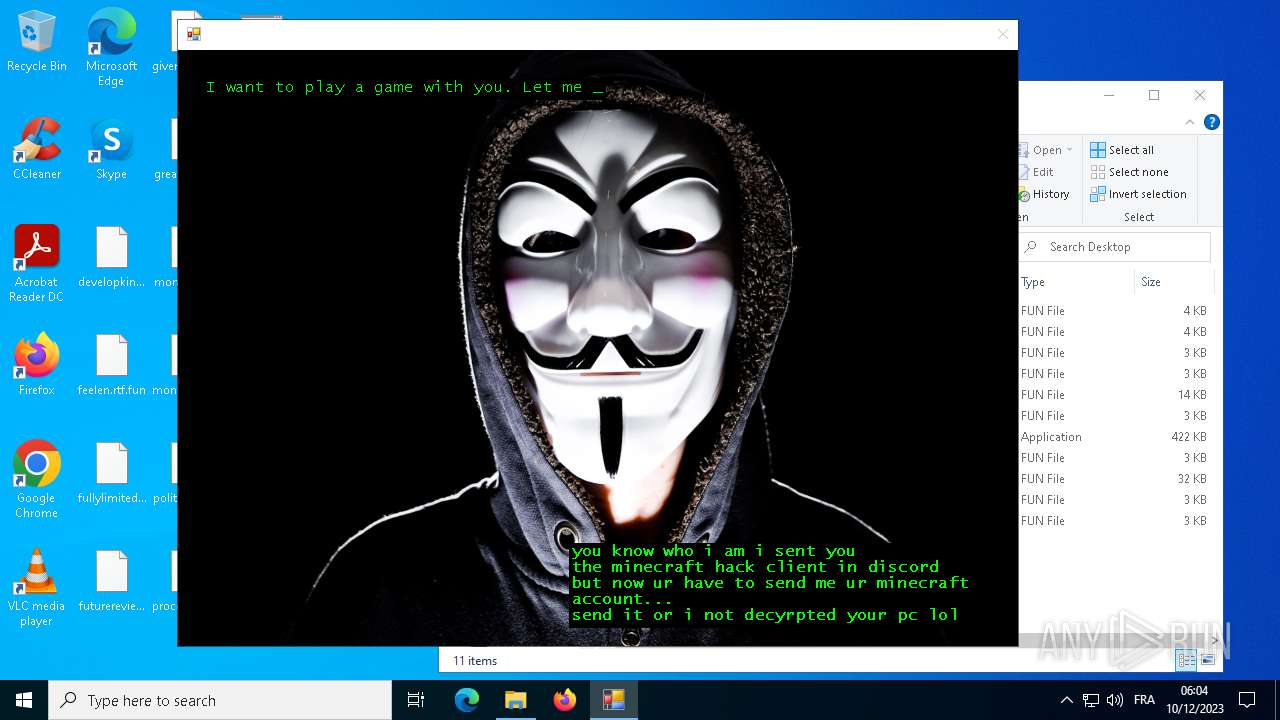
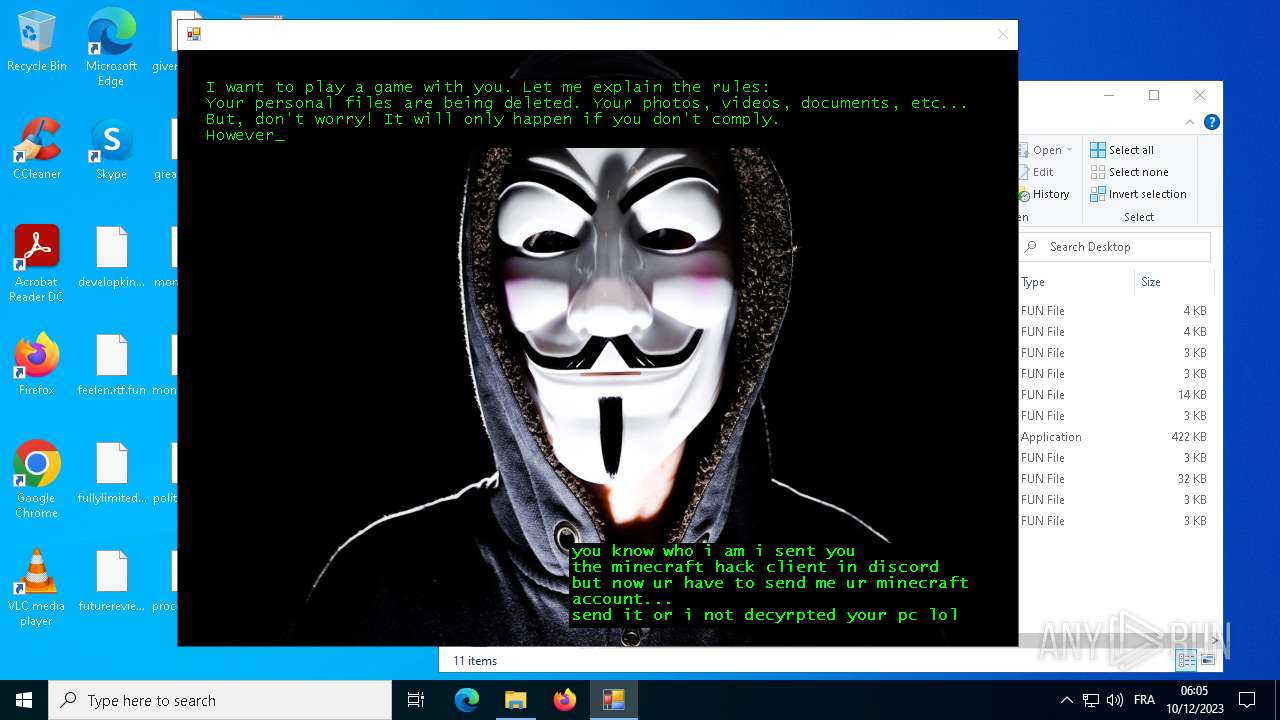
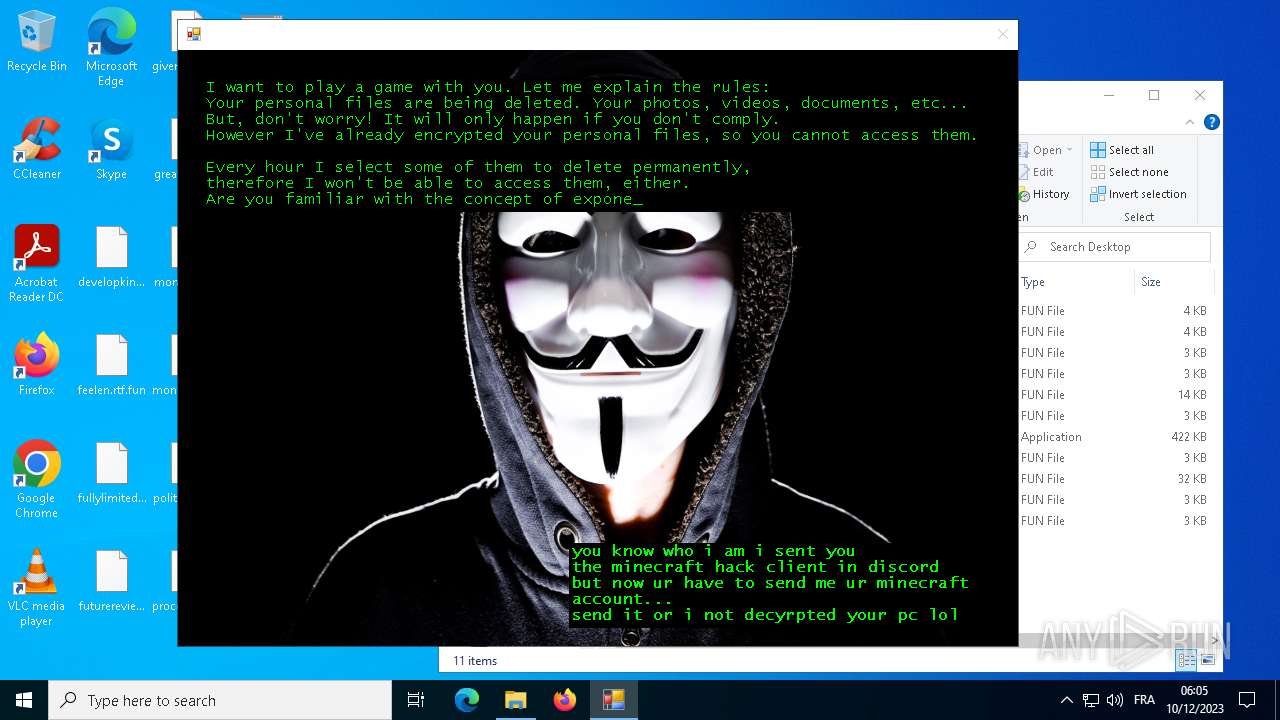
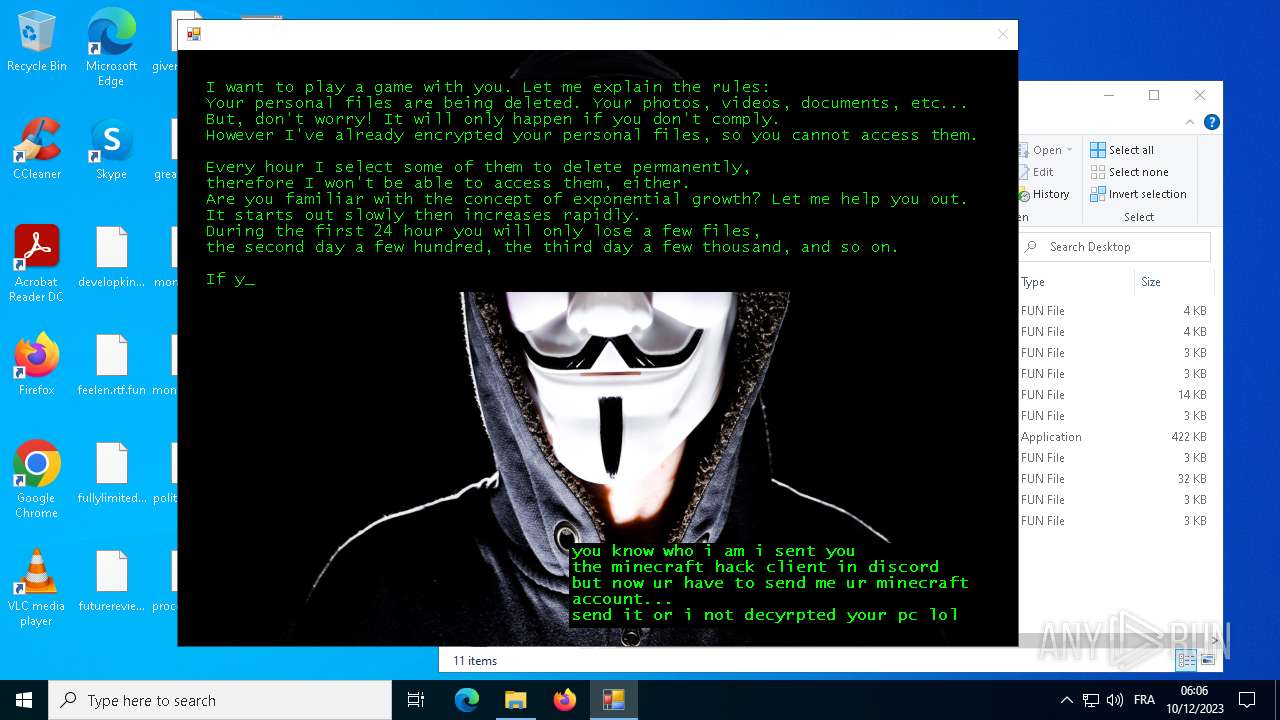
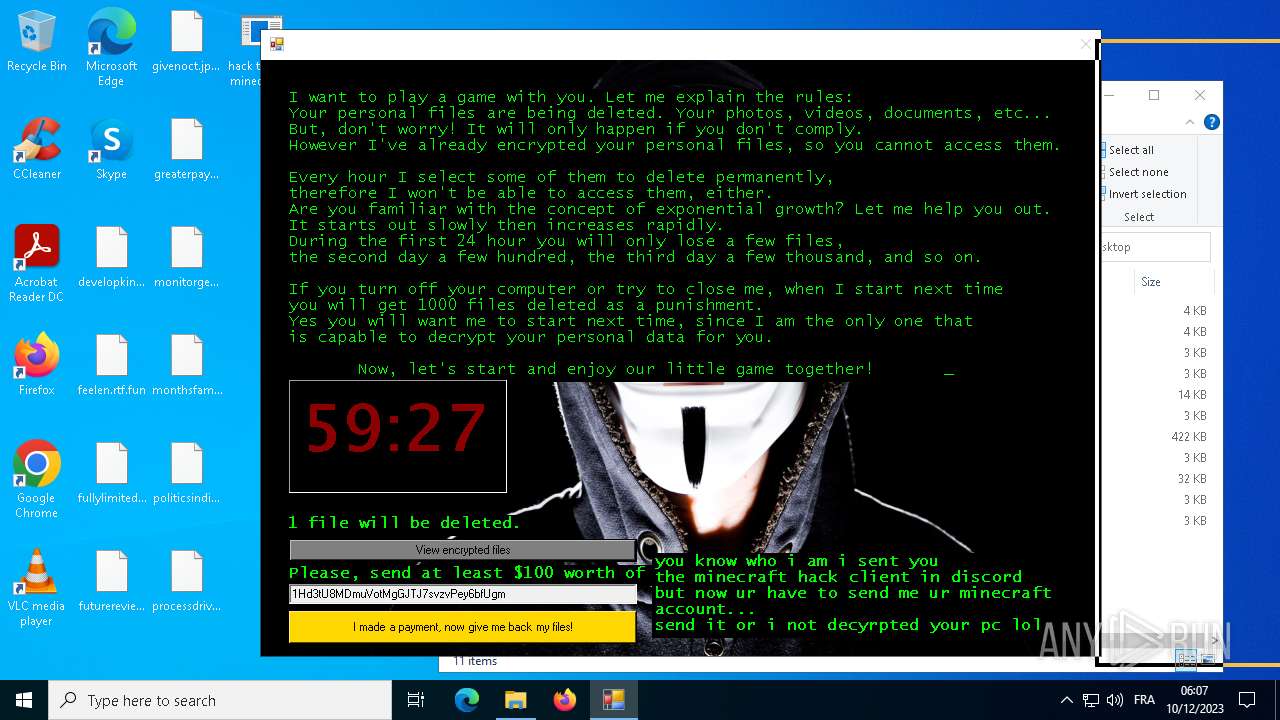
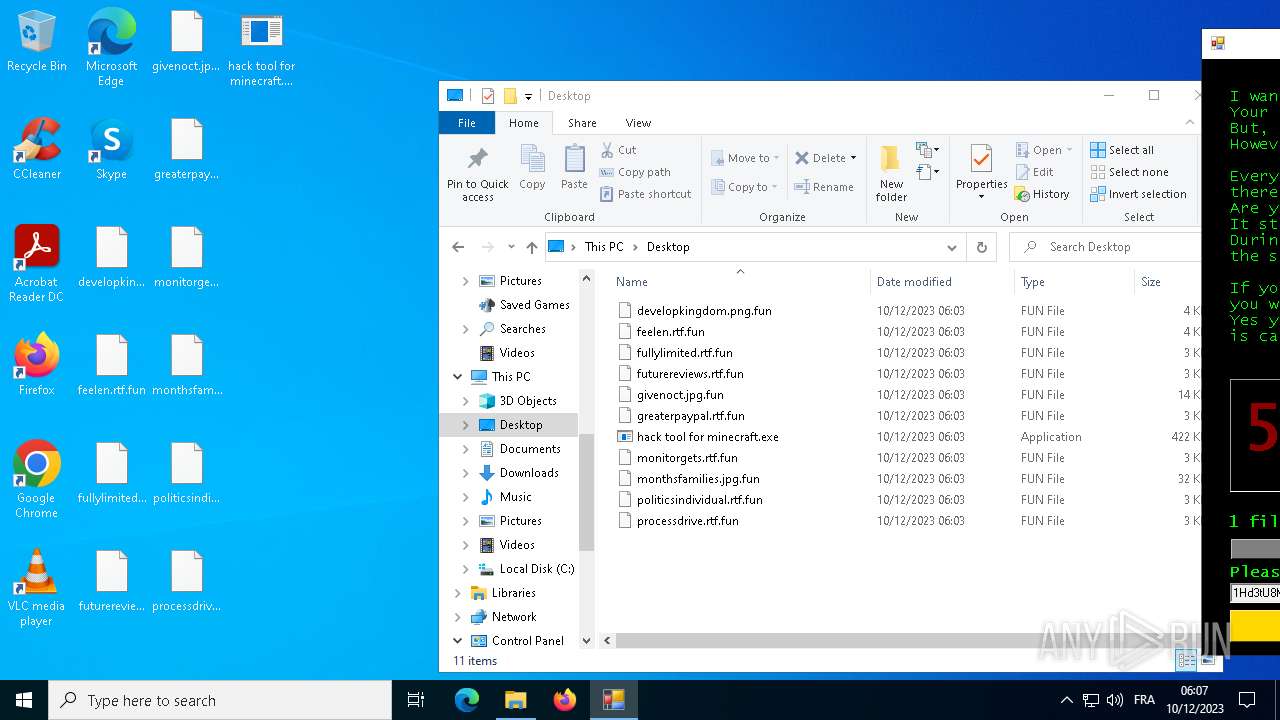
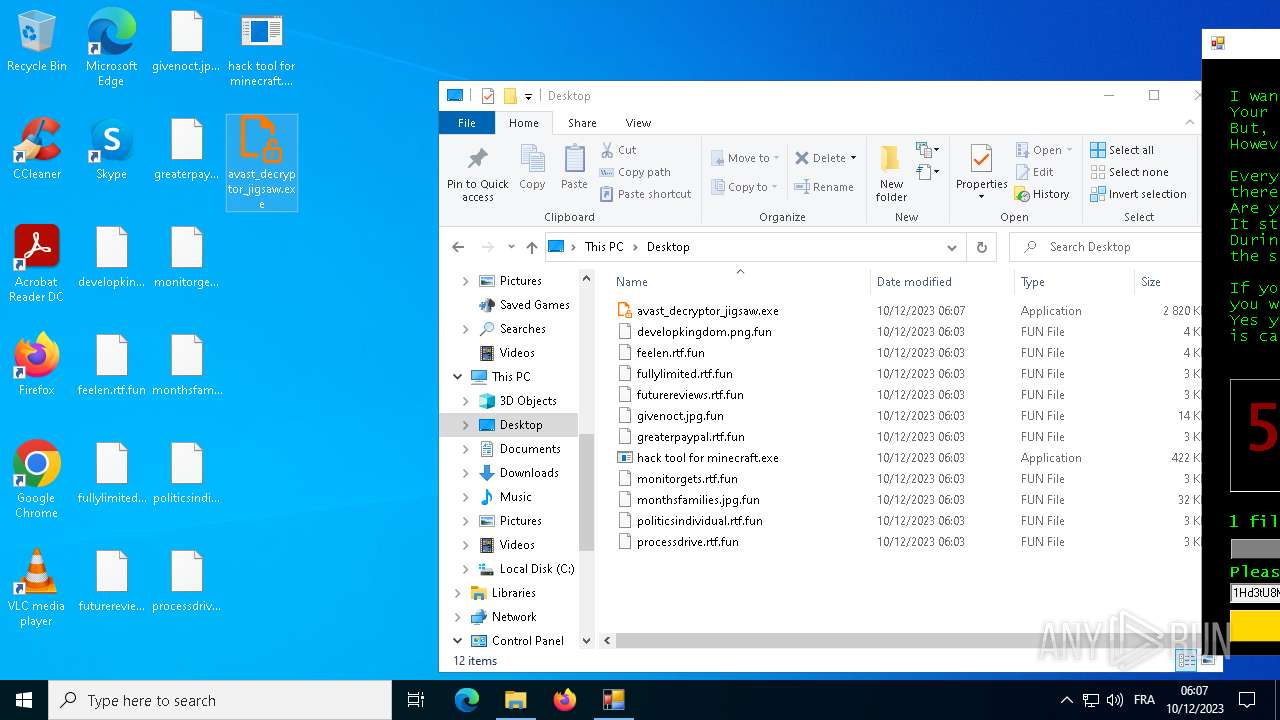
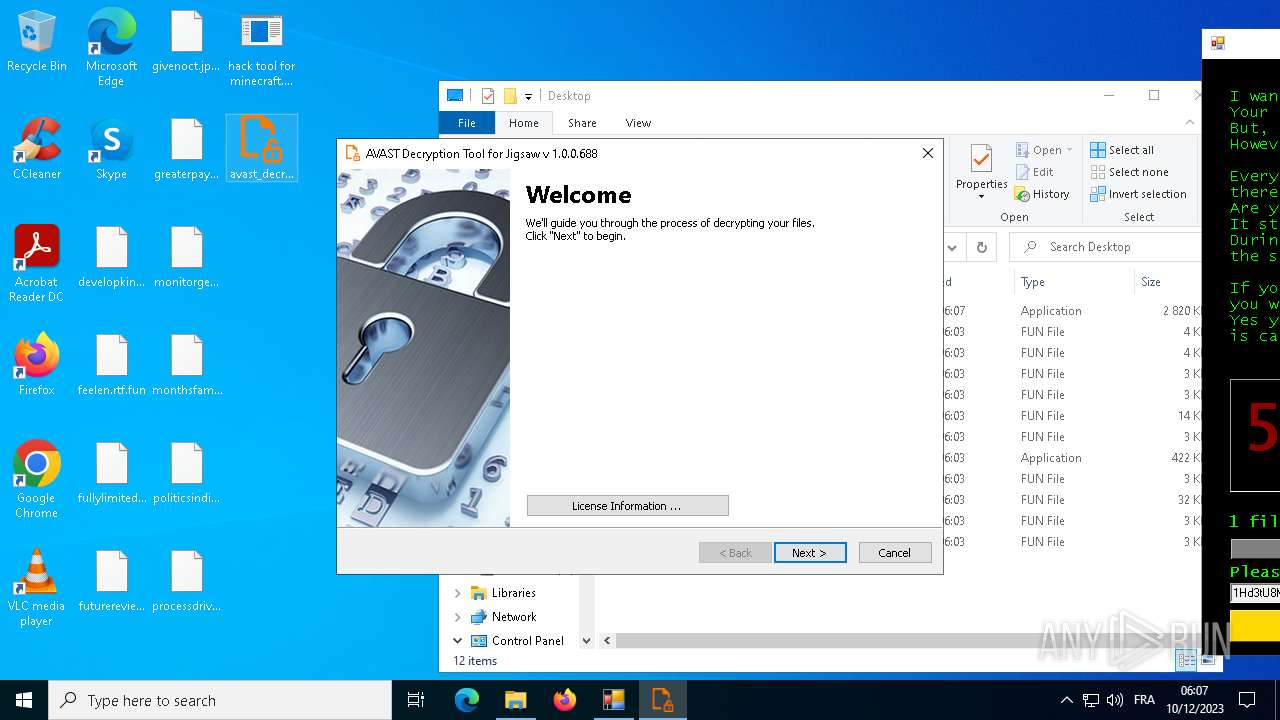
| File name: | hack tool for minecraft.exe |
| Full analysis: | https://app.any.run/tasks/0b174c8a-67fa-4fea-9fb3-186cc9d890c4 |
| Verdict: | Malicious activity |
| Analysis date: | December 10, 2023, 05:03:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 1FF8649E8F8D0652D583B9A648161D3F |
| SHA1: | 3441FF983221742ED460F8310E49203B5DC59A15 |
| SHA256: | 9F3C538A1118F82D49A993967C520BE4C7F14AD994EB17C4D778E5D7F32241A7 |
| SSDEEP: | 12288:2w1pOfl/oUzs8vwfzNquSgkE9tSF/aXx6:3po/oUNwfpqVrktOc6 |
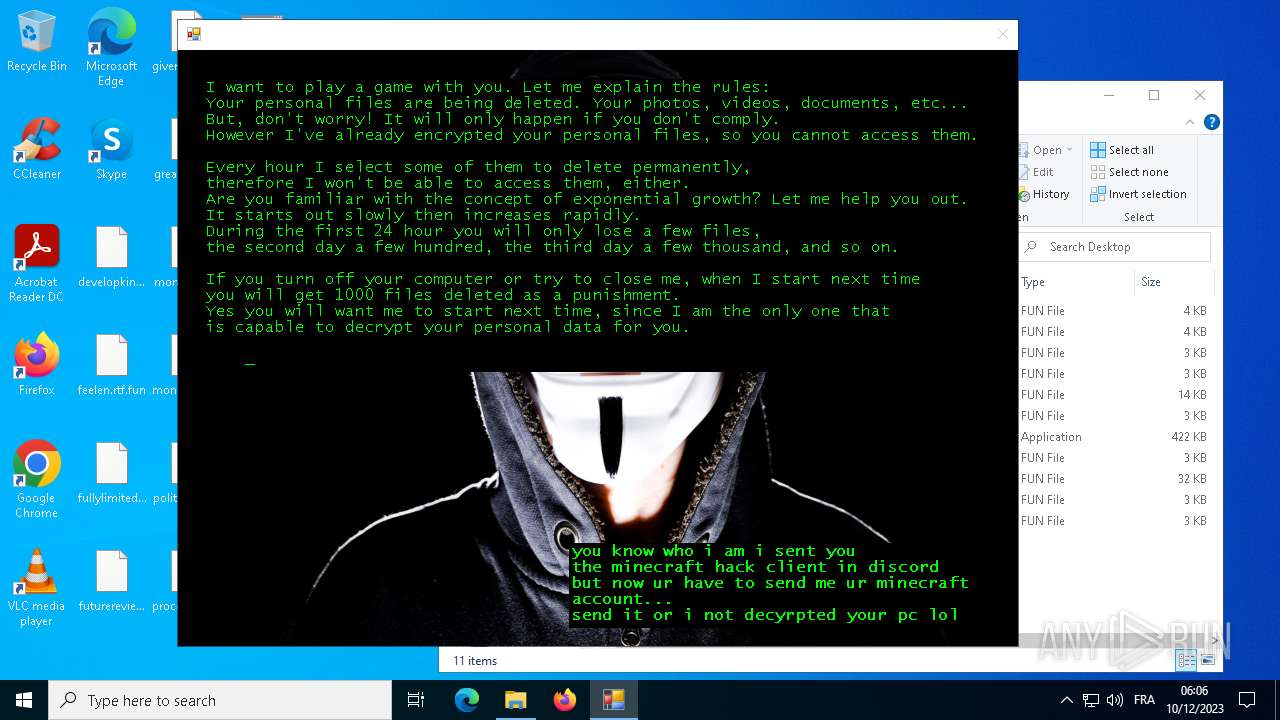
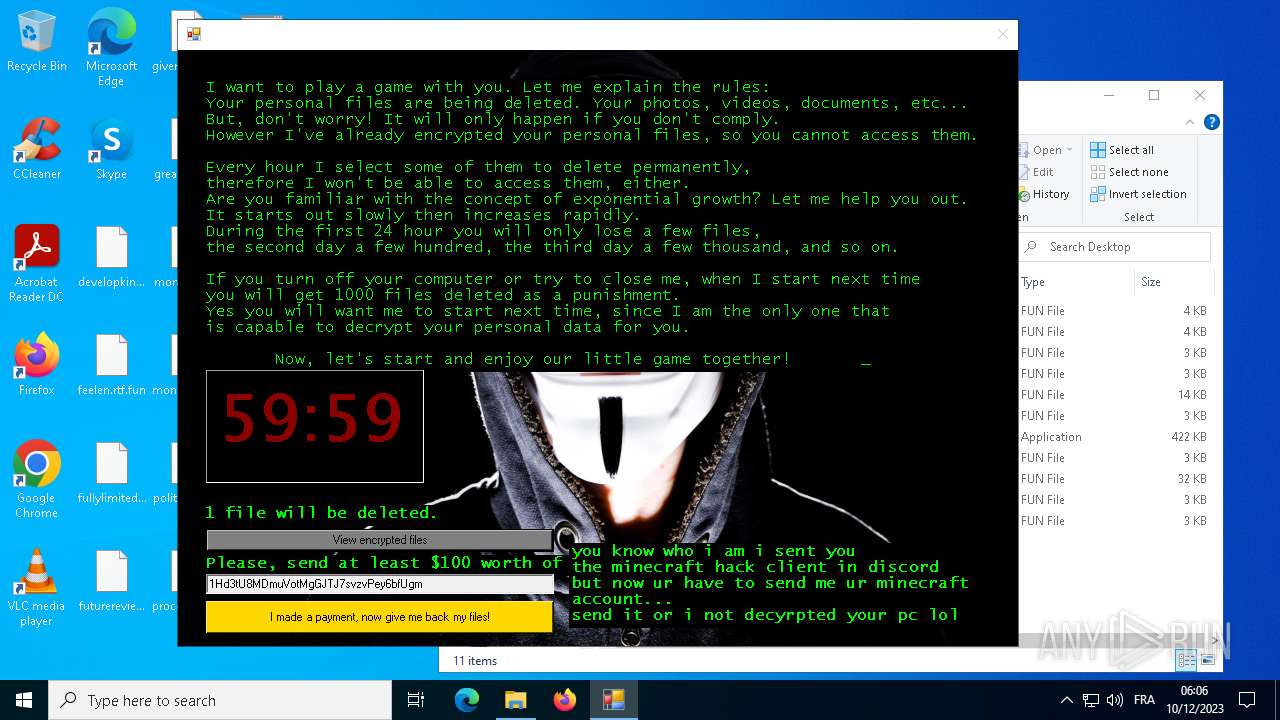
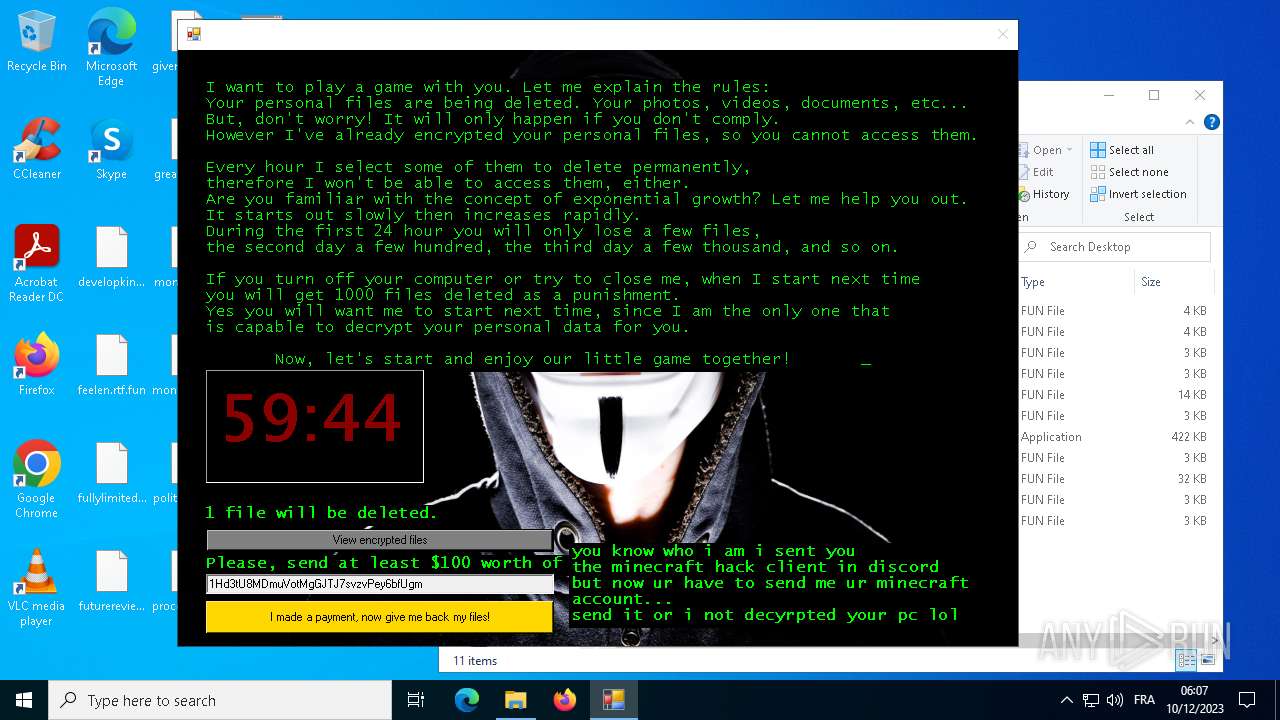
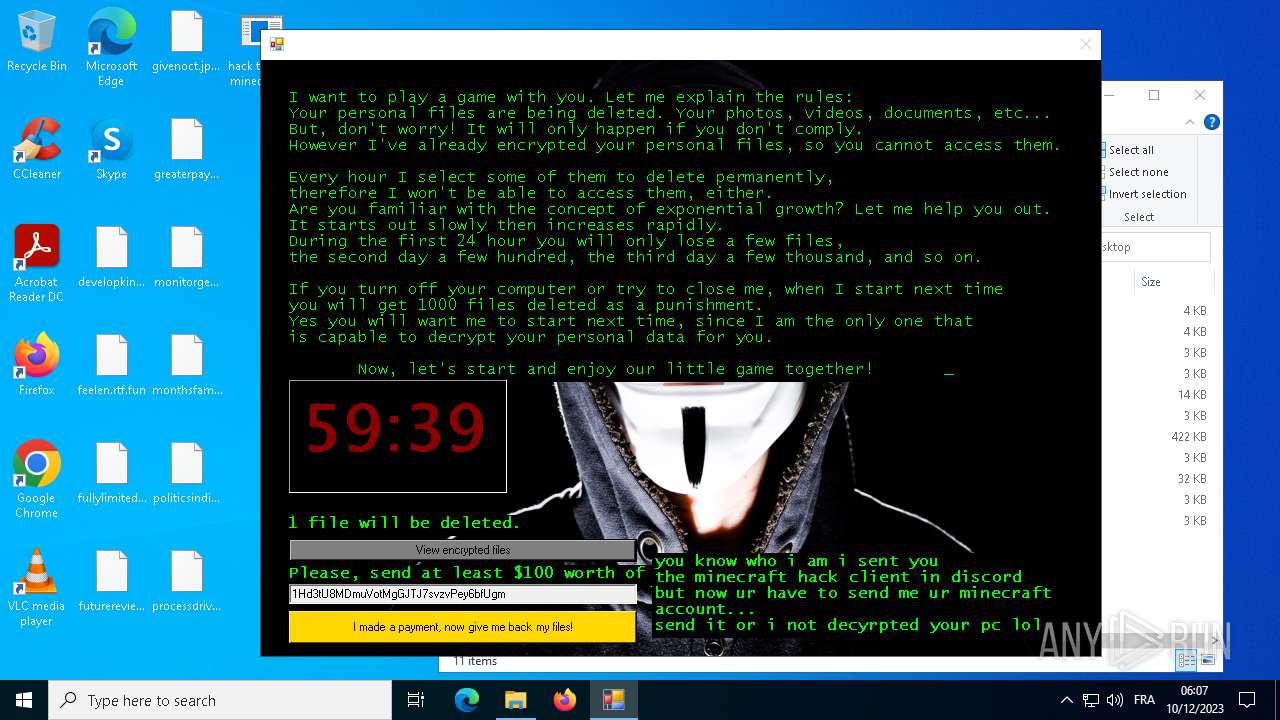
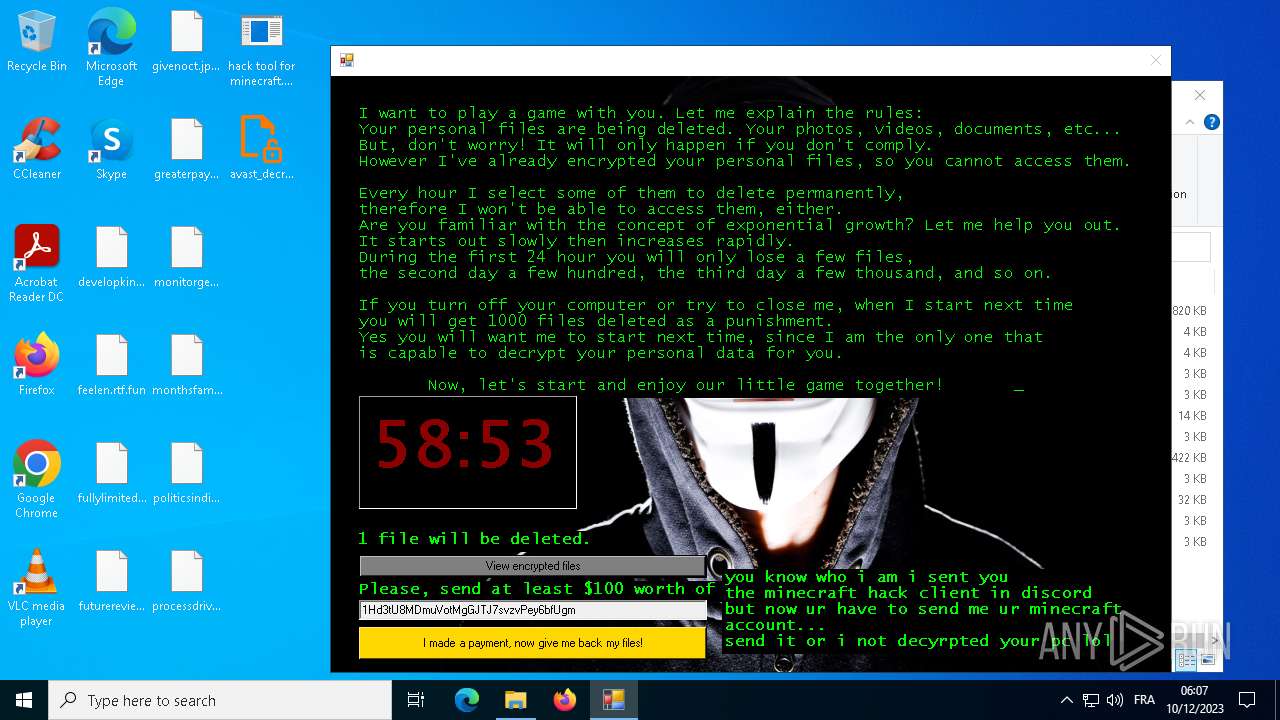
MALICIOUS
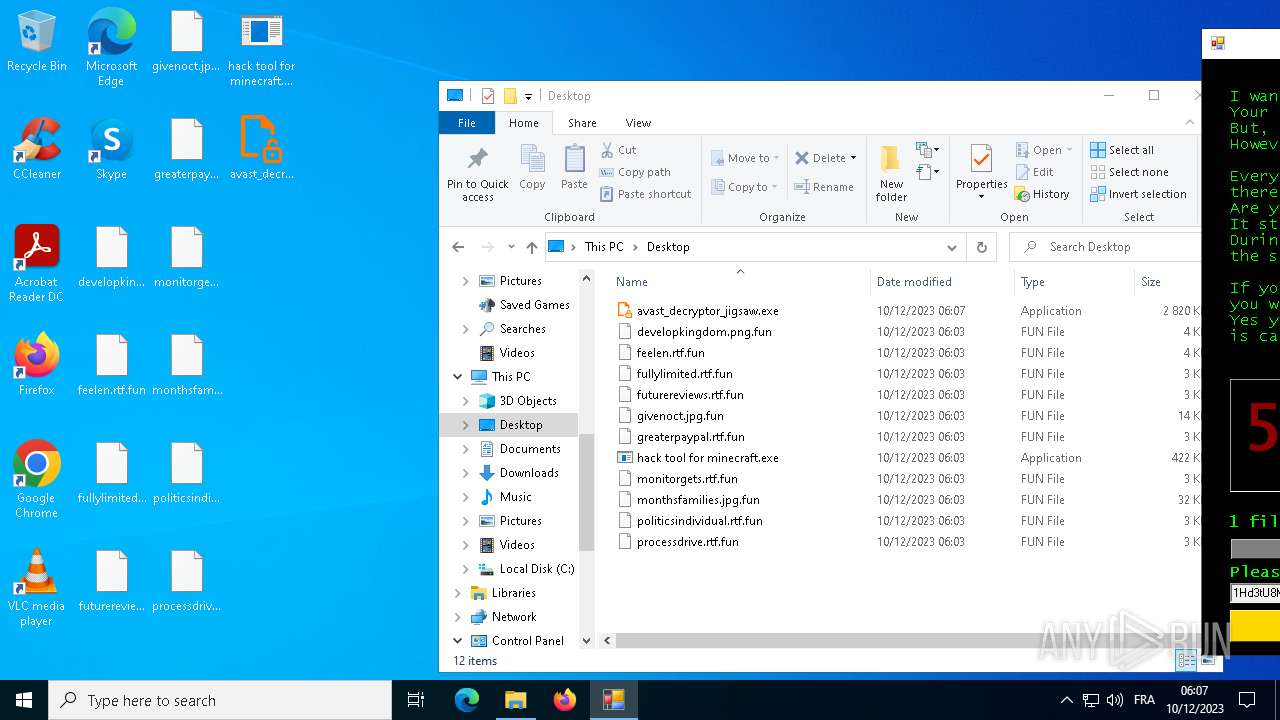
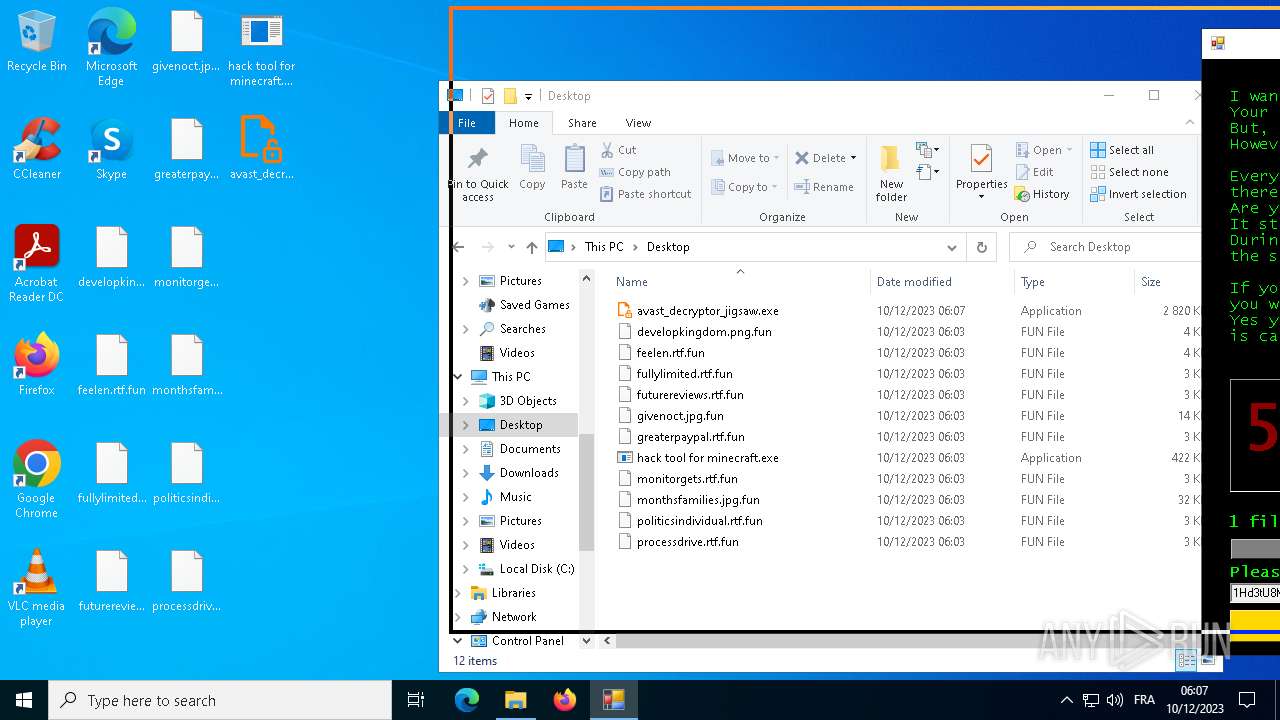
Drops the executable file immediately after the start
- hack tool for minecraft.exe (PID: 5432)
- drpbx.exe (PID: 5772)
Steals credentials from Web Browsers
- drpbx.exe (PID: 5772)
Actions looks like stealing of personal data
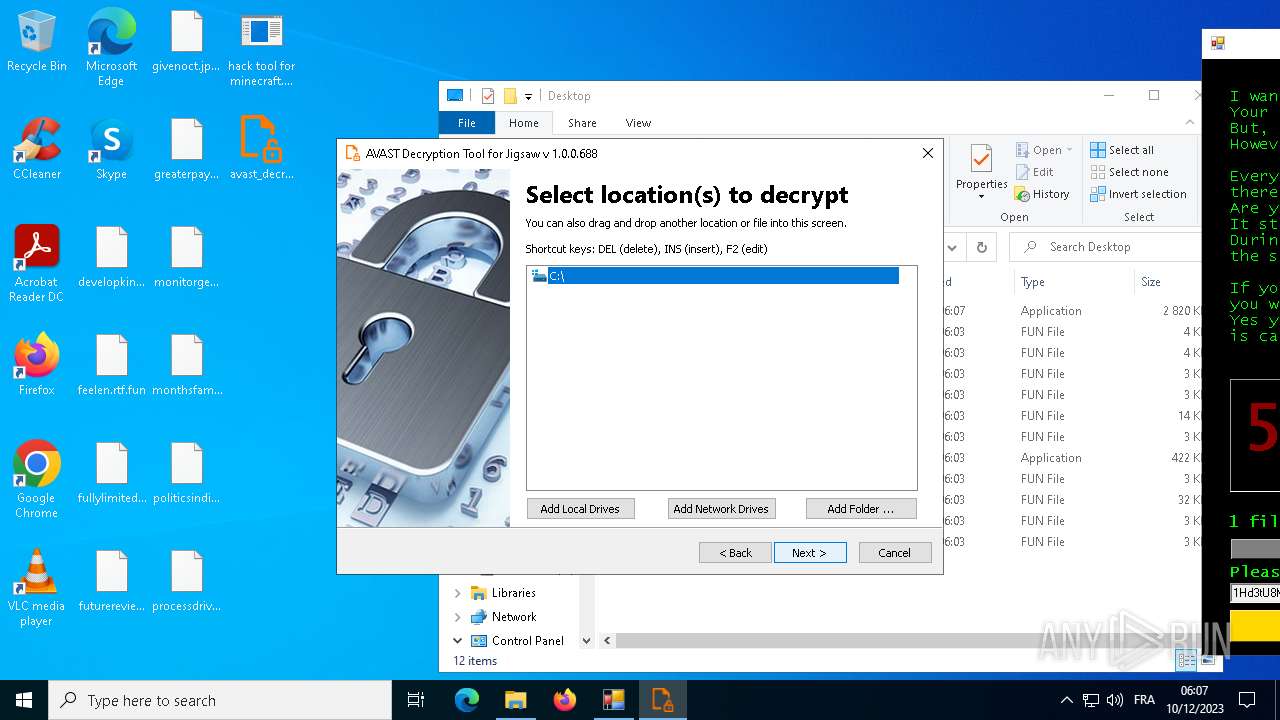
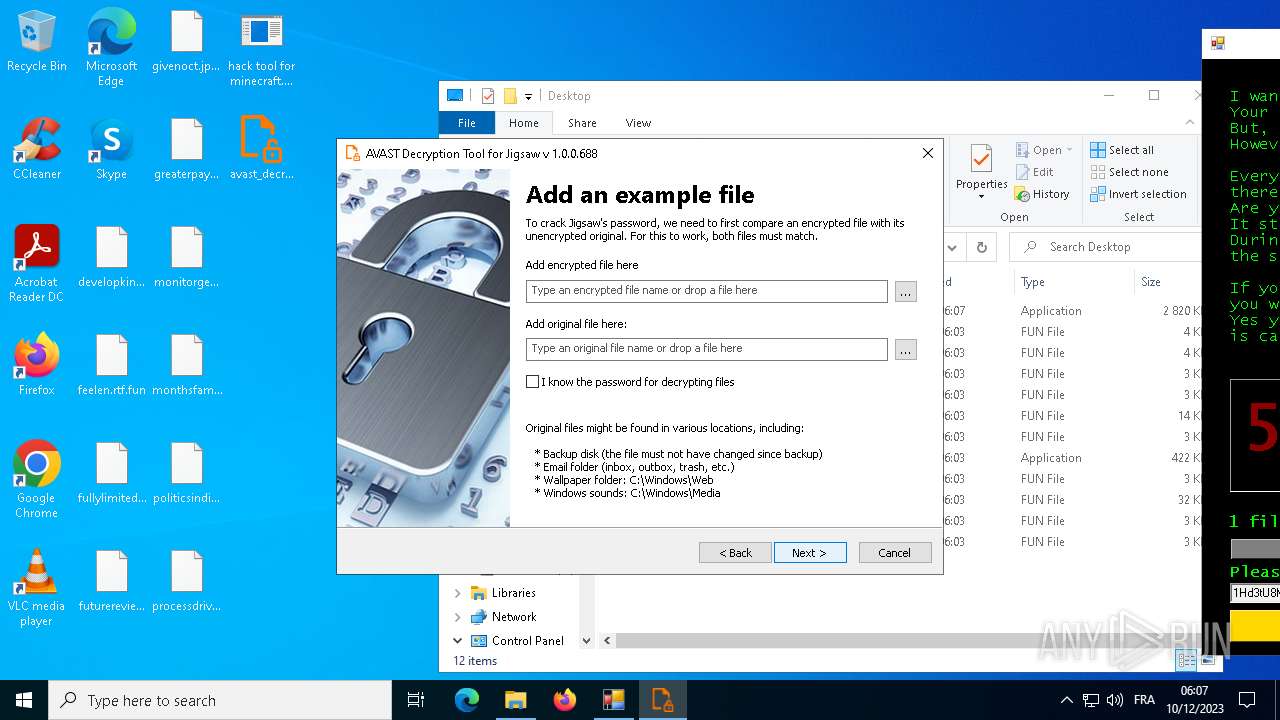
- avast_decryptor_jigsaw.exe (PID: 2864)
- drpbx.exe (PID: 5772)
SUSPICIOUS
Starts itself from another location
- hack tool for minecraft.exe (PID: 5432)
Reads browser cookies
- drpbx.exe (PID: 5772)
INFO
Reads the machine GUID from the registry
- hack tool for minecraft.exe (PID: 5432)
- drpbx.exe (PID: 5772)
Checks supported languages
- hack tool for minecraft.exe (PID: 5432)
- drpbx.exe (PID: 5772)
- avast_decryptor_jigsaw.exe (PID: 2864)
Reads the computer name
- hack tool for minecraft.exe (PID: 5432)
- drpbx.exe (PID: 5772)
- avast_decryptor_jigsaw.exe (PID: 2864)
Creates files or folders in the user directory
- hack tool for minecraft.exe (PID: 5432)
- drpbx.exe (PID: 5772)
Creates files in the program directory
- drpbx.exe (PID: 5772)
Manual execution by a user
- avast_decryptor_jigsaw.exe (PID: 2864)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:10:26 00:50:34+02:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 428544 |
| InitializedDataSize: | 2560 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6a97e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 37.0.2.5583 |
| ProductVersionNumber: | 37.0.2.5583 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Firefox |
| FileVersion: | 37.0.2.5583 |
| InternalName: | JigsawRansomware.exe |
| LegalCopyright: | Copyright 1999-2012 Firefox and Mozzilla developers. All rights reserved. |
| LegalTrademarks: | - |
| OriginalFileName: | JigsawRansomware.exe |
| ProductName: | Firefox |
| ProductVersion: | 37.0.2.5583 |
| AssemblyVersion: | 37.0.2.5583 |
Total processes
127
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2864 | "C:\Users\admin\Desktop\avast_decryptor_jigsaw.exe" | C:\Users\admin\Desktop\avast_decryptor_jigsaw.exe | explorer.exe | ||||||||||||
User: admin Company: AVAST Software Integrity Level: MEDIUM Description: Ransomware Decryptor Exit code: 0 Version: 1.0.0.688 Modules
| |||||||||||||||
| 5432 | "C:\Users\admin\Desktop\hack tool for minecraft.exe" | C:\Users\admin\Desktop\hack tool for minecraft.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
| 5772 | "C:\Users\admin\AppData\Local\Drpbx\drpbx.exe" C:\Users\admin\Desktop\hack?tool?for?minecraft.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | hack tool for minecraft.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 37.0.2.5583 Modules
| |||||||||||||||
Total events
68 602
Read events
68 594
Write events
8
Delete events
0
Modification events
| (PID) Process: | (5432) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (5432) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (5432) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (5432) hack tool for minecraft.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
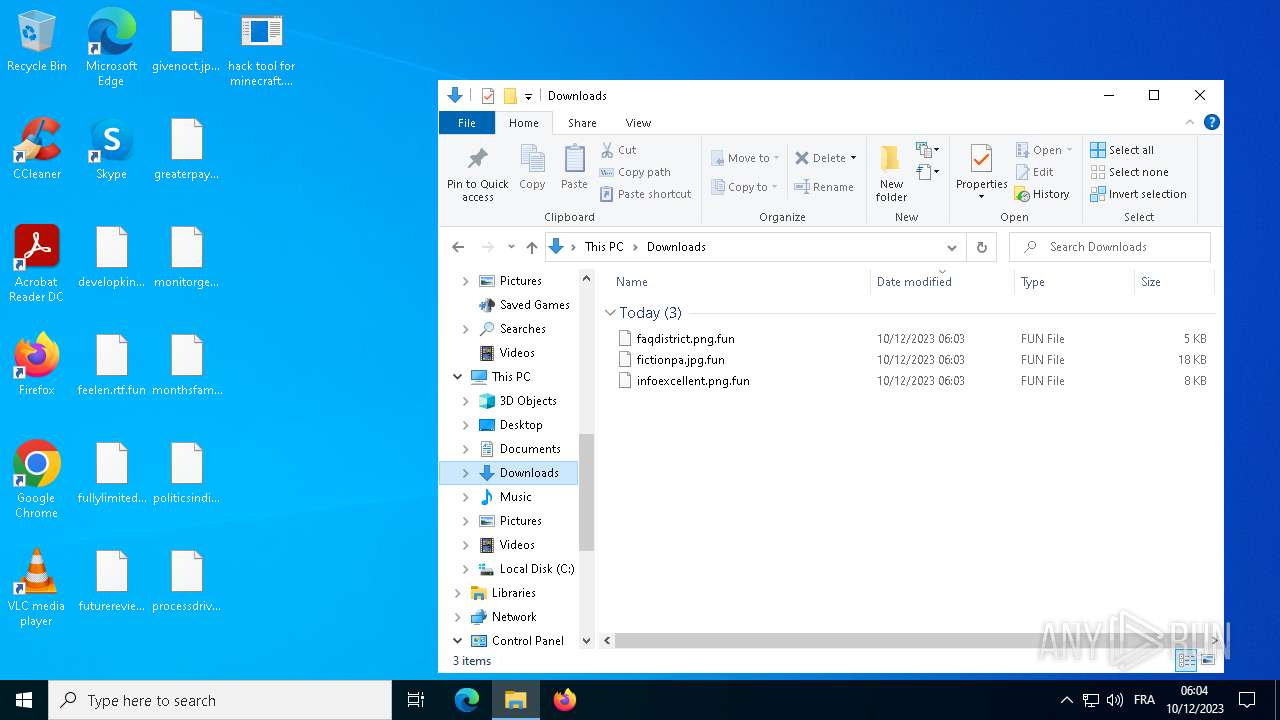
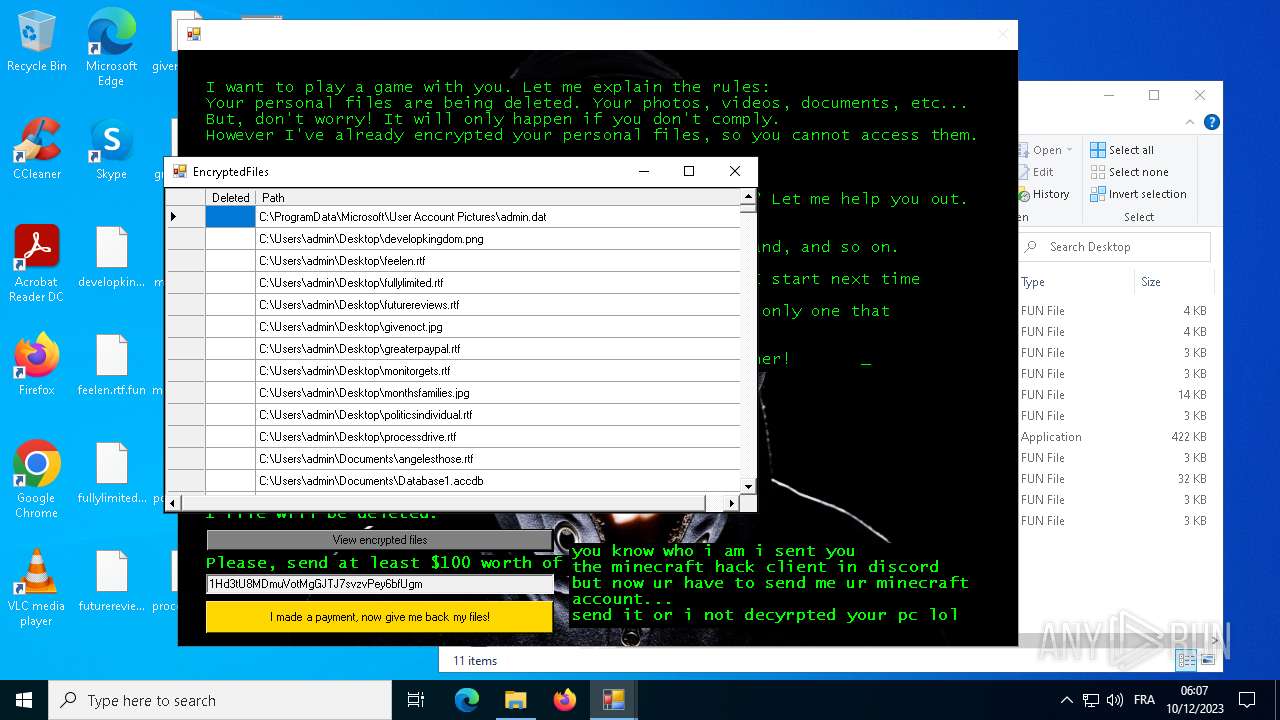
Executable files
5
Suspicious files
950
Text files
6
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5432 | hack tool for minecraft.exe | C:\Users\admin\AppData\Roaming\Frfx\firefox.exe | executable | |
MD5:1FF8649E8F8D0652D583B9A648161D3F | SHA256:9F3C538A1118F82D49A993967C520BE4C7F14AD994EB17C4D778E5D7F32241A7 | |||
| 5772 | drpbx.exe | C:\Users\admin\Desktop\fullylimited.rtf.fun | binary | |
MD5:7C47B68D054367C165D0EEB275928CC3 | SHA256:838DDAD956D4E411247C43F83905F0E950F0642408762208DE696A740F1D85CD | |||
| 5432 | hack tool for minecraft.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v2.0\UsageLogs\hack tool for minecraft.exe.log | text | |
MD5:7BBA658A9241C70ACB49137516C3D0A2 | SHA256:4302D33D36311F70811394BB5167CB5493B6B182FF7040B8827226F502F5A70D | |||
| 5432 | hack tool for minecraft.exe | C:\Users\admin\AppData\Local\Drpbx\drpbx.exe | executable | |
MD5:1FF8649E8F8D0652D583B9A648161D3F | SHA256:9F3C538A1118F82D49A993967C520BE4C7F14AD994EB17C4D778E5D7F32241A7 | |||
| 5772 | drpbx.exe | C:\ProgramData\Microsoft\User Account Pictures\admin.dat.fun | binary | |
MD5:CFDAE8214D34112DBEE6587664059558 | SHA256:33088CB514406F31E3D96A92C03294121EE9F24E176F7062625C2B36BEE7A325 | |||
| 5772 | drpbx.exe | C:\Users\admin\Documents\downloadsrequires.rtf.fun | binary | |
MD5:EAAA228408DC31AA88135796B157B819 | SHA256:8689813EBE093528FDE0DE405FD6A0D2098A4FF4FD8B1D4B2B119C970F00D5A7 | |||
| 5772 | drpbx.exe | C:\Users\admin\Desktop\processdrive.rtf.fun | binary | |
MD5:58FF0CD58F76E0093A66781D96E37BA1 | SHA256:B2230F1644B3AB47893AB8A2311E5866B1E16D7398BE51767229766AEC445070 | |||
| 5772 | drpbx.exe | C:\Users\admin\Documents\Database1.accdb.fun | binary | |
MD5:4E23D6262B5935B323607B0C3A8E7D45 | SHA256:61B9915710B441DDC6EC6B2540B62AC5BAB4B50867A1034A142BCCDD515D45C9 | |||
| 5772 | drpbx.exe | C:\Users\admin\Documents\angelesthose.rtf.fun | binary | |
MD5:D76E4F89E3D70F6A196242E905D639F3 | SHA256:480B5DA380A5572E08723F51551843BF0308776FCE4193808FF45C834E84880F | |||
| 5772 | drpbx.exe | C:\Users\admin\Documents\surfacemountain.rtf.fun | binary | |
MD5:6893F7FC24C698489CAE591397098196 | SHA256:0837824B41FC074233EF90A1DBA06F924BC2CFC7A8AD1A8AFDBA017ECECF2C34 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
40
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6336 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3344 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
4288 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | binary | 409 b | unknown |
4288 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | binary | 418 b | unknown |
2344 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | binary | 1.11 Kb | unknown |
2344 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | binary | 1.05 Kb | unknown |
2344 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | binary | 824 b | unknown |
2344 | svchost.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | binary | 814 b | unknown |
2344 | svchost.exe | GET | 200 | 2.16.164.72:80 | http://crl.microsoft.com/pki/crl/products/MicWinPCA_2010-07-06.crl | unknown | binary | 552 b | unknown |
2152 | OfficeClickToRun.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3764 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3344 | svchost.exe | 20.190.159.64:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3344 | svchost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
6336 | backgroundTaskHost.exe | 20.105.99.58:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
6336 | backgroundTaskHost.exe | 192.229.221.95:80 | — | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4288 | SIHClient.exe | 40.127.169.103:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4288 | SIHClient.exe | 88.221.125.143:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
4288 | SIHClient.exe | 13.95.31.18:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |