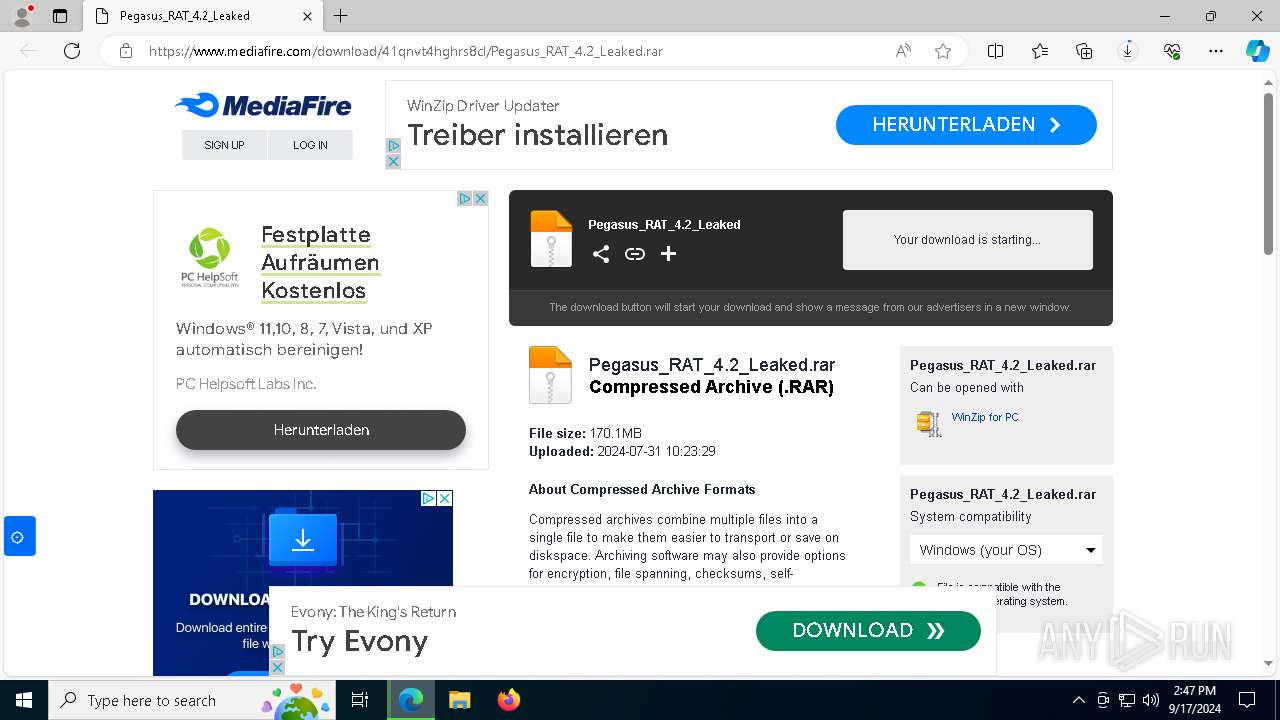
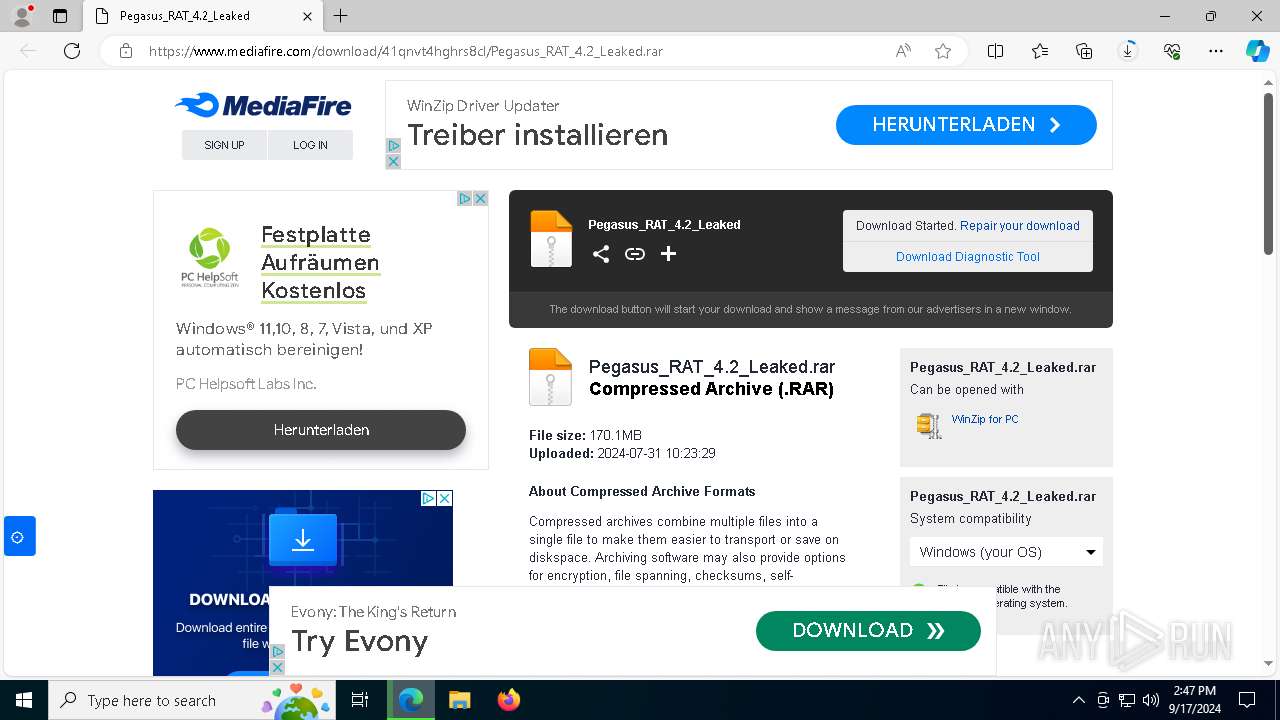
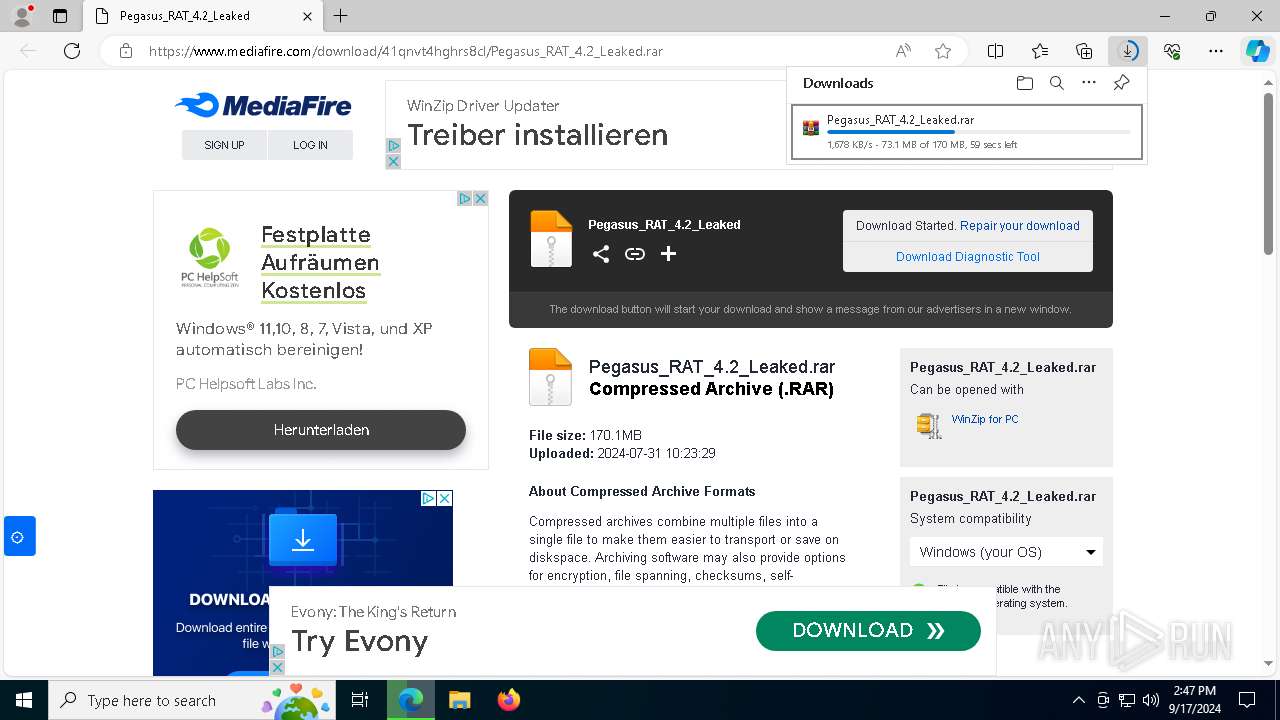
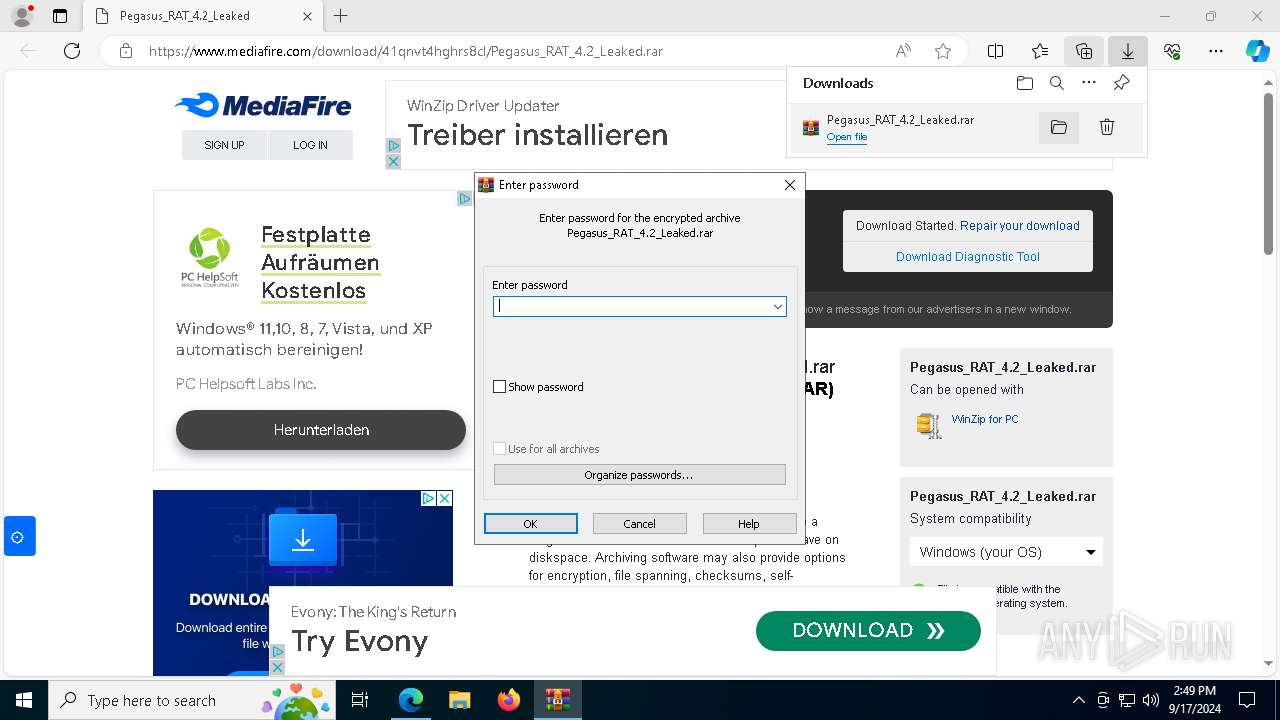
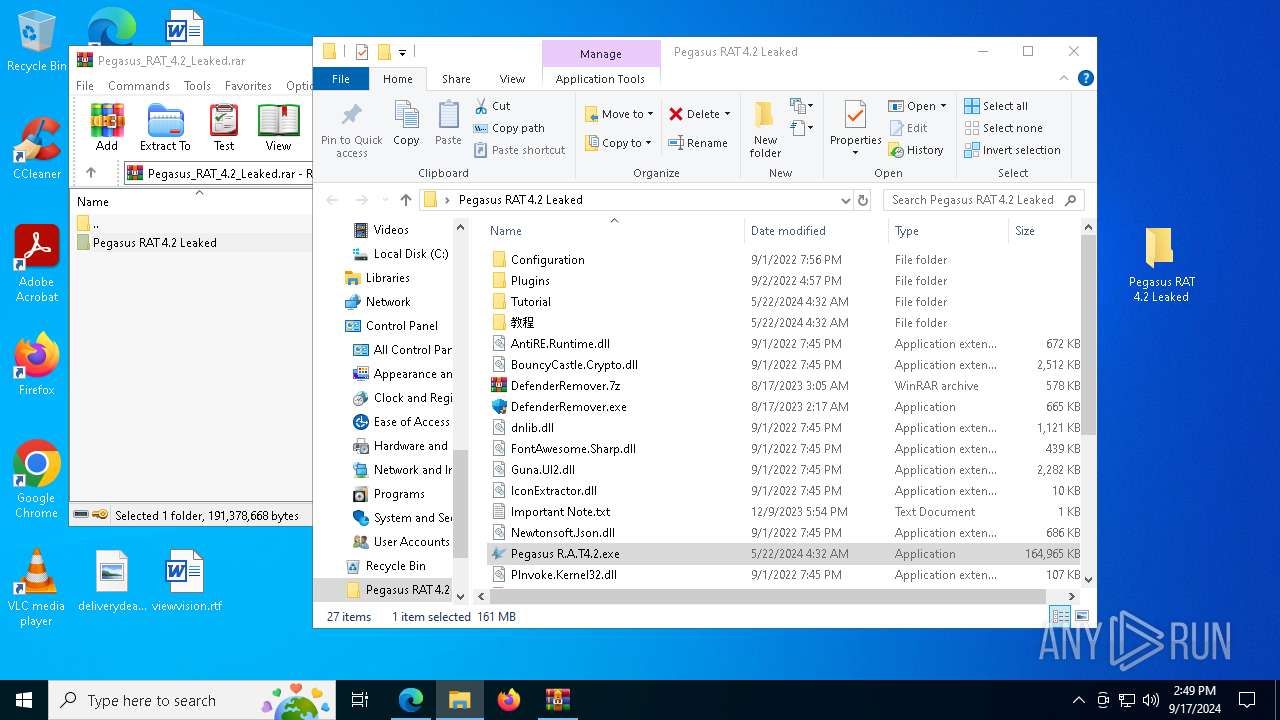
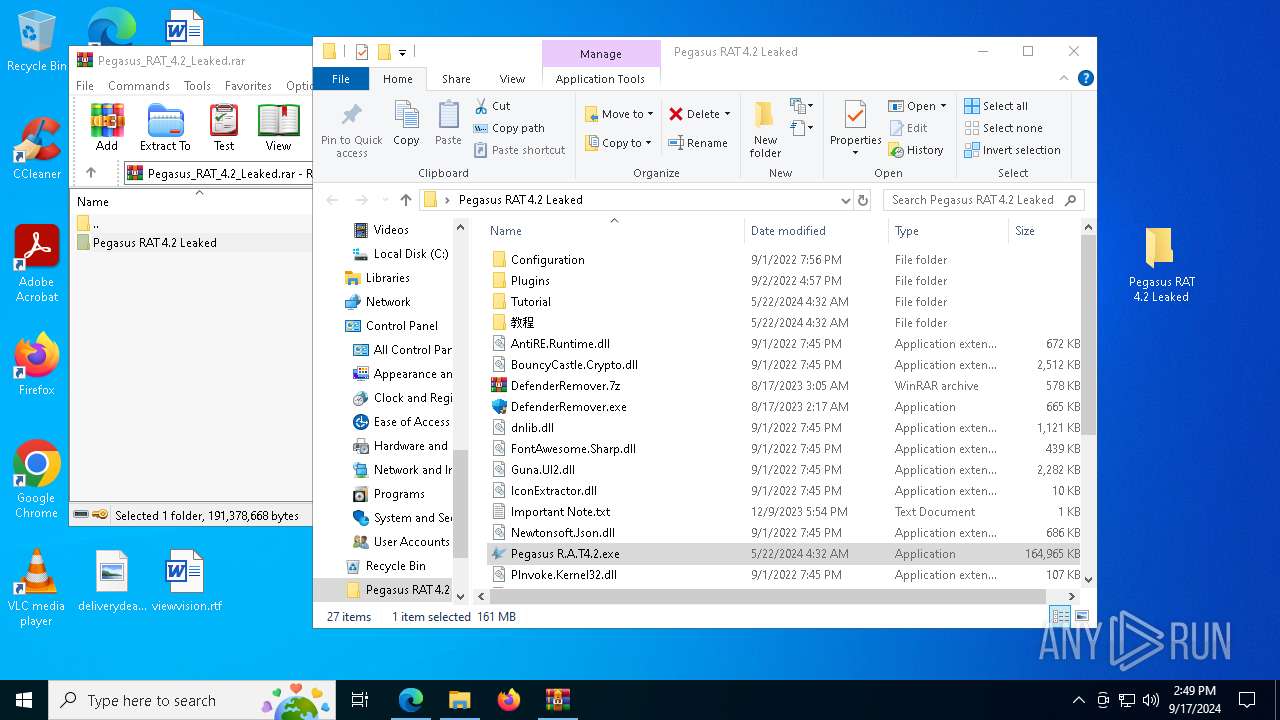
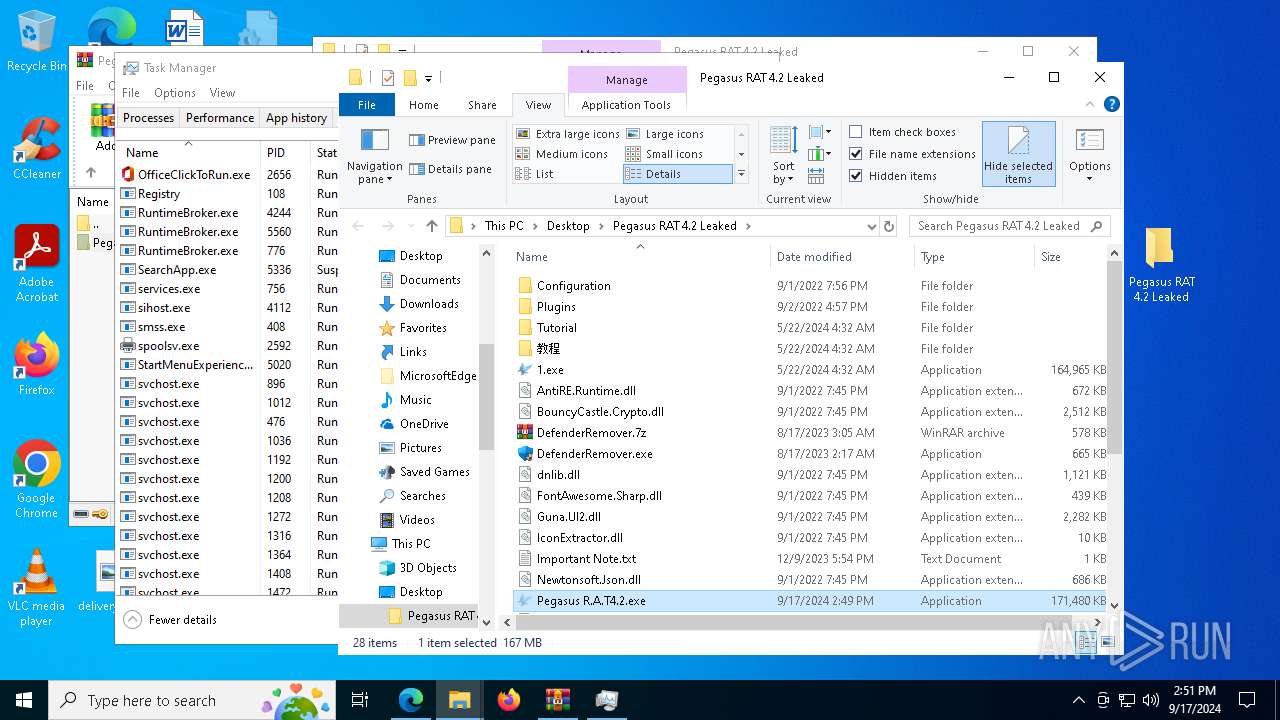
| URL: | https://www.mediafire.com/download/41qnvt4hghrs8cl/Pegasus_RAT_4.2_Leaked.rar |
| Full analysis: | https://app.any.run/tasks/d36883d9-e053-4175-a5dc-a00194ff87cb |
| Verdict: | Malicious activity |
| Threats: | XWorm is a remote access trojan (RAT) sold as a malware-as-a-service. It possesses an extensive hacking toolset and is capable of gathering private information and files from the infected computer, hijacking MetaMask and Telegram accounts, and tracking user activity. XWorm is typically delivered to victims' computers through multi-stage attacks that start with phishing emails. |
| Analysis date: | September 17, 2024, 14:47:05 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 4FB594ECEE7462EE1250597AEE6DC1A3 |
| SHA1: | 0FE9B4F38F71EC9E94A918132947FF001EFF8E86 |
| SHA256: | 9E33ECADE0CE10CECE01D869A4B2D70C851EDF0DA6D68AC1C824FF0CD585070C |
| SSDEEP: | 3:N8DSLw3eGWKLRt3NbdoCEt3kx6+zj+:2OLw3eGNrN5olkx6t |
MALICIOUS
XWORM has been detected (YARA)
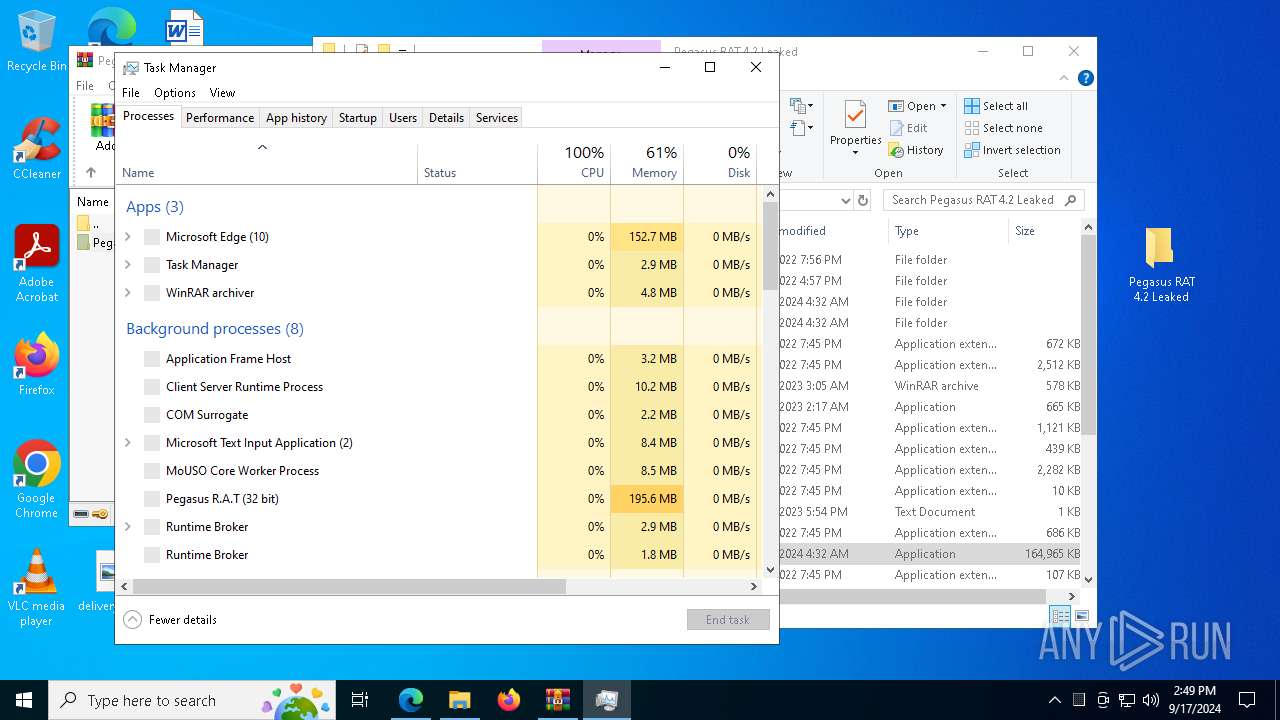
- svchost.exe (PID: 5532)
SUSPICIOUS
Possible usage of Discord/Telegram API has been detected (YARA)
- svchost.exe (PID: 5532)
- csrss.exe (PID: 6256)
Executable content was dropped or overwritten
- Pegasus R.A.T4.2.exe (PID: 7716)
- Pegasus R.A.T4.2.exe (PID: 6740)
Process communicates with Telegram (possibly using it as an attacker's C2 server)
- svchost.exe (PID: 5532)
Found regular expressions for crypto-addresses (YARA)
- csrss.exe (PID: 6256)
Potential Corporate Privacy Violation
- svchost.exe (PID: 2256)
Connects to unusual port
- svchost.exe (PID: 5532)
INFO
Executable content was dropped or overwritten
- msedge.exe (PID: 7436)
- WinRAR.exe (PID: 7068)
Attempting to use instant messaging service
- svchost.exe (PID: 5532)
- svchost.exe (PID: 2256)
Application launched itself
- msedge.exe (PID: 4164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
XWorm
(PID) Process(5532) svchost.exe
C2dsasinject-58214.portmap.io:3389
Keys
AESdefaultdev
Options
Splitter<Xwormmm>
Sleep time3
USB drop nameXWorm V5.6
Mutexr0DPd6eccbr7amlK
ims-api
(PID) Process(5532) svchost.exe
Telegram-Tokens (1)7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk
Telegram-Info-Links
7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk
Get info about bothttps://api.telegram.org/bot7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk/getMe
Get incoming updateshttps://api.telegram.org/bot7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk/getUpdates
Get webhookhttps://api.telegram.org/bot7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk/deleteWebhook?drop_pending_updates=true
Telegram-Requests
Token7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk
End-PointsendMessage
Args
chat_id (1)6354844663
Token7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk
End-PointsendMessage
Args
chat_id (1)6354844663
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : XWorm V5.6 HTTP/1.1
Host: api.telegram.org
Connection: Keep-Alive
Token7023899363:AAFEzgbfWzhyE32Lf95TKSRYEYXMd4AfMyk
End-PointsendMessage
Args
chat_id (1)6354844663
text (1)☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10
Telegram-Responses
oktrue
result
message_id58160
from
id7023899363
is_bottrue
first_name𝕏 Worm
usernameXWormNotifyBot_Bot
chat
id6354844663
first_nameDSAS
usernameDsasSec
typeprivate
date1726584579
text☠ [XWorm V5.6]
New Clinet :
3C54740F7CC0F23B53E5
UserName : admin
OSFullName : Microsoft Windows 10 Pro
USB : False
CPU : Intel i5-6400 @ 2.70GHz
GPU : Microsoft Basic Display Adapter
RAM : 3.99 GB
Groub : XWorm V5.6
(PID) Process(6256) csrss.exe
Telegram-Tokens (1)7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0
Telegram-Info-Links
7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0
Get info about bothttps://api.telegram.org/bot7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0/getMe
Get incoming updateshttps://api.telegram.org/bot7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0/getUpdates
Get webhookhttps://api.telegram.org/bot7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0/getWebhookInfo
Delete webhookhttps://api.telegram.org/bot7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0/deleteWebhook
Drop incoming updateshttps://api.telegram.org/bot7100757996:AAEJpwjH8ugpGk6aMy5fBGtTOc68RQFHaw0/deleteWebhook?drop_pending_updates=true
Discord-Webhook-Tokens (1)1199461955170205769/yzG-CnYBJSYEVcctSaKM0t725UNyOuSROX7wwFB5GocZs5XwGH0p9qOj0JtaMu23bzN6
Discord-Info-Links
1199461955170205769/yzG-CnYBJSYEVcctSaKM0t725UNyOuSROX7wwFB5GocZs5XwGH0p9qOj0JtaMu23bzN6
Get Webhook Infohttps://discord.com/api/webhooks/1199461955170205769/yzG-CnYBJSYEVcctSaKM0t725UNyOuSROX7wwFB5GocZs5XwGH0p9qOj0JtaMu23bzN6
Total processes
217
Monitored processes
77
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=7196 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 360 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2848 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1020 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 7716 -s 1756 | C:\Windows\SysWOW64\WerFault.exe | — | Pegasus R.A.T4.2.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 1064 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=44 --mojo-platform-channel-handle=7980 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1256 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=25 --mojo-platform-channel-handle=5920 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1432 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --no-appcompat-clear --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=41 --mojo-platform-channel-handle=3580 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:1 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1488 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6080 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1492 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=5564 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1792 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5620 --field-trial-handle=2396,i,16566476136538860494,1274738892819016672,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2256 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 767
Read events
11 736
Write events
31
Delete events
0
Modification events
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 28223E0CE8802F00 | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 8ADC430CE8802F00 | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {A276229F-6FA6-438F-84B5-270ECD400BEE} | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {1D92766F-7BA6-4A55-B854-9AB43A12CF16} | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {87479B08-F39A-4B96-A6FD-2F37B87BF209} | |||
| (PID) Process: | (4164) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197538 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {8A03638F-4A1B-415E-B115-7AE6F09FE49D} | |||
Executable files
25
Suspicious files
622
Text files
155
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF1c8360.TMP | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1c8331.TMP | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF1c8360.TMP | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF1c8370.TMP | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1c8360.TMP | — | |
MD5:— | SHA256:— | |||
| 4164 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
75
TCP/UDP connections
227
DNS requests
244
Threats
14
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6328 | svchost.exe | GET | — | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1964 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8096 | svchost.exe | HEAD | 200 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7aedcc9a-74db-486d-833c-3f9898813873?P1=1727164621&P2=404&P3=2&P4=NCXBBWM7ig9Icf0jdtxntBKsJK2CDyOU78x12%2fQWdU8GMp3wHFSlx45Dvbt%2bpWOOSzfB3U8%2faCc%2bncBpIcNDLg%3d%3d | unknown | — | — | whitelisted |
7768 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7768 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8096 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7aedcc9a-74db-486d-833c-3f9898813873?P1=1727164621&P2=404&P3=2&P4=NCXBBWM7ig9Icf0jdtxntBKsJK2CDyOU78x12%2fQWdU8GMp3wHFSlx45Dvbt%2bpWOOSzfB3U8%2faCc%2bncBpIcNDLg%3d%3d | unknown | — | — | whitelisted |
8096 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7aedcc9a-74db-486d-833c-3f9898813873?P1=1727164621&P2=404&P3=2&P4=NCXBBWM7ig9Icf0jdtxntBKsJK2CDyOU78x12%2fQWdU8GMp3wHFSlx45Dvbt%2bpWOOSzfB3U8%2faCc%2bncBpIcNDLg%3d%3d | unknown | — | — | whitelisted |
8096 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7aedcc9a-74db-486d-833c-3f9898813873?P1=1727164621&P2=404&P3=2&P4=NCXBBWM7ig9Icf0jdtxntBKsJK2CDyOU78x12%2fQWdU8GMp3wHFSlx45Dvbt%2bpWOOSzfB3U8%2faCc%2bncBpIcNDLg%3d%3d | unknown | — | — | whitelisted |
8096 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7aedcc9a-74db-486d-833c-3f9898813873?P1=1727164621&P2=404&P3=2&P4=NCXBBWM7ig9Icf0jdtxntBKsJK2CDyOU78x12%2fQWdU8GMp3wHFSlx45Dvbt%2bpWOOSzfB3U8%2faCc%2bncBpIcNDLg%3d%3d | unknown | — | — | whitelisted |
8096 | svchost.exe | GET | 206 | 199.232.210.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/7aedcc9a-74db-486d-833c-3f9898813873?P1=1727164621&P2=404&P3=2&P4=NCXBBWM7ig9Icf0jdtxntBKsJK2CDyOU78x12%2fQWdU8GMp3wHFSlx45Dvbt%2bpWOOSzfB3U8%2faCc%2bncBpIcNDLg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6624 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5656 | msedge.exe | 104.21.42.32:443 | the.gatekeeperconsent.com | — | — | unknown |
5656 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4164 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5656 | msedge.exe | 104.17.150.117:443 | www.mediafire.com | — | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
www.mediafire.com |
| shared |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.bing.com |
| whitelisted |
the.gatekeeperconsent.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5656 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
5656 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain (www .mediafire .com) in DNS Lookup |
5656 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
5656 | msedge.exe | Potentially Bad Traffic | ET HUNTING File Sharing Related Domain in DNS Lookup (download .mediafire .com) |
5656 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
5656 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
5656 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
5656 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
2256 | svchost.exe | Misc activity | ET HUNTING Telegram API Domain in DNS Lookup |
5532 | svchost.exe | Misc activity | ET HUNTING Observed Telegram API Domain (api .telegram .org in TLS SNI) |