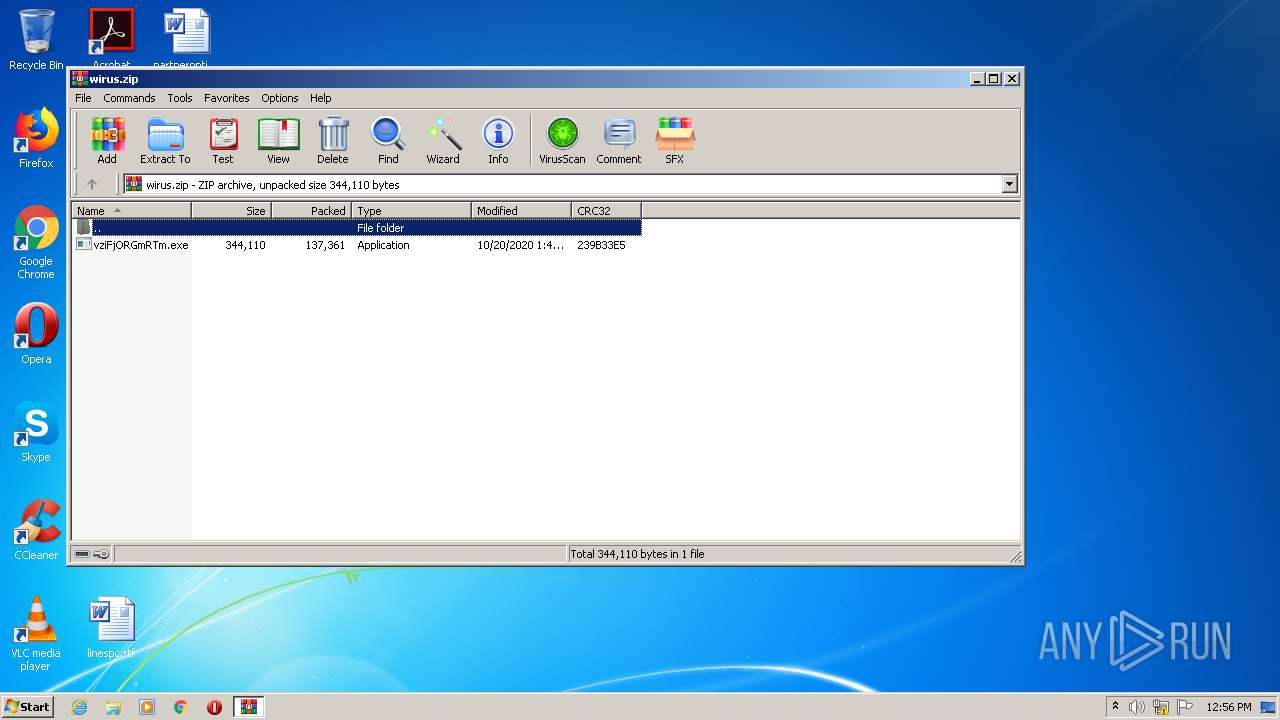
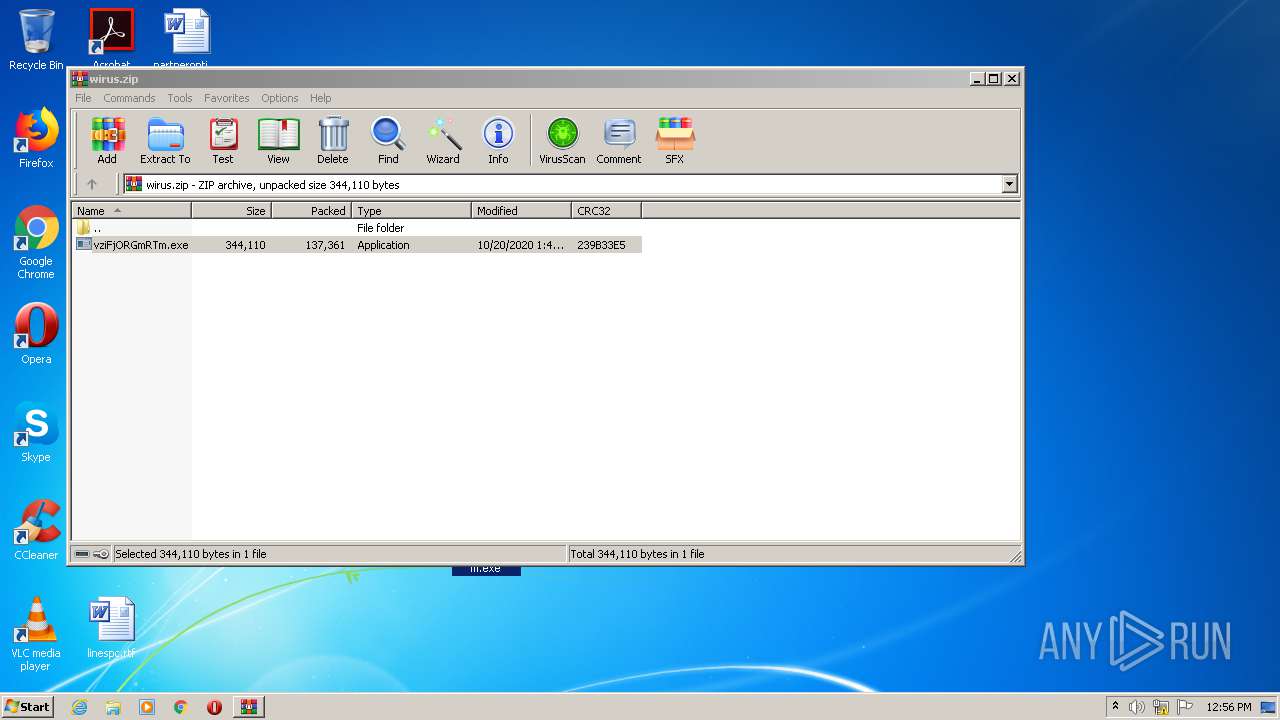
| File name: | wirus.zip |
| Full analysis: | https://app.any.run/tasks/dbf8fb0d-d05b-47b8-8747-a2785eb1985f |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 11:55:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9028E94885758EB087B4C2DBE18272B4 |
| SHA1: | 10284E1FAB3FC670480E6611F81A441F129E366E |
| SHA256: | 9DFABC6FFD041A6C71CBDCFB85D574ACF2A36CD6638D546A32E1BBB2D586FCDD |
| SSDEEP: | 3072:BG8QIi1h5pG3rZNn9FmB0LFDg3DR99c+4+DypuA:BAIi9o9FmFbB4Cs |
MALICIOUS
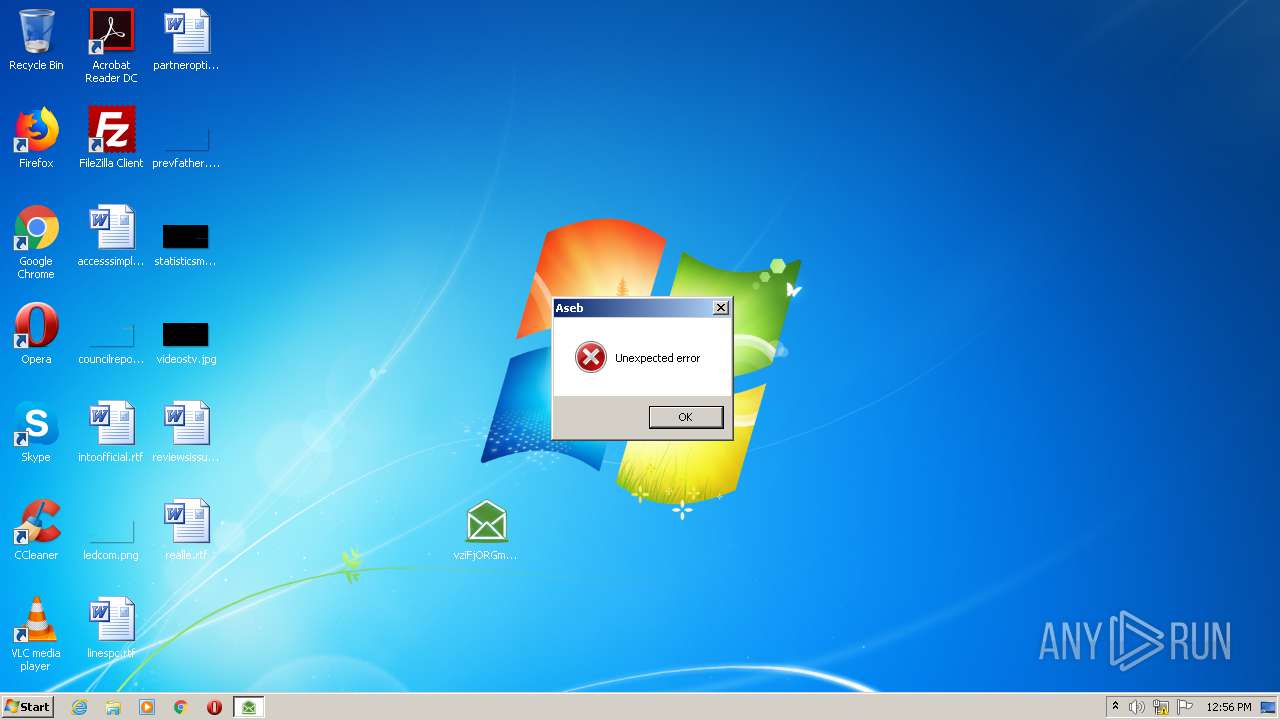
Application was dropped or rewritten from another process
- vziFjORGmRTm.exe (PID: 3512)
- vziFjORGmRTm.exe (PID: 2052)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2532)
INFO
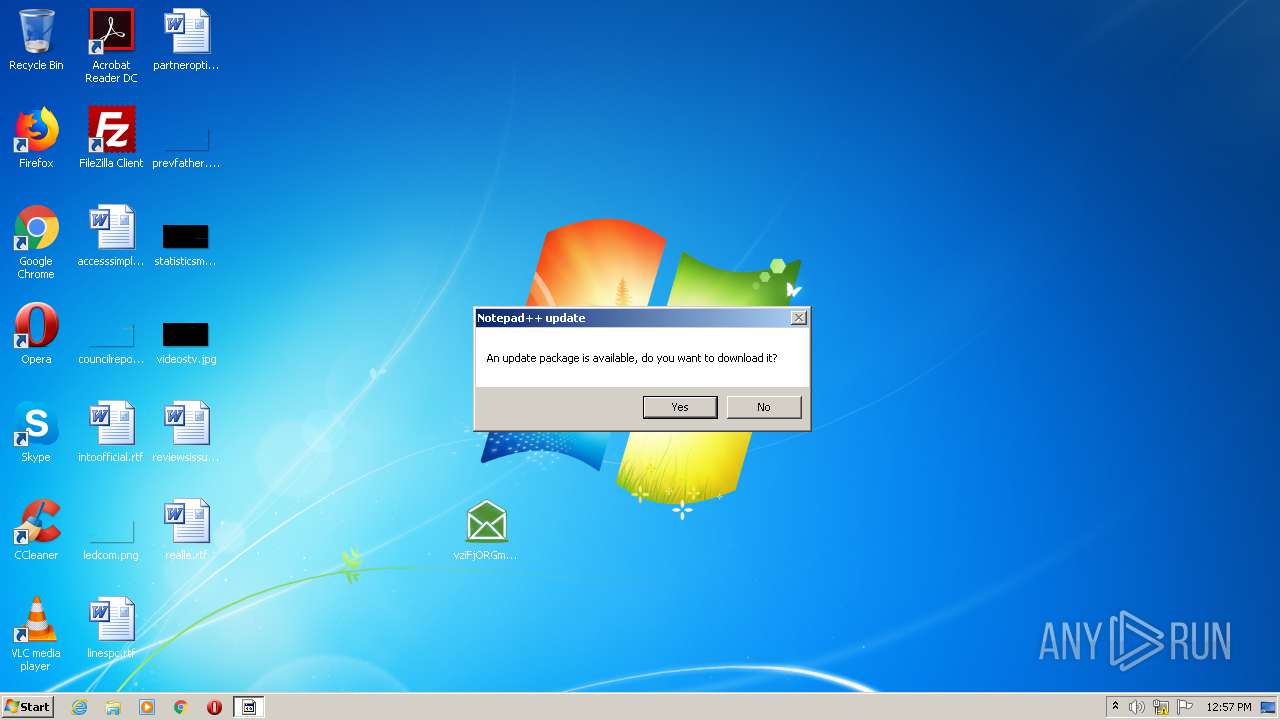
Manual execution by user
- vziFjORGmRTm.exe (PID: 3512)
- notepad++.exe (PID: 2492)
- vziFjORGmRTm.exe (PID: 2052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:10:20 13:49:27 |
| ZipCRC: | 0x239b33e5 |
| ZipCompressedSize: | 137361 |
| ZipUncompressedSize: | 344110 |
| ZipFileName: | vziFjORGmRTm.exe |
Total processes
41
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 612 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
| 2052 | "C:\Users\admin\Desktop\vziFjORGmRTm.exe" | C:\Users\admin\Desktop\vziFjORGmRTm.exe | — | explorer.exe | |||||||||||
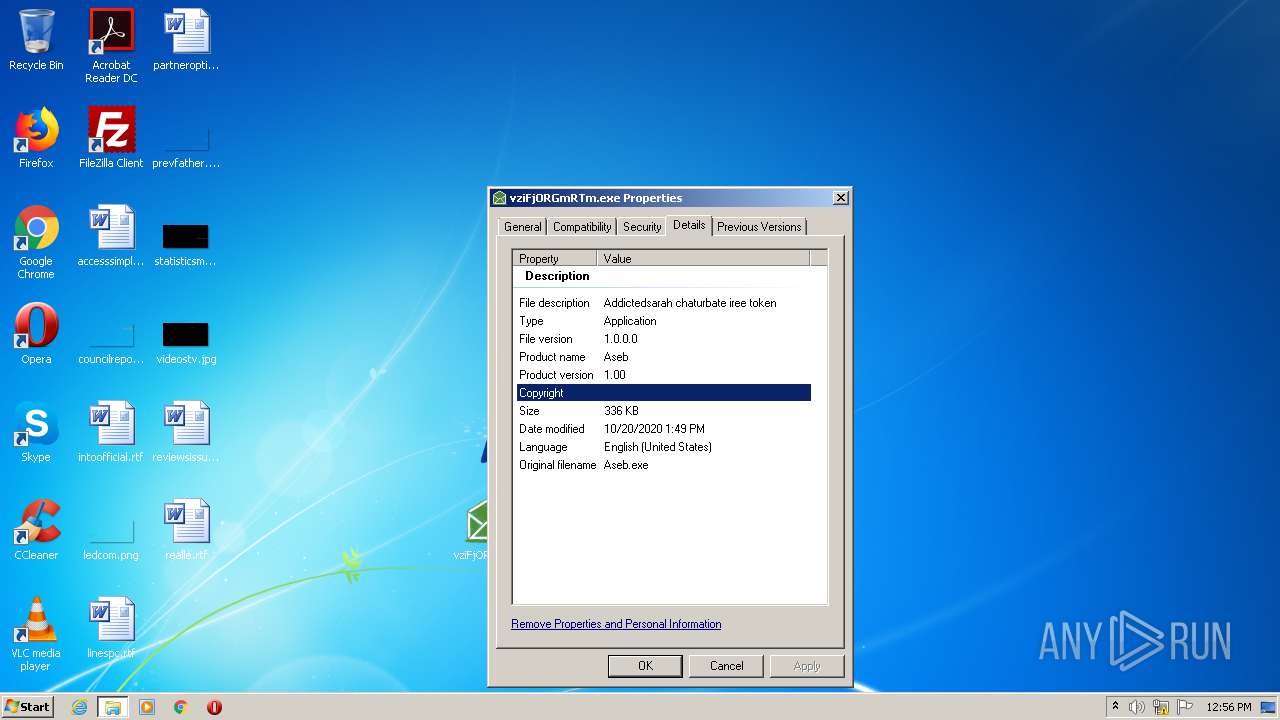
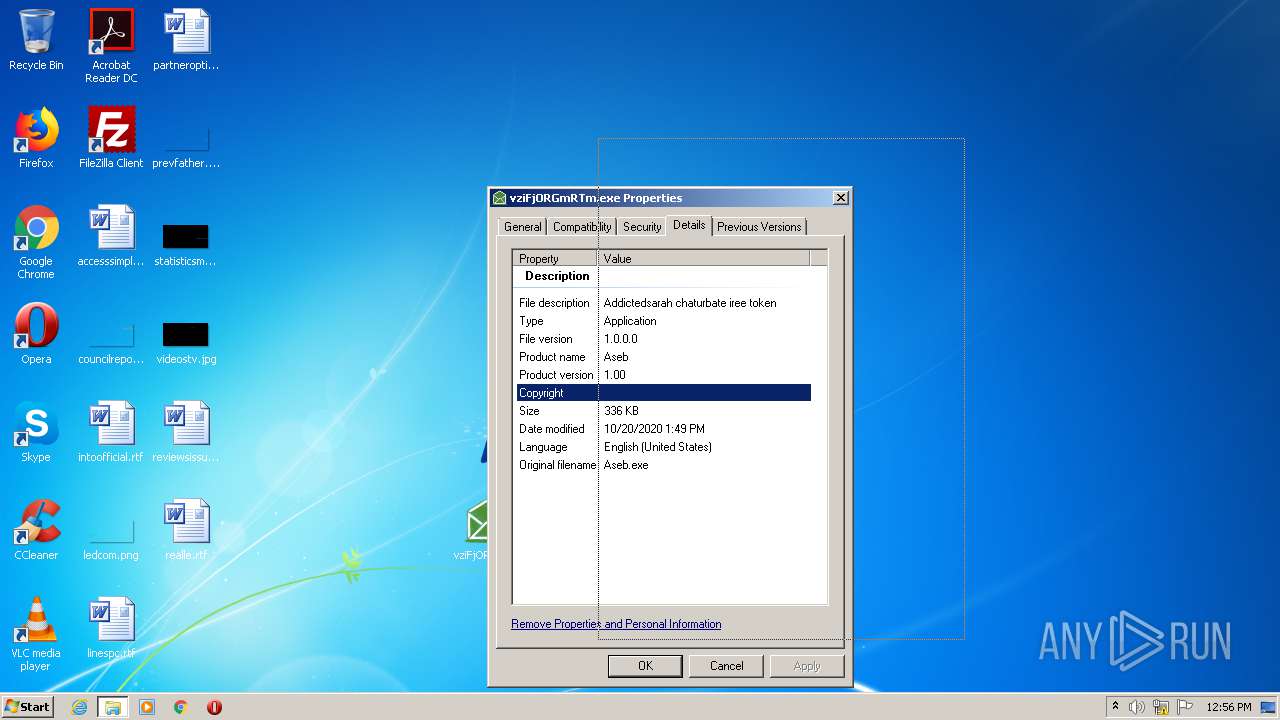
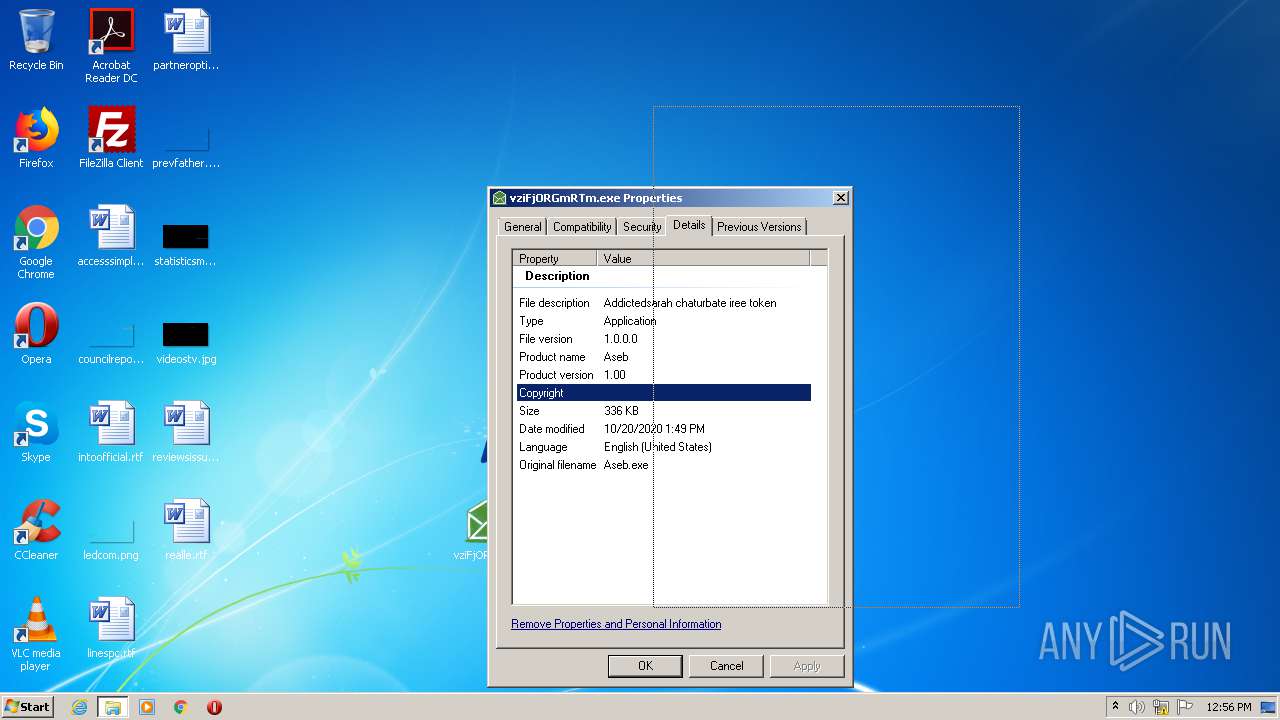
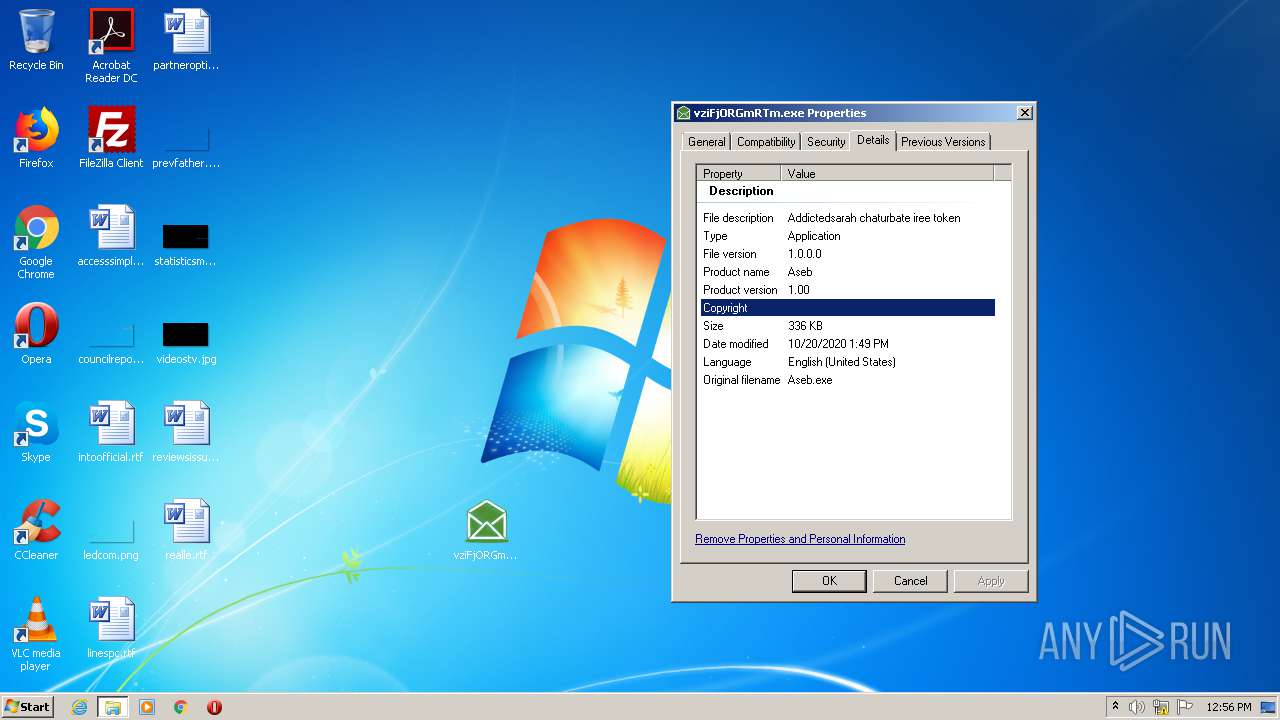
User: admin Company: Twenty Squares Integrity Level: MEDIUM Description: Addictedsarah chaturbate iree token Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
| 2492 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\vziFjORGmRTm.exe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2532 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\wirus.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3512 | "C:\Users\admin\Desktop\vziFjORGmRTm.exe" | C:\Users\admin\Desktop\vziFjORGmRTm.exe | — | explorer.exe | |||||||||||
User: admin Company: Twenty Squares Integrity Level: MEDIUM Description: Addictedsarah chaturbate iree token Exit code: 0 Version: 1.00 Modules
| |||||||||||||||
Total events
500
Read events
467
Write events
33
Delete events
0
Modification events
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\wirus.zip | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
| (PID) Process: | (2532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\AppData\Local\Temp | |||
Executable files
1
Suspicious files
0
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3512 | vziFjORGmRTm.exe | C:\Users\admin\AppData\Local\Temp\~DFBFDD8A4974737D37.TMP | — | |
MD5:— | SHA256:— | |||
| 2052 | vziFjORGmRTm.exe | C:\Users\admin\AppData\Local\Temp\~DF56C8DF4BA659A6C7.TMP | — | |
MD5:— | SHA256:— | |||
| 2532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa2532.31120\vziFjORGmRTm.exe | executable | |
MD5:— | SHA256:— | |||
| 2492 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:— | SHA256:— | |||
| 2492 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
3
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
612 | gup.exe | 172.67.218.84:443 | notepad-plus-plus.org | — | US | malicious |
612 | gup.exe | 104.31.89.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|