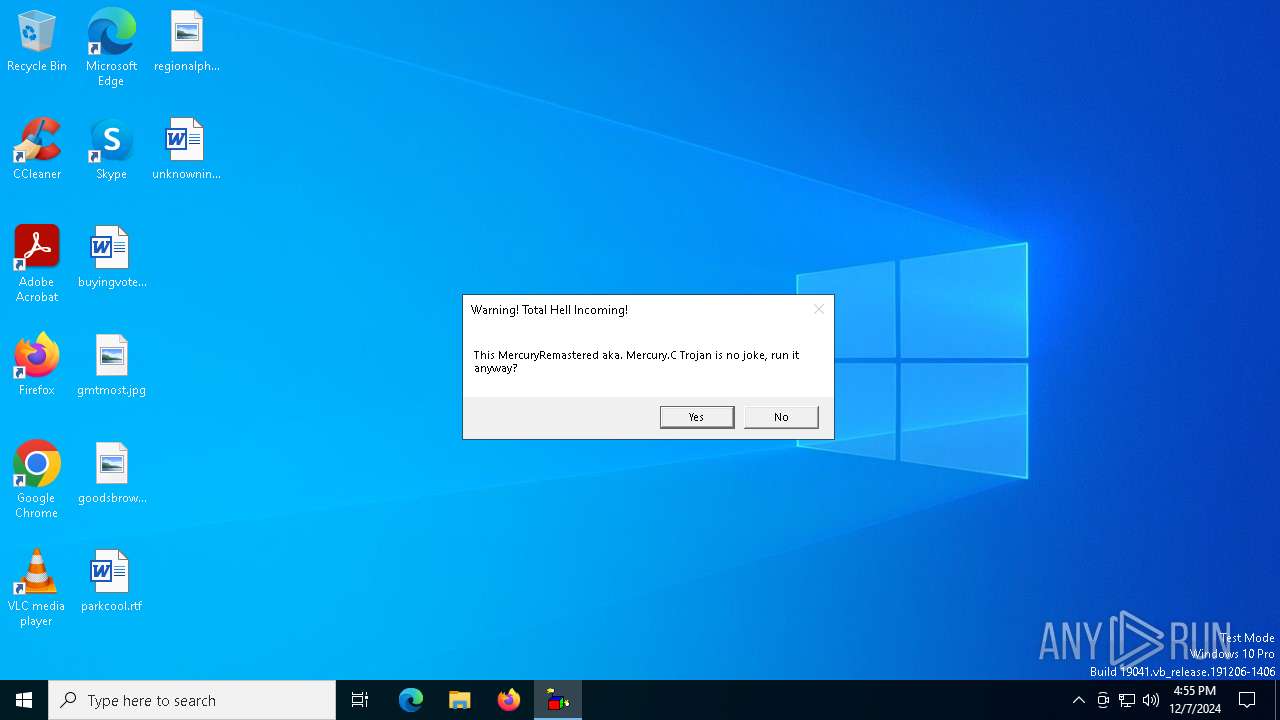
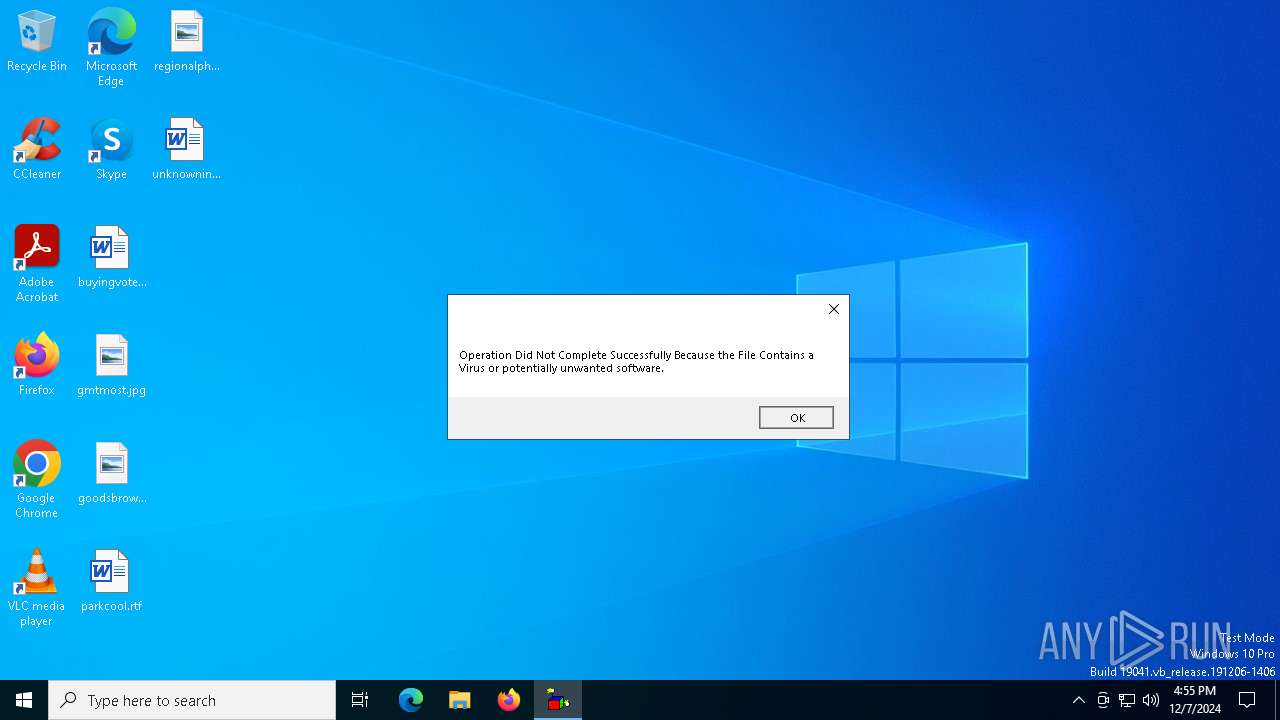
| File name: | Mercury.C.exe |
| Full analysis: | https://app.any.run/tasks/9f0cbf3f-b78e-4dd1-bbd2-1abfa33015bb |
| Verdict: | Malicious activity |
| Analysis date: | December 07, 2024, 16:55:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | F7B55502A71CEF2D1E70D88AEEB63D73 |
| SHA1: | BFD5A73A583A78464CB9F46D3799F6C9F47663FF |
| SHA256: | 9EB6551959A913DE98898302EC764841BE357C0786038BDFA1C3D7F269D490A6 |
| SSDEEP: | 49152:li2bdYx6l+9MYW3VU0F0Wnn9VSKCjBVBC0sIRwkuFNmC39CXhvIV4kjyiYpeWqzW:licg6l+mYWm0Fx9VSKarsfTgJ+ByLpvH |
MALICIOUS
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6428)
SUSPICIOUS
Reads security settings of Internet Explorer
- Mercury.C.exe (PID: 6228)
Runs WScript without displaying logo
- wscript.exe (PID: 6428)
Executable content was dropped or overwritten
- Mercury.C.exe (PID: 6228)
The process executes VB scripts
- Mercury.C.exe (PID: 6228)
- wscript.exe (PID: 6428)
Application launched itself
- wscript.exe (PID: 6428)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 6888)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6428)
- wscript.exe (PID: 6888)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6888)
INFO
Checks supported languages
- Mercury.C.exe (PID: 6228)
- mbr.exe (PID: 6916)
- bytebeat.exe (PID: 6936)
- ColorA.exe (PID: 6968)
- GlitchB.exe (PID: 5748)
The process uses the downloaded file
- Mercury.C.exe (PID: 6228)
- wscript.exe (PID: 6428)
Process checks computer location settings
- Mercury.C.exe (PID: 6228)
Reads the computer name
- Mercury.C.exe (PID: 6228)
- bytebeat.exe (PID: 6936)
Create files in a temporary directory
- Mercury.C.exe (PID: 6228)
Reads Microsoft Office registry keys
- wscript.exe (PID: 6428)
UPX packer has been detected
- Mercury.C.exe (PID: 6228)
Reads security settings of Internet Explorer
- wscript.exe (PID: 6428)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.1) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.5) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:02:01 20:46:09+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 1060864 |
| InitializedDataSize: | 8192 |
| UninitializedDataSize: | 61440 |
| EntryPoint: | 0x111570 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.6.6.6 |
| ProductVersionNumber: | 3.6.6.6 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileVersion: | 3.6.6.6 |
| ProductVersion: | 3.6.6.6 |
| ProductName: | MercuryRemastered |
| InternalName: | death |
| FileDescription: | Mercury Trojan variant C |
| CompanyName: | HorrorTrojans |
| LegalCopyright: | 2022 |
Total processes
137
Monitored processes
8
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5340 | "C:\Users\admin\AppData\Local\Temp\Mercury.C.exe" | C:\Users\admin\AppData\Local\Temp\Mercury.C.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 5748 | "C:\Users\admin\AppData\Local\Temp\53FF.tmp\GlitchB.exe" | C:\Users\admin\AppData\Local\Temp\53FF.tmp\GlitchB.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6228 | "C:\Users\admin\AppData\Local\Temp\Mercury.C.exe" | C:\Users\admin\AppData\Local\Temp\Mercury.C.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6428 | "C:\WINDOWS\sysnative\wscript.exe" C:\Users\admin\AppData\Local\Temp\53FF.tmp\5400.tmp\5401.vbs //Nologo | C:\Windows\System32\wscript.exe | — | Mercury.C.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6888 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\AppData\Local\Temp\53FF.tmp\t.vbs" | C:\Windows\System32\wscript.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6916 | "C:\Users\admin\AppData\Local\Temp\53FF.tmp\mbr.exe" | C:\Users\admin\AppData\Local\Temp\53FF.tmp\mbr.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 6936 | "C:\Users\admin\AppData\Local\Temp\53FF.tmp\bytebeat.exe" | C:\Users\admin\AppData\Local\Temp\53FF.tmp\bytebeat.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6968 | "C:\Users\admin\AppData\Local\Temp\53FF.tmp\ColorA.exe" | C:\Users\admin\AppData\Local\Temp\53FF.tmp\ColorA.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
Total events
2 124
Read events
2 123
Write events
1
Delete events
0
Modification events
| (PID) Process: | (6428) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.vbs\OpenWithProgids |
| Operation: | write | Name: | VBSFile |
Value: | |||
Executable files
7
Suspicious files
2
Text files
209
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6916 | mbr.exe | \Device\Harddisk0\DR0 | — | |
MD5:— | SHA256:— | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\bytebeat.txt | text | |
MD5:8C3BFEFF54B0DC46348107C9BE9E6A74 | SHA256:A2F74FB3C74C170962E74B9FF6CDF7394EE4B85BF3410BFBC710A7373882D9D0 | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\mbr.cpp | text | |
MD5:D20EDDECB5625B60D61D80C067537188 | SHA256:45EAA30A90C739FD9FB32D59B29D3E7CD8871431670A3E64D6C34FD53A08F979 | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\bsod.exe | executable | |
MD5:A0778D97321E407D5EEFA6FDAFE8C984 | SHA256:3665036C52175AD759E0305FB5CB02B11AA0F812DF245BA3E4FDDE89C4E4A272 | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\bytebeat.wav | wav | |
MD5:0D6E9332C0DCABA834CBF616017B0CAD | SHA256:007FCB6EF5AF82CF8325263D6E55A2AA32418A420866FE53E95F29861663449A | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\bytebeat.exe | executable | |
MD5:6DBA963D56AE1FCDFD6E840A52416801 | SHA256:EB3940FB1F2A0B16F5E58C7F4B707FB26B6EE08EBE7F5C43B9C02FCF02FE4506 | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\bytebeat.cpp | text | |
MD5:661EF63AF49D0535151DE251603FA846 | SHA256:55C63887EAEF6D2DAF1DC697A3D824008AA7BFEBC81AC4E7E574596440E5595A | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\ColorA.exe | executable | |
MD5:D50FBC1A509EF70153D458AA657A1416 | SHA256:F41D9FDCDCEBF89EA570158E5D00AFF3A7F31970E92B929258777A1BB52D328D | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\GlitchB.cpp | text | |
MD5:AB9B1236ECF727A56C97729EF989FF61 | SHA256:D7FD6D05AD1EE75CA8524B319FF9803EC0908C2A3DE6EC51CD6F9367F93799B5 | |||
| 6228 | Mercury.C.exe | C:\Users\admin\AppData\Local\Temp\53FF.tmp\ScreenShuffle.exe | executable | |
MD5:042412143D162CE4877E700F1E0E00A3 | SHA256:29D6CB7222B713379111559D5A9DF6F3F500E9B78940BAFA82EBFF0DC80F5690 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5036 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5036 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.9:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6336 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3040 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.9:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.23.209.144:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
1176 | svchost.exe | 40.126.32.134:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |