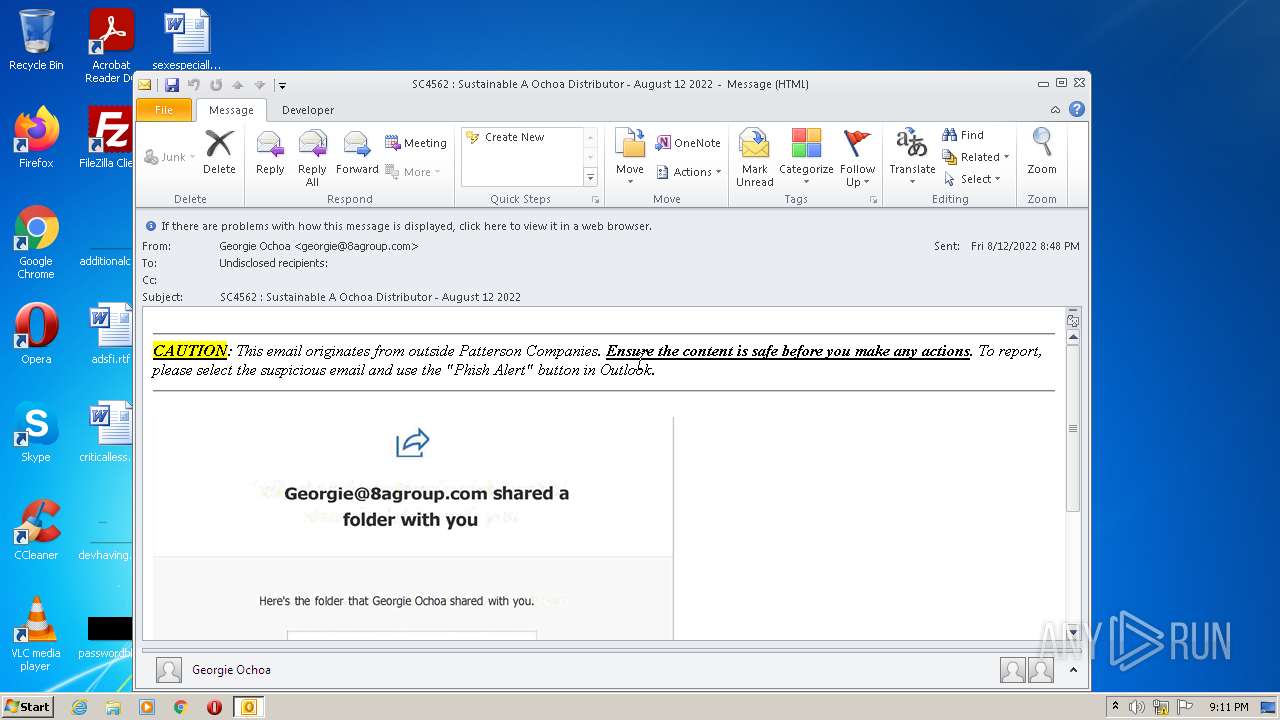
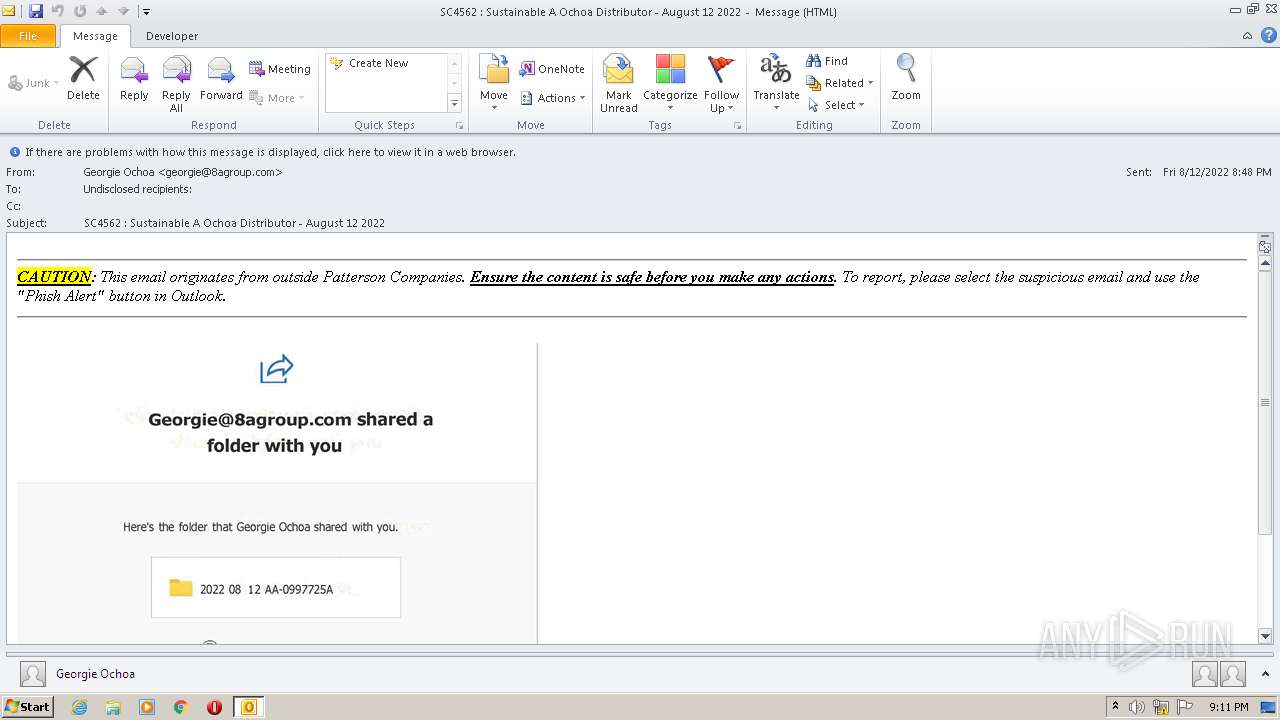
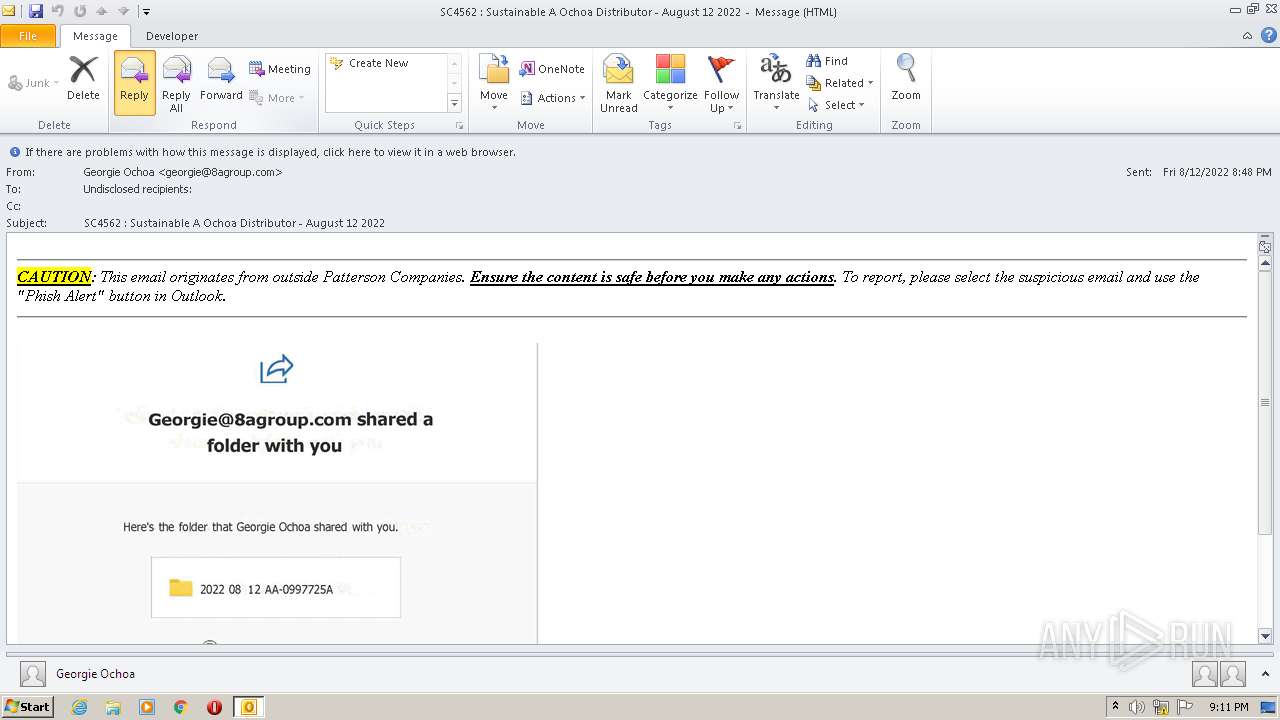
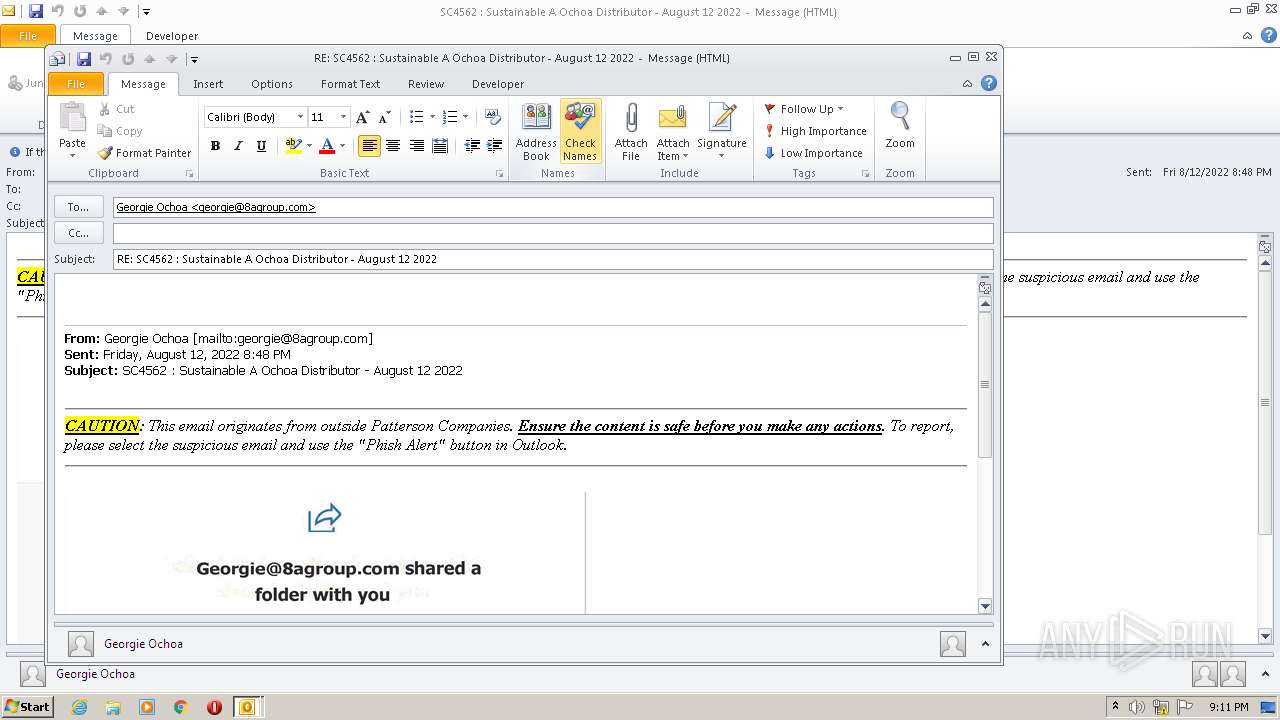
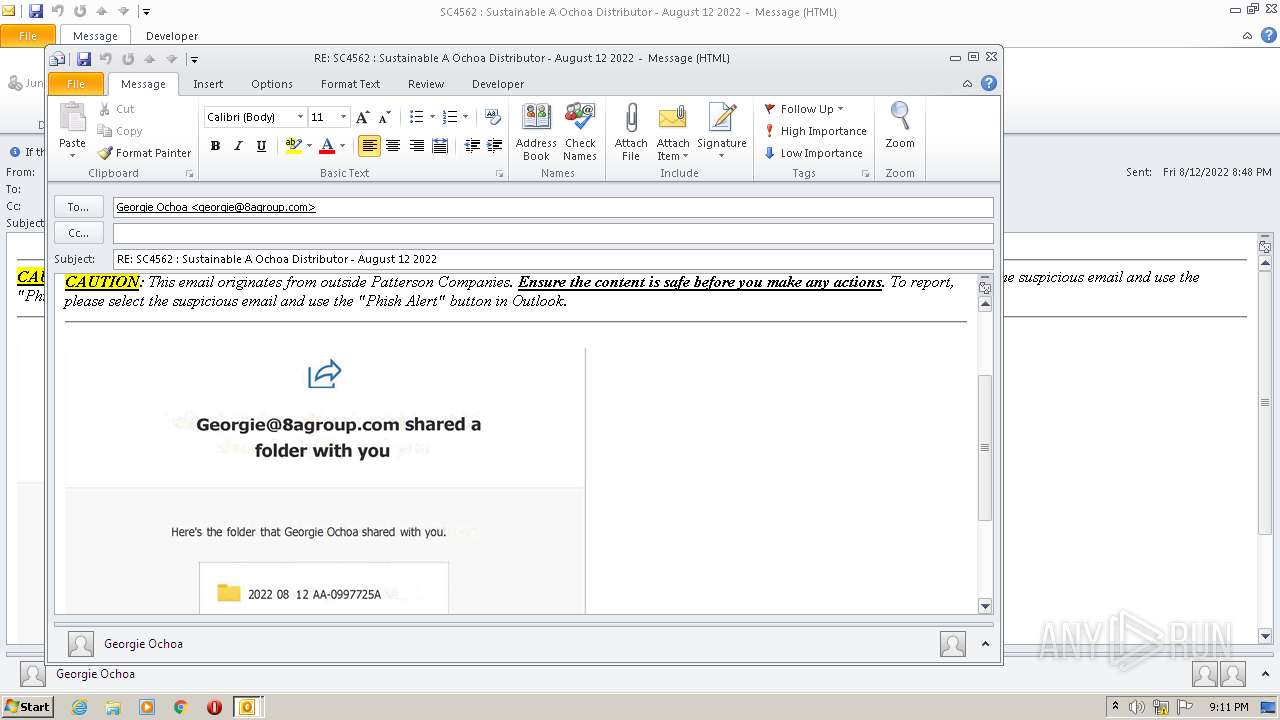
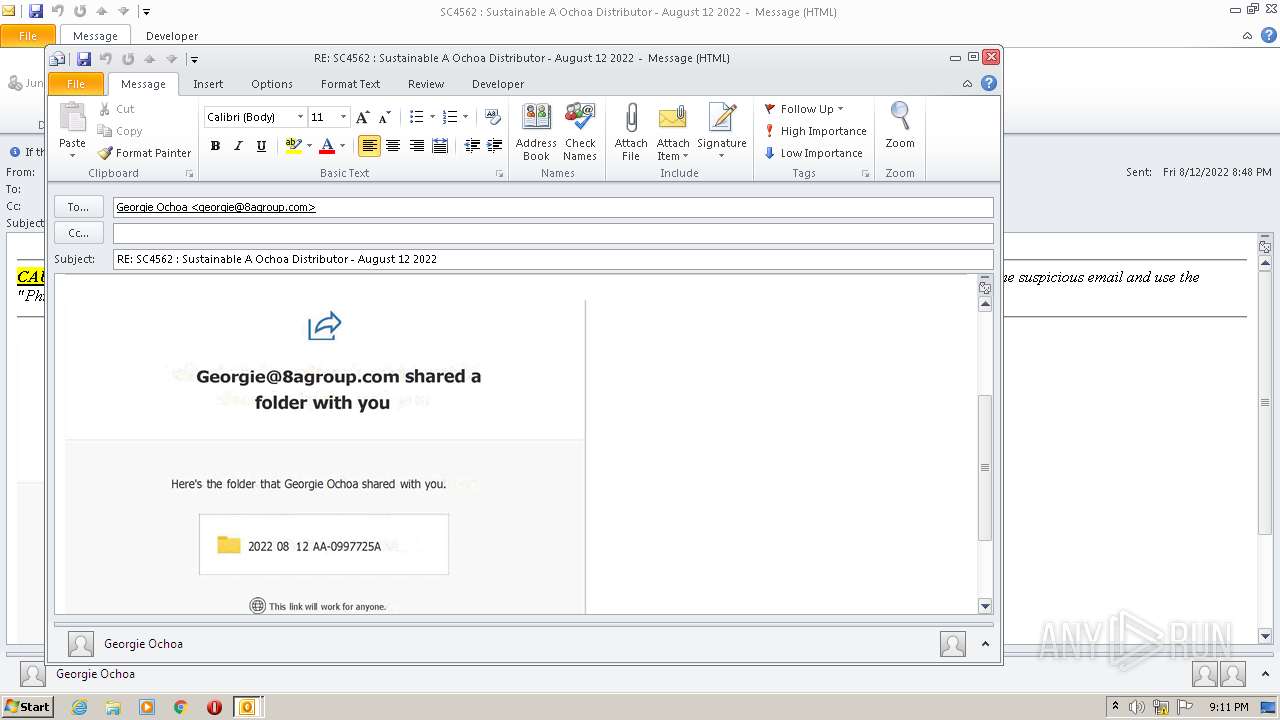
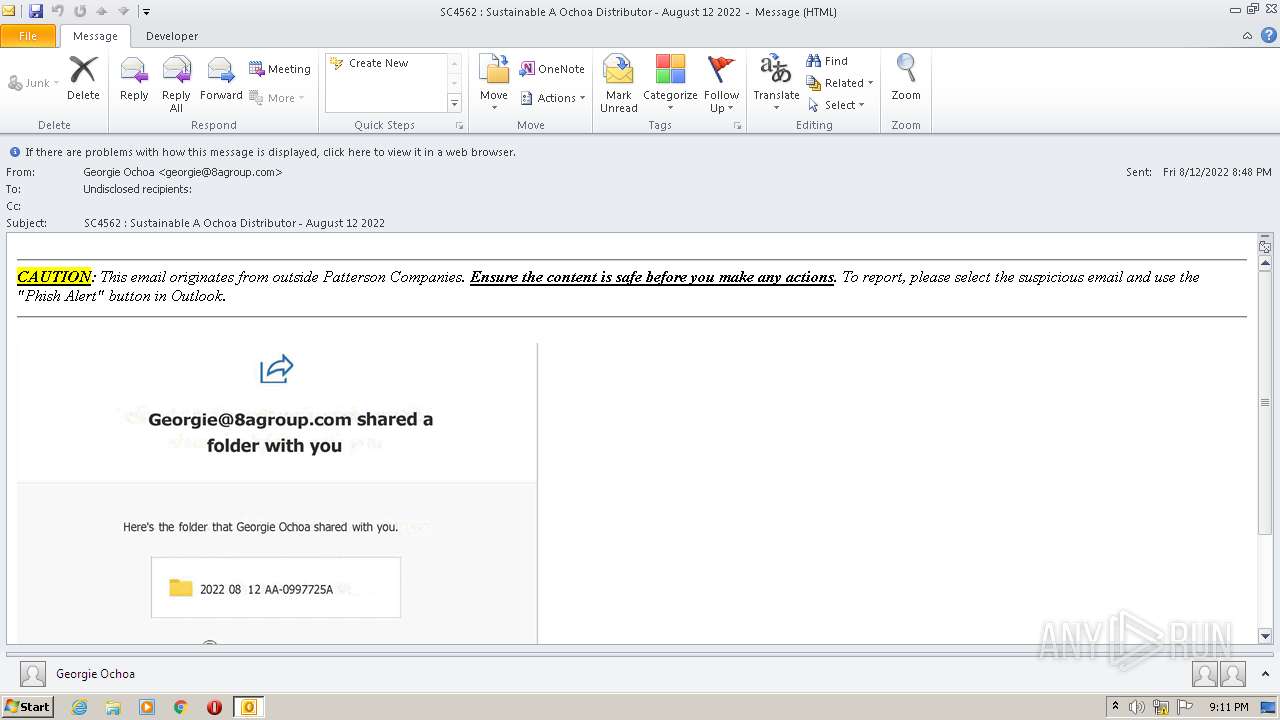
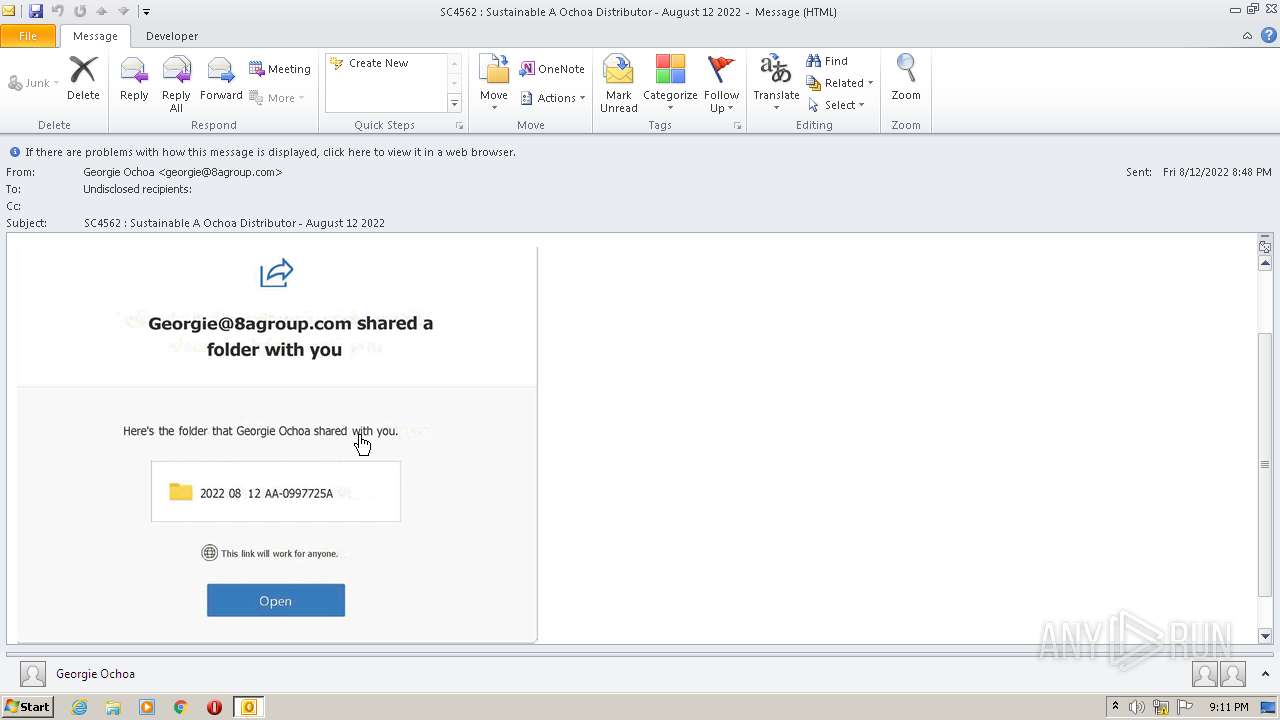
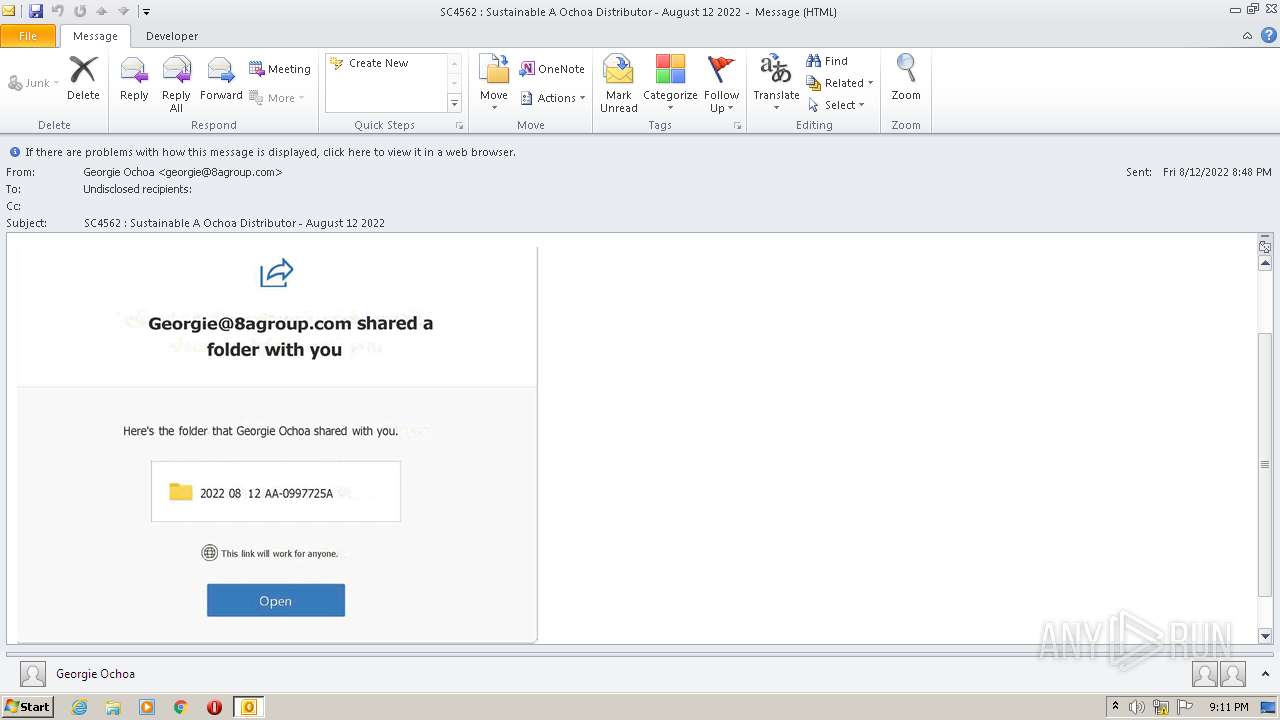
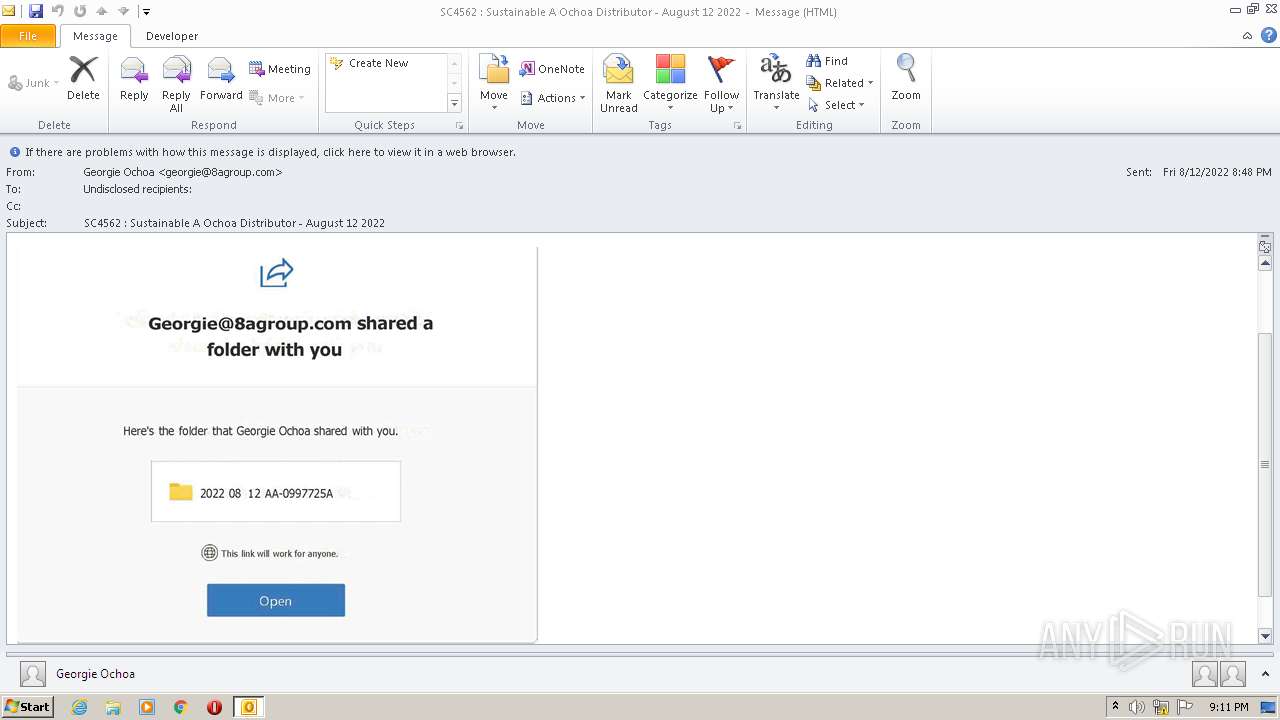
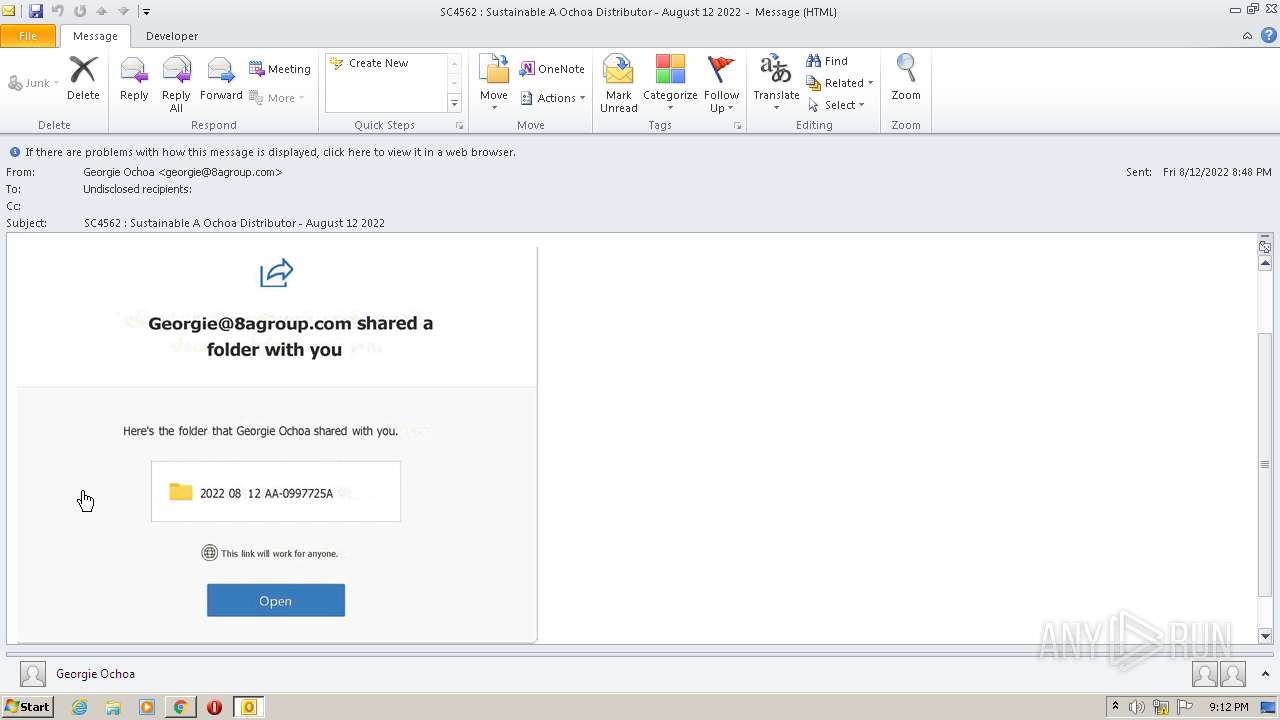
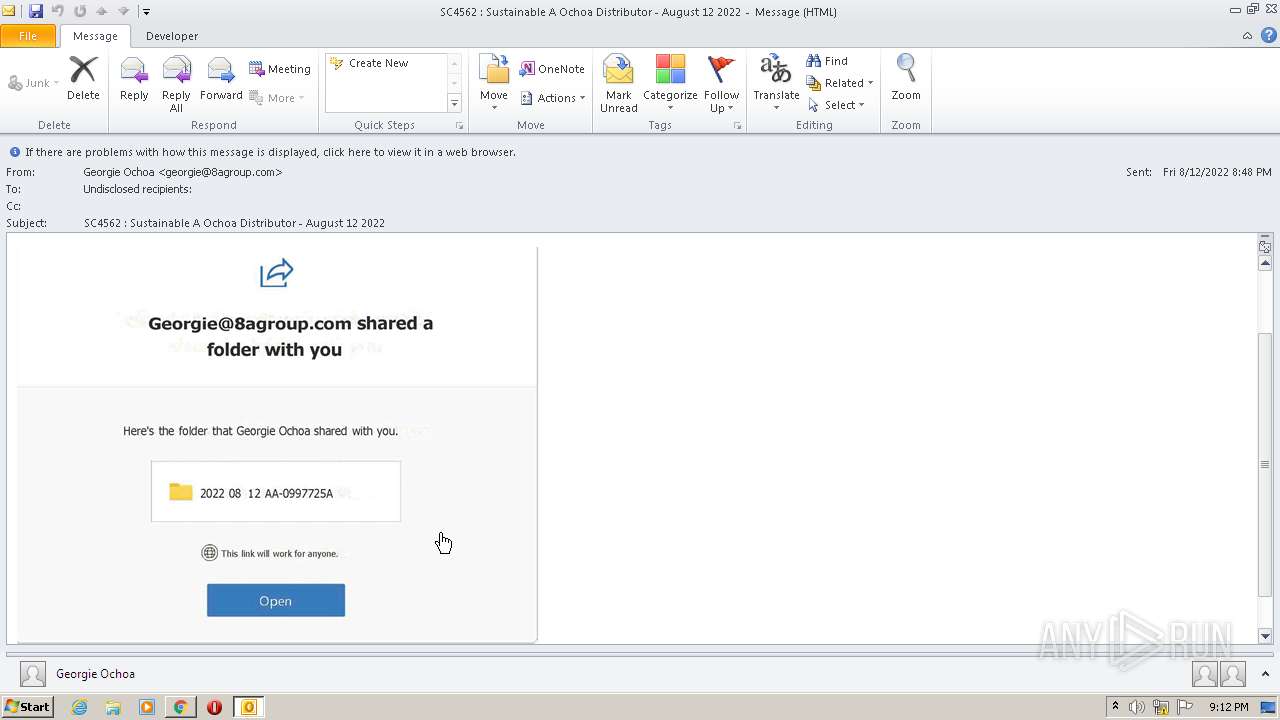
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/ce9f3d59-a147-4ca1-9148-2fa4083081e7 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 20:11:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 06A4680F66A1E56424CC647C4D1BA22D |
| SHA1: | 53E3034FD746BEC4F567B73A801F9446E39881AF |
| SHA256: | 9E55739120616D9527355CCE5C2B33FCBBC2C6057814B35594E6F25D94843159 |
| SSDEEP: | 6144:nmKbz1Tggk0r87PI/EUl0H8GU1aRgjU7fIjSg1Nk:nmKbuT0yPId48nf8f41Nk |
MALICIOUS
Drops executable file immediately after starts
- chrome.exe (PID: 4040)
- chrome.exe (PID: 2792)
SUSPICIOUS
Searches for installed software
- OUTLOOK.EXE (PID: 868)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2388)
- iexplore.exe (PID: 2008)
Checks supported languages
- OUTLOOK.EXE (PID: 868)
Reads the computer name
- OUTLOOK.EXE (PID: 868)
Modifies files in Chrome extension folder
- chrome.exe (PID: 4040)
Executable content was dropped or overwritten
- chrome.exe (PID: 4040)
- chrome.exe (PID: 2792)
Drops a file with a compile date too recent
- chrome.exe (PID: 4040)
- chrome.exe (PID: 2792)
INFO
Checks supported languages
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 2388)
- chrome.exe (PID: 4040)
- chrome.exe (PID: 2212)
- chrome.exe (PID: 1984)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 3048)
- chrome.exe (PID: 3856)
- chrome.exe (PID: 2432)
- chrome.exe (PID: 2660)
- chrome.exe (PID: 3364)
- chrome.exe (PID: 2556)
- chrome.exe (PID: 3708)
- chrome.exe (PID: 2620)
- chrome.exe (PID: 2320)
- chrome.exe (PID: 672)
- chrome.exe (PID: 1040)
- iexplore.exe (PID: 3980)
- chrome.exe (PID: 3660)
- iexplore.exe (PID: 2008)
- chrome.exe (PID: 3032)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 3312)
- chrome.exe (PID: 3540)
- chrome.exe (PID: 3736)
- chrome.exe (PID: 3104)
- chrome.exe (PID: 3636)
- chrome.exe (PID: 2796)
- chrome.exe (PID: 3712)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 2188)
- chrome.exe (PID: 3164)
- chrome.exe (PID: 4044)
- chrome.exe (PID: 1704)
- chrome.exe (PID: 3176)
Application launched itself
- iexplore.exe (PID: 3628)
- chrome.exe (PID: 4040)
- iexplore.exe (PID: 3980)
Reads the computer name
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 2388)
- chrome.exe (PID: 4040)
- chrome.exe (PID: 1984)
- chrome.exe (PID: 2792)
- chrome.exe (PID: 2556)
- chrome.exe (PID: 2320)
- iexplore.exe (PID: 2008)
- iexplore.exe (PID: 3980)
- chrome.exe (PID: 3032)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 3712)
- chrome.exe (PID: 3204)
- chrome.exe (PID: 3176)
Changes internet zones settings
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 3980)
Checks Windows Trust Settings
- iexplore.exe (PID: 2388)
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 3980)
- chrome.exe (PID: 4040)
Reads the date of Windows installation
- iexplore.exe (PID: 3628)
- iexplore.exe (PID: 3980)
- chrome.exe (PID: 3916)
Reads settings of System Certificates
- iexplore.exe (PID: 2388)
- iexplore.exe (PID: 3628)
- chrome.exe (PID: 2792)
- iexplore.exe (PID: 3980)
- chrome.exe (PID: 4040)
Manual execution by user
- chrome.exe (PID: 4040)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 868)
Reads internet explorer settings
- iexplore.exe (PID: 2008)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
78
Monitored processes
36
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 672 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1048,13238664211473495160,7361256346317335277,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3448 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 868 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\phish_alert_sp2_2.0.0.0.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1040 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1048,13238664211473495160,7361256346317335277,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3524 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1048,13238664211473495160,7361256346317335277,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=3816 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1984 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,13238664211473495160,7361256346317335277,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --mojo-platform-channel-handle=1072 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2008 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3980 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --field-trial-handle=1048,13238664211473495160,7361256346317335277,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=2004 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2212 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=86.0.4240.198 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x67e9d988,0x67e9d998,0x67e9d9a4 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,13238664211473495160,7361256346317335277,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2760 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 2388 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3628 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
40 891
Read events
39 910
Write events
945
Delete events
36
Modification events
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (868) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
4
Suspicious files
165
Text files
143
Unknown types
21
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 868 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR9710.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 868 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 868 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp9879.tmp | binary | |
MD5:— | SHA256:— | |||
| 868 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 868 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 868 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\98BF1E04.dat | image | |
MD5:— | SHA256:— | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarD812.tmp | cat | |
MD5:— | SHA256:— | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2388 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabD811.tmp | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
61
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
880 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.70 Kb | whitelisted |
2388 | iexplore.exe | GET | 200 | 184.24.77.47:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgTLHuaPVDG7%2FV8P20xAx4f6hg%3D%3D | US | der | 503 b | shared |
2388 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?b2ef6a463a1da7b9 | US | compressed | 60.2 Kb | whitelisted |
3980 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2792 | chrome.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | US | crx | 242 Kb | whitelisted |
2388 | iexplore.exe | GET | 200 | 96.16.145.230:80 | http://x1.c.lencr.org/ | US | der | 717 b | whitelisted |
880 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 5.64 Kb | whitelisted |
2388 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?736dca194375b198 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2388 | iexplore.exe | 184.24.77.47:80 | r3.o.lencr.org | Time Warner Cable Internet LLC | US | unknown |
2388 | iexplore.exe | 65.9.66.60:443 | brave.com | AT&T Services, Inc. | US | unknown |
3628 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2388 | iexplore.exe | 13.225.84.66:80 | o.ss2.us | — | US | suspicious |
2792 | chrome.exe | 142.250.185.68:443 | www.google.com | Google Inc. | US | whitelisted |
2792 | chrome.exe | 142.250.185.174:443 | clients2.google.com | Google Inc. | US | whitelisted |
2792 | chrome.exe | 142.250.185.77:443 | accounts.google.com | Google Inc. | US | suspicious |
2792 | chrome.exe | 142.251.36.10:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2792 | chrome.exe | 142.250.185.161:443 | clients2.googleusercontent.com | Google Inc. | US | whitelisted |
2792 | chrome.exe | 142.250.186.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
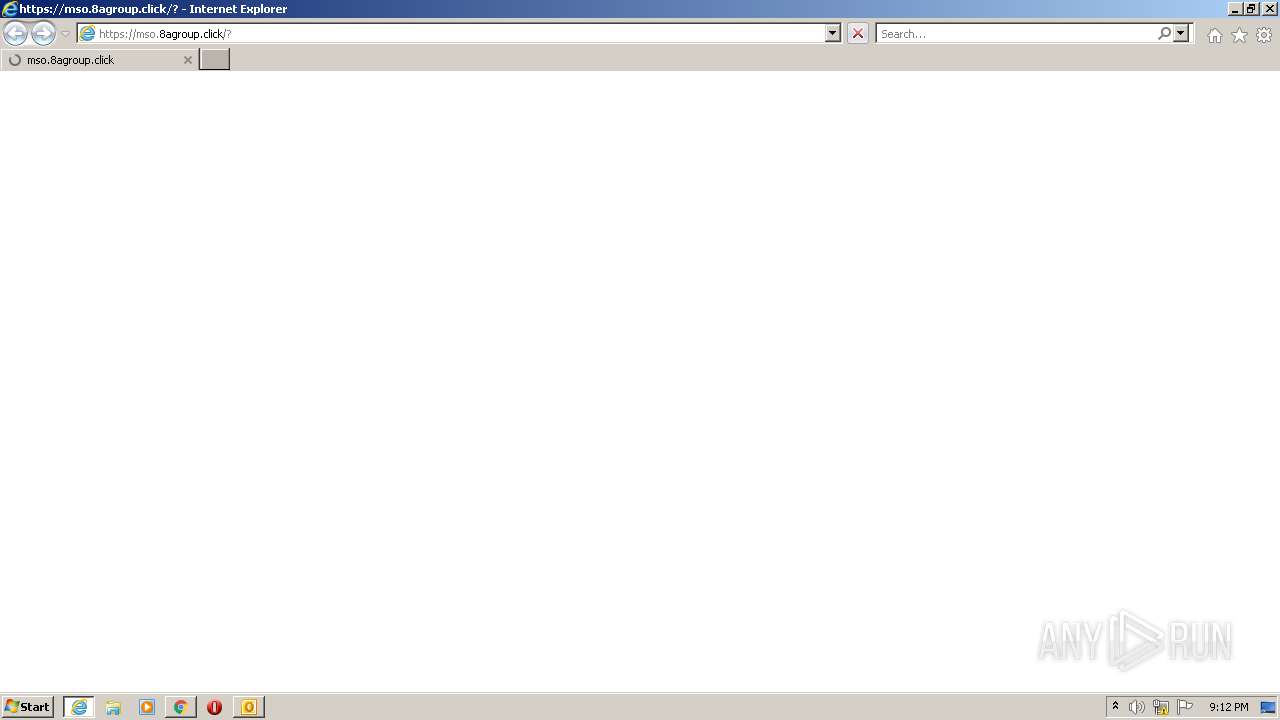
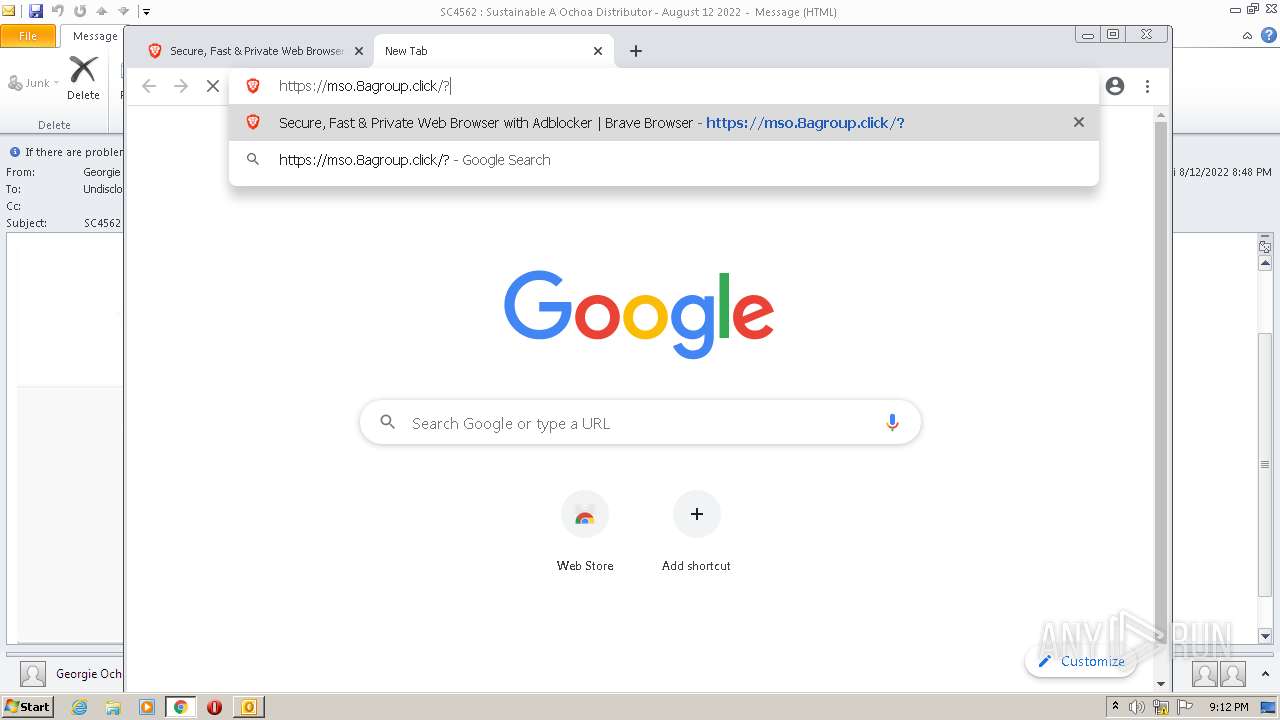
mso.8agroup.click |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
brave.com |
| whitelisted |
o.ss2.us |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |