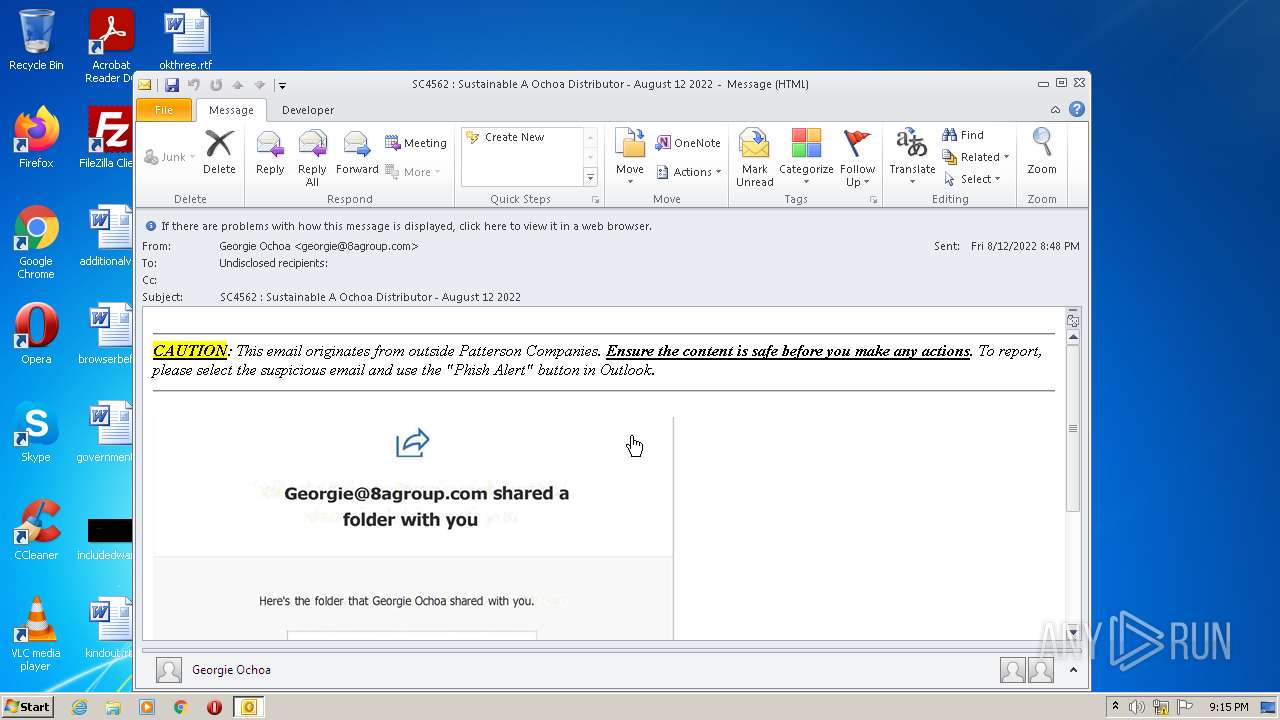
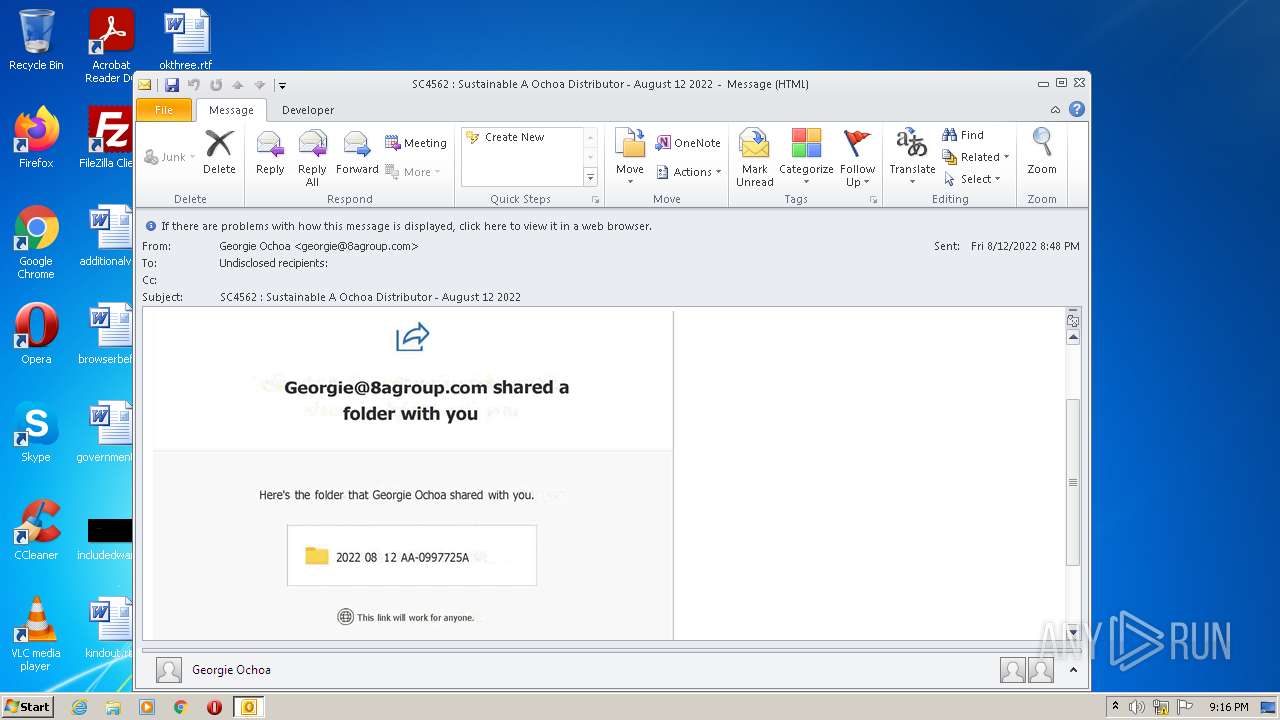
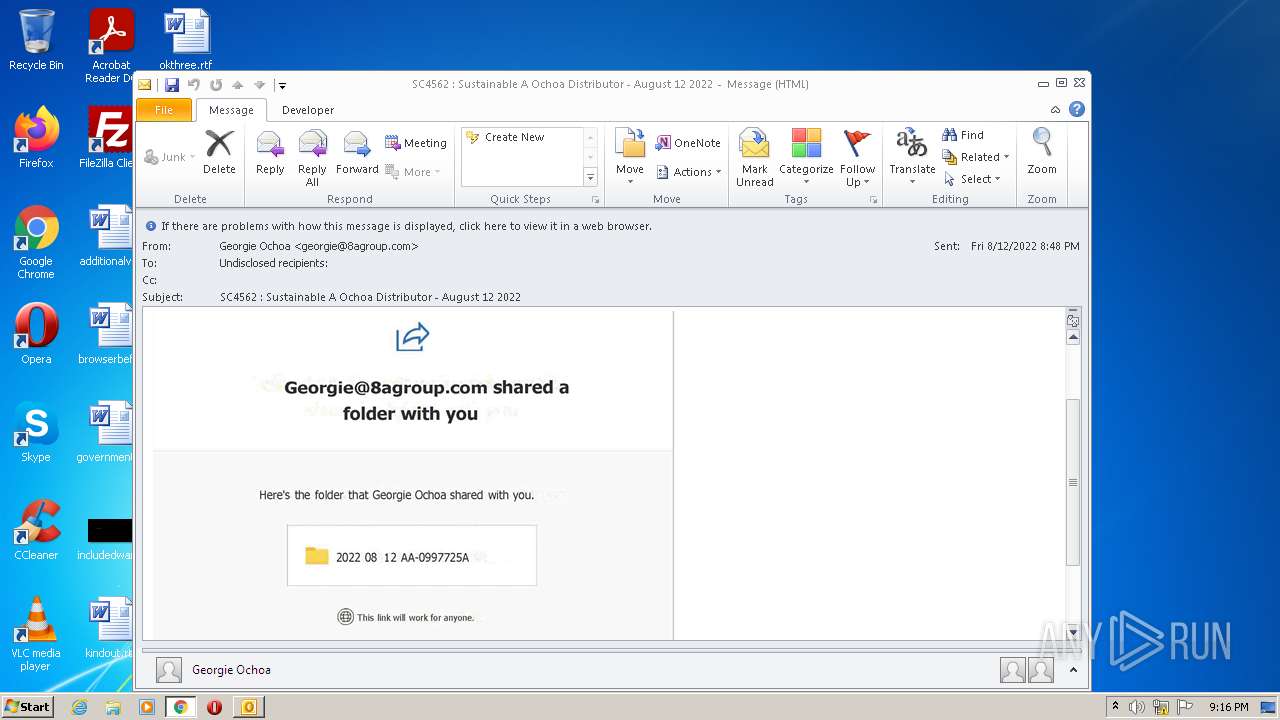
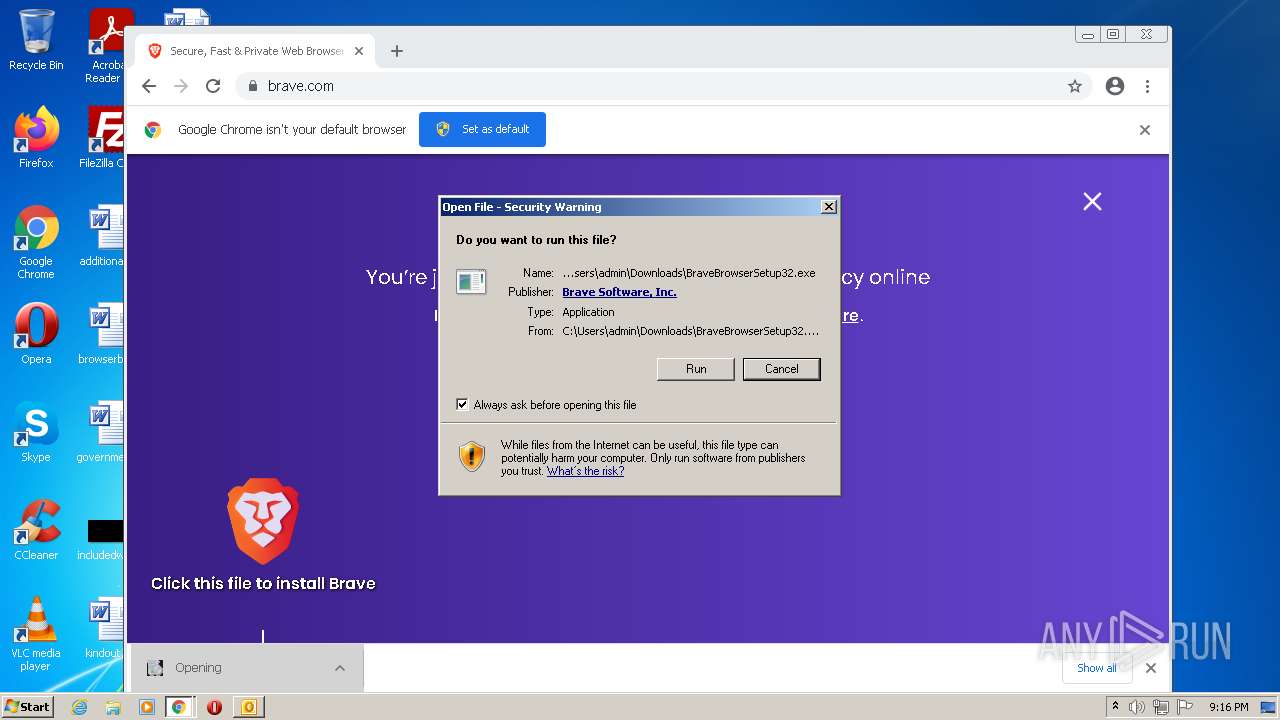
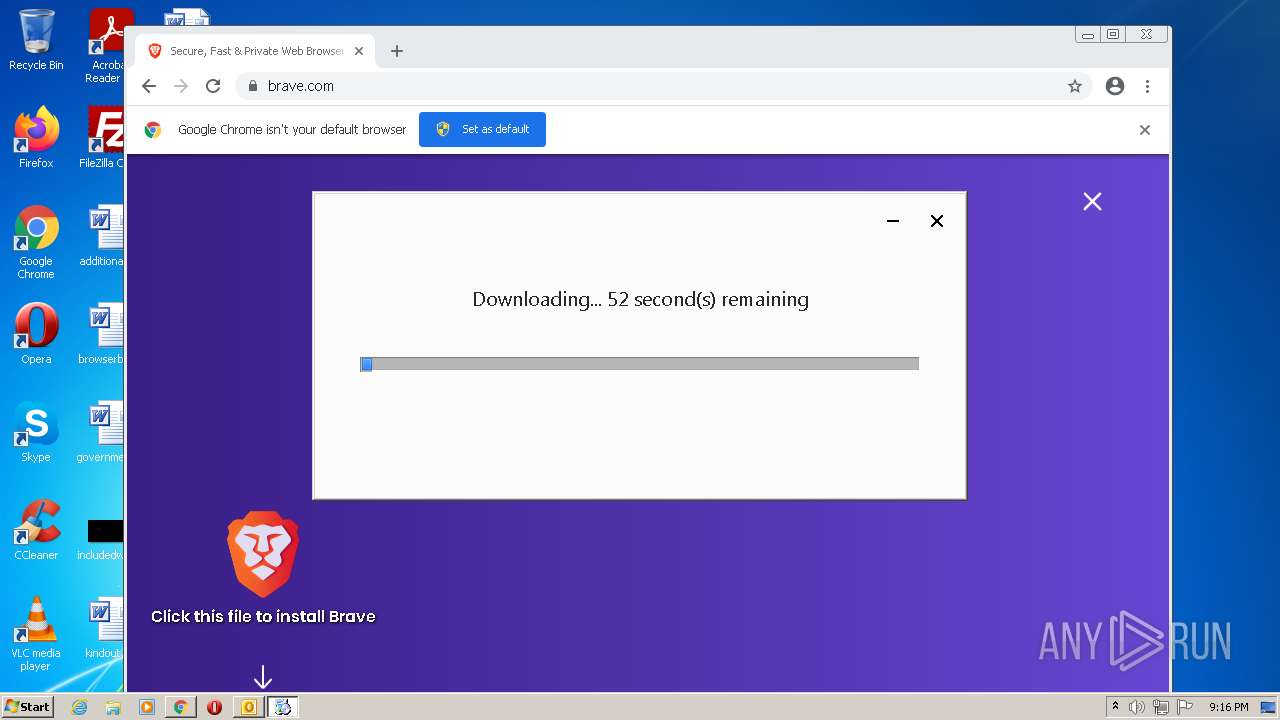
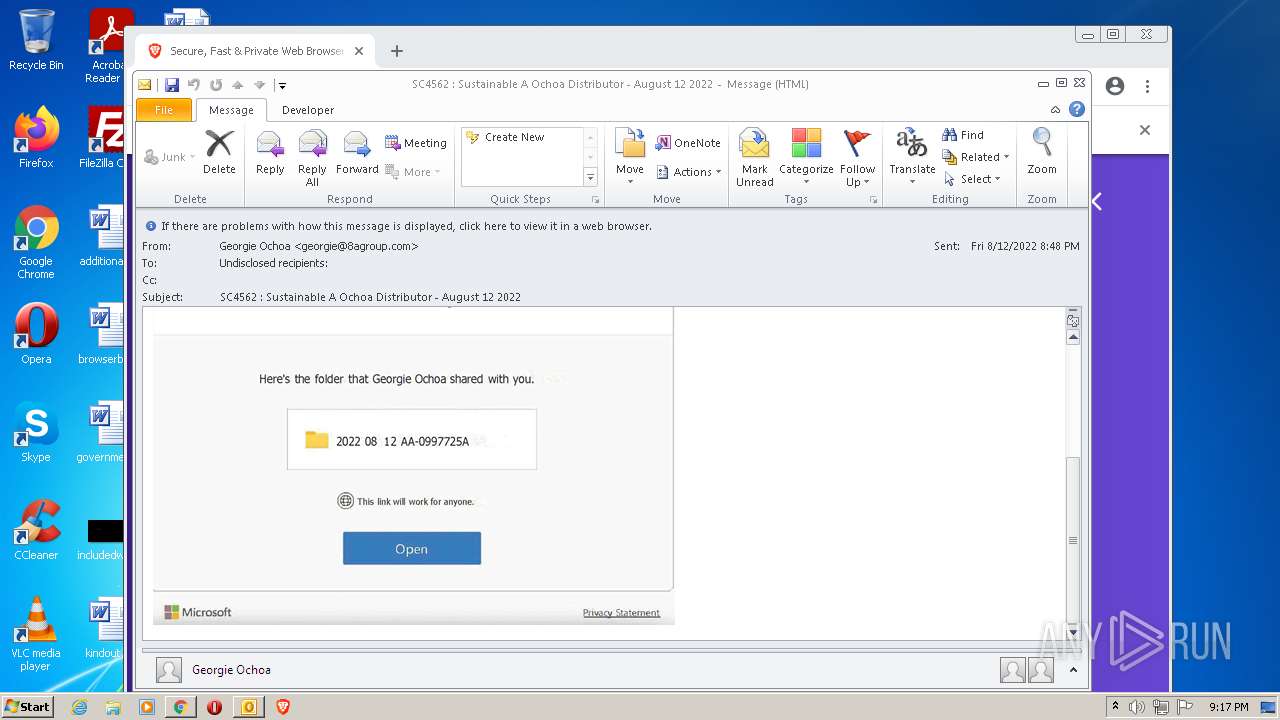
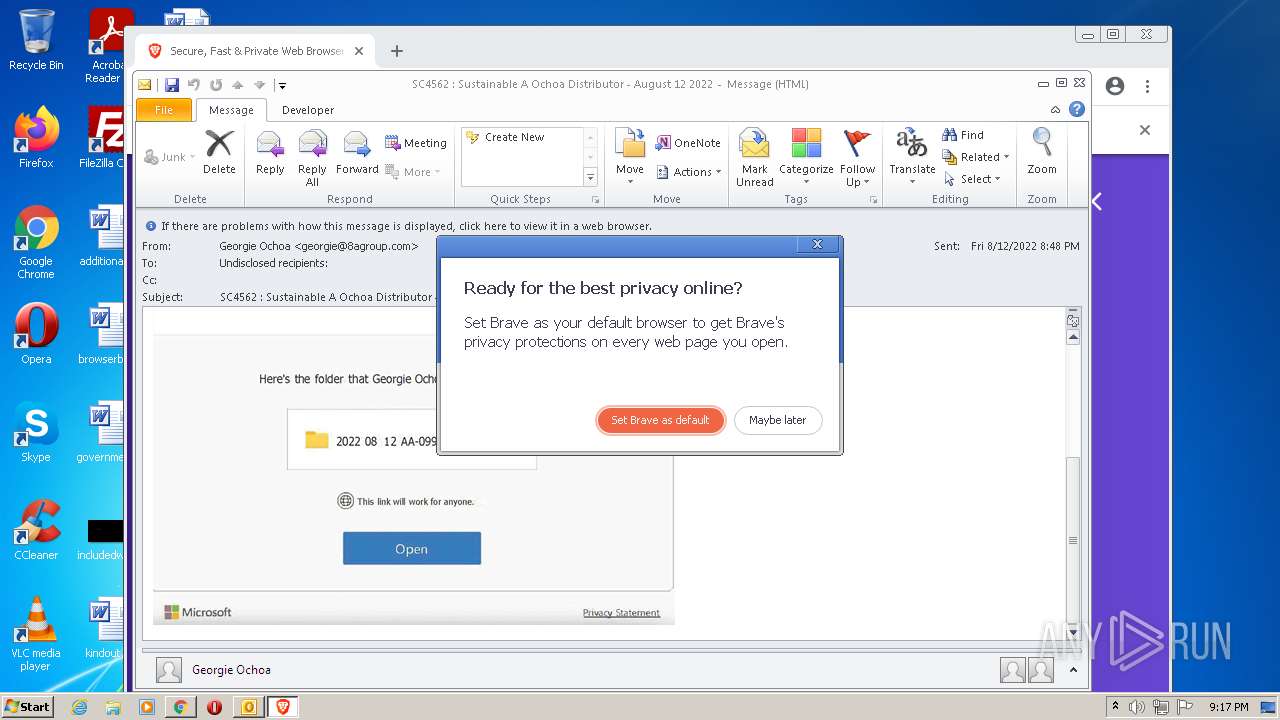
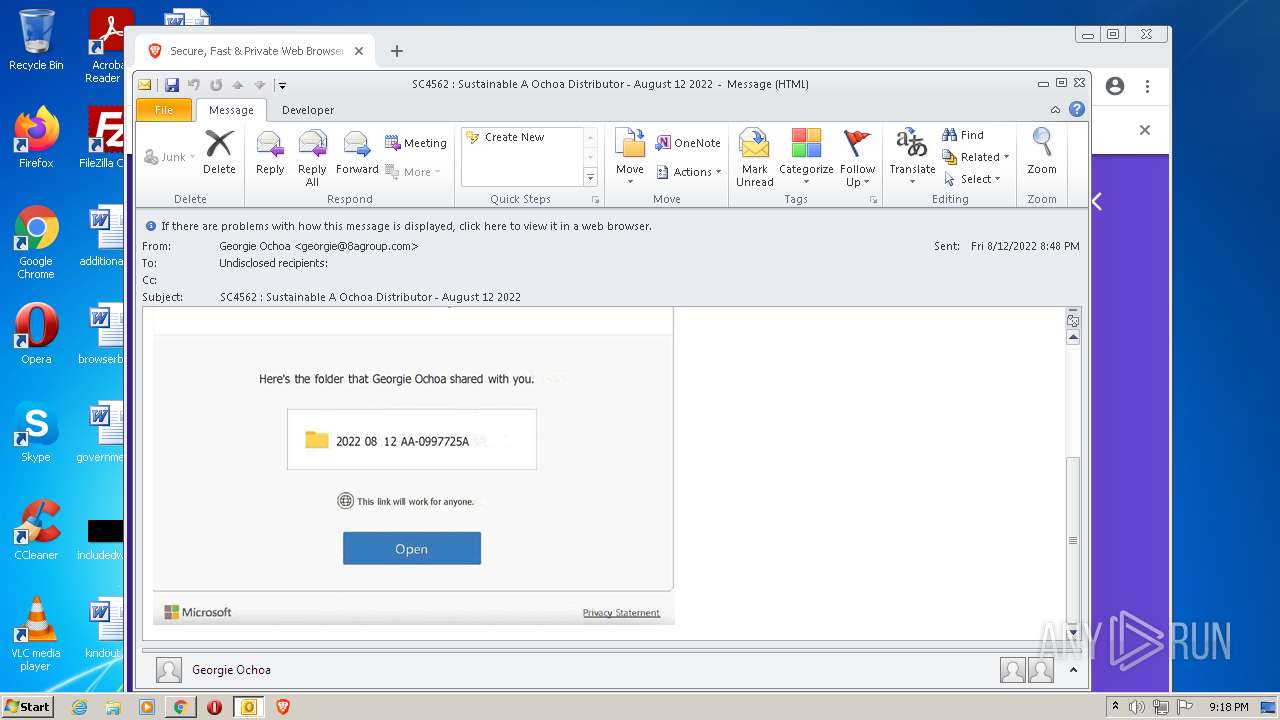
| File name: | phish_alert_sp2_2.0.0.0.eml |
| Full analysis: | https://app.any.run/tasks/924a5451-ebaa-40ae-b754-7217e30433be |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2022, 20:15:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | 06A4680F66A1E56424CC647C4D1BA22D |
| SHA1: | 53E3034FD746BEC4F567B73A801F9446E39881AF |
| SHA256: | 9E55739120616D9527355CCE5C2B33FCBBC2C6057814B35594E6F25D94843159 |
| SSDEEP: | 6144:nmKbz1Tggk0r87PI/EUl0H8GU1aRgjU7fIjSg1Nk:nmKbuT0yPId48nf8f41Nk |
MALICIOUS
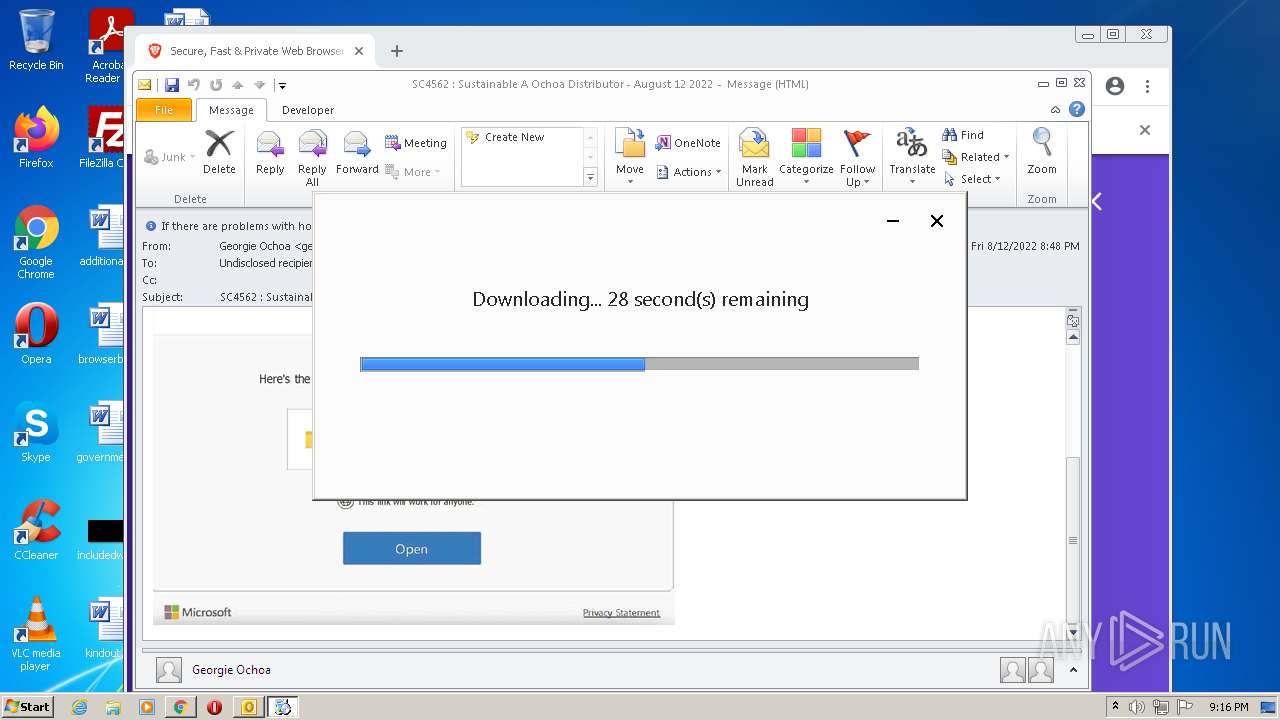
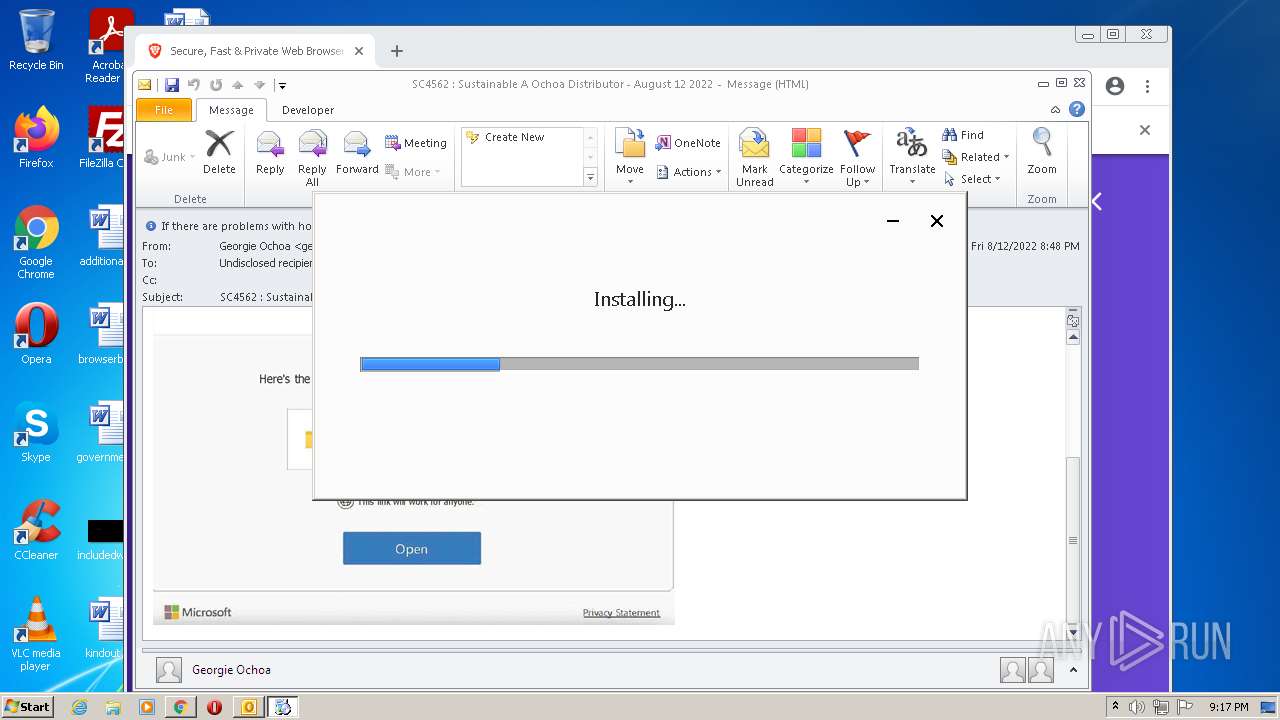
Drops executable file immediately after starts
- chrome.exe (PID: 300)
- chrome.exe (PID: 3156)
- BraveBrowserSetup32.exe (PID: 3292)
- BraveUpdate.exe (PID: 1800)
- BraveUpdateSetup.exe (PID: 3116)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3968)
- chrome.exe (PID: 3388)
Application was dropped or rewritten from another process
- BraveUpdate.exe (PID: 3352)
- BraveUpdateSetup.exe (PID: 3116)
- BraveUpdate.exe (PID: 1800)
- BraveBrowserSetup32.exe (PID: 3292)
- BraveUpdate.exe (PID: 3672)
- BraveUpdate.exe (PID: 3488)
- BraveUpdate.exe (PID: 2088)
- BraveUpdate.exe (PID: 2972)
- BraveUpdate.exe (PID: 868)
- setup.exe (PID: 3968)
- setup.exe (PID: 3388)
- setup.exe (PID: 3552)
- setup.exe (PID: 2140)
- BraveUpdateOnDemand.exe (PID: 2408)
- BraveUpdate.exe (PID: 3556)
- BraveUpdate.exe (PID: 3492)
- brave.exe (PID: 3896)
- brave.exe (PID: 2324)
- brave.exe (PID: 3200)
- brave.exe (PID: 3252)
- brave.exe (PID: 2104)
- brave.exe (PID: 476)
- brave.exe (PID: 3996)
- brave.exe (PID: 124)
- brave.exe (PID: 3712)
- brave.exe (PID: 2952)
- brave.exe (PID: 968)
- chrmstp.exe (PID: 2192)
- chrmstp.exe (PID: 760)
- brave.exe (PID: 2088)
- brave.exe (PID: 580)
- chrmstp.exe (PID: 396)
- chrmstp.exe (PID: 3968)
- brave.exe (PID: 1872)
- brave.exe (PID: 3924)
- brave.exe (PID: 1648)
- brave.exe (PID: 2832)
- brave.exe (PID: 3336)
- brave.exe (PID: 3936)
- brave.exe (PID: 2496)
Loads dropped or rewritten executable
- BraveUpdate.exe (PID: 3352)
- BraveUpdate.exe (PID: 1800)
- BraveUpdate.exe (PID: 3488)
- BraveUpdate.exe (PID: 2088)
- BraveUpdate.exe (PID: 3672)
- BraveUpdate.exe (PID: 2972)
- BraveUpdate.exe (PID: 868)
- svchost.exe (PID: 1708)
- BraveUpdate.exe (PID: 3556)
- BraveUpdate.exe (PID: 3492)
Actions looks like stealing of personal data
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3388)
- BraveUpdate.exe (PID: 3556)
- brave.exe (PID: 2324)
- brave.exe (PID: 3200)
- brave.exe (PID: 3252)
- brave.exe (PID: 3996)
- brave.exe (PID: 2104)
- brave.exe (PID: 124)
- brave.exe (PID: 3712)
- brave.exe (PID: 968)
- brave.exe (PID: 476)
- brave.exe (PID: 2952)
- chrmstp.exe (PID: 396)
- chrmstp.exe (PID: 3968)
- chrmstp.exe (PID: 2192)
- brave.exe (PID: 2088)
- brave.exe (PID: 580)
- chrmstp.exe (PID: 760)
- brave.exe (PID: 3924)
- brave.exe (PID: 1872)
- brave.exe (PID: 2832)
- brave.exe (PID: 2496)
- brave.exe (PID: 3936)
- brave.exe (PID: 1648)
- brave.exe (PID: 3336)
- brave.exe (PID: 3896)
- setup.exe (PID: 3968)
Changes the autorun value in the registry
- setup.exe (PID: 3968)
Steals credentials from Web Browsers
- brave.exe (PID: 3896)
SUSPICIOUS
Checks supported languages
- OUTLOOK.EXE (PID: 2176)
- BraveUpdate.exe (PID: 3352)
- BraveUpdateSetup.exe (PID: 3116)
- BraveBrowserSetup32.exe (PID: 3292)
- BraveUpdate.exe (PID: 1800)
- BraveUpdate.exe (PID: 3488)
- BraveUpdate.exe (PID: 3672)
- BraveUpdate.exe (PID: 2088)
- BraveUpdate.exe (PID: 868)
- BraveUpdate.exe (PID: 2972)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3968)
- setup.exe (PID: 2140)
- setup.exe (PID: 3388)
- setup.exe (PID: 3552)
- BraveUpdateOnDemand.exe (PID: 2408)
- BraveUpdate.exe (PID: 3492)
- BraveUpdate.exe (PID: 3556)
- brave.exe (PID: 3896)
- brave.exe (PID: 3200)
- brave.exe (PID: 2104)
- brave.exe (PID: 2324)
- brave.exe (PID: 3996)
- brave.exe (PID: 3252)
- brave.exe (PID: 124)
- brave.exe (PID: 476)
- brave.exe (PID: 3712)
- brave.exe (PID: 2952)
- brave.exe (PID: 968)
- chrmstp.exe (PID: 2192)
- chrmstp.exe (PID: 760)
- chrmstp.exe (PID: 3968)
- brave.exe (PID: 2088)
- chrmstp.exe (PID: 396)
- brave.exe (PID: 1872)
- brave.exe (PID: 580)
- brave.exe (PID: 3924)
- brave.exe (PID: 1648)
- brave.exe (PID: 2832)
- brave.exe (PID: 3936)
- brave.exe (PID: 2496)
- brave.exe (PID: 3336)
Searches for installed software
- OUTLOOK.EXE (PID: 2176)
Reads the computer name
- OUTLOOK.EXE (PID: 2176)
- BraveUpdate.exe (PID: 3352)
- BraveUpdate.exe (PID: 3488)
- BraveUpdate.exe (PID: 1800)
- BraveUpdate.exe (PID: 2088)
- BraveUpdate.exe (PID: 3672)
- BraveUpdate.exe (PID: 2972)
- BraveUpdate.exe (PID: 868)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3968)
- setup.exe (PID: 3388)
- BraveUpdate.exe (PID: 3492)
- BraveUpdate.exe (PID: 3556)
- brave.exe (PID: 3896)
- brave.exe (PID: 2104)
- brave.exe (PID: 2324)
- chrmstp.exe (PID: 2192)
- brave.exe (PID: 2952)
- chrmstp.exe (PID: 760)
- brave.exe (PID: 2088)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3928)
Modifies files in Chrome extension folder
- chrome.exe (PID: 300)
Executable content was dropped or overwritten
- chrome.exe (PID: 300)
- chrome.exe (PID: 3156)
- BraveBrowserSetup32.exe (PID: 3292)
- BraveUpdateSetup.exe (PID: 3116)
- BraveUpdate.exe (PID: 1800)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3968)
- chrome.exe (PID: 3388)
Drops a file with a compile date too recent
- chrome.exe (PID: 300)
- chrome.exe (PID: 3156)
- BraveBrowserSetup32.exe (PID: 3292)
- BraveUpdateSetup.exe (PID: 3116)
- BraveUpdate.exe (PID: 1800)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3968)
- chrome.exe (PID: 3388)
Creates a directory in Program Files
- BraveUpdateSetup.exe (PID: 3116)
- BraveUpdate.exe (PID: 1800)
- BraveUpdate.exe (PID: 868)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3968)
Creates files in the program directory
- BraveUpdate.exe (PID: 1800)
- BraveUpdateSetup.exe (PID: 3116)
- BraveUpdate.exe (PID: 868)
- brave_installer-ia32.exe (PID: 2376)
- setup.exe (PID: 3388)
- setup.exe (PID: 3968)
Disables SEHOP
- BraveUpdate.exe (PID: 1800)
Starts itself from another location
- BraveUpdate.exe (PID: 1800)
Creates/Modifies COM task schedule object
- BraveUpdate.exe (PID: 3672)
Executed as Windows Service
- BraveUpdate.exe (PID: 868)
Application launched itself
- setup.exe (PID: 3968)
- setup.exe (PID: 3388)
- BraveUpdate.exe (PID: 868)
- brave.exe (PID: 3896)
- chrmstp.exe (PID: 760)
- chrmstp.exe (PID: 2192)
Creates a software uninstall entry
- setup.exe (PID: 3968)
Reads the date of Windows installation
- setup.exe (PID: 3388)
- chrmstp.exe (PID: 760)
Changes default file association
- setup.exe (PID: 3968)
- brave.exe (PID: 3896)
Executed via COM
- BraveUpdateOnDemand.exe (PID: 2408)
INFO
Reads the computer name
- iexplore.exe (PID: 2456)
- iexplore.exe (PID: 3928)
- chrome.exe (PID: 300)
- chrome.exe (PID: 2916)
- chrome.exe (PID: 3156)
- chrome.exe (PID: 508)
- chrome.exe (PID: 3752)
- chrome.exe (PID: 3268)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 3552)
- chrome.exe (PID: 760)
- chrome.exe (PID: 2068)
Checks supported languages
- svchost.exe (PID: 1708)
- iexplore.exe (PID: 2456)
- iexplore.exe (PID: 3928)
- chrome.exe (PID: 300)
- chrome.exe (PID: 2428)
- chrome.exe (PID: 3156)
- chrome.exe (PID: 3884)
- chrome.exe (PID: 3444)
- chrome.exe (PID: 2916)
- chrome.exe (PID: 3912)
- chrome.exe (PID: 3556)
- chrome.exe (PID: 508)
- chrome.exe (PID: 3548)
- chrome.exe (PID: 3752)
- chrome.exe (PID: 4032)
- chrome.exe (PID: 2008)
- chrome.exe (PID: 3692)
- chrome.exe (PID: 2624)
- chrome.exe (PID: 2848)
- chrome.exe (PID: 3568)
- chrome.exe (PID: 3268)
- chrome.exe (PID: 3372)
- chrome.exe (PID: 3632)
- chrome.exe (PID: 3488)
- chrome.exe (PID: 2388)
- chrome.exe (PID: 3552)
- chrome.exe (PID: 760)
- chrome.exe (PID: 2856)
- chrome.exe (PID: 3344)
- chrome.exe (PID: 2068)
- chrome.exe (PID: 2716)
- chrome.exe (PID: 3916)
- chrome.exe (PID: 2556)
- chrome.exe (PID: 3620)
- chrome.exe (PID: 3388)
Application launched itself
- iexplore.exe (PID: 2456)
- chrome.exe (PID: 300)
Checks Windows Trust Settings
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 2456)
- chrome.exe (PID: 300)
Changes internet zones settings
- iexplore.exe (PID: 2456)
Reads settings of System Certificates
- iexplore.exe (PID: 3928)
- iexplore.exe (PID: 2456)
- chrome.exe (PID: 3156)
- chrome.exe (PID: 300)
- BraveUpdate.exe (PID: 868)
- BraveUpdate.exe (PID: 2088)
- BraveUpdate.exe (PID: 3492)
- brave.exe (PID: 3896)
Reads Microsoft Office registry keys
- svchost.exe (PID: 1708)
- OUTLOOK.EXE (PID: 2176)
Reads internet explorer settings
- iexplore.exe (PID: 3928)
Reads the date of Windows installation
- iexplore.exe (PID: 2456)
- chrome.exe (PID: 760)
Manual execution by user
- chrome.exe (PID: 300)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
121
Monitored processes
77
Malicious processes
44
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe" --type=renderer --extension-process --display-capture-permissions-policy-allowed --origin-trial-public-key=bYUKPJoPnCxeNvu72j4EmPuK7tr1PAC7SHh8ld9Mw3E=,fMS4mpO6buLQ/QMd+zJmxzty/VQ6B1EUZqoCU04zoRU= --brave_session_token=7248986777545460158 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2100 --field-trial-handle=1208,i,3302873709325944986,6197433699587453561,131072 /prefetch:1 | C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe | brave.exe | ||||||||||||
User: admin Company: Brave Software, Inc. Integrity Level: LOW Description: Brave Browser Exit code: 0 Version: 104.1.42.88 Modules
| |||||||||||||||
| 300 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | Explorer.EXE | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 396 | "C:\Program Files\BraveSoftware\Brave-Browser\Application\104.1.42.88\Installer\chrmstp.exe" --type=crashpad-handler /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler --database=C:\Windows\TEMP\Crashpad --url=https://cr.brave.com --annotation=plat=Win32 --annotation=prod=Brave --annotation=ver=104.1.42.88 --initial-client-data=0x148,0x14c,0x150,0x11c,0x154,0x131a698,0x131a6a8,0x131a6b4 | C:\Program Files\BraveSoftware\Brave-Browser\Application\104.1.42.88\Installer\chrmstp.exe | chrmstp.exe | ||||||||||||
User: admin Company: Brave Software, Inc. Integrity Level: MEDIUM Description: Brave Installer Exit code: 0 Version: 104.1.42.88 Modules
| |||||||||||||||
| 476 | "C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe" --type=renderer --extension-process --display-capture-permissions-policy-allowed --origin-trial-public-key=bYUKPJoPnCxeNvu72j4EmPuK7tr1PAC7SHh8ld9Mw3E=,fMS4mpO6buLQ/QMd+zJmxzty/VQ6B1EUZqoCU04zoRU= --brave_session_token=7248986777545460158 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --mojo-platform-channel-handle=2296 --field-trial-handle=1208,i,3302873709325944986,6197433699587453561,131072 /prefetch:1 | C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe | brave.exe | ||||||||||||
User: admin Company: Brave Software, Inc. Integrity Level: LOW Description: Brave Browser Exit code: 0 Version: 104.1.42.88 Modules
| |||||||||||||||
| 508 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1048,16813580231221841337,5355498346689388146,131072 --enable-features=PasswordImport --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --use-gl=swiftshader-webgl --mojo-platform-channel-handle=2984 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 580 | "C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4024 --field-trial-handle=1208,i,3302873709325944986,6197433699587453561,131072 /prefetch:8 | C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe | brave.exe | ||||||||||||
User: admin Company: Brave Software, Inc. Integrity Level: LOW Description: Brave Browser Exit code: 0 Version: 104.1.42.88 Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1048,16813580231221841337,5355498346689388146,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=948 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 760 | "C:\Program Files\BraveSoftware\Brave-Browser\Application\104.1.42.88\Installer\chrmstp.exe" --system-level --verbose-logging --installerdata="C:\Program Files\BraveSoftware\Brave-Browser\Application\master_preferences" --create-shortcuts=1 --install-level=0 | C:\Program Files\BraveSoftware\Brave-Browser\Application\104.1.42.88\Installer\chrmstp.exe | chrmstp.exe | ||||||||||||
User: admin Company: Brave Software, Inc. Integrity Level: MEDIUM Description: Brave Installer Exit code: 73 Version: 104.1.42.88 Modules
| |||||||||||||||
| 868 | "C:\Program Files\BraveSoftware\Update\BraveUpdate.exe" /svc | C:\Program Files\BraveSoftware\Update\BraveUpdate.exe | services.exe | ||||||||||||
User: SYSTEM Company: BraveSoftware Inc. Integrity Level: SYSTEM Description: BraveSoftware Update Exit code: 0 Version: 1.3.361.131 Modules
| |||||||||||||||
| 968 | "C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe" --type=renderer --display-capture-permissions-policy-allowed --origin-trial-public-key=bYUKPJoPnCxeNvu72j4EmPuK7tr1PAC7SHh8ld9Mw3E=,fMS4mpO6buLQ/QMd+zJmxzty/VQ6B1EUZqoCU04zoRU= --brave_session_token=7248986777545460158 --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=10 --mojo-platform-channel-handle=4076 --field-trial-handle=1208,i,3302873709325944986,6197433699587453561,131072 /prefetch:1 | C:\Program Files\BraveSoftware\Brave-Browser\Application\brave.exe | brave.exe | ||||||||||||
User: admin Company: Brave Software, Inc. Integrity Level: LOW Description: Brave Browser Exit code: 0 Version: 104.1.42.88 Modules
| |||||||||||||||
Total events
54 288
Read events
50 474
Write events
3 756
Delete events
58
Modification events
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2176) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
215
Suspicious files
594
Text files
368
Unknown types
75
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2176 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR7F91.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2176 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook Data File - NoMail.pst | — | |
MD5:— | SHA256:— | |||
| 2176 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2176 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:— | SHA256:— | |||
| 2176 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\69188E25.dat | image | |
MD5:— | SHA256:— | |||
| 2176 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\tmp80CA.tmp | binary | |
MD5:— | SHA256:— | |||
| 3928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3928 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:— | SHA256:— | |||
| 3928 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarB298.tmp | cat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
81
DNS requests
50
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
876 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvODJiQUFYYVJaZ0k5di1hUFlXS1prX2xDZw/1.0.0.13_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | US | — | — | whitelisted |
2176 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3928 | iexplore.exe | GET | 200 | 104.110.191.133:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c09da86dee0c6f02 | US | compressed | 60.2 Kb | whitelisted |
876 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ocefq4ae6dpr2n3qpxdhoix5nm_2856/jflookgnkcckhobaglndicnbbgbonegd_2856_all_bzgmdvlsll2xgmaankecykz7se.crx3 | US | binary | 5.64 Kb | whitelisted |
876 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ocefq4ae6dpr2n3qpxdhoix5nm_2856/jflookgnkcckhobaglndicnbbgbonegd_2856_all_bzgmdvlsll2xgmaankecykz7se.crx3 | US | binary | 21.0 Kb | whitelisted |
876 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ocefq4ae6dpr2n3qpxdhoix5nm_2856/jflookgnkcckhobaglndicnbbgbonegd_2856_all_bzgmdvlsll2xgmaankecykz7se.crx3 | US | binary | 10.2 Kb | whitelisted |
3928 | iexplore.exe | GET | 200 | 52.222.250.185:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | US | der | 1.51 Kb | whitelisted |
3928 | iexplore.exe | GET | 200 | 18.155.152.226:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | US | der | 1.70 Kb | whitelisted |
3928 | iexplore.exe | GET | 200 | 18.155.139.181:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwZ%2FlFeFh%2Bisd96yUzJbvJmLVg0%3D | US | der | 1.39 Kb | shared |
3928 | iexplore.exe | GET | 200 | 18.66.121.29:80 | http://ocsp.sca1b.amazontrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQz9arGHWbnBV0DFzpNHz4YcTiFDQQUWaRmBlKge5WSPKOUByeWdFv5PdACEA8D5QeEOMSYIvOoUuvAIlQ%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2176 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
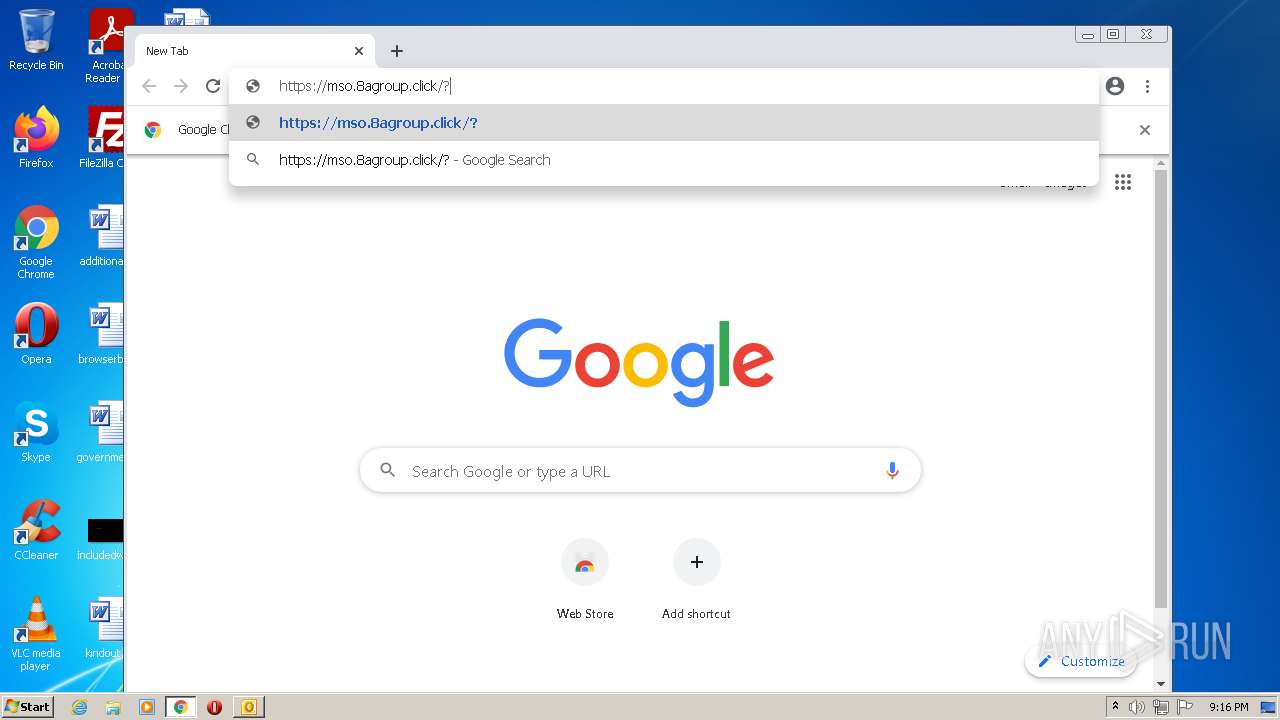
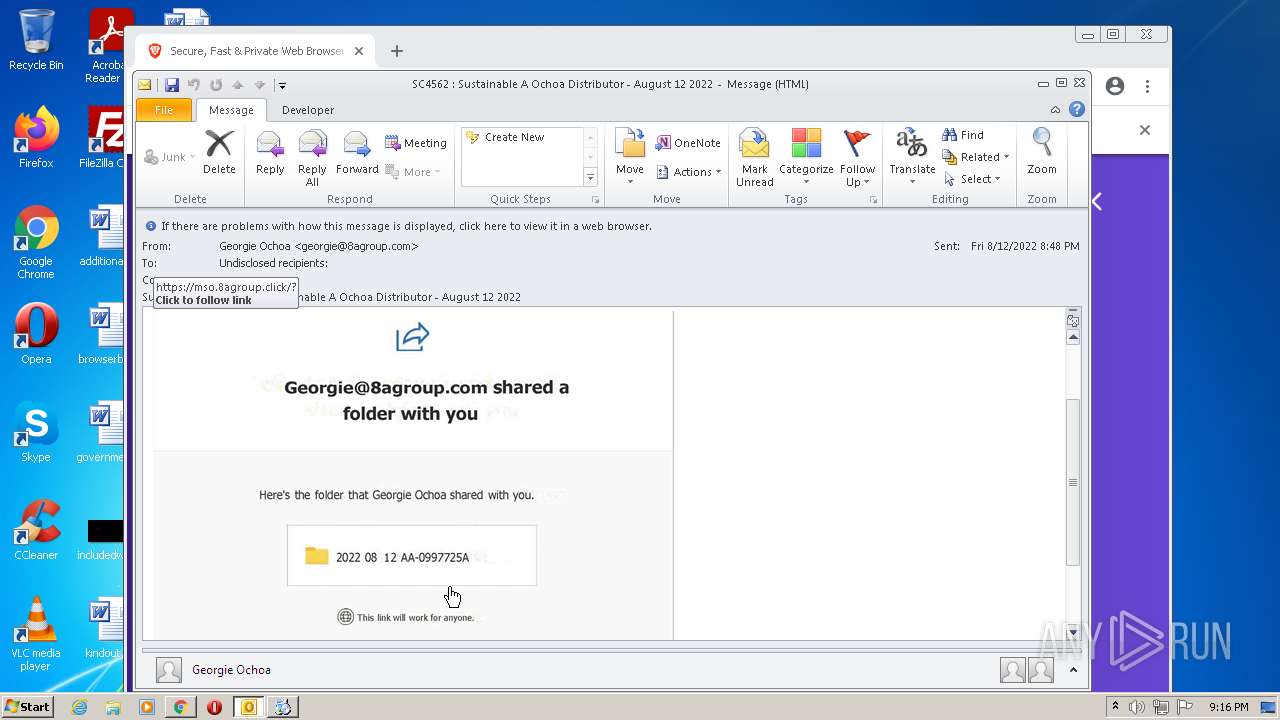
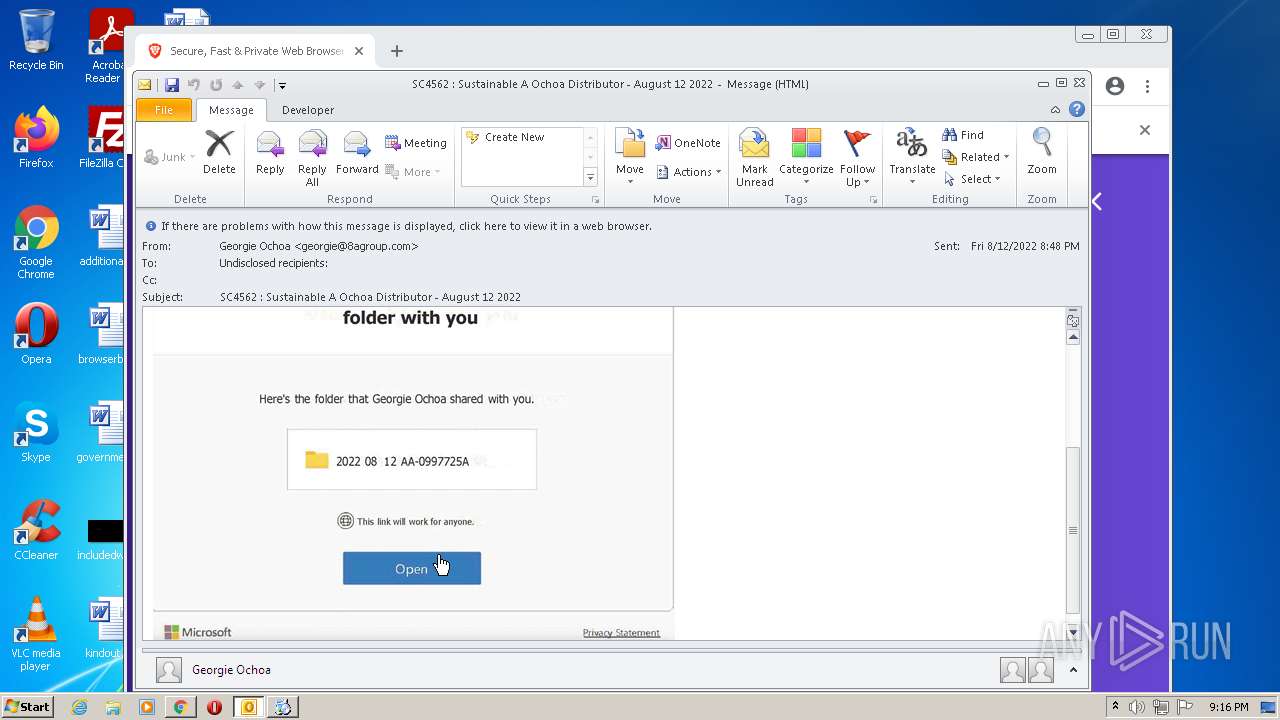
3928 | iexplore.exe | 185.189.151.13:443 | mso.8agroup.click | SOFTplus Entwicklungen GmbH | CH | unknown |
3928 | iexplore.exe | 104.110.191.133:80 | ctldl.windowsupdate.com | Akamai Technologies, Inc. | US | unknown |
3928 | iexplore.exe | 104.125.75.233:80 | x1.c.lencr.org | Akamai Technologies, Inc. | NL | suspicious |
3928 | iexplore.exe | 2.22.117.227:80 | r3.o.lencr.org | Akamai International B.V. | GB | suspicious |
2456 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3928 | iexplore.exe | 52.222.250.185:80 | ocsp.rootg2.amazontrust.com | Amazon.com, Inc. | US | whitelisted |
3928 | iexplore.exe | 65.9.95.90:443 | brave.com | AT&T Services, Inc. | US | unknown |
2456 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3928 | iexplore.exe | 18.66.121.29:80 | ocsp.sca1b.amazontrust.com | Massachusetts Institute of Technology | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
mso.8agroup.click |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
r3.o.lencr.org |
| shared |
brave.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
876 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
876 | svchost.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
Process | Message |
|---|---|
brave.exe | [0812/211741.305:ERROR:crash_report_database_win.cc(613)] CreateDirectory C:\Users\admin\AppData\Local\BraveSoftware\Brave-Browser\User Data\Crashpad: The system cannot find the path specified. (0x3)
|