| URL: | static.bshare.cn |
| Full analysis: | https://app.any.run/tasks/108e41a4-4d89-44c5-811b-cbd82add1da1 |
| Verdict: | Malicious activity |
| Analysis date: | December 15, 2023, 14:01:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 3C2C5A21AB12F97F35058444460546BC |
| SHA1: | 023AEB17246B0AB36588E0A7DF78B0743D8D1283 |
| SHA256: | 9EEA0C5958F7AE26F09FCE8B7E0D2FB92577BCF3B6C8185D2213D59D1D73CA71 |
| SSDEEP: | 3:NrBLn:1BLn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- wmpnscfg.exe (PID: 3468)
Application launched itself
- iexplore.exe (PID: 2464)
Checks supported languages
- wmpnscfg.exe (PID: 3468)
Reads the computer name
- wmpnscfg.exe (PID: 3468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2464 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2464 | "C:\Program Files\Internet Explorer\iexplore.exe" "static.bshare.cn" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3468 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 563
Read events
13 498
Write events
63
Delete events
2
Modification events
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005A010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2464) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
0
Suspicious files
10
Text files
8
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:E5034468F4C766A164BB3E28D4F0E6C8 | SHA256:C22DF2802E5DA3ECE8D548EE7280F764D7EDB5BA19A3661D0749DD13ACF8F2DB | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\5X9A3JUV.htm | html | |
MD5:B3EDB334B9EFE5DBB512CFE2EA8CD34D | SHA256:A905619ED83F35B1EFB7AE59D4CC5E8958688F10A937D59521814BBA6F2D97F1 | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\B6QGX7LP\favicon[2].ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:D2CBE2C1EF0A91251C036D4A91C2DCC0 | SHA256:0596DC0EC76B96D1D4E825B7D3ADC7F76CCBE71CF29A6BCDC6257F2BC5A680DB | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\0DA515F703BB9B49479E8697ADB0B955_786387CC77858B88BA3234B304062475 | binary | |
MD5:54CB46AB69DC9E1E52AF8B3E135F8E45 | SHA256:EDFD9DD85AB4D7AB8A37A1F02861949FDE2ED535F8873574B97964CF73370946 | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | binary | |
MD5:D6DD198EC272A487DC89651B11FB6803 | SHA256:13633F8BB10640C89FB65C3D5CAA8AEF3205F0D2E0CF08EC4302D0902DB1CC5A | |||
| 1116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0DA515F703BB9B49479E8697ADB0B955_786387CC77858B88BA3234B304062475 | binary | |
MD5:D8A32BC4F30ADB16C26F5B0BCC8B6C85 | SHA256:75DBC9D17A57324A7E960B6665DE9E3BF8A77CDA193D5407649931A57B6AF34C | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:2FF1DAB7A20EB915F7684690FA71A710 | SHA256:88D65170A71D6AF0542A1E7F6F89A7D7F6D073E605AD034C693A0234537F0FB2 | |||
| 2464 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:49AD5A644C2A98A40CDAADCD54C1F914 | SHA256:8FCD3FAB567B37D8F633804E0D640444465D32D9310E41753C2D3151FDD6E1F1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
31
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
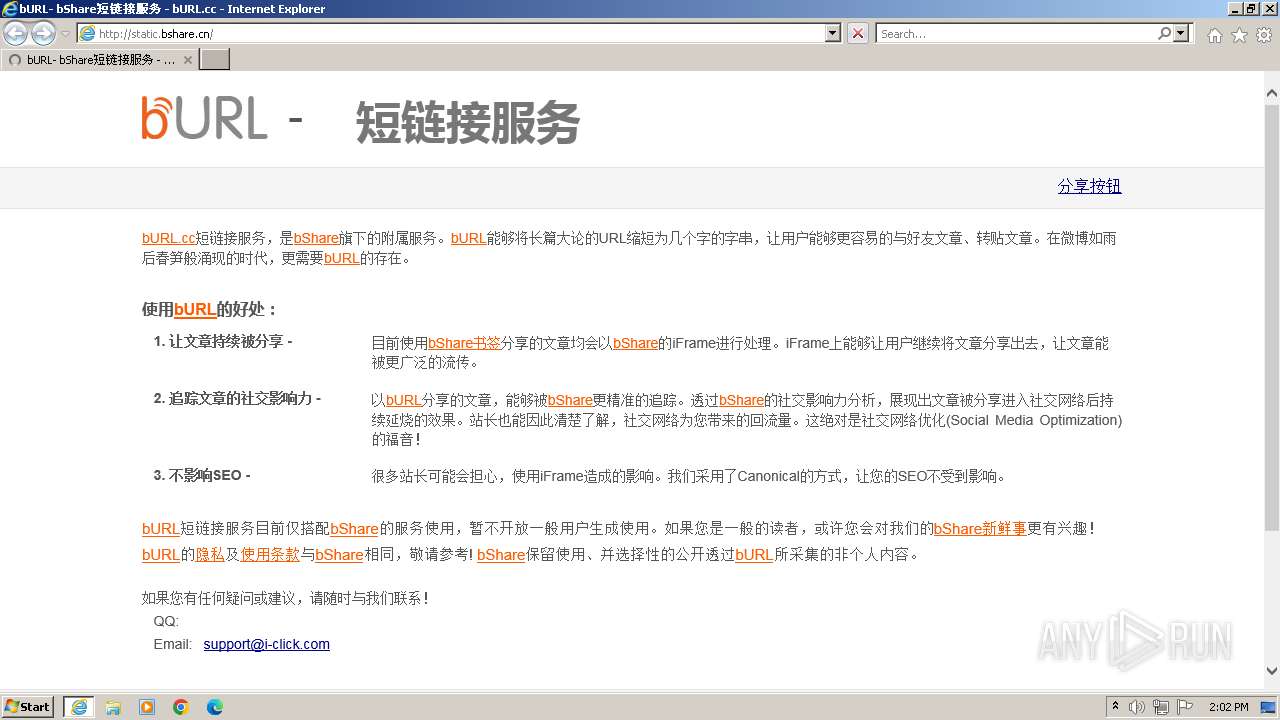
1116 | iexplore.exe | GET | 200 | 101.33.5.163:80 | http://static.bshare.cn/ | unknown | html | 3.70 Kb | unknown |
1116 | iexplore.exe | GET | — | 101.33.5.163:80 | http://static.bshare.cn/images/logo-burl.jpg | unknown | — | — | unknown |
1116 | iexplore.exe | GET | — | 101.33.5.163:80 | http://static.bshare.cn/images/logo-bshare.jpg | unknown | — | — | unknown |
1116 | iexplore.exe | GET | — | 101.33.5.163:80 | http://static.bshare.cn/images/net-police.png | unknown | — | — | unknown |
1116 | iexplore.exe | GET | 200 | 101.33.5.163:80 | http://static.bshare.cn/b/buttonLite.js | unknown | text | 8.23 Kb | unknown |
1116 | iexplore.exe | GET | — | 101.33.5.163:80 | http://static.bshare.cn/images/logo-burl.jpg | unknown | — | — | unknown |
1116 | iexplore.exe | GET | — | 101.33.5.163:80 | http://static.bshare.cn/images/logo-bshare.jpg | unknown | — | — | unknown |
1116 | iexplore.exe | GET | 302 | 101.91.33.148:80 | http://wpa.b.qq.com/cgi/wpa.php | unknown | html | 137 b | unknown |
2464 | iexplore.exe | GET | 200 | 46.228.146.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?851c751b721441d0 | unknown | compressed | 4.66 Kb | unknown |
2464 | iexplore.exe | GET | 200 | 46.228.146.0:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3121f6cf0a82b697 | unknown | compressed | 4.66 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1116 | iexplore.exe | 101.33.5.163:80 | static.bshare.cn | Tencent Building, Kejizhongyi Avenue | ID | unknown |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
1116 | iexplore.exe | 101.91.33.148:80 | wpa.b.qq.com | China Telecom Group | CN | unknown |
1116 | iexplore.exe | 101.91.33.148:443 | wpa.b.qq.com | China Telecom Group | CN | unknown |
2464 | iexplore.exe | 92.122.215.60:443 | www.bing.com | Akamai International B.V. | DE | unknown |
2464 | iexplore.exe | 46.228.146.0:80 | ctldl.windowsupdate.com | LLNW | US | unknown |
2464 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
static.bshare.cn |
| whitelisted |
wpa.b.qq.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dns.msftncsi.com |
| shared |
ocsp.globalsign.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |