| File name: | Hola-Setup-C-HPE.exe |
| Full analysis: | https://app.any.run/tasks/532f0f42-d70f-4613-aa9d-1c233b70333f |
| Verdict: | Malicious activity |
| Analysis date: | September 01, 2024, 21:11:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 203ACCDF587DD38B24A1A5021F3F46DA |
| SHA1: | FC8F3E96A67C8A92313C9987B7F7C8E7CFC3810F |
| SHA256: | 9E65B85E4E33AACA1A3BD8AA5E2C5F67D9EC82224386B5B713479B4073FDA32D |
| SSDEEP: | 98304:7UINMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM/:gf |
MALICIOUS
Changes the autorun value in the registry
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
Actions looks like stealing of personal data
- 7zr.exe (PID: 4068)
SUSPICIOUS
Reads security settings of Internet Explorer
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 1124)
Reads the date of Windows installation
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
Application launched itself
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- hola_svc.exe (PID: 964)
Executable content was dropped or overwritten
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- net_updater64.exe (PID: 1964)
Drops the executable file immediately after the start
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- net_updater64.exe (PID: 1964)
Drops 7-zip archiver for unpacking
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
Drops a system driver (possible attempt to evade defenses)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
Creates a software uninstall entry
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
Checks Windows Trust Settings
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- net_updater64.exe (PID: 1964)
Process drops legitimate windows executable
- net_updater64.exe (PID: 2136)
The process drops C-runtime libraries
- net_updater64.exe (PID: 2136)
Executes as Windows Service
- net_updater64.exe (PID: 3980)
- hola_svc.exe (PID: 964)
- WmiApSrv.exe (PID: 4020)
Detected use of alternative data streams (AltDS)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- net_updater64.exe (PID: 1964)
Creates file in the systems drive root
- hola_svc.exe (PID: 964)
The process checks if it is being run in the virtual environment
- net_updater64.exe (PID: 3980)
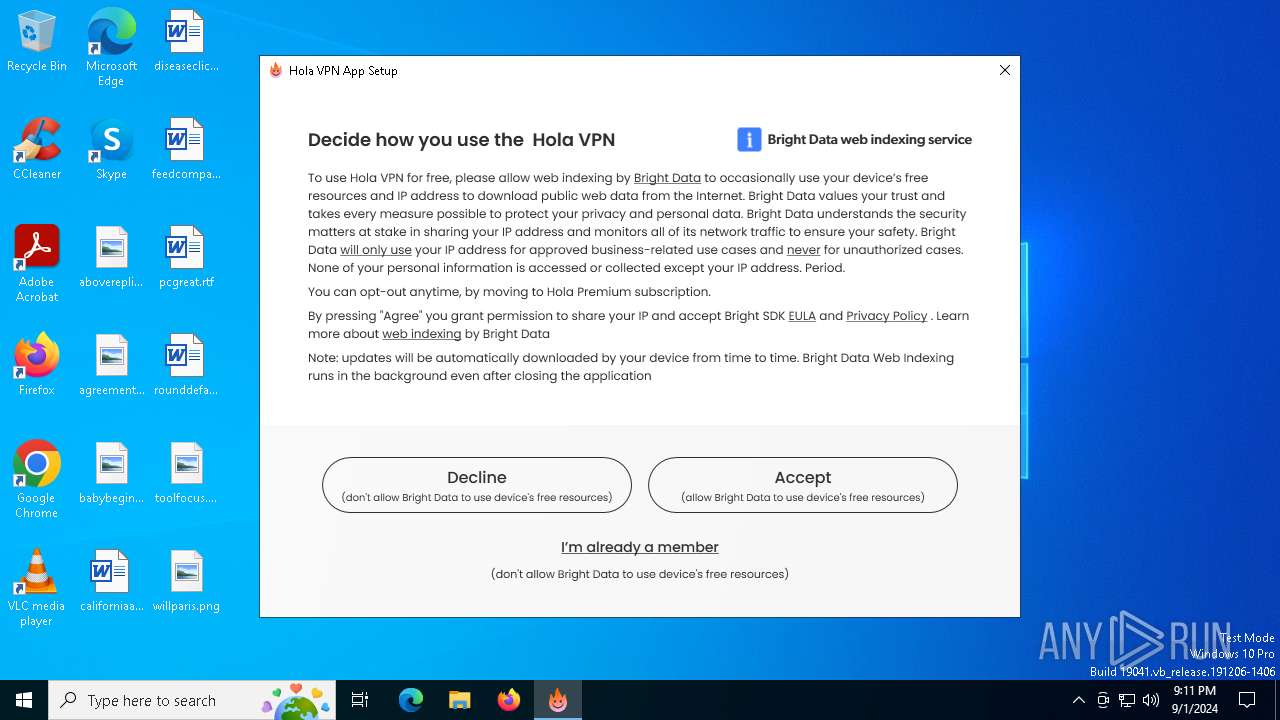
Checks for external IP
- net_updater64.exe (PID: 3980)
Potential Corporate Privacy Violation
- net_updater64.exe (PID: 3980)
Connects to unusual port
- hola_svc.exe (PID: 964)
INFO
Reads the computer name
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- net_updater64.exe (PID: 2136)
- test_wpf.exe (PID: 6372)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- test_wpf.exe (PID: 6156)
- hola_svc.exe (PID: 964)
- idle_report.exe (PID: 1944)
- net_updater64.exe (PID: 1964)
- test_wpf.exe (PID: 3176)
- test_wpf.exe (PID: 7020)
- Hola-Setup-x64-1.228.101.exe (PID: 6460)
- 7zr.exe (PID: 4068)
Reads the machine GUID from the registry
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- net_updater64.exe (PID: 2136)
- test_wpf.exe (PID: 6372)
- net_updater64.exe (PID: 3980)
- test_wpf.exe (PID: 3176)
- net_updater64.exe (PID: 1124)
- hola_svc.exe (PID: 964)
- idle_report.exe (PID: 1944)
- net_updater64.exe (PID: 1964)
- test_wpf.exe (PID: 7020)
- test_wpf.exe (PID: 6156)
Reads Environment values
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- net_updater64.exe (PID: 1964)
Disables trace logs
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- net_updater64.exe (PID: 3980)
- rasdial.exe (PID: 5284)
- hola_svc.exe (PID: 964)
Checks proxy server information
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- net_updater64.exe (PID: 2136)
Create files in a temporary directory
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- Hola-Setup-x64-1.228.101.exe (PID: 6460)
Reads the software policy settings
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- net_updater64.exe (PID: 1964)
- Hola-Setup-x64-1.228.101.exe (PID: 6460)
The process uses the downloaded file
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
Process checks computer location settings
- Hola-Setup-C-HPE.exe (PID: 7140)
- Hola-Setup-C-HPE.exe (PID: 4980)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 1124)
- net_updater64.exe (PID: 1964)
- net_updater64.exe (PID: 3980)
Checks supported languages
- Hola-Setup-C-HPE.exe (PID: 4980)
- Hola-Setup-C-HPE.exe (PID: 2232)
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- net_updater64.exe (PID: 2136)
- Hola-Setup-C-HPE.exe (PID: 7140)
- test_wpf.exe (PID: 6372)
- net_updater64.exe (PID: 3980)
- test_wpf.exe (PID: 3176)
- net_updater64.exe (PID: 1124)
- test_wpf.exe (PID: 6156)
- idle_report.exe (PID: 1944)
- hola_svc.exe (PID: 6396)
- net_updater64.exe (PID: 1964)
- test_wpf.exe (PID: 7020)
- Hola-Setup-x64-1.228.101.exe (PID: 6460)
- hola_svc.exe (PID: 6704)
- 7zr.exe (PID: 4068)
- hola_svc.exe (PID: 964)
Creates files in the program directory
- Hola-Setup-x64-1.228.101.exe (PID: 3316)
- net_updater64.exe (PID: 2136)
- net_updater64.exe (PID: 3980)
- net_updater64.exe (PID: 1124)
- hola_svc.exe (PID: 964)
- net_updater64.exe (PID: 1964)
- 7zr.exe (PID: 4068)
Creates files or folders in the user directory
- net_updater64.exe (PID: 2136)
Reads CPU info
- net_updater64.exe (PID: 3980)
Reads the time zone
- net_updater64.exe (PID: 3980)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2094:07:16 03:28:36+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 2917888 |
| InitializedDataSize: | 414208 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x2ca596 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.227.226.0 |
| ProductVersionNumber: | 1.227.226.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | - |
| CompanyName: | Hola VPN Ltd. |
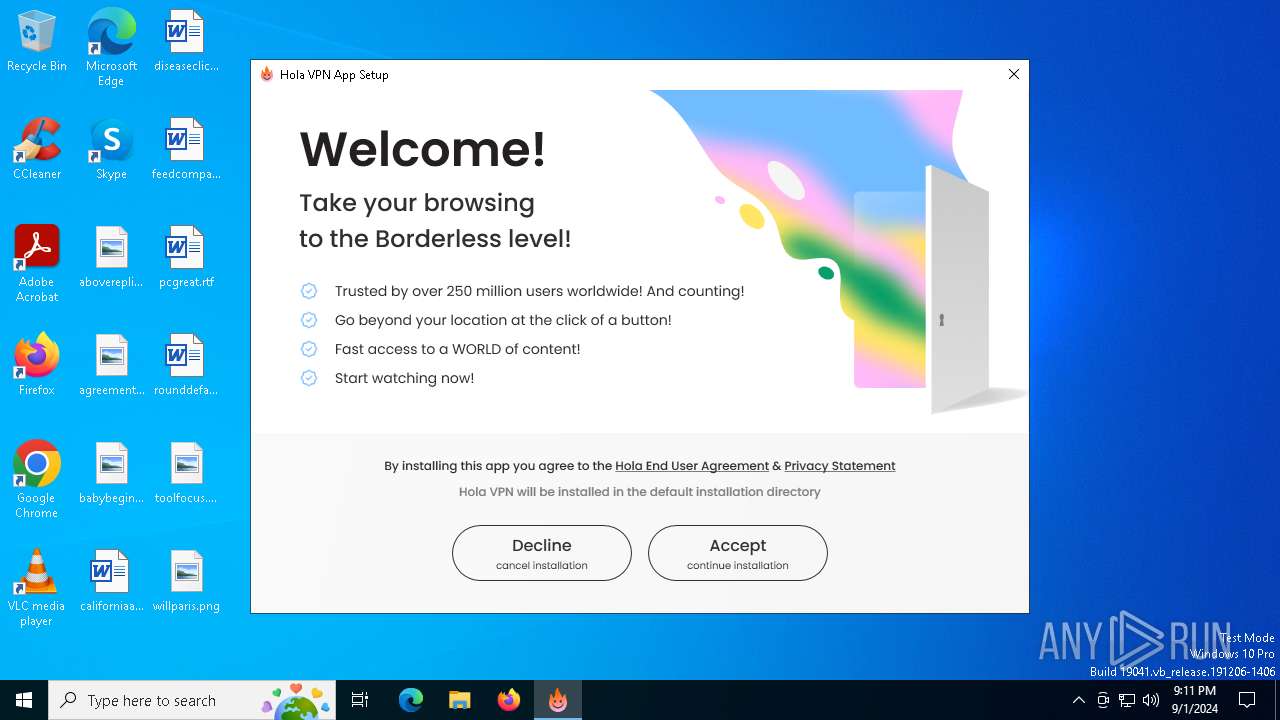
| FileDescription: | Hola VPN App Setup |
| FileVersion: | 1.227.226.0 |
| InternalName: | hola_setup.exe |
| LegalCopyright: | Copyright © 2023 Hola VPN Ltd. |
| LegalTrademarks: | - |
| OriginalFileName: | hola_setup.exe |
| ProductName: | Hola Setup |
| ProductVersion: | 1.227.226.0 |
| AssemblyVersion: | 1.227.226.0 |
Total processes
156
Monitored processes
28
Malicious processes
7
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 964 | "C:\Program Files\Hola\app\hola_svc.exe" --service | C:\Program Files\Hola\app\hola_svc.exe | services.exe | ||||||||||||
User: SYSTEM Company: Hola Networks Ltd. Integrity Level: SYSTEM Description: Hola VPN Service Version: 1.228.101 Modules
| |||||||||||||||
| 1124 | "C:\Program Files\Hola\app\net_updater64.exe" --uuid | C:\Program Files\Hola\app\net_updater64.exe | Hola-Setup-x64-1.228.101.exe | ||||||||||||
User: admin Company: BrightData Ltd. (certified) Integrity Level: HIGH Description: BrightData service allows free use of certain features in an app you installed Exit code: 0 Version: 1.474.630 Modules
| |||||||||||||||
| 1140 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net_updater64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1944 | C:\ProgramData\BrightData\108a47921d08860d64656218998ab66204caf497\idle_report.exe --id 79515 --screen | C:\ProgramData\BrightData\108a47921d08860d64656218998ab66204caf497\idle_report.exe | — | net_updater64.exe | |||||||||||
User: admin Company: BrightData Ltd. Integrity Level: MEDIUM Description: idle_report Exit code: 0 Version: 1.474.630 Modules
| |||||||||||||||
| 1964 | "C:\Program Files\Hola\app\net_updater64.exe" --uuid | C:\Program Files\Hola\app\net_updater64.exe | hola_svc.exe | ||||||||||||
User: SYSTEM Company: BrightData Ltd. (certified) Integrity Level: SYSTEM Description: BrightData service allows free use of certain features in an app you installed Exit code: 0 Version: 1.474.630 Modules
| |||||||||||||||
| 1964 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7zr.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2008 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net_updater64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | net_updater64.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2136 | "C:\Program Files\Hola\app\net_updater64.exe" --install win_hola.org --campaign hpe | C:\Program Files\Hola\app\net_updater64.exe | Hola-Setup-x64-1.228.101.exe | ||||||||||||
User: admin Company: BrightData Ltd. (certified) Integrity Level: HIGH Description: BrightData service allows free use of certain features in an app you installed Exit code: 0 Version: 1.474.630 Modules
| |||||||||||||||
| 2232 | "C:\Users\admin\AppData\Local\Temp\Hola-Setup-C-HPE.exe" --monitor 1988 | C:\Users\admin\AppData\Local\Temp\Hola-Setup-C-HPE.exe | Hola-Setup-C-HPE.exe | ||||||||||||
User: admin Company: Hola VPN Ltd. Integrity Level: HIGH Description: Hola VPN App Setup Version: 1.227.226.0 Modules
| |||||||||||||||
Total events
39 197
Read events
39 070
Write events
126
Delete events
1
Modification events
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7140) Hola-Setup-C-HPE.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\Hola-Setup-C-HPE_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
Executable files
16
Suspicious files
104
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | Hola-Setup-x64-1.228.101.exe | C:\Users\admin\AppData\Local\Temp\install.log | binary | |
MD5:8816ED3D5B193B24247ABC0B9EE7E9A8 | SHA256:E7336087162D223A8F44381131DE211CCDF29FA24B57889BC175797C348CB50D | |||
| 7140 | Hola-Setup-C-HPE.exe | C:\Users\admin\AppData\Local\Temp\hola_setup.log | binary | |
MD5:FDC896A1BC41C185B243C8A81B3B47EE | SHA256:93909261E351FA68F7B792B2D28E56DFA5B79D542B5C0D87972002C01DA14DF3 | |||
| 3316 | Hola-Setup-x64-1.228.101.exe | C:\Program Files\Hola\app\hola.exe | executable | |
MD5:9112BEA314BB9692FFBCFDEA07BB21CF | SHA256:A3BC9F44FFF837B5DD1D74E033C054D31699AE31CE256F7FFC03F8367A0DF098 | |||
| 3316 | Hola-Setup-x64-1.228.101.exe | C:\Program Files\Hola\app\lum_sdk64.dll | executable | |
MD5:B0D95A0B3D9DA0F1A053E5461A387849 | SHA256:24347DE0C339F3E635CC9FF4C07EE60D3E6908D282D7AEE20F3545A7C330932C | |||
| 3316 | Hola-Setup-x64-1.228.101.exe | C:\Program Files\Hola\app\README.txt | text | |
MD5:E2F387B53A340A507BBB2A28D7917484 | SHA256:A2B79E73F4F317AD3F44A383722F05E739CF260C49E54AD6B7001CB7AF6BD252 | |||
| 2136 | net_updater64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:1DC693C3D88DB65500DE62B9143630BF | SHA256:CA1B351EF51C31419E805DB90EAFB14E953F49E7DFB02E0BD0B12771AB866005 | |||
| 2136 | net_updater64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8EC9B1D0ABBD7F98B401D425828828CE_7BC6BAD757FCD9C147D141E8A9D5A2A0 | binary | |
MD5:64D49D48911EE76D59C46C91B31004A7 | SHA256:34B3F64FEF357F78FBBD31ECE5EF643221BEB6BDA2DA5B2A535F8D62A8094C6C | |||
| 2136 | net_updater64.exe | C:\ProgramData\BrightData\108a47921d08860d64656218998ab66204caf497\20240901_211154_01_install_1.474.630.log | binary | |
MD5:68B329DA9893E34099C7D8AD5CB9C940 | SHA256:01BA4719C80B6FE911B091A7C05124B64EEECE964E09C058EF8F9805DACA546B | |||
| 2136 | net_updater64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\698460A0B6E60F2F602361424D832905_8BB23D43DE574E82F2BEE0DF0EC47EEB | binary | |
MD5:0F8911F4878D271F3A8367F5F448F586 | SHA256:6CAB4D125EB47091CA9F77194F35EC6A1A563E11CBCFF921B584057AE55924A8 | |||
| 2136 | net_updater64.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C8E534EE129F27D55460CE17FD628216_1130D9B25898B0DB0D4F04DC5B93F141 | binary | |
MD5:7327332A7FF3290684FEBF9728F937CF | SHA256:BC1BF7D60E813F1741B7CDB35FE0B74F8495E3D5066649B0705FF06808D25432 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
146
DNS requests
38
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1764 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2136 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
2136 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAdTF0YC22Gdh8cnyPwWxE0%3D | unknown | — | — | whitelisted |
2136 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
3980 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
3980 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
3980 | net_updater64.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAdTF0YC22Gdh8cnyPwWxE0%3D | unknown | — | — | whitelisted |
964 | hola_svc.exe | GET | 200 | 142.250.186.164:80 | http://142.250.186.164:80/blank.html | unknown | — | — | unknown |
964 | hola_svc.exe | GET | 301 | 23.35.237.160:80 | http://i.s-microsoft.com/library/svy/close.gif | unknown | — | — | whitelisted |
6204 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6856 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
892 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7140 | Hola-Setup-C-HPE.exe | 23.22.252.240:443 | perr.hola.org | AMAZON-AES | US | whitelisted |
7140 | Hola-Setup-C-HPE.exe | 54.225.121.9:443 | hola.org | AMAZON-AES | US | whitelisted |
4980 | Hola-Setup-C-HPE.exe | 54.225.121.9:443 | hola.org | AMAZON-AES | US | whitelisted |
3260 | svchost.exe | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2232 | Hola-Setup-C-HPE.exe | 54.225.121.9:443 | hola.org | AMAZON-AES | US | whitelisted |
4980 | Hola-Setup-C-HPE.exe | 23.22.252.240:443 | perr.hola.org | AMAZON-AES | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
perr.hola.org |
| whitelisted |
hola.org |
| whitelisted |
client.wns.windows.com |
| whitelisted |
hola-rmt-update.b-cdn.net |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.hola.org |
| whitelisted |
perr.lum-sdk.io |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
3980 | net_updater64.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
2 ETPRO signatures available at the full report