| URL: | https://www.stamps.com/site/resources/stamps.exe |
| Full analysis: | https://app.any.run/tasks/a79abac3-b270-40a0-beb4-f4c0187d767e |
| Verdict: | Malicious activity |
| Analysis date: | August 17, 2020, 21:07:04 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A6C2FA203A3CBE848B42D2968B4B2983 |
| SHA1: | 9F11BC67F5B39F8E74979D125538006AAADBB050 |
| SHA256: | 9F354620E90850E8FEE9E5AFCE47B056D6B85D9B6A553A08F6788AA58624C010 |
| SSDEEP: | 3:N8DSLX2NMRbLWHwn:2OLXkQb6Hwn |
MALICIOUS
Loads dropped or rewritten executable
- stamps.exe (PID: 2344)
- regall.exe (PID: 3396)
- RegAsm.exe (PID: 1404)
- Launchipostage.exe (PID: 2212)
- WerFault.exe (PID: 2476)
- IPostage.exe (PID: 2520)
Application was dropped or rewritten from another process
- installworks.exe (PID: 2264)
- stamps.exe (PID: 2344)
- regall.exe (PID: 3396)
- Launchipostage.exe (PID: 2212)
- IPostage.exe (PID: 2520)
Changes the autorun value in the registry
- ie4uinit.exe (PID: 4004)
SUSPICIOUS
Executable content was dropped or overwritten
- stamps.exe (PID: 2344)
- stamps.exe (PID: 3784)
- msiexec.exe (PID: 2656)
Reads the Windows organization settings
- stamps.exe (PID: 2344)
Creates files in the Windows directory
- stamps.exe (PID: 2344)
- msiexec.exe (PID: 2656)
Reads Windows owner or organization settings
- stamps.exe (PID: 2344)
Changes IE settings (feature browser emulation)
- stamps.exe (PID: 2344)
Creates files in the program directory
- stamps.exe (PID: 3784)
- stamps.exe (PID: 2344)
- WerFault.exe (PID: 2476)
Removes files from Windows directory
- msiexec.exe (PID: 2656)
Modifies the open verb of a shell class
- msiexec.exe (PID: 2656)
- ie4uinit.exe (PID: 4004)
Creates COM task schedule object
- regall.exe (PID: 3396)
- RegAsm.exe (PID: 1404)
Creates a software uninstall entry
- stamps.exe (PID: 2344)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1720)
- iexplore.exe (PID: 588)
Changes internet zones settings
- iexplore.exe (PID: 1720)
Creates files in the user directory
- iexplore.exe (PID: 588)
- iexplore.exe (PID: 1720)
Application launched itself
- iexplore.exe (PID: 1720)
- msiexec.exe (PID: 2656)
Modifies the phishing filter of IE
- iexplore.exe (PID: 1720)
Changes settings of System certificates
- iexplore.exe (PID: 1720)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 588)
- stamps.exe (PID: 3784)
Reads settings of System Certificates
- iexplore.exe (PID: 1720)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1720)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3964)
- msiexec.exe (PID: 2656)
- MsiExec.exe (PID: 3160)
Creates a software uninstall entry
- msiexec.exe (PID: 2656)
Creates files in the program directory
- msiexec.exe (PID: 2656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
65
Monitored processes
16
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 588 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1720 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1404 | "C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe" "C:\Program Files\Stamps.com Internet Postage\DbApi.dll" /tlb:dbapi.tlb /codebase /nologo /silent | C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe | — | stamps.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 2.0.50727.5420 (Win7SP1.050727-5400) Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.stamps.com/site/resources/stamps.exe" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2064 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stamps.exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stamps.exe | — | iexplore.exe | |||||||||||
User: admin Company: Stamps.com, Inc. Integrity Level: MEDIUM Description: Stamps.com Installation Exit code: 3221226540 Version: 17.4.1.4142 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Stamps.com Internet Postage\Launchipostage.exe" | C:\Program Files\Stamps.com Internet Postage\Launchipostage.exe | — | stamps.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2264 | "C:\Program Files\Stamps.com Internet Postage\MSWorks\installworks.exe" -i | C:\Program Files\Stamps.com Internet Postage\MSWorks\installworks.exe | — | stamps.exe | |||||||||||
User: admin Company: Stamps.com Inc. Integrity Level: HIGH Description: Stamps.com MS Works Install and Uninstall utility Exit code: 0 Version: 17.4.1.4142 Modules
| |||||||||||||||
| 2344 | .\stamps.exe /m="C:\Users\admin\AppData\Local\MICROS~1\Windows\TEMPOR~1\Content.IE5\6Z2BCOUL\stamps.exe" /k="" | C:\ProgramData\mia7072.tmp\stamps.exe | stamps.exe | ||||||||||||
User: admin Company: Stamps.com, Inc. Integrity Level: HIGH Description: Stamps.com Installation Exit code: 0 Version: 17.4.1.4142 Modules
| |||||||||||||||
| 2476 | C:\Windows\system32\WerFault.exe -u -p 2520 -s 548 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
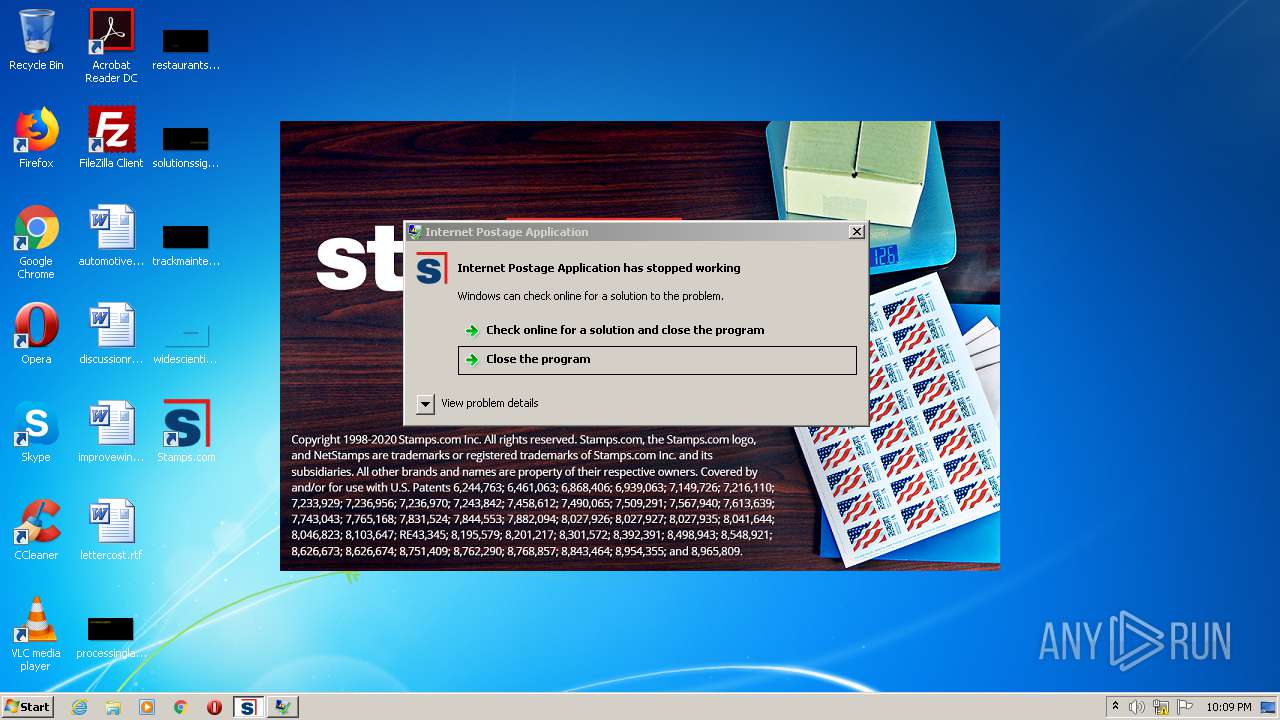
| 2520 | "C:\Program Files\Stamps.com Internet Postage\IPostage.exe" | C:\Program Files\Stamps.com Internet Postage\IPostage.exe | Launchipostage.exe | ||||||||||||
User: admin Company: Stamps.com Inc. Integrity Level: HIGH Description: Internet Postage Application Exit code: 3221225620 Version: 17.4.1.4142 Modules
| |||||||||||||||
| 2656 | C:\Windows\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
6 392
Read events
2 167
Write events
4 113
Delete events
112
Modification events
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 2032582886 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30831834 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1720) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
337
Suspicious files
78
Text files
972
Unknown types
95
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9227.tmp | — | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9228.tmp | — | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\stamps[1].exe | — | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stamps.exe.zl04v6u.partial | — | |
MD5:— | SHA256:— | |||
| 1720 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC6FDCA9DE3C0013F.TMP | — | |
MD5:— | SHA256:— | |||
| 1720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stamps.exe.zl04v6u.partial:Zone.Identifier | — | |
MD5:— | SHA256:— | |||
| 1720 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\stamps.exe | — | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\FC5A820A001B41D68902E051F36A5282_C8AB0CE7E5587E07F3C4BA771D0F5A79 | der | |
MD5:— | SHA256:— | |||
| 588 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
21
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
588 | iexplore.exe | GET | 200 | 143.204.208.165:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
588 | iexplore.exe | GET | 200 | 143.204.208.29:80 | http://crl.rootg2.amazontrust.com/rootg2.crl | US | der | 608 b | whitelisted |
1044 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAKXB1YM1Knrv%2BJy8eCW2II%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 143.204.208.127:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
588 | iexplore.exe | GET | 200 | 143.204.208.150:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEAkCM0AeT6chC1zrw4aVmWI%3D | US | der | 471 b | whitelisted |
588 | iexplore.exe | GET | 200 | 13.35.253.185:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
588 | iexplore.exe | GET | 200 | 13.35.253.148:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
1720 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1720 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
588 | iexplore.exe | 45.60.155.44:443 | www.stamps.com | — | US | unknown |
588 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
588 | iexplore.exe | 143.204.202.72:443 | resources.stamps.com | — | US | suspicious |
588 | iexplore.exe | 143.204.208.165:80 | o.ss2.us | — | US | malicious |
588 | iexplore.exe | 143.204.208.127:80 | o.ss2.us | — | US | malicious |
588 | iexplore.exe | 13.35.253.185:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
588 | iexplore.exe | 13.35.253.148:80 | ocsp.rootg2.amazontrust.com | — | US | whitelisted |
588 | iexplore.exe | 143.204.208.150:80 | ocsp.sca1b.amazontrust.com | — | US | whitelisted |
1044 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
588 | iexplore.exe | 143.204.208.29:80 | crl.rootg2.amazontrust.com | — | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.stamps.com |
| malicious |
ocsp.digicert.com |
| whitelisted |
resources.stamps.com |
| malicious |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.sca1b.amazontrust.com |
| whitelisted |
crl.rootg2.amazontrust.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |