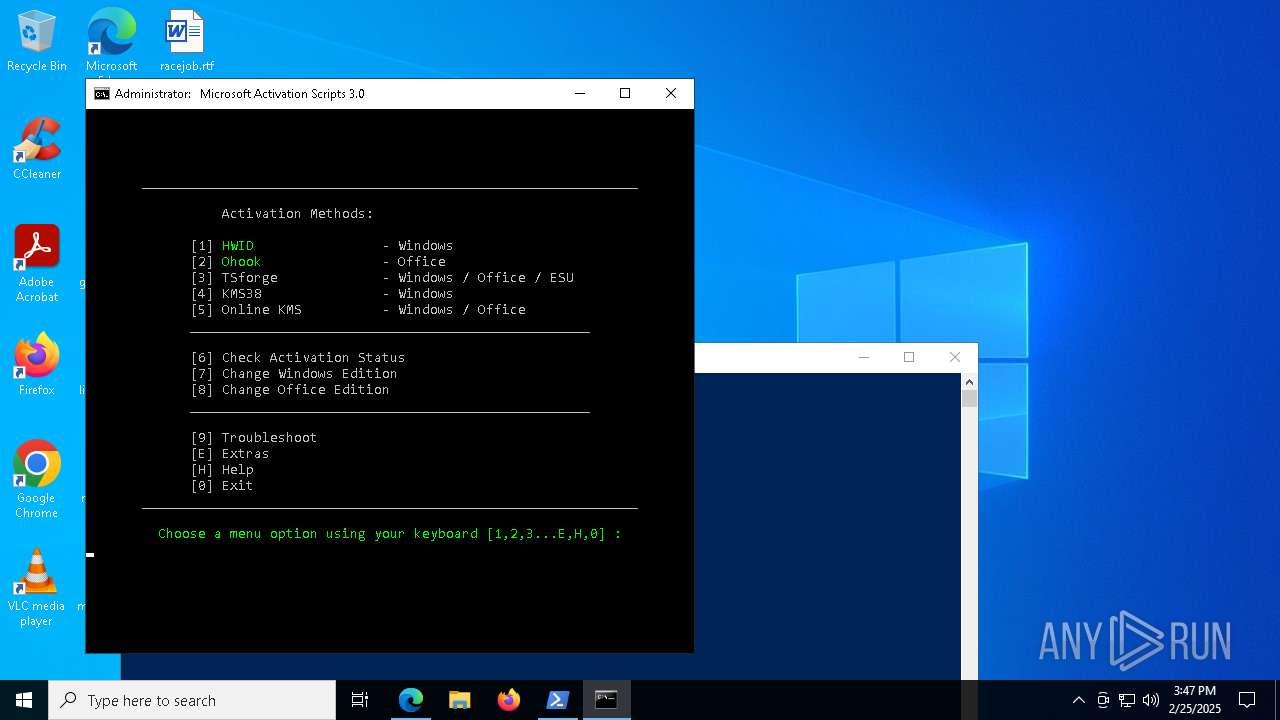
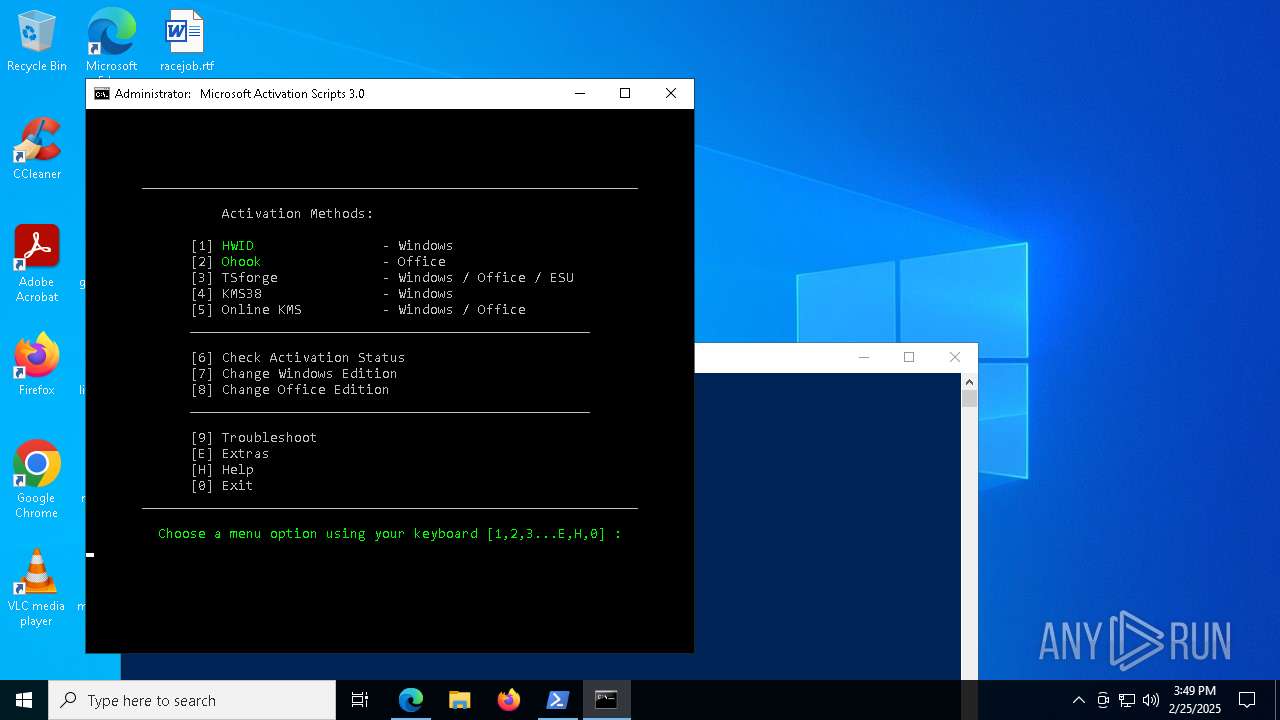
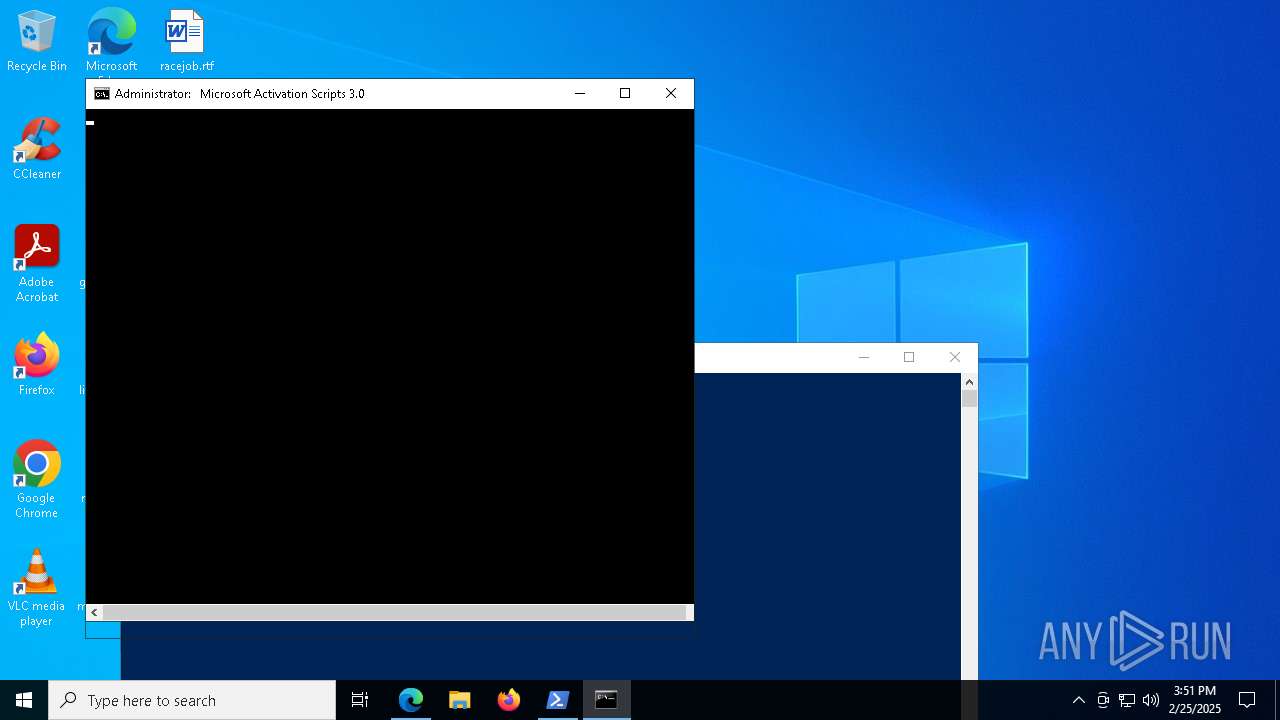
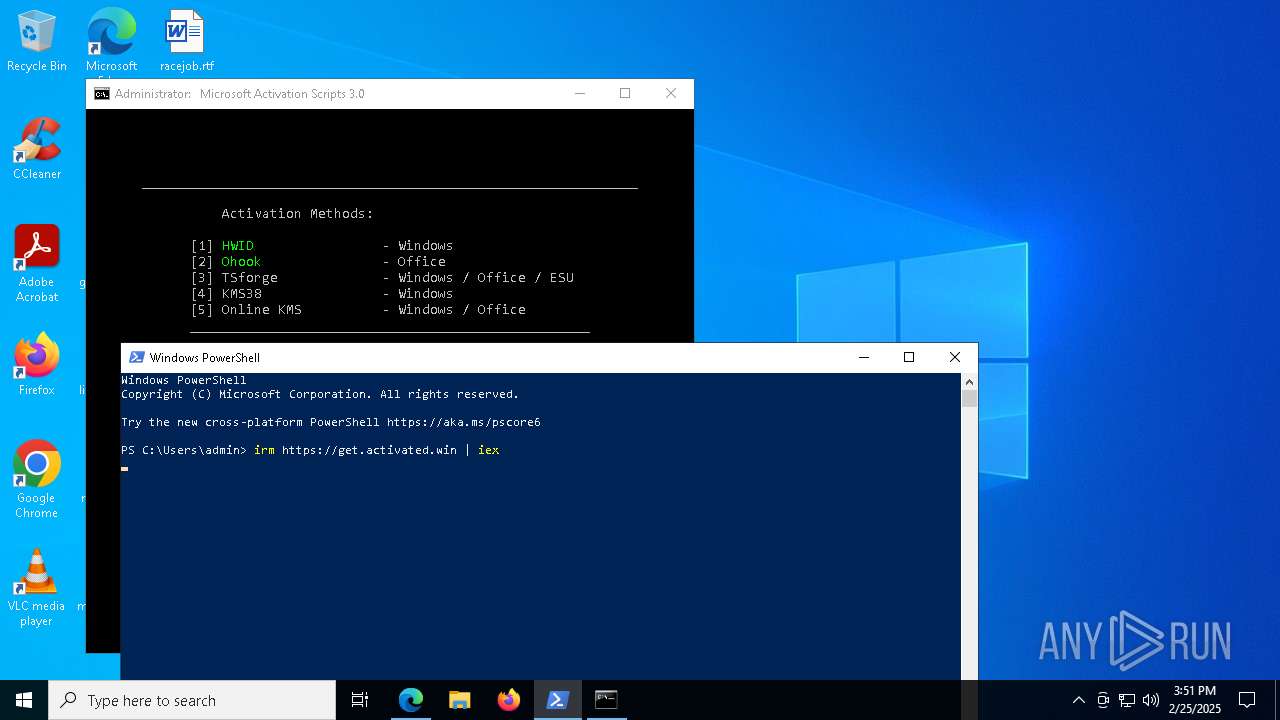
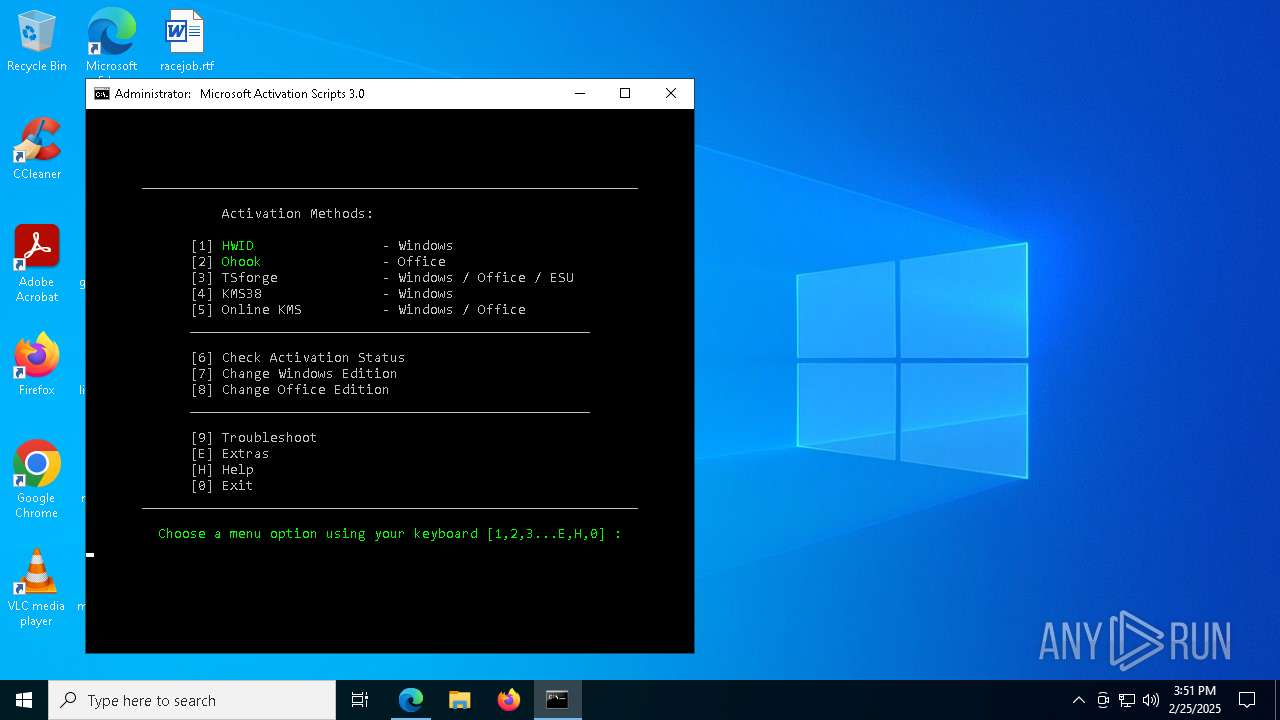
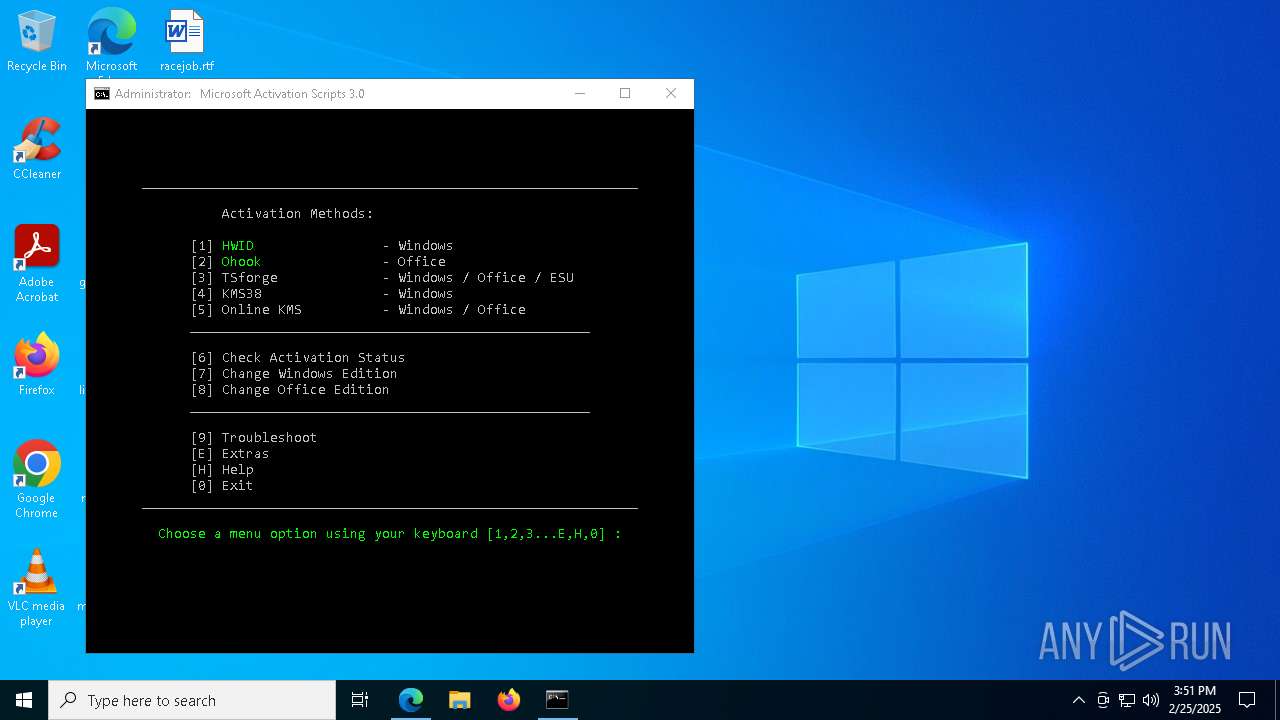
| URL: | https://github.com/massgravel/Microsoft-Activation-Scripts |
| Full analysis: | https://app.any.run/tasks/1bc907ab-9570-44e5-a7be-a06338ea6ca2 |
| Verdict: | Malicious activity |
| Analysis date: | February 25, 2025, 15:46:45 |
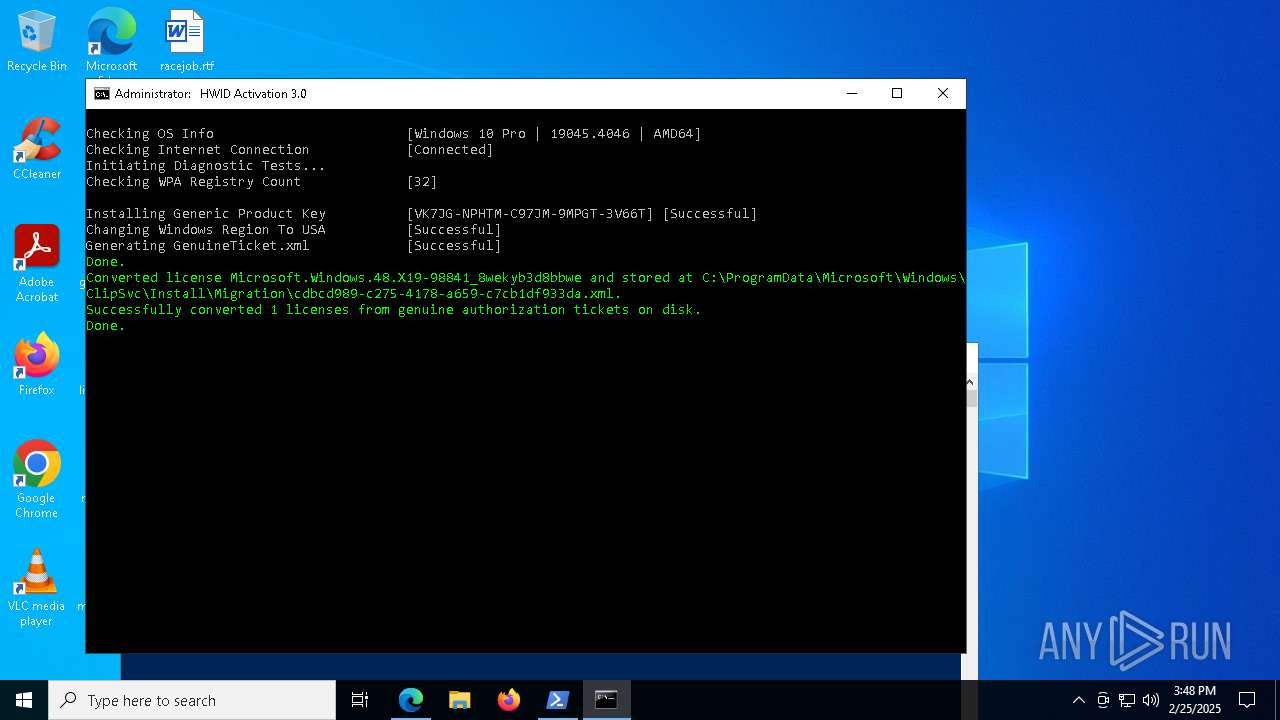
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | AFD6FF84DA2D0BA12E52C775DF44B55B |
| SHA1: | 01C9074D7E2703A728921432F53128804DA08B5E |
| SHA256: | 9E176C48748F3D4D4303D5D603F477906CE34A381ACACC46ADB8DC346A2F00D9 |
| SSDEEP: | 3:N8tEd4PKoHXuukGR3RLLLGXUw:2uuPKzukGv/LGXUw |
MALICIOUS
No malicious indicators.SUSPICIOUS
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
- powershell.exe (PID: 2148)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 396)
Uses sleep to delay execution (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
Executing commands from ".cmd" file
- powershell.exe (PID: 396)
- cmd.exe (PID: 720)
- powershell.exe (PID: 7016)
- cmd.exe (PID: 7276)
- powershell.exe (PID: 7956)
- cmd.exe (PID: 8044)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 396)
- cmd.exe (PID: 720)
- cmd.exe (PID: 236)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 7564)
- powershell.exe (PID: 7016)
- powershell.exe (PID: 7956)
- cmd.exe (PID: 3416)
- cmd.exe (PID: 8044)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 396)
Starts SC.EXE for service management
- cmd.exe (PID: 720)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 8044)
Windows service management via SC.EXE
- sc.exe (PID: 2232)
- sc.exe (PID: 7356)
- sc.exe (PID: 8064)
- sc.exe (PID: 6864)
- sc.exe (PID: 5580)
- sc.exe (PID: 3544)
- sc.exe (PID: 7004)
- sc.exe (PID: 1704)
- sc.exe (PID: 7496)
- sc.exe (PID: 6628)
- sc.exe (PID: 7024)
- sc.exe (PID: 7452)
- sc.exe (PID: 7668)
- sc.exe (PID: 7712)
- sc.exe (PID: 1752)
- sc.exe (PID: 7924)
- sc.exe (PID: 8092)
- sc.exe (PID: 2804)
- sc.exe (PID: 1576)
- sc.exe (PID: 8000)
- sc.exe (PID: 5652)
- sc.exe (PID: 7216)
- sc.exe (PID: 1740)
- sc.exe (PID: 7204)
- sc.exe (PID: 3816)
- sc.exe (PID: 6616)
- sc.exe (PID: 4204)
- sc.exe (PID: 7420)
- sc.exe (PID: 7332)
- sc.exe (PID: 6828)
- sc.exe (PID: 7516)
- sc.exe (PID: 4136)
- sc.exe (PID: 7056)
- sc.exe (PID: 7268)
- sc.exe (PID: 7624)
- sc.exe (PID: 7356)
- sc.exe (PID: 7584)
- sc.exe (PID: 8188)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 5652)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 720)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 8044)
- powershell.exe (PID: 3564)
- cmd.exe (PID: 7472)
- cmd.exe (PID: 7640)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 4336)
- cmd.exe (PID: 7404)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 8148)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 7460)
- cmd.exe (PID: 7352)
- cmd.exe (PID: 5320)
- cmd.exe (PID: 6888)
- cmd.exe (PID: 7224)
- cmd.exe (PID: 8112)
- cmd.exe (PID: 4320)
- cmd.exe (PID: 6616)
- cmd.exe (PID: 4036)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 5836)
- cmd.exe (PID: 6808)
- cmd.exe (PID: 7568)
- cmd.exe (PID: 7344)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 720)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 2280)
Application launched itself
- cmd.exe (PID: 720)
- cmd.exe (PID: 236)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 7564)
- cmd.exe (PID: 3416)
- cmd.exe (PID: 8044)
- powershell.exe (PID: 3564)
- ClipUp.exe (PID: 5788)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 8148)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 5652)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 7640)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 5652)
- cmd.exe (PID: 7668)
- cmd.exe (PID: 7236)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 7640)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 5652)
- cmd.exe (PID: 8044)
- cmd.exe (PID: 3896)
Hides command output
- cmd.exe (PID: 2232)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7640)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 8124)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 8036)
- cmd.exe (PID: 7676)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 5640)
- cmd.exe (PID: 5160)
- cmd.exe (PID: 488)
- cmd.exe (PID: 7496)
- cmd.exe (PID: 7512)
- cmd.exe (PID: 2452)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 7332)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 8044)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 3564)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 8148)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 8044)
- cmd.exe (PID: 3532)
- cmd.exe (PID: 8164)
- cmd.exe (PID: 7676)
- cmd.exe (PID: 5160)
- cmd.exe (PID: 2452)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 3564)
- powershell.exe (PID: 4980)
- powershell.exe (PID: 8148)
- powershell.exe (PID: 7704)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 8044)
Executable content was dropped or overwritten
- Dism.exe (PID: 6776)
- Dism.exe (PID: 3188)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 3680)
- DismHost.exe (PID: 7568)
INFO
Checks current location (POWERSHELL)
- powershell.exe (PID: 396)
Manual execution by a user
- powershell.exe (PID: 396)
Disables trace logs
- powershell.exe (PID: 396)
Reads Environment values
- identity_helper.exe (PID: 3820)
Checks supported languages
- identity_helper.exe (PID: 3820)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
Reads the computer name
- identity_helper.exe (PID: 3820)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
- powershell.exe (PID: 7300)
Checks proxy server information
- powershell.exe (PID: 396)
Creates a byte array (POWERSHELL)
- powershell.exe (PID: 396)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 7704)
- powershell.exe (PID: 7300)
- powershell.exe (PID: 7360)
- powershell.exe (PID: 7484)
Checks operating system version
- cmd.exe (PID: 720)
- cmd.exe (PID: 7276)
- cmd.exe (PID: 8044)
Application launched itself
- msedge.exe (PID: 4076)
Starts MODE.COM to configure console settings
- mode.com (PID: 7024)
- mode.com (PID: 6512)
- mode.com (PID: 7160)
- mode.com (PID: 8168)
- mode.com (PID: 5912)
- mode.com (PID: 1344)
- mode.com (PID: 6732)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 5936)
- WMIC.exe (PID: 7576)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 3060)
Creates files in the program directory
- cmd.exe (PID: 8044)
The sample compiled with english language support
- msedge.exe (PID: 7332)
- Dism.exe (PID: 6776)
- Dism.exe (PID: 3188)
Create files in a temporary directory
- ClipUp.exe (PID: 6616)
Executable content was dropped or overwritten
- msedge.exe (PID: 7332)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1752)
- powershell.exe (PID: 7476)
- powershell.exe (PID: 7644)
- powershell.exe (PID: 1580)
- powershell.exe (PID: 1876)
- powershell.exe (PID: 2164)
- powershell.exe (PID: 6208)
- powershell.exe (PID: 4336)
- powershell.exe (PID: 8144)
- powershell.exe (PID: 6868)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 7432)
- powershell.exe (PID: 4764)
- powershell.exe (PID: 7532)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 7644)
- powershell.exe (PID: 1876)
- powershell.exe (PID: 2164)
- powershell.exe (PID: 5576)
- powershell.exe (PID: 4336)
- powershell.exe (PID: 1752)
- powershell.exe (PID: 7532)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
670
Monitored processes
515
Malicious processes
6
Suspicious processes
12
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | findstr /i "CountrySpecific CloudEdition" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | C:\WINDOWS\System32\cmd.exe /c echo prompt $E | cmd | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | reg query HKLM\SYSTEM\CurrentControlSet\Services\Winmgmt /v ImagePath | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 396 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 448 | choice /C:123456789EH0 /N | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 7 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 488 | C:\WINDOWS\System32\cmd.exe /c DISM /English /Online /Get-CurrentEdition 2>nul | find /i "Current Edition :" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | find /i " IoTEnterprise " | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 624 | wmic path SoftwareLicensingService where __CLASS='SoftwareLicensingService' call RefreshLicenseStatus | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 648 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "C:\Users\admin\AppData\Local\Temp\MAS_f556133a-5ae5-4094-b62c-e6e63adf57ac.cmd" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 712 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "AMD64 " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
223 338
Read events
223 307
Write events
29
Delete events
2
Modification events
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 475101A68F8D2F00 | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 2F2DFAA58F8D2F00 | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328470 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {B2C9306F-AE8C-4DF1-981C-EB8A0AEFDA30} | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328470 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {06154E67-5BDD-4889-A15F-F12B665F5B87} | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328470 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {5E2C4E34-78D3-4B1B-B365-B7E8269E629C} | |||
| (PID) Process: | (4076) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\328470 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {C46A0313-2AA1-4255-B424-F5A75DED9FD7} | |||
Executable files
115
Suspicious files
503
Text files
182
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF13543e.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF13543e.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF13543e.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF13543e.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF13545d.TMP | — | |
MD5:— | SHA256:— | |||
| 4076 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
55
TCP/UDP connections
102
DNS requests
98
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2232 | RUXIMICS.exe | GET | 200 | 23.48.23.149:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2232 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7672 | svchost.exe | HEAD | 200 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1741003880&P2=404&P3=2&P4=G%2bNJN%2bSZGwc3e%2fxwbZH1Cqfl4%2fkyF17hJGzjzvf07QWP4mtm4OPOZn2%2bEE2GcLCTEldl1tnjCasuToQQS6uKvQ%3d%3d | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2632 | SIHClient.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7672 | svchost.exe | GET | 206 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1741003880&P2=404&P3=2&P4=G%2bNJN%2bSZGwc3e%2fxwbZH1Cqfl4%2fkyF17hJGzjzvf07QWP4mtm4OPOZn2%2bEE2GcLCTEldl1tnjCasuToQQS6uKvQ%3d%3d | unknown | — | — | whitelisted |
7672 | svchost.exe | GET | 206 | 2.19.11.113:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1741003880&P2=404&P3=2&P4=G%2bNJN%2bSZGwc3e%2fxwbZH1Cqfl4%2fkyF17hJGzjzvf07QWP4mtm4OPOZn2%2bEE2GcLCTEldl1tnjCasuToQQS6uKvQ%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4308 | svchost.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4076 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6300 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6300 | msedge.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
6300 | msedge.exe | 13.107.253.72:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6300 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6300 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
github.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
github.githubassets.com |
| whitelisted |
avatars.githubusercontent.com |
| whitelisted |
user-images.githubusercontent.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=6776 TID=4716 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=6776 TID=4716 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6776 TID=4716 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6776 TID=4716 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6776 TID=4716 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6776 TID=4716 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=3680 TID=1704 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=3680 TID=1704 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=3680 TID=1704 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=6776 TID=4716 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |