| File name: | 9e0cfd00991a3d387a78770a7748418b4d0ab978717f84a399d766b19a971df0 |
| Full analysis: | https://app.any.run/tasks/41af01ee-39f4-42f5-be97-d601c3287432 |
| Verdict: | Malicious activity |
| Analysis date: | November 29, 2020, 16:00:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (DLL) (console) Intel 80386, for MS Windows |
| MD5: | B0F3A46ADF98EFB3A9AC7CEAD9B4FC5A |
| SHA1: | 01B0ECE80907F2D9E500ADA1CD2D555B782DD3A2 |
| SHA256: | 9E0CFD00991A3D387A78770A7748418B4D0AB978717F84A399D766B19A971DF0 |
| SSDEEP: | 3072:6YcS7/elK+/8OclqVHCWPR02j7UFMuhSNVqTZFnT0urv:z7C8uHCWPRp71uEOrnourv |
MALICIOUS
Loads dropped or rewritten executable
- rundll32.exe (PID: 2884)
SUSPICIOUS
Executed via COM
- iexplore.exe (PID: 320)
- DllHost.exe (PID: 2604)
Uses RUNDLL32.EXE to load library
- rundll32.exe (PID: 2352)
- control.exe (PID: 1720)
- control.exe (PID: 2560)
INFO
Reads settings of System Certificates
- iexplore.exe (PID: 320)
Changes internet zones settings
- iexplore.exe (PID: 320)
Creates files in the user directory
- iexplore.exe (PID: 320)
Reads internet explorer settings
- IEXPLORE.EXE (PID: 2424)
Changes settings of System certificates
- iexplore.exe (PID: 320)
Manual execution by user
- control.exe (PID: 1720)
- control.exe (PID: 2560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2020:11:24 18:26:23+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 9 |
| CodeSize: | 26112 |
| InitializedDataSize: | 119808 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1fb0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows command line |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 24-Nov-2020 17:26:23 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 24-Nov-2020 17:26:23 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00006452 | 0x00006600 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.51083 |
.rdata | 0x00008000 | 0x00000CAB | 0x00000E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.05222 |
.data | 0x00009000 | 0x0001BDA0 | 0x00018800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.56243 |
.reloc | 0x00025000 | 0x0000063C | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 4.96273 |
Imports
ADVAPI32.dll |
KERNEL32.dll |
USER32.dll |
ole32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
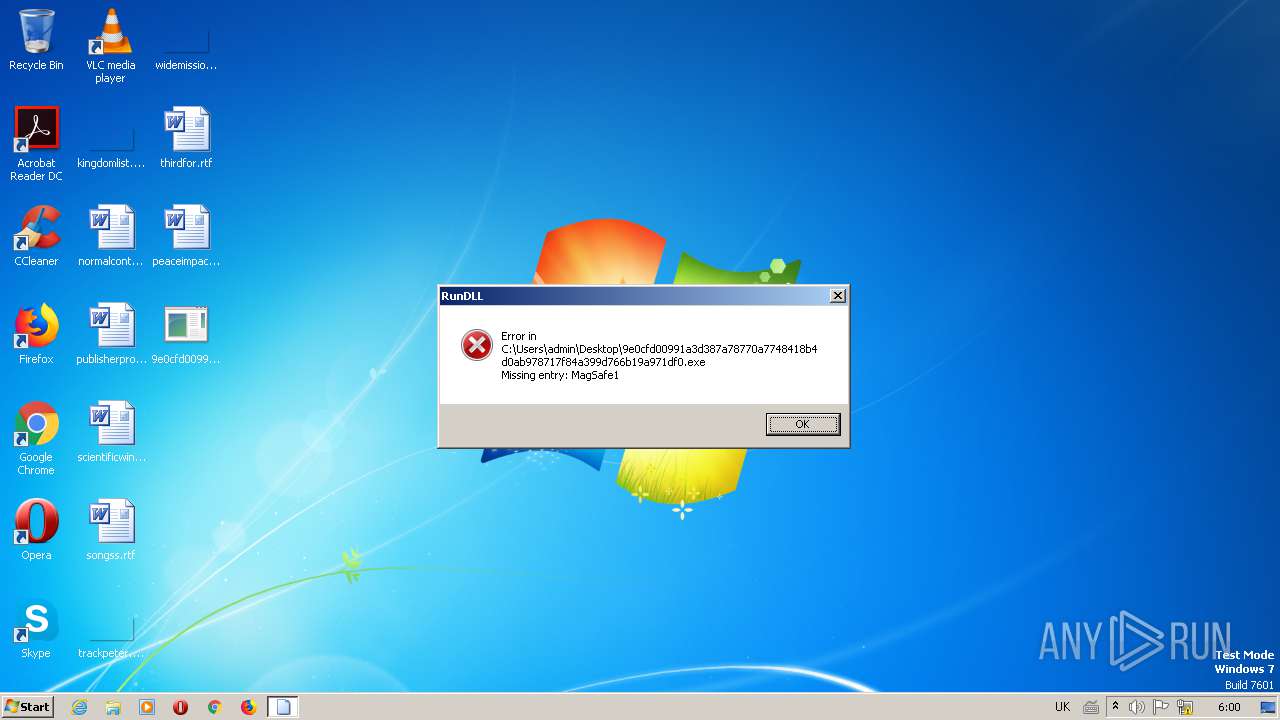
MagSafe1 | 1 | 0x00002640 |
MagSafe2 | 2 | 0x00002640 |
Total processes
52
Monitored processes
9
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 320 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1720 | "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl", | C:\Windows\System32\control.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2124 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\timedate.cpl", | C:\Windows\system32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2224 | "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\timedate.cpl", | C:\Windows\system32\rundll32.exe | — | control.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2352 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\Desktop\9e0cfd00991a3d387a78770a7748418b4d0ab978717f84a399d766b19a971df0.exe", MagSafe1 | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2424 | "C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE" SCODEF:320 CREDAT:267521 /prefetch:2 | C:\Program Files (x86)\Internet Explorer\IEXPLORE.EXE | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2560 | "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl", | C:\Windows\System32\control.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Control Panel Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2604 | C:\Windows\system32\DllHost.exe /Processid:{9DF523B0-A6C0-4EA9-B5F1-F4565C3AC8B8} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2884 | "C:\Windows\System32\rundll32.exe" "C:\Users\admin\Desktop\9e0cfd00991a3d387a78770a7748418b4d0ab978717f84a399d766b19a971df0.exe", MagSafe1 | C:\Windows\SysWOW64\rundll32.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
599
Read events
495
Write events
104
Delete events
0
Modification events
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 3 | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: 3396473248 | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30852712 | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3696630591 | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30852712 | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (320) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\C59EOZ9C.txt | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\W6HWK0DB.txt | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\DHE0NNT2.txt | — | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\toi5kkc\imagestore.dat | binary | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\CP7XB3Q8.txt | text | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\YJRTG2J4.txt | text | |
MD5:— | SHA256:— | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\IECompatData\iecompatdata.xml | xml | |
MD5:037B0D0C011D329C8E8442BBFC8B1A65 | SHA256:81931102C3CD33A4704C858298FDE8805B24D411C5CF26A5C8B586BA8B1E1513 | |||
| 320 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\BDW1XBVN\urlblockindex[1].bin | binary | |
MD5:FA518E3DFAE8CA3A0E495460FD60C791 | SHA256:775853600060162C4B4E5F883F9FD5A278E61C471B3EE1826396B6D129499AA7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
19
DNS requests
13
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
320 | iexplore.exe | GET | 302 | 92.123.16.55:443 | https://go.microsoft.com/fwlink/?linkid=859328&locale=uk-ua&market=ua | FR | — | — | whitelisted |
336 | svchost.exe | GET | 200 | 152.199.19.161:443 | https://r20swj13mr.microsoft.com/ieblocklist/v1/urlblockindex.bin | US | binary | 16 b | whitelisted |
320 | iexplore.exe | GET | 302 | 204.79.197.203:443 | https://www.msn.com/spartan/ientpgbconfig?locale=uk-ua&market=ua | US | html | 319 b | whitelisted |
320 | iexplore.exe | GET | 200 | 13.92.246.37:443 | https://query.prod.cms.msn.com/cms/api/amp/search?$filter='$type'eq'list'and'_locale'eq'uk-ua'and'_name'eq'IE%20NTP%20Goldbar'&tenant=amp&$select=list | US | text | 2 b | whitelisted |
320 | iexplore.exe | GET | 200 | 45.67.229.97:443 | https://njoopsday.website/favicon.ico | unknown | image | 318 b | suspicious |
884 | svchost.exe | POST | 502 | 45.67.229.97:443 | https://njoopsday.website/index.htm | unknown | html | 182 b | suspicious |
320 | iexplore.exe | GET | 304 | 152.199.19.161:443 | https://iecvlist.microsoft.com/ie11blocklist/1401746408/versionlistWin7.xml | US | — | — | whitelisted |
320 | iexplore.exe | GET | 200 | 152.199.19.161:443 | https://r20swj13mr.microsoft.com/ieblocklist/v1/urlblocklist.bin | US | — | — | whitelisted |
320 | iexplore.exe | GET | 200 | 204.79.197.200:443 | https://ieonline.microsoft.com/iedomainsuggestions/ie11/suggestions.uk-UA | US | binary | 17.7 Kb | whitelisted |
336 | svchost.exe | GET | 200 | 204.79.197.200:443 | https://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
320 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
320 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2424 | IEXPLORE.EXE | 45.67.229.97:443 | njoopsday.website | — | — | suspicious |
320 | iexplore.exe | 204.79.197.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
320 | iexplore.exe | 45.67.229.97:443 | njoopsday.website | — | — | suspicious |
320 | iexplore.exe | 13.92.246.37:443 | query.prod.cms.msn.com | Microsoft Corporation | US | whitelisted |
320 | iexplore.exe | 92.123.16.55:443 | go.microsoft.com | Telia Company AB | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
njoopsday.website |
| suspicious |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.msn.com |
| whitelisted |
query.prod.cms.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2424 | IEXPLORE.EXE | Misc Attack | ET TOR Known Tor Exit Node Traffic group 142 |
2424 | IEXPLORE.EXE | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 142 |
320 | iexplore.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 142 |
320 | iexplore.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 142 |