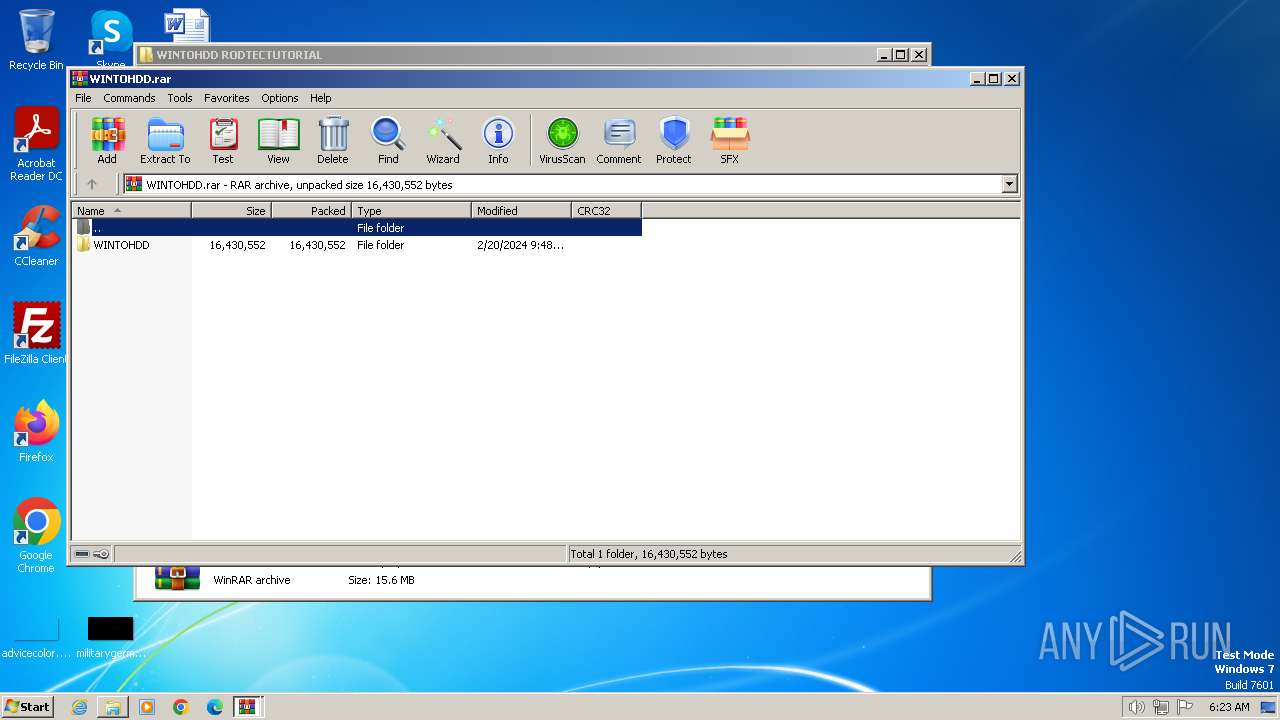
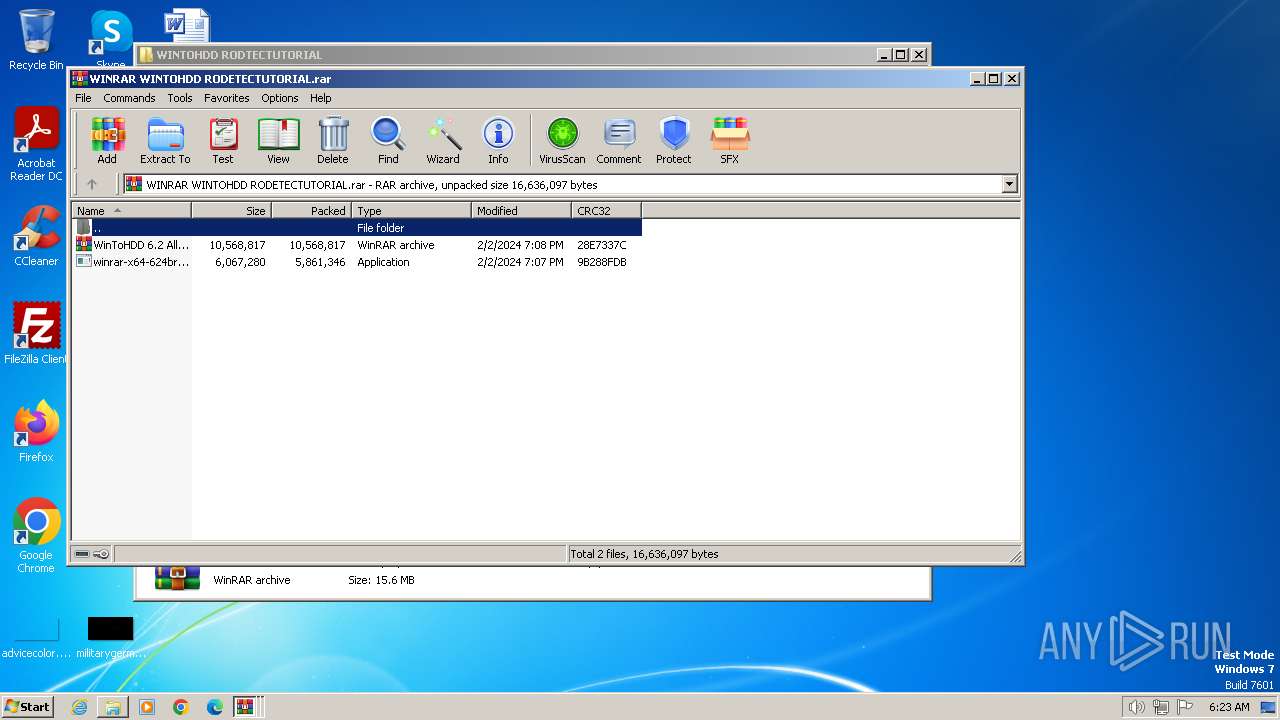
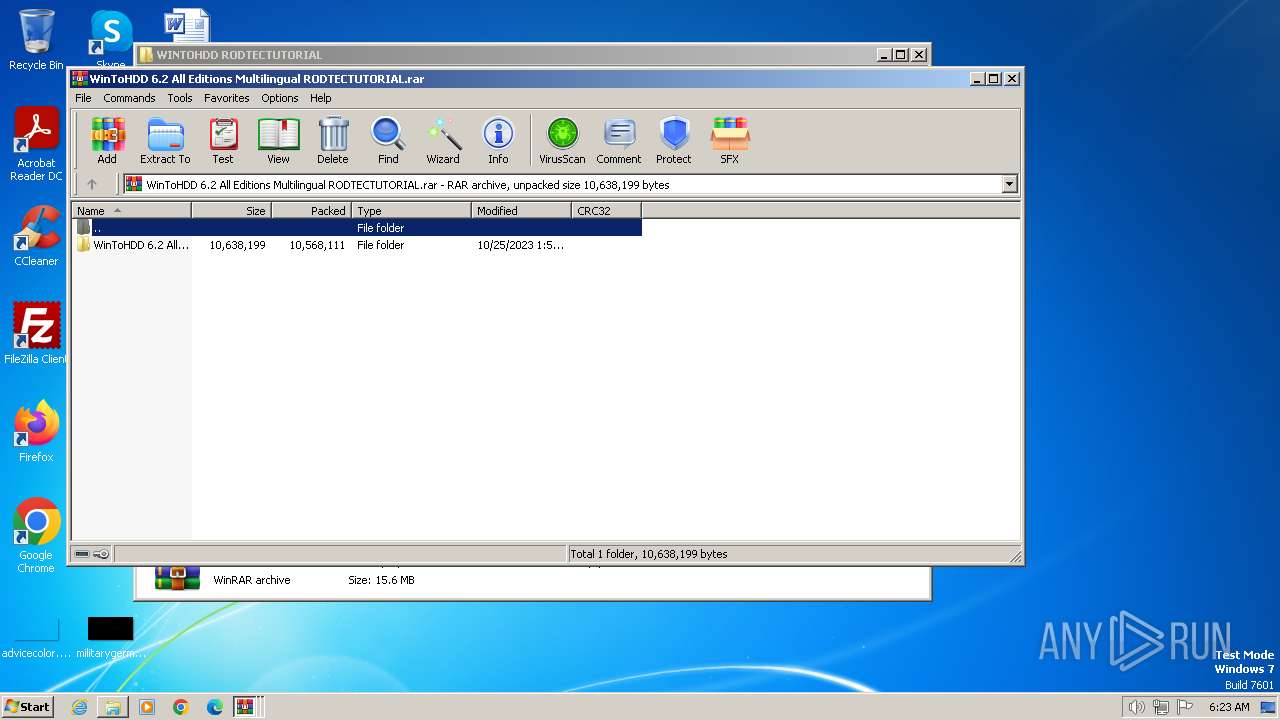
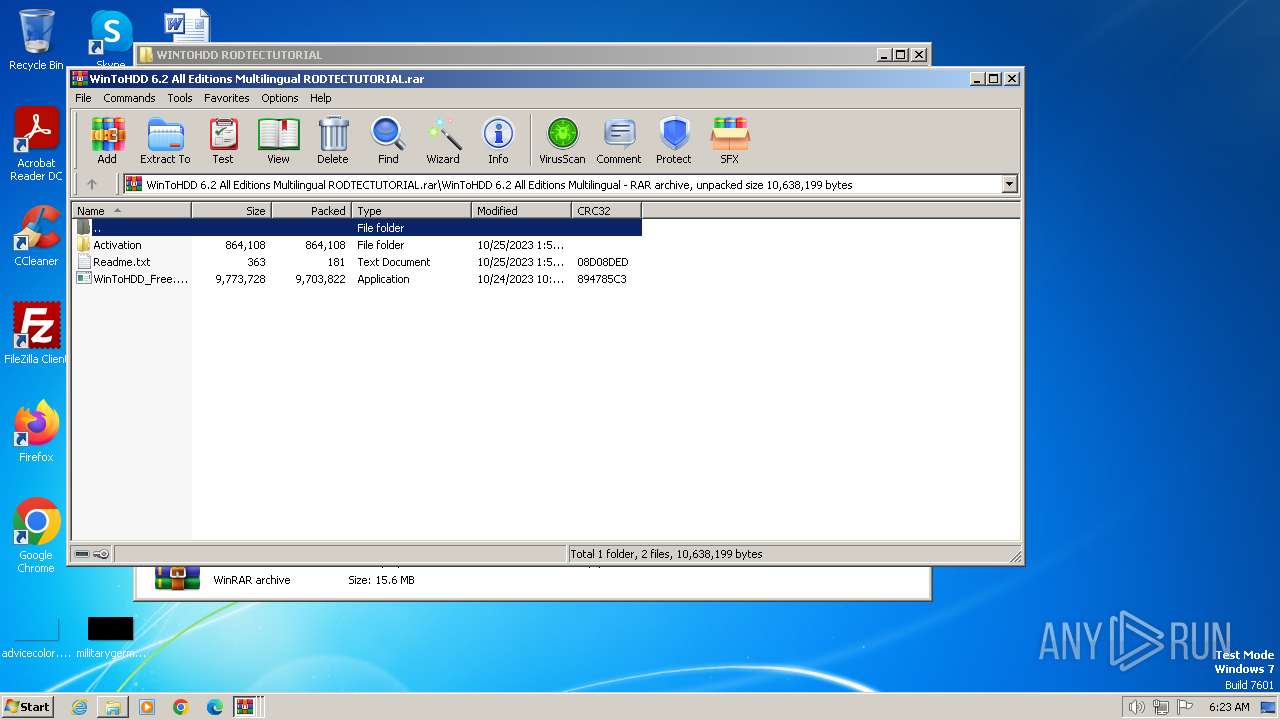
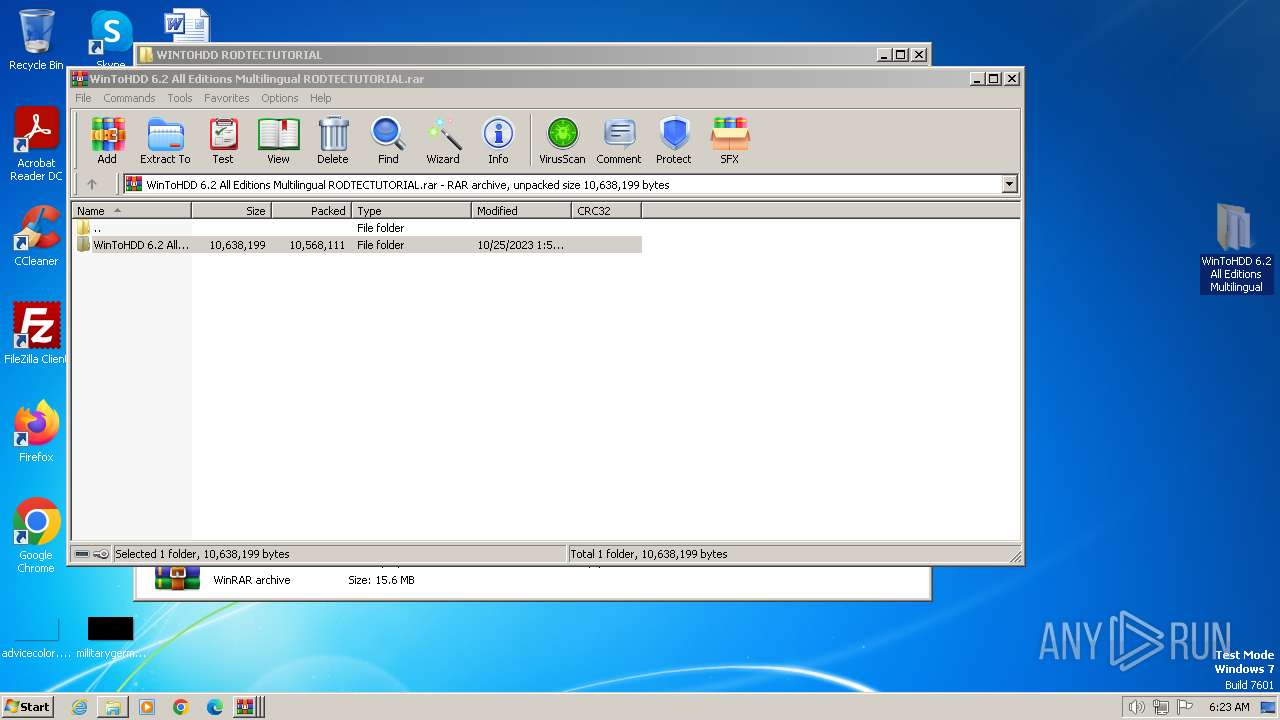
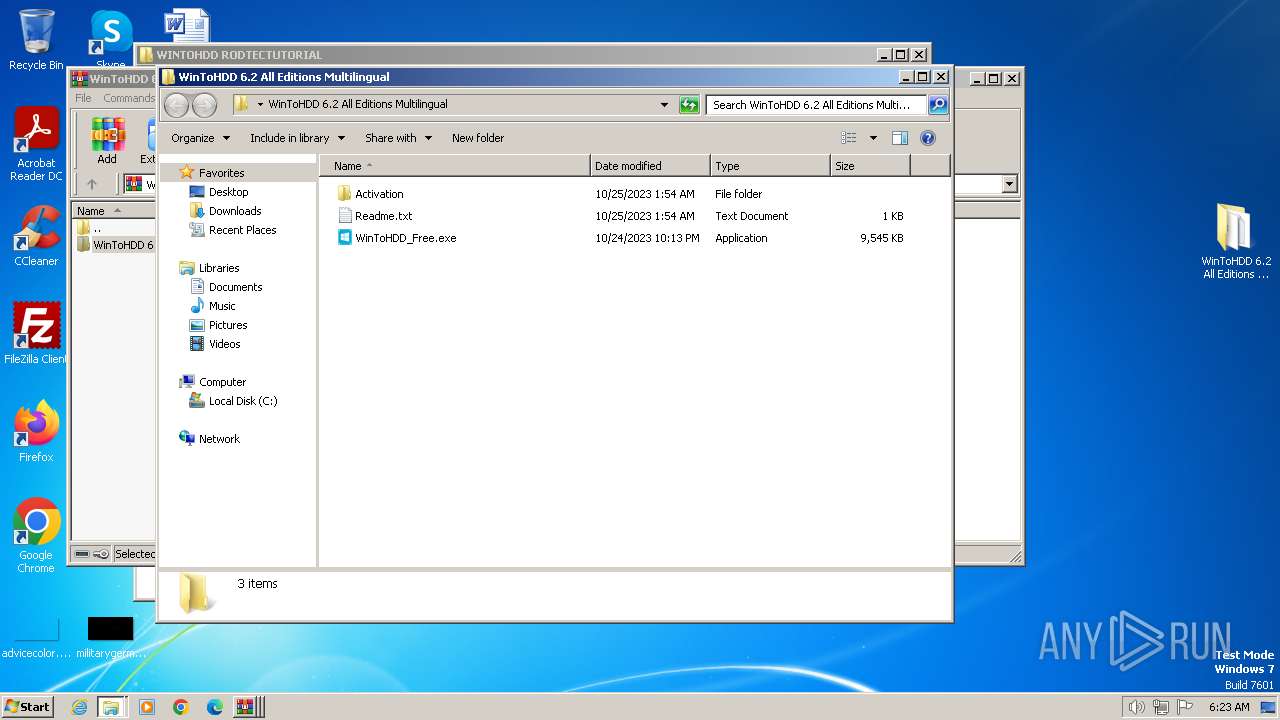
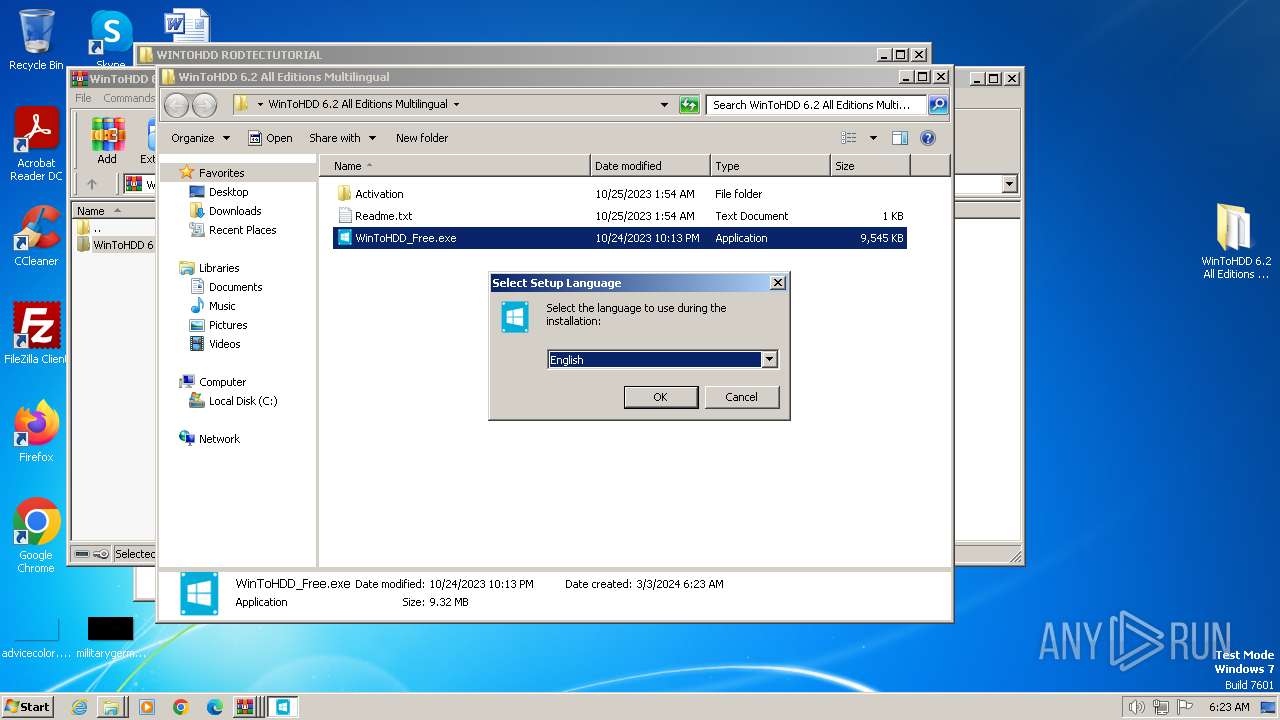
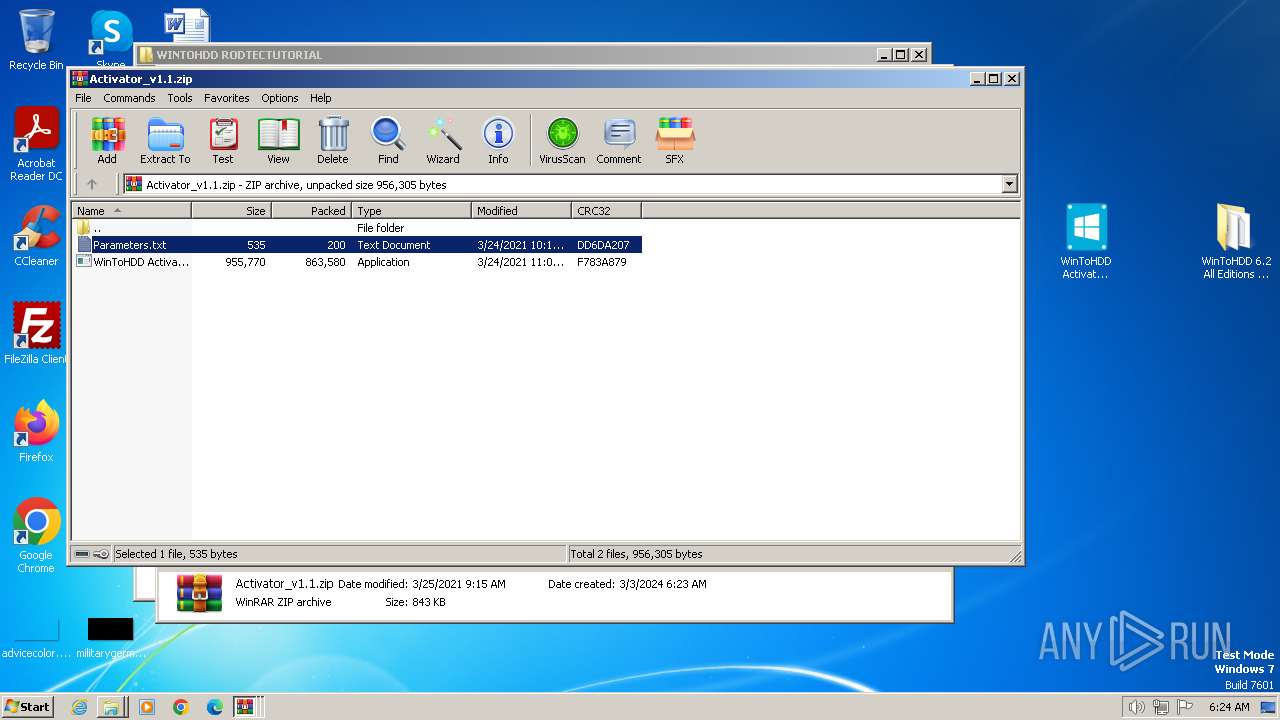
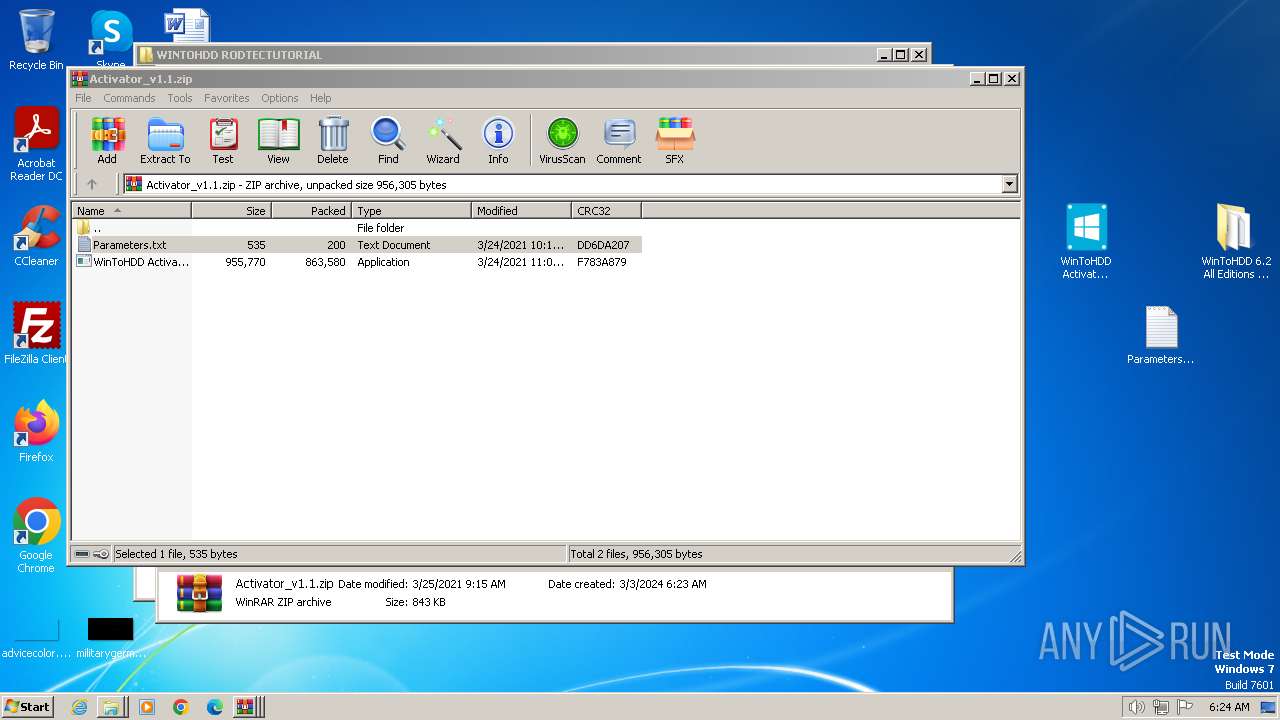
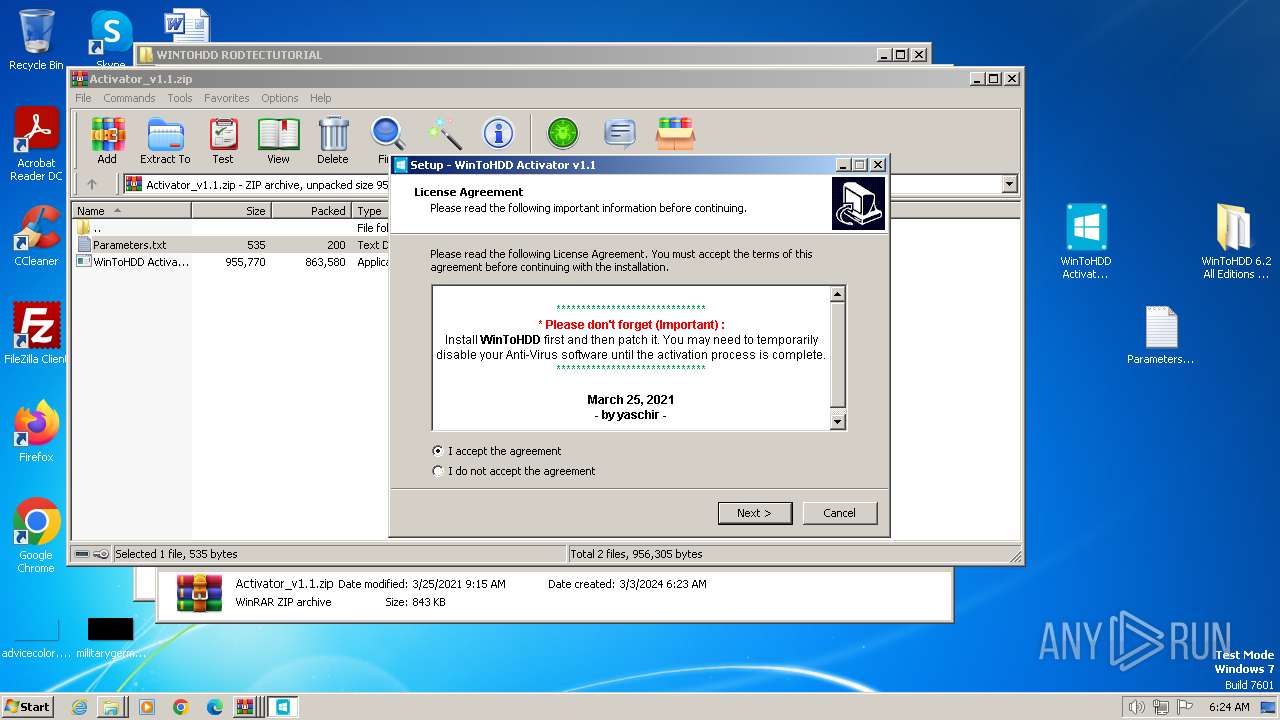
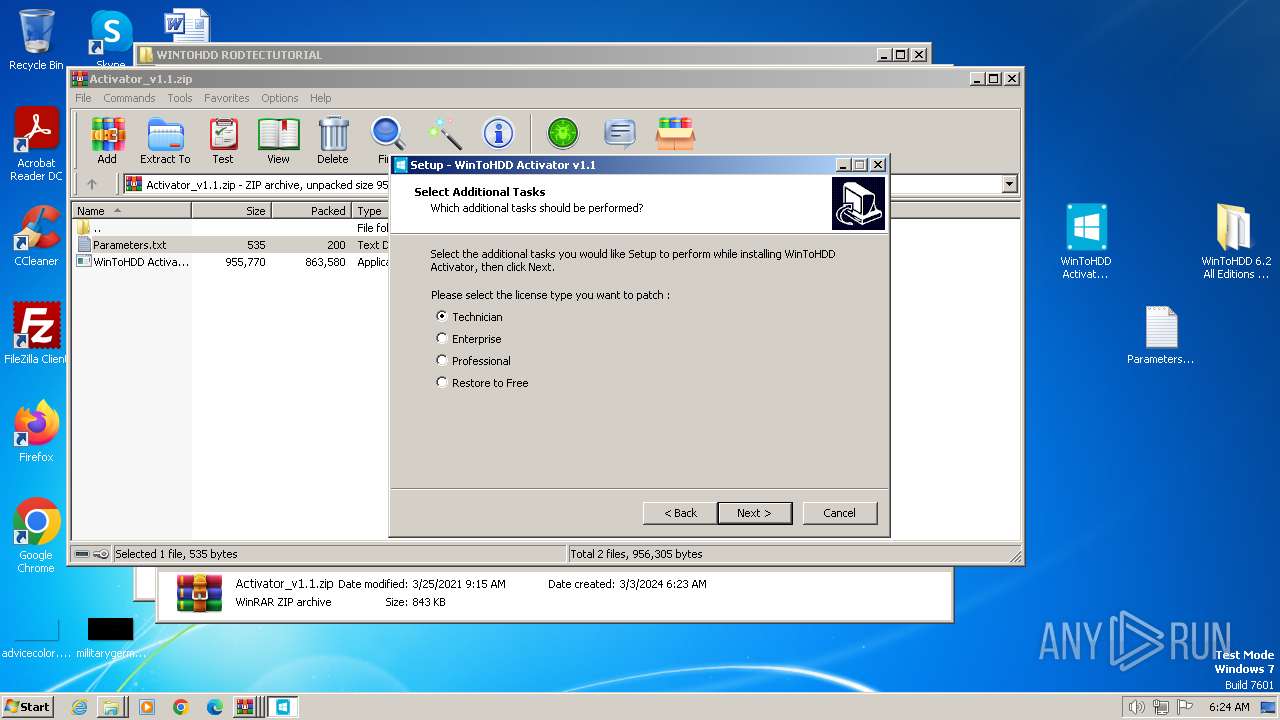
| File name: | WINTOHDD RODTECTUTORIAL.rar |
| Full analysis: | https://app.any.run/tasks/cae7eea0-4784-4daf-a615-ffcb384d8a2b |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 06:23:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | E8FE47CFC61F434F4623602B01A1BFF0 |
| SHA1: | D4582FC8B9808ACFFDCF33C2777D615940C30E91 |
| SHA256: | 9E6BAD73CE40B60CB0959E79D9C4CEFE56CECE4370111B46D9CC9E6888A55AED |
| SSDEEP: | 98304:IsF1mcqZPnfmIg7mTLoU/I03Lygdm/FCzsNcq3b1elaNQOFtXh0RMxShhyldr3bZ:GOBAr4kfHFoeILxD3/JJvp |
MALICIOUS
Drops the executable file immediately after the start
- WinToHDD_Free.exe (PID: 3964)
- WinToHDD_Free.exe (PID: 2688)
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.exe (PID: 1168)
- WinToHDD Activator v1.1.exe (PID: 2340)
- WinToHDD Activator v1.1.tmp (PID: 1696)
- WinToHDD Patcher.exe (PID: 3724)
Creates a writable file in the system directory
- WinToHDD_Free.tmp (PID: 2364)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 2036)
- WinRAR.exe (PID: 3944)
- WinToHDD Activator v1.1.tmp (PID: 1696)
Application launched itself
- WinRAR.exe (PID: 2036)
- WinRAR.exe (PID: 3944)
Executable content was dropped or overwritten
- WinToHDD_Free.exe (PID: 3964)
- WinToHDD_Free.exe (PID: 2688)
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.exe (PID: 1168)
- WinToHDD Activator v1.1.tmp (PID: 1696)
- WinToHDD Activator v1.1.exe (PID: 2340)
- WinToHDD Patcher.exe (PID: 3724)
Reads the Windows owner or organization settings
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.tmp (PID: 1696)
Process checks presence of unattended files
- WinToHDD_Free.tmp (PID: 2364)
Reads the Internet Settings
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.tmp (PID: 1696)
Start notepad (likely ransomware note)
- WinRAR.exe (PID: 3356)
Searches for installed software
- WinToHDD Activator v1.1.tmp (PID: 1696)
Uses TASKKILL.EXE to kill process
- WinToHDD Activator v1.1.tmp (PID: 1696)
INFO
Manual execution by a user
- WinRAR.exe (PID: 2036)
- WinToHDD_Free.exe (PID: 3964)
- msedge.exe (PID: 2176)
- WinRAR.exe (PID: 3356)
- WinToHDD Activator v1.1.exe (PID: 1168)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3304)
- WinRAR.exe (PID: 3356)
Checks supported languages
- WinToHDD_Free.exe (PID: 3964)
- WinToHDD_Free.tmp (PID: 3960)
- WinToHDD_Free.exe (PID: 2688)
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.tmp (PID: 1696)
- WinToHDD Activator v1.1.tmp (PID: 2940)
- WinToHDD Activator v1.1.exe (PID: 2340)
- WinToHDD Activator v1.1.exe (PID: 1168)
- WinToHDD Patcher.exe (PID: 3724)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3304)
- WinRAR.exe (PID: 3356)
Create files in a temporary directory
- WinToHDD_Free.exe (PID: 3964)
- WinToHDD_Free.exe (PID: 2688)
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.exe (PID: 1168)
- WinToHDD Activator v1.1.exe (PID: 2340)
- WinToHDD Patcher.exe (PID: 3724)
Reads the computer name
- WinToHDD_Free.tmp (PID: 3960)
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.tmp (PID: 2940)
- WinToHDD Activator v1.1.tmp (PID: 1696)
Creates files in the program directory
- WinToHDD_Free.tmp (PID: 2364)
- WinToHDD Activator v1.1.tmp (PID: 1696)
Reads Environment values
- WinToHDD_Free.tmp (PID: 2364)
Creates a software uninstall entry
- WinToHDD_Free.tmp (PID: 2364)
Application launched itself
- msedge.exe (PID: 2176)
- msedge.exe (PID: 1112)
Reads the machine GUID from the registry
- WinToHDD_Free.tmp (PID: 2364)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
80
Monitored processes
31
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 712 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xdc,0x698cf598,0x698cf5a8,0x698cf5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 764 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1520 --field-trial-handle=1288,i,4464193092073239800,602660152542960281,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 956 | "C:\Windows\System32\taskkill.exe" /f /im WinToHDD.exe | C:\Windows\System32\taskkill.exe | — | WinToHDD Activator v1.1.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 992 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --gpu-preferences=UAAAAAAAAADgAAAYAAAAAAAAAAAAAAAAAABgAAAAAAAwAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAAAAAAEgAAAAAAAAASAAAAAAAAAAYAAAAAgAAABAAAAAAAAAAGAAAAAAAAAAQAAAAAAAAAAAAAAAOAAAAEAAAAAAAAAABAAAADgAAAAgAAAAAAAAACAAAAAAAAAA= --mojo-platform-channel-handle=1188 --field-trial-handle=1288,i,4464193092073239800,602660152542960281,131072 /prefetch:2 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2232 --field-trial-handle=1288,i,4464193092073239800,602660152542960281,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1036 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --first-renderer-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2192 --field-trial-handle=1288,i,4464193092073239800,602660152542960281,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
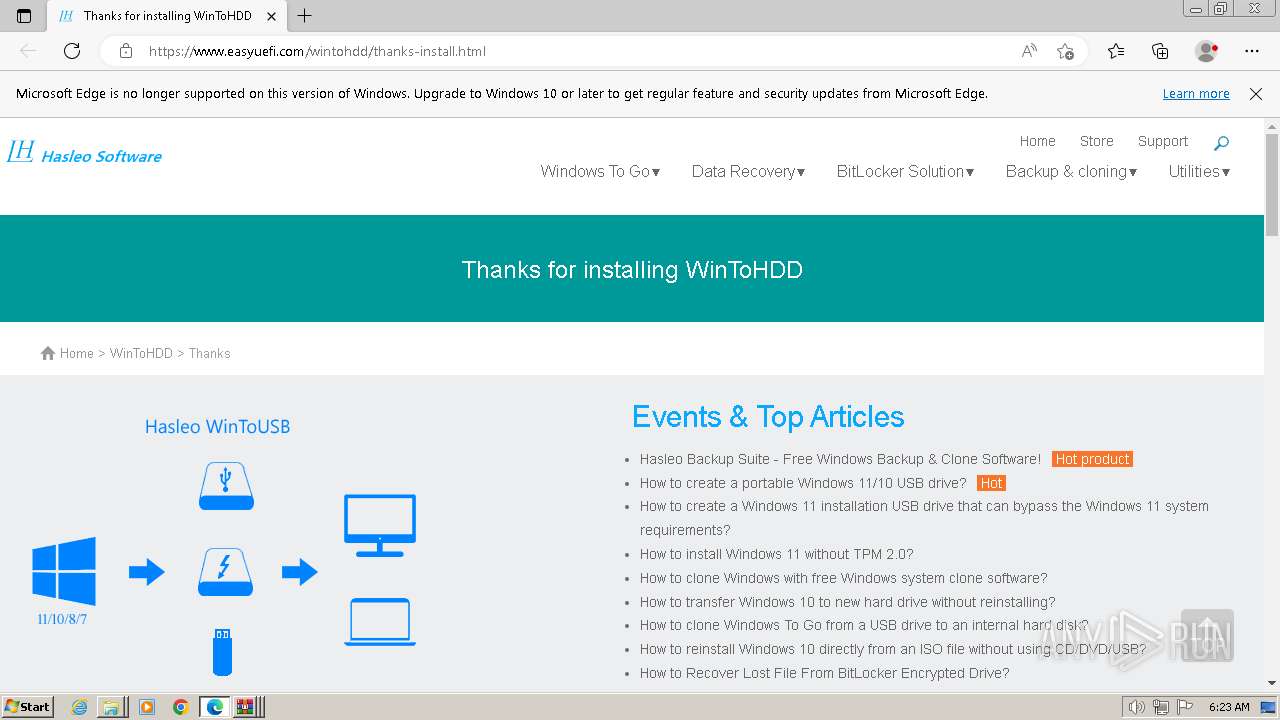
| 1112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --single-argument http://www.easyuefi.com/wintohdd/thanks-install.html | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | WinToHDD_Free.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1168 | "C:\Users\admin\Desktop\WinToHDD Activator v1.1.exe" | C:\Users\admin\Desktop\WinToHDD Activator v1.1.exe | explorer.exe | ||||||||||||
User: admin Company: yaschir Integrity Level: MEDIUM Description: WinToHDD Activator Exit code: 0 Version: 1.1 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=3268 --field-trial-handle=1288,i,4464193092073239800,602660152542960281,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1696 | "C:\Users\admin\AppData\Local\Temp\is-224BV.tmp\WinToHDD Activator v1.1.tmp" /SL5="$B0336,446673,164352,C:\Users\admin\Desktop\WinToHDD Activator v1.1.exe" /SPAWNWND=$A0328 /NOTIFYWND=$7034E | C:\Users\admin\AppData\Local\Temp\is-224BV.tmp\WinToHDD Activator v1.1.tmp | WinToHDD Activator v1.1.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
Total events
23 471
Read events
23 307
Write events
148
Delete events
16
Modification events
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\WINTOHDD RODTECTUTORIAL.rar | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
51
Suspicious files
85
Text files
82
Unknown types
76
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3864.48302\WINTOHDD RODTECTUTORIAL\WINTOHDD.rar | — | |
MD5:— | SHA256:— | |||
| 2036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2036.48950\WINRAR WINTOHDD RODETECTUTORIAL.rar | — | |
MD5:— | SHA256:— | |||
| 3944 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa3944.49139\WinToHDD 6.2 All Editions Multilingual RODTECTUTORIAL.rar | — | |
MD5:— | SHA256:— | |||
| 2364 | WinToHDD_Free.tmp | C:\Program Files\Hasleo\WinToHDD\bin\is-LNJSJ.tmp | executable | |
MD5:7FF16D34C610D5EF9CF5A7E43D8D20C6 | SHA256:90439FDCA599B33DC02253DA0A6C648B4412C75F1CDC29FD0FDFAB8D6BA4BB91 | |||
| 3304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3304.49511\WinToHDD 6.2 All Editions Multilingual\Readme.txt | text | |
MD5:0B43D9E766C172CB29CC5697B4070BE1 | SHA256:FB7D2B225E0B75CFBBDEE48B40282ADE2D0D3A80EDCA15E031DA7CB583AFD58B | |||
| 2364 | WinToHDD_Free.tmp | C:\Program Files\Hasleo\WinToHDD\unins000.exe | executable | |
MD5:5F4CBB5EB986D866AFDBA9A1D318A3B6 | SHA256:0033EBB4829D1612C632EAF738743E66D589E31C0037234442ED0E795A0F0F07 | |||
| 2364 | WinToHDD_Free.tmp | C:\Program Files\Hasleo\WinToHDD\bin\is-GSO33.tmp | executable | |
MD5:D795C8BB570BE33E0EA31CC0DFDB8E52 | SHA256:C65C24A34FE3B417E82DAFC87BF600DA1B78DE41D9CDCB8D3B34E82ECAB75FDC | |||
| 2364 | WinToHDD_Free.tmp | C:\Program Files\Hasleo\WinToHDD\bin\is-F7QRV.tmp | executable | |
MD5:20252B14A7A26E2BA3002C6088203E9E | SHA256:E3564A1240A3DB8183216DC065A0880B53AB533EF486B92E9135E7981939E8F4 | |||
| 2364 | WinToHDD_Free.tmp | C:\Program Files\Hasleo\WinToHDD\bin\intl.dll | executable | |
MD5:7FF16D34C610D5EF9CF5A7E43D8D20C6 | SHA256:90439FDCA599B33DC02253DA0A6C648B4412C75F1CDC29FD0FDFAB8D6BA4BB91 | |||
| 2364 | WinToHDD_Free.tmp | C:\Program Files\Hasleo\WinToHDD\bin\is-GIOPF.tmp | executable | |
MD5:DDF1C474946C543E3B31D039F50ADF89 | SHA256:CD937FCCF8C1F603C04C33D7065176D19A11C323CC7C4C763CC9C593E585E141 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
15
DNS requests
16
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
764 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2176 | msedge.exe | 239.255.255.250:1900 | — | — | — | unknown |
764 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
764 | msedge.exe | 104.21.95.81:443 | www.easyuefi.com | CLOUDFLARENET | — | unknown |
764 | msedge.exe | 142.250.185.200:443 | www.googletagmanager.com | GOOGLE | US | unknown |
764 | msedge.exe | 152.199.19.160:443 | ajax.aspnetcdn.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
www.easyuefi.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
www.googletagmanager.com |
| whitelisted |
ajax.aspnetcdn.com |
| whitelisted |
region1.google-analytics.com |
| whitelisted |
www.bing.com |
| whitelisted |