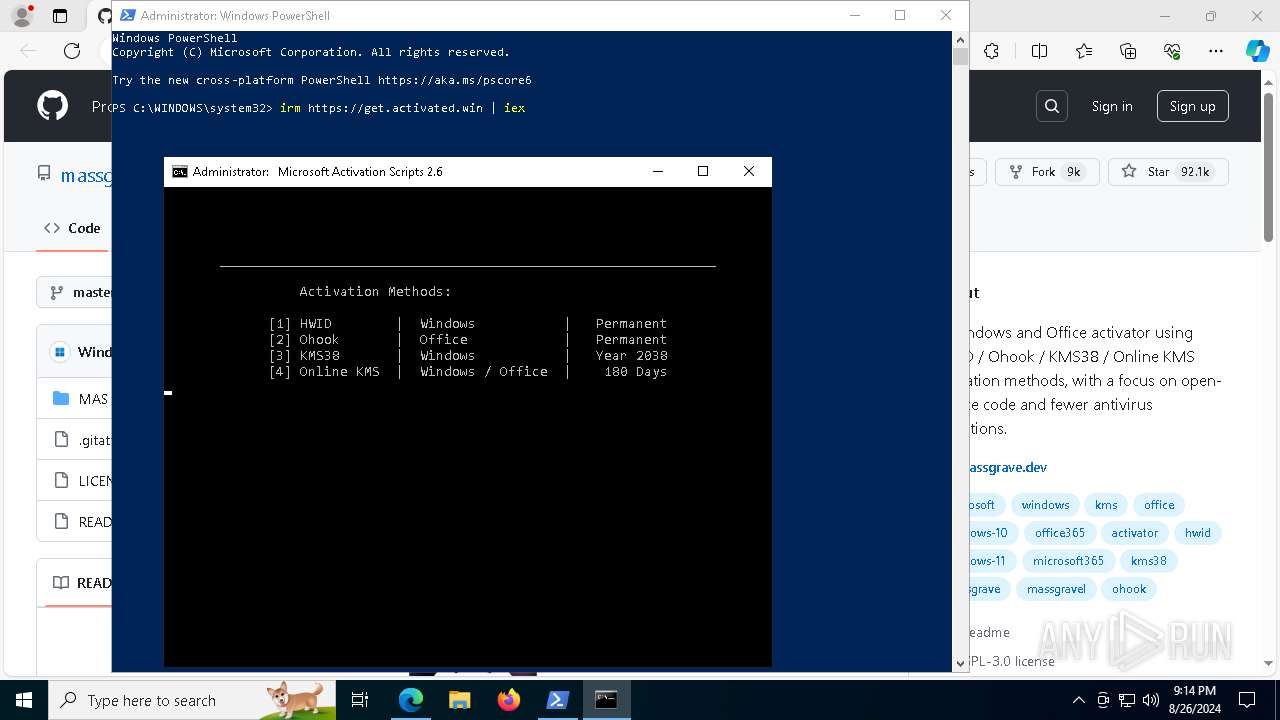
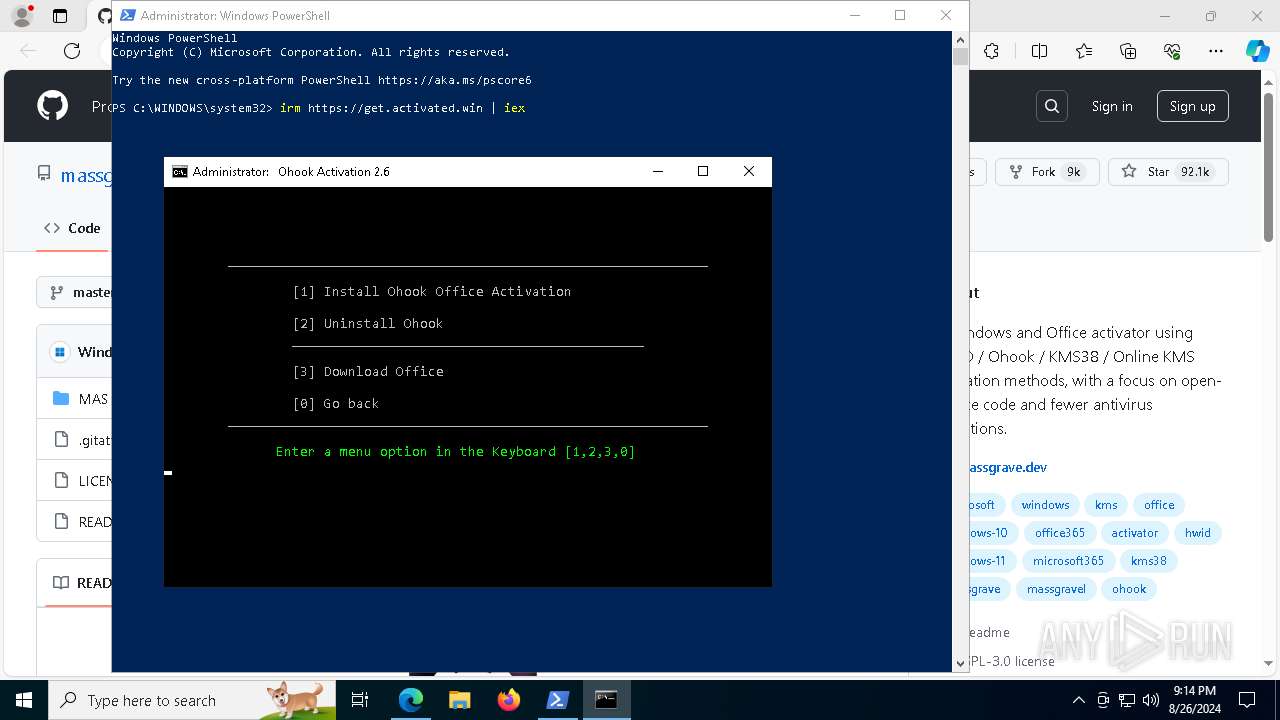
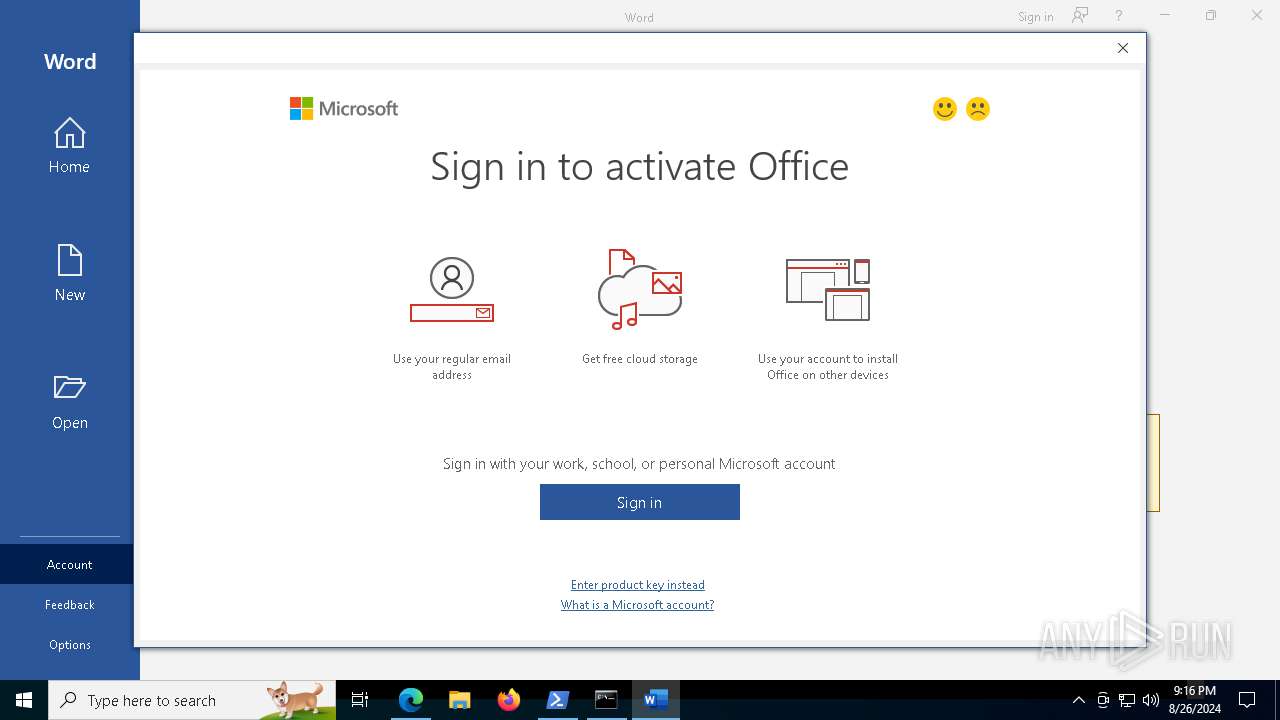
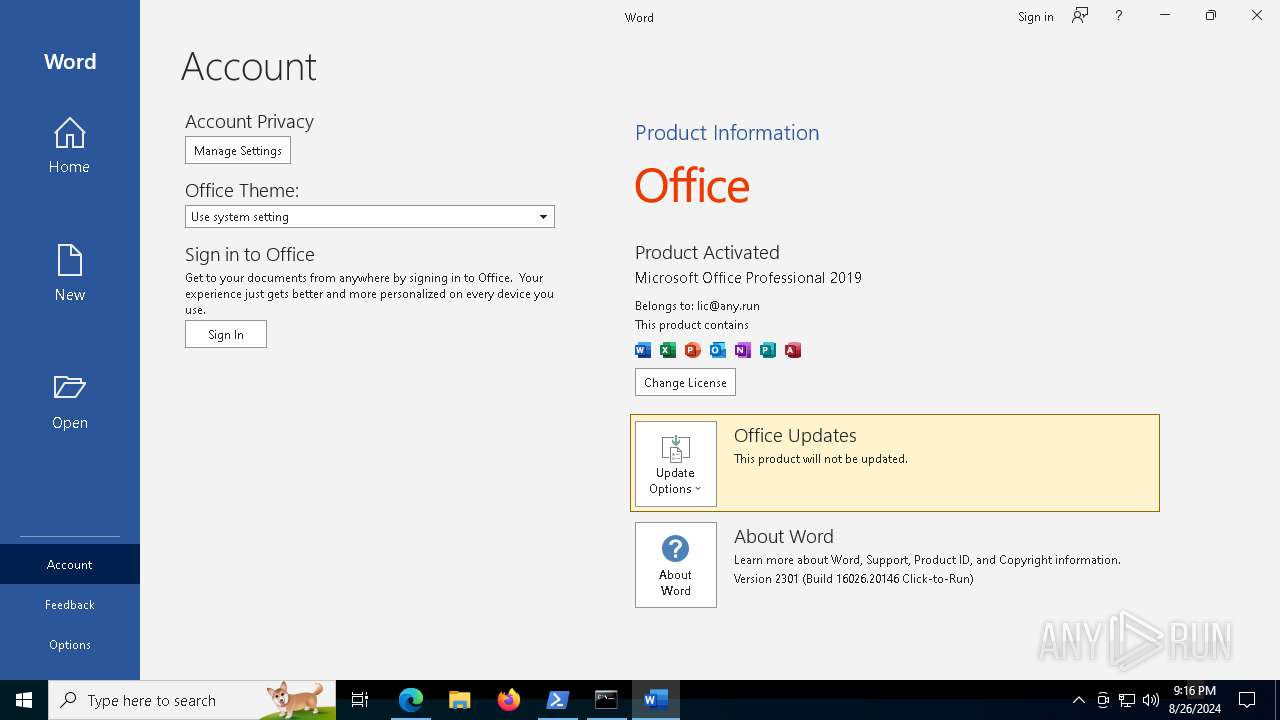
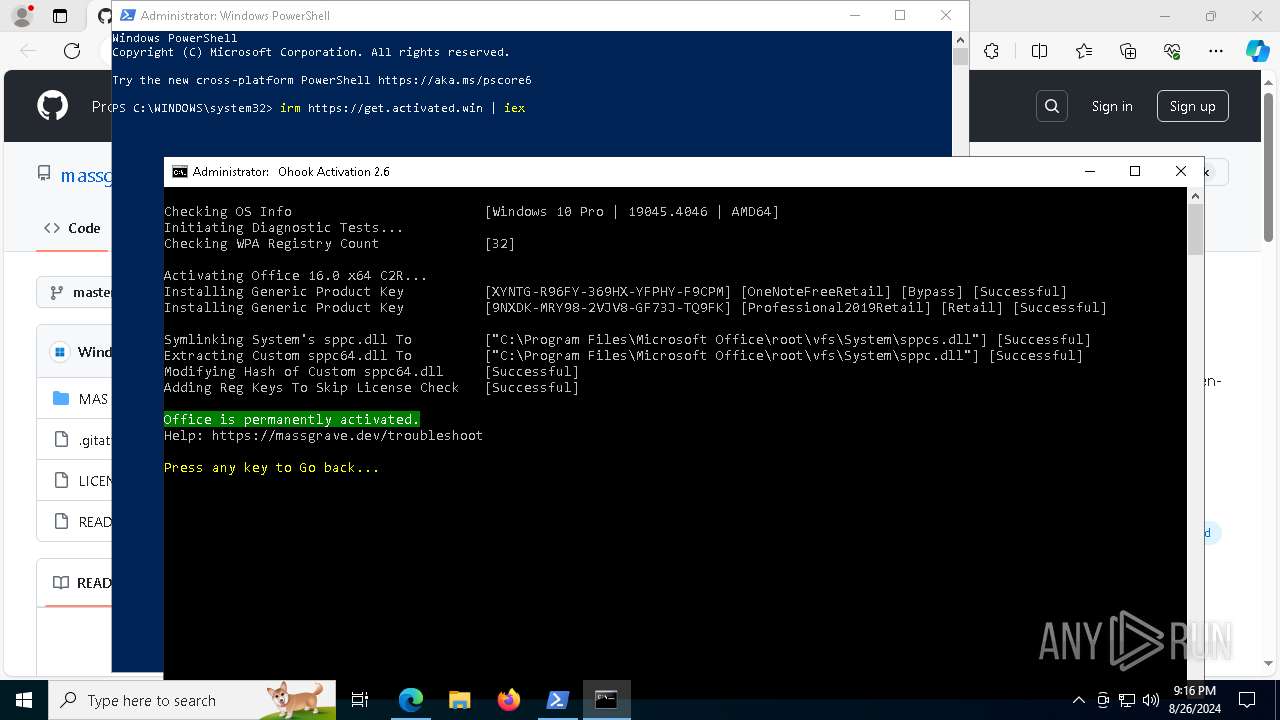
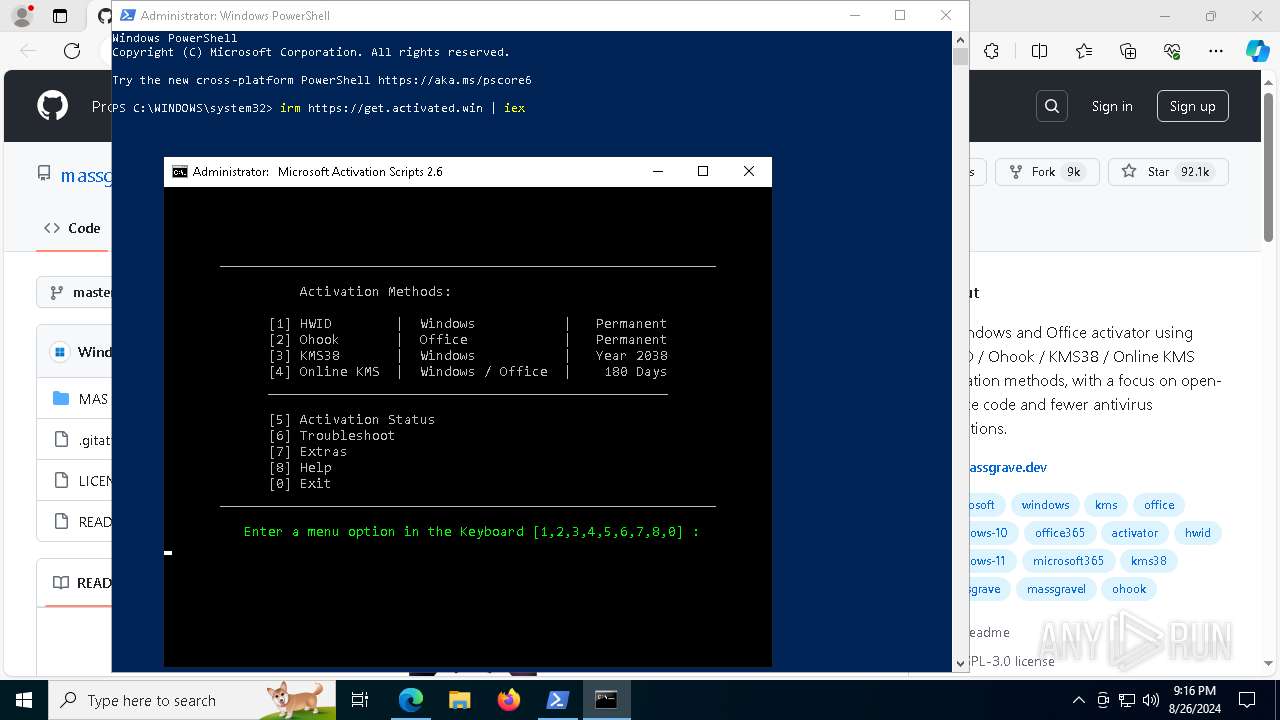
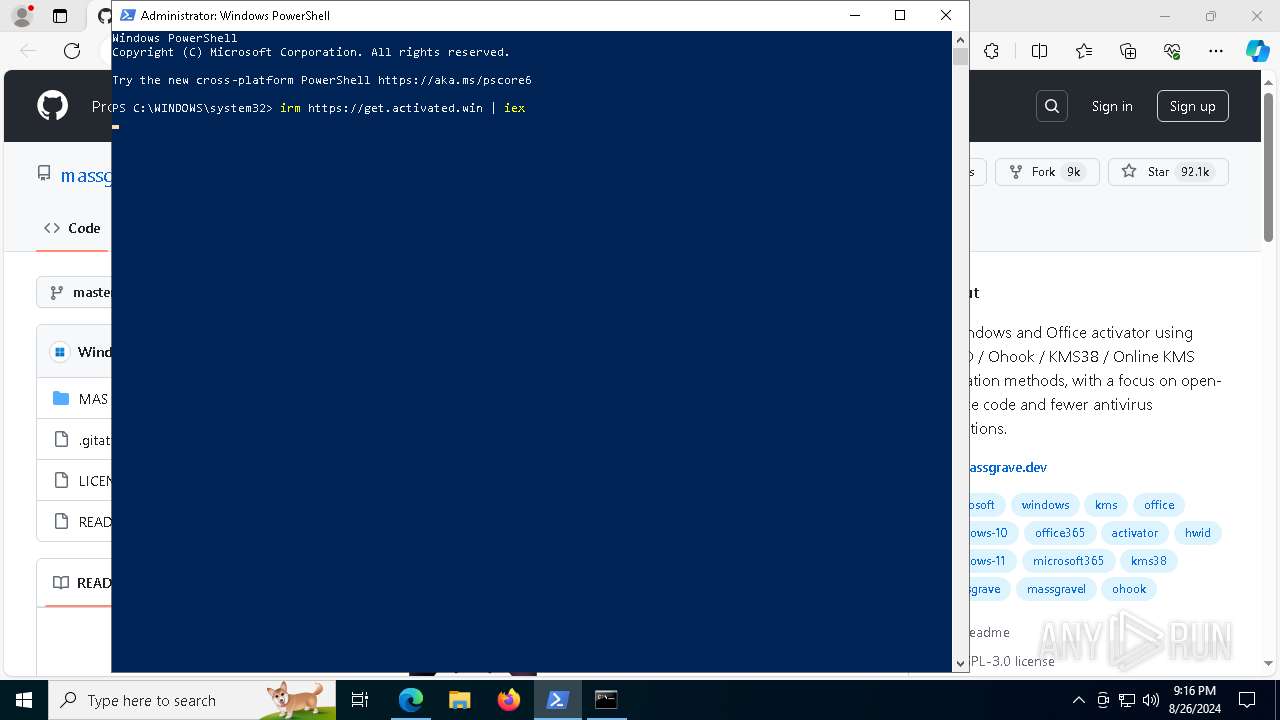
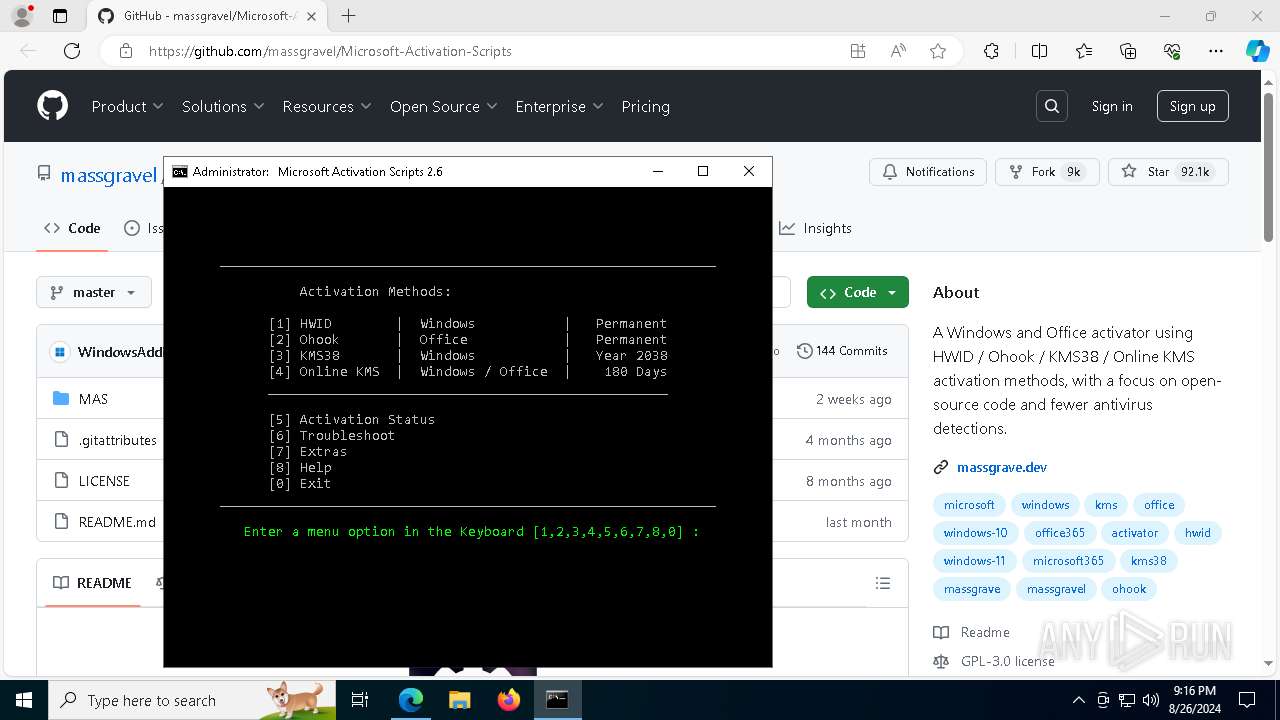
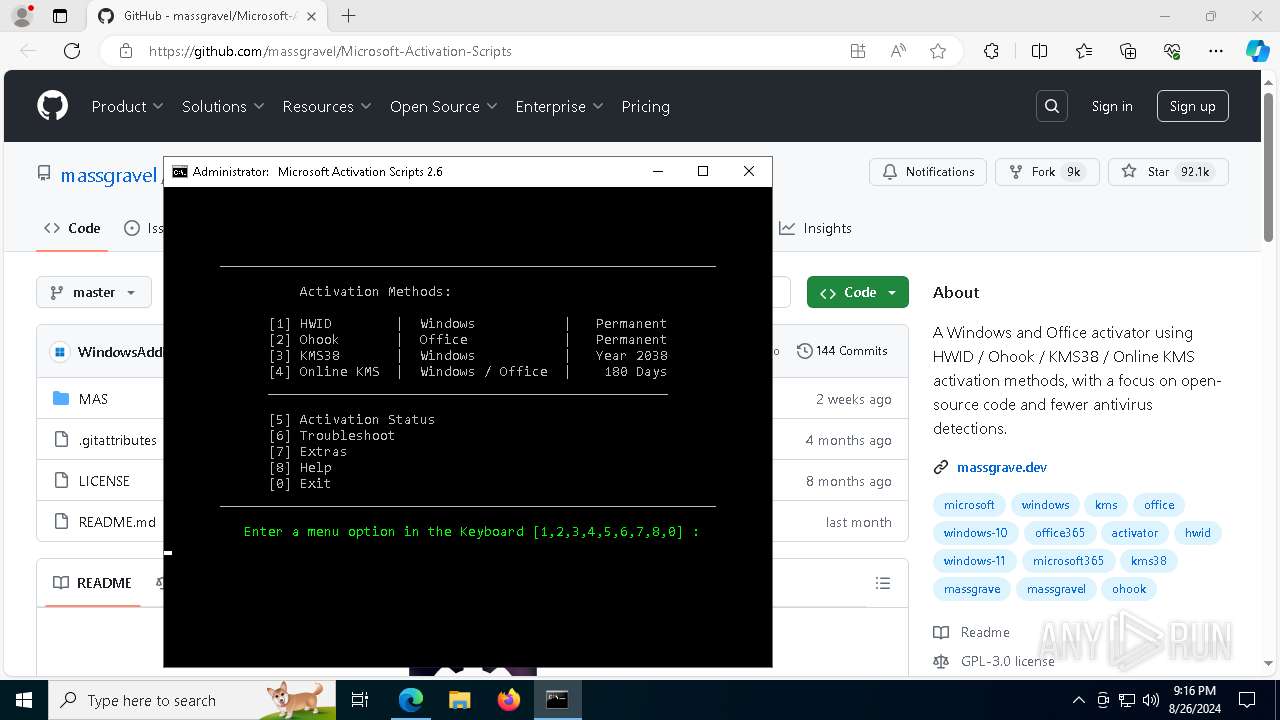
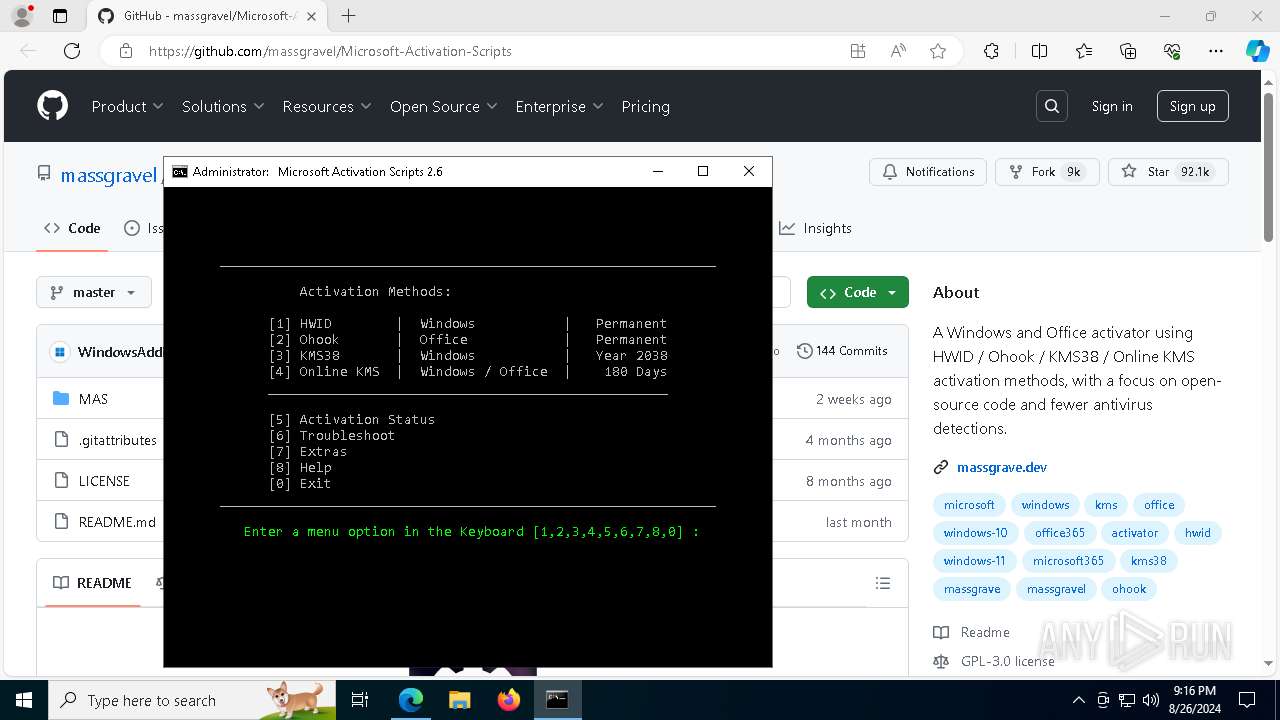
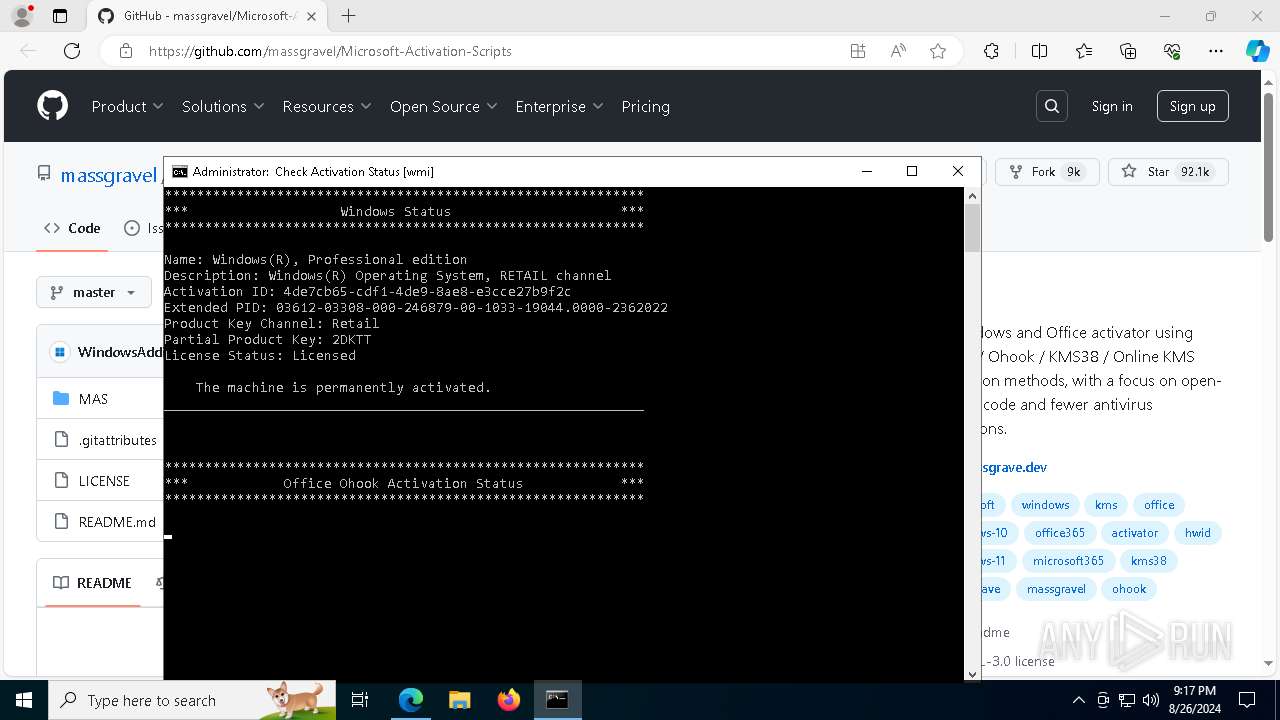
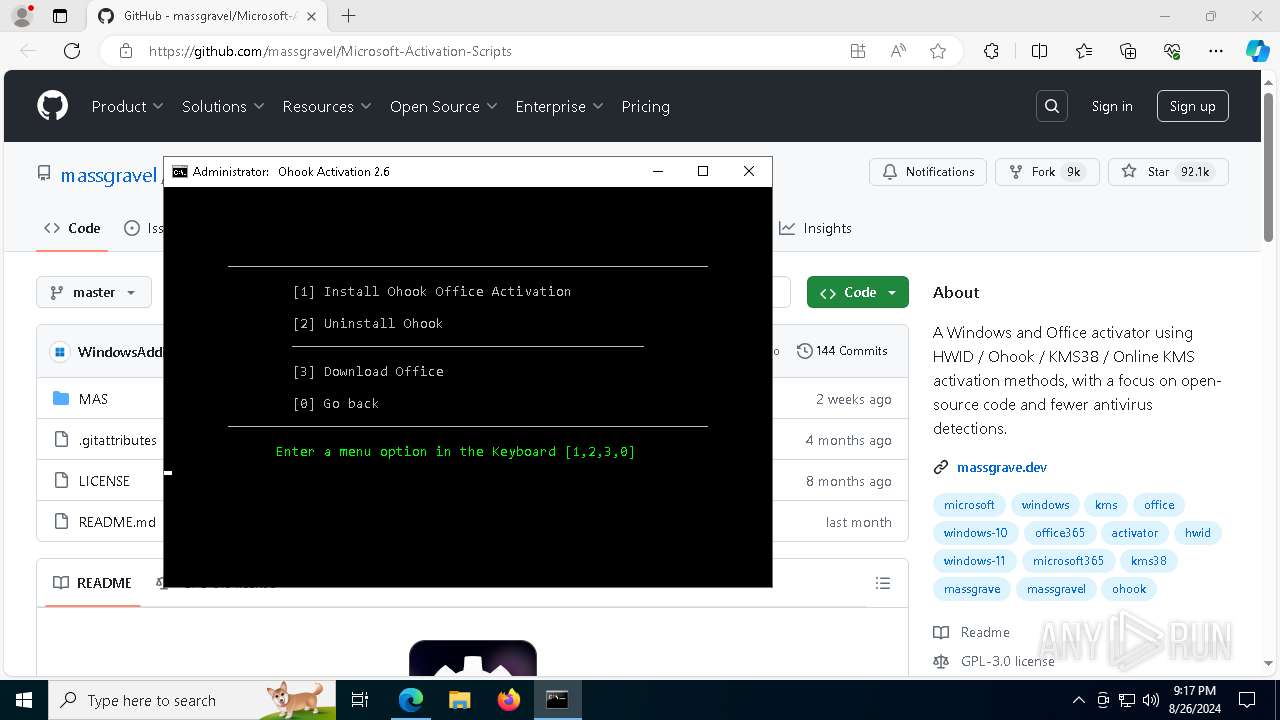
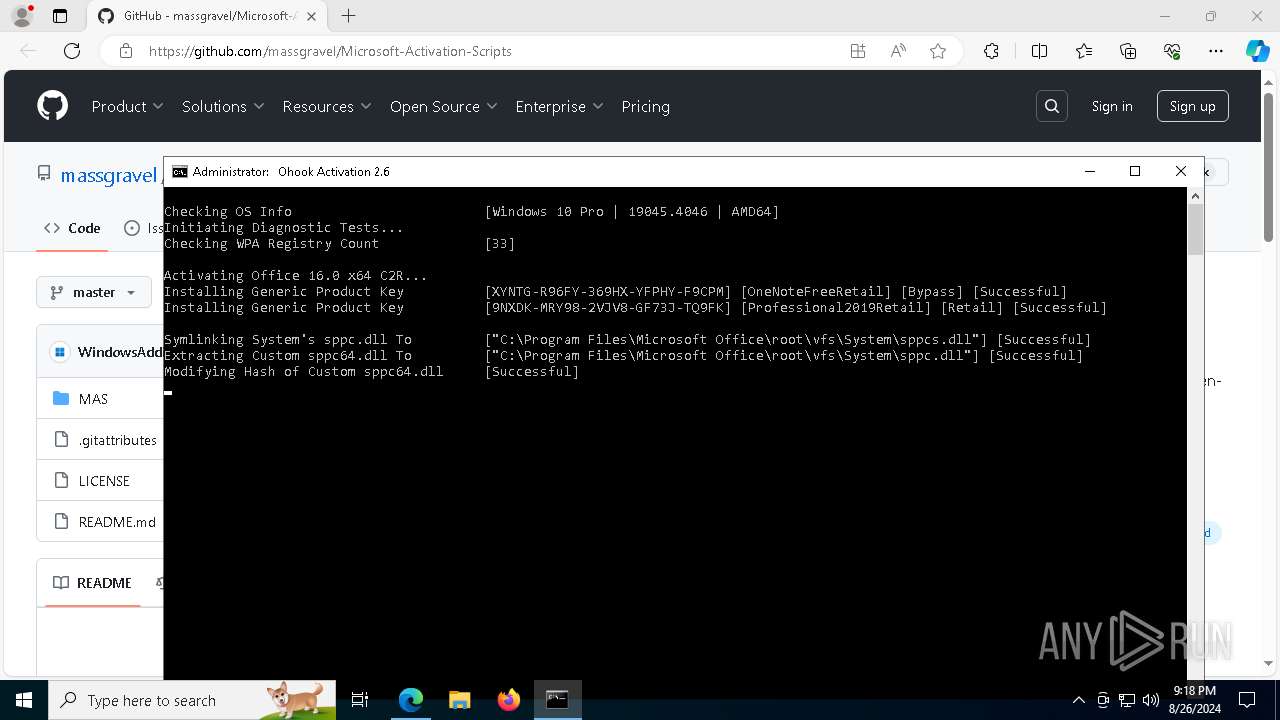
| URL: | https://github.com/massgravel/Microsoft-Activation-Scripts |
| Full analysis: | https://app.any.run/tasks/9d80fb6d-6e24-4128-b191-439845e61440 |
| Verdict: | Malicious activity |
| Analysis date: | August 26, 2024, 21:13:44 |
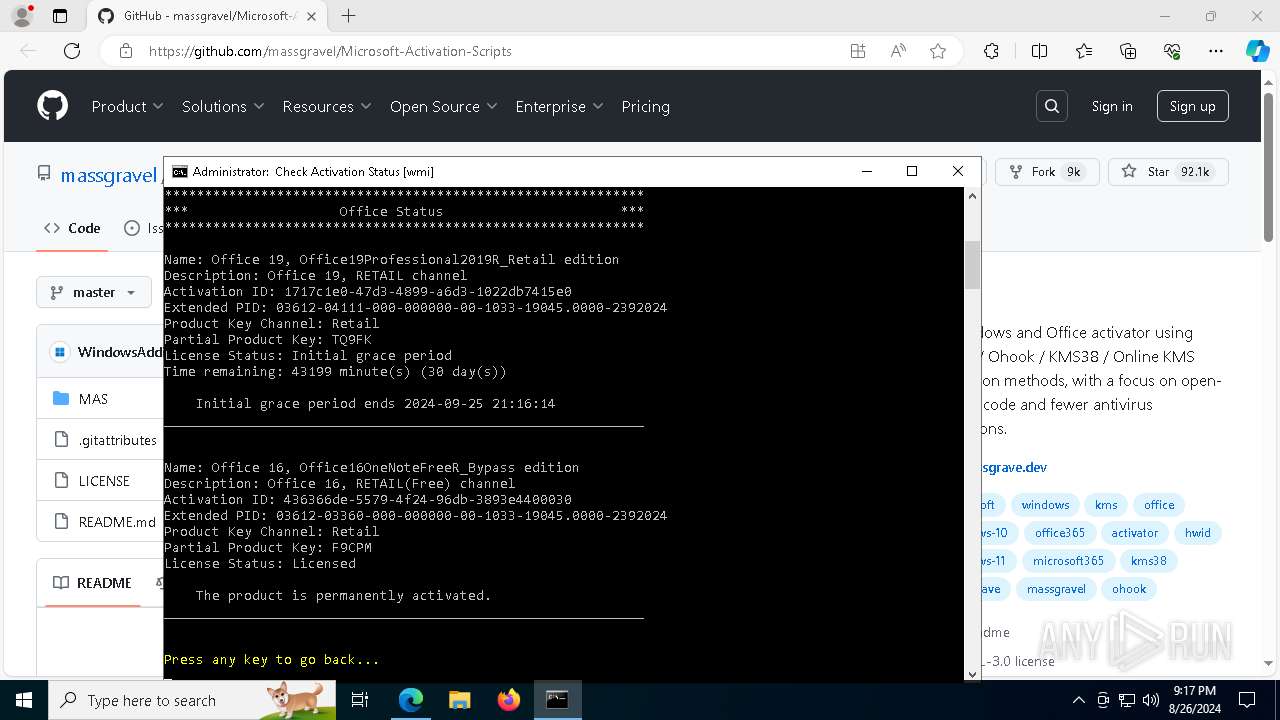
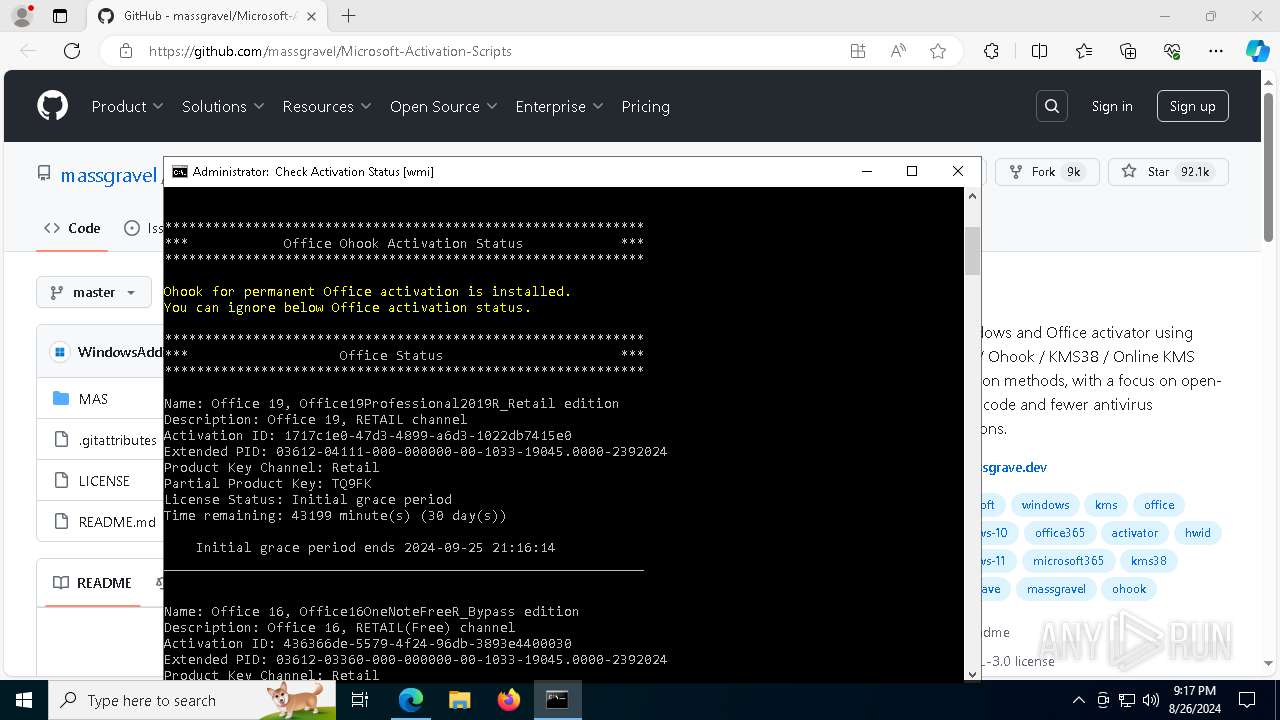
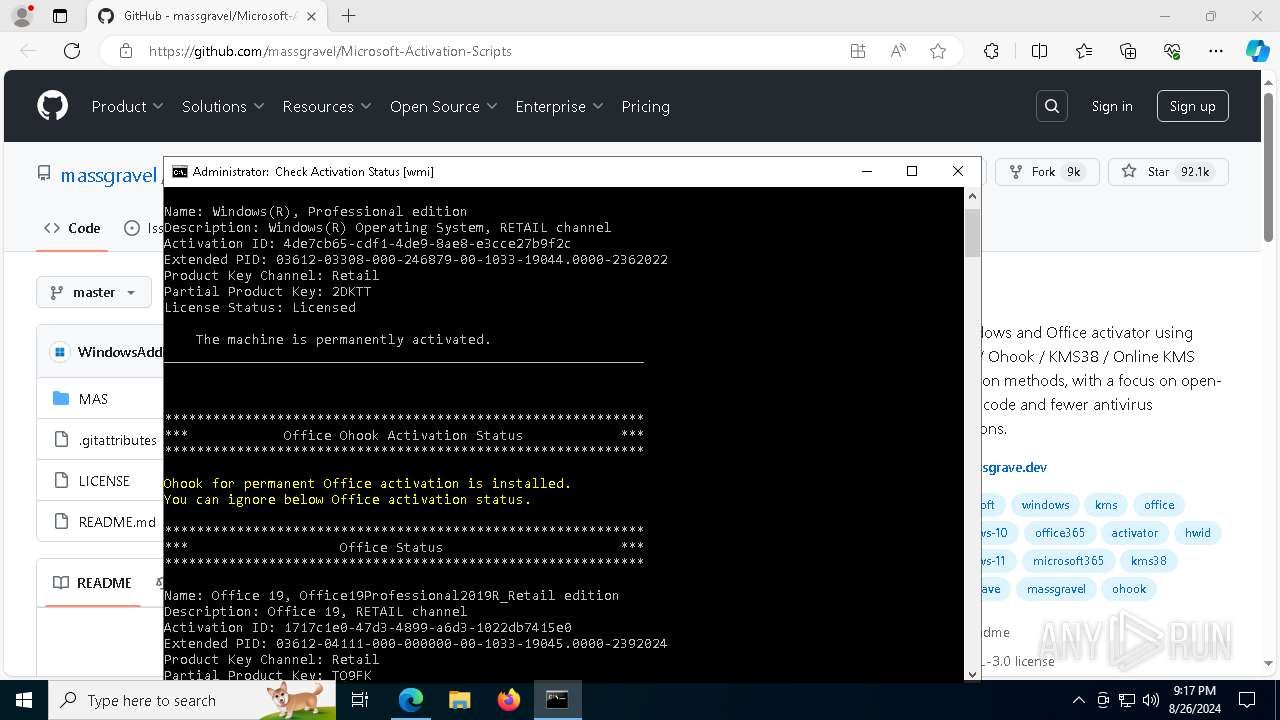
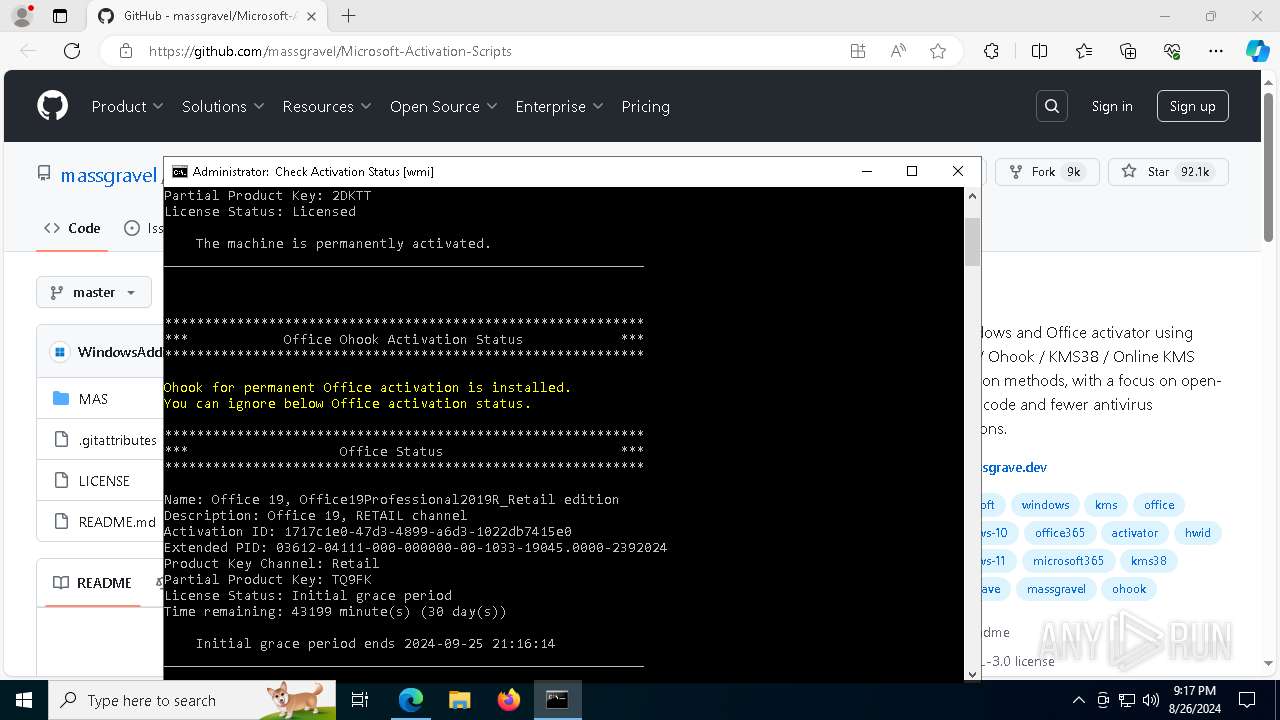
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | AFD6FF84DA2D0BA12E52C775DF44B55B |
| SHA1: | 01C9074D7E2703A728921432F53128804DA08B5E |
| SHA256: | 9E176C48748F3D4D4303D5D603F477906CE34A381ACACC46ADB8DC346A2F00D9 |
| SSDEEP: | 3:N8tEd4PKoHXuukGR3RLLLGXUw:2uuPKzukGv/LGXUw |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 7372)
- net.exe (PID: 6052)
SUSPICIOUS
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 7456)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 7456)
- powershell.exe (PID: 6528)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 8064)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 7456)
- powershell.exe (PID: 6528)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 8064)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 7456)
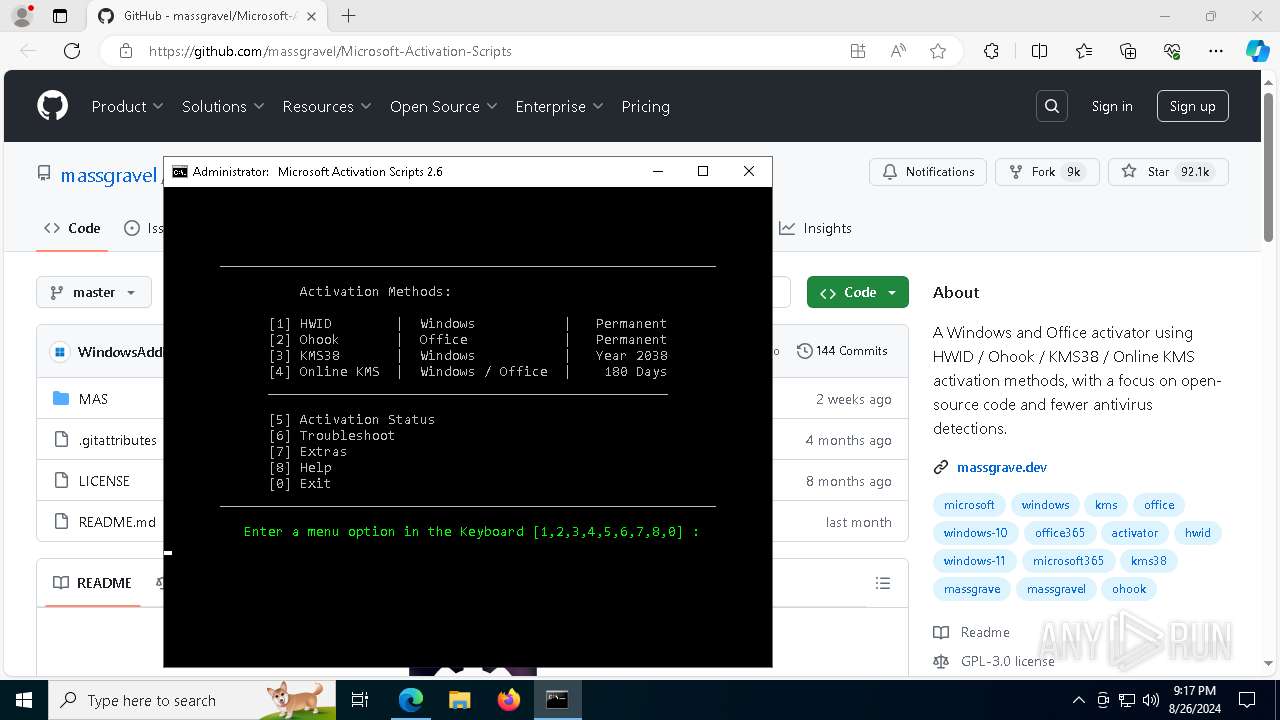
Executing commands from ".cmd" file
- powershell.exe (PID: 7456)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7372)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 7456)
- cmd.exe (PID: 7856)
- cmd.exe (PID: 8040)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6252)
Starts SC.EXE for service management
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7372)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6140)
- cmd.exe (PID: 5740)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 3812)
Application launched itself
- cmd.exe (PID: 7856)
- cmd.exe (PID: 6028)
- cmd.exe (PID: 8040)
- cmd.exe (PID: 4436)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6252)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6140)
- cmd.exe (PID: 3812)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6864)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 6364)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 608)
- cmd.exe (PID: 300)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 7372)
Process drops legitimate windows executable
- Dism.exe (PID: 6680)
- Dism.exe (PID: 7616)
Hides command output
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6864)
- cmd.exe (PID: 1216)
- cmd.exe (PID: 1148)
- cmd.exe (PID: 6636)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 5980)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 1492)
- cmd.exe (PID: 7948)
- cmd.exe (PID: 7540)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 4820)
- cmd.exe (PID: 1440)
- cmd.exe (PID: 3852)
- cmd.exe (PID: 3880)
- cmd.exe (PID: 7544)
- cmd.exe (PID: 6140)
- cmd.exe (PID: 7872)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 6364)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 6668)
- cmd.exe (PID: 4448)
- cmd.exe (PID: 4160)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 8176)
- cmd.exe (PID: 7292)
- cmd.exe (PID: 6984)
- cmd.exe (PID: 4936)
- cmd.exe (PID: 2112)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 1148)
- cmd.exe (PID: 5244)
- cmd.exe (PID: 6504)
- cmd.exe (PID: 6920)
- cmd.exe (PID: 7500)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 300)
- cmd.exe (PID: 3812)
- cmd.exe (PID: 6936)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 6712)
- cmd.exe (PID: 6876)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6316)
- cmd.exe (PID: 300)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6712)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 6316)
The process creates files with name similar to system file names
- Dism.exe (PID: 6680)
- Dism.exe (PID: 7616)
Executable content was dropped or overwritten
- Dism.exe (PID: 6680)
- powershell.exe (PID: 6148)
- Dism.exe (PID: 7616)
- powershell.exe (PID: 8064)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 7536)
- DismHost.exe (PID: 7792)
The process executes VB scripts
- cmd.exe (PID: 7372)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 7248)
- cscript.exe (PID: 1064)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7248)
- cscript.exe (PID: 1064)
Reads data from a binary Stream object (SCRIPT)
- cscript.exe (PID: 7248)
- cscript.exe (PID: 1064)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6636)
- cmd.exe (PID: 7948)
- cmd.exe (PID: 6948)
- cmd.exe (PID: 7372)
- cmd.exe (PID: 3840)
- cmd.exe (PID: 6192)
- cmd.exe (PID: 6248)
- cmd.exe (PID: 7160)
- cmd.exe (PID: 5740)
- cmd.exe (PID: 7972)
- cmd.exe (PID: 6936)
- cmd.exe (PID: 6936)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7372)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8064)
Drops the executable file immediately after the start
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8064)
INFO
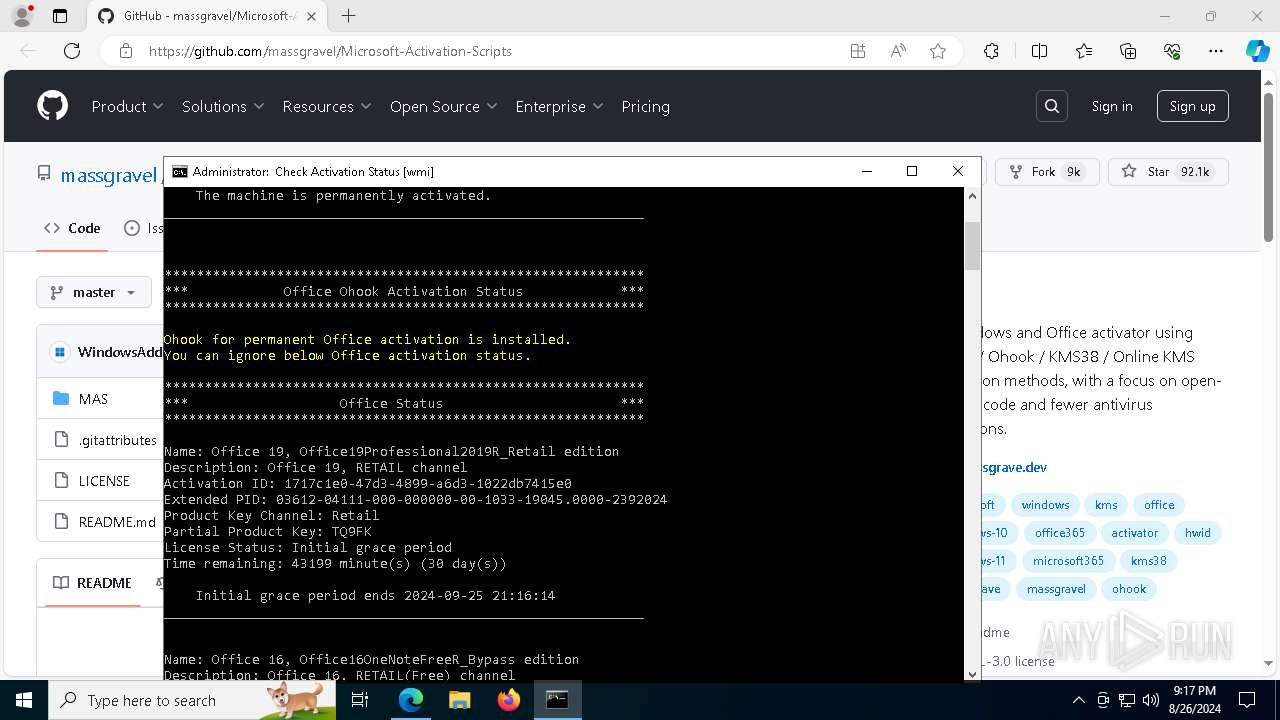
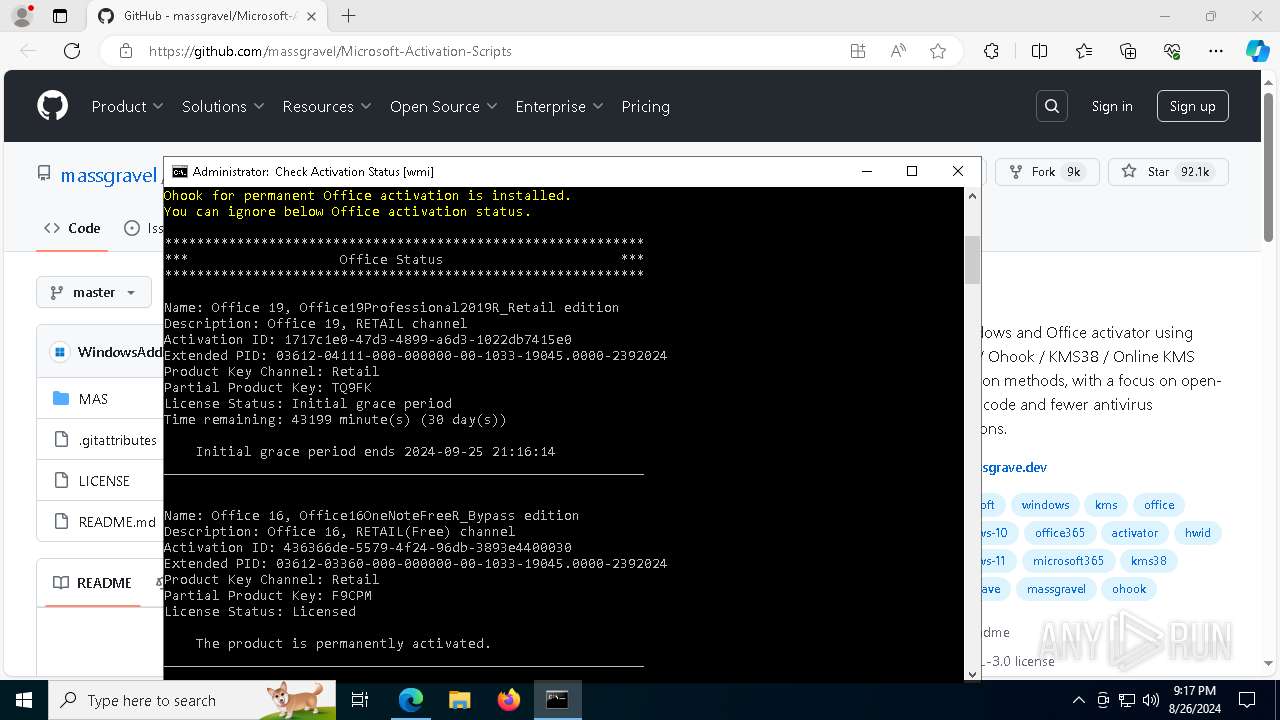
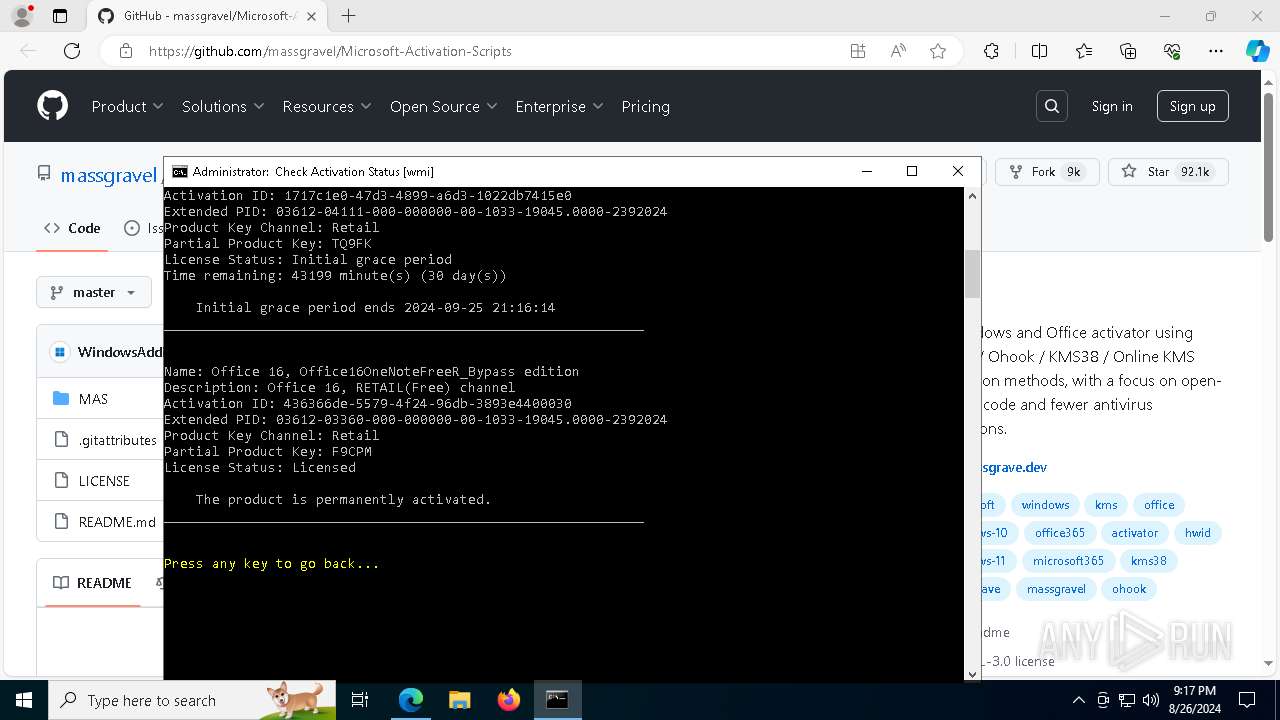
Reads Microsoft Office registry keys
- msedge.exe (PID: 4084)
- reg.exe (PID: 7352)
- reg.exe (PID: 5040)
- reg.exe (PID: 6256)
- reg.exe (PID: 6192)
- reg.exe (PID: 4364)
- reg.exe (PID: 7356)
- reg.exe (PID: 1084)
- reg.exe (PID: 5044)
- reg.exe (PID: 7548)
- reg.exe (PID: 6196)
- reg.exe (PID: 7304)
- reg.exe (PID: 6984)
- reg.exe (PID: 7688)
- reg.exe (PID: 2228)
- reg.exe (PID: 7208)
- reg.exe (PID: 7432)
- reg.exe (PID: 7352)
- reg.exe (PID: 5052)
- reg.exe (PID: 6140)
- reg.exe (PID: 7504)
- reg.exe (PID: 1044)
- reg.exe (PID: 1356)
- reg.exe (PID: 2340)
- reg.exe (PID: 3568)
Reads Environment values
- identity_helper.exe (PID: 5112)
- DismHost.exe (PID: 7536)
- DismHost.exe (PID: 7792)
Application launched itself
- msedge.exe (PID: 4084)
Disables trace logs
- powershell.exe (PID: 7456)
Manual execution by a user
- powershell.exe (PID: 7456)
- WINWORD.EXE (PID: 1044)
Checks proxy server information
- powershell.exe (PID: 7456)
Checks supported languages
- identity_helper.exe (PID: 5112)
- mode.com (PID: 6676)
- mode.com (PID: 2008)
- mode.com (PID: 6616)
- DismHost.exe (PID: 7536)
- mode.com (PID: 5552)
- mode.com (PID: 1656)
- mode.com (PID: 7324)
- mode.com (PID: 7756)
- mode.com (PID: 3316)
- DismHost.exe (PID: 7792)
Checks current location (POWERSHELL)
- powershell.exe (PID: 7456)
Reads the computer name
- identity_helper.exe (PID: 5112)
- DismHost.exe (PID: 7536)
- DismHost.exe (PID: 7792)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 7456)
- powershell.exe (PID: 6528)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 8064)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 7456)
- powershell.exe (PID: 6528)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8124)
- powershell.exe (PID: 8064)
Checks operating system version
- cmd.exe (PID: 7856)
- cmd.exe (PID: 7372)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8188)
- cscript.exe (PID: 7248)
- WMIC.exe (PID: 6596)
- WMIC.exe (PID: 5520)
- WMIC.exe (PID: 7944)
- WMIC.exe (PID: 1680)
- WMIC.exe (PID: 1828)
- WMIC.exe (PID: 7564)
- WMIC.exe (PID: 5400)
- WMIC.exe (PID: 7540)
- WMIC.exe (PID: 7316)
- WMIC.exe (PID: 3708)
- WMIC.exe (PID: 5508)
- WMIC.exe (PID: 7500)
- WMIC.exe (PID: 7332)
- WMIC.exe (PID: 5212)
- WMIC.exe (PID: 6412)
- WMIC.exe (PID: 300)
- WMIC.exe (PID: 8048)
- cscript.exe (PID: 1064)
- WMIC.exe (PID: 3292)
- WMIC.exe (PID: 7072)
- WMIC.exe (PID: 1608)
- WMIC.exe (PID: 5760)
- WMIC.exe (PID: 7072)
- WMIC.exe (PID: 7184)
- WMIC.exe (PID: 2660)
- WMIC.exe (PID: 7188)
Create files in a temporary directory
- Dism.exe (PID: 6680)
- Dism.exe (PID: 7616)
Creates files in the program directory
- cmd.exe (PID: 7372)
- powershell.exe (PID: 6148)
- powershell.exe (PID: 8064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
682
Monitored processes
533
Malicious processes
9
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | reg query HKLM\SYSTEM\CurrentControlSet\Services\sppsvc /v Description | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 8 | powershell.exe "Get-AppxPackage -name "Microsoft.Office.Desktop"" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | find /i "0x0" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | find /i "RUNNING" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=4244 --field-trial-handle=2416,i,14592436223173210613,7372620702579209918,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 236 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=5144 --field-trial-handle=2416,i,14592436223173210613,7372620702579209918,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 300 | wmic path Win32_ComputerSystem get CreationClassName /value | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | C:\WINDOWS\system32\cmd.exe /c powershell.exe "Get-ChildItem -Path 'HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProfileList' | ForEach-Object { Split-Path -Path $_.PSPath -Leaf }" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 400 | choice /C:1230 /N | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | powershell "&{$W=$Host.UI.RawUI.WindowSize;$B=$Host.UI.RawUI.BufferSize;$W.Height=31;$B.Height=300;$Host.UI.RawUI.WindowSize=$W;$Host.UI.RawUI.BufferSize=$B;}" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
159 310
Read events
157 761
Write events
1 436
Delete events
113
Modification events
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\EdgeUpdate\ClientState\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (4084) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062} |
| Operation: | write | Name: | urlstats |
Value: 0 | |||
Executable files
112
Suspicious files
658
Text files
261
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF12a7e1.TMP | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF12a7e1.TMP | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF12a7f0.TMP | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF12a7e1.TMP | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF12a81f.TMP | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4084 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
216
DNS requests
124
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAFSnug2jwtdcrpDPi2Opi0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
2032 | svchost.exe | HEAD | 200 | 23.48.23.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/087c052d-2d1c-4c24-9226-26ea74392e49?P1=1725262445&P2=404&P3=2&P4=UxxqhLvY%2b4vSrSC8%2fTZLTMfi1TzqkRgCwGiT7PxtfDnI69NYUTSVe4nIV6NCV4dVtRoBVw%2b9t4Pi%2bT18QSiL4Q%3d%3d | unknown | — | — | whitelisted |
7968 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7968 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1780 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2032 | svchost.exe | GET | 206 | 23.48.23.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/087c052d-2d1c-4c24-9226-26ea74392e49?P1=1725262445&P2=404&P3=2&P4=UxxqhLvY%2b4vSrSC8%2fTZLTMfi1TzqkRgCwGiT7PxtfDnI69NYUTSVe4nIV6NCV4dVtRoBVw%2b9t4Pi%2bT18QSiL4Q%3d%3d | unknown | — | — | whitelisted |
2032 | svchost.exe | GET | 206 | 23.48.23.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/087c052d-2d1c-4c24-9226-26ea74392e49?P1=1725262445&P2=404&P3=2&P4=UxxqhLvY%2b4vSrSC8%2fTZLTMfi1TzqkRgCwGiT7PxtfDnI69NYUTSVe4nIV6NCV4dVtRoBVw%2b9t4Pi%2bT18QSiL4Q%3d%3d | unknown | — | — | whitelisted |
2032 | svchost.exe | GET | 206 | 23.48.23.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/087c052d-2d1c-4c24-9226-26ea74392e49?P1=1725262445&P2=404&P3=2&P4=UxxqhLvY%2b4vSrSC8%2fTZLTMfi1TzqkRgCwGiT7PxtfDnI69NYUTSVe4nIV6NCV4dVtRoBVw%2b9t4Pi%2bT18QSiL4Q%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6232 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6364 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4084 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7052 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7052 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | shared |
7052 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7052 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7052 | msedge.exe | 13.107.246.67:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| shared |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
github.githubassets.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=6680 TID=7172 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=6680 TID=7172 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6680 TID=7172 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6680 TID=7172 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6680 TID=7172 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6680 TID=7172 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=7536 TID=7528 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=7536 TID=7528 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=7536 TID=7528 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=6680 TID=7172 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |