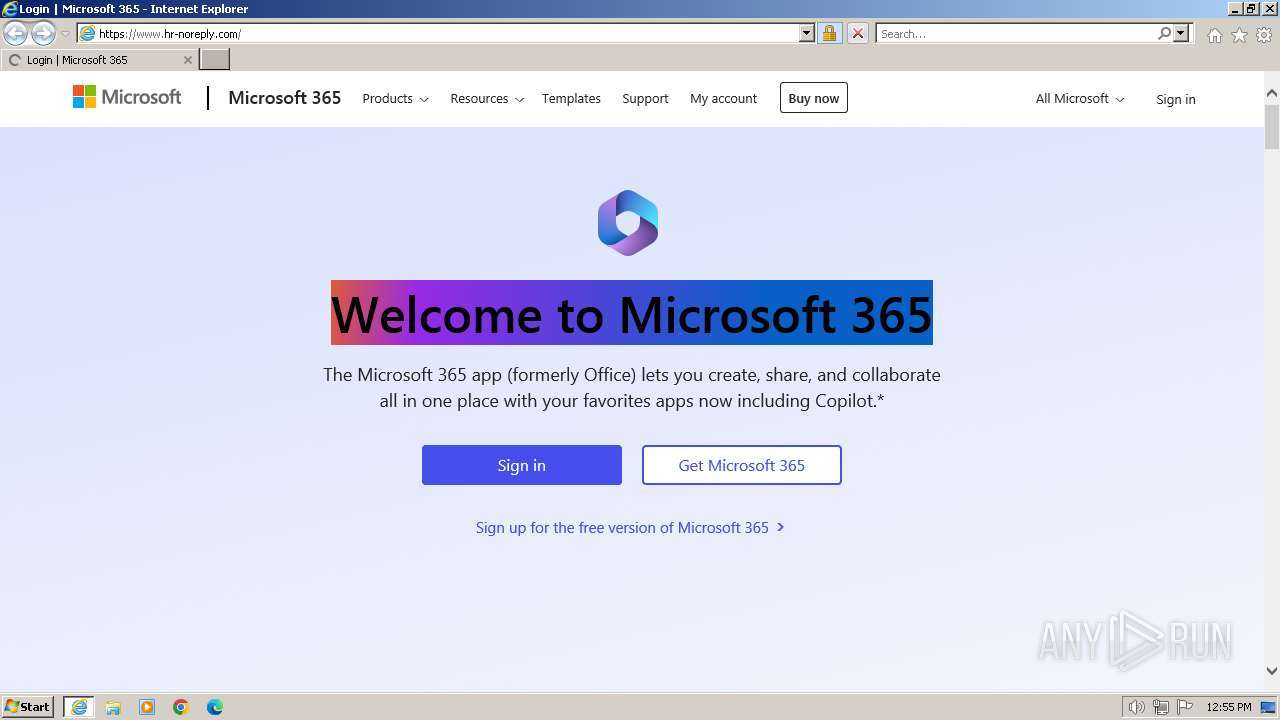
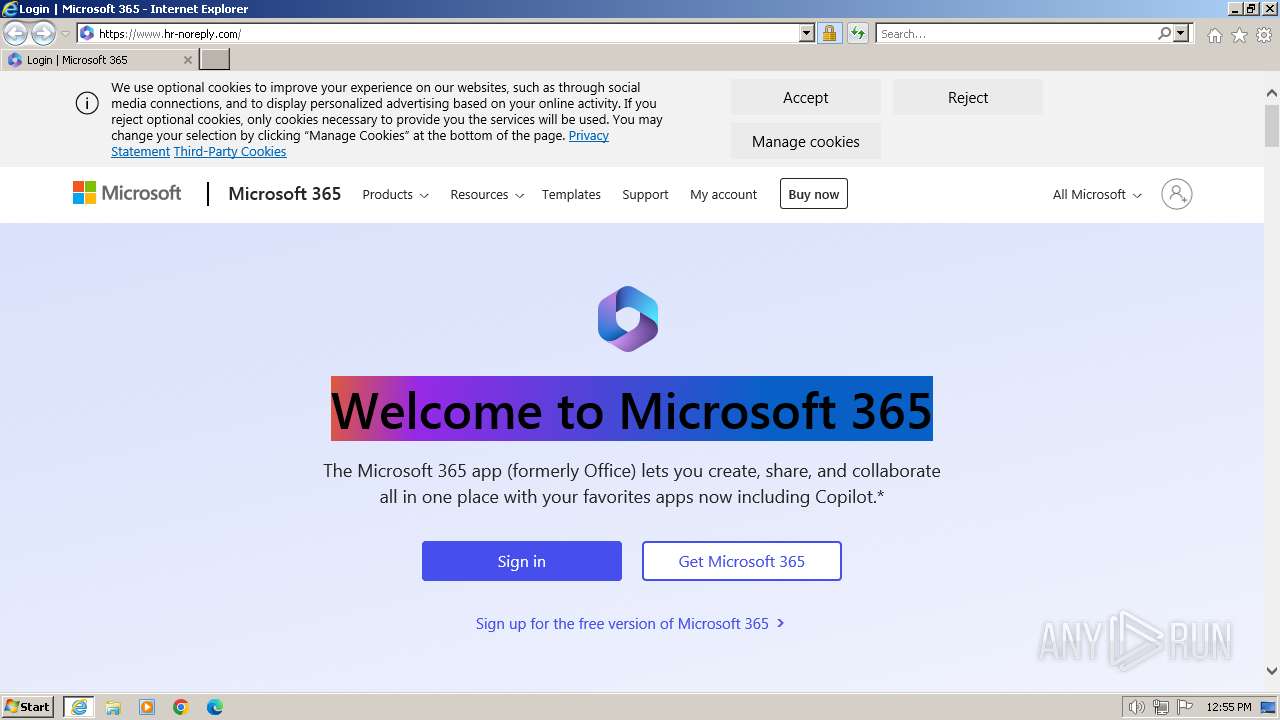
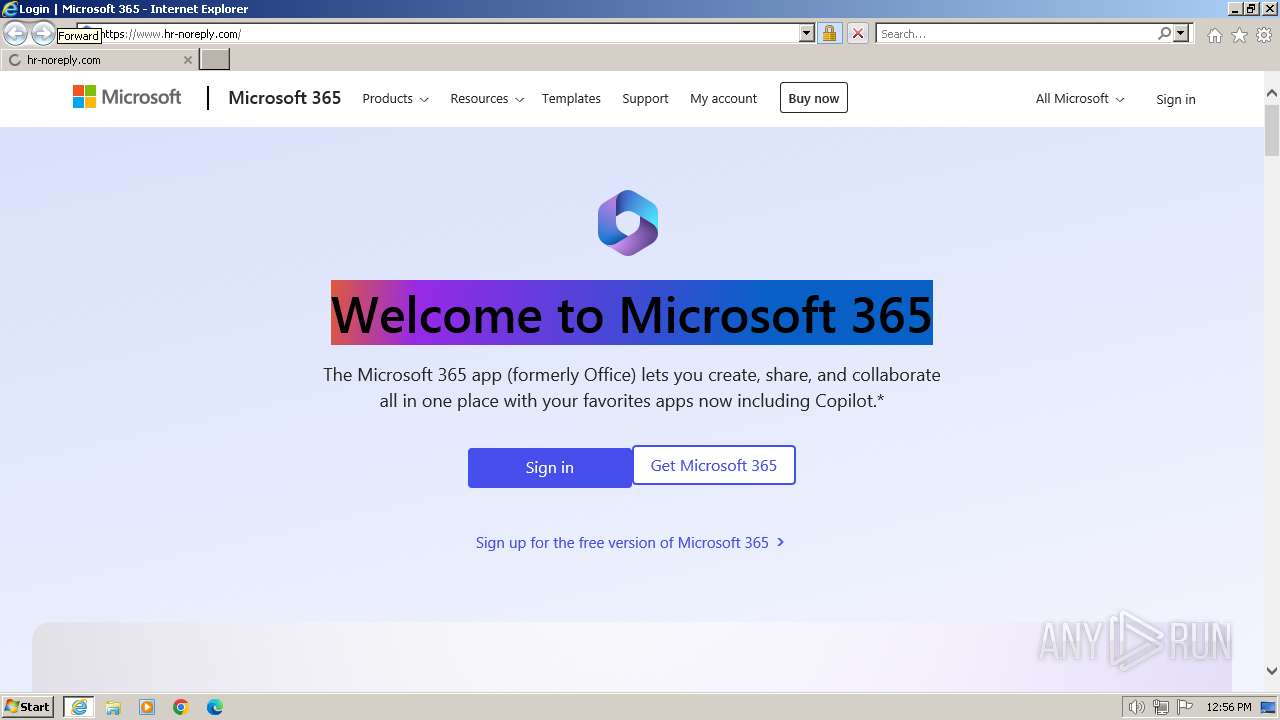
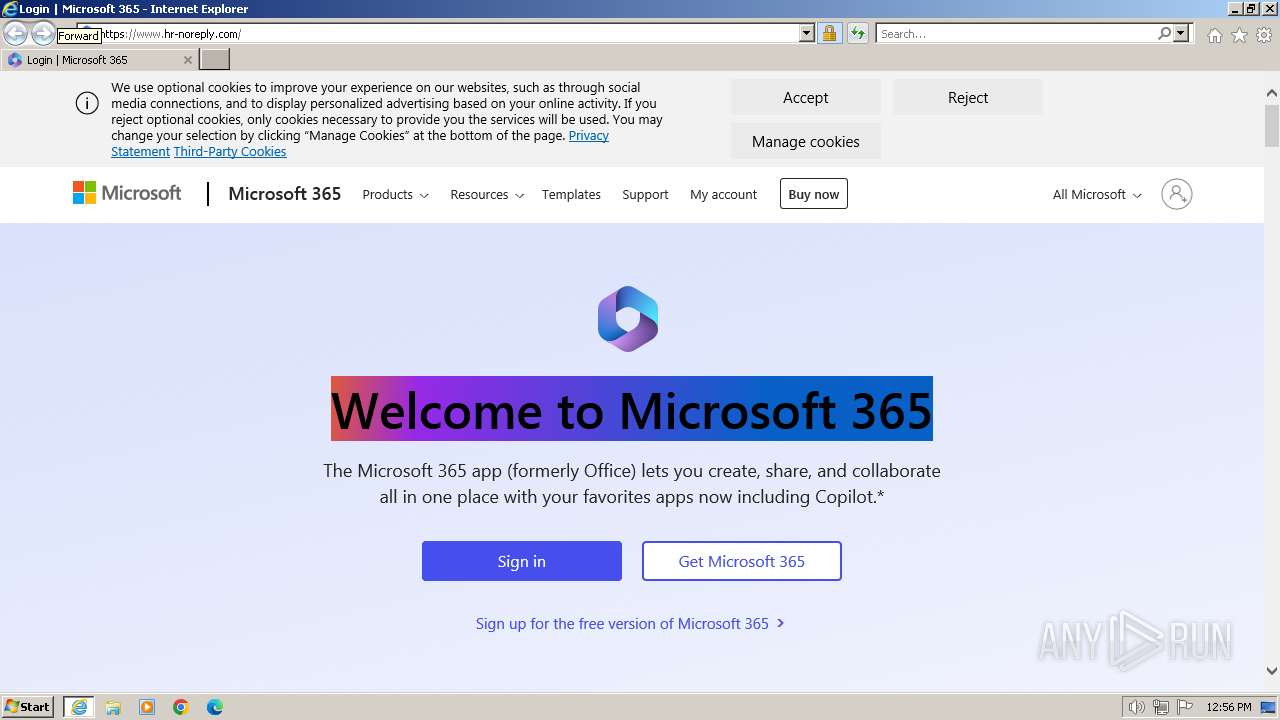
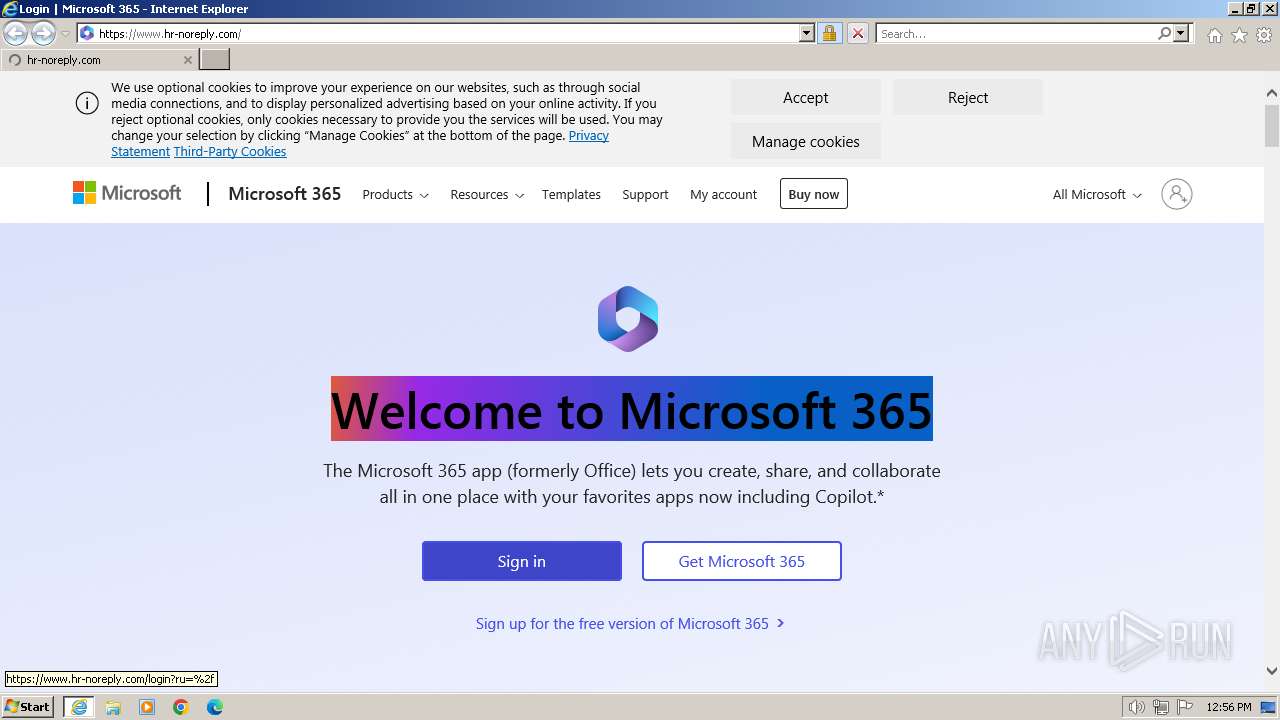
| URL: | https://www.hr-noreply.com/ |
| Full analysis: | https://app.any.run/tasks/b7684d52-c6e3-476e-8a5d-cd511ee67c75 |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2024, 11:55:24 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 12D999F8CCA487AA23069B4F149D3B94 |
| SHA1: | 3C558A6C4DFE36AD2ED805164D9FD3CBC363A47A |
| SHA256: | 9F2040ED7D85AEB3A2F32AEC7BFBD8775B2843308EE051A81F09DD7EF782C1B5 |
| SSDEEP: | 3:N8DSLy+AJ43:2OLnA+3 |
MALICIOUS
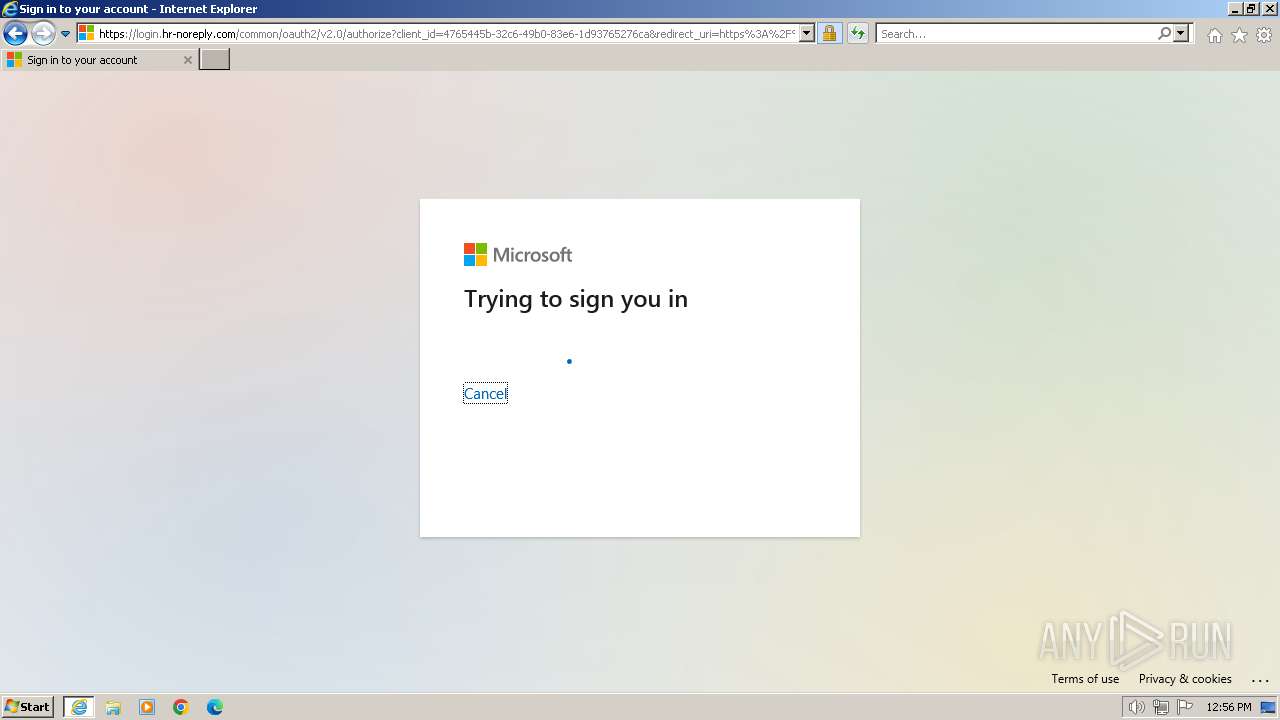
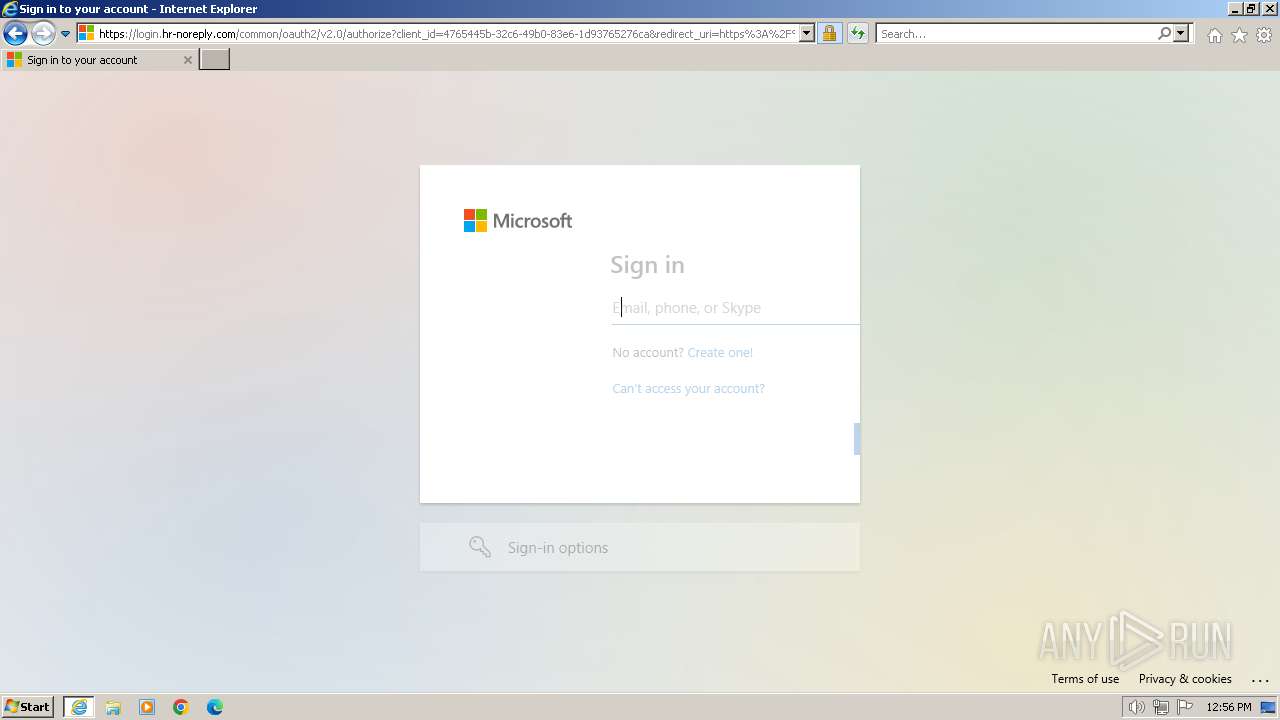
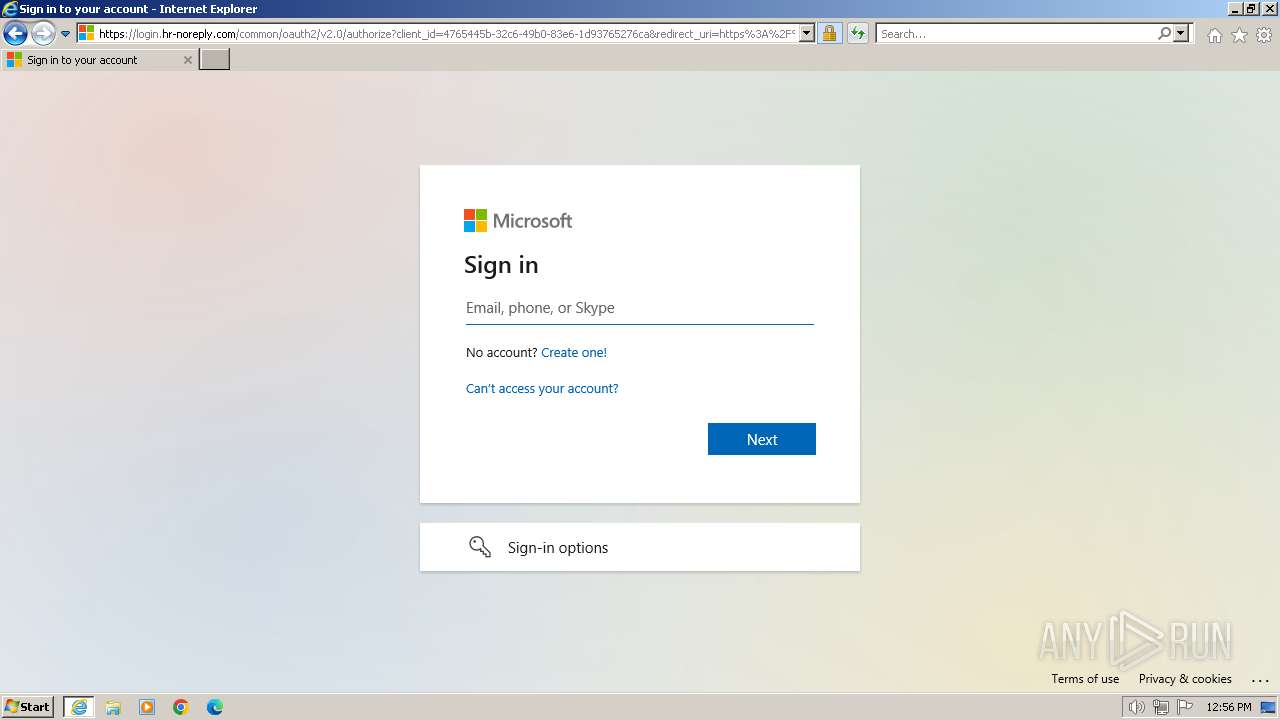
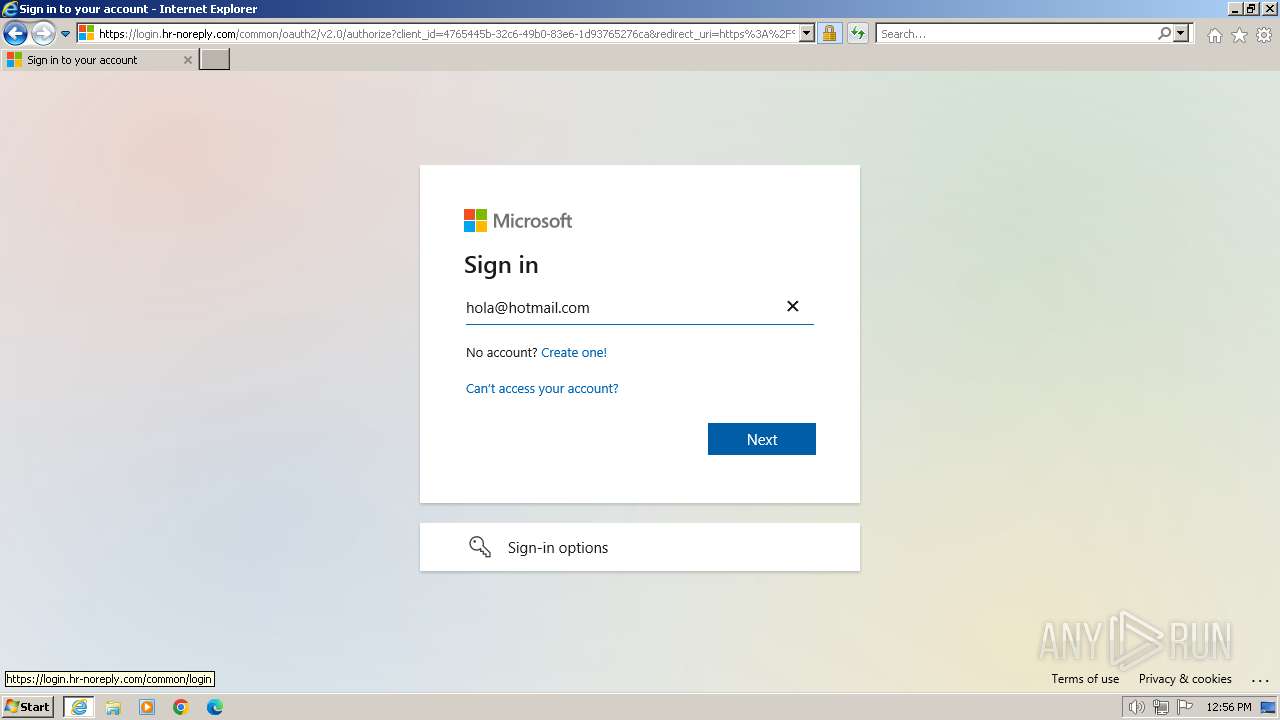
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 1060)
SUSPICIOUS
No suspicious indicators.INFO
Checks supported languages
- wmpnscfg.exe (PID: 2920)
Application launched itself
- iexplore.exe (PID: 3212)
Manual execution by a user
- wmpnscfg.exe (PID: 2920)
Reads the computer name
- wmpnscfg.exe (PID: 2920)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1060 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2920 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
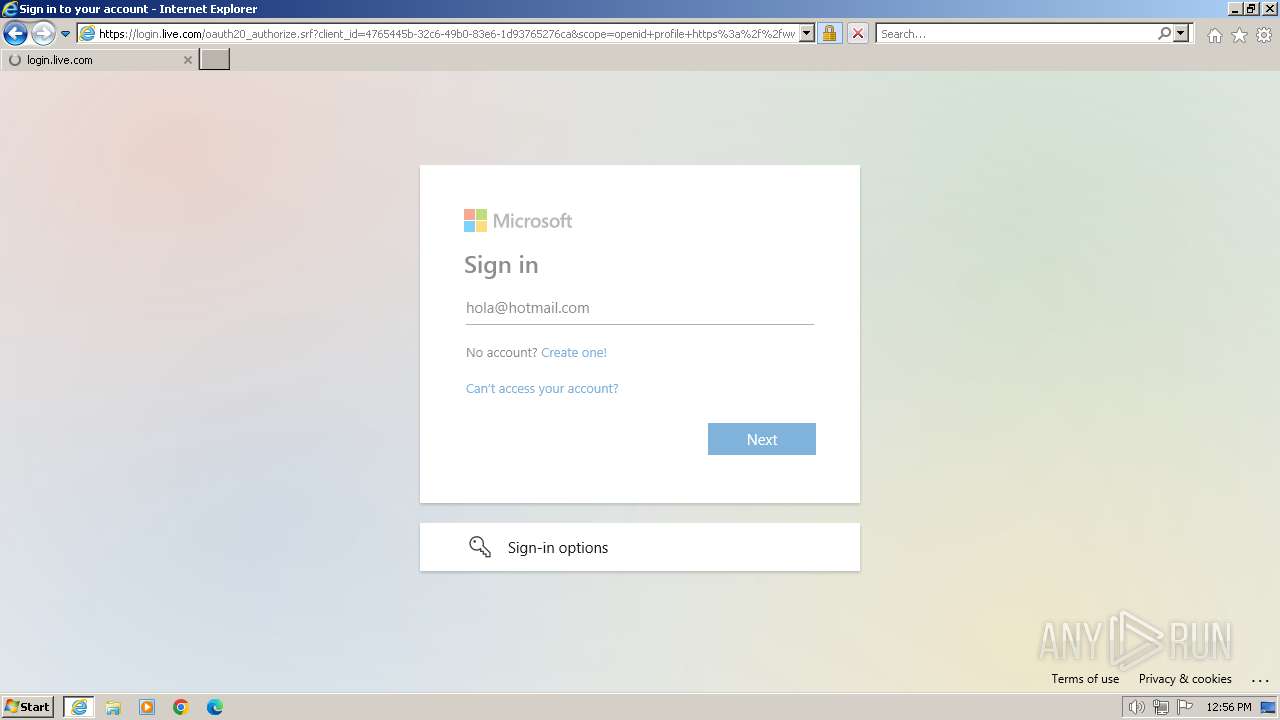
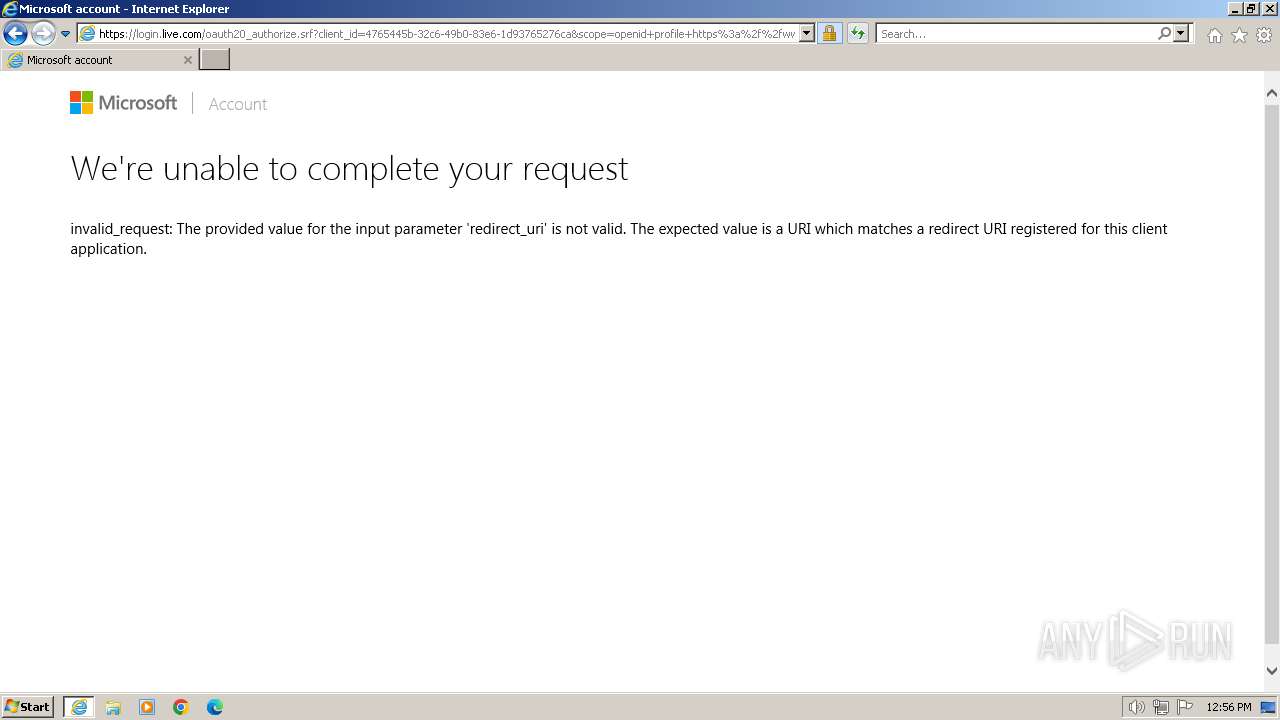
| 3212 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.hr-noreply.com/" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3396 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3212 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
23 273
Read events
23 032
Write events
137
Delete events
104
Modification events
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31139540 | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31139540 | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3212) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
55
Text files
66
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:75E09138EAAA9264C6B918B314B64518 | SHA256:36C6F6396967FAB3F94FC0FA818197C27802359D8DD8D406142E754153B14B7D | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\CabC62B.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:159DF1F7391F337F398FA222AF7ED8BB | SHA256:4CED644F9C3C33BA302816C39EE575A9413C15DFCBB40B283B2D81BB014CD41F | |||
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:60E163D84932DA0B3C4C95F1B62B416D | SHA256:E55937AA6C2B3C44A98EE04F0E3C4BEE532B36B2F327B7D339F129A65EED6A4D | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\TarC62D.tmp | binary | |
MD5:78785956AB4E54D6116D673C3491EDFF | SHA256:C514DBDBB13632CBB378C59086C1EBB0BC9B25FFB0A349F2B052B065C0D913E6 | |||
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:3CB9579A431435DEC97E20F21D54D66C | SHA256:6FC6B8116F614343AD471BDAAB2798B0E68E0E64E2060144B16B5228F0FDD0AC | |||
| 1060 | svchost.exe | C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\CabC62C.tmp | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\83D863F495E7D991917B3ABB3E1EB382_D68434B865CCAB38C4C17779495F8D80 | binary | |
MD5:187503A00D07FAF36BF4774C9E5F0700 | SHA256:4425182B77F9F439F46AACFBA424AA79C73A15570082AEFEB2F882889567A729 | |||
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:B51A34B2A0F62DF2579B658491034A47 | SHA256:48994F82409A33BDB76107CC373FD893A89D61D61F668B0222EB440837C2C0E8 | |||
| 3396 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\83D863F495E7D991917B3ABB3E1EB382_D68434B865CCAB38C4C17779495F8D80 | binary | |
MD5:EE984A086B0488E7A8C9CE2DC6C9747B | SHA256:BC096B088FCF985A9F491DDF66EEE268F216B90421D7FD75A927ABBE5A156449 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
63
DNS requests
31
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3396 | iexplore.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?dc0fe8ee60fd2676 | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3396 | iexplore.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?478efdca39ffb224 | unknown | — | — | whitelisted |
3396 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | whitelisted |
3396 | iexplore.exe | GET | 200 | 18.66.142.79:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
3396 | iexplore.exe | GET | 200 | 18.245.65.219:80 | http://ocsp.r2m03.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQqHI%2BsdmapawQncL1rpCEZZ8gTSAQUVdkYX9IczAHhWLS%2Bq9lVQgHXLgICEAPpmCf29JqBnERzAvfaPdg%3D | unknown | — | — | unknown |
3396 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3396 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3212 | iexplore.exe | GET | 304 | 23.50.131.216:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?75c895dbbeaca3ce | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?98791cd21e713d78 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
3396 | iexplore.exe | 13.224.189.22:443 | www.hr-noreply.com | AMAZON-02 | US | unknown |
3396 | iexplore.exe | 23.50.131.216:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3396 | iexplore.exe | 18.66.142.79:80 | ocsp.rootg2.amazontrust.com | AMAZON-02 | US | shared |
3396 | iexplore.exe | 18.245.65.219:80 | ocsp.r2m03.amazontrust.com | — | US | unknown |
3396 | iexplore.exe | 23.35.229.160:443 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3396 | iexplore.exe | 23.207.210.157:443 | res.cdn.office.net | Akamai International B.V. | DE | whitelisted |
3396 | iexplore.exe | 184.24.77.23:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.hr-noreply.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
ocsp.r2m03.amazontrust.com |
| unknown |
res.cdn.office.net |
| whitelisted |
www.microsoft.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1060 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .hr-noreply .com) |
1060 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Phishing domain by CrossDomain ( .hr-noreply .com) |
1060 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Request to Azure content delivery network (aadcdn .msauth .net) |