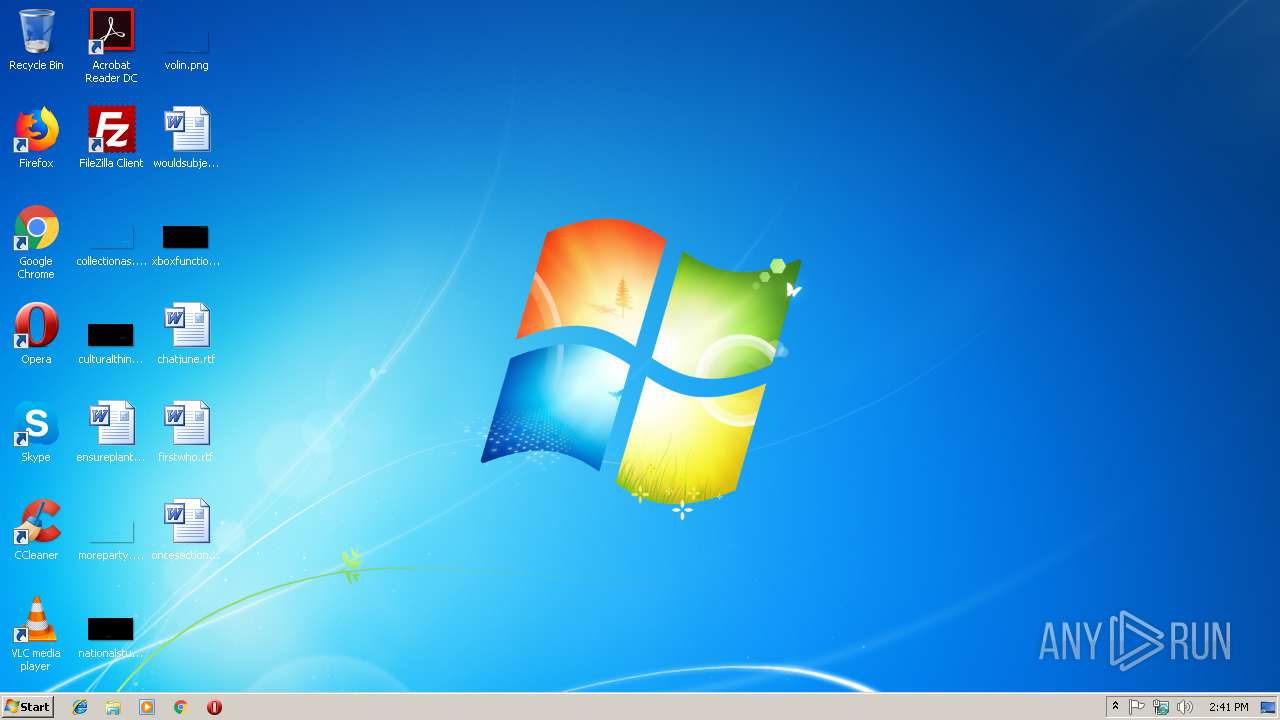
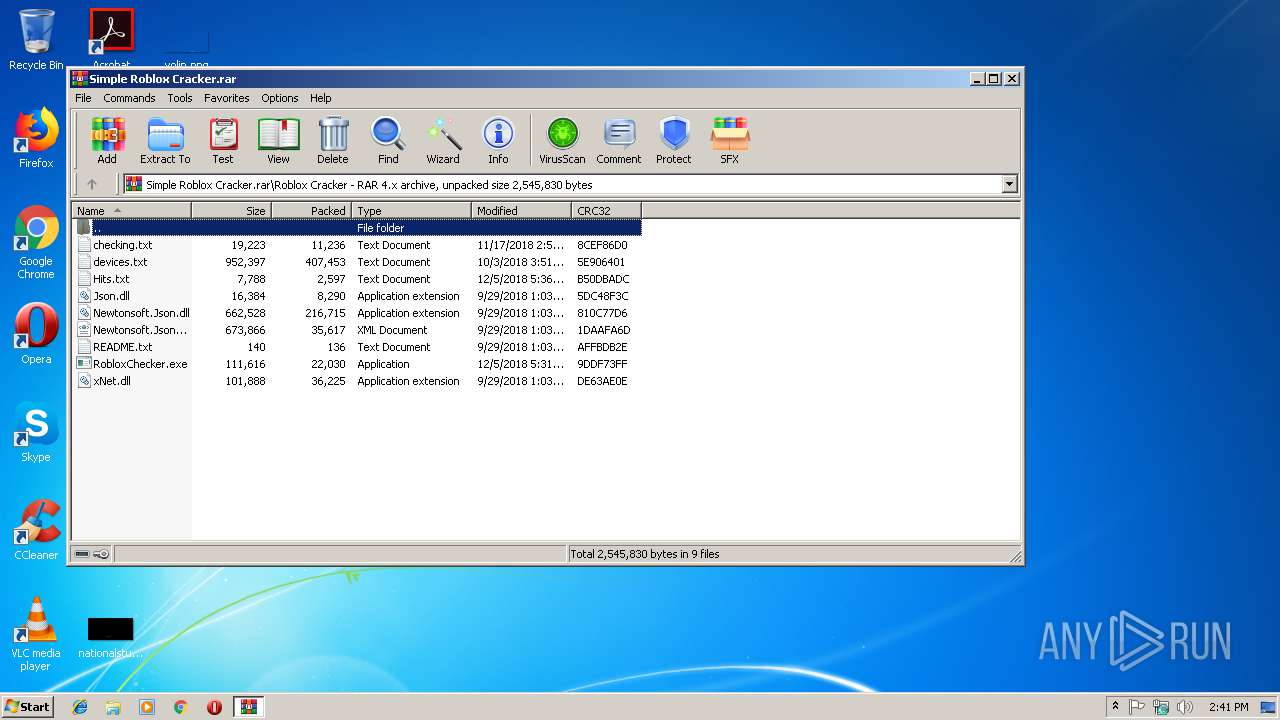
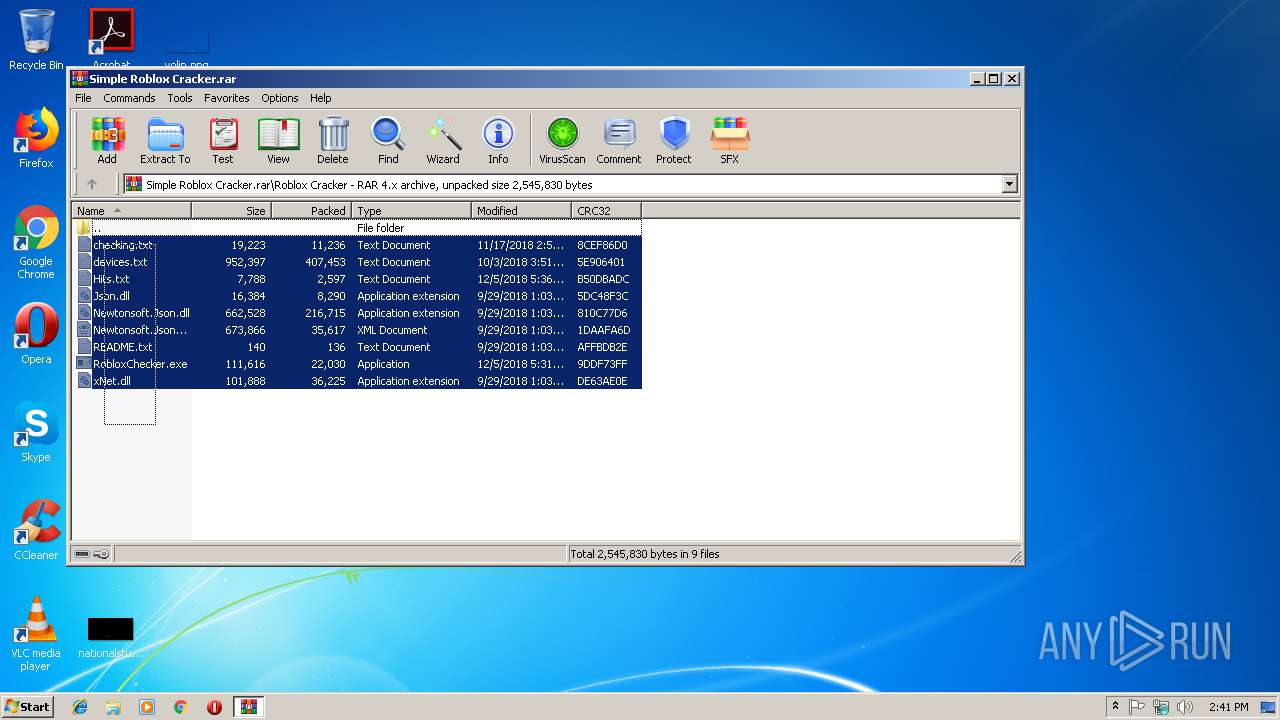
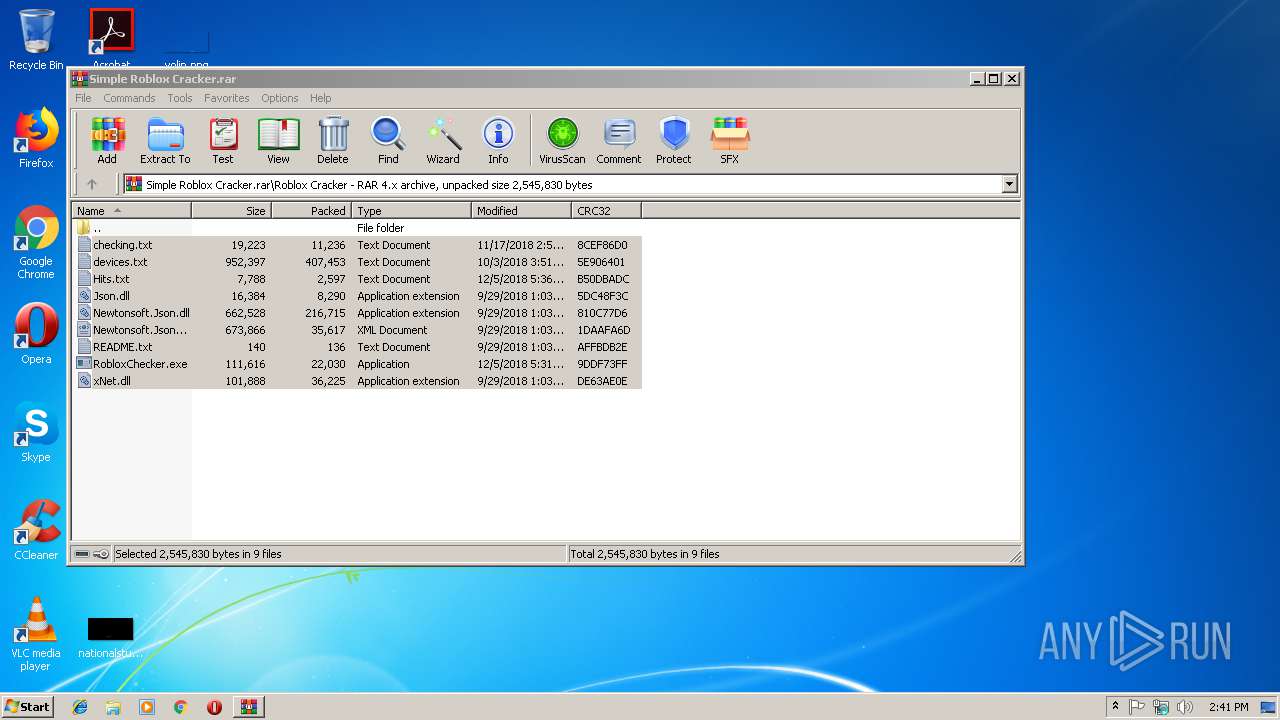
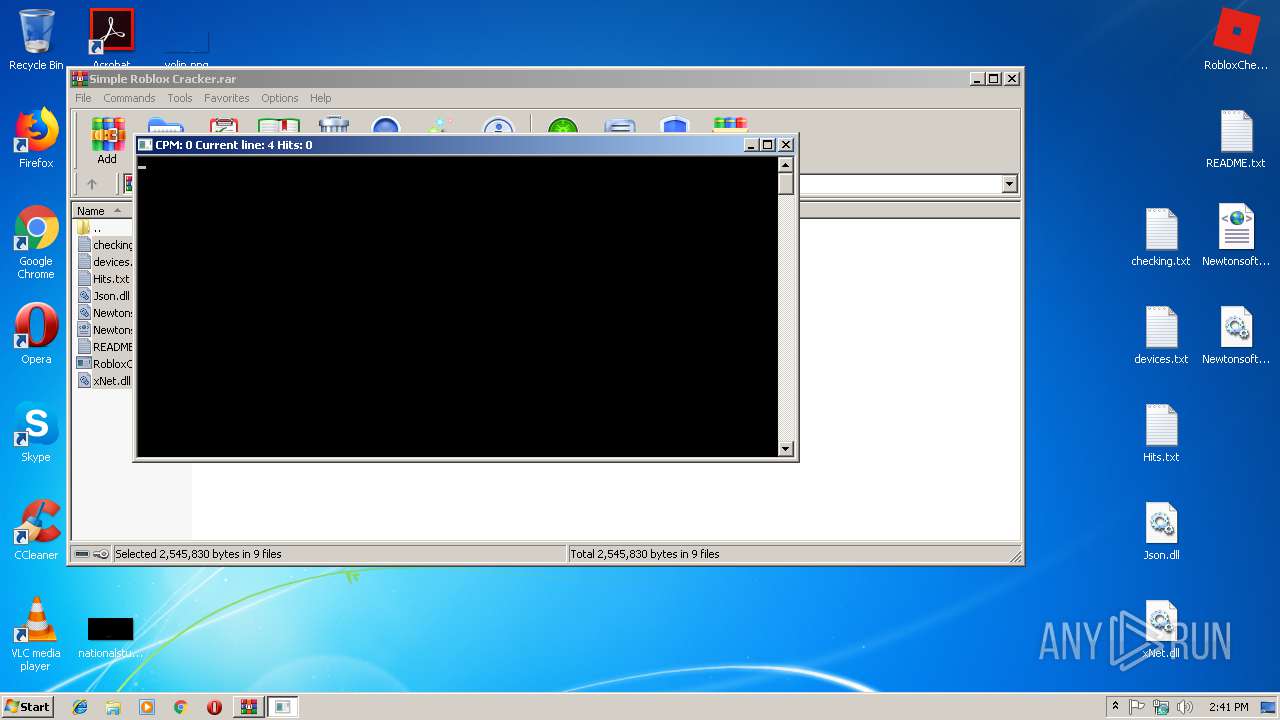
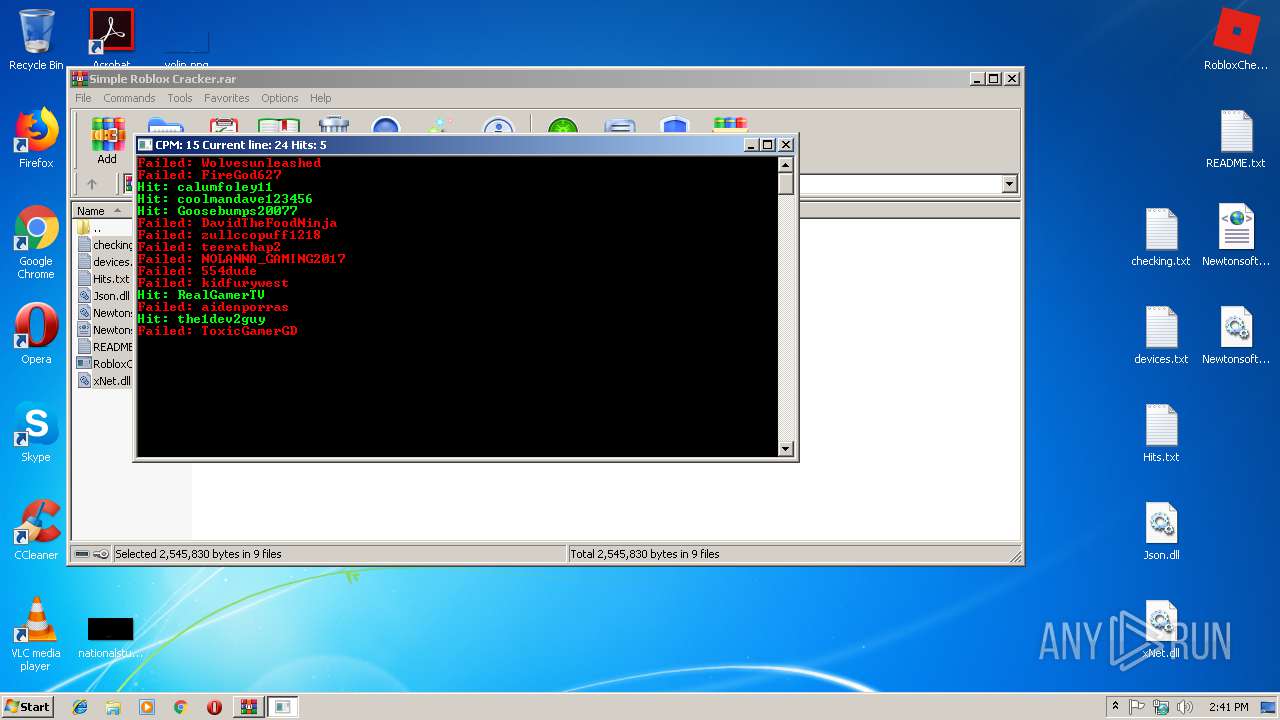
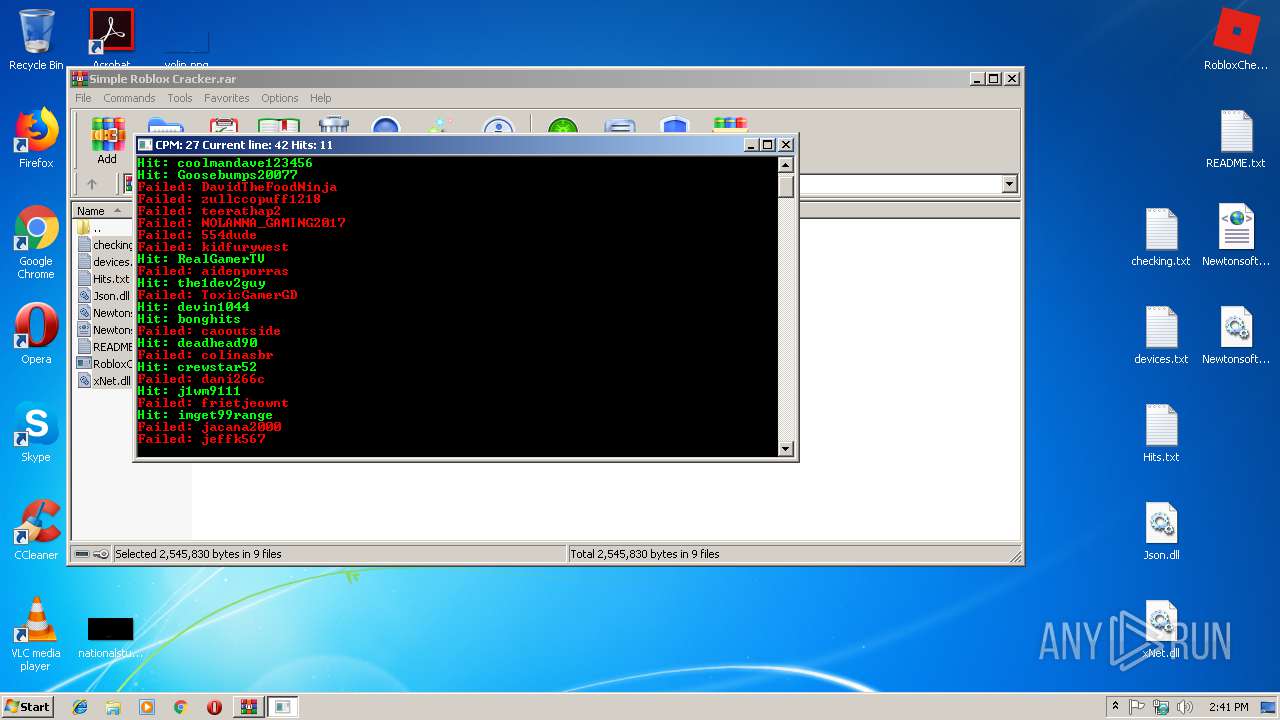
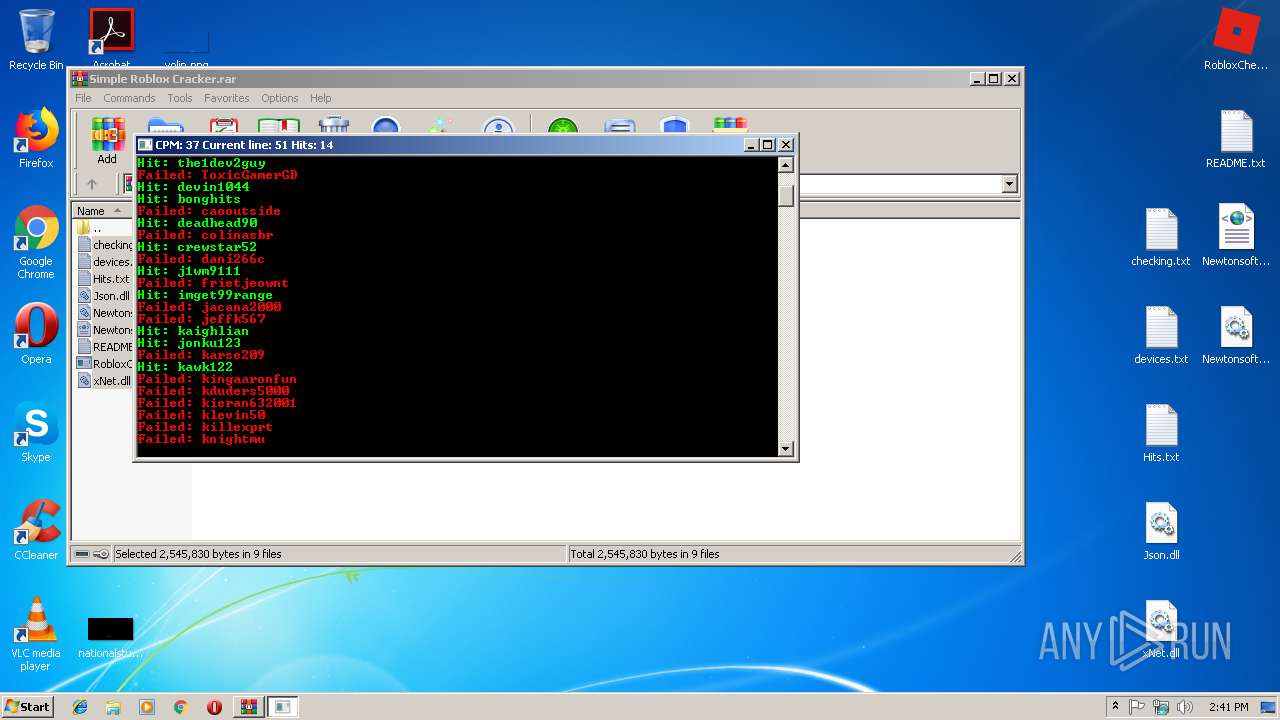
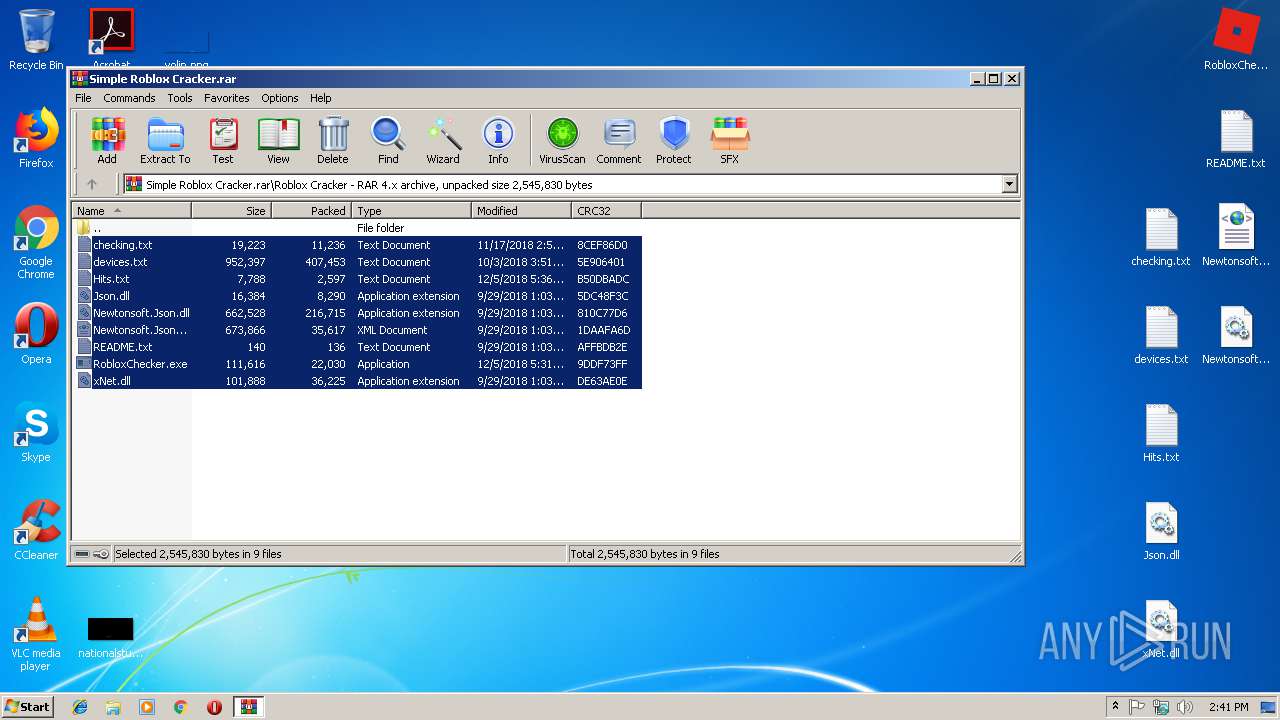
| File name: | Simple Roblox Cracker.rar |
| Full analysis: | https://app.any.run/tasks/ecef002f-ea29-4984-90ba-dda9f383f773 |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2018, 14:40:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 3ABD9E3083C717AE93D4B4C11D12F04A |
| SHA1: | 6440BD9E58BF9761DAAAD0DD97DA565DC57F8FD7 |
| SHA256: | 9E1EFD1C7C6EDD275AF0AF9F415753EDACA9B2AC2E863B1FD74CE9A2BBB890E6 |
| SSDEEP: | 12288:gcdu7gfMazkIDcAszqepOO7MVaxnhfxQlgQ9cov2Lmum4v32d8egvbtP4+Uy:3dGgfZYccAsOXh8vil7VKmB4O3mpP4+j |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 416)
Application was dropped or rewritten from another process
- RobloxChecker.exe (PID: 2508)
- stub.exe (PID: 2252)
- Cracker.exe (PID: 2868)
SUSPICIOUS
Executable content was dropped or overwritten
- RobloxChecker.exe (PID: 2508)
- WinRAR.exe (PID: 2940)
- stub.exe (PID: 2252)
Reads the cookies of Google Chrome
- stub.exe (PID: 2252)
INFO
Reads settings of System Certificates
- Cracker.exe (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 11289 |
|---|---|
| UncompressedSize: | 19223 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2018:11:17 14:59:16 |
| PackingMethod: | Normal |
| ArchivedFileName: | Roblox Cracker\checking.txt |
Total processes
36
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 416 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2252 | "C:\Users\admin\AppData\Local\Temp\stub.exe" | C:\Users\admin\AppData\Local\Temp\stub.exe | RobloxChecker.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 4294967295 Version: 0.0.0.0 Modules
| |||||||||||||||
| 2508 | "C:\Users\admin\Desktop\RobloxChecker.exe" | C:\Users\admin\Desktop\RobloxChecker.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 4294967295 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2868 | "C:\Users\admin\AppData\Local\Temp\Cracker.exe" | C:\Users\admin\AppData\Local\Temp\Cracker.exe | stub.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ConsoleApp6 Exit code: 3221225786 Version: 1.0.0.0 Modules
| |||||||||||||||
| 2940 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Simple Roblox Cracker.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
1 379
Read events
1 289
Write events
90
Delete events
0
Modification events
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Simple Roblox Cracker.rar | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2940) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
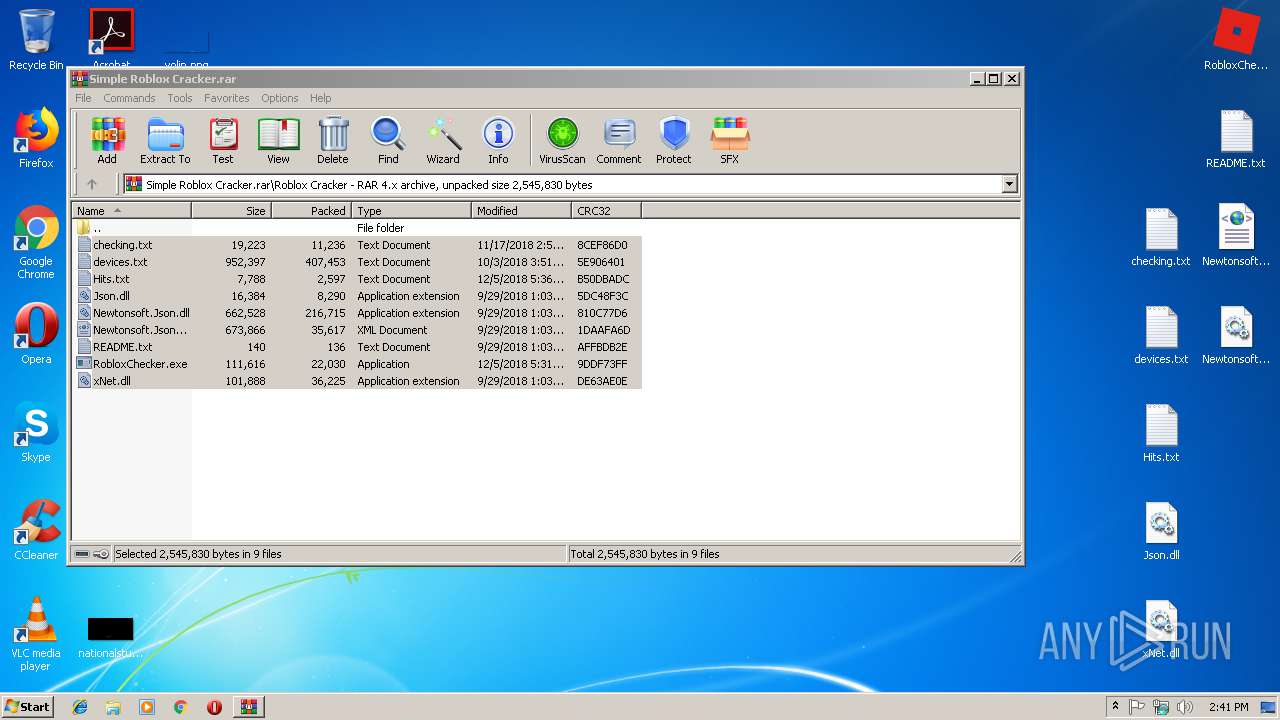
Executable files
4
Suspicious files
0
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\README.txt | — | |
MD5:— | SHA256:— | |||
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\RobloxChecker.exe | — | |
MD5:— | SHA256:— | |||
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\xNet.dll | — | |
MD5:— | SHA256:— | |||
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\devices.txt | text | |
MD5:— | SHA256:— | |||
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\checking.txt | text | |
MD5:— | SHA256:— | |||
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\Newtonsoft.Json.dll | executable | |
MD5:5AFDA7C7D4F7085E744C2E7599279DB3 | SHA256:F58C374FFCAAE4E36D740D90FBF7FE70D0ABB7328CD9AF3A0A7B70803E994BA4 | |||
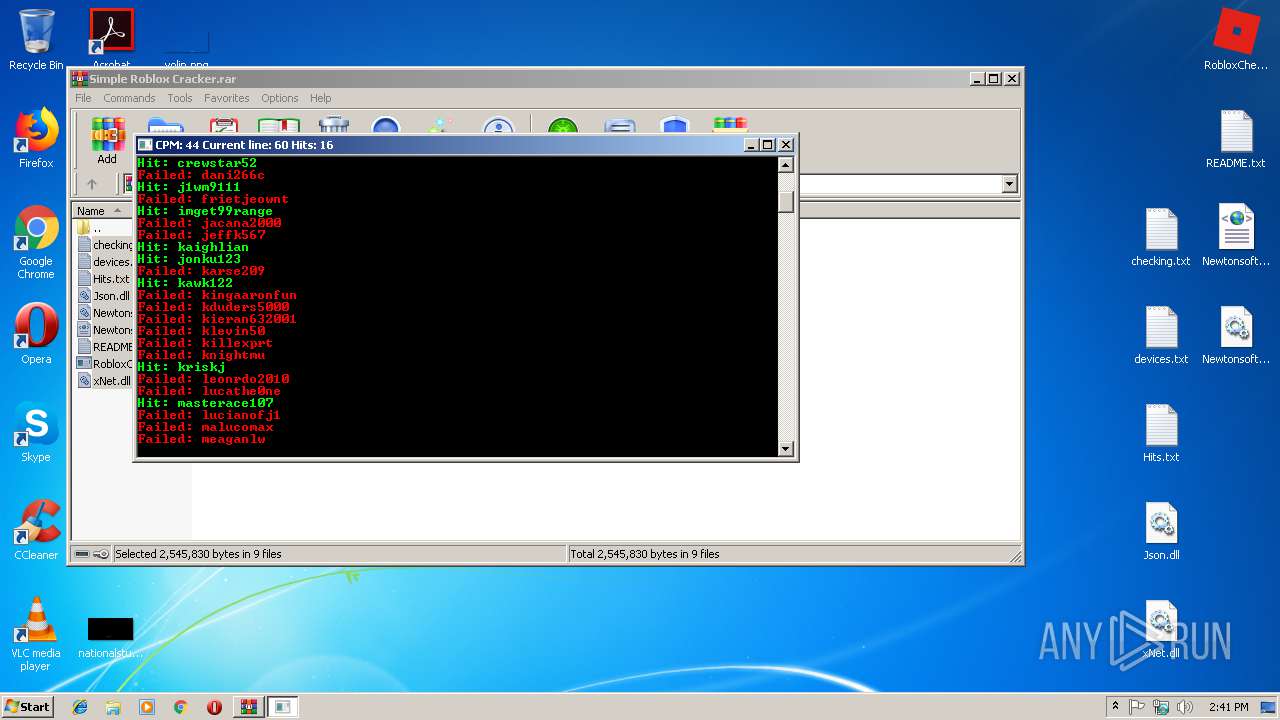
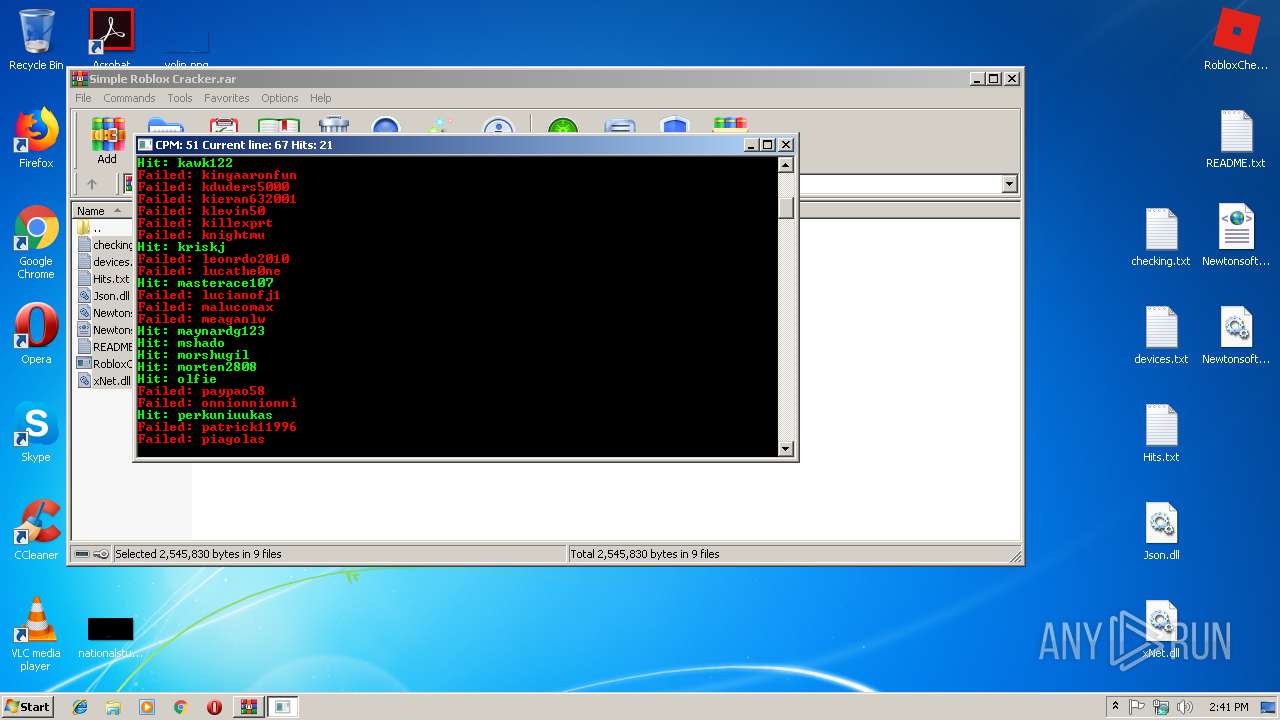
| 2868 | Cracker.exe | C:\Users\admin\Desktop\Hits.txt | text | |
MD5:— | SHA256:— | |||
| 2940 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2940.28635\Roblox Cracker\Hits.txt | text | |
MD5:— | SHA256:— | |||
| 2508 | RobloxChecker.exe | C:\Users\admin\AppData\Local\Temp\stub.exe | executable | |
MD5:— | SHA256:— | |||
| 2252 | stub.exe | C:\Users\admin\AppData\Local\Temp\Cracker.exe | executable | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
47
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 203 b | whitelisted |
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 203 b | whitelisted |
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 208 b | whitelisted |
2508 | RobloxChecker.exe | GET | 200 | 198.91.80.25:80 | http://cookiemuncher.x10host.com/CMR7Files/check.php?hwid=OTM7v7nJFts6B5pbS5SSB5GqILMeEBpoqyZIIXo/HlDyA9Xy5eVRmFyiCsN6nmnzeRexvimhnU6kOsBWM2IF4V%2BCxq3kGY6Vt7KhntxkPZUnCVFcOwbVn2XwWps4/sWl | US | html | 6.03 Kb | malicious |
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 201 b | whitelisted |
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 202 b | whitelisted |
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 197 b | whitelisted |
2868 | Cracker.exe | GET | 200 | 209.206.41.46:80 | http://www.roblox.com/mobileapi/userinfo | US | text | 198 b | whitelisted |
2252 | stub.exe | GET | 200 | 198.91.80.25:80 | http://cookiemuncher.x10host.com/CMR7Files/check.php?hwid=OTM7v7nJFts6B5pbS5SSB5GqILMeEBpoqyZIIXo/HlDyA9Xy5eVRmFyiCsN6nmnzeRexvimhnU6kOsBWM2IF4V%2BCxq3kGY6Vt7KhntxkPZUnCVFcOwbVn2XwWps4/sWl | US | html | 6.03 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2868 | Cracker.exe | 209.206.41.46:443 | www.roblox.com | Roblox | US | unknown |
2868 | Cracker.exe | 209.206.41.46:80 | www.roblox.com | Roblox | US | unknown |
2252 | stub.exe | 198.91.80.25:80 | cookiemuncher.x10host.com | SingleHop, Inc. | US | malicious |
2252 | stub.exe | 104.16.58.5:443 | discordapp.com | Cloudflare Inc | US | shared |
2868 | Cracker.exe | 209.206.41.3:443 | api.roblox.com | Roblox | US | unknown |
2508 | RobloxChecker.exe | 198.91.80.25:80 | cookiemuncher.x10host.com | SingleHop, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cookiemuncher.x10host.com |
| malicious |
discordapp.com |
| whitelisted |
api.roblox.com |
| malicious |
www.roblox.com |
| whitelisted |