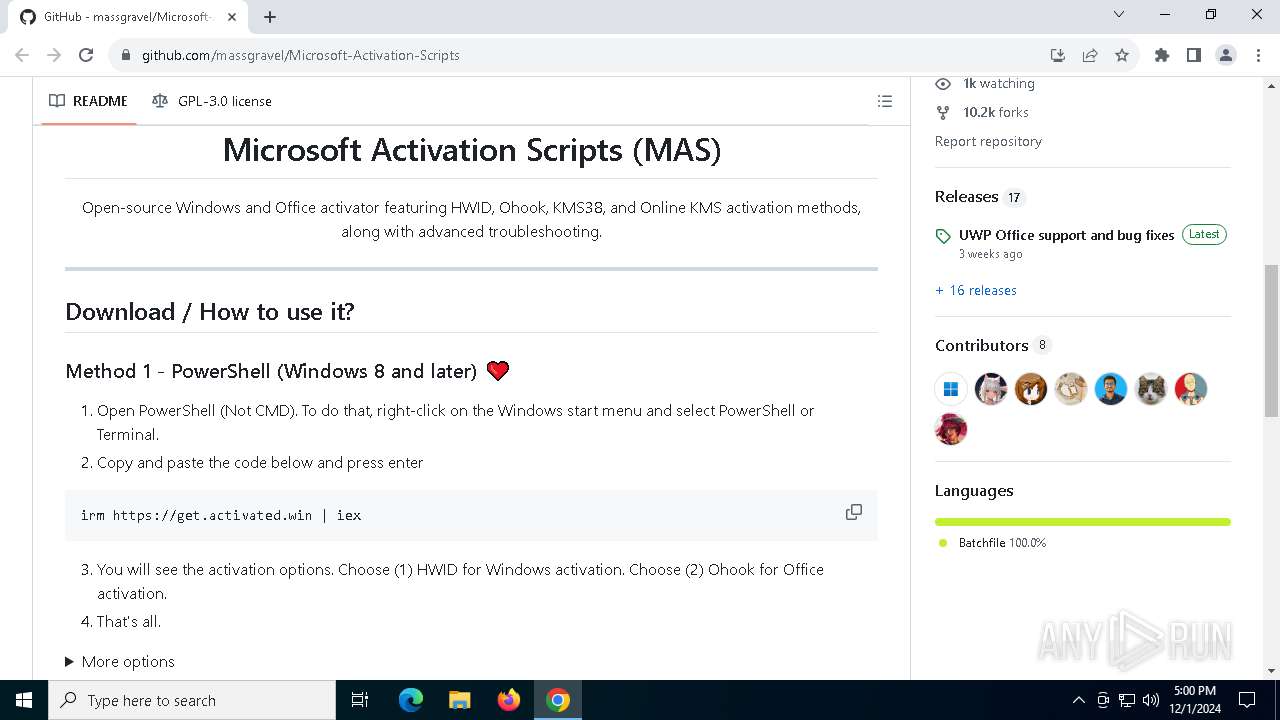
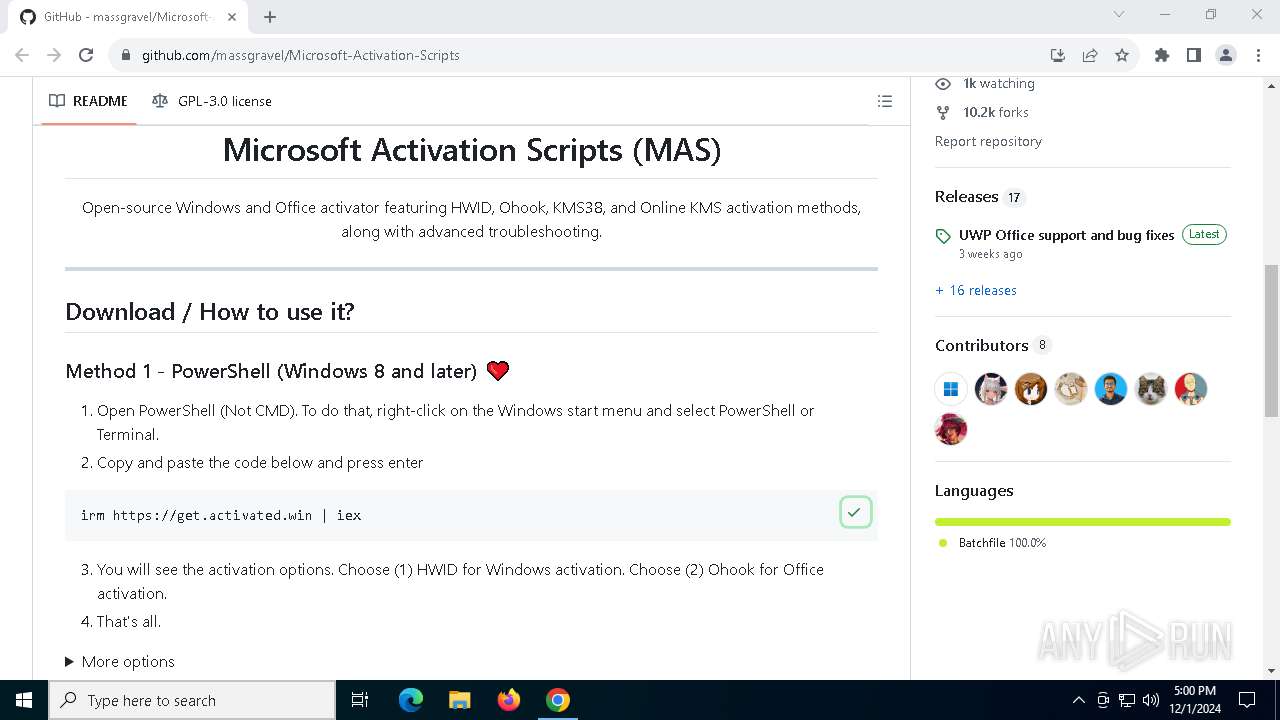
| URL: | https://github.com/massgravel/Microsoft-Activation-Scripts |
| Full analysis: | https://app.any.run/tasks/b1dbceca-837a-4b5b-956e-db55740e94b1 |
| Verdict: | Malicious activity |
| Analysis date: | December 01, 2024, 16:59:45 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | AFD6FF84DA2D0BA12E52C775DF44B55B |
| SHA1: | 01C9074D7E2703A728921432F53128804DA08B5E |
| SHA256: | 9E176C48748F3D4D4303D5D603F477906CE34A381ACACC46ADB8DC346A2F00D9 |
| SSDEEP: | 3:N8tEd4PKoHXuukGR3RLLLGXUw:2uuPKzukGv/LGXUw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts CMD.EXE for commands execution
- pwsh.exe (PID: 5544)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 7612)
- powershell.exe (PID: 7884)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 5240)
- powershell.exe (PID: 7344)
- cmd.exe (PID: 7676)
- cmd.exe (PID: 7492)
Starts SC.EXE for service management
- cmd.exe (PID: 7392)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7492)
Executing commands from ".cmd" file
- pwsh.exe (PID: 5544)
- cmd.exe (PID: 7392)
- powershell.exe (PID: 7884)
- cmd.exe (PID: 8016)
- powershell.exe (PID: 7344)
- cmd.exe (PID: 7492)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7392)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7492)
- cmd.exe (PID: 7828)
Application launched itself
- cmd.exe (PID: 7392)
- cmd.exe (PID: 7612)
- cmd.exe (PID: 5240)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7676)
- powershell.exe (PID: 5576)
- cmd.exe (PID: 7492)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7720)
- cmd.exe (PID: 7152)
- cmd.exe (PID: 7828)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7720)
- cmd.exe (PID: 7392)
- cmd.exe (PID: 7152)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7828)
- cmd.exe (PID: 7492)
- powershell.exe (PID: 5576)
- cmd.exe (PID: 7664)
- cmd.exe (PID: 8140)
- cmd.exe (PID: 5268)
- cmd.exe (PID: 3696)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 396)
- cmd.exe (PID: 7396)
- cmd.exe (PID: 7228)
- cmd.exe (PID: 4576)
- cmd.exe (PID: 3792)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 936)
- cmd.exe (PID: 4872)
- cmd.exe (PID: 4360)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 7720)
- cmd.exe (PID: 7152)
- cmd.exe (PID: 7828)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 5576)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 6848)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 5576)
Hides command output
- cmd.exe (PID: 7796)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 7728)
- cmd.exe (PID: 8012)
- cmd.exe (PID: 7920)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6156)
- cmd.exe (PID: 7920)
Executable content was dropped or overwritten
- Dism.exe (PID: 7808)
- Dism.exe (PID: 7904)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 6428)
- DismHost.exe (PID: 4944)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7492)
INFO
Application launched itself
- chrome.exe (PID: 6292)
Reads the computer name
- pwsh.exe (PID: 5544)
Checks supported languages
- pwsh.exe (PID: 5544)
Manual execution by a user
- pwsh.exe (PID: 5544)
Checks operating system version
- cmd.exe (PID: 7392)
- cmd.exe (PID: 8016)
- cmd.exe (PID: 7492)
Starts MODE.COM to configure console settings
- mode.com (PID: 5748)
- mode.com (PID: 7316)
- mode.com (PID: 7328)
- mode.com (PID: 7288)
Executable content was dropped or overwritten
- chrome.exe (PID: 7528)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
404
Monitored processes
263
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5240 --field-trial-handle=1932,i,13899568886106625310,11182392149807670529,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 188 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | C:\WINDOWS\System32\cmd.exe /c powershell.exe "$AssemblyBuilder = [AppDomain]::CurrentDomain.DefineDynamicAssembly(4, 1); $ModuleBuilder = $AssemblyBuilder.DefineDynamicModule(2, $False); $TypeBuilder = $ModuleBuilder.DefineType(0); [void]$TypeBuilder.DefinePInvokeMethod('PidGenX', 'pidgenx.dll', 'Public, Static', 1, [int], @([String], [String], [String], [int], [IntPtr], [IntPtr], [IntPtr]), 1, 3); $r = [byte[]]::new(0x04F8); $r[0] = 0xF8; $r[1] = 0x04; $f = [Runtime.InteropServices.Marshal]::AllocHGlobal(0x04F8); [Runtime.InteropServices.Marshal]::Copy($r, 0, $f, 0x04F8); [void]$TypeBuilder.CreateType()::PidGenX('+', 'C:\WINDOWS\System32\spp\tokens\pkeyconfig\pkeyconfig.xrm-ms', '00000', 0, 0, 0, $f); [Runtime.InteropServices.Marshal]::Copy($f, $r, 0, 0x04F8); [Runtime.InteropServices.Marshal]::FreeHGlobal($f); [Text.Encoding]::Unicode.GetString($r, 1016, 128)" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 540 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 628 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "AMD64 " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | find /i " ServerRdsh " | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 768 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo Education " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 936 | C:\WINDOWS\System32\cmd.exe /c powershell.exe "$AssemblyBuilder = [AppDomain]::CurrentDomain.DefineDynamicAssembly(4, 1); $ModuleBuilder = $AssemblyBuilder.DefineDynamicModule(2, $False); $TypeBuilder = $ModuleBuilder.DefineType(0); [void]$TypeBuilder.DefinePInvokeMethod('PidGenX', 'pidgenx.dll', 'Public, Static', 1, [int], @([String], [String], [String], [int], [IntPtr], [IntPtr], [IntPtr]), 1, 3); $r = [byte[]]::new(0x04F8); $r[0] = 0xF8; $r[1] = 0x04; $f = [Runtime.InteropServices.Marshal]::AllocHGlobal(0x04F8); [Runtime.InteropServices.Marshal]::Copy($r, 0, $f, 0x04F8); [void]$TypeBuilder.CreateType()::PidGenX('+', 'C:\WINDOWS\System32\spp\tokens\pkeyconfig\pkeyconfig.xrm-ms', '00000', 0, 0, 0, $f); [Runtime.InteropServices.Marshal]::Copy($f, $r, 0, 0x04F8); [Runtime.InteropServices.Marshal]::FreeHGlobal($f); [Text.Encoding]::Unicode.GetString($r, 1016, 128)" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1080 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
118 292
Read events
118 264
Write events
22
Delete events
6
Modification events
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2408) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31147026 | |||
| (PID) Process: | (2408) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (6292) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
Executable files
105
Suspicious files
100
Text files
84
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1365a3.TMP | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1365b2.TMP | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1365b2.TMP | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF1365b2.TMP | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1365c2.TMP | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6292 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
27
TCP/UDP connections
99
DNS requests
63
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5544 | pwsh.exe | GET | 200 | 23.48.23.147:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7272 | SIHClient.exe | GET | 200 | 23.37.237.227:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7520 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7520 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7520 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
7520 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2356 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.147:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.37.237.227:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 2.16.204.158:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 40.126.31.67:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
github.com |
| shared |
accounts.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5544 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
Process | Message |
|---|---|
Dism.exe | PID=7808 TID=7824 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=7808 TID=7824 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=7808 TID=7824 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=7808 TID=7824 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=7808 TID=7824 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=7808 TID=7824 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=6428 TID=2152 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=6428 TID=2152 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=6428 TID=2152 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=7808 TID=7824 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |