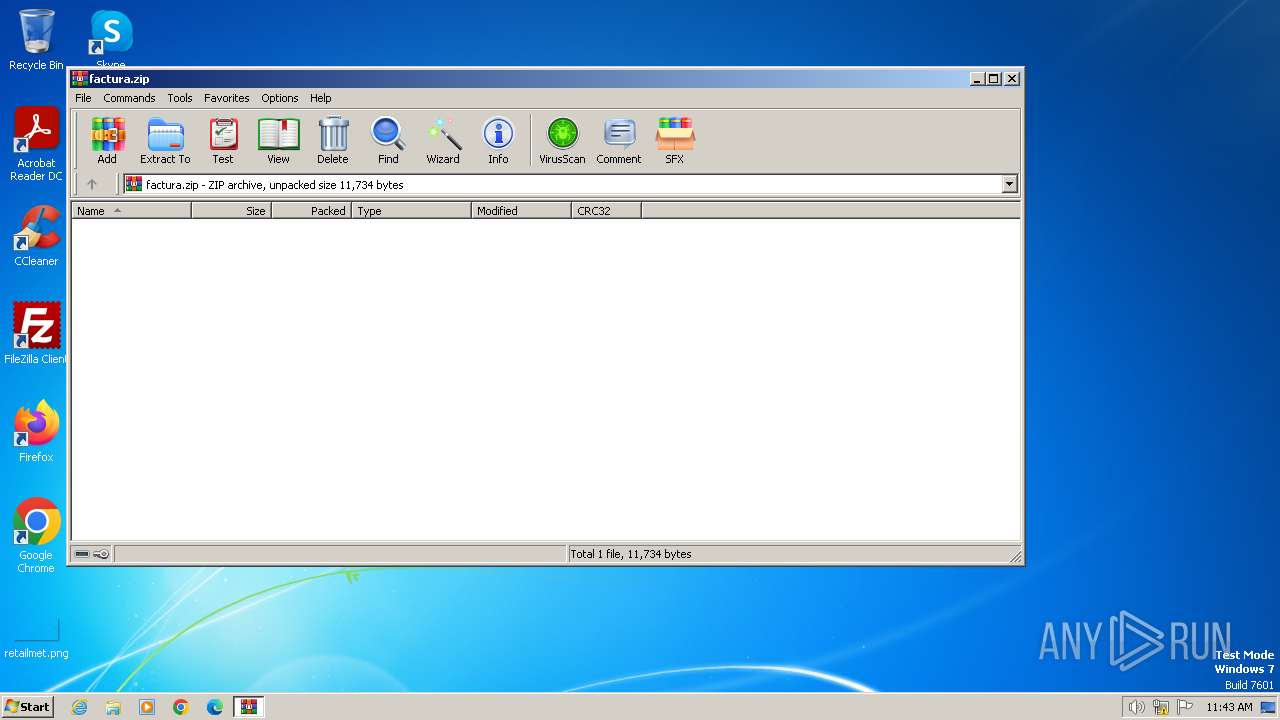
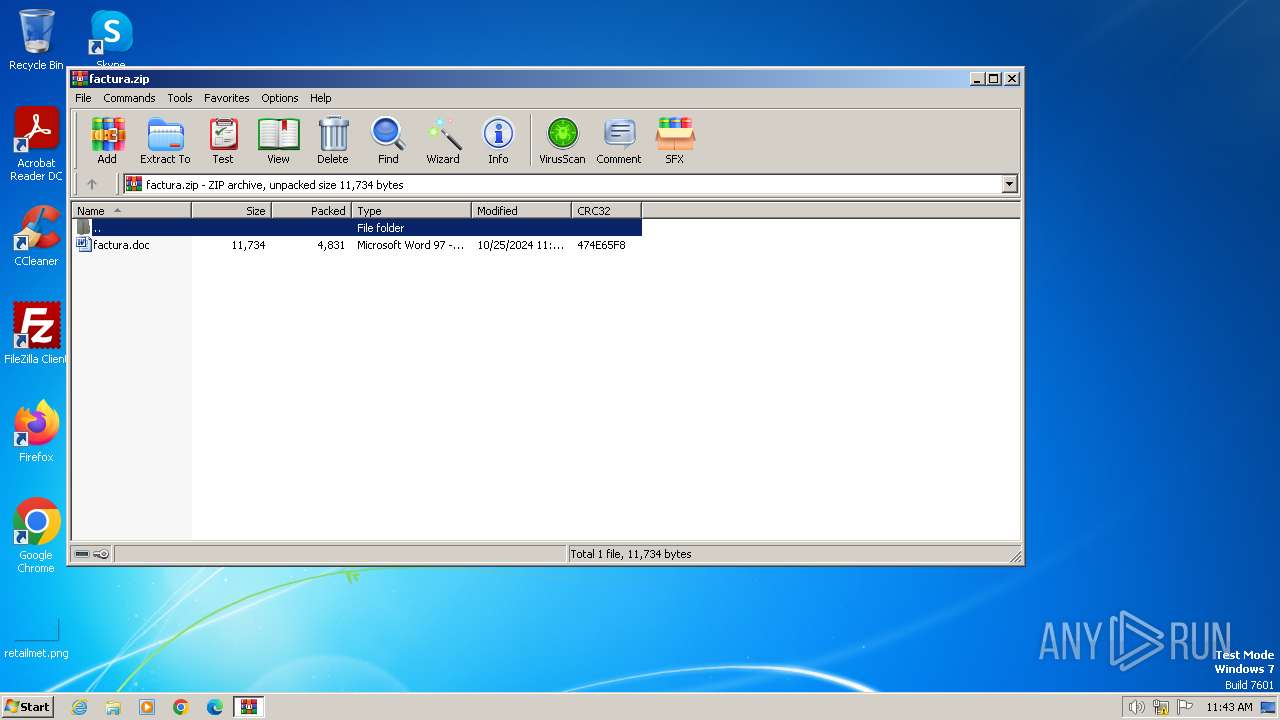
| File name: | factura.zip |
| Full analysis: | https://app.any.run/tasks/5d10a1da-7f1e-48b0-a590-426555bf2a34 |
| Verdict: | Malicious activity |
| Analysis date: | October 25, 2024, 10:43:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 8FBC43847462DCC1B26FABF8ED9BB331 |
| SHA1: | A7228129E74B3AFE7676447DC8E45AEB89EEB393 |
| SHA256: | 9E5B9F83A78E116387346AD010D4A0F5A81A0B12BDD06CEEFE6183477ADB8977 |
| SSDEEP: | 192:QDQ+U/+StuMWBKgCqlC5/XP3bxuGC2p3+NjyjwWrFVB:QD+8M1gCq85//TC2p3+xyMuB |
MALICIOUS
Equation Editor starts application (likely CVE-2017-11882)
- EQNEDT32.EXE (PID: 3592)
Suspicious connection from the Equation Editor
- EQNEDT32.EXE (PID: 3592)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1652)
Reads the Internet Settings
- EQNEDT32.EXE (PID: 3592)
Reads security settings of Internet Explorer
- EQNEDT32.EXE (PID: 3592)
INFO
The process uses the downloaded file
- WINWORD.EXE (PID: 1504)
- WinRAR.exe (PID: 1652)
Manual execution by a user
- WINWORD.EXE (PID: 1504)
- wmpnscfg.exe (PID: 3940)
Checks supported languages
- EQNEDT32.EXE (PID: 3592)
- wmpnscfg.exe (PID: 3940)
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 3592)
Reads the computer name
- EQNEDT32.EXE (PID: 3592)
- wmpnscfg.exe (PID: 3940)
Checks proxy server information
- EQNEDT32.EXE (PID: 3592)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:10:25 03:35:44 |
| ZipCRC: | 0x474e65f8 |
| ZipCompressedSize: | 4831 |
| ZipUncompressedSize: | 11734 |
| ZipFileName: | factura.doc |
Total processes
41
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1504 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\factura\factura.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 1652 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\factura.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3592 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\microsoft shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3940 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 512
Read events
4 584
Write events
596
Delete events
332
Modification events
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\factura.zip | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1652) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1504 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRE113.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 1504 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:1D40407AC41EBDAD0C5D18C07E1D2FA5 | SHA256:09D01A6EA502229AFC1BD37AD411F12B8231FBD45F2902A2C889C1C563144F55 | |||
| 1504 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:0B9F91949DBE299F7F4AB54E24DF3843 | SHA256:6940E5B37E2C66B80F16215BF757177FC22E450778D14C8C4702437A888905F5 | |||
| 1652 | WinRAR.exe | C:\Users\admin\Desktop\factura\factura.doc | text | |
MD5:05C137D8E79CE59ED6E4B7CD78E5B8A2 | SHA256:5A31C77293AF2920D7020D5D0236691ADCEA2C57C2716658CE118A5CBA9D4913 | |||
| 1504 | WINWORD.EXE | C:\Users\admin\Desktop\factura\~$actura.doc | pgc | |
MD5:E045BE65A5C5AB6D4D7F2BABD0212D31 | SHA256:55FE5C4E59276C6AD4620F4EF59919A3B5D54E06331C85ACBF154AC75C5D2232 | |||
| 1504 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\factura.doc.LNK | binary | |
MD5:E040DBAC2E6D99911A3698ACC8B9F5BE | SHA256:27BCCB799B72C959B5D6D6F0CE952C4B606EC132A42377749B29A794A1BC3322 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
8
DNS requests
2
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 404 | 185.36.74.48:80 | http://seed-bc.com/juop4/plwr/mklo/rbn/jan2.exe | unknown | — | — | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3592 | EQNEDT32.EXE | 185.36.74.48:80 | seed-bc.com | Fastweb | IT | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
seed-bc.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3592 | EQNEDT32.EXE | Potentially Bad Traffic | ET MALWARE Terse alphanumeric executable downloader high likelihood of being hostile |