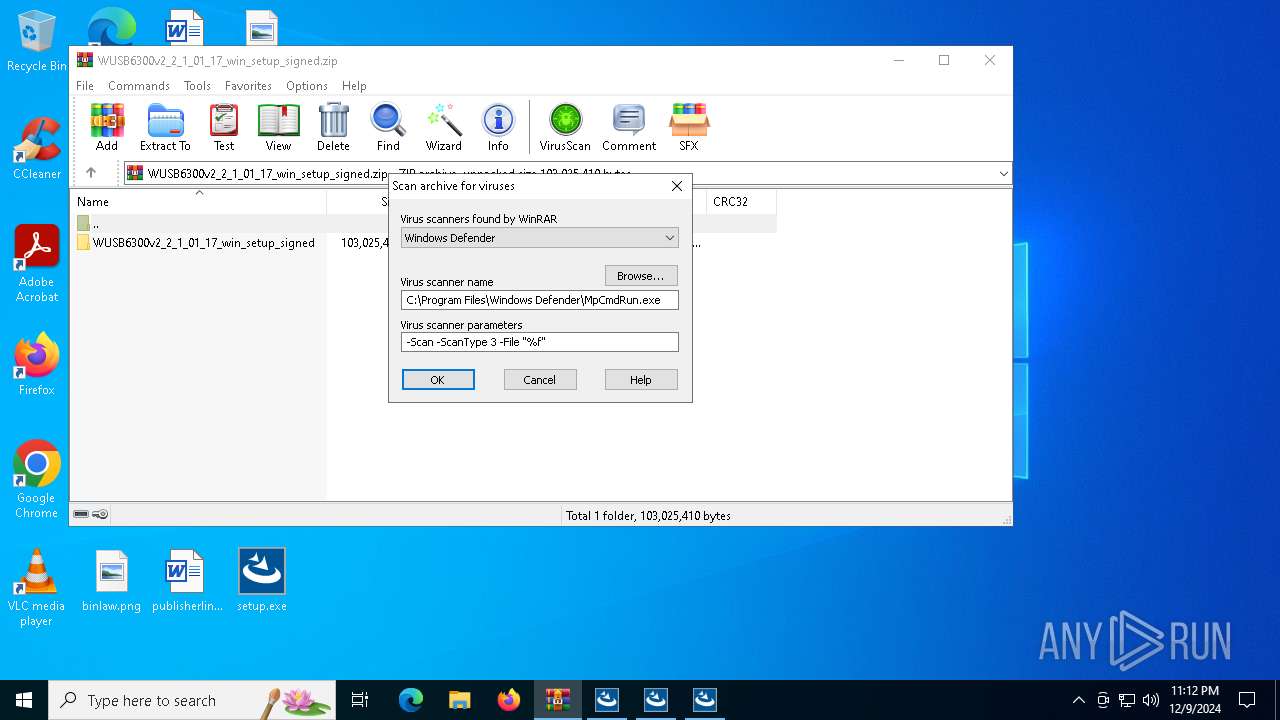
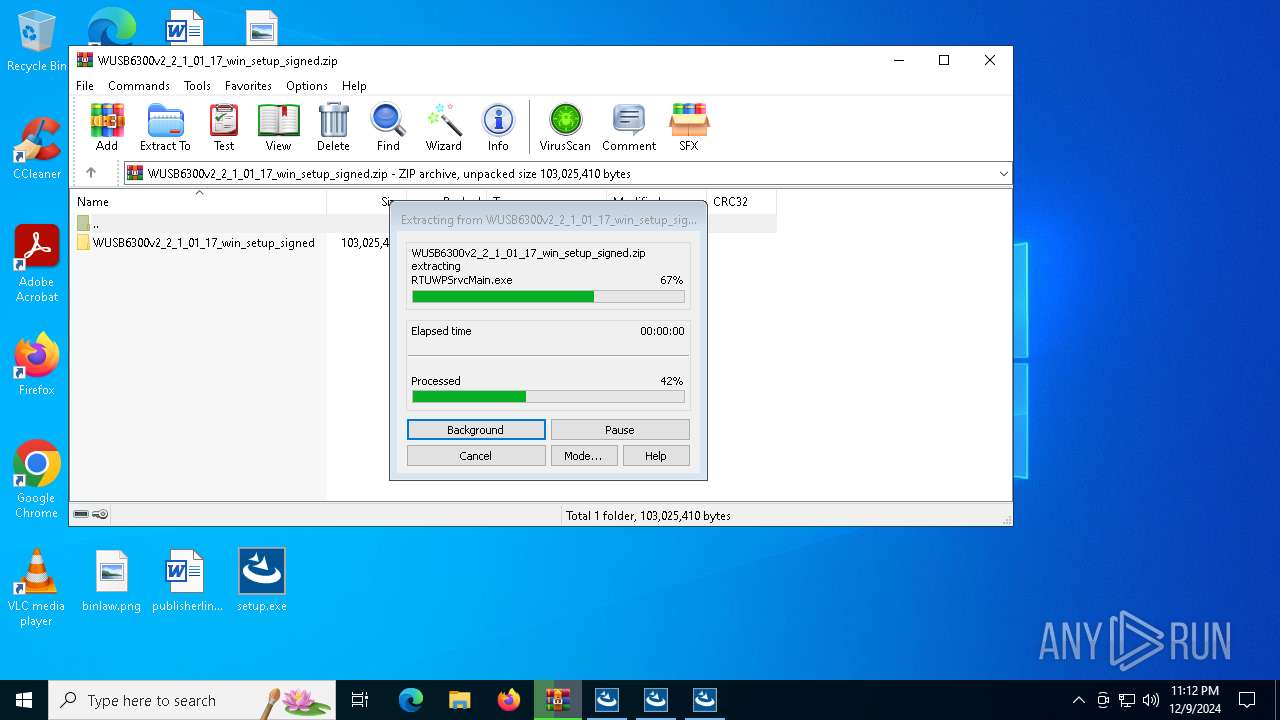
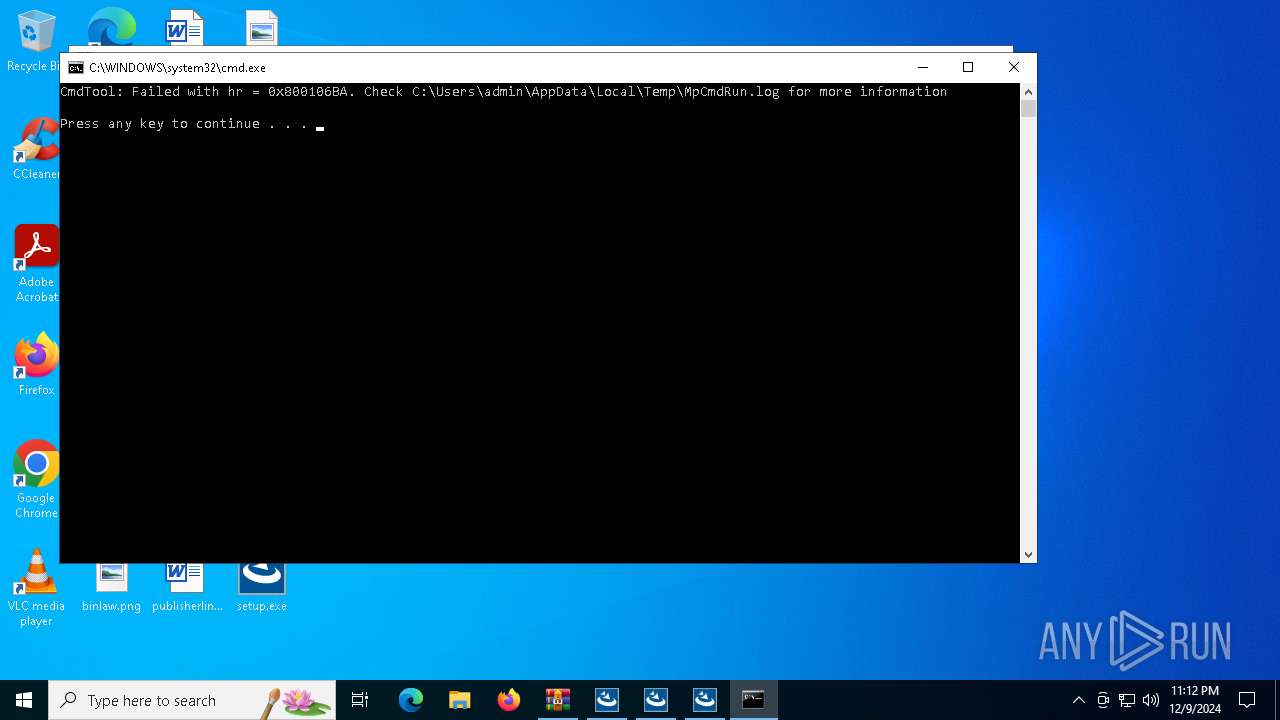
| File name: | WUSB6300v2_2_1_01_17_win_setup_signed.zip |
| Full analysis: | https://app.any.run/tasks/3432d314-beb6-4dc9-a87f-d7e38069bb29 |
| Verdict: | Malicious activity |
| Analysis date: | December 09, 2024, 23:10:08 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 30343A2A29DAC17B92EA95C9B463C657 |
| SHA1: | 2EB1656F7D6C82ABF26115BB1B315F3D3112ADD5 |
| SHA256: | 9E769BE25D117249B79981054A01D61AEBF43A3A5117E2ECF62AB37BADFCC212 |
| SSDEEP: | 393216:uQg2ogb46sMmftoYLSaLwVxr2uIk7zE/ZaLwVxr2u0MfTzbs6S5fTzAwx:+2ogb4Us1WaLwLrCk3E/ZaLwLricwx |
MALICIOUS
Antivirus name has been found in the command line (generic signature)
- MpCmdRun.exe (PID: 4556)
SUSPICIOUS
Executable content was dropped or overwritten
- setup.exe (PID: 7080)
- setup.exe (PID: 7128)
- setup.exe (PID: 4516)
Starts itself from another location
- setup.exe (PID: 7080)
- setup.exe (PID: 7128)
- setup.exe (PID: 4516)
Creates file in the systems drive root
- setup.exe (PID: 7080)
- setup.exe (PID: 7128)
- setup.exe (PID: 4516)
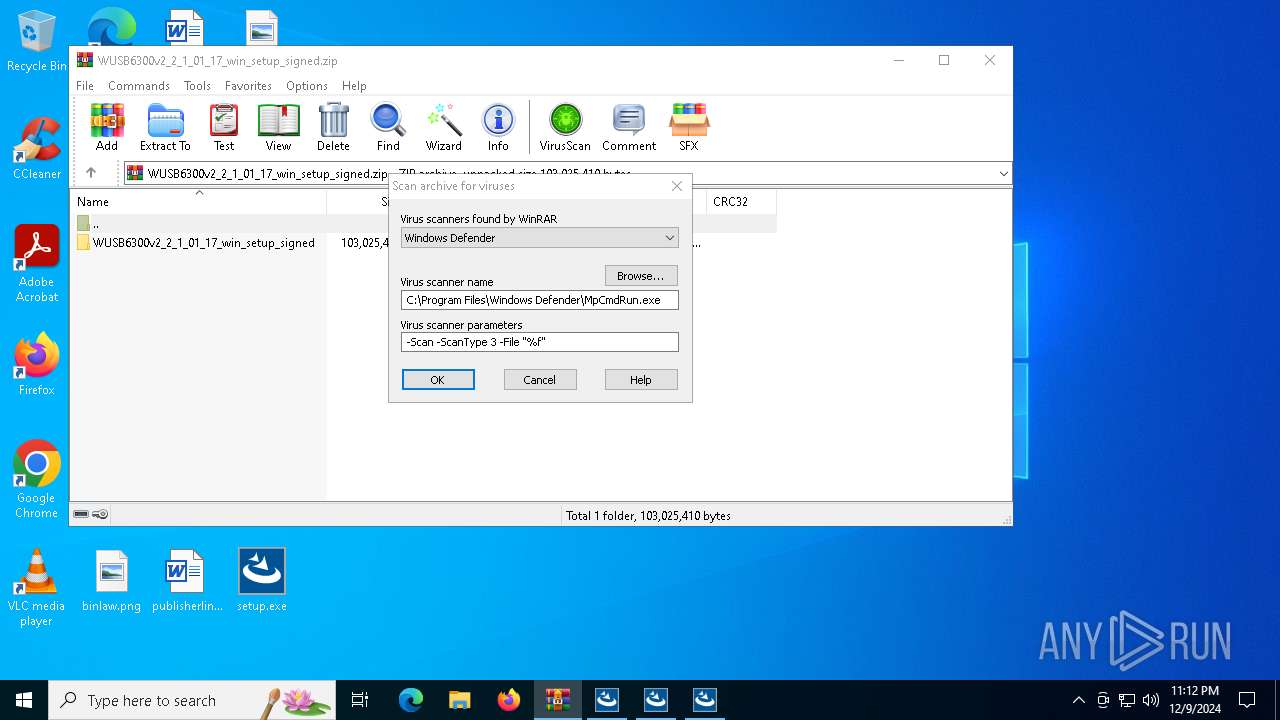
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6668)
Drops a system driver (possible attempt to evade defenses)
- WinRAR.exe (PID: 6668)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 6668)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 6668)
INFO
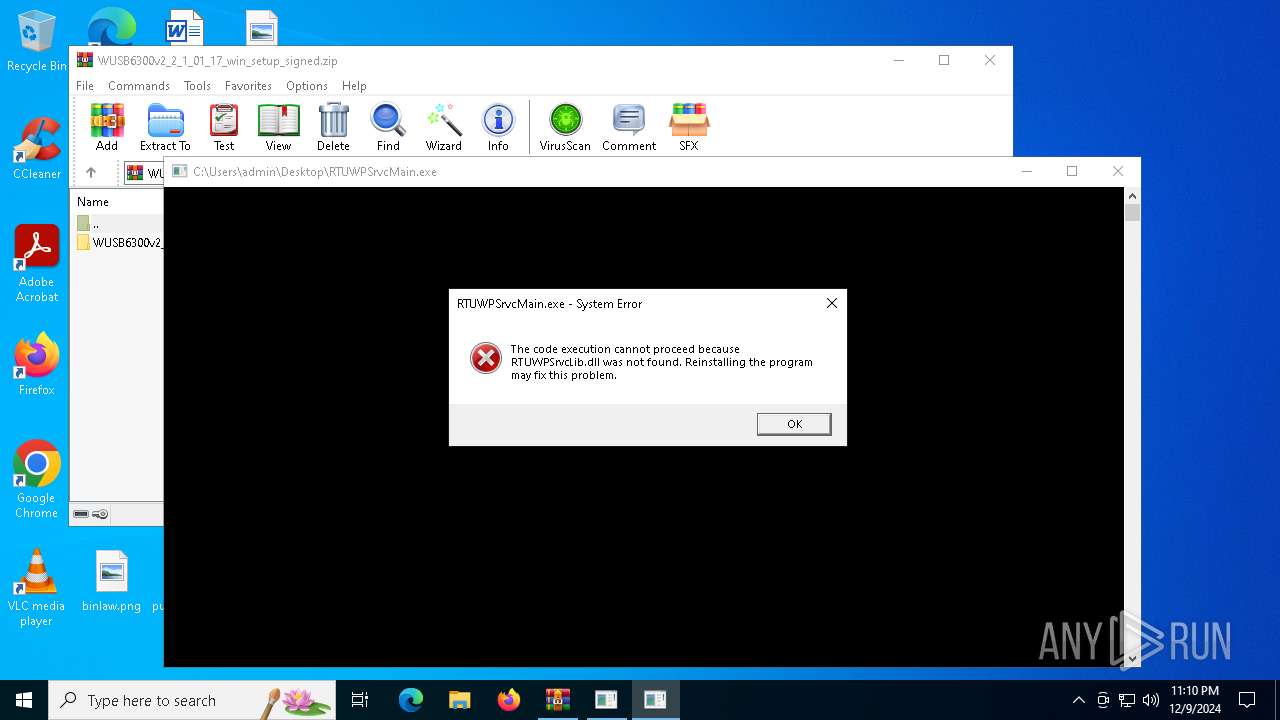
Manual execution by a user
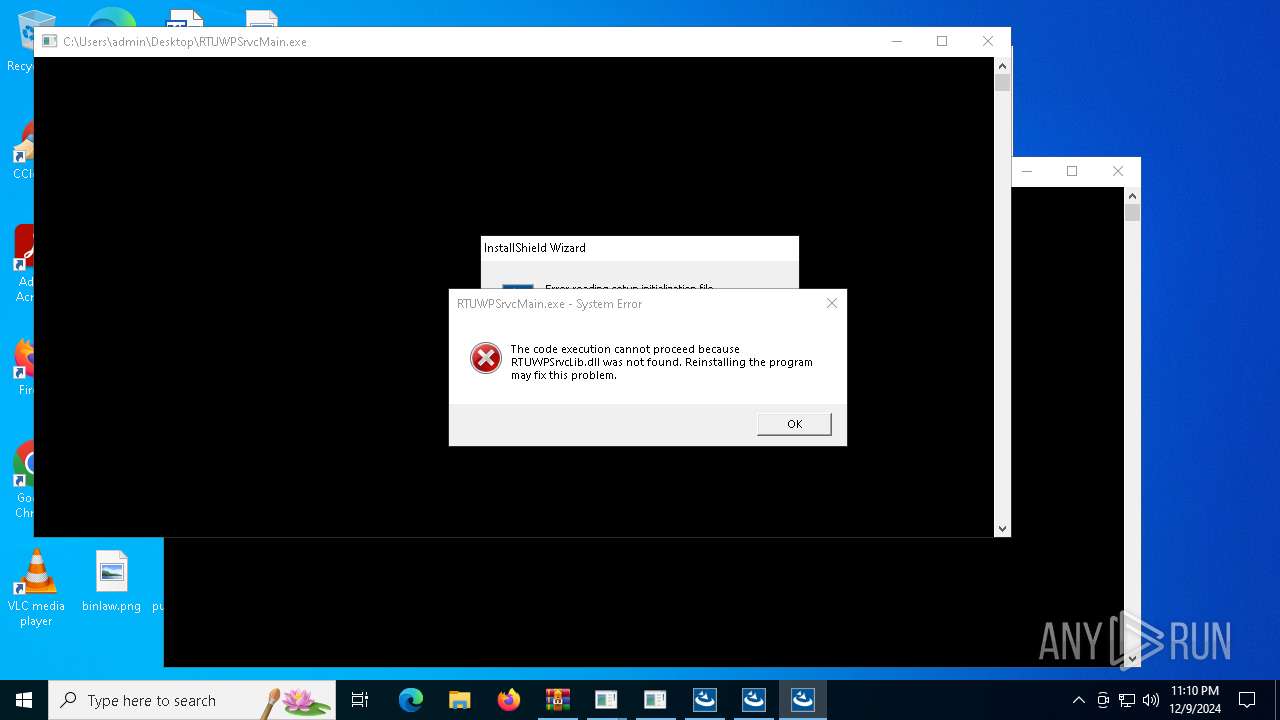
- RTUWPSrvcMain.exe (PID: 6936)
- setup.exe (PID: 7080)
- RTUWPSrvcMain.exe (PID: 6992)
- setup.exe (PID: 7128)
- RTUWPSrvcMain.exe (PID: 6084)
- RTUWPSrvcMain.exe (PID: 6192)
- setup.exe (PID: 4516)
Checks supported languages
- setup.exe (PID: 7080)
- setup.exe (PID: 7128)
- setup.exe (PID: 7144)
- setup.exe (PID: 4516)
- setup.exe (PID: 5720)
- MpCmdRun.exe (PID: 4556)
- setup.exe (PID: 7096)
Reads the computer name
- setup.exe (PID: 7080)
- setup.exe (PID: 7128)
- setup.exe (PID: 7144)
- setup.exe (PID: 4516)
- setup.exe (PID: 5720)
- MpCmdRun.exe (PID: 4556)
- setup.exe (PID: 7096)
Create files in a temporary directory
- setup.exe (PID: 7096)
- setup.exe (PID: 7128)
- setup.exe (PID: 7144)
- setup.exe (PID: 4516)
- setup.exe (PID: 5720)
- MpCmdRun.exe (PID: 4556)
- setup.exe (PID: 7080)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6668)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2021:01:28 15:43:32 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | WUSB6300v2_2_1_01_17_win_setup_signed/ |
Total processes
131
Monitored processes
16
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | RTUWPSrvcMain.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4516 | "C:\Users\admin\Desktop\setup.exe" | C:\Users\admin\Desktop\setup.exe | explorer.exe | ||||||||||||
User: admin Company: Linksys LLC Integrity Level: MEDIUM Description: Setup Launcher Unicode Exit code: 0 Version: 20.08.0003 Modules
| |||||||||||||||
| 4556 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5720 | C:\Users\admin\AppData\Local\Temp\{162618EC-8FC1-4BB1-B947-2DDD61F85E25}\setup.exe /q"C:\Users\admin\Desktop\setup.exe" /tempdisk1folder"C:\Users\admin\AppData\Local\Temp\{162618EC-8FC1-4BB1-B947-2DDD61F85E25}" /IS_temp | C:\Users\admin\AppData\Local\Temp\{162618EC-8FC1-4BB1-B947-2DDD61F85E25}\setup.exe | — | setup.exe | |||||||||||
User: admin Company: Linksys LLC Integrity Level: MEDIUM Description: Setup Launcher Unicode Version: 20.08.0003 Modules
| |||||||||||||||
| 5728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5872 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\Rar$Scan124879.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6084 | "C:\Users\admin\Desktop\RTUWPSrvcMain.exe" | C:\Users\admin\Desktop\RTUWPSrvcMain.exe | explorer.exe | ||||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: HIGH Description: RealTek Service Main Program (UWP) Exit code: 3221225781 Version: 12.1.0116.2019 Modules
| |||||||||||||||
| 6192 | "C:\Users\admin\Desktop\RTUWPSrvcMain.exe" | C:\Users\admin\Desktop\RTUWPSrvcMain.exe | — | explorer.exe | |||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: MEDIUM Description: RealTek Service Main Program (UWP) Exit code: 3221226540 Version: 12.1.0116.2019 Modules
| |||||||||||||||
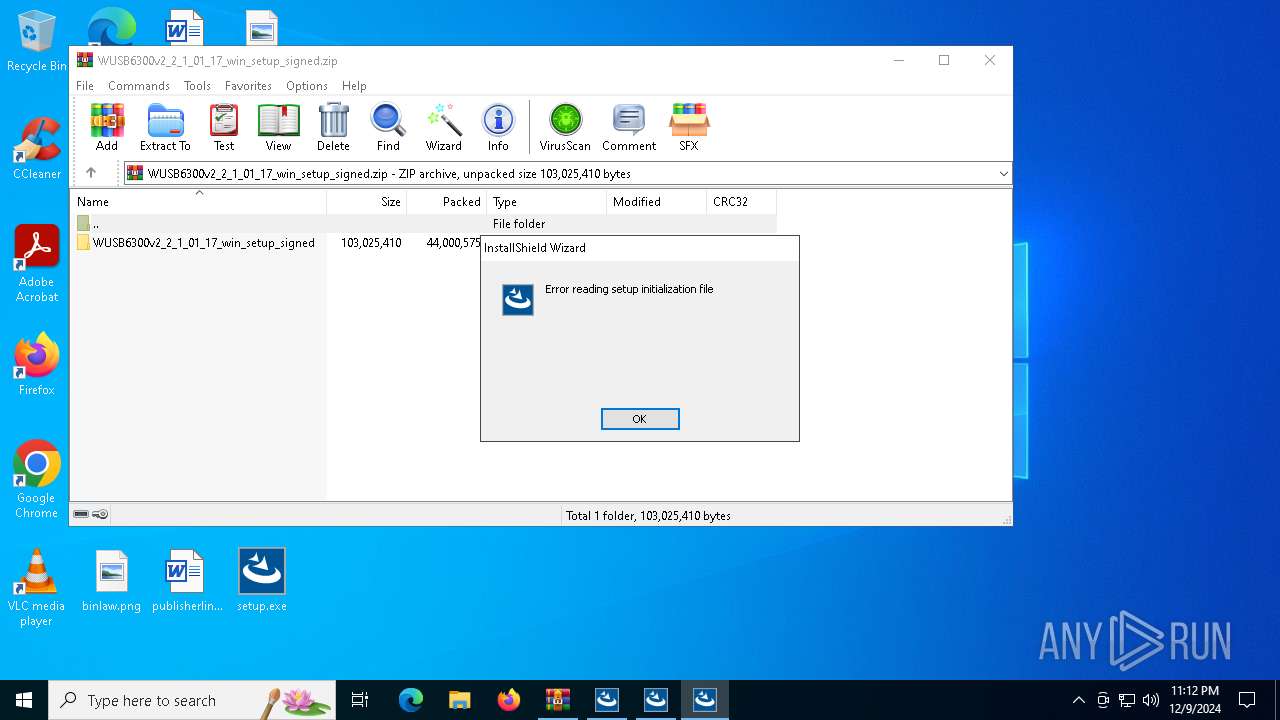
| 6668 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\WUSB6300v2_2_1_01_17_win_setup_signed.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6936 | "C:\Users\admin\Desktop\RTUWPSrvcMain.exe" | C:\Users\admin\Desktop\RTUWPSrvcMain.exe | — | explorer.exe | |||||||||||
User: admin Company: Realtek Semiconductor Corp. Integrity Level: MEDIUM Description: RealTek Service Main Program (UWP) Exit code: 3221226540 Version: 12.1.0116.2019 Modules
| |||||||||||||||
Total events
1 755
Read events
1 746
Write events
9
Delete events
0
Modification events
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\WUSB6300v2_2_1_01_17_win_setup_signed.zip | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6668) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\VirusScan |
| Operation: | write | Name: | DefScanner |
Value: Windows Defender | |||
Executable files
30
Suspicious files
11
Text files
29
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7080 | setup.exe | C:\Users\admin\AppData\Local\Temp\{306AA957-9E44-4027-81AF-189E07E22B7B}\setup.exe | executable | |
MD5:7113EBAD78D35CA58B4F1D2B17BC45D9 | SHA256:A76886E1430DAA899641B2EF6B55D975AE95B908218B87E29CFFD4E6B6FACA66 | |||
| 7080 | setup.exe | C:\Users\admin\AppData\Local\Temp\{306AA957-9E44-4027-81AF-189E07E22B7B}\_ISMSIDEL.INI | text | |
MD5:9104E059107EAE7E6964E8B8EDAFEC11 | SHA256:5591C516F5AAD68E06498124DA993990E720EDD1EB7A2FD00FEC1ADED081958D | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\WUSB6300v2_2_1_01_17_win_setup_signed.zip\WUSB6300v2_2_1_01_17_win_setup_signed\{A140086C-FB1F-4DE9-81E9-636CD279F70D}\program files\WUSB6300\WUSB6300\netrtwlanu\GEMTEKPHY_REG_PG.txt | text | |
MD5:40961FAA112987F734711B73204B90F1 | SHA256:48927AADD4DE81F4311D76CBE6011C365F0C26AAE8A5621CDAB27F1D317987C1 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\WUSB6300v2_2_1_01_17_win_setup_signed.zip\WUSB6300v2_2_1_01_17_win_setup_signed\Setup.exe | executable | |
MD5:7B75EEF670B28E3A0AB8F2CE5F8498FA | SHA256:44B94E9243BD6EE0679F90F29C7E066CD897FA44E32DC38AD414C44209389F7E | |||
| 4516 | setup.exe | C:\Users\admin\AppData\Local\Temp\{162618EC-8FC1-4BB1-B947-2DDD61F85E25}\setup.exe | executable | |
MD5:B73520B3B918CB71B1AFE978366ECF86 | SHA256:E05510E0ECD36B62CDFFB2729372D69A194CC36D2483C98EA1B16F491064E91E | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\WUSB6300v2_2_1_01_17_win_setup_signed.zip\WUSB6300v2_2_1_01_17_win_setup_signed\{A140086C-FB1F-4DE9-81E9-636CD279F70D}\program files\WUSB6300\WUSB6300\netrtwlanu\GEMTEKTXPWR_LMT.txt | text | |
MD5:B2A5AF604C738954ED40AAFC918A7231 | SHA256:1CC571F4DD4F41196337CAC8992CE309C33ACF0B21A213C20FEDF14FB65390A8 | |||
| 4516 | setup.exe | C:\Users\admin\AppData\Local\Temp\{162618EC-8FC1-4BB1-B947-2DDD61F85E25}\_ISMSIDEL.INI | text | |
MD5:C44F2D0FE22DCA0BD27F593221635D65 | SHA256:6E0FAE9F31E6B022BD86789B9D43DD3705D09BB1C3BAFBE76C38D5401C70B495 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\WUSB6300v2_2_1_01_17_win_setup_signed.zip\WUSB6300v2_2_1_01_17_win_setup_signed\{2471626C-B03B-440E-A3C6-B24440F043F7}\program files\WUSB6300\WUSB6300\netrtwlanu\netrtwlanu.cat | cat | |
MD5:19E3C9421C06B9752C4D67F9B244FEDA | SHA256:C3B719C38FB0BDBBE6C4E2684113A7A31CB4D8F573AA7D4F0E7DE16EEB194808 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\WUSB6300v2_2_1_01_17_win_setup_signed.zip\WUSB6300v2_2_1_01_17_win_setup_signed\{2471626C-B03B-440E-A3C6-B24440F043F7}\0x0409.ini | text | |
MD5:A108F0030A2CDA00405281014F897241 | SHA256:8B76DF0FFC9A226B532B60936765B852B89780C6E475C152F7C320E085E43948 | |||
| 6668 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR6668.26059\WUSB6300v2_2_1_01_17_win_setup_signed.zip\WUSB6300v2_2_1_01_17_win_setup_signed\{A140086C-FB1F-4DE9-81E9-636CD279F70D}\0x0409.ini | text | |
MD5:A108F0030A2CDA00405281014F897241 | SHA256:8B76DF0FFC9A226B532B60936765B852B89780C6E475C152F7C320E085E43948 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
23
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2624 | svchost.exe | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2624 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.37:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 104.126.37.139:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2624 | svchost.exe | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.24.77.37:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2624 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3976 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |