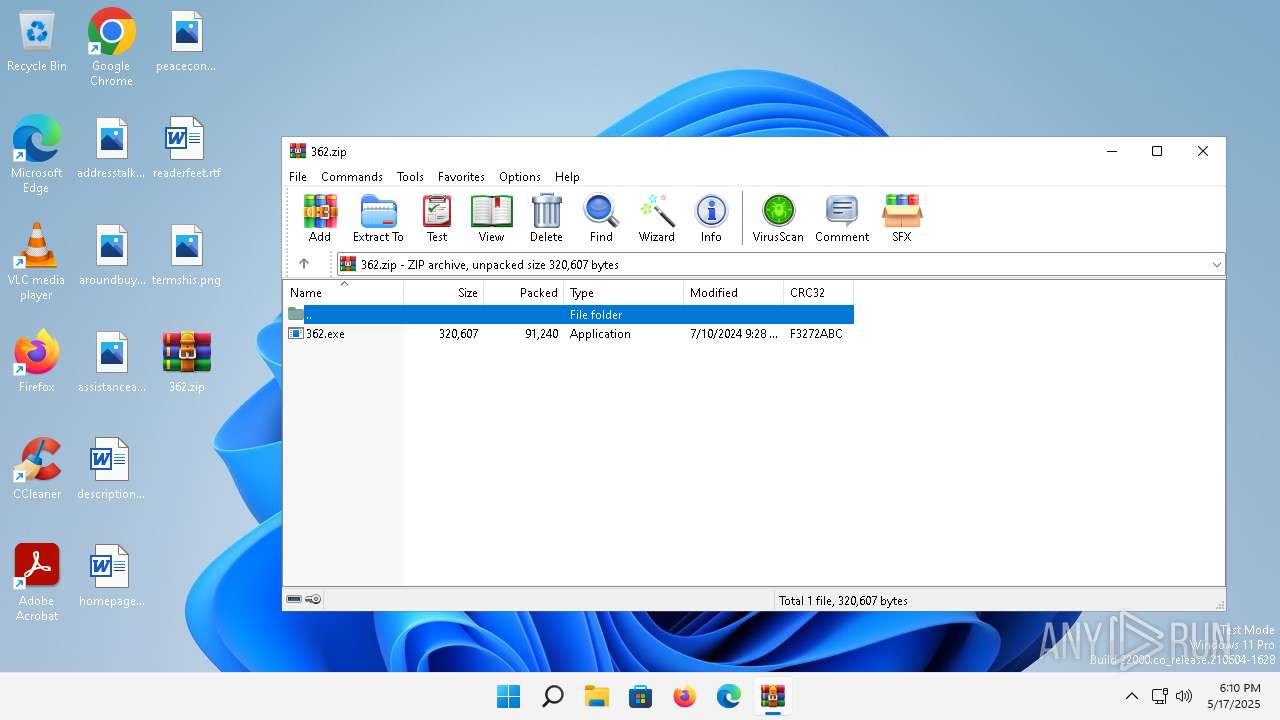
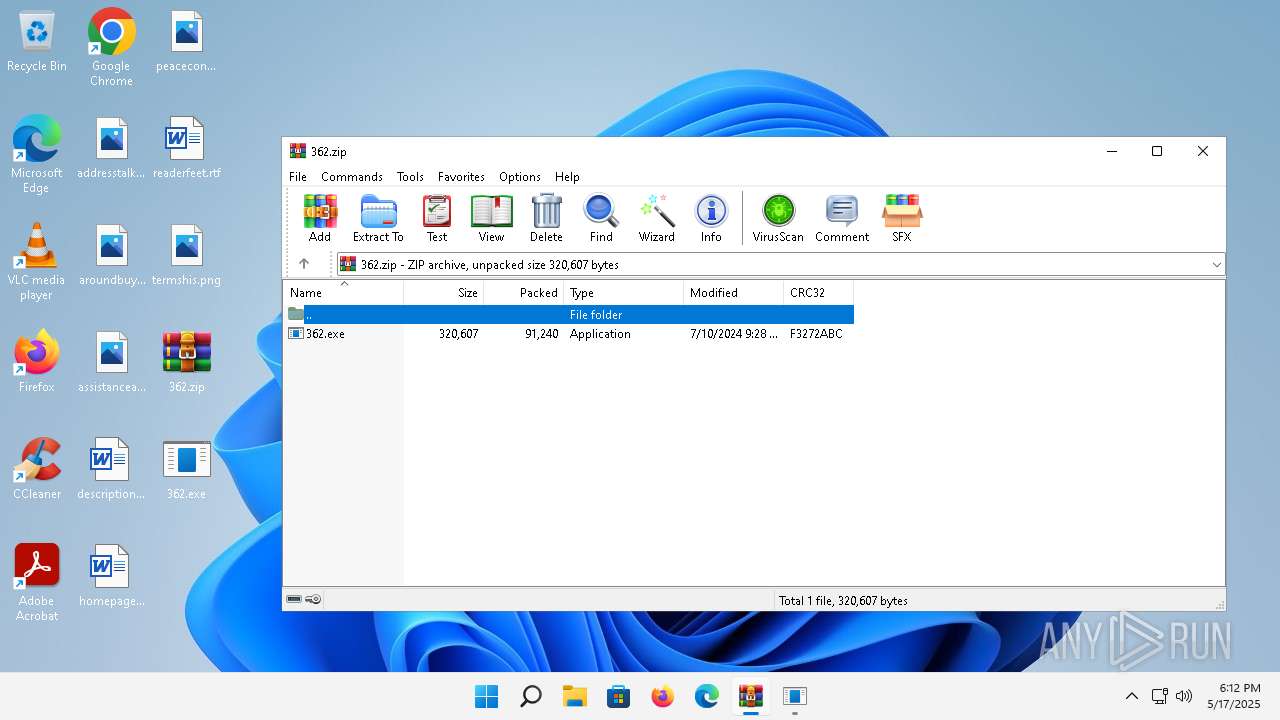
| File name: | 362.zip |
| Full analysis: | https://app.any.run/tasks/6b115d9d-5587-407a-9537-da6d60d6c64e |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 18:10:14 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3C7E89B3CD2AC8B1E364F4944787CC56 |
| SHA1: | B2DC65F4CF93242F3B14CF4C65274510E4CB06F3 |
| SHA256: | 9E4C9B7898BB61D79DC1AC746AA5D281623B2D131E4482B39FB36173289AF2CE |
| SSDEEP: | 1536:vvEvvK+O8uAK2HMFfWgAAq5F193fUSTb5csHVN7Teug3tvAPbF8deie7k7a5witP:l58rNHkAHl9NXgdIPbeuVWitaM |
MALICIOUS
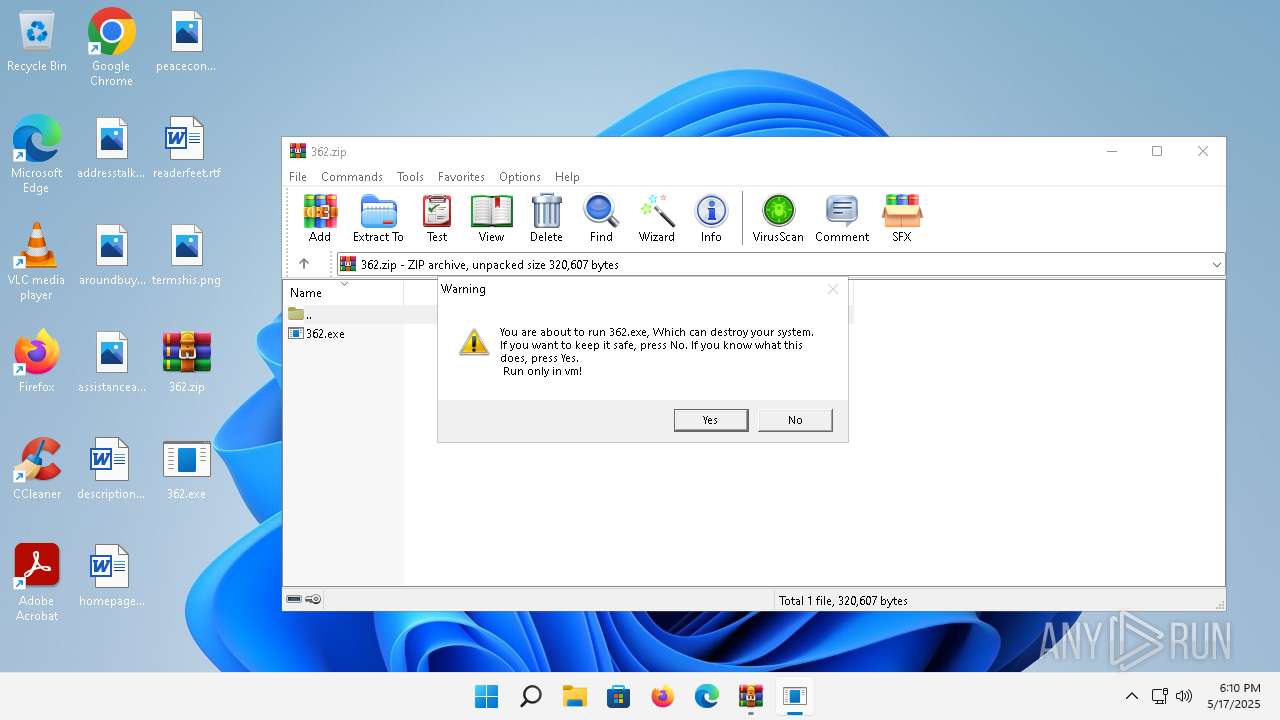
DISKWRITER has been found (auto)
- WinRAR.exe (PID: 5512)
SUSPICIOUS
There is functionality for taking screenshot (YARA)
- 362.exe (PID: 4040)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 5512)
Checks supported languages
- 362.exe (PID: 4040)
Manual execution by a user
- 362.exe (PID: 4040)
Reads the computer name
- 362.exe (PID: 4040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:07:11 00:28:38 |
| ZipCRC: | 0xf3272abc |
| ZipCompressedSize: | 91240 |
| ZipUncompressedSize: | 320607 |
| ZipFileName: | 362.exe |
Total processes
101
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4040 | "C:\Users\admin\Desktop\362.exe" | C:\Users\admin\Desktop\362.exe | — | explorer.exe | |||||||||||
User: admin Company: Yedboy33k Integrity Level: MEDIUM Description: Delete your pc with this malware!! Version: 666 Modules
| |||||||||||||||
| 5512 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\362.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
1 746
Read events
1 689
Write events
57
Delete events
0
Modification events
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\362.zip | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList |
| Operation: | write | Name: | ArcSort |
Value: 32 | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (5512) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
0
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
16
DNS requests
9
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.110.216:80 | http://www.msftconnecttest.com/connecttest.txt | unknown | — | — | whitelisted |
4432 | MoUsoCoreWorker.exe | GET | 200 | 23.50.131.221:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?98ae7ede53c7a5c4 | unknown | — | — | whitelisted |
3640 | svchost.exe | GET | 200 | 23.50.131.221:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1c72c40ea367be93 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?01658cdb802755c3 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e8295883656f7dad | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?e631054164025918 | unknown | — | — | whitelisted |
2768 | svchost.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/pinrulesstl.cab?d58461112108c32f | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 88.221.110.216:80 | — | Akamai International B.V. | DE | unknown |
4432 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4432 | MoUsoCoreWorker.exe | 23.50.131.221:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
3640 | svchost.exe | 40.126.31.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3640 | svchost.exe | 23.50.131.221:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5468 | smartscreen.exe | 108.141.15.7:443 | checkappexec.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
3952 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
296 | svchost.exe | 23.199.214.10:443 | fs.microsoft.com | AKAMAI-AS | DE | whitelisted |
2768 | svchost.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
login.live.com |
| whitelisted |
checkappexec.microsoft.com |
| whitelisted |
fs.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |