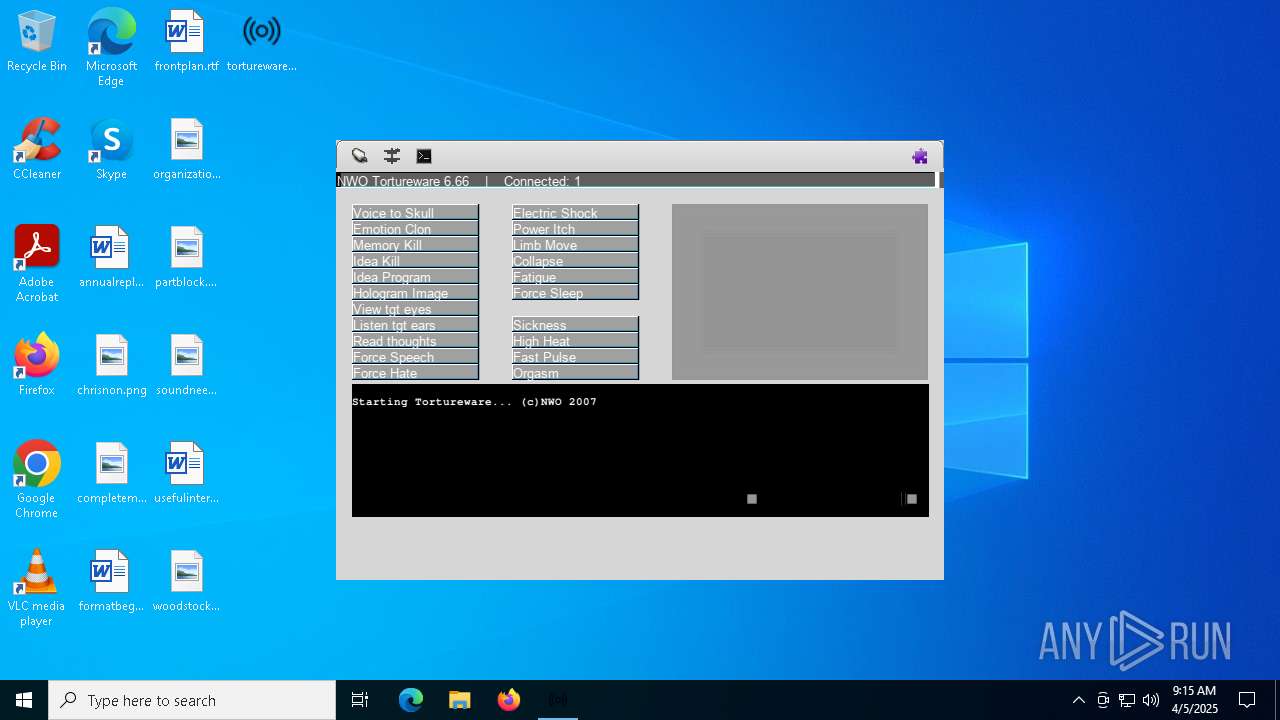
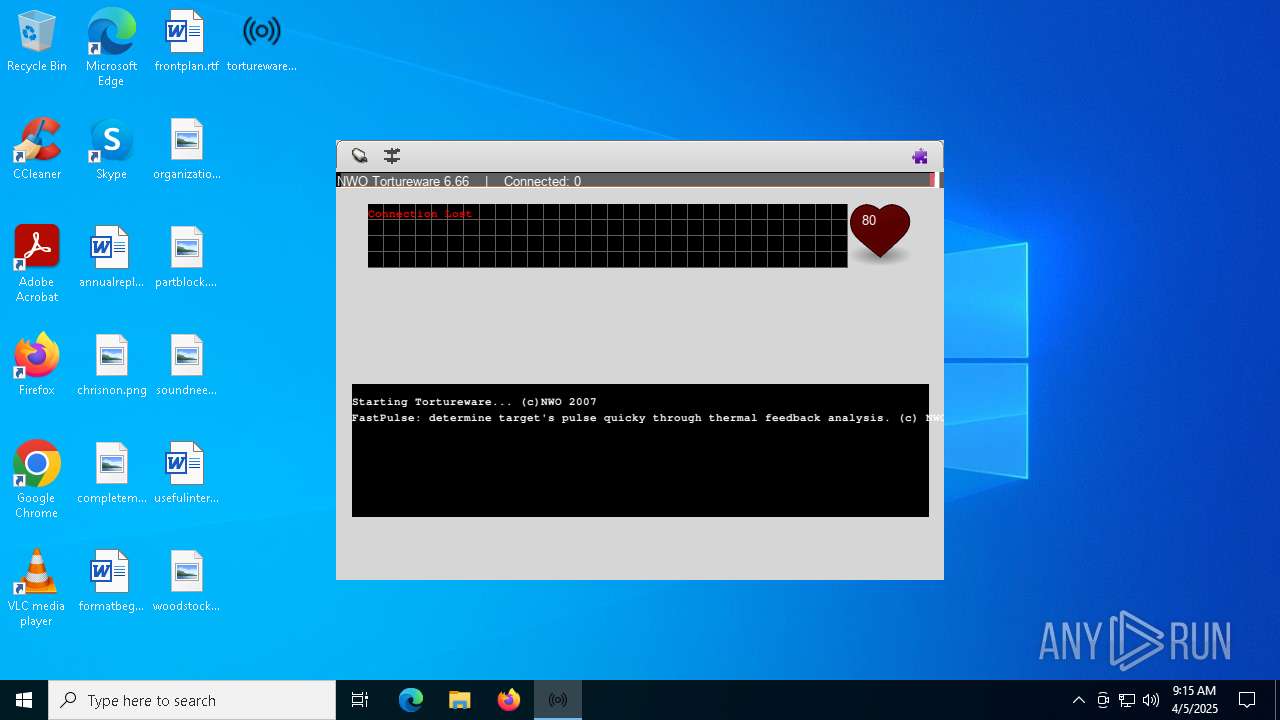
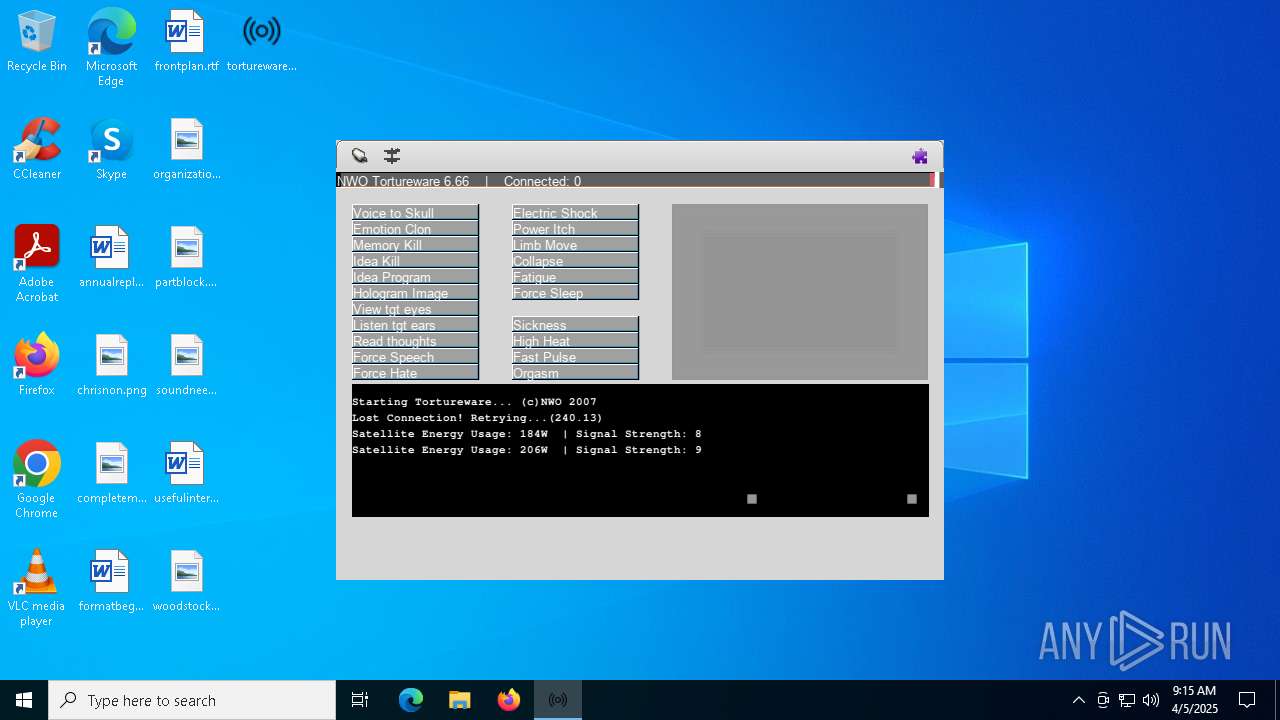
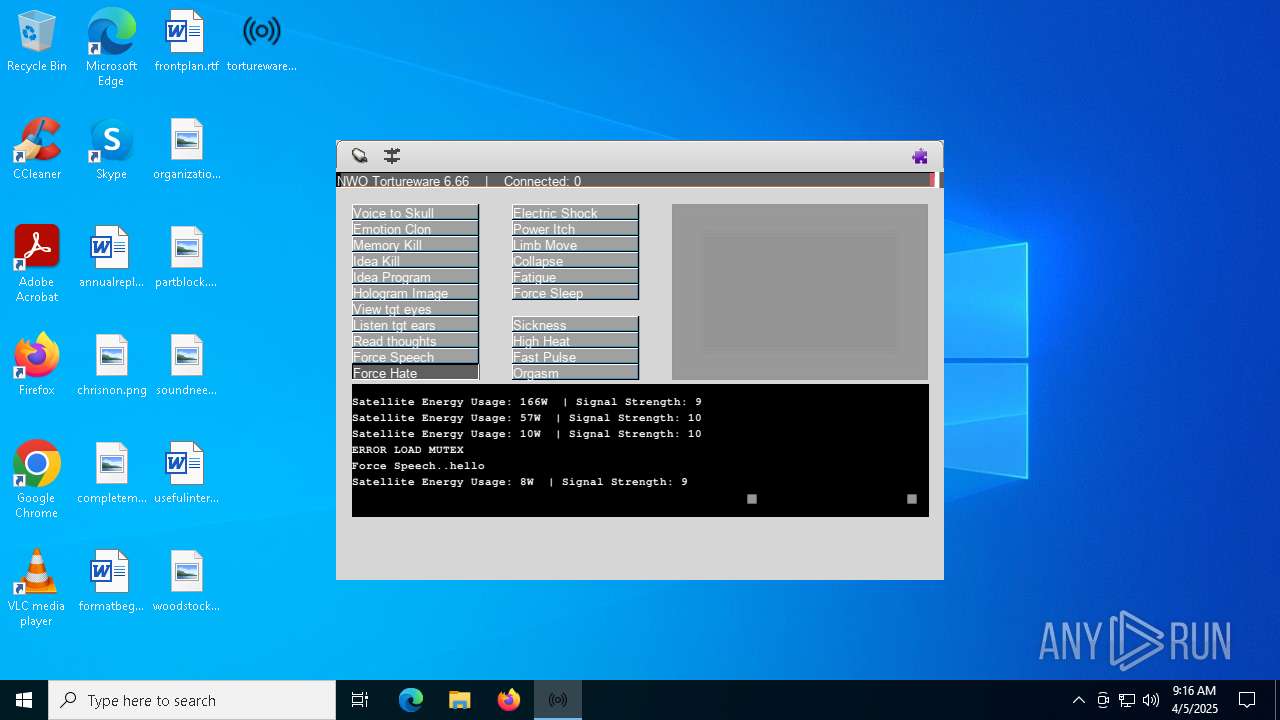
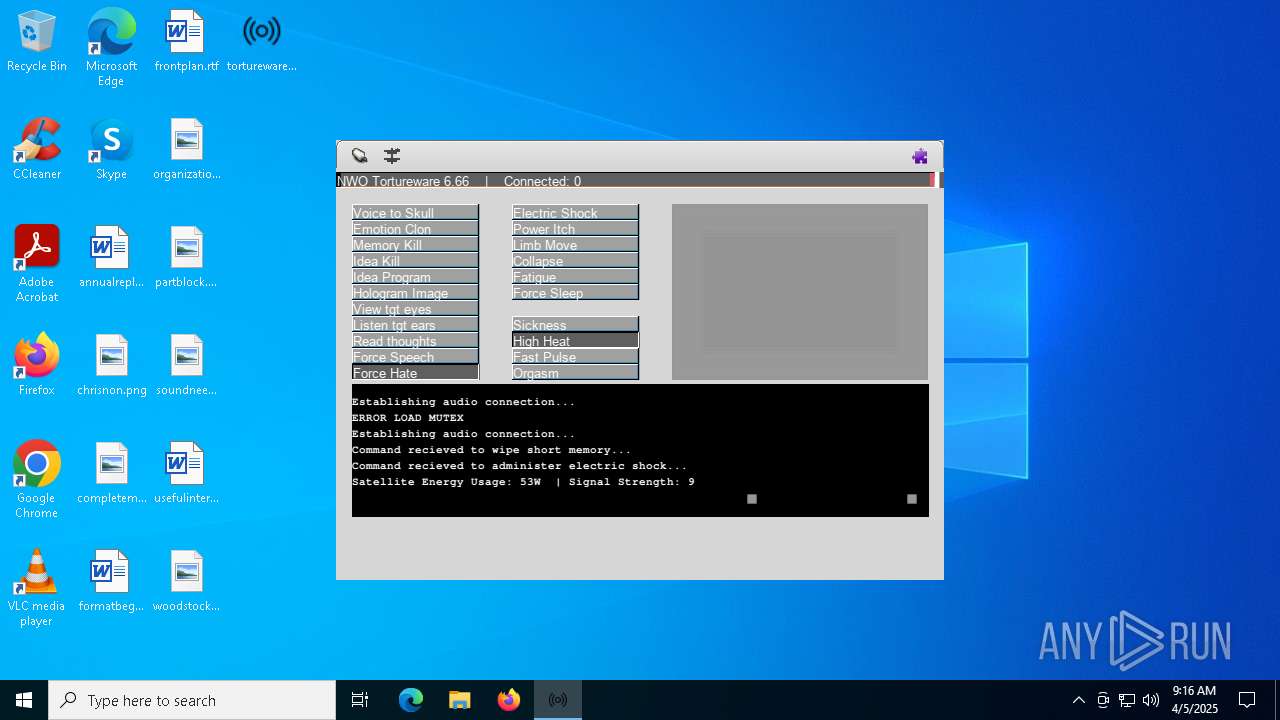
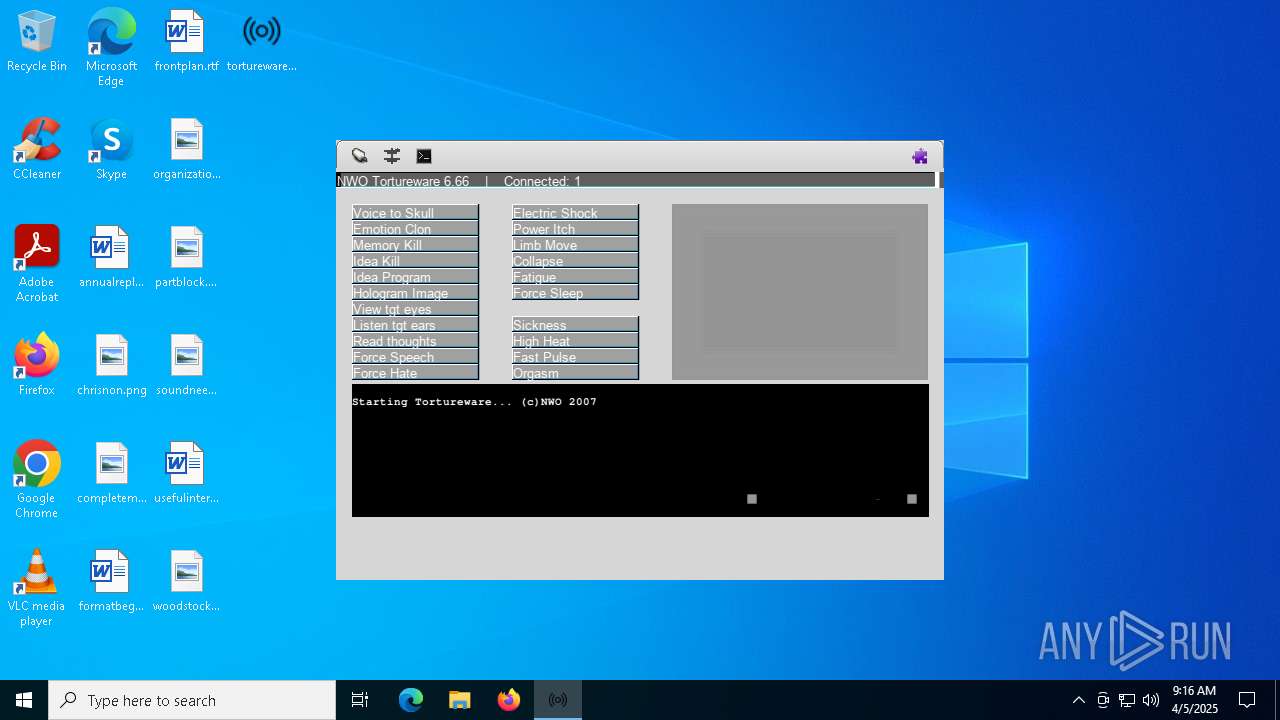
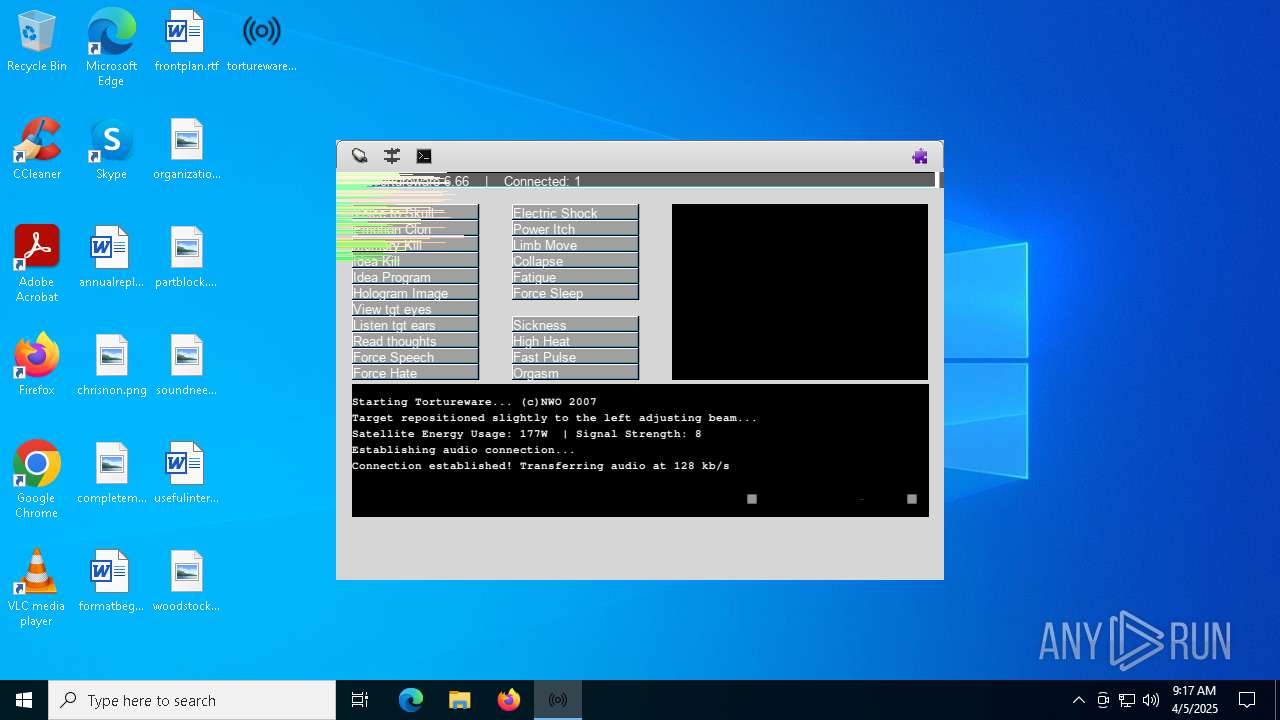
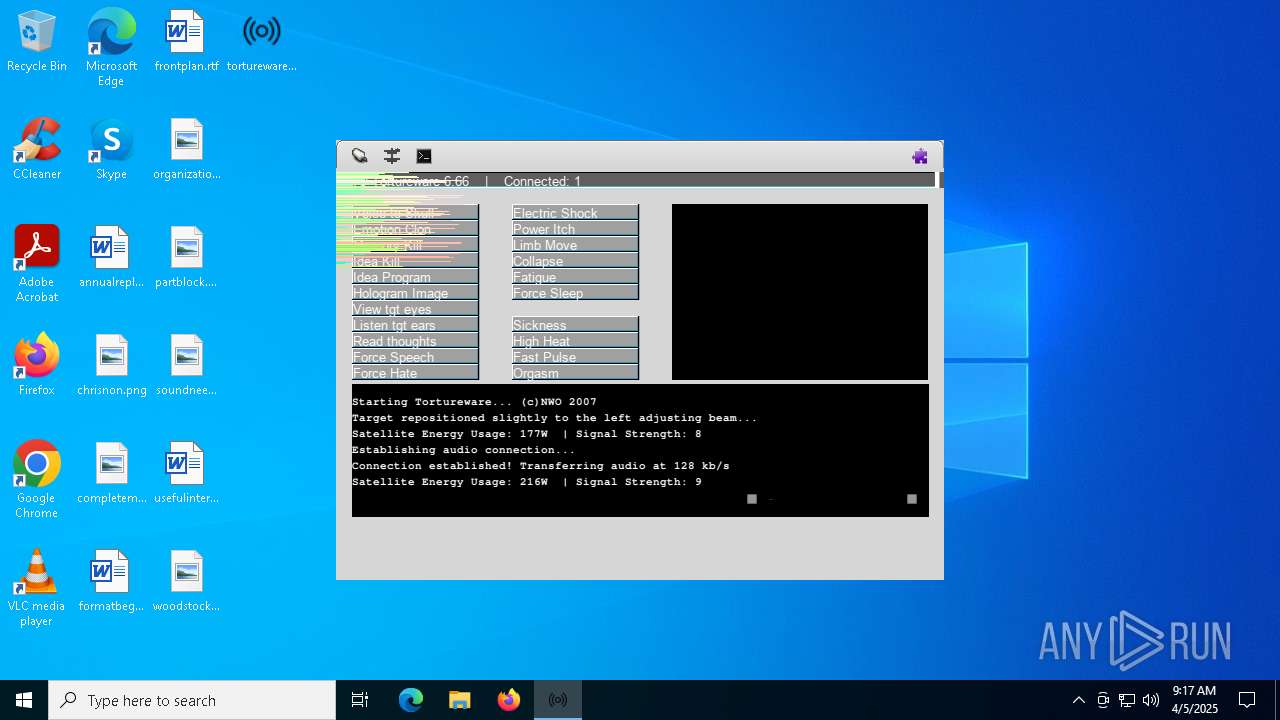
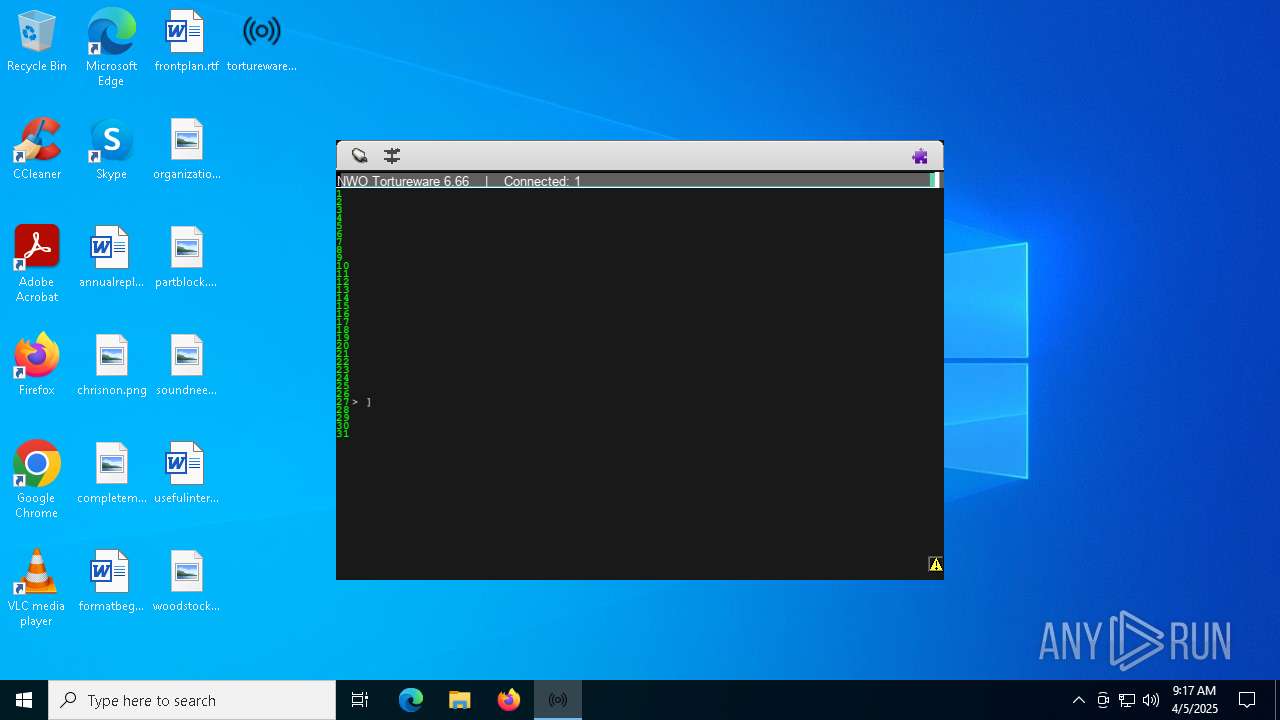
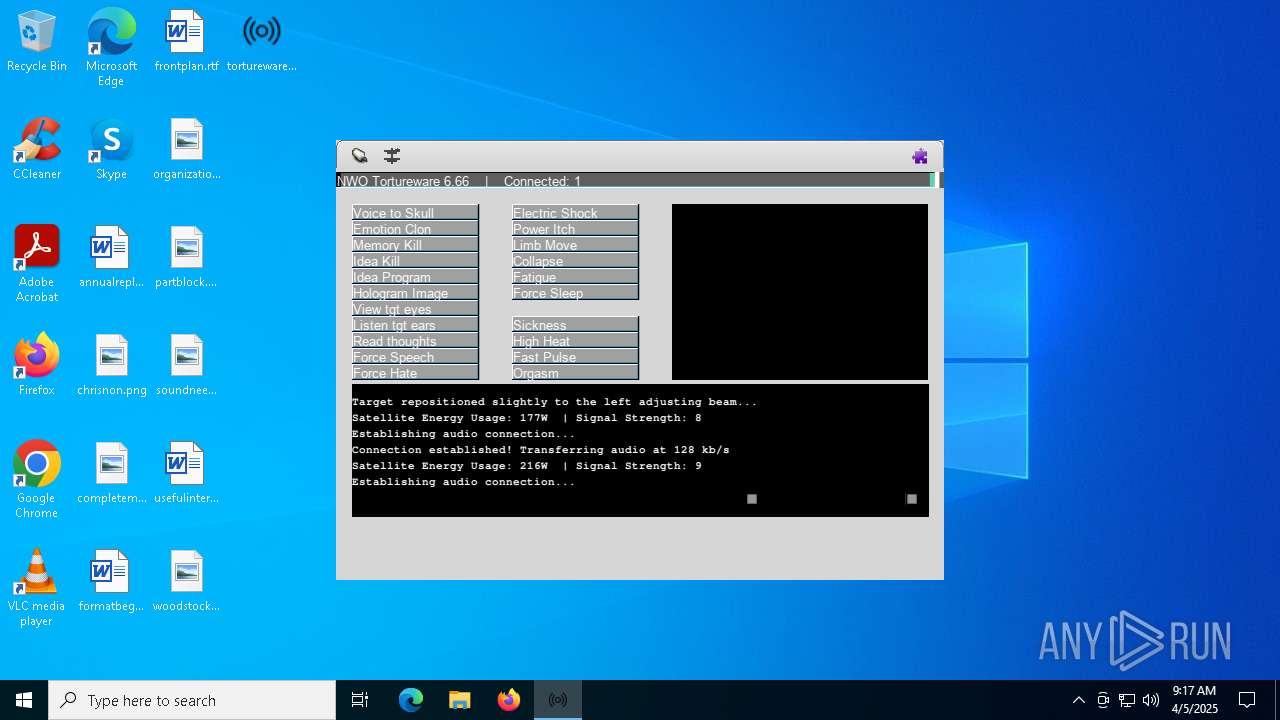
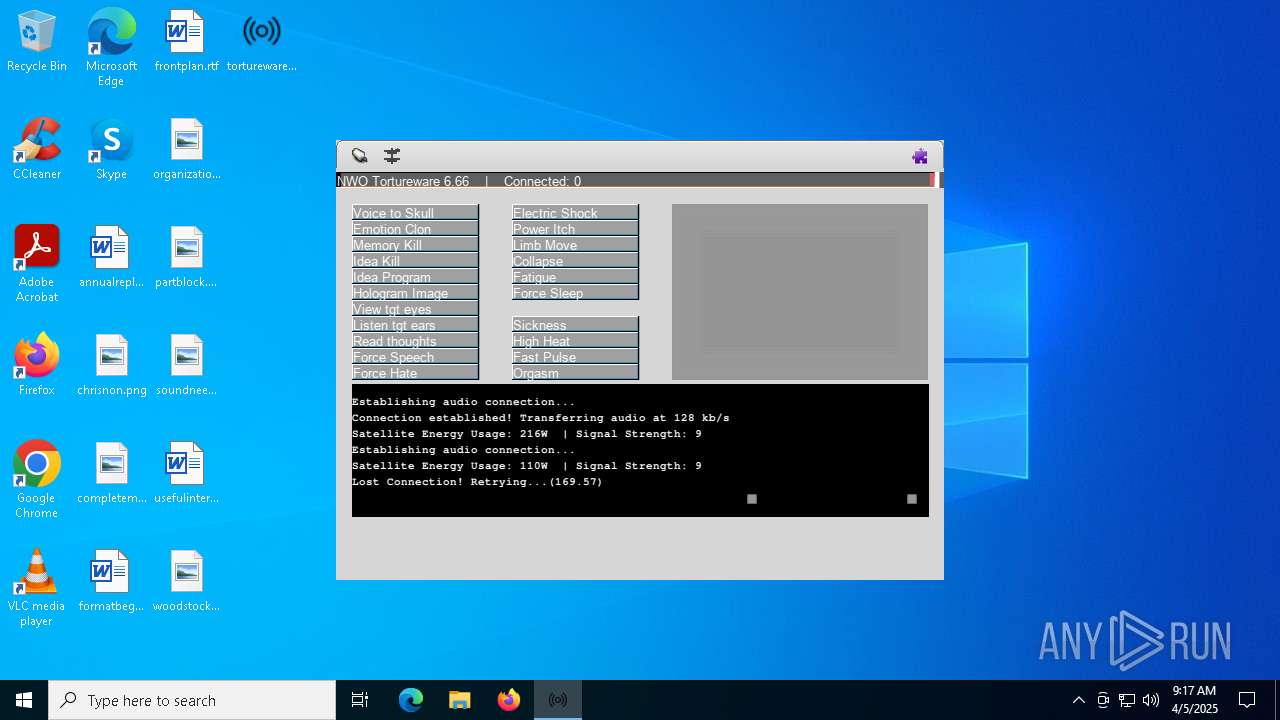
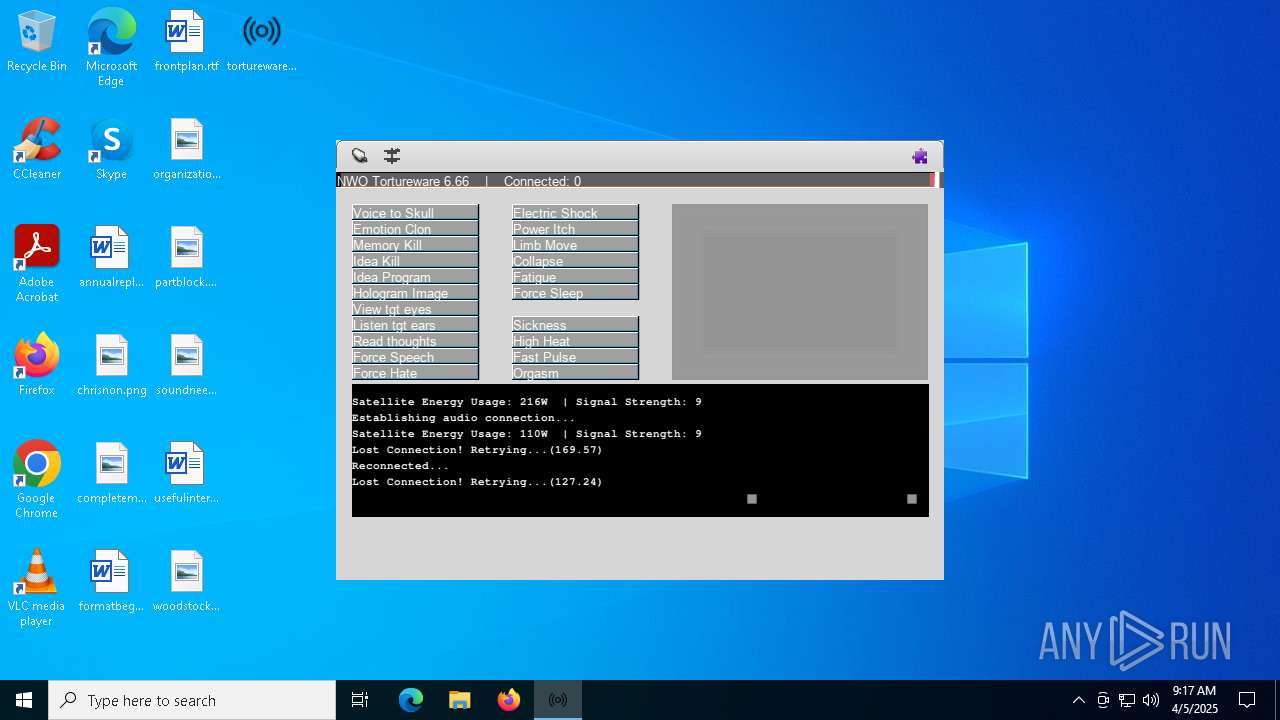
| File name: | tortureware.exe |
| Full analysis: | https://app.any.run/tasks/1097ed4a-42d0-4085-8be6-7587eb12ad53 |
| Verdict: | Malicious activity |
| Analysis date: | April 05, 2025, 09:14:33 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | 7310A1B5DA166B665BC58C9F9073168A |
| SHA1: | 0F79DCE98086499164E063860E7E7C2726D40A4A |
| SHA256: | 9F0973EA84F1A0C96D68D667BD5F72F4D62EB30991AB6A702F8DD2532A2EB5E9 |
| SSDEEP: | 98304:bHVEmQXW9aAXNlZG7GN0ht9DyibyKWLpBcaTz8ClbZQ7e8V3alJlS3o1f6ba/2rJ:10CTSp |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes as Windows Service
- VSSVC.exe (PID: 5892)
Executable content was dropped or overwritten
- tortureware.exe (PID: 4208)
- TiWorker.exe (PID: 3888)
- tortureware.exe (PID: 4000)
There is functionality for taking screenshot (YARA)
- tortureware.exe (PID: 4208)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 4724)
- tortureware.exe (PID: 4000)
- tortureware.exe (PID: 4208)
Process drops legitimate windows executable
- TiWorker.exe (PID: 3888)
Searches for installed software
- TiWorker.exe (PID: 3888)
INFO
Checks supported languages
- tortureware.exe (PID: 4208)
- ShellExperienceHost.exe (PID: 4724)
- tortureware.exe (PID: 4000)
UPX packer has been detected
- tortureware.exe (PID: 4208)
Manages system restore points
- SrTasks.exe (PID: 6940)
Reads the software policy settings
- TiWorker.exe (PID: 3888)
- slui.exe (PID: 4040)
- slui.exe (PID: 6656)
The sample compiled with english language support
- TiWorker.exe (PID: 3888)
- tortureware.exe (PID: 4208)
Create files in a temporary directory
- tortureware.exe (PID: 4208)
- tortureware.exe (PID: 4000)
Reads the machine GUID from the registry
- tortureware.exe (PID: 4208)
- tortureware.exe (PID: 4000)
Compiled with Borland Delphi (YARA)
- tortureware.exe (PID: 4208)
Manual execution by a user
- tortureware.exe (PID: 4000)
Reads the computer name
- tortureware.exe (PID: 4208)
- ShellExperienceHost.exe (PID: 4724)
- tortureware.exe (PID: 4000)
Checks proxy server information
- tortureware.exe (PID: 4208)
- slui.exe (PID: 6656)
- tortureware.exe (PID: 4000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic Win/DOS Executable (50) |
|---|---|---|
| .exe | | | DOS Executable Generic (49.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 663552 |
| InitializedDataSize: | 20480 |
| UninitializedDataSize: | 2899968 |
| EntryPoint: | 0x366d60 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.6.6.0 |
| ProductVersionNumber: | 6.6.6.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | NWO |
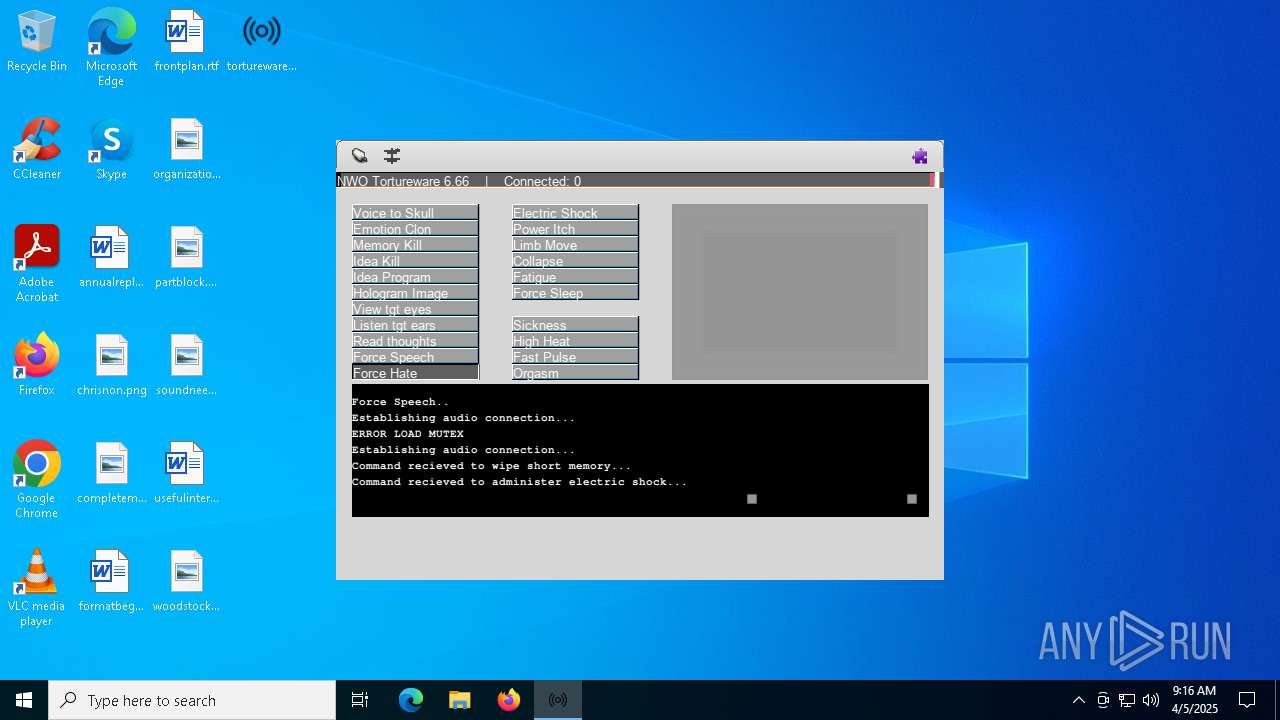
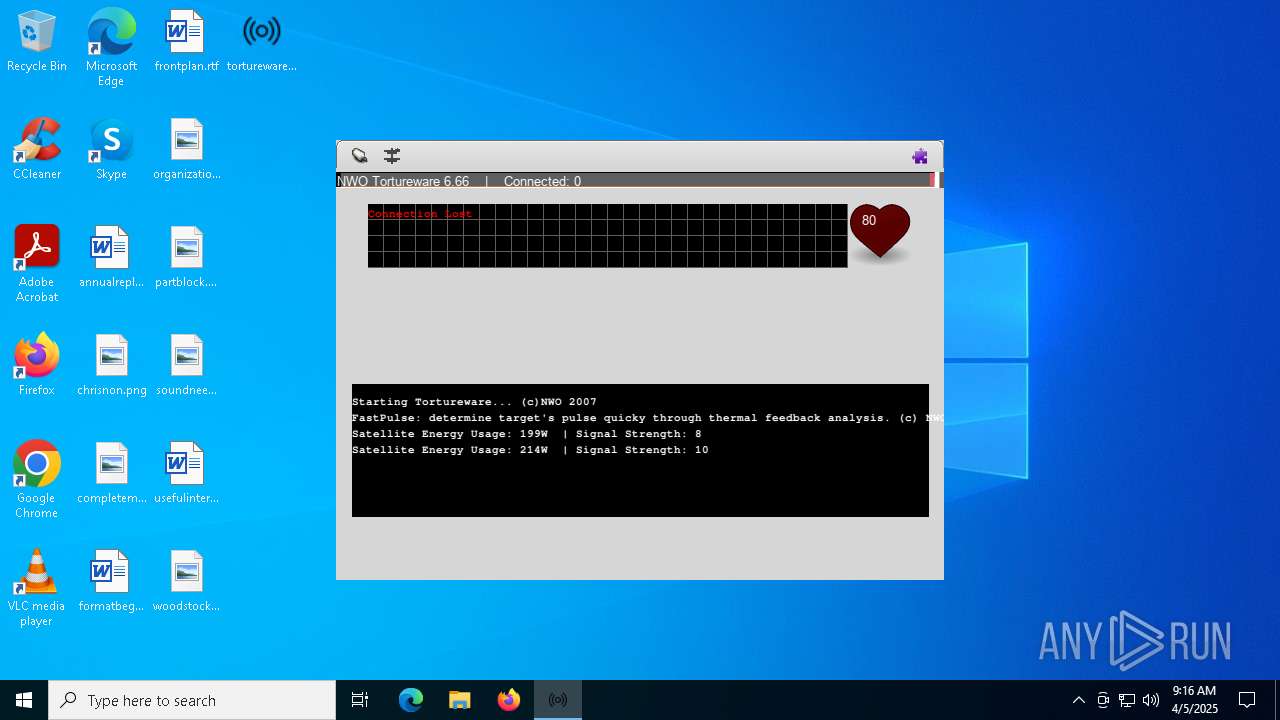
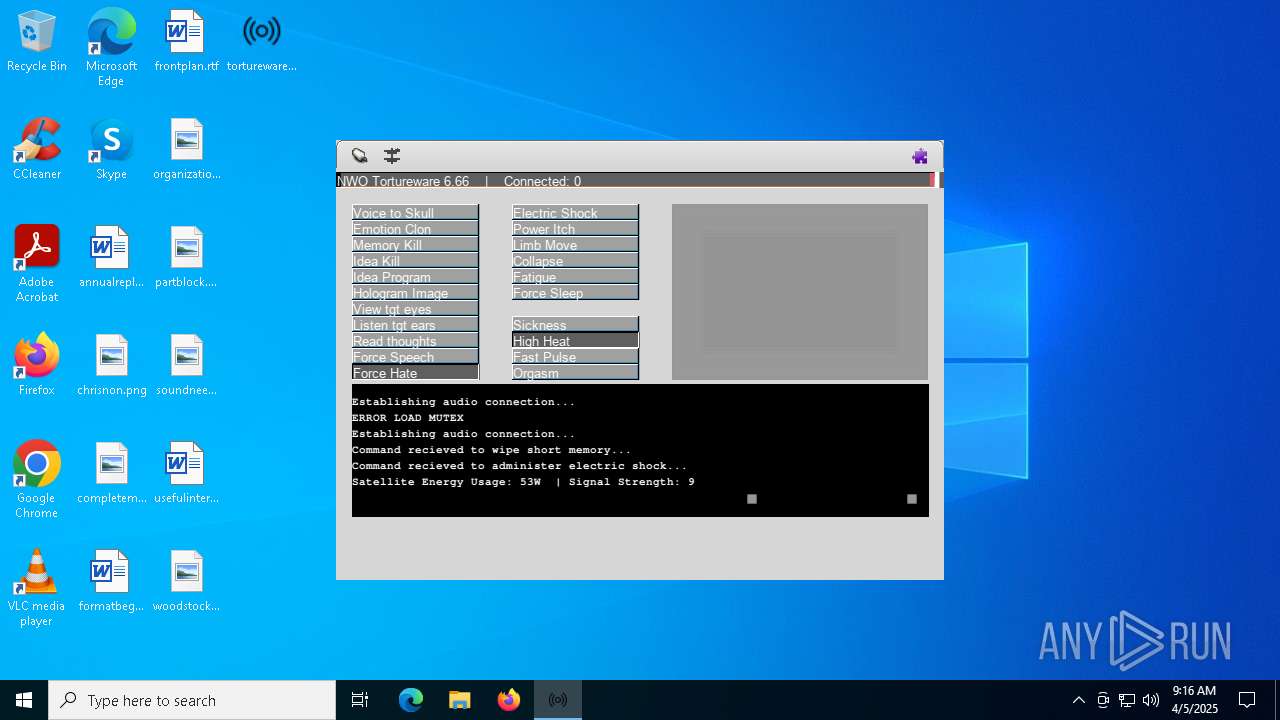
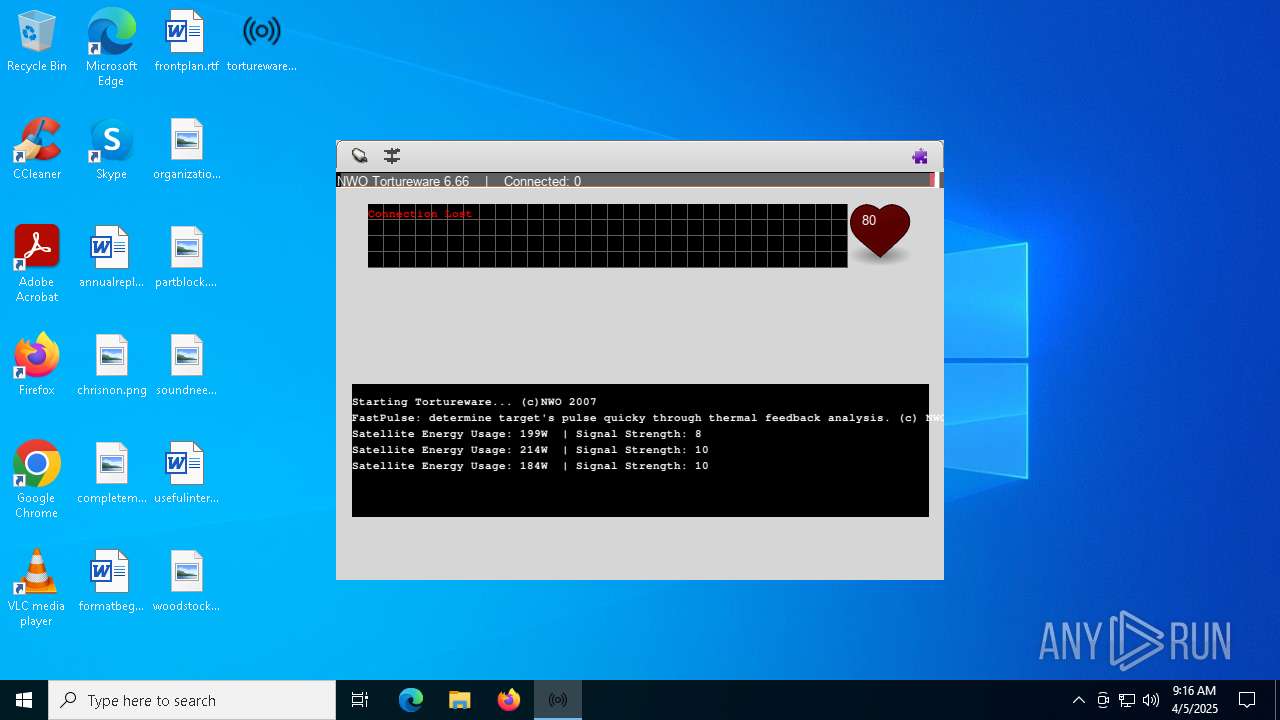
| FileDescription: | A robust software solution for targeting individuals. |
| FileVersion: | 6.6.6.0 |
| InternalName: | - |
| LegalCopyright: | - |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Tortureware 6.66 |
| ProductVersion: | 6.6.6.0 |
| Comments: | - |
Total processes
149
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3888 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Exit code: 0 Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4000 | "C:\Users\admin\Desktop\tortureware.exe" | C:\Users\admin\Desktop\tortureware.exe | explorer.exe | ||||||||||||
User: admin Company: NWO Integrity Level: MEDIUM Description: A robust software solution for targeting individuals. Exit code: 0 Version: 6.6.6.0 Modules
| |||||||||||||||
| 4040 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4208 | "C:\Users\admin\Desktop\tortureware.exe" | C:\Users\admin\Desktop\tortureware.exe | explorer.exe | ||||||||||||
User: admin Company: NWO Integrity Level: MEDIUM Description: A robust software solution for targeting individuals. Exit code: 0 Version: 6.6.6.0 Modules
| |||||||||||||||
| 4724 | "C:\WINDOWS\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe" -ServerName:App.AppXtk181tbxbce2qsex02s8tw7hfxa9xb3t.mca | C:\Windows\SystemApps\ShellExperienceHost_cw5n1h2txyewy\ShellExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shell Experience Host Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5588 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6656 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6940 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | TiWorker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
28 755
Read events
28 289
Write events
380
Delete events
86
Modification events
| (PID) Process: | (4208) tortureware.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: tortureware.exe | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31172107 | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 689703571 | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: 788972772 | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingRequired |
Value: | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PoqexecFailure |
Value: | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | ExecutionState |
Value: | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | RepairTransactionPended |
Value: | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqTime |
Value: 0 | |||
| (PID) Process: | (3888) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqCount |
Value: 0 | |||
Executable files
46
Suspicious files
37
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3888 | TiWorker.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3888 | TiWorker.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{0389c0bb-6a48-4b47-87a0-e493073f64cd}_OnDiskSnapshotProp | binary | |
MD5:EEA704B386D12F5CED6062384DA133BB | SHA256:623895E51B580C71637704662DBC4E64BAB9462101D9ED0017C725255A7C2976 | |||
| 3888 | TiWorker.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:EEA704B386D12F5CED6062384DA133BB | SHA256:623895E51B580C71637704662DBC4E64BAB9462101D9ED0017C725255A7C2976 | |||
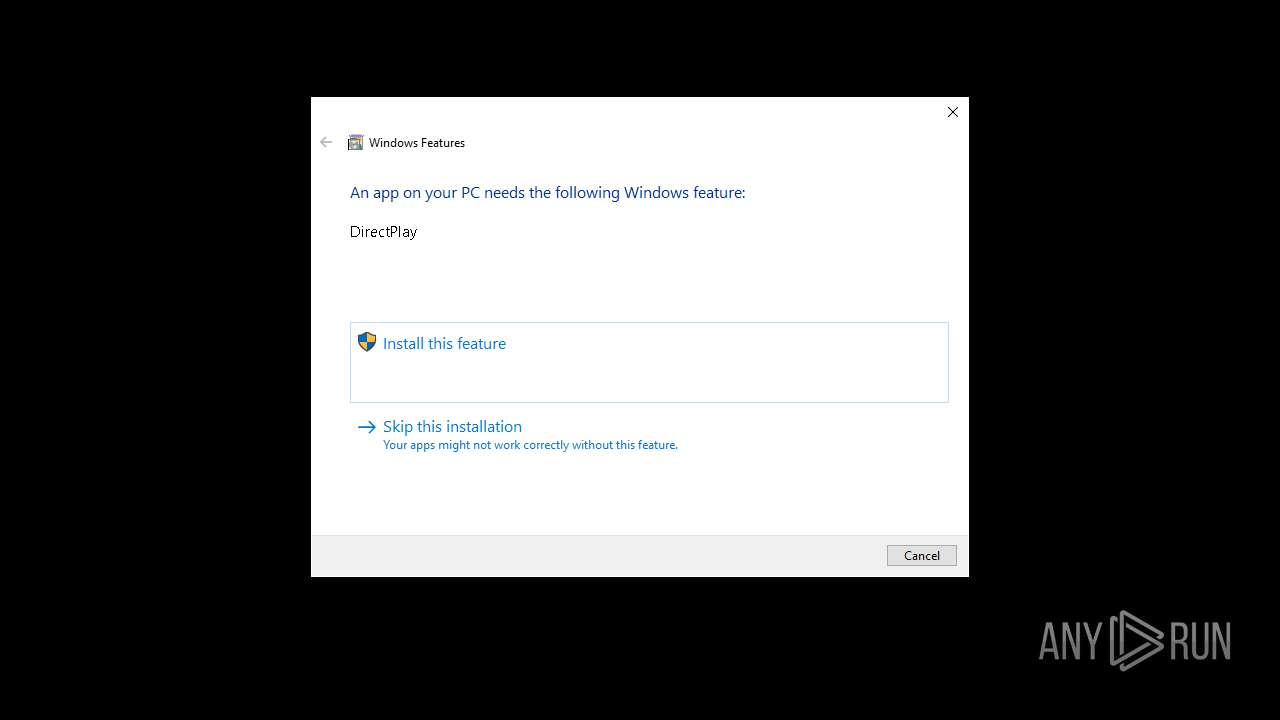
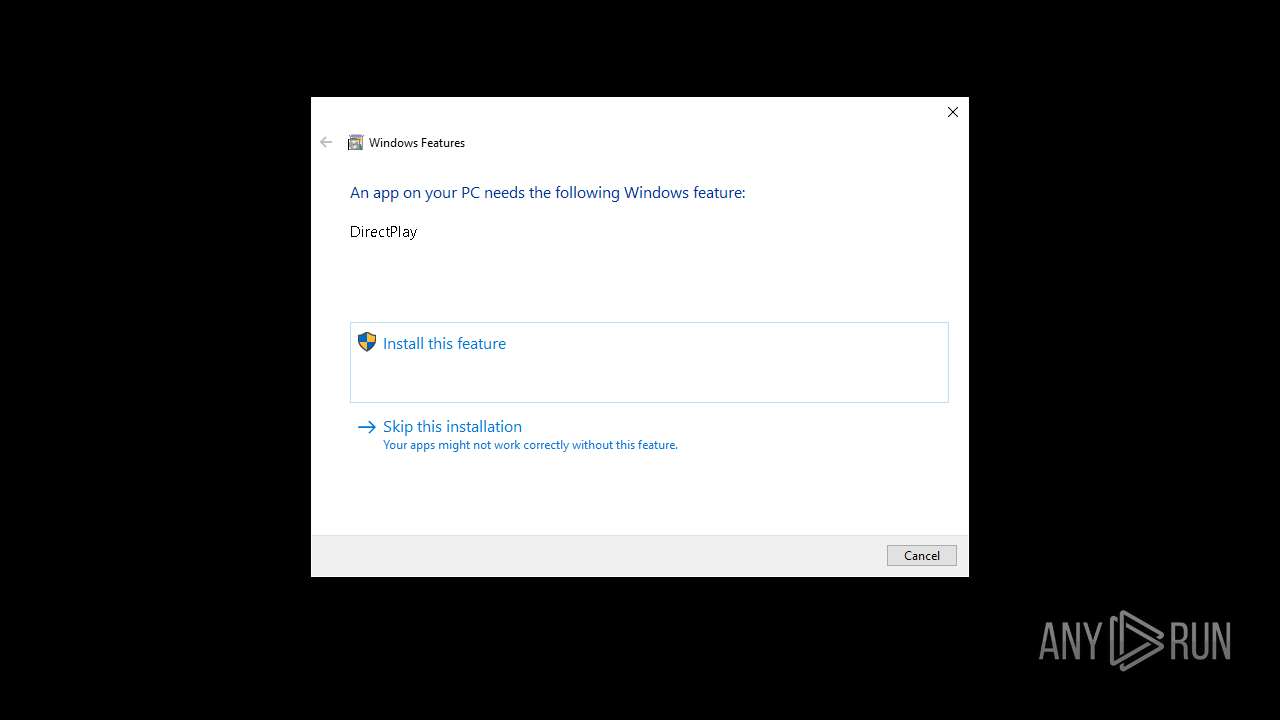
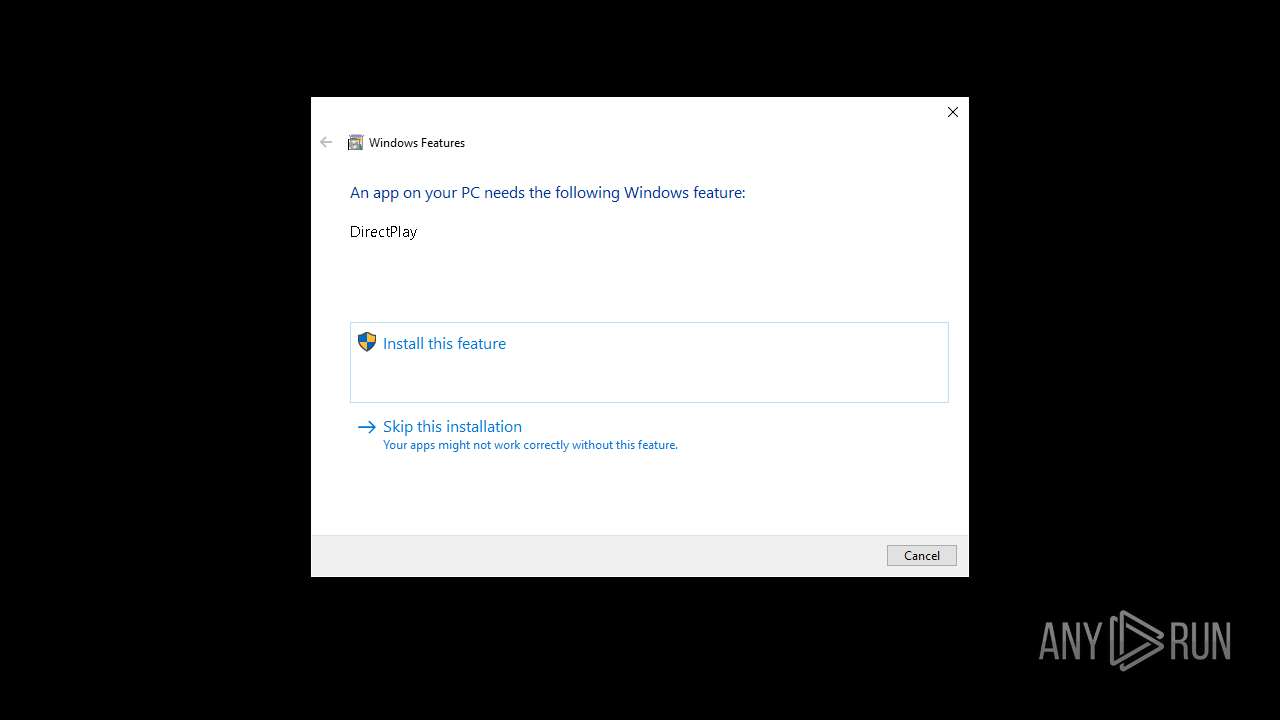
| 3888 | TiWorker.exe | C:\Windows\WinSxS\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dpwsockx.dll | executable | |
MD5:152786505316BF34B54D68F3731C62AE | SHA256:48D98E0F6F3854AD1CE9955E2FDD6719C3D57AB9C951FD0B707C701EEF8AA7F4 | |||
| 3888 | TiWorker.exe | C:\Windows\WinSxS\Temp\PendingDeletes\027483400ba6db0112000000300f4c1b.dplaysvr.exe | binary | |
MD5:00AF941460A4DDBC9EE252B33713E94E | SHA256:5303EF7D0F6F248B1CD3F3569D547E25B4A5238B2D3CDFFC4424106C9851EF1D | |||
| 3888 | TiWorker.exe | C:\Windows\WinSxS\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dplaysvr.exe | executable | |
MD5:F825C2679BB5177E015FD3F0133B7788 | SHA256:EBC69C1285014C40D286ABFAC9CB3CE18B99B422AA9A30B56313C9CA7E1E8804 | |||
| 3888 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\84e379400ba6db0111000000300f4c1b\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dpmodemx.dll | executable | |
MD5:CDE67309989D9E0944501F71A690DA95 | SHA256:4482FDFA30C60A6FF68DAB91B3DD340A16990A7BCE04A4D11481B09BB6BD796E | |||
| 3888 | TiWorker.exe | C:\Windows\servicing\Sessions\31172107_788972772.xml | xml | |
MD5:13B394FCC86B2F4A1FC9E6AF3238A736 | SHA256:93E53849DB4ACEDAED3E1E0064C8A2338D2145FCAE426734F8533B3D122D2B22 | |||
| 3888 | TiWorker.exe | C:\Windows\WinSxS\x86_microsoft-windows-d..4-payload.resources_31bf3856ad364e35_10.0.19041.1_en-us_38ee2e45b9a48a7e\dpmodemx.dll.mui | executable | |
MD5:C7DF217B5C1177B004FA7B211CDC6423 | SHA256:E8FDA508DE4A0B415ACA9A7AC3FB65A65C4A31FC2976F682AB3E4DC77F1D2208 | |||
| 3888 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:35DCB07A9F850D6A80462E8E689C08EC | SHA256:30F89A00C1EFC7B27EA385FCAE8FD94786F3F18CFC930FBB1D2E13FB90493EF4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
33
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5360 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5360 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.172.255.216:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6544 | svchost.exe | 40.126.32.140:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |