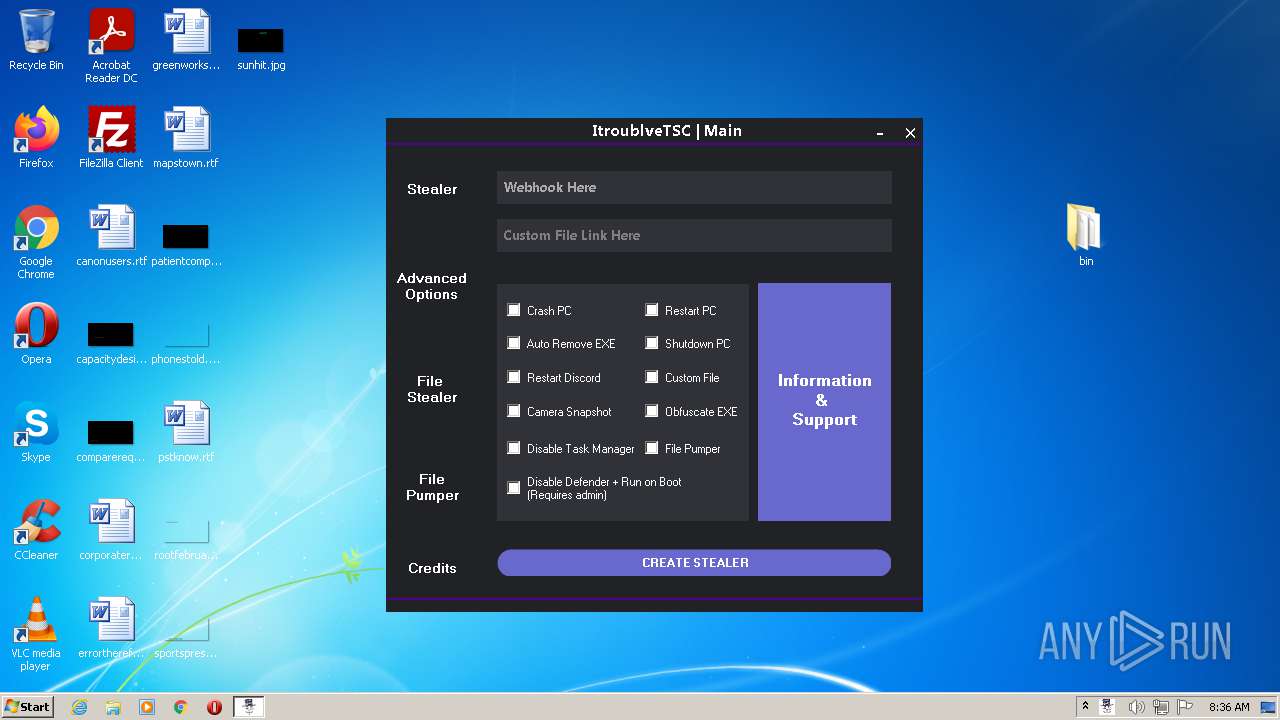
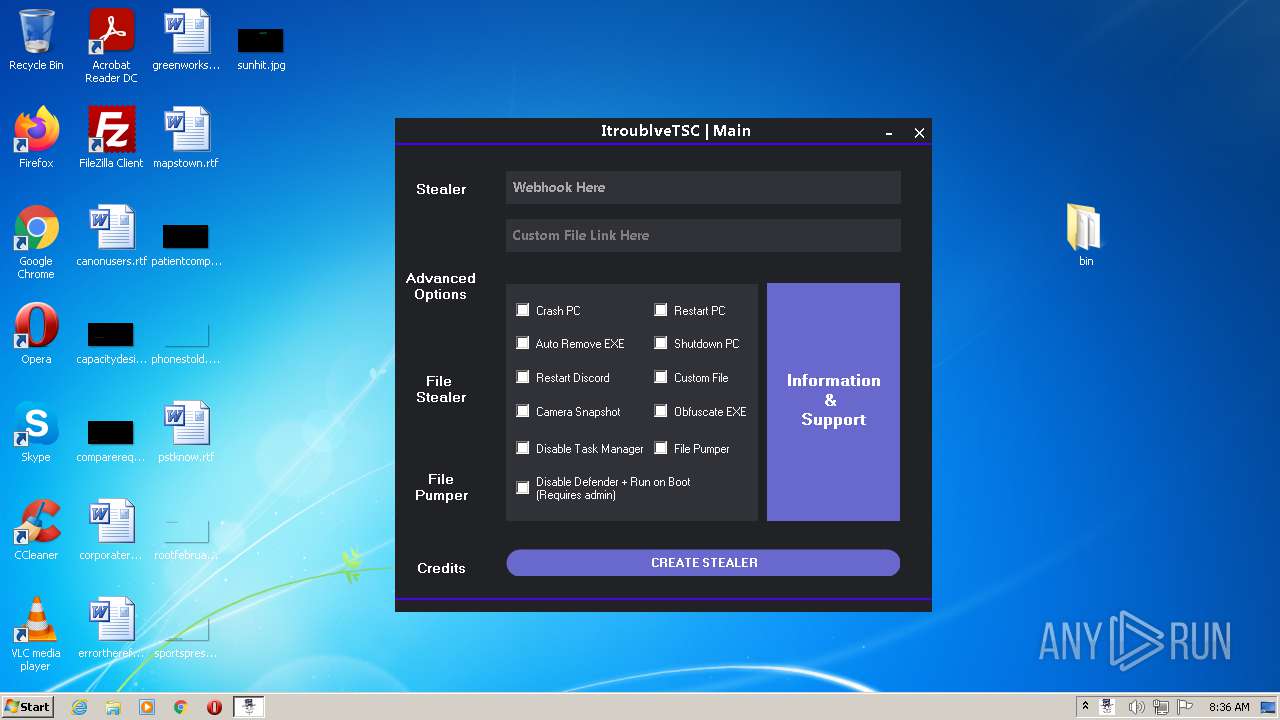
| URL: | https://github.com/Itroublve/ItroublveTSC/releases/download/6.1/ItroublveTSC.v6.Fix.7.2.rar |
| Full analysis: | https://app.any.run/tasks/c7a6e741-6934-43a5-8499-9903e7d09cc8 |
| Verdict: | Malicious activity |
| Analysis date: | August 19, 2021, 07:35:31 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | ABA4D566D8D35A2B0BAC7D8D4CECBC06 |
| SHA1: | 052BA2CC0F5D0F0F408FEBF8CFD00390A1DDBA8B |
| SHA256: | 9E58F28797037740CCB580D98CCD938FC97AD5902822C134177E845EEB594825 |
| SSDEEP: | 3:N8tEdSzdgdU2KJMkCTPpSdU2QLWSjLO:2ukSvSMb4vQLBLO |
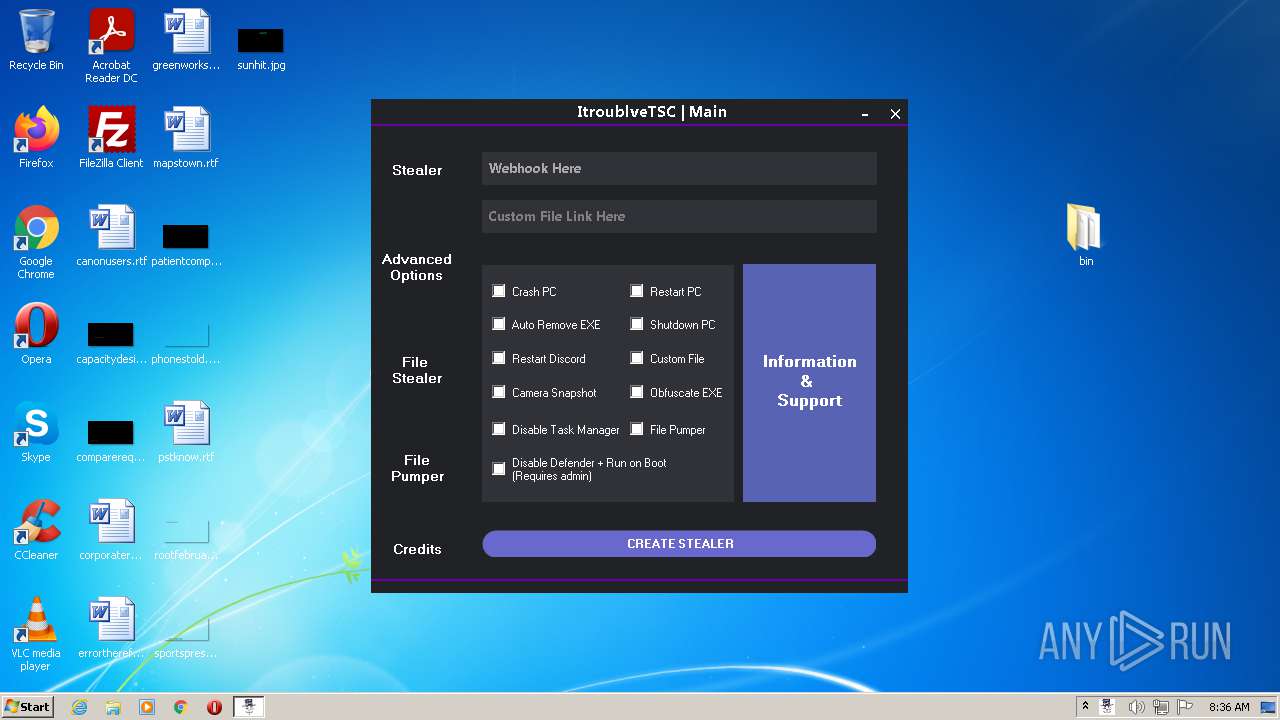
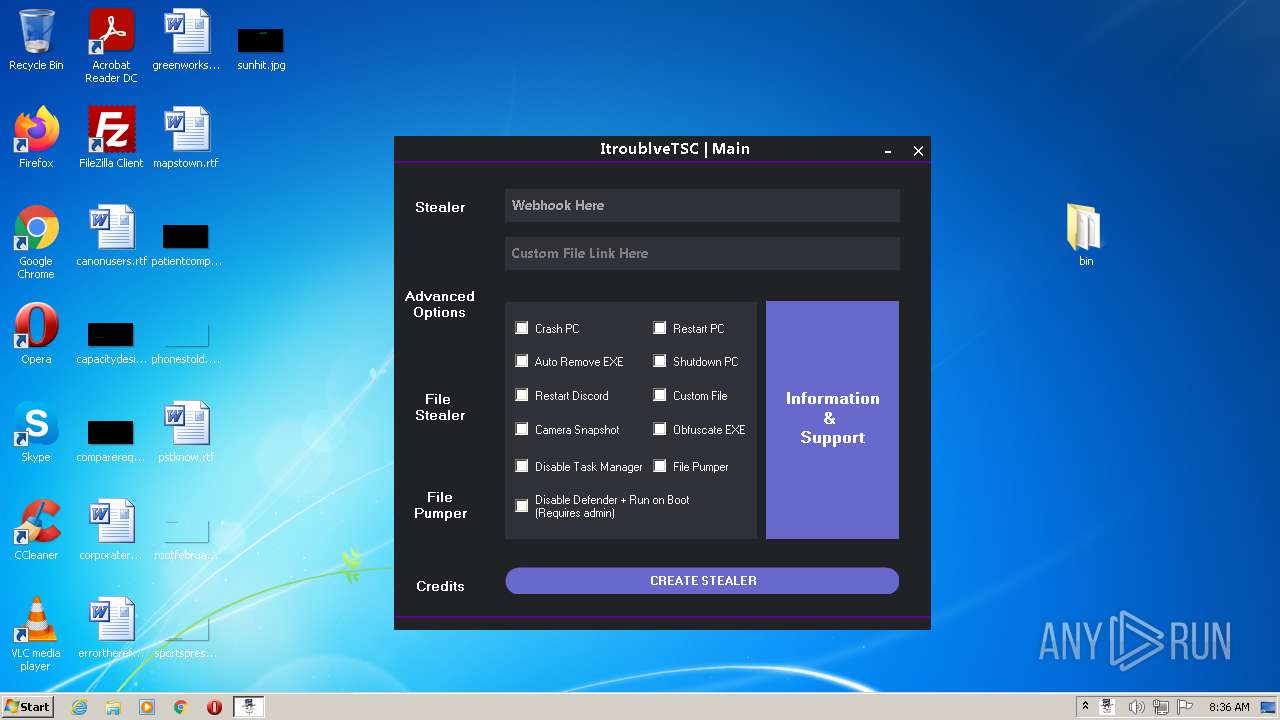
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3864)
Application was dropped or rewritten from another process
- ItroublveTSC.exe (PID: 2372)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1256)
Reads the computer name
- WinRAR.exe (PID: 1808)
- ItroublveTSC.exe (PID: 2372)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1808)
Checks supported languages
- WinRAR.exe (PID: 1808)
- ItroublveTSC.exe (PID: 2372)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1808)
Reads Environment values
- ItroublveTSC.exe (PID: 2372)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3820)
Reads the computer name
- iexplore.exe (PID: 1256)
- iexplore.exe (PID: 3820)
Reads the date of Windows installation
- iexplore.exe (PID: 3820)
Checks supported languages
- iexplore.exe (PID: 1256)
- iexplore.exe (PID: 3820)
Checks Windows Trust Settings
- iexplore.exe (PID: 1256)
- iexplore.exe (PID: 3820)
Application launched itself
- iexplore.exe (PID: 3820)
Manual execution by user
- ItroublveTSC.exe (PID: 2372)
Reads settings of System Certificates
- iexplore.exe (PID: 1256)
Modifies the phishing filter of IE
- iexplore.exe (PID: 3820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1256 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3820 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1808 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\ItroublveTSC.v6.Fix.7.2.rar" | C:\Program Files\WinRAR\WinRAR.exe | iexplore.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2372 | "C:\Users\admin\Desktop\ItroublveTSC.exe" | C:\Users\admin\Desktop\ItroublveTSC.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: ItroublveTSC Exit code: 0 Version: 6.0.0.0 Modules
| |||||||||||||||
| 3820 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://github.com/Itroublve/ItroublveTSC/releases/download/6.1/ItroublveTSC.v6.Fix.7.2.rar" | C:\Program Files\Internet Explorer\iexplore.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3864 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe9_ Global\UsGthrCtrlFltPipeMssGthrPipe9 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
Total events
10 177
Read events
10 067
Write events
109
Delete events
1
Modification events
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30905548 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30905548 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
14
Suspicious files
10
Text files
29
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3864 | SearchProtocolHost.exe | C:\Users\admin\Downloads\ItroublveTSC.v6.Fix.7.2.rar.w3k3vsc.partial | — | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\Downloads\ItroublveTSC.v6.Fix.7.2.rar | — | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFA81A76490C3CD090.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2A7611428D62805A3E4E5BC4103D82E4_D0FA13DADFB59BDF00C474952E166CC1 | binary | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | binary | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\ItroublveTSC.v6.Fix.7.2[1].rar | compressed | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\35DDEDF268117918D1D277A171D8DF7B_3D5FFC72733D0751B94B517D33876F5B | der | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EDC238BFF48A31D55A97E1E93892934B_C20E0DA2D0F89FE526E1490F4A2EE5AB | der | |
MD5:— | SHA256:— | |||
| 1256 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2A7611428D62805A3E4E5BC4103D82E4_D0FA13DADFB59BDF00C474952E166CC1 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
8
DNS requests
6
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1672 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?0968e9df1e2aec06 | US | — | — | whitelisted |
1672 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ed53382d525bee76 | US | — | — | whitelisted |
1256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTGMlruL6P9M9B3if1rTM7wyj%2FQKQQUUGGmoNI1xBEqII0fD6xC8M0pz0sCEA6L83cNktGW8Lth%2BTxBZr4%3D | US | der | 280 b | whitelisted |
1256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAJJPgf6njdaLbvGHZRDD88%3D | US | der | 471 b | whitelisted |
1256 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?cc400e3b380bef51 | US | compressed | 4.70 Kb | whitelisted |
1256 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9faa5d4c18e82370 | US | compressed | 4.70 Kb | whitelisted |
1256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAZnA1u7FP1jr8DWqFNO%2FhY%3D | US | der | 471 b | whitelisted |
1256 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEATh56TcXPLzbcArQrhdFZ8%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1256 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1256 | iexplore.exe | 185.199.110.154:443 | github-releases.githubusercontent.com | GitHub, Inc. | NL | suspicious |
1256 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1672 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
1256 | iexplore.exe | 140.82.121.3:443 | github.com | — | US | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
github.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
github-releases.githubusercontent.com |
| whitelisted |
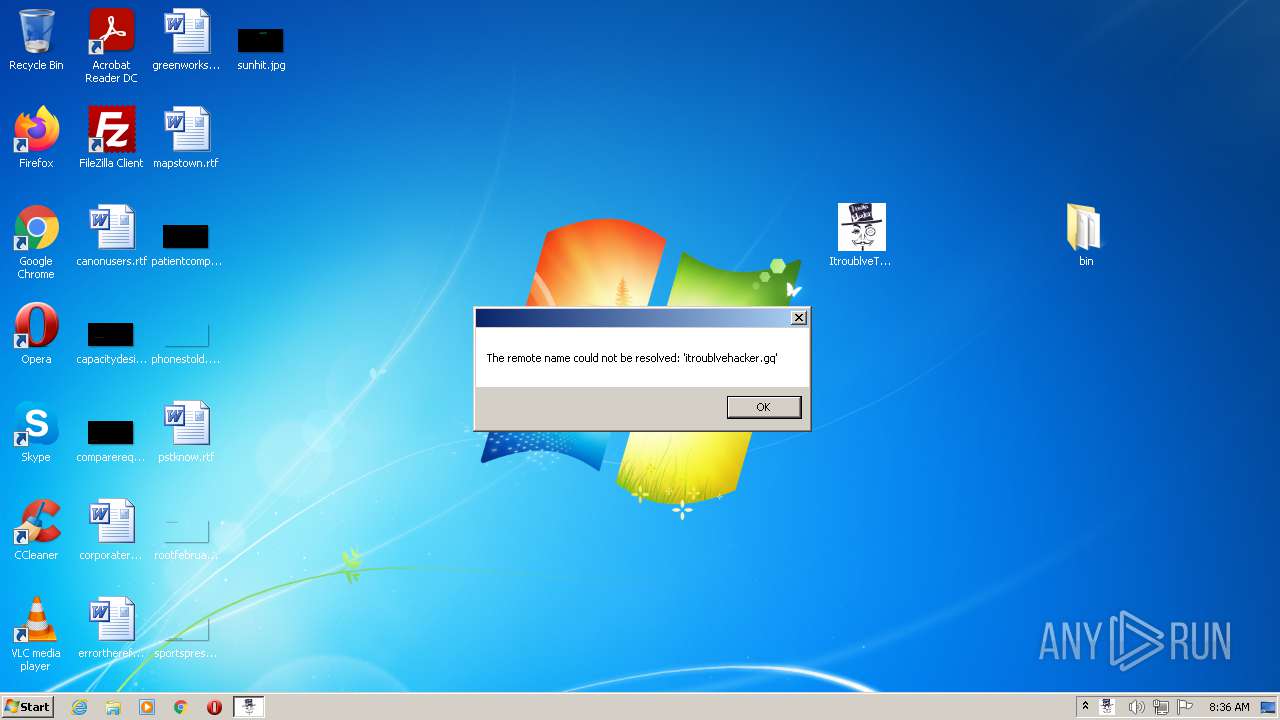
itroublvehacker.gq |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .gq Domain |